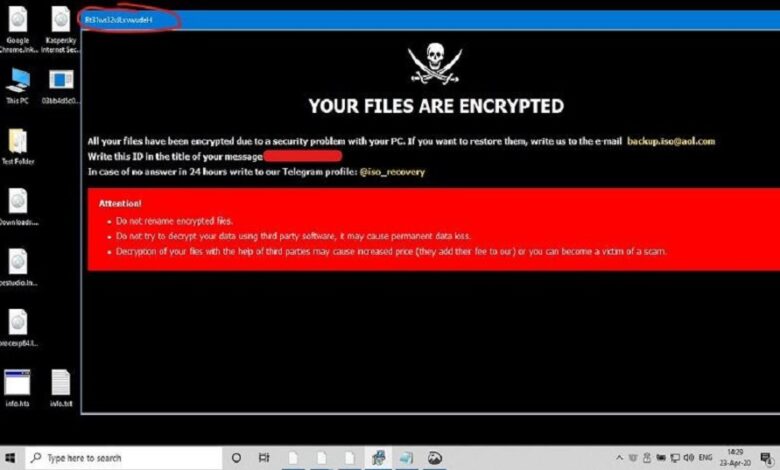
Dont Restart Your Computer After a Ransomware Attack
Dont restart your computer after a ransomware attack – Don’t restart your computer after a ransomware attack! That seemingly simple instruction is crucial in the fight to recover your data and secure your system. Acting quickly and strategically in the immediate aftermath of a ransomware attack can significantly increase your chances of a successful recovery. This post will guide you through the critical steps to take, focusing on what to do
-before* you even think about rebooting.
Ransomware attacks can be incredibly stressful, but understanding the correct procedure can significantly improve your outcome. We’ll cover isolating your system, creating a disk image, exploring data recovery options, investigating the attack’s origin, and hardening your security – all without the fatal mistake of restarting your computer. By following these steps, you’ll maximize your chances of recovering your data and minimizing the long-term damage.
The Immediate Aftermath of a Ransomware Attack
Discovering your system is under ransomware attack is terrifying. Panic won’t help; swift, decisive action will. The first few minutes are critical in minimizing the damage and increasing your chances of recovery. Remember, the goal is containment and preservation of evidence, not immediate decryption.
Your immediate priority is to prevent further infection and preserve potential evidence for recovery or investigation. This means isolating the affected system and creating a forensic image before attempting any remediation.
Isolating the Affected System
Isolating the infected system from your network is paramount. This prevents the ransomware from spreading to other computers, servers, or network shares. Failure to do so could result in a far more extensive and costly attack. This involves physically disconnecting the infected machine from the network (unplugging the Ethernet cable) and disabling Wi-Fi. If the infected machine is a server, this isolation will require immediate and decisive action to prevent further propagation.
Consider the potential impact of not isolating a server immediately; the spread of ransomware could cripple your entire operation.
Creating a Full Disk Image of the Affected Drive
Creating a forensic image of the affected hard drive is crucial for data recovery and investigation. This creates an exact copy of the drive’s contents, allowing you to analyze the attack without risking further data loss on the original drive. This image can then be used by forensic specialists or data recovery experts. Remember, any attempt at decryption or malware removal on the original drive could overwrite crucial evidence.
Okay, ransomware hit? Don’t even THINK about restarting! That could permanently encrypt your files. Seriously, focus on recovery – and while you’re strategizing, check out this fascinating article on domino app dev, the low-code and pro-code future , it might give you some ideas for building more resilient systems. Then, get back to tackling that ransomware; remember, a restart could be disastrous.
