Chinese Investment in Cyber Security Startups Worries Pentagon
Chinese investment in cyber security startups worries pentagon. This isn’t just some geopolitical chess match; it’s a potential threat to national security. The Pentagon’s concerns are valid, stemming from the potential for sensitive US technology to be siphoned off, creating vulnerabilities in our critical infrastructure and defense systems. The sheer scale of Chinese investment in this sector, coupled with their often opaque business practices, raises serious questions about the long-term implications for US technological dominance and national security.
This increasing investment isn’t solely focused on acquiring cutting-edge tech; it’s also about gaining access to the US market and potentially influencing policy. The intricate web of financial relationships, coupled with the inherent vulnerabilities within the cybersecurity landscape itself, paints a complex picture that demands careful consideration. We’ll explore the Pentagon’s anxieties, the potential risks, and what measures might be taken to mitigate this burgeoning threat.
The Nature of Chinese Investment in Cybersecurity

Chinese investment in global cybersecurity startups is a complex and increasingly significant phenomenon, raising concerns and sparking debate amongst policymakers and industry experts alike. This investment reflects China’s growing technological ambitions and its desire to establish a robust domestic cybersecurity ecosystem, while simultaneously impacting the global cybersecurity landscape. Understanding the nature of this investment is crucial to assessing its potential implications.
The Current Landscape of Chinese Cybersecurity Investment, Chinese investment in cyber security startups worries pentagon
Chinese investment in global cybersecurity startups is characterized by a multifaceted approach. It’s not limited to a single type of company or investment strategy. Rather, it involves a range of activities, from direct equity investments in promising startups to acquisitions of established companies and the fostering of joint ventures. This investment is driven by both private and state-backed entities, blurring the lines between commercial and strategic objectives.
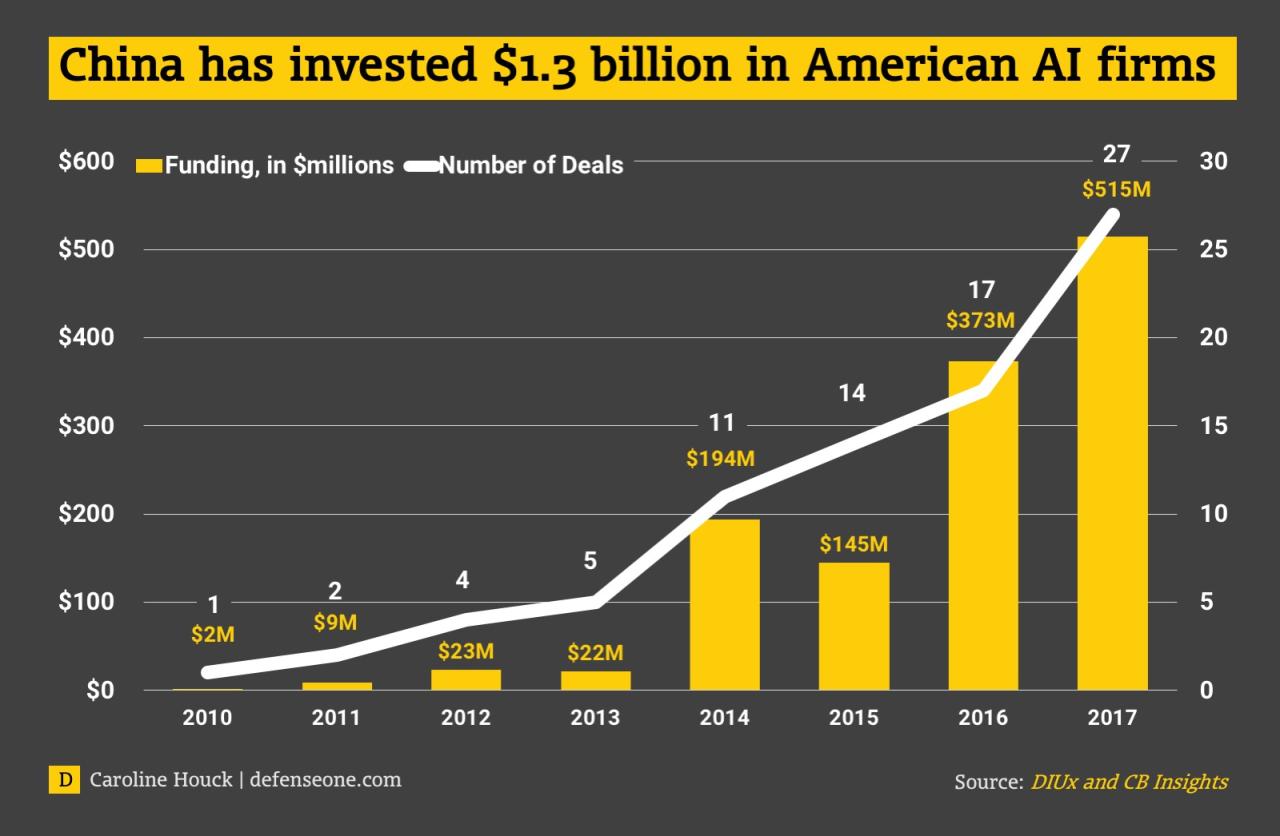
The scale of this investment has been steadily increasing over the past decade, although precise figures are difficult to obtain due to the opaque nature of some transactions. Anecdotal evidence suggests a significant surge in investment in recent years, particularly in areas deemed critical to national security and technological advancement.
Types of Cybersecurity Companies Attracting Chinese Investment
