Companies Rush to Secure Google Cloud SCC Runtimes
Companies rush to provide container runtime security to Google Cloud SCC – it’s a gold rush in the cloud security world! The increasing sophistication of attacks targeting containerized applications on Google Cloud Platform (GCP) has created a massive demand for robust security solutions. This isn’t just about patching vulnerabilities; it’s about proactively defending against breaches that could cripple entire businesses.
We’re seeing a surge in companies offering specialized solutions designed to integrate seamlessly with Google Cloud’s Security Center (SCC), promising a more secure environment for businesses of all sizes.
The core issue lies in the nature of containers themselves. Their ephemeral and distributed nature makes traditional security approaches less effective. Attackers are exploiting this, finding new ways to penetrate containerized workloads and gain unauthorized access to sensitive data. This rapid growth in container adoption on GCP has consequently created a huge need for reliable, integrated security solutions.
The response from security companies has been swift, with many rushing to provide solutions that meet the increasing demands of organizations deploying containerized applications on Google Cloud.
The Growing Need for Container Runtime Security on Google Cloud
The explosive growth of cloud-native applications and the increasing adoption of containerization technologies like Kubernetes on Google Cloud Platform (GCP) have created a rich ecosystem for innovation. However, this rapid expansion also presents a significantly expanded attack surface for malicious actors. The lack of robust container runtime security measures leaves GCP deployments vulnerable to a range of sophisticated threats, demanding a proactive and comprehensive security strategy.The vulnerabilities inherent in containerized environments on GCP are multifaceted and often go unnoticed until exploited.
Unlike traditional virtual machines, containers share the host operating system kernel, creating a potential pathway for attackers to compromise multiple containers simultaneously. Misconfigurations in container images, network policies, and access controls further exacerbate these risks, allowing attackers to easily gain unauthorized access and control. Furthermore, the ephemeral nature of containers and the dynamic orchestration of Kubernetes clusters can make identifying and responding to security incidents significantly more challenging.
Container Runtime Vulnerabilities in GCP Environments, Companies rush to provide container runtime security to google cloud scc
Containers, while offering numerous advantages, introduce unique vulnerabilities within a GCP environment. These include vulnerabilities within the container images themselves, such as outdated libraries with known exploits, malicious code injected during the build process, or vulnerabilities in the application code running within the container. Improperly configured network policies can allow unauthorized communication between containers or external networks, enabling lateral movement by attackers.
Furthermore, weak or absent secrets management practices leave sensitive data, like API keys and database credentials, exposed, enabling attackers to gain full control over applications and potentially the entire GCP project. Finally, insufficient monitoring and logging capabilities make it difficult to detect and respond to security incidents effectively.
Examples of Real-World Attacks Targeting Containerized Workloads on GCP
While specific details of attacks are often kept confidential for security reasons, public reports and security advisories frequently highlight successful attacks against containerized applications across various cloud platforms, including GCP. For instance, a common attack vector involves exploiting vulnerabilities in container images to gain initial access. Once inside a container, an attacker can leverage this foothold to move laterally to other containers within the same cluster, ultimately gaining access to sensitive data or disrupting critical services.
Another frequent attack involves compromising the Kubernetes control plane itself, enabling attackers to manipulate the entire cluster’s configuration, deploy malicious pods, or steal sensitive information. These attacks underscore the importance of comprehensive security measures throughout the entire container lifecycle.
Hypothetical Attack Scenario and Impact
Imagine a scenario where a company deploys a microservices application on GCP using Kubernetes. A developer inadvertently uses a vulnerable version of a popular library within a container image. An attacker discovers this vulnerability and exploits it to gain access to the compromised container. Due to insufficient network segmentation, the attacker can then move laterally to other containers within the same namespace, eventually gaining access to the database container holding sensitive customer data.
The attacker exfiltrates this data, resulting in a significant data breach, regulatory fines, reputational damage, and potential legal action. This scenario highlights the cascading effect of a single vulnerability and the critical need for robust security measures at every stage, from image creation to runtime protection.
Google Cloud Security Center (SCC) and its Role: Companies Rush To Provide Container Runtime Security To Google Cloud Scc

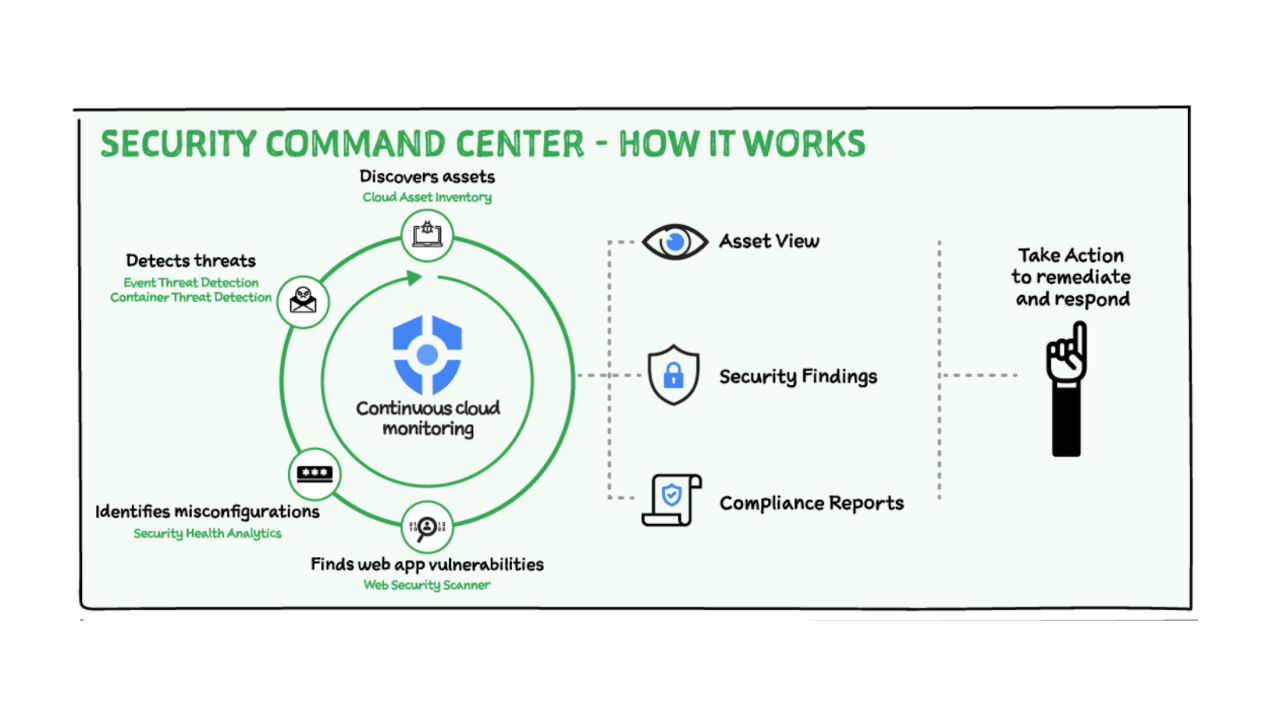
Google Cloud Security Center (SCC) is a crucial component of any robust Google Cloud Platform (GCP) security strategy, and its role in securing containerized environments is particularly significant. It provides a centralized view of your security posture across your GCP resources, offering comprehensive vulnerability management and threat detection capabilities specifically tailored for the complexities of container orchestration platforms like Kubernetes.
This allows organizations to proactively identify and mitigate risks before they can be exploited.SCC’s container security features go beyond simple vulnerability scanning. It leverages its deep integration with other GCP services to provide a holistic understanding of your container security posture. This includes monitoring container images for vulnerabilities, enforcing security policies, and detecting anomalous behavior that could indicate a compromise.
This proactive approach significantly reduces the attack surface and helps organizations maintain compliance with industry best practices and regulations.
SCC’s Key Features for Container Security
SCC offers several key features specifically designed to enhance container security. These include continuous vulnerability scanning of container images stored in Container Registry, detection of misconfigurations in Kubernetes clusters, and monitoring for suspicious activity within your containerized workloads. It also provides recommendations for remediation, enabling security teams to quickly address identified vulnerabilities and misconfigurations. The integration with other GCP services like Cloud Audit Logs allows for comprehensive threat detection and response.
For example, SCC can correlate events from different services to identify potential attacks involving compromised containers.
SCC’s Threat Detection and Response Capabilities
SCC’s threat detection capabilities rely on a combination of automated analysis and machine learning. It continuously monitors your container environment for suspicious activity, such as unauthorized access attempts, unusual network traffic patterns, or the execution of malicious code within containers. When a potential threat is detected, SCC generates alerts, providing security teams with the necessary information to investigate and respond effectively.
These alerts include details such as the affected container, the type of threat, and recommended remediation steps. This proactive approach significantly reduces the time it takes to identify and respond to security incidents. For instance, SCC might detect a container running a vulnerable version of a database and alert the security team, enabling them to quickly update the container image to a patched version.
Comparison with Other Cloud Security Platforms
While other cloud security platforms offer container security features, SCC distinguishes itself through its deep integration with the GCP ecosystem. This integration allows for a more comprehensive and holistic view of your security posture compared to solutions that operate as standalone tools. Many other platforms may require manual configuration and integration, leading to potential gaps in coverage. SCC’s automated vulnerability scanning, threat detection, and remediation recommendations streamline the security workflow, making it more efficient and effective.
The level of context provided by SCC, derived from its integration with various GCP services, is a significant advantage over solutions with less comprehensive visibility.
Integrating SCC into an Existing GCP Container Security Strategy
Integrating SCC into an existing GCP container security strategy involves several key steps. First, ensure that all relevant GCP resources are enabled for SCC’s monitoring capabilities. This includes your Kubernetes clusters, Container Registry, and other relevant services. Next, configure SCC’s security health analytics to receive alerts and notifications for critical security events. Regularly review SCC’s findings and recommendations to identify and address vulnerabilities and misconfigurations promptly.
Finally, integrate SCC with your existing security information and event management (SIEM) system to gain a consolidated view of your security posture across your entire infrastructure. This holistic approach ensures comprehensive security coverage and enables efficient threat response.
Analysis of Companies’ Response to the Security Gap
The rapid growth of containerized applications on Google Cloud Platform (GCP) has created a significant demand for robust container runtime security solutions. This security gap, stemming from the inherent complexities of container orchestration and the distributed nature of cloud environments, has spurred a flurry of activity from security vendors. Many are rushing to provide integrated solutions compatible with Google Cloud Security Center (SCC), aiming to simplify security management and improve threat detection for organizations leveraging GCP’s container services.
Leading Container Runtime Security Solutions for Google Cloud SCC
Several companies have emerged as leaders in providing container runtime security solutions that integrate seamlessly with Google Cloud SCC. These solutions offer a range of capabilities, from vulnerability scanning and runtime threat detection to compliance monitoring and incident response. Understanding their features and pricing is crucial for organizations choosing the best fit for their security posture.
Comparison of Container Runtime Security Solutions
The following table compares three prominent solutions: (Note: Pricing is highly variable and dependent on factors such as usage, features, and support level. The pricing shown here represents a general range and should be verified with the respective vendors.)
| Feature | Solution A (e.g., Aqua Security) | Solution B (e.g., Sysdig Secure) | Solution C (e.g., Twistlock) |
|---|---|---|---|
| Vulnerability Scanning | Image scanning, runtime vulnerability detection | Comprehensive image and runtime vulnerability analysis | Deep image scanning, runtime threat detection |
| Runtime Threat Detection | Behavioral analysis, intrusion detection | Real-time threat detection and response | Advanced threat detection using machine learning |
| Compliance Monitoring | Support for various compliance standards (e.g., PCI DSS, HIPAA) | Built-in compliance dashboards and reporting | Automated compliance checks and reporting |
| Integration with Google Cloud SCC | Direct integration via API | Seamless integration with SCC for centralized security management | Integration with SCC for threat alerts and reporting |
| Pricing Model | Subscription based, per-node or per-container pricing | Subscription based, tiered pricing model | Subscription based, usage-based pricing |
Motivations for Market Expansion in Container Runtime Security
The rapid expansion of these companies into the GCP container runtime security market is driven by several key factors:* Growing adoption of containers on GCP: The increasing popularity of Kubernetes and container orchestration platforms on GCP has created a massive market opportunity for security solutions.
Increased sophistication of cyberattacks
Modern attacks often target containerized environments, making robust security crucial.
Demand for integrated security solutions
Organizations prefer solutions that integrate seamlessly with existing security tools like Google Cloud SCC, simplifying security management.
Compliance requirements
Meeting regulatory requirements (e.g., PCI DSS, HIPAA) necessitates strong container security practices.
Timeline of Container Runtime Security Solutions for GCP
Illustrating the evolution of container runtime security on GCP requires acknowledging that precise dates for each innovation are often proprietary. However, a generalized timeline can be constructed:* 2015-2017: Early adoption of container technologies on GCP. Basic security measures (e.g., image scanning) are implemented, often manually.
2018-2020
Emergence of dedicated container runtime security solutions, focusing on vulnerability scanning and basic runtime protection. Integration with GCP’s security tools begins.
