5 Steps to Resolve an SMB Attack
5 Steps to Resolve an SMB Attack: Ever felt that sinking feeling when you suspect a security breach? SMB attacks can be terrifying, but knowing how to react quickly and effectively can minimize the damage. This guide walks you through a five-step process to neutralize an SMB attack, from identifying the intrusion to restoring your systems and data.
We’ll cover everything from spotting the telltale signs of an attack to implementing robust security measures to prevent future incidents. Get ready to become a cybersecurity ninja!
This post isn’t just about theoretical knowledge; it’s a practical guide designed to help you navigate the crisis. We’ll cover identifying the attack through analyzing network traffic and logs, isolating the infected system to prevent further spread, and then systematically eradicating the malware. We’ll also explore crucial steps to reinforce your security posture, including patching vulnerabilities, strengthening passwords, and leveraging firewalls.
Finally, we’ll look at data recovery and system restoration, ensuring you get back to business as usual as quickly as possible. Let’s dive in!
Identify the SMB Attack
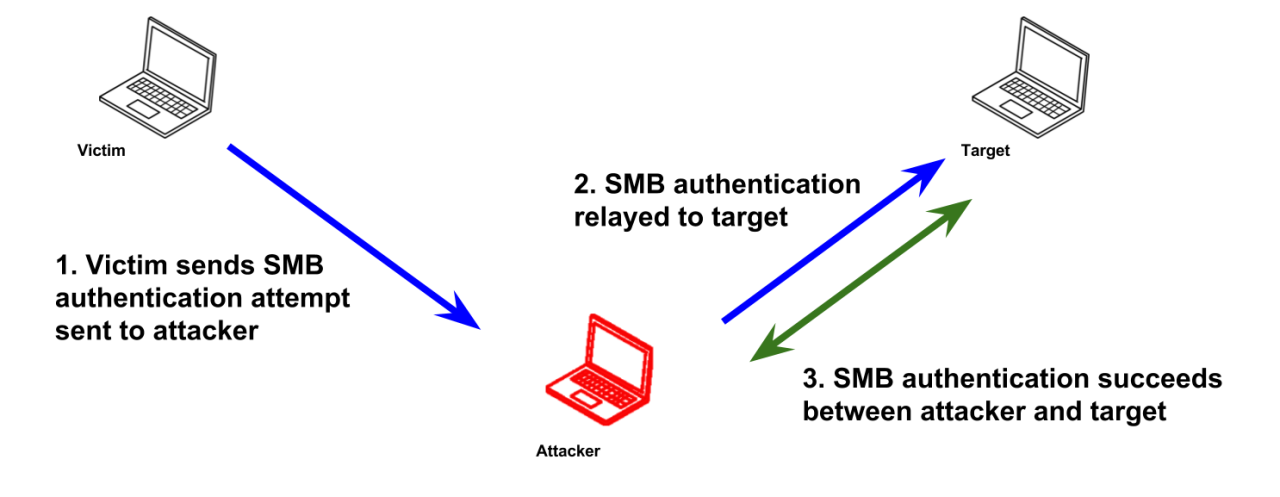
Detecting an SMB attack requires a proactive approach, combining real-time monitoring with post-incident analysis. Understanding the common indicators and employing effective detection methods are crucial for minimizing damage and ensuring a swift recovery. This section details the key steps in identifying an SMB attack.
Common Indicators of Compromise (IOCs)
Several signs indicate a potential SMB attack. These IOCs can manifest in unusual network activity, suspicious log entries, or performance degradation. For instance, a sudden surge in SMB traffic originating from an unexpected source or involving unusual ports might suggest malicious activity. Similarly, a large number of failed login attempts targeting SMB shares, especially from external IP addresses, is a strong indicator of a brute-force attack.
Unusual file access patterns, such as mass file creation or deletion on shared drives, also warrant immediate investigation. Finally, the presence of malware known to exploit SMB vulnerabilities, like EternalBlue, should trigger a thorough security review.
Methods for Detecting Unauthorized SMB Connections
Detecting unauthorized SMB connections relies on a multi-layered approach involving network monitoring tools, intrusion detection systems (IDS), and security information and event management (SIEM) systems. Network monitoring tools can capture and analyze network traffic, identifying suspicious SMB connections based on their source, destination, and frequency. IDSs can be configured to alert on unusual SMB activity, such as connections from blocked IP addresses or attempts to access restricted shares.
SIEM systems consolidate security logs from various sources, allowing security analysts to identify patterns and anomalies indicative of an SMB attack. Implementing proper network segmentation and access control lists (ACLs) further restricts unauthorized access to SMB shares.
