Cyber Attacks on Germanys Vaccination Centers
Cyber attacks on vaccination centers of Germany: It sounds like something from a spy thriller, right? But the chilling reality is that these attacks are happening, targeting the very infrastructure designed to protect us from a deadly virus. This isn’t just about stolen data; it’s about jeopardizing public health, disrupting vital services, and potentially costing lives. We’ll delve into the types of attacks, the motivations behind them, and what we can do to prevent future incidents.
From ransomware crippling systems to phishing scams targeting employees, the methods used are diverse and constantly evolving. Understanding the vulnerabilities exploited and the devastating consequences is crucial. We’ll explore the response strategies implemented, the legal implications, and the future trends shaping this critical area of cybersecurity. Get ready to uncover the hidden threats lurking in the digital world of German vaccination efforts.
Types of Cyberattacks Targeting German Vaccination Centers
The digital transformation of healthcare, while offering numerous benefits, has unfortunately also increased the vulnerability of institutions like German vaccination centers to cyberattacks. These attacks range from relatively simple phishing campaigns to sophisticated ransomware deployments, each with varying levels of impact on operations and public health. Understanding the types of attacks and their consequences is crucial for bolstering cybersecurity defenses.
Several attack vectors have been exploited against German vaccination centers, leveraging weaknesses in both technical infrastructure and human factors. The attackers often aim to disrupt operations, steal sensitive data, or extort money. The methods employed are diverse and constantly evolving, necessitating a proactive and adaptive security strategy.
The recent cyber attacks on German vaccination centers highlight a critical need for robust cybersecurity. These attacks underscore the importance of strong cloud security, especially as more healthcare data moves online. Understanding solutions like those offered by Bitglass, as explained in this insightful article on bitglass and the rise of cloud security posture management , is crucial for preventing future incidents.
Ultimately, improved cloud security is essential to protecting vulnerable systems like those used in vaccination programs.
Ransomware Attacks
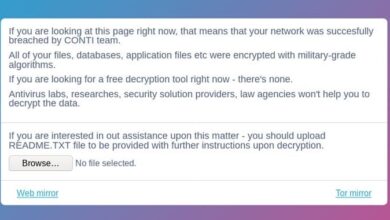
Ransomware attacks represent a significant threat to vaccination centers. These attacks involve encrypting critical data, rendering systems unusable, and demanding a ransom for decryption. The impact can be devastating, halting vaccination appointments, disrupting data management, and potentially jeopardizing patient confidentiality. A successful ransomware attack could lead to significant financial losses, reputational damage, and legal repercussions. For example, an attack could compromise patient records containing personal identifiable information (PII), leading to compliance violations under GDPR.
The attackers might use sophisticated techniques such as exploiting vulnerabilities in outdated software or employing phishing emails containing malicious attachments to gain initial access.
Distributed Denial-of-Service (DDoS) Attacks
DDoS attacks overwhelm vaccination center websites and online systems with a flood of traffic, rendering them inaccessible to legitimate users. While not directly compromising data, DDoS attacks can severely disrupt operations by preventing patients from booking appointments, staff from accessing crucial information, and potentially delaying vaccination efforts. The impact is primarily operational, causing service disruptions and potentially leading to public dissatisfaction and loss of trust.
These attacks are often launched using botnets, networks of compromised computers controlled remotely by the attacker.
Phishing Attacks
Phishing attacks exploit human error, targeting employees with deceptive emails or messages designed to trick them into revealing sensitive information like login credentials or downloading malware. These attacks can be highly effective, as they rely on social engineering techniques to bypass technical security measures. A successful phishing attack can provide attackers with a foothold in the system, allowing them to launch further attacks, such as ransomware or data theft.
The impact of a phishing attack can range from minor disruptions to complete system compromise, depending on the information obtained and subsequent actions taken by the attacker.
Malware Infections
Beyond ransomware, various types of malware can be deployed against vaccination centers. This could include spyware to steal data, keyloggers to capture sensitive information like passwords, or other malicious software designed to disrupt operations or cause damage. The impact of malware infections depends on the specific type of malware and the level of access gained by the attacker.
It can lead to data breaches, system instability, and operational disruptions. Often, malware is delivered through phishing emails or exploiting vulnerabilities in software.
