Fake COVID Papers Darknets Passport to Freedom
Canadian Healthcares Identity Theft Crisis
F1000 Biotech Firm Bio Rad Selects CloudPassage 2
Google to Offer Cybersecurity Warning for Insecure Forms
European Ecommerce Market Booms Marketplaces are King
France Slaps €210m Fine on Facebook and Google
Cybersecurity Startup Resonance Secures Funding
Harnessing the Power of Implicit Intent
Change Your Password Day A Cybersecurity Message
Installing Z and I Emulator for Web
Answering Key Business Questions As You Go Digital
How Citizen Developers Stop Development Lifecycle Traffic Jams
Australian Citizen Runs $220M Dark Web Operation
Becoming Digital Enablement and Collaboration
BlackSwan Vulnerability Risks Billions of Windows Systems
How to Make the Most Out of ODI Plugin in Workload Automation
Recent Posts
-
Dec- 2025 -12 DecemberNetworking & Security

How to Quickly Integrate Your SD-WAN with Bitglass
How to quickly integrate your sd wan with bitglass – How to quickly integrate your…
Read More » -
11 DecemberCareer Development

How to Progress in Your Cybersecurity Career
How to progress in your cybersecurity career is a journey, not a sprint. From entry-level…
Read More » -
11 DecemberOnline Security

How to Prevent Social Media Data Leak
How to prevent social media data leak is crucial in today’s digital landscape. Protecting your…
Read More » -
10 DecemberBusiness Management

How to Plan for Data Recovery A Comprehensive Guide
How to plan for data recovery is crucial for any organization. Data loss can cripple…
Read More » -
9 DecemberCybersecurity
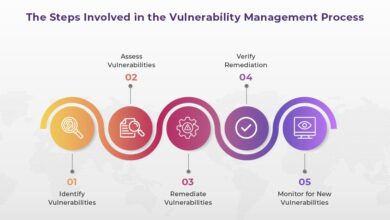
Future-Proofing Vulnerability Management
How to prepare for the future of vulnerability management is crucial in today’s rapidly evolving…
Read More » -
9 DecemberDigital Marketing

How to Overcome Cybersecurity Challenges in Digital Marketing
How to overcome cybersecurity challenges in digital marketing is crucial in today’s online landscape. Protecting…
Read More » -
8 DecemberCybersecurity

Negotiating Ransomware Attacks A Guide
How to negotiate ransomware attacks a strategic guide sets the stage for understanding the complex…
Read More » -
7 DecemberTechnology

How to Make Your Smartphone Private
How to make your smartphone private? This guide delves into crucial steps to protect your…
Read More » -
7 DecemberCybersecurity

How to Make Threat Intelligence Practical
How to make threat intelligence practical for your organization is crucial in today’s complex digital…
Read More » -
6 DecemberRemote Work

How to Make Remote Work Easy A Complete Guide
How to make remote work easy? This guide dives deep into the essential elements for…
Read More » -
6 DecemberCybersecurity
How to Make 5 Million a Day in Cybercrime A Risky Proposition
How to make 5 million a day in cybercrime? This is a tempting question, but…
Read More » -
5 DecemberFinancial Services
How to Make KYC Compliance Less Difficult for Banks
How to make KYC compliance less difficult for banks is a critical issue for financial…
Read More »