Analyzing Network Traffic to Pinpoint the Source and Scope
Analyzing network traffic is essential to determine the source, scope, and impact of an SMB attack. Tools like Wireshark can capture and dissect SMB packets, revealing details such as the source and destination IP addresses, the type of SMB request, and the files accessed. This analysis can help pinpoint the attacker’s origin and identify compromised systems. Correlation with other security logs, such as authentication logs and file system logs, can further illuminate the attack’s scope and impact.
By examining the content of SMB packets, analysts can determine whether data exfiltration or malware deployment occurred.
Examples of Log Entries Indicating SMB Attacks
Analyzing logs is crucial for identifying both successful and attempted SMB attacks. Below is a table illustrating potential log entries. Note that the exact format will vary depending on the logging system used.
| Timestamp | Source IP | Destination IP | Event Description |
|---|---|---|---|
| 2024-10-27 10:00:00 | 192.168.1.100 | 192.168.1.1 | Successful SMB connection from an unknown device. |
| 2024-10-27 10:01:30 | 172.217.160.142 | 192.168.1.1 | Multiple failed SMB login attempts from a known malicious IP address. |
| 2024-10-27 10:05:00 | 192.168.1.100 | 192.168.1.1 | Large file transfer detected via SMB to an external IP address. |
| 2024-10-27 10:10:00 | 192.168.1.100 | 192.168.1.1 | Access denied attempt to a sensitive SMB share. |
Isolate the Infected System
Containing the spread of an SMB attack is paramount. Once you’ve identified the infected system, your immediate priority is to isolate it from the rest of your network to prevent the malware from spreading to other machines and causing further damage. This isolation process involves several key steps, all designed to minimize the impact of the attack and facilitate a more thorough cleanup.Network segmentation is a critical defense strategy.
By dividing your network into smaller, isolated segments, you limit the blast radius of a successful attack. If one segment is compromised, the others remain protected. This is far superior to a flat network architecture where a single breach can compromise the entire system. The process of isolating the infected system will reinforce this principle.
Network Disconnection Procedures
Safely disconnecting a compromised machine requires a methodical approach. First, physically disconnect the Ethernet cable from the infected machine. This immediate action prevents any further network communication. If the machine is wirelessly connected, disable the wireless adapter through the operating system, followed by physically switching off the device’s wireless capabilities if possible (e.g., turning off the Wi-Fi router or the wireless card itself).
Avoid using remote shutdown commands, as this could inadvertently execute malicious code and further compromise the system. After disconnecting, immediately change the passwords of any network devices that were compromised. This includes routers, switches, and firewalls.
Network Segmentation Implementation
Implementing network segmentation involves using firewalls, VLANs (Virtual LANs), and other network devices to create isolated network segments. For example, you might separate your critical servers onto a dedicated VLAN, keeping them isolated from less critical workstations. In the context of an SMB attack, once the infected machine is identified, it should be immediately moved (virtually, using VLANs, or physically, using network switches) to a quarantined network segment.
This isolated segment should have limited or no access to other parts of your network, including critical data stores and servers. This prevents the malware from spreading laterally.
Internet Disconnection
Disconnecting the infected system from the internet is crucial to prevent the attacker from accessing the system remotely, exfiltrating data, or receiving further commands. Simply disconnecting the Ethernet cable or disabling Wi-Fi will suffice in most cases. This prevents further communication with command-and-control servers that the malware might be communicating with.
Data Loss Prevention During Isolation
While isolating the infected system is crucial, it’s also important to consider data loss prevention. Before disconnecting the machine, if possible and safe to do so, consider backing up any crucial data that might be present on the machine. However, exercise extreme caution; only do this if you are confident the backup process won’t further compromise the system. If the system is heavily compromised, attempting a backup might spread the malware further.
In such scenarios, prioritize system isolation and investigate data recovery options after the system has been fully sanitized. A professional data recovery service might be necessary in extreme cases.
Eradicate the Malware
After successfully isolating the infected system, the next crucial step is to completely remove the malware responsible for the SMB attack. This involves a multi-pronged approach, combining automated tools with potentially manual intervention, depending on the severity and type of malware. Remember, data loss is a real possibility, highlighting the importance of having a recent, reliable backup.
The eradication process requires a careful and methodical approach to ensure complete removal and prevent reinfection. Failing to completely remove the malware can lead to persistent vulnerabilities and future attacks. This section details the steps involved in eliminating the threat and restoring your system to a secure state.
Antivirus Software and Security Tool Usage
Effective malware removal often begins with your antivirus software. A comprehensive scan in safe mode (disabling non-essential startup programs to prevent malware interference) is the first step. Safe mode boots Windows with minimal drivers and services, making it harder for the malware to hide or interfere with the scan. After the scan completes, carefully review the results and follow the software’s instructions for quarantine or removal.
If your existing antivirus software fails to identify or remove the malware, consider using a secondary, reputable anti-malware tool for a second opinion scan. These tools often employ different detection methods and can uncover threats missed by the primary antivirus. For instance, Malwarebytes is a popular and effective secondary scanner. Remember to run these tools in safe mode as well.
Manual Malware Removal
In some cases, automated tools may not be sufficient. Advanced malware often requires manual removal, a process that involves identifying and deleting infected files and registry entries. This requires a deep understanding of the operating system and malware behavior. It is crucial to proceed with extreme caution during manual removal. A single incorrect action could damage your system beyond repair.
Consult online resources and guides specific to the identified malware for detailed instructions. If you’re unsure, seeking professional help from a cybersecurity expert is strongly recommended. This method is generally not advised for users without significant technical expertise. Improper manual removal can worsen the situation.
System File Restoration from Backups, 5 steps to resolve an smb attack
Restoring your system from a known-good backup is often the most efficient and safest way to completely eradicate the malware and return your system to a pre-infection state. This method bypasses the complexities of manual malware removal and significantly reduces the risk of residual threats. Before initiating a restore, ensure the backup is indeed from a timebefore* the SMB attack.
Verify the integrity of the backup to ensure it is complete and uncorrupted. Follow the instructions provided by your backup software to restore the system to its previous state. This may involve reinstalling the operating system and applications.
Comparison of Malware Removal Techniques
Automated solutions, such as antivirus and anti-malware software, provide a convenient and often effective method for malware removal. They are generally user-friendly and require minimal technical expertise. However, they may not be successful against sophisticated or deeply entrenched malware. Manual removal offers a more precise approach but requires significant technical skills and carries a higher risk of system damage if not performed correctly.
Restoring from backups provides the most comprehensive and secure solution, effectively eliminating all traces of the malware but relies on having a valid and accessible backup. The choice of method depends on the specific situation, the type of malware involved, and the user’s technical capabilities. A hybrid approach, combining automated scans with manual removal or system restore, may be the most effective strategy in many cases.
Reinforce Security Measures
After successfully identifying, isolating, and eradicating the SMB attack, the next crucial step is to bolster your network’s security to prevent future incidents. This involves implementing robust security measures that address vulnerabilities exploited by the attack and strengthen your overall defense posture. Proactive security is far more effective and cost-efficient than reactive remediation.Strengthening your defenses involves a multi-pronged approach focusing on patching, authentication, and network security appliances.
Ignoring these steps leaves your system vulnerable to repeat attacks or exploitation via other vulnerabilities. Remember, a single point of weakness can compromise the entire system.
Patching and Updating Vulnerable Systems
Regular patching and updating of all systems, including operating systems, applications, and firmware, is paramount. Outdated software often contains known vulnerabilities that attackers actively exploit. Patches often address these security flaws, minimizing the attack surface. A comprehensive patching strategy should include automated updates wherever possible, regular security scans to identify outdated software, and a strict schedule for applying critical patches.
Failing to patch known vulnerabilities increases the likelihood of future attacks, potentially leading to data breaches and significant financial losses. For example, the WannaCry ransomware attack in 2017 exploited a known vulnerability in older versions of Windows that Microsoft had already patched. Organizations that hadn’t applied the patch were severely affected.
Strong Passwords and Multi-Factor Authentication
Weak passwords are a significant security risk. Implementing strong password policies, including password complexity requirements (length, character types), and enforcing regular password changes significantly reduces the risk of unauthorized access. However, even strong passwords can be compromised. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile app or security token.
MFA makes it exponentially harder for attackers to gain access even if they obtain a password. For instance, imagine an attacker obtaining a user’s password through phishing. With MFA, they still need to overcome the second authentication factor, rendering the stolen password useless.
Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS)
Firewalls act as a gatekeeper, controlling network traffic in and out of your system. They filter malicious traffic based on predefined rules, blocking unauthorized access attempts. Intrusion Detection/Prevention Systems (IDS/IPS) monitor network traffic for malicious activity, identifying and blocking or alerting on suspicious patterns. A robust firewall and IDS/IPS combination provides a layered defense, detecting and mitigating threats before they can cause significant damage.
Proper configuration of these systems is crucial; a poorly configured firewall can leave vulnerabilities exposed. Consider a scenario where a firewall isn’t properly configured to block SMB traffic from untrusted sources. This could allow an attacker to easily penetrate the network.
Security Recommendations to Prevent Future SMB Attacks
Before listing the recommendations, it’s important to understand that a layered security approach is essential. No single measure guarantees complete protection; instead, multiple layers work together to provide robust security. The following recommendations, when implemented together, significantly reduce the risk of future SMB attacks.
- Implement a robust patching and updating schedule for all systems.
- Enforce strong password policies and mandatory multi-factor authentication.
- Deploy and properly configure firewalls and intrusion detection/prevention systems.
- Regularly conduct security audits and vulnerability assessments.
- Educate users about phishing and social engineering techniques.
- Segment your network to limit the impact of a breach.
- Enable network access control (NAC) to ensure only authorized devices can connect to the network.
- Implement proper logging and monitoring to detect suspicious activity.
- Regularly back up your data to a secure offsite location.
- Develop and test an incident response plan.
Recover Data and Restore Systems

After successfully eradicating the malware and reinforcing your security measures, the final crucial step in recovering from an SMB attack is restoring your data and systems to their pre-attack state. This process requires careful planning, execution, and verification to ensure business continuity and data integrity. A methodical approach is vital to minimize downtime and potential data loss.Data recovery and system restoration are not simply about getting things back online; it’s about ensuring everything is back to a secure and reliable state.
This involves not just retrieving files, but verifying their integrity and ensuring the systems are patched and hardened against future attacks. This process requires a well-defined plan and a clear understanding of your backup strategy and system architecture.
Data Recovery from Backups
The cornerstone of effective data recovery is a robust and regularly tested backup strategy. Ideally, you should have multiple backups stored in different locations, utilizing both on-site and off-site storage. This redundancy protects against data loss due to physical damage or ransomware encryption. The recovery process begins by identifying the most recent clean backup, which predates the SMB attack.
This backup should then be verified for completeness and integrity before restoration commences. The type of backup (full, incremental, differential) will influence the recovery time and steps involved. For instance, a full backup will be faster to restore but requires more storage space, whereas incremental backups take longer to restore but consume less storage.
System Restoration to Pre-Attack State
Restoring systems to their pre-attack state involves reinstalling the operating system and applications from known good images, followed by the restoration of data from the verified backups. This ensures that no remnants of the malware remain on the system. Before restoring the data, it’s crucial to thoroughly scan the restored system for any lingering malware. This often involves using multiple antivirus and anti-malware tools.
System configuration files should also be restored from backup, ensuring that all settings are returned to their pre-attack configuration. A phased approach, starting with critical systems and then moving to less critical ones, is recommended.
Validating Restored Data Integrity
Simply restoring data doesn’t guarantee its integrity. After restoring data, it’s vital to verify its completeness and accuracy. This can involve checksum verification, comparing file sizes and modification dates against the pre-attack versions, or using specialized data integrity tools. For critical databases, database consistency checks are crucial. This step ensures that no data corruption occurred during the backup or restoration process, and that the restored data is indeed usable and reliable.
If inconsistencies are found, further investigation is required to identify the source of the problem and potentially recover data from an earlier backup.
Data Recovery and System Restoration Plan
A well-defined plan is essential for efficient and effective recovery. This plan should Artikel responsibilities, timelines, and procedures.A simplified flowchart illustrating the process:
1. Identify the most recent clean backup
This step involves reviewing backup logs and metadata to determine the latest backup that predates the SMB attack. Responsibility: IT Administrator. Timeline: Within 1 hour of attack identification.
2. Verify backup integrity
This involves checking checksums and performing data consistency checks. Responsibility: IT Administrator. Timeline: 2-4 hours.
3. Restore critical systems
Prioritize restoring systems essential for business operations. Responsibility: System Administrator. Timeline: 4-8 hours.
4. Restore non-critical systems
Restore remaining systems in a phased approach. Responsibility: System Administrator. Timeline: 8-24 hours.
5. Validate data integrity
Verify the accuracy and completeness of restored data. Responsibility: Data Integrity Specialist. Timeline: 24-48 hours.
6. Post-recovery security assessment
Conduct a thorough security review to identify vulnerabilities. Responsibility: Security Analyst. Timeline: 48-72 hours.
Ultimate Conclusion
Successfully navigating an SMB attack requires a swift and methodical response. By following these five steps – identification, isolation, eradication, reinforcement, and recovery – you can significantly reduce the impact of a breach and bolster your overall security. Remember, prevention is key, but knowing how to respond effectively is equally crucial. This process isn’t just about fixing the immediate problem; it’s about learning from the experience and strengthening your defenses for the future.
So, take the time to review your security practices, stay updated on the latest threats, and empower yourself with the knowledge to confidently handle any future cybersecurity challenges. Stay safe out there!
Question Bank: 5 Steps To Resolve An Smb Attack
What are some common signs of an SMB attack that might go unnoticed?
Subtle signs can include unusually high network traffic, slow system performance, unexpected file changes, or unusual login attempts. Regularly monitoring system logs and network activity is crucial for early detection.
How do I choose the right malware removal tool?
Consider factors like reputation, compatibility with your operating system, and the type of malware detected. A combination of antivirus software and manual removal techniques might be necessary in some cases. Always back up your data before attempting any malware removal.
What if I don’t have backups?
Data recovery without backups is significantly more challenging and may not be completely successful. Consider professional data recovery services, but understand the potential costs and limitations. This highlights the critical importance of regular backups!