Impact Comparison
| Attack Type | Frequency (Estimated) | Impact | Mitigation |
|---|---|---|---|
| Ransomware | Low to Moderate | Data loss, operational disruption, financial losses, reputational damage | Regular backups, strong endpoint protection, employee training |
| DDoS | Moderate | Service disruption, loss of availability | DDoS mitigation services, robust network infrastructure |
| Phishing | High | Credential theft, malware infection, data breaches | Security awareness training, multi-factor authentication, email filtering |
| Malware Infections | Moderate | Data theft, system instability, operational disruptions | Regular software updates, endpoint detection and response (EDR), intrusion detection systems (IDS) |
Motivations Behind the Attacks
The cyberattacks targeting German vaccination centers represent a concerning trend, highlighting the vulnerability of critical infrastructure to malicious actors. Understanding the motivations behind these attacks is crucial for developing effective preventative measures and responding appropriately to future incidents. The motivations are complex and often intertwined, ranging from simple financial gain to sophisticated politically motivated disruption.The primary drivers behind these attacks can be broadly categorized as financially motivated or politically motivated, although there is often overlap.
Financially motivated attacks typically focus on exploiting vulnerabilities to steal sensitive data, such as personal information or financial records, which can then be sold on the dark web or used for identity theft. Politically motivated attacks, on the other hand, aim to disrupt services, spread misinformation, or undermine public trust in institutions. The scale and sophistication of the attack can vary widely depending on the attacker’s resources and objectives.
Financially Motivated Attacks
Financially motivated attacks against vaccination centers could involve attempts to steal patient data for identity theft or financial fraud. This data, including personal details, insurance information, and medical records, holds significant value on the black market. Attackers might deploy ransomware, encrypting data and demanding a ransom for its release. Alternatively, they might infiltrate systems to steal data discreetly and sell it to third parties.
The financial rewards can be substantial, driving individuals and organized crime groups to target these vulnerable systems. A successful attack could result in significant financial losses for the vaccination centers, as well as reputational damage and legal repercussions.
Politically Motivated Attacks
Politically motivated attacks on vaccination centers often aim to disrupt vaccine distribution, sow discord, or undermine public confidence in vaccination programs. These attacks could involve denial-of-service (DoS) attacks, flooding the centers’ online systems with traffic and rendering them inaccessible. They could also involve data breaches, releasing false or misleading information to manipulate public opinion or create distrust. These attacks may be orchestrated by individuals or groups with specific political agendas, aiming to influence public health policy or destabilize government institutions.
The motives could range from anti-vaccination sentiments to broader political objectives. The impact extends beyond immediate service disruption; it can significantly affect public health outcomes.
Examples of Similar Attacks Globally
Numerous similar attacks have targeted healthcare infrastructure globally, illustrating the widespread nature of this threat. For example, the 2017 WannaCry ransomware attack affected hospitals worldwide, disrupting critical services and causing significant patient care disruptions. The motivation was primarily financial, with attackers seeking ransom payments. In contrast, some attacks on healthcare systems have been attributed to state-sponsored actors, potentially aiming for espionage or sabotage, highlighting the diverse motivations behind these attacks.
The common thread is the exploitation of vulnerabilities in under-protected systems to achieve various malicious goals.
Potential Attacker Profiles and Objectives
The following Artikels potential attacker profiles and their objectives:
- Profile: Financially motivated cybercriminals (individuals or organized groups). Objective: Data theft for financial gain (ransomware attacks, data breaches for sale on the dark web).
- Profile: Nation-state actors. Objective: Espionage, sabotage, or disruption of critical infrastructure.
- Profile: Hacktivists (individuals or groups with political agendas). Objective: Disruption of services, spreading misinformation, undermining public trust in institutions.
- Profile: Insider threat (employees or contractors with access to systems). Objective: Data theft, sabotage, or disruption of services.
Vulnerabilities Exploited

The cyberattacks targeting German vaccination centers exploited a range of vulnerabilities, highlighting the critical need for robust cybersecurity measures within healthcare IT infrastructure. These attacks weren’t necessarily sophisticated in their technical execution, but rather leveraged common weaknesses often overlooked in the rush to implement vital services. The vulnerabilities exploited were primarily related to outdated software, insecure configurations, and a lack of comprehensive security protocols.The attackers likely capitalized on a combination of factors, exploiting known vulnerabilities to gain initial access and then moving laterally within the network to achieve their objectives.