| Action | Description | Expected Outcome | Potential Issues |
|---|---|---|---|
| Identify the Affected Drive | Determine which hard drive or partition contains the encrypted data. This may involve checking file system properties or looking for unusual activity. | Accurate identification of the drive to be imaged. | Incorrect drive selection could lead to imaging the wrong data. |
| Acquire Forensic Imaging Software | Download and install reputable forensic imaging software, such as FTK Imager or dd (Linux). Ensure the software is from a trusted source to avoid introducing additional malware. | Access to a reliable forensic imaging tool. | Choosing unreliable software could introduce further security risks. |
| Create the Image | Follow the software’s instructions to create a bit-by-bit copy of the affected drive to an external hard drive or other storage device. Verify the integrity of the image after creation. | A complete and accurate copy of the affected drive. | Insufficient storage space, hardware failure during imaging, or image corruption. |
| Verify Image Integrity | Use a hash function (e.g., SHA-256) to generate a checksum for both the original drive and the image. Compare the checksums to ensure they match. | Confirmation that the image is an exact copy of the original drive. | Discrepancies in checksums indicate image corruption. |
Data Recovery Strategies (Without Restarting)
Ransomware attacks can be devastating, but immediate action can significantly improve your chances of data recovery. Crucially, avoid restarting your computer after an attack, as this can overwrite crucial data and hinder recovery efforts. The following strategies focus on recovering data without restarting, maximizing your chances of restoring your files.Data recovery after a ransomware attack without restarting requires a multi-pronged approach, prioritizing methods that minimize the risk of further data corruption.
The key is to act swiftly and systematically, exploring various avenues for recovery before resorting to more drastic measures.
Shadow Copies
Shadow copies are essentially snapshots of your files and folders created by the Windows Volume Shadow Copy Service (VSS). They’re a built-in feature that creates backups at regular intervals. If ransomware encrypted your files, a shadow copy from before the attack might contain unencrypted versions. To access them, you’ll need to use specialized recovery software or a command prompt.
Successfully restoring from a shadow copy requires the ransomware not to have deleted the shadow copies as part of its operation. A successful recovery would involve selecting the desired shadow copy and restoring the files to a safe location.
Previous Backups
External hard drives, cloud storage, or network-attached storage (NAS) devices provide offsite backups, offering a crucial safety net against ransomware attacks. If you have a recent backup made before the attack, restoring from it is the most straightforward and reliable method for data recovery. This involves connecting the backup drive, accessing the backup, and restoring the files to a clean, uninfected system.
The speed and success of this method depend entirely on the backup’s recency and completeness.
Identifying and Extracting Unencrypted Files
Ransomware attacks don’t always encrypt every single file. Some files might be overlooked, or the encryption process might fail for certain files. Thoroughly examine your hard drive for any unencrypted files or folders. This manual search can be time-consuming, but it’s worth the effort. You might find crucial documents or data that were spared by the ransomware.
Using file search tools with specific filters for file types known to be often spared (like specific image types or text files) can help accelerate this process.
Data Recovery Technique Selection Flowchart
The following flowchart visually represents the decision-making process for choosing the most suitable data recovery method:[Imagine a flowchart here. The flowchart would begin with a “Ransomware Attack Detected” box. This would branch to “Shadow Copies Available?” A “Yes” branch would lead to “Attempt Shadow Copy Restoration,” and a “No” branch would lead to “Backup Available?” A “Yes” branch would lead to “Restore from Backup,” and a “No” branch would lead to “Search for Unencrypted Files.” All three recovery attempts would converge at a final “Data Recovery Complete/Incomplete” box.
Each stage of the flowchart could contain additional branching points based on success or failure at each step. For example, “Attempt Shadow Copy Restoration” might branch to “Successful” or “Unsuccessful” before proceeding to the next step.]
Investigating the Ransomware Infection
So, your system is encrypted. Panic is understandable, but now’s the time for methodical investigation. Understanding how the ransomware got in and what type it is is crucial for both immediate recovery and future prevention. This investigation should be done
before* attempting any data recovery, as improper steps can hinder the process or even worsen the situation.
The goal here is to identify the attack vector, the specific ransomware variant, and any lingering indicators that could compromise your system further. This information is invaluable for cleaning your system thoroughly and preventing future infections.
Potential Ransomware Entry Points
Identifying the point of entry is like tracing a criminal back to their crime scene. Common entry points include phishing emails containing malicious attachments or links, exploiting software vulnerabilities (often unpatched), infected USB drives, or compromised remote access tools. Analyzing recent activity, such as emails received, websites visited, and software installed, can help pinpoint the likely source of the infection.
Consider reviewing system logs for unusual activity around the time of the infection. A compromised RDP (Remote Desktop Protocol) session is also a common entry point, so verifying access logs is crucial. Thorough examination of your network security logs may reveal unusual traffic patterns that point to the infection source.