2021-Present
The scramble to bolster container runtime security on Google Cloud SCC is intense, with vendors vying for a piece of the action. This heightened focus on security is interesting when you consider the parallel rise of rapid application development; check out this insightful piece on domino app dev the low code and pro code future to see how development speed impacts security considerations.
Ultimately, the need for robust container security remains paramount, regardless of how quickly applications are built.
Sophisticated solutions incorporating advanced threat detection, behavioral analysis, and automated response capabilities become prevalent. Seamless integration with Google Cloud SCC and other GCP services is prioritized. The market consolidates around a few key players.
Specific Security Solutions and their Integrations with SCC
The rapid adoption of containerized applications on Google Cloud Platform (GCP) has highlighted the critical need for robust runtime security. Many vendors are stepping up to address this need, offering solutions that integrate with Google Cloud Security Center (SCC) to provide comprehensive visibility and control. Let’s delve into one such solution and explore its capabilities and integration with SCC.
We’ll use Aqua Security’s container security platform as a representative example.
Aqua Security Integration with Google Cloud Security Center
Aqua Security offers a cloud-native security platform that integrates seamlessly with Google Cloud’s Security Center. This integration allows for centralized security management, consolidating container security data alongside other GCP security findings within SCC. This unified view simplifies security monitoring and incident response. The integration leverages SCC’s APIs to ingest Aqua’s security findings, enriching the overall security posture assessment provided by SCC.
Security Controls Offered by Aqua Security
Aqua Security provides a wide range of security controls for containerized workloads, many of which are directly reflected in SCC. These include runtime protection against vulnerabilities, malware, and malicious activity. Specifically, Aqua’s runtime Application Control prevents unauthorized processes and code execution within containers. Its image scanning capabilities, integrated with SCC, identify vulnerabilities in container images before deployment, preventing deployment of insecure images.
Furthermore, Aqua’s compliance features ensure that containers meet organizational security policies and regulatory requirements. These compliance checks and their results are reported to and visible within SCC. Finally, Aqua’s network security features control and monitor the traffic flows between containers, limiting the blast radius of potential attacks. This network security information is also reported to SCC.
Implementing Aqua Security and SCC Integration
Implementing Aqua Security within a GCP environment and integrating it with SCC involves several steps.
- Deploy Aqua Security: Deploy the Aqua agent in your GCP environment, either as a standalone deployment or as part of a Kubernetes cluster. This agent will monitor and protect your containerized applications.
- Configure SCC Integration: Configure the Aqua platform to send security findings to SCC. This typically involves setting up an API connection between Aqua and SCC, specifying the relevant GCP project and the required permissions.
- Enable Integrations: Within the Aqua platform, enable the specific integrations for the desired security features. For example, enable integration for vulnerability scanning, runtime protection, and network security monitoring.
- Monitor and Respond: Regularly monitor the security findings in SCC, which will now include data from Aqua. Use this information to investigate potential threats and take appropriate remediation actions. Aqua’s platform provides detailed context and remediation guidance for each finding.
Enhanced Security Posture with Aqua Security
By integrating Aqua Security with SCC, organizations gain several key benefits. First, they achieve centralized security management, simplifying monitoring and response. Second, they gain improved visibility into the security posture of their containerized applications, thanks to the consolidated view in SCC. Third, they proactively prevent vulnerabilities and attacks, reducing the risk of breaches. For example, if a vulnerable image is identified by Aqua’s image scanning, SCC alerts administrators, preventing the deployment of the vulnerable image and preventing potential exploits.
The scramble to bolster container security on Google Cloud’s Security Command Center (SCC) is intense, with vendors vying for a piece of the action. This heightened focus on runtime security is directly related to the broader trend of Cloud Security Posture Management (CSPM) solutions gaining traction, as highlighted in this insightful article on bitglass and the rise of cloud security posture management.
Ultimately, the demand for comprehensive container security solutions for Google Cloud SCC will only continue to grow as cloud adoption expands.
The enhanced visibility and control offered by this integration significantly strengthen the overall security posture of containerized applications on GCP, reducing the risk of costly security incidents.
Future Trends in Container Runtime Security on GCP
The rapid adoption of containerized applications on Google Cloud Platform (GCP) necessitates a constantly evolving approach to security. The next 2-3 years will see significant shifts in how container runtime security is managed, driven by advancements in technology and a growing awareness of sophisticated attack vectors. We’ll see a move towards more proactive, automated, and integrated security solutions, all while grappling with the inherent complexities of a dynamic containerized environment.
AI-Powered Threat Detection and Response
Artificial intelligence and machine learning (AI/ML) will play a crucial role in enhancing container runtime security. We can expect to see a surge in solutions that leverage AI/ML to analyze vast amounts of runtime data, identifying anomalous behavior and potential threats in real-time. This will go beyond simple signature-based detection, moving towards anomaly detection that can identify zero-day exploits and sophisticated attacks that bypass traditional security measures.
For example, an AI-powered system could learn the normal CPU and memory usage patterns of a specific containerized application and flag any significant deviations, indicating a potential compromise. This proactive approach allows for faster response times and minimizes the impact of security breaches.
Serverless Security Integration
As serverless computing gains traction, the need for seamless integration between serverless functions and container runtime security solutions will become paramount. Future solutions will need to extend their protection to serverless environments, ensuring consistent security posture across all deployment models. This will involve developing mechanisms to monitor and control access to serverless functions, as well as integrating security policies directly into the serverless deployment pipeline.
Imagine a scenario where a serverless function automatically triggers a security alert if an unauthorized attempt to access sensitive data is detected. This seamless integration across different deployment models will be crucial for maintaining a unified security posture.
Enhanced Supply Chain Security
The increasing complexity of containerized application supply chains creates a significant security vulnerability. Future solutions will focus on securing the entire lifecycle, from image building to deployment, employing techniques like Software Bill of Materials (SBOM) integration and automated vulnerability scanning throughout the process. This will involve tighter integration with tools like Grafeas and Grype, allowing for continuous monitoring and automated remediation of vulnerabilities detected in container images.
For instance, an automated system could prevent deployment of an image containing a known vulnerability, alerting developers and automatically triggering a rebuild process with a patched image. This holistic approach to supply chain security will become increasingly vital to prevent attacks originating from compromised images.
Shift-Left Security and DevSecOps
The trend of “shifting security left” will accelerate, integrating security practices earlier in the software development lifecycle. This will require closer collaboration between development and security teams, adopting DevSecOps principles. Future container runtime security solutions will be tightly integrated with CI/CD pipelines, automating security checks and enforcing security policies at every stage of the development process. This proactive approach will reduce the likelihood of vulnerabilities reaching production environments.
For example, automated security scans during the build process could identify and flag potential vulnerabilities before the image is even deployed to a testing environment. This integrated approach ensures security is treated as a core component of the development process rather than an afterthought.
Conceptual Model for an Ideal Future Solution
An ideal future container runtime security solution integrated with SCC would be a highly automated, AI-powered system providing comprehensive visibility and control across the entire container lifecycle. It would seamlessly integrate with SCC, enriching its data with real-time runtime insights. This system would leverage AI/ML for proactive threat detection, automatically identifying and responding to anomalies. It would integrate with CI/CD pipelines for shift-left security, and offer granular control over access and resource usage.
Furthermore, it would provide comprehensive supply chain security, integrating with SBOM tools and automated vulnerability scanning to ensure only secure images are deployed. This unified approach, combining real-time monitoring, automated responses, and proactive threat hunting, would provide a robust and adaptive security posture for containerized workloads on GCP.
Last Point
The race to secure Google Cloud’s container runtimes is far from over. As containerization continues its rapid expansion, so too will the sophistication of the attacks targeting these environments. The companies leading the charge are not just providing point solutions; they are building integrated ecosystems that work seamlessly with Google Cloud’s security infrastructure. The future of container security hinges on continuous innovation, proactive threat detection, and a collaborative approach between cloud providers and security vendors.
It’s a dynamic landscape, and staying ahead of the curve is critical for anyone operating in the cloud.
Questions and Answers
What are the biggest risks associated with insecure container runtimes on GCP?
Data breaches, unauthorized access to sensitive information, application downtime, compliance violations, and reputational damage are all major risks.
How does Google Cloud Security Center (SCC) help with container security?
SCC provides visibility into container security posture, vulnerability detection, and threat detection capabilities, often integrating with other security tools.
Are open-source solutions sufficient for securing container runtimes on GCP?
Open-source tools can be part of a comprehensive strategy, but often require significant expertise to implement and maintain effectively. Commercial solutions usually offer broader functionality and support.
What’s the difference between runtime security and image security?
Image security focuses on securing the container image
-before* it runs, while runtime security focuses on protecting the container while it’s actively running.