Chinese investment isn’t uniformly distributed across the cybersecurity sector. Specific areas have attracted disproportionately high levels of interest. These include companies specializing in artificial intelligence (AI)-driven threat detection, cloud security, critical infrastructure protection, and data security. Companies developing advanced technologies like blockchain and quantum cryptography are also increasingly sought after. Furthermore, Chinese investors often target startups with a strong technological base and the potential for rapid scaling, even if those startups are in their early stages of development.
This preference for cutting-edge technology reflects China’s focus on becoming a global leader in cybersecurity innovation.
Motivations Behind Chinese Cybersecurity Investment
Several factors drive Chinese investment in the global cybersecurity sector. Firstly, there’s a clear strategic imperative to bolster China’s national cybersecurity capabilities. This includes protecting critical infrastructure, government networks, and sensitive data from both domestic and foreign threats. Secondly, there’s a strong economic motivation to develop a thriving domestic cybersecurity industry, fostering innovation and creating high-value jobs. Finally, acquiring advanced technologies and expertise from foreign companies offers a faster route to technological advancement than relying solely on indigenous development.
This “leapfrogging” strategy aims to rapidly close the technological gap with leading nations.
The Pentagon’s concern over Chinese investment in cybersecurity startups is definitely a hot topic. It makes you wonder about the future of secure app development, and how platforms like those discussed in this article on domino app dev the low code and pro code future can help us build more resilient systems. Ultimately, the question remains: can we build truly secure applications fast enough to stay ahead of these potential threats?
Comparison of Chinese Investment Strategies with Other Nations
Chinese investment strategies differ significantly from those of other nations. While countries like the US and Israel also invest heavily in cybersecurity, their approaches often prioritize private sector-led innovation and market forces. Chinese investment, however, often involves a greater degree of state involvement and a more explicit focus on strategic national interests. This difference leads to distinct investment priorities and risk tolerance levels.
For example, Chinese investors might be more willing to invest in companies with less-proven track records but significant technological potential, reflecting a higher tolerance for risk associated with achieving national strategic goals.