Determining the Type and Variant of Ransomware
The ransom note itself often provides clues. Many ransomware families have distinctive ransom notes with specific demands and contact information. Beyond the note, analyzing the file extensions that have been encrypted, the encryption method used (if visible in the file metadata), and any other files left behind by the ransomware (like configuration files or executables) can help identify the specific variant.
Online resources like VirusTotal can help by scanning suspicious files for known signatures. Searching for the ransom note text online can also reveal information about the specific ransomware variant involved.
Comparison of Ransomware Families and Encryption Methods
Ransomware families employ various encryption techniques. Some, like Ryuk, use AES encryption with a unique key for each victim, while others might employ RSA for key exchange. The strength of the encryption and the level of sophistication vary greatly. For instance, WannaCry used a relatively simple encryption algorithm, while more advanced variants use multi-layered encryption making decryption significantly harder.
So, you’ve been hit with ransomware – the first thing you should NOT do is restart your computer! That could permanently encrypt your files. Understanding robust security practices is key, and that’s where learning about cloud security becomes crucial, like exploring bitglass and the rise of cloud security posture management to prevent future attacks.
Proper cloud security is your best defense against this kind of nightmare; remember, don’t restart until you’ve taken the proper steps to recover your data.
Understanding the ransomware’s encryption method informs the feasibility of decryption—some are easier to crack than others. The difference in sophistication also affects the recovery process.
Indicators of Compromise (IOCs)
A systematic search for IOCs is vital to ensure a complete cleanup. These indicators can include newly created files, modified system files, unusual network connections, registry changes, and the presence of malicious processes. Checking for unusual processes running in Task Manager and reviewing system logs for suspicious events are crucial steps. Examining the network traffic using a network monitoring tool can reveal any communication the ransomware might be trying to establish with command-and-control servers.
A thorough examination of the system’s registry can uncover any malicious registry entries added by the ransomware. Specific IOCs will depend on the ransomware variant, but this systematic approach helps uncover them.
System Security Hardening (Post-Attack, Pre-Reboot)
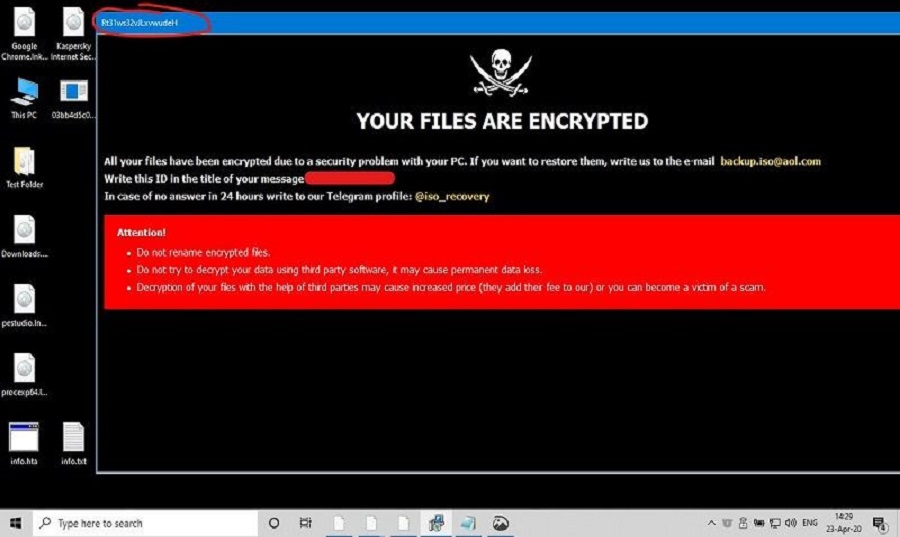
After a ransomware attack, before even thinking about recovery or rebooting, it’s crucial to take immediate steps to contain the damage and prevent further infection. This involves a process called system security hardening, which focuses on limiting the ransomware’s access and activity. This pre-reboot hardening is vital because rebooting could spread the infection or overwrite crucial evidence needed for investigation and recovery.System security hardening in this context involves disabling unnecessary services and processes that the ransomware might exploit to spread or encrypt more data.
This reduces the ransomware’s attack surface and limits its potential for further damage. It also involves implementing crucial security best practices to minimize the risk of future attacks. Remember, the goal is to stabilize the system before any recovery attempts are made.