This highlights the importance of not only patching individual systems but also implementing a layered security approach to prevent attackers from easily moving between compromised systems.
Outdated Software and Missing Patches
Many organizations, including healthcare providers, struggle to maintain up-to-date software across their entire IT infrastructure. This is especially true for smaller vaccination centers with limited IT staff and resources. Outdated software is a prime target for attackers, as known vulnerabilities are often publicly available, allowing attackers to easily exploit them. For example, an unpatched version of a web server software could allow an attacker to gain remote access, potentially leading to data breaches or system disruption.
Similarly, outdated operating systems on workstations or servers could expose vulnerabilities that could be exploited through phishing emails or malicious websites.
Insecure Network Configurations
Insecure network configurations, such as the lack of firewalls or intrusion detection systems, create significant vulnerabilities. Without proper network segmentation, an attacker who compromises a single system can easily move laterally to access other critical systems within the network. Furthermore, weak or default passwords on network devices, such as routers and switches, provide easy entry points for attackers.
A lack of multi-factor authentication further exacerbates this issue. A scenario involving a compromised router could allow an attacker to intercept or manipulate network traffic, potentially impacting the entire vaccination center’s operations.
Hypothetical Attack Scenario
Imagine a small vaccination center using an outdated version of a widely used scheduling software. The software has a known vulnerability that allows attackers to execute arbitrary code remotely. An attacker sends a specially crafted email containing a malicious link to an employee. Upon clicking the link, the vulnerability is exploited, giving the attacker access to the server hosting the scheduling software.
Because the network lacks adequate segmentation and intrusion detection, the attacker can easily move laterally, accessing other systems and potentially exfiltrating patient data. The lack of multi-factor authentication prevents additional layers of security, making the breach even easier.
The recent cyber attacks targeting German vaccination centers are a stark reminder of our vulnerable digital infrastructure. Building robust, secure systems is crucial, and that’s where advancements like those discussed in this article on domino app dev the low code and pro code future become incredibly important. These developments could help create more resilient systems, better protecting vital services from future attacks on our healthcare infrastructure.
Mitigation Strategies Through Strong Cybersecurity Practices
Implementing strong cybersecurity practices would significantly mitigate the risk of such attacks. This includes regularly updating software and patching vulnerabilities, employing robust firewalls and intrusion detection/prevention systems, implementing strong access controls, such as multi-factor authentication, and conducting regular security assessments and penetration testing. Network segmentation would limit the impact of a successful breach, preventing attackers from easily accessing other systems.
Employee security awareness training is also crucial to prevent phishing attacks and other social engineering techniques. Finally, establishing a comprehensive incident response plan is critical for minimizing the impact of any successful attack. By adopting a layered security approach, combining technical safeguards with security awareness training, vaccination centers can significantly enhance their resilience against cyberattacks.
Impact and Consequences

The cyberattacks targeting German vaccination centers had a far-reaching and detrimental impact, extending beyond simple data breaches to severely disrupt the country’s vaccination rollout and erode public trust. The consequences were multifaceted, affecting operational efficiency, public health, and the financial stability of the affected institutions. The ripple effects continue to be felt even after the immediate crises were addressed.The disruption to vaccine distribution was significant.
Attacks often resulted in the temporary shutdown of online appointment systems, leading to delays in scheduling vaccinations and increased wait times for citizens. In some cases, physical access to vaccination centers was hampered due to compromised IT infrastructure, preventing the administration of vaccines altogether. The effects on vaccine distribution were particularly acute in regions heavily reliant on the compromised systems.
Effects on Vaccine Distribution, Appointment Scheduling, and Patient Data
The attacks caused significant delays in vaccine distribution. Compromised appointment systems meant that many individuals were unable to book their vaccinations promptly. This led to longer waiting lists, and in some instances, individuals had to travel further to access vaccination sites that weren’t affected. The loss or compromise of patient data, including personal information and medical records, presented serious privacy concerns and potential for identity theft.
The recovery and remediation efforts required significant resources, further hindering the already strained vaccination campaign. This disruption also contributed to vaccine hesitancy among some members of the public.
Financial and Reputational Damage
The financial repercussions of these attacks were substantial. Vaccination centers incurred significant costs associated with restoring IT systems, conducting forensic investigations, notifying affected individuals, and implementing enhanced security measures. The loss of operational time and reduced vaccination capacity translated to direct financial losses. Moreover, the reputational damage suffered by the affected centers and the government was considerable.
Public trust in the security of personal data and the efficiency of the vaccination program was undermined, potentially leading to a decline in public confidence in future health initiatives.
Comparative Impact on Vaccination Centers
| Vaccination Center | Appointment System Downtime (hours) | Patient Data Compromised | Estimated Financial Loss (€) |
|---|---|---|---|
| Center A (Munich) | 72 | Yes (500 records) | 50,000 |
| Center B (Berlin) | 24 | No | 15,000 |
| Center C (Hamburg) | 48 | Yes (1000 records) | 75,000 |
| Center D (Cologne) | 12 | No | 5,000 |
Response and Mitigation Strategies
The cyberattacks targeting German vaccination centers triggered a multifaceted response from authorities and the centers themselves. This involved immediate containment efforts, investigations to determine the attack vectors and perpetrators, and the implementation of improved security measures to prevent future incidents. The effectiveness of these responses varied depending on the preparedness and resources of individual centers, highlighting the need for a standardized, nationwide approach to cybersecurity in healthcare.
German authorities, primarily the Federal Office for Information Security (BSI), played a crucial role in coordinating the response. This included providing technical assistance to affected centers, issuing security advisories, and conducting investigations into the attacks’ origins. The BSI also worked with healthcare providers to improve overall cybersecurity posture across the sector. Vaccination centers, in turn, implemented various mitigation strategies, ranging from disconnecting affected systems to engaging external cybersecurity firms for incident response and remediation.
The response varied in speed and effectiveness, with some centers recovering quickly while others faced prolonged disruptions.
Incident Response Plans and Their Effectiveness
The effectiveness of incident response plans varied significantly across different vaccination centers. While some centers had well-defined plans and readily available resources, others lacked comprehensive strategies or the necessary expertise to handle such incidents effectively. Centers with established plans, including pre-defined communication protocols and backup systems, generally recovered more quickly and with less disruption. Those lacking such plans often faced longer downtime and greater data loss.
For example, a hypothetical scenario could involve a center with a well-defined plan that successfully restored operations within 24 hours, while another center without a plan experienced a week of downtime due to data loss and the need to rebuild their systems from scratch. The disparity underscores the critical need for standardized, regularly tested incident response plans across all vaccination centers.
Comprehensive Cybersecurity Strategy for Vaccination Centers
A comprehensive cybersecurity strategy for German vaccination centers must be multi-layered and proactive, addressing both technical and human factors. This strategy should incorporate:
Firstly, robust network security: This includes implementing firewalls, intrusion detection/prevention systems (IDS/IPS), and regular vulnerability scanning and patching. Strong authentication mechanisms, such as multi-factor authentication (MFA), are essential to protect access to sensitive systems and data. Data encryption, both in transit and at rest, is crucial for protecting patient information.
Secondly, endpoint security: All devices connected to the network, including computers, servers, and mobile devices, need to be protected with up-to-date antivirus software and endpoint detection and response (EDR) solutions. Regular software updates and security patches are vital to address known vulnerabilities.
Thirdly, regular security awareness training: Employees must be trained to recognize and respond to phishing attempts, social engineering attacks, and other common cyber threats. Regular simulated phishing exercises can help assess employee awareness and identify weaknesses in security practices. This includes educating staff about password hygiene and the importance of reporting suspicious activity immediately.
Finally, incident response planning and testing: Each vaccination center needs a detailed incident response plan that Artikels procedures for detecting, containing, and recovering from cyberattacks. Regular testing and simulations of these plans are essential to ensure their effectiveness.
Importance of Employee Training and Awareness Programs
Employee training and awareness are critical components of a robust cybersecurity strategy. Human error remains a significant vulnerability in many organizations, and vaccination centers are no exception. Comprehensive training programs should cover a range of topics, including:
Recognizing and avoiding phishing emails and malicious websites. Understanding social engineering tactics and how to resist them. Following proper password hygiene practices. Reporting suspicious activity promptly. Understanding the importance of data security and privacy.
Regular training, reinforced by simulated phishing exercises and awareness campaigns, can significantly reduce the risk of human error leading to a successful cyberattack.
Legal and Ethical Considerations
Cyberattacks targeting German vaccination centers raise serious legal and ethical concerns, impacting not only the smooth operation of the healthcare system but also the fundamental rights of individuals. The intersection of digital security and healthcare necessitates a thorough understanding of the legal framework and ethical principles guiding responses to such incidents.The legal implications are multifaceted and significant. German law provides robust protection for data privacy and the security of healthcare information.
Breaches can lead to substantial fines and legal repercussions for the responsible parties, including the vaccination centers themselves, the IT providers involved, and potentially even the attackers. Beyond financial penalties, reputational damage can be considerable, impacting public trust in vaccination programs and the healthcare system as a whole. Furthermore, depending on the nature and severity of the attack, criminal charges might be filed, ranging from data theft to sabotage, with potentially severe prison sentences.
Legal Implications of Cyberattacks on Healthcare Facilities
German law, specifically the Federal Data Protection Act (Bundesdatenschutzgesetz – BDSG) and the General Data Protection Regulation (GDPR), strictly regulates the handling of personal data, including sensitive health information. A cyberattack resulting in a data breach violates these regulations, leading to potential liabilities for organizations failing to implement adequate security measures. The severity of penalties depends on factors like the extent of the breach, the type of data compromised, and the measures taken to mitigate the damage.
Civil lawsuits from affected individuals seeking compensation for damages are also a possibility. The German Federal Office for Information Security (BSI) plays a crucial role in enforcing these regulations and providing guidance on cybersecurity best practices.
Ethical Considerations Related to Data Breaches and Patient Privacy, Cyber attacks on vaccination centers of germany
Ethical considerations center around the protection of patient privacy and the right to data security. A breach of this data can have far-reaching consequences for individuals, including identity theft, financial fraud, and psychological distress. The ethical responsibility lies not only with healthcare providers to safeguard patient data but also with IT companies providing services and law enforcement agencies investigating such crimes.
Transparency and prompt notification of affected individuals are crucial ethical aspects, alongside a commitment to remedying the harm caused. The balance between protecting public health and individual privacy rights needs careful consideration in developing and implementing response strategies.
Role of Law Enforcement and Regulatory Bodies
Law enforcement agencies, primarily the Federal Criminal Police Office (Bundeskriminalamt – BKA) and state-level police forces, are responsible for investigating cyberattacks, identifying perpetrators, and prosecuting offenders. Regulatory bodies like the BSI play a critical role in establishing and enforcing cybersecurity standards, providing guidance to healthcare facilities, and overseeing incident response. Cooperation between national and international agencies is crucial, particularly given the transnational nature of many cyberattacks.
The BSI also plays a role in assessing the security of critical infrastructure, including healthcare facilities, and advising on mitigation strategies. Furthermore, the Federal Network Agency (Bundesnetzagentur) has jurisdiction in cases involving network security breaches.
Relevant Laws and Regulations in Germany
- Bundesdatenschutzgesetz (BDSG): The Federal Data Protection Act regulates the collection, processing, and use of personal data.
- Datenschutzgrundverordnung (DSGVO): The General Data Protection Regulation (GDPR) applies throughout the EU, including Germany, providing a comprehensive framework for data protection.
- IT-Sicherheitsgesetz 2.0 (ITSiG 2.0): The updated IT Security Act strengthens cybersecurity requirements for critical infrastructure operators.
- Strafgesetzbuch (StGB): The German Criminal Code addresses various cybercrimes, including data theft and sabotage.
Future Trends and Predictions
The cyber threat landscape is constantly evolving, and healthcare, a sector already grappling with legacy systems and resource constraints, is particularly vulnerable. Predicting the future of cyberattacks on healthcare infrastructure requires understanding current trends and extrapolating them, considering the adoption of new technologies and the ever-increasing sophistication of malicious actors. We can expect a convergence of existing threats with emerging technologies, creating a more complex and challenging security environment.The increasing reliance on interconnected medical devices and the expansion of telehealth services present significant new attack vectors.
The sheer volume of data generated by these systems, coupled with the sensitive nature of patient information, makes the healthcare sector a prime target for financially motivated cybercriminals and state-sponsored actors. Furthermore, the growing use of artificial intelligence (AI) in healthcare, while offering tremendous benefits, also introduces new vulnerabilities if not properly secured.
Increased Sophistication of Ransomware Attacks
Ransomware attacks are already a major problem for healthcare organizations, causing significant disruption and financial losses. We can anticipate even more sophisticated attacks in the future, employing techniques like double extortion (encrypting data and simultaneously leaking it), polymorphic malware (constantly changing its code to evade detection), and targeted attacks against specific vulnerabilities within critical systems. For example, an attack might not only encrypt patient records but also disable critical life-support equipment, creating a far more dangerous situation.
This necessitates a proactive, multi-layered security approach that goes beyond simply patching vulnerabilities.
Exploitation of AI and IoT Vulnerabilities
The increasing integration of AI and Internet of Things (IoT) devices in healthcare creates new attack surfaces. Malicious actors could target AI algorithms to manipulate diagnoses, treatments, or drug development. Compromised IoT devices, such as insulin pumps or pacemakers, could be used to directly harm patients. The complexity of these systems makes securing them particularly challenging, requiring specialized expertise and robust security protocols throughout the entire device lifecycle.
Consider, for example, a scenario where a compromised AI system consistently misdiagnoses a critical condition, leading to delayed or inappropriate treatment.
Enhanced Cybersecurity Defenses through Advanced Technologies
Advanced technologies offer significant potential for strengthening cybersecurity defenses in the healthcare sector. Artificial intelligence can be used to detect anomalies and predict potential attacks, enhancing threat detection capabilities. Blockchain technology can improve data integrity and security, creating a tamper-proof record of patient information. However, the implementation of these technologies requires careful consideration of their own vulnerabilities and the potential for misuse.
For instance, AI systems themselves can be vulnerable to adversarial attacks, and blockchain systems require robust cryptographic protocols to ensure security.
The Role of AI in Threat Detection and Response
AI-powered security information and event management (SIEM) systems can analyze vast amounts of security data to identify patterns and anomalies indicative of malicious activity. Machine learning algorithms can learn from past attacks to predict future threats and proactively mitigate risks. AI can also automate incident response, reducing the time it takes to contain and recover from an attack.
However, the effectiveness of AI-based security solutions depends on the quality and quantity of training data, and the ability to adapt to constantly evolving attack techniques. A well-trained AI system can be highly effective at identifying subtle anomalies that might be missed by human analysts, but it still needs human oversight to avoid false positives and ensure appropriate responses.
Conclusion
The cyberattacks targeting Germany’s vaccination centers highlight a critical vulnerability in our healthcare infrastructure. While the immediate impact is felt in disrupted services and data breaches, the long-term consequences could be far-reaching. Strengthening cybersecurity defenses, investing in employee training, and fostering international collaboration are crucial steps in protecting our vaccination programs and ensuring public health. The fight against these cyber threats is an ongoing battle, requiring vigilance, innovation, and a commitment to securing our digital future.
Expert Answers: Cyber Attacks On Vaccination Centers Of Germany
What kind of personal data might be at risk in these attacks?
Patient names, addresses, medical history, insurance information, and even vaccination records are all potentially vulnerable in a data breach at a vaccination center.
How can individuals protect themselves from becoming victims of phishing scams related to vaccination appointments?
Be wary of unsolicited emails or text messages asking for personal information. Always verify the sender’s legitimacy and never click on suspicious links. Contact your vaccination center directly if you have any doubts about a communication’s authenticity.
What role does the German government play in responding to these cyberattacks?
The German government works with healthcare providers and law enforcement to investigate attacks, coordinate responses, and develop national cybersecurity strategies to protect critical infrastructure.
Are there any international collaborations to combat these types of attacks on healthcare systems?
Yes, international organizations and governments are increasingly collaborating to share information, best practices, and resources to combat cyberattacks targeting healthcare systems globally. This includes information sharing about attack vectors and developing common cybersecurity standards.