
7 Essential Security Tips to Identify Fake Mobile Apps
7 Essential Security Tips to Identify Fake Mobile Apps – Downloading the wrong app can be a real headache, leading to everything from annoying pop-ups to serious security breaches. In today’s app-saturated world, it’s more crucial than ever to be able to spot a fake app before it’s too late. This post will equip you with seven essential security tips to help you navigate the app stores safely and confidently, keeping your phone and your data protected.
We’ll cover everything from verifying developers to checking app permissions and reviews, so let’s dive in!
We’ll explore practical ways to verify app developers and publishers, analyze app permissions and reviews, and identify red flags like spelling errors and inconsistencies in online presence. Learning to use reputable antivirus software and sticking to official app stores are also key strategies we’ll discuss. By the end of this guide, you’ll be better prepared to make informed decisions about which apps you download, significantly reducing your risk of encountering malicious software.
Verify App Developers and Publishers

Downloading apps from untrusted sources can expose your device to malware and data breaches. Therefore, verifying the app developer and publisher is a crucial first step in ensuring your digital safety. Malicious actors often employ sophisticated techniques to mask their true identities, making this verification process more important than ever.Cybercriminals use various tactics to create a façade of legitimacy.
They might mimic the names and logos of well-known brands, creating apps that look strikingly similar to popular applications. They may also use seemingly professional-looking developer names and descriptions, masking their true intentions. Some even purchase seemingly legitimate developer accounts to further enhance their credibility. Another tactic is to register domains that closely resemble those of trusted companies to add another layer of deception.
Cross-Referencing Developer Information
To verify a developer’s legitimacy, cross-referencing information across multiple app stores is highly recommended. If an app is available on both the Google Play Store and the Apple App Store, compare the developer’s name, contact information, and app descriptions across both platforms. Discrepancies could indicate a fraudulent app. Look for consistent branding and information; any inconsistencies should raise red flags.
Furthermore, searching for the developer’s name online can reveal additional information, such as their website or social media presence, which can help corroborate their legitimacy.
Identifying Legitimate App Publishers
Several methods exist for identifying legitimate app publishers. Checking the developer’s website for transparency and detailed information about their company is a valuable step. A legitimate publisher will likely have a well-established online presence, including contact information, a privacy policy, and terms of service. Look for reviews and ratings from other users, both on the app store and independent review sites.
Negative reviews or a lack of user feedback can be a warning sign. Also, verify if the developer is registered with relevant authorities or has a verifiable business address.
Comparison of Legitimate and Fake App Stores
The following table highlights key differences between legitimate and fake app stores to aid in identification.
| Feature | Legitimate App Store (e.g., Google Play Store, Apple App Store) | Fake App Store | Identifying Difference |
|---|---|---|---|
| Security Measures | Robust security protocols, malware scanning, and developer verification processes. | Lack of security measures, easily bypassed security, and minimal or no verification. | Presence/absence of security features, verification badges, and developer information. |
| Developer Verification | Rigorous verification process for developers, including identity checks and background checks. | Minimal or no developer verification, often using fake or stolen identities. | Verification badges, developer contact information, and consistent information across platforms. |
| App Reviews and Ratings | Open and transparent system for user reviews and ratings, moderated to prevent manipulation. | Manipulated reviews, limited or no user feedback, or suspicious review patterns. | Check for unusually high or low ratings, inconsistent feedback, and the number of reviews. |
| Website and Contact Information | Clear and accessible website with contact information, privacy policy, and terms of service. | Lack of a proper website or contact information, often using generic or non-functional details. | Website quality, contact information availability and accuracy, and presence of a privacy policy. |
Check App Permissions: 7 Essential Security Tips To Identify Fake Mobile Apps
Before you download and install any mobile application, carefully reviewing the requested permissions is crucial. Understanding what permissions an app requests and why is a fundamental step in protecting your privacy and security. Granting unnecessary permissions can expose your personal data to potential misuse, so a thorough assessment is essential.Apps request permissions to access various aspects of your device and data.
This access ranges from seemingly innocuous requests like accessing your location for weather updates to more sensitive requests like accessing your contacts or microphone. Understanding the implications of granting each permission is vital to making informed decisions.
Red Flag App Permissions
Certain app permissions should raise immediate red flags. These are permissions that are either excessive for the app’s stated functionality or permissions that could be easily misused to compromise your security and privacy. For example, a flashlight app requesting access to your contacts list is clearly suspicious. Similarly, a simple game requiring access to your camera and microphone without a clear justification should be treated with caution.
A calculator app requesting access to your location is another example of an incongruous permission request. These discrepancies indicate a potential for malicious intent.
Implications of Granting Excessive Permissions
Granting excessive permissions to an app significantly increases your risk of data breaches and privacy violations. Malicious apps can exploit these permissions to steal your personal information, track your location, access your sensitive files, or even monitor your online activities. For instance, an app with access to your contacts could potentially send spam messages or phishing emails to your friends and family.
An app with access to your microphone could secretly record your conversations, while an app with access to your location could track your movements without your knowledge. The consequences can range from minor annoyances to significant financial and reputational damage.
Examples of Seemingly Benign Permissions That Could Be Misused
Some permissions may appear harmless at first glance, but they can be misused by malicious actors. For example, an app requesting access to your device’s storage might seem reasonable if it needs to save game data or user preferences. However, this permission could also allow the app to access and steal other sensitive files on your device. Similarly, an app requesting access to your camera might seem justifiable if it’s a photo editing app, but this access could also be used to secretly take pictures or videos without your consent.
Another example is an app requesting access to your Bluetooth connection; while seemingly benign for certain functionalities, this permission could be misused for unauthorized pairing with other devices, potentially allowing attackers to compromise your system.
App Permission Decision-Making Flowchart
Imagine a flowchart. The starting point is “App requests permission.” The first decision point is: “Is the permission necessary for the app’s stated functionality?” If yes, proceed to the next decision point: “Does the app’s reputation and developer legitimacy inspire trust?” If yes, grant permission. If no at either point, deny permission. This flowchart simplifies the decision-making process, prompting users to consider both the necessity of the permission and the trustworthiness of the app.
The process emphasizes critical thinking and cautious decision-making regarding granting app permissions.
Examine App Reviews and Ratings
App store reviews are a goldmine of information, offering a glimpse into the real-world experiences of other users. While not foolproof, carefully analyzing both positive and negative reviews can significantly reduce your risk of downloading a malicious or poorly-made app. Don’t just look at the star rating; dig deeper to understand the context behind the scores.Analyzing app reviews involves more than just skimming the top few comments.
You need to develop a critical eye to discern genuine feedback from cleverly disguised promotional material or coordinated attempts to manipulate the rating. This involves understanding review patterns, identifying inconsistencies, and recognizing common tactics used by malicious actors.
Knowing the 7 essential security tips to identify fake mobile apps is crucial for your digital safety. Building secure apps, however, is also paramount, which is why I’ve been researching the advancements in app development, particularly domino app dev the low code and pro code future , to understand how these platforms can help developers create more secure applications.
Ultimately, understanding both app security and development best practices is key to protecting yourself from malicious apps.
Identifying Fake or Manipulated Reviews
Fake reviews often appear suspiciously similar, using repetitive phrases or overly enthusiastic language without specific details. They might praise aspects of the app that are irrelevant or nonexistent. Conversely, negative reviews might be suspiciously short, generic, or lack any specific examples to support their claims. Look for patterns – a sudden surge in either positive or negative reviews within a short time frame can be a red flag.
A consistent, overwhelmingly positive rating with no negative feedback whatsoever should also raise suspicion. Many legitimate apps will have a mix of positive and negative reviews reflecting the diversity of user experiences.
Distinguishing Genuine User Feedback from Promotional Reviews
Genuine user feedback tends to be specific and detailed, offering concrete examples of their experience. For example, a genuine positive review might describe how a specific feature helped them solve a problem, while a fake review might simply say “This app is amazing!” Promotional reviews often lack this level of detail. They may focus on general aspects of the app rather than specific features, or use superlative language without providing any substantiation.
Also, look for reviews that seem disconnected from the app’s actual functionality. These might praise features that simply don’t exist or misrepresent the app’s purpose.
Warning Signs in App Reviews Indicating a Potentially Fake App
Before downloading an app, consider these warning signs in the reviews:
- An overwhelming number of five-star ratings with very few, if any, lower ratings.
- Reviews that are short, generic, and lack specific details about the user’s experience.
- Reviews that use repetitive phrases or overly enthusiastic language (“This app is the best ever!”).
- Reviews that praise aspects of the app that are irrelevant or nonexistent.
- A sudden surge in either positive or negative reviews within a short period.
- Reviews that seem suspiciously similar to each other, suggesting coordinated reviews.
- A lack of negative reviews, even for apps with known issues or limitations.
- Reviews that focus solely on general aspects of the app without mentioning specific features.
Remember, while app reviews provide valuable insights, they are not a perfect indicator of an app’s quality or security. Use them in conjunction with other security measures to make informed decisions about the apps you download.
Look for Spelling and Grammar Errors
Poor spelling and grammar in an app’s description or within the app itself can be a major red flag. Cybercriminals often operate across language barriers, leading to clumsy translations and frequent errors. This lack of attention to detail suggests a rushed or unprofessional development process, which is often a hallmark of malicious apps. Trust your instincts; if the language looks suspect, the app likely is too.Legitimate app developers usually invest time in creating polished descriptions and user interfaces.
They understand that clear communication builds trust and attracts users. Conversely, fake apps often prioritize speed and efficiency over quality, resulting in noticeable linguistic flaws. These errors aren’t just minor typos; they represent a larger pattern of carelessness that can indicate malicious intent.
Examples of Spelling and Grammatical Errors in Fake App Descriptions, 7 essential security tips to identify fake mobile apps
Common errors include misspelled words (e.g., “acount” instead of “account,” “downlod” instead of “download”), incorrect grammar (e.g., subject-verb agreement errors, misplaced modifiers), and awkward phrasing. Imagine seeing an app description that boasts “Unlimted features” or promises “Freee dowloads.” These obvious errors immediately raise suspicion. Another common tactic is using broken English, often relying on machine translation without human review.
This might manifest as sentences that are grammatically correct but nonsensical in context. For example, a finance app might describe a feature as “The algorithm precisely calculates your financial gains, optimizing your wealth to the maximum extent, resulting in significant monetary advantages.” While grammatically correct, the phrasing is overly verbose and unnatural.
Inconsistencies Between App Language and Official Website Language
If the app claims to be associated with a known company or brand, compare the language used in the app description and within the app itself to the language used on the company’s official website. Significant discrepancies in tone, style, and vocabulary should raise concerns. For instance, if the official website uses formal and precise language, but the app description is filled with slang and informal expressions, it could be a sign of a fraudulent app.
A discrepancy in branding elements, such as logos or color schemes, should also raise a red flag. A legitimate app will maintain consistent branding across all platforms.
Investigate the App’s Website and Social Media Presence
Before you download an app, take the time to investigate its online presence. A legitimate app developer will usually have a well-maintained website and active social media accounts, offering another layer of verification beyond the app store itself. Inconsistencies between the app’s description and its online presence can be a major red flag.A thorough investigation can reveal crucial details about the app’s developer and help you distinguish between a trustworthy source and a potential scam.
Checking for a website and social media presence is a simple yet effective step in protecting your device and data.
Website Verification
Verifying the legitimacy of an app’s associated website involves several steps. First, look for a professional and well-designed website with clear contact information, including a physical address and email address. Avoid websites that look amateurish, have broken links, or lack basic contact details. Secondly, examine the website’s content for consistency with the app’s description. If the app claims to offer specific features or services, the website should clearly describe and support these claims.
Discrepancies between the app store listing and the website content should raise concerns. Finally, check the website’s security. Look for a secure HTTPS connection (indicated by a padlock icon in the browser address bar). A lack of HTTPS suggests a lack of commitment to security, increasing the risk of data breaches.
Inconsistencies Between App Description and Online Presence
Inconsistencies between the app’s description on the app store and its online presence can be a significant indicator of a fake app. For example, an app claiming to be a sophisticated financial tool might have a poorly designed website with grammatical errors and outdated information. Or, an app promising a revolutionary gaming experience might have a website that simply redirects to an unrelated advertisement.
These disparities suggest a lack of effort and professionalism, traits rarely found in legitimate app developers.
Website Design and Quality Comparison
The design and quality of a legitimate app’s website are typically professional and consistent with the app’s functionality. A legitimate app developer will invest in a clean, well-organized website that reflects the quality of their app. In contrast, a fake app’s website might look rushed, have broken links, and contain obvious grammatical errors or inconsistencies in its design.
The difference in quality can be striking, with legitimate websites often incorporating high-quality images, clear navigation, and detailed information about the app and the development team. A poorly designed website, on the other hand, may raise serious doubts about the authenticity of the associated app.
Use a Reputable Antivirus or Security App
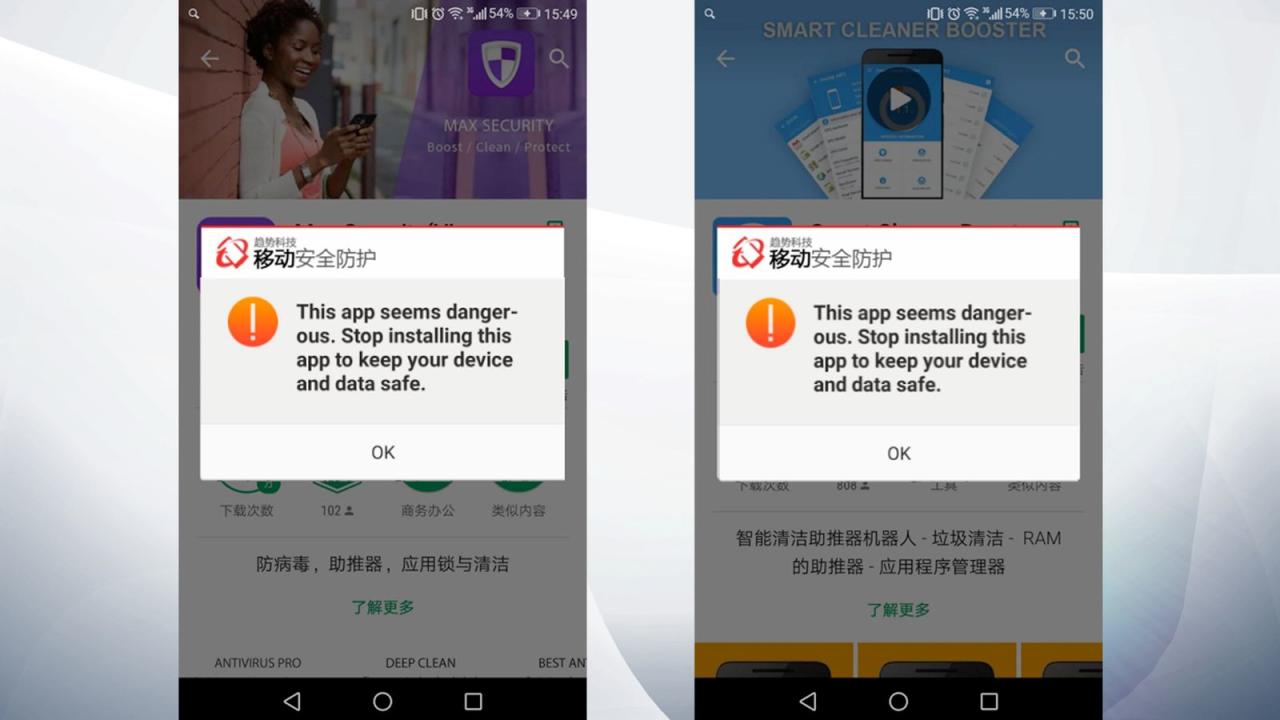
Protecting your mobile device from malicious apps is crucial, and a robust antivirus app acts as your first line of defense. These apps scan apps before installation, monitor for suspicious activity, and can even block known harmful websites. Think of them as your digital security guards, constantly vigilant against threats.Antivirus software employs various techniques to detect malicious apps.
They use signature-based detection, identifying known malware through their unique code signatures. Heuristic analysis examines the app’s behavior for suspicious patterns, even if it’s a new, previously unseen threat. Sandboxing allows the app to run in a controlled environment, allowing the antivirus to observe its actions without risking the entire system. Real-time protection constantly monitors for suspicious activity, preventing threats before they can cause damage.
Antivirus App Features and Capabilities
Different antivirus apps offer varying levels of protection and features. Some focus primarily on malware detection, while others provide additional features like VPNs, anti-theft tools, and web protection. Consider your needs when choosing an app; a basic malware scanner might suffice for casual users, while someone handling sensitive data might benefit from a more comprehensive suite. Features such as real-time protection, automatic updates, and a user-friendly interface are essential considerations.
The level of support offered by the developer is also critical; you want an app that’s actively maintained and updated to combat emerging threats. Some apps might offer features like app scanning before installation, while others provide ongoing monitoring for suspicious behavior.
Reputable Antivirus Apps and Their Key Security Features
Choosing a reputable antivirus app is vital. Here are a few examples, but remember that the best app for you will depend on your individual needs and preferences. This is not an exhaustive list, and the market is constantly evolving.
Before listing specific apps, it’s important to note that the effectiveness of any antivirus app can vary depending on factors like the specific threats encountered and the user’s device and usage habits. Regular updates and responsible online behavior remain crucial for optimal security.
- Avast Mobile Security: Offers features like anti-theft, VPN, and a web shield. Known for its user-friendly interface and comprehensive protection.
- Bitdefender Mobile Security: Emphasizes speed and efficiency, with a focus on real-time protection and minimal impact on battery life. It often scores highly in independent testing.
- McAfee Mobile Security: Provides a solid range of security features, including anti-malware, anti-theft, and a call blocker. It’s a well-established brand with a long history in security.
- Kaspersky Mobile Antivirus: Known for its robust malware detection capabilities and advanced security features. It provides a high level of protection but may consume more resources.
- Norton Mobile Security: Offers a strong reputation and comprehensive protection against various threats. Features include anti-malware, anti-phishing, and a secure VPN.
Download Apps Only from Official App Stores

Downloading apps from outside official app stores significantly increases your risk of installing malware or malicious software onto your device. These unofficial sources often lack the security checks and verification processes that reputable app stores employ, leaving you vulnerable to a range of threats, from data theft and financial fraud to device damage and privacy violations. Sticking to official app stores is a crucial first step in protecting your mobile security.Unofficial app stores typically lack the robust security measures found in official stores like Google Play or the Apple App Store.
Official app stores employ rigorous vetting processes, including code analysis, security scans, and developer verification, to minimize the risk of malicious apps slipping through. Unofficial sources, however, often bypass these crucial steps, resulting in a higher likelihood of encountering compromised or harmful apps. The difference in security protocols is a significant factor when considering where to download your apps.
Comparison of Official and Unofficial App Store Interfaces
Imagine two app store interfaces side-by-side. The legitimate app store, like Google Play or the Apple App Store, features a clean, organized layout with clear categories and search functionality. Prominent security elements are visible, such as clear indicators of verified developers and user ratings and reviews. The overall design conveys a sense of professionalism and trustworthiness. The color scheme is typically consistent and calming, and navigation is intuitive.
Security badges or certifications may be clearly displayed, further reinforcing trust. In contrast, a fake app store might appear cluttered and disorganized, with questionable graphics and potentially misleading descriptions. Security elements are either absent or poorly implemented, lacking clear verification processes or user review sections. The overall aesthetic might feel unprofessional or even suspicious, perhaps using garish colors or an overly busy layout.
The navigation might be confusing or difficult to use, and a lack of clear contact information adds to the sense of distrust. The difference is stark: one inspires confidence, the other raises immediate red flags.
Epilogue
Protecting yourself from fake mobile apps is a continuous process, but with these seven essential security tips, you’re already well on your way to a safer mobile experience. Remember, a little vigilance can go a long way in safeguarding your phone and your personal information. Stay informed, stay safe, and happy app-ing!
FAQ Explained
What if an app asks for permissions that seem unnecessary?
It’s a huge red flag. Carefully consider why an app needs access to your contacts, location, or microphone. If the permission request doesn’t align with the app’s stated function, it’s best to avoid it.
How can I tell if an app store is legitimate?
Look for secure connections (HTTPS), professional design, and clear contact information. Legitimate app stores usually have a robust review system and customer support. If something feels off, it probably is.
Are all antivirus apps created equal?
No. Some offer more comprehensive protection than others. Research different antivirus apps, reading reviews and comparing features before choosing one.
What should I do if I’ve already downloaded a fake app?
Uninstall it immediately! Then, run a full scan with your antivirus software and change all your passwords. Consider monitoring your accounts for any suspicious activity.