Disabling Unnecessary Services and Processes
Identifying and disabling unnecessary services and processes requires careful consideration. You should prioritize disabling services related to file sharing, network access, and remote administration. The specific services to disable will depend on your operating system and the software installed. For example, in Windows, you might disable services like “Remote Desktop,” “File and Printer Sharing,” and any unnecessary background applications.
Using Task Manager (Windows) or Activity Monitor (macOS) can help you identify resource-intensive processes that might be related to the ransomware. Remember to only disable services you understand; disabling critical services could destabilize your system.
Security Best Practices Before Recovery or Reboot
Before attempting any data recovery or rebooting your system, implementing the following security best practices is essential:
- Disconnect from the Network: Immediately disconnect your computer from the internet and any network to prevent the ransomware from spreading to other devices or communicating with its command-and-control server.
- Isolate Affected Devices: If multiple devices are affected, isolate each one to prevent cross-contamination.
- Disable Auto-Run: Disable the autorun feature in your operating system to prevent malicious scripts from automatically executing.
- Review System Logs: Check your system logs for any suspicious activity that might provide clues about the ransomware’s entry point and behavior. This information is crucial for future investigation.
- Create a System Image (If Possible): If you can access a reliable backup or imaging tool, creating a system image before rebooting can help preserve the system’s state for forensic analysis.
Preventing Future Ransomware Infections, Dont restart your computer after a ransomware attack
Implementing robust security measures is paramount to prevent future ransomware infections. This includes a multi-layered approach combining technological and procedural safeguards.
- Regular Software Updates: Regularly update your operating system, applications, and antivirus software to patch known vulnerabilities.
- Strong Passwords and Multi-Factor Authentication (MFA): Use strong, unique passwords for all accounts and enable MFA wherever possible.
- Robust Antivirus and Endpoint Detection and Response (EDR): Employ a comprehensive security suite including robust antivirus software and EDR solutions for real-time threat detection and response.
- Employee Security Awareness Training: Educate your employees about phishing scams, malicious attachments, and other social engineering tactics used to deliver ransomware.
- Regular Backups: Regularly back up your important data to an offline location, such as an external hard drive or cloud storage that is not connected to your network.
- Network Segmentation: Segment your network to isolate critical systems and data from less critical ones. This limits the impact of a breach.
- Principle of Least Privilege: Restrict user access to only the resources they need to perform their jobs. This minimizes the potential damage from a compromised account.
Malware Scanning Software (Pre-Reboot)
Several security software solutions can scan for malware without requiring a reboot. This is crucial in a ransomware situation, as a reboot might spread the infection or corrupt data.
| Software Name | Description | Key Features | Compatibility |
|---|---|---|---|
| Malwarebytes | A popular anti-malware program known for its effectiveness against ransomware. | Real-time protection, malware scanning, removal tools, quarantine feature. | Windows, macOS, Android, iOS |
| HitmanPro | A second-opinion scanner designed to detect and remove malware that other antivirus programs might miss. | Cloud-based scanning, quick scans, removal tools. | Windows |
| Kaspersky Rescue Disk | A bootable rescue disk that can scan and remove malware from a system even if it’s heavily compromised. | Bootable from USB, comprehensive malware scanning, system repair tools. | Windows |
| ESET NOD32 Antivirus | A reputable antivirus solution offering powerful malware detection and removal capabilities. | Real-time protection, advanced threat detection, proactive defense. | Windows, macOS, Linux, Android |
Communicating with Law Enforcement and/or Cybersecurity Experts
Facing a ransomware attack is incredibly stressful, and knowing who to contact and how to proceed can feel overwhelming. Effective communication with law enforcement and cybersecurity experts is crucial for mitigating the damage and potentially recovering your data. This involves careful documentation, a structured reporting process, and a commitment to preserving the integrity of evidence.Gathering the right information before contacting authorities is paramount.
This proactive approach streamlines the investigation and helps experts understand the scope of the attack more efficiently.
Information to Collect Before Contacting Authorities
Before contacting law enforcement or cybersecurity professionals, meticulously document all aspects of the ransomware attack. This includes the date and time of discovery, the method of infection (e.g., phishing email, malicious link), the type of ransomware (if identified), the affected systems and data, and any ransom demands received. Screenshots of ransom notes, encrypted files, and system logs are invaluable.
Note down any unusual network activity or suspicious emails received prior to the attack. If you have any backups, document their location, date of creation, and accessibility. This detailed record significantly assists investigators in their analysis.