Comparative Investment Focus of Different Countries in Cybersecurity Startups
| Country | Investment Focus | Key Characteristics | Examples (Illustrative, not exhaustive) |
|---|---|---|---|
| China | AI-driven threat detection, cloud security, critical infrastructure protection, data security, emerging technologies (blockchain, quantum cryptography) | High state involvement, strategic national interests, risk tolerance for high-growth potential, potential for technology transfer | Investments in companies developing AI-powered threat intelligence platforms, secure cloud solutions for government agencies. |
| United States | Broad range, including endpoint security, network security, data loss prevention, cloud security, incident response | Primarily private sector-led, emphasis on market forces, strong focus on established companies and proven technologies | Investments in large, established cybersecurity firms, venture capital funding for various security solutions. |
| Israel | Cybersecurity for critical infrastructure, government, and financial institutions, emphasis on AI and automation | Strong entrepreneurial ecosystem, government support for R&D, focus on innovative solutions for niche markets | Investments in companies developing advanced threat detection and response technologies. |
| United Kingdom | Cybersecurity for critical national infrastructure, data protection, cloud security, fintech security | Government initiatives to encourage investment, focus on collaboration between industry and academia | Investments in companies specializing in national security, data privacy, and financial services security. |
Pentagon Concerns and National Security Implications
The Pentagon’s apprehension regarding Chinese investment in US cybersecurity startups stems from legitimate concerns about potential national security breaches and the erosion of American technological advantage. This isn’t simply about economic competition; it’s about protecting critical infrastructure, sensitive data, and ultimately, national sovereignty in the digital realm. The potential for malicious actors to exploit vulnerabilities introduced through seemingly benign investments is a significant threat.The potential national security risks are multifaceted and far-reaching.
Chinese investment, even if seemingly focused on market expansion, could offer a backdoor for state-sponsored espionage or sabotage. This includes access to sensitive government data, military technology, and critical infrastructure systems. Furthermore, the acquisition of US cybersecurity firms by Chinese entities could lead to a transfer of valuable intellectual property and technological know-how, potentially strengthening China’s own cyber capabilities while weakening those of the US.
Scenarios of Compromise
Several scenarios illustrate how Chinese-backed cybersecurity firms could compromise US interests. For instance, a seemingly legitimate cybersecurity firm could subtly introduce backdoors into software or hardware used by government agencies or private companies managing critical infrastructure. This could allow for undetected surveillance, data theft, or even the ability to disrupt essential services. Another scenario involves the use of seemingly innocuous software updates to introduce malware or gain unauthorized access to systems.
This kind of “supply chain attack” is particularly insidious because it leverages the trust placed in established software providers. Finally, compromised firms could be used to gain intelligence on US cyber defenses, allowing China to develop more effective offensive capabilities.
Examples of State-Sponsored Cyberattacks
Numerous examples of state-sponsored cyberattacks highlight the very real threat posed by foreign actors. The SolarWinds attack, attributed to Russian state-sponsored actors, demonstrated the devastating potential of supply chain attacks. Similarly, Chinese state-sponsored actors have been linked to numerous cyber espionage campaigns targeting US government agencies and businesses, stealing intellectual property and sensitive data. These attacks highlight the capability and willingness of nation-states to use cyber tools for strategic advantage.
Potential Vulnerabilities Exploitable Through Investment
The potential vulnerabilities that could be exploited through Chinese investment are numerous and vary widely depending on the target and the nature of the investment. A list of potential vulnerabilities includes:
- Backdoors in software and hardware: Deliberately introduced vulnerabilities allowing unauthorized access.
- Data exfiltration: The theft of sensitive data through compromised systems.
- Supply chain attacks: Compromising software or hardware at the manufacturing or distribution level.
- Denial-of-service attacks: Overwhelming systems with traffic to render them unusable.
- Insider threats: Employees with access to sensitive information who are compromised or coerced.
- Intellectual property theft: The theft of valuable technology and trade secrets.
- Disruption of critical infrastructure: Targeting power grids, communication networks, or other essential services.
The potential for these vulnerabilities to be exploited is amplified when a foreign power, like China, has direct or indirect control over a US cybersecurity firm. The consequences could be severe, impacting everything from national security to the economic stability of the United States.
Technological Capabilities and Transfer of Knowledge: Chinese Investment In Cyber Security Startups Worries Pentagon
The intersection of Chinese investment in US cybersecurity startups and national security concerns is complex, particularly regarding the transfer of technological capabilities and sensitive knowledge. Analyzing the technological prowess of involved Chinese firms, the potential pathways for technology transfer, and the strategic advantages gained through US market access is crucial to understanding the Pentagon’s anxieties. This assessment will examine the technological landscape, highlighting potential risks and illustrating a hypothetical scenario to underscore the gravity of the situation.
Chinese cybersecurity firms, while rapidly advancing, often possess strengths in specific areas rather than across the board. For instance, some excel in network security and data analytics, leveraging large datasets for threat detection. Others might focus on specific hardware or software solutions, often tailored to the Chinese market’s unique regulatory environment. However, a critical gap often exists in advanced research and development, particularly in areas like AI-driven threat hunting and zero-trust architectures, where US firms often maintain a significant lead.
Chinese Cybersecurity Firms’ Technological Capabilities
Several Chinese cybersecurity companies have demonstrated significant capabilities in areas such as network security, data analytics, and intrusion detection. However, their technological advancements are often concentrated in specific niches, reflecting the prioritization of domestic needs and the regulatory landscape in China. While some firms have made inroads into international markets, their technological reach often lags behind leading US companies in areas requiring cutting-edge research and development.
This disparity highlights the potential for knowledge transfer through strategic investments and collaborations.
Potential Pathways for Technology Transfer
Several pathways exist for the transfer of sensitive US technology to China through investments in US cybersecurity startups. Joint ventures, mergers and acquisitions, and even seemingly innocuous licensing agreements can facilitate this transfer. For example, access to source code, proprietary algorithms, and even employee expertise could be unintentionally or deliberately transferred. Furthermore, the acquisition of a US startup by a Chinese firm might provide access to a vast network of clients and partners, potentially revealing sensitive information about US infrastructure and critical systems.
This presents a clear national security risk.
Benefits of US Market Access for Chinese Firms
Access to the US market offers several significant benefits to Chinese cybersecurity firms. The sheer size and sophistication of the US market provide a lucrative testing ground for new technologies and a valuable source of revenue. Furthermore, establishing a presence in the US allows Chinese firms to gain valuable insights into market trends, customer preferences, and competitive landscapes.
This knowledge can be leveraged to improve their products and services, ultimately enhancing their competitiveness both domestically and internationally. This access, however, comes at a cost to US national security if not properly managed.
Technological Advancements: US vs. China
The US maintains a significant lead in several critical areas of cybersecurity, including artificial intelligence (AI)-driven threat detection, zero-trust security architectures, and quantum-resistant cryptography. While China is making rapid progress in these areas, a substantial gap remains, particularly in the development and deployment of advanced technologies. This technological gap is often a primary driver behind Chinese investment in US cybersecurity startups, aiming to accelerate their own technological development and reduce the reliance on foreign technologies.
Hypothetical Scenario: Transfer of Sensitive Information
Imagine a scenario where a Chinese firm invests in a US startup specializing in AI-driven threat detection. During the integration process, access to the startup’s proprietary algorithms and training datasets is granted to the Chinese investors. These datasets might inadvertently contain sensitive information about US critical infrastructure, such as power grids or financial institutions. The Chinese firm could then leverage this information to develop more sophisticated attack tools or to identify vulnerabilities within US systems, posing a significant national security threat.
This scenario highlights the need for stringent oversight and due diligence in such investments.
Economic and Geopolitical Ramifications
The influx of Chinese investment into US cybersecurity startups presents a complex web of economic and geopolitical ramifications. While some argue it fosters innovation and competition, others express serious concerns about potential national security risks and economic vulnerabilities. Understanding the interplay of these factors is crucial for developing effective policy responses.The economic impact of Chinese investment on the US cybersecurity industry is multifaceted.
On one hand, it can inject capital into promising startups, accelerating technological development and creating jobs. However, this investment can also lead to intellectual property theft, market distortion through unfair competition practices, and the potential erosion of US technological leadership in a critical sector. The long-term economic consequences depend heavily on the extent to which safeguards are implemented to mitigate these risks.
US Cybersecurity Industry Economic Impact
Chinese investment, while potentially providing funding, raises concerns about the potential for intellectual property theft and the creation of dependencies on Chinese technology. This could stifle innovation within the US cybersecurity sector and lead to a loss of competitive advantage in the global market. For example, if a Chinese company gains significant control over a crucial US cybersecurity firm, it could gain access to sensitive data and algorithms, potentially undermining national security and giving China a strategic advantage.
Conversely, successful integration of Chinese capital could lead to technological advancements and a more robust cybersecurity ecosystem, though this outcome requires robust regulatory oversight.
Geopolitical Implications of Chinese Influence
The geopolitical implications are even more profound. Increased Chinese influence in the global cybersecurity landscape could lead to the proliferation of backdoors in critical infrastructure, the exploitation of vulnerabilities for espionage or sabotage, and the erosion of trust in the integrity of global digital systems. China’s growing technological capabilities, coupled with its assertive foreign policy, create a scenario where cybersecurity becomes a tool for geopolitical leverage.
The potential for disruption to essential services like power grids, financial systems, and communication networks poses a significant threat to national and international stability.
Countermeasures to Mitigate Risks
The US government can implement several countermeasures to mitigate these risks. Strengthening existing regulations on foreign investment in sensitive sectors, particularly cybersecurity, is paramount. This includes stricter scrutiny of acquisitions and investments by Chinese companies, enhanced due diligence processes, and clearer definitions of what constitutes a national security risk. Investing in domestic cybersecurity research and development is also crucial to maintaining technological leadership and reducing reliance on foreign technologies.
Furthermore, international cooperation with allies to establish common standards and best practices for cybersecurity can help to counter China’s influence and create a more secure global digital environment.
Existing Regulations and Policies
The Committee on Foreign Investment in the United States (CFIUS) already reviews foreign investments that could pose a national security risk. However, the current regulatory framework may need strengthening to address the evolving nature of Chinese investment in the cybersecurity sector. Examples of existing regulations include those under the Export Administration Regulations (EAR) and the International Traffic in Arms Regulations (ITAR), which control the export of sensitive technologies.
However, these regulations may need to be updated to specifically address the risks posed by Chinese investment in cybersecurity startups. The focus needs to be on preventing technology transfer that could compromise national security.
Impact of Economic Sanctions
Economic sanctions can be a powerful tool to deter Chinese investment in US cybersecurity. Targeted sanctions against specific Chinese companies or individuals involved in malicious cyber activities could significantly impact their ability to invest in US startups. However, sanctions need to be carefully calibrated to avoid unintended consequences, such as harming legitimate businesses or triggering retaliatory actions. The effectiveness of sanctions also depends on international cooperation and the willingness of other countries to enforce them.
The use of sanctions should be considered strategically as part of a broader approach to managing the risks associated with Chinese investment in cybersecurity.
The Pentagon’s concern over Chinese investment in cybersecurity startups is definitely understandable, given the potential for data breaches and intellectual property theft. This highlights the critical need for robust security measures, especially as more companies transition to the cloud. Understanding the intricacies of cloud security is key, and a great resource for that is this article on bitglass and the rise of cloud security posture management , which sheds light on crucial strategies.
Ultimately, strengthening our own domestic cybersecurity infrastructure is crucial to counter potential threats from foreign investment.
International Cooperation and Regulatory Frameworks
The increasing interconnectedness of global cybersecurity and the significant role of Chinese investment in this sector necessitates a robust framework for international cooperation and effective regulatory mechanisms. The current landscape, however, presents both opportunities and challenges in balancing the promotion of innovation with the mitigation of national security risks. Effective regulation requires a delicate balance; over-restrictive measures could stifle innovation and economic growth, while lax regulations could expose nations to significant vulnerabilities.The effectiveness of existing regulatory frameworks governing foreign investment in cybersecurity varies considerably across nations.
Some countries employ broad screening mechanisms for all foreign investments with potential national security implications, while others adopt a more targeted approach, focusing on specific sectors or technologies. The effectiveness of these frameworks depends heavily on their implementation, transparency, and the level of international cooperation in sharing information and best practices.
Existing Regulatory Frameworks and Their Effectiveness
Existing frameworks, such as the Committee on Foreign Investment in the United States (CFIUS) in the US and similar bodies in other countries, offer a baseline for evaluating foreign investments. However, their effectiveness in addressing the nuances of cybersecurity investment, particularly those from China, remains a subject of ongoing debate. The complexity of supply chains, the rapid pace of technological advancement, and the often-opaque nature of investment vehicles present challenges to effective oversight.
Furthermore, a lack of harmonization across different national frameworks hinders effective global cooperation and creates potential loopholes for circumvention. For example, some countries may focus heavily on direct investment, while overlooking indirect investment channels or the acquisition of smaller companies with crucial technologies. This inconsistent application of regulations allows for a lack of transparency and potential exploitation.
Potential Improvements to Regulatory Frameworks
Several improvements could enhance the effectiveness of existing regulatory frameworks. Firstly, greater transparency and harmonization of standards across nations are crucial. A collaborative effort to develop common definitions of critical cybersecurity technologies and methodologies for risk assessment would significantly improve regulatory efficacy. Secondly, enhancing information sharing between countries is paramount. This includes the sharing of intelligence on malicious actors, vulnerabilities, and suspicious investment activities.
Thirdly, the frameworks should be adaptable to the ever-evolving nature of cybersecurity threats and technologies. Regular reviews and updates are necessary to account for emerging risks and technological advancements. Finally, consideration should be given to the development of international dispute resolution mechanisms to address inconsistencies and disagreements between nations regarding regulatory actions.
Comparative Analysis of National Approaches
The approaches taken by different countries vary widely. The US, for example, takes a relatively aggressive stance, using CFIUS to scrutinize investments in critical infrastructure and technology sectors. The European Union is developing a more unified approach, aiming for greater harmonization across member states, though the implementation remains complex. Other countries, particularly those with less developed regulatory frameworks, may have a more lenient approach, potentially creating vulnerabilities.
This diversity of approaches necessitates a stronger international collaborative effort to establish a common ground and minimize the potential for regulatory arbitrage.
Recommendations for Strengthening International Cooperation in Cybersecurity
- Establish a global cybersecurity forum for information sharing and collaborative threat assessment.
- Develop a standardized framework for evaluating the national security risks associated with foreign investment in cybersecurity.
- Promote the adoption of internationally recognized cybersecurity standards and best practices.
- Foster capacity building initiatives to assist developing countries in strengthening their cybersecurity capabilities and regulatory frameworks.
- Create mechanisms for international cooperation in investigating and responding to cybersecurity incidents involving foreign investment.
Ultimate Conclusion

The Pentagon’s worry over Chinese investment in US cybersecurity startups is a legitimate concern with far-reaching implications. The potential for technology transfer, market manipulation, and the exploitation of vulnerabilities presents a significant challenge. While international cooperation and robust regulatory frameworks are crucial, a proactive and multi-faceted approach is needed to safeguard US national security interests in the face of this evolving threat.
The stakes are high, and the need for vigilance is paramount.
FAQ
What specific types of cybersecurity companies are attracting Chinese investment?
Chinese investment spans various cybersecurity areas, including network security, cloud security, AI-driven threat detection, and critical infrastructure protection. Companies with advanced technologies or access to sensitive data are particularly attractive.
How does Chinese investment compare to that of other nations?
While other nations also invest in cybersecurity startups, the scale and strategic focus of Chinese investment are often seen as more aggressive and potentially concerning, particularly regarding access to sensitive US technologies.
What countermeasures are being considered to address these concerns?
Countermeasures include stricter regulations on foreign investment in sensitive sectors, enhanced due diligence processes, and increased scrutiny of Chinese acquisitions of US cybersecurity firms. International cooperation to establish common standards and norms is also being explored.