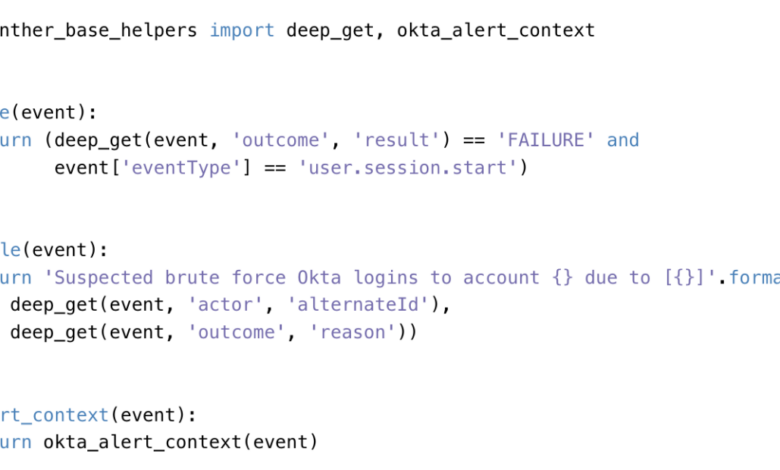
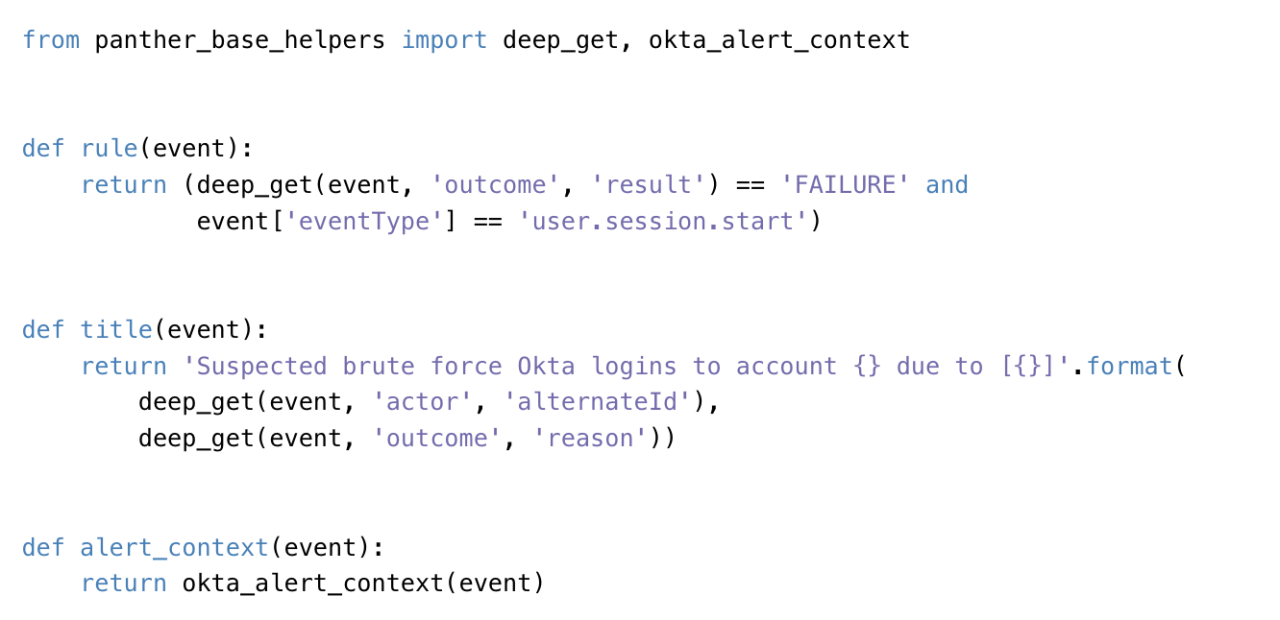
5 Benefits of Detection as Code
5 Benefits of Detection as Code: Ever felt like your security systems are playing catch-up with the ever-evolving threat landscape? Traditional methods often struggle to keep pace, leaving gaping holes in your defenses. But what if I told you there’s a better way? Enter “Detection as Code,” a revolutionary approach that’s transforming how we think about security.
This isn’t just about tweaking existing systems; it’s about building a more robust, adaptable, and efficient security posture from the ground up. Let’s dive into five compelling reasons why you should consider this game-changer.
Imagine a world where your security rules are as easily managed as your website’s codebase. That’s the promise of Detection as Code. By treating detection rules as code, we unlock a whole new level of automation, collaboration, and scalability. This means less manual effort, fewer errors, and a significantly stronger defense against cyber threats. We’ll explore how this approach improves accuracy, enhances collaboration, boosts efficiency, scales effortlessly, and ultimately strengthens your overall security posture.
Enhanced Collaboration and Maintainability

Detection-as-code transforms the way security teams manage detection rules, moving away from siloed, manually-maintained systems to a collaborative, version-controlled environment. This shift dramatically improves maintainability and allows for faster response times to emerging threats. The benefits extend beyond simple rule management; it fosters a culture of shared responsibility and continuous improvement within the security team.This approach leverages the power of collaborative development platforms like Git, enabling multiple team members to contribute, review, and refine detection rules concurrently.
This shared responsibility reduces the burden on any single individual and fosters a more robust and resilient detection system. Furthermore, the version control inherent in these systems allows for easy tracking of changes, facilitating rollback to previous versions if needed and providing a clear audit trail for regulatory compliance.
Version Control and Collaborative Editing Best Practices
Effective version control is paramount to successful detection-as-code implementation. Employing a robust branching strategy within Git, such as Gitflow, allows for parallel development of new rules and features without disrupting the main production branch. Pull requests provide a formal mechanism for code review, ensuring that changes are thoroughly vetted before deployment. Clear and concise commit messages are essential for tracking the rationale behind modifications.
Regular integration and testing of changes prevent the accumulation of conflicts and ensure a stable, reliable system. Furthermore, using a standardized coding style guide ensures readability and maintainability across all detection rules.
Simplified Updating and Maintenance of Detection Logic
The ability to easily update and maintain detection logic is a cornerstone of detection-as-code. Instead of manually modifying complex configurations, changes are made through code, which is then subject to the rigorous review and testing processes already established. This streamlined process significantly reduces the risk of errors and allows for rapid deployment of updated rules, improving the overall responsiveness of the security system.
For example, consider a scenario where a new malware variant emerges. With detection-as-code, a security analyst can quickly write a new detection rule, submit it for review, and deploy it to the entire system with minimal disruption. This contrasts sharply with the lengthy, error-prone process often associated with manual rule updates.
Workflow Diagram for Updating Detection Rules
Imagine a simple workflow diagram. It begins with a “New Rule Request” box, representing the identification of a need for a new rule or an update to an existing one. This flows into a “Development Branch” box, where a developer creates a new branch from the main branch and implements the necessary changes. The next box is “Code Review,” where the changes are reviewed by peers for accuracy and adherence to coding standards.
Following this is a “Testing” box, where the updated rule is rigorously tested in a controlled environment. Finally, the updated rule is “Merged into Main Branch” and deployed to the production environment. This visual representation showcases the collaborative and controlled nature of updating detection rules within a detection-as-code framework. The entire process is transparent and traceable, minimizing errors and maximizing efficiency.
Increased Automation and Efficiency
Detection-as-code dramatically boosts efficiency by automating many traditionally manual tasks. This automation reduces human error, frees up security personnel for more strategic work, and allows for faster response times to emerging threats. The shift from reactive to proactive security is a key benefit.Automating testing and deployment streamlines the entire detection process. Instead of manually updating detection rules across multiple systems, changes are version-controlled, tested rigorously, and deployed automatically.
This ensures consistency, minimizes downtime, and reduces the risk of introducing errors during the update process.
Automated Testing and Deployment Processes
The core of detection-as-code lies in its ability to integrate seamlessly with existing CI/CD pipelines. This allows for automated testing of new and updated detection rules before deployment. Automated testing includes unit tests, integration tests, and even simulated attack scenarios to verify the effectiveness of the rules. Upon successful testing, the changes are automatically deployed to the relevant security tools, ensuring a smooth and consistent update process.
This contrasts sharply with traditional methods where updates often involve manual intervention at multiple stages, increasing the risk of human error and delays.
Tools and Technologies for Detection-as-Code
Implementing detection-as-code requires leveraging several tools and technologies. A robust selection allows for flexibility and scalability depending on specific organizational needs.
- Version Control Systems (e.g., Git): Essential for tracking changes, collaborating on rules, and managing different versions of detection logic.
- Infrastructure as Code (IaC) tools (e.g., Terraform, Ansible): Used to automate the provisioning and management of security infrastructure.
- CI/CD pipelines (e.g., Jenkins, GitLab CI, Azure DevOps): Automate the testing and deployment of detection rules.
- Security Information and Event Management (SIEM) systems (e.g., Splunk, QRadar, Elastic Stack): Centralized platforms for collecting, analyzing, and responding to security events, often integrated with detection-as-code workflows.
- Security Orchestration, Automation, and Response (SOAR) platforms (e.g., Palo Alto Networks Cortex XSOAR, IBM Resilient): Automate security workflows, including incident response based on detection rules.
Comparison of Traditional and Detection-as-Code Updates, 5 benefits of detection as code
The following table highlights the stark contrast in time and resource consumption between traditional methods and detection-as-code approaches. These values are estimates based on common industry experiences and can vary depending on the complexity of the detection rules and the size of the organization.
| Task | Traditional Time | Traditional Resources | Detection-as-Code Time | Detection-as-Code Resources |
|---|---|---|---|---|
| Creating a new detection rule | 1-2 days | 1-2 Security Analysts | 1-4 hours | 1 Security Analyst |
| Testing a new detection rule | 0.5-1 day | 1 Security Analyst | 1-2 hours | Automated testing |
| Deploying a new detection rule | 0.5-1 day | 1-2 System Administrators | < 1 hour | Automated deployment |
| Updating an existing detection rule | 0.5-1 day | 1 Security Analyst | 1-2 hours | 1 Security Analyst (minimal intervention) |
Scalability and Reusability

Detection-as-code offers significant advantages in scaling security operations and reusing valuable detection components. This approach moves away from manually creating and maintaining individual detection rules, allowing for a more efficient and adaptable security posture, particularly crucial in today’s dynamic threat landscape.Detection-as-code allows for scaling detection efforts to handle the ever-increasing volume of data generated by modern systems and the constantly evolving nature of cyber threats.
Instead of manually adjusting individual rules across multiple systems, changes are made in a central, version-controlled repository. This ensures consistency and reduces the risk of errors. Furthermore, the automation inherent in detection-as-code enables rapid deployment of new detections or updates to existing ones, crucial for responding quickly to emerging threats.
So, I’ve been diving into the 5 benefits of detection as code lately – it’s a game-changer for security! The improved efficiency and automation are amazing, especially when you consider how it integrates with modern development. For example, thinking about the future of app development, check out this insightful article on domino app dev the low code and pro code future to see how these approaches are evolving.
Ultimately, understanding these advancements helps us better appreciate the power of detection as code in building robust and secure applications.
Modular Design Advantages
A modular design is key to the scalability and reusability of detection-as-code. By breaking down complex detection logic into smaller, independent modules, we create reusable components that can be easily combined and adapted for different systems or use cases. This modularity promotes better organization, simplifies maintenance, and reduces the overall complexity of the detection system. Changes to one module do not necessitate widespread changes across the entire system, minimizing the risk of introducing errors and improving overall efficiency.
For example, a module detecting suspicious login attempts can be reused across various platforms, simply by adapting the specific data sources and logging formats.
Reusable Detection Components
Several reusable detection components can be easily adapted for different systems or use cases. For instance, a module designed to identify unusual file access patterns could be applied to both Windows and Linux servers, requiring only minor adjustments to account for operating system-specific log formats. Similarly, a module detecting anomalous network traffic could be used across various network devices, including firewalls and intrusion detection systems.
This reuse significantly reduces development time and effort while ensuring consistency in detection capabilities across diverse environments.
Reusability Across Platforms
The following table illustrates how a modular approach facilitates the reuse of detection components across different platforms or systems.
| Component | Platform 1 (Windows Server) | Platform 2 (Linux Server) | Platform 3 (Cloud Platform – AWS) |
|---|---|---|---|
| Suspicious Login Attempts | Uses Windows event logs | Uses syslog and auth.log | Uses CloudTrail logs |
| Unusual File Access | Uses Windows file system auditing | Uses auditd logs | Uses CloudWatch logs |
| Anomalous Network Traffic | Uses Windows firewall logs | Uses iptables logs | Uses AWS Flow Logs |
Improved Security Posture
Adopting a detection-as-code approach significantly bolsters an organization’s security posture by shifting security detection from a reactive, manual process to a proactive, automated, and version-controlled system. This allows for more consistent, reliable, and repeatable security monitoring, ultimately reducing the risk of breaches and improving incident response times. The inherent repeatability and auditability of code also significantly improves compliance efforts.Detection-as-code facilitates the creation of reusable and easily maintainable security detection rules.
This ensures that security monitoring remains effective even as systems and environments evolve. This proactive approach is a key differentiator from traditional, often ad-hoc, security monitoring strategies.
Mitigating Security Vulnerabilities with Detection-as-Code
By codifying security detection logic, organizations can proactively address a wide range of vulnerabilities. For instance, a code-based approach can readily detect suspicious network activity, such as unusual login attempts or data exfiltration attempts, by analyzing network logs for patterns indicative of malicious behavior. Similarly, it can identify anomalies in system logs, flagging unusual process executions or file modifications that might signal malware infections or unauthorized access.
The consistent application of these coded detection rules minimizes the chances of overlooking critical security events, regardless of the scale or complexity of the environment.
Automated Testing and Continuous Integration for Enhanced Security
Automated testing and continuous integration (CI/CD) pipelines play a crucial role in improving the security of detection logic. Automated tests, such as unit tests and integration tests, verify the accuracy and effectiveness of the detection rules before they are deployed into production environments. This prevents the deployment of faulty or ineffective rules that could lead to false positives or missed threats.
The CI/CD pipeline automates the process of building, testing, and deploying the detection logic, ensuring that updates are rolled out quickly and efficiently while maintaining a high level of security. This streamlined process reduces human error and significantly shortens the time it takes to respond to emerging threats.
Hypothetical Security Incident and Improved Response with Detection-as-Code
Imagine a scenario where a sophisticated phishing campaign targets an organization. Traditional security monitoring might rely on manual analysis of security logs, potentially leading to delayed detection of the breach. With detection-as-code, however, pre-defined rules could immediately flag suspicious login attempts from unusual locations or devices. These alerts would trigger automated responses, such as blocking access and initiating incident response protocols, all within minutes of the initial attack.
The automated nature of detection-as-code would dramatically reduce the time to detection and response, minimizing the potential damage caused by the attack. The entire process, from detection to response, would be documented and auditable, providing valuable insights for future improvements to the security posture.
Final Wrap-Up
So, there you have it – five compelling reasons to embrace Detection as Code. From enhanced accuracy and seamless collaboration to increased automation and improved scalability, the benefits are undeniable. By adopting this modern approach, you’re not just improving your security; you’re building a future-proof system that can adapt to the ever-changing landscape of cyber threats. It’s about moving beyond reactive security measures and embracing a proactive, code-driven approach that empowers your team and strengthens your defenses.
Ready to revolutionize your security strategy? Let’s get coding!
Detailed FAQs: 5 Benefits Of Detection As Code
What are some examples of tools used in Detection as Code?
Popular tools include Git for version control, CI/CD pipelines (like Jenkins or GitLab CI), and various security information and event management (SIEM) systems that support scripting or API integrations.
How does Detection as Code handle false positives?
Because detection rules are code, you can test them rigorously, reducing false positives. Automated testing and continuous integration help identify and address these issues early in the development cycle.
Is Detection as Code suitable for small organizations?
Absolutely! While larger organizations may benefit from more advanced implementations, the core principles of Detection as Code – automation, collaboration, and version control – are valuable regardless of size.
What about training for my team?
Transitioning to Detection as Code often requires upskilling your team in scripting and DevOps practices. Many online resources and training courses are available to help bridge the knowledge gap.