Reporting a Ransomware Attack
Reporting the attack involves contacting the appropriate authorities. For significant attacks affecting critical infrastructure or involving large-scale data breaches, reporting to the FBI’s Internet Crime Complaint Center (IC3) is essential. For smaller-scale attacks, local law enforcement might be the first point of contact. Simultaneously, engaging a reputable cybersecurity firm specializing in incident response is highly recommended. They possess the expertise to contain the attack, investigate its origins, and help in data recovery efforts.
Remember to provide them with the comprehensive documentation you’ve already prepared. The quicker the response, the better the chances of limiting the damage.
Preserving Evidence Integrity
Maintaining the integrity of evidence is critical for a successful investigation. Avoid accessing or modifying any files on affected systems. This includes refraining from attempts to decrypt files using unlicensed tools or engaging with the attackers without expert guidance. Any action taken without proper forensic expertise could compromise the evidence and hinder the investigation. Isolate affected systems from the network to prevent further spread of the ransomware.
If possible, create forensic images of affected drives before attempting any recovery efforts. This ensures that the original data remains untouched for analysis.
Sample Email for Reporting a Ransomware Attack
Subject: Urgent: Ransomware Attack – [Your Company Name/Personal Information]To: [Recipient Email Address – e.g., IC3, Local Law Enforcement, Cybersecurity Firm]Dear [Recipient Name],Our organization/I have experienced a ransomware attack on [Date] at approximately [Time]. The attack affected [List affected systems and data]. We believe the attack originated from [Suspected source, if known]. We have attached [List of attached documents, e.g., ransom note, system logs, screenshots].We request immediate assistance in investigating this incident and containing the spread of the ransomware.
We are currently [Describe actions taken, e.g., isolating affected systems]. We are available to answer any questions and provide further information as needed.Sincerely,[Your Name/Company Name][Your Contact Information]
Visual Representation of the Infection Process
Understanding the visual progression of a ransomware attack is crucial for effective mitigation and recovery. This section will detail the typical stages, the impact on system resources, and the telltale signs of ransomware’s destructive work on system files and registry entries. Visualizing these aspects allows for quicker identification and response during an active attack.
A typical ransomware attack unfolds in several distinct phases. We can represent this as a flowchart, moving from initial infection to full encryption and the display of the ransom note.
Ransomware Infection Stages
The following diagram depicts the typical stages of a ransomware attack. Imagine a simple flowchart with boxes connected by arrows.
Stage 1: Initial Infection. (Box 1) This is the entry point, often through a phishing email containing a malicious attachment or link, a software vulnerability exploit, or a compromised remote desktop protocol (RDP) session. The arrow points to…
Stage 2: Lateral Movement. (Box 2) Once inside, the ransomware may attempt to spread to other systems on the network, accessing shared drives and exploiting vulnerabilities to maximize its impact. The arrow points to…
Stage 3: Data Encryption. (Box 3) This is the core of the attack. The ransomware identifies and encrypts targeted files, often using strong encryption algorithms making decryption without the decryption key extremely difficult. The arrow points to…
Stage 4: Ransom Note Display. (Box 4) After encryption, the ransomware displays a ransom note, providing instructions on how to pay the ransom and often including a timer or threat of data deletion. The arrow stops here.
Impact on System Resources
The visual impact of a ransomware attack on system resources can be observed through various system monitoring tools. Imagine a graph showing CPU usage, memory usage, and disk I/O.
During the encryption phase, you’d see a significant spike in CPU and disk I/O usage. The CPU would be heavily utilized by the encryption algorithms, and the disk I/O would reflect the massive read and write operations as files are encrypted. Memory usage might also increase as the ransomware loads and executes its malicious code. A noticeable slowdown of the system would be a visual cue.
This heavy resource consumption can lead to system freezes or crashes in severe cases.
System File and Registry Alterations
Ransomware leaves distinct digital footprints within the system’s files and registry entries. These alterations can be detected using forensic tools. Let’s consider some examples.
File Alterations: Imagine a file explorer window showing a folder full of files. Many files will have an extension appended to their original names (e.g., “document.docx” becomes “document.docx.crypt”). This clearly shows the encryption process. Also, the ransomware might create additional files related to its operation, such as configuration files or log files, often hidden or located in unusual directories.
Registry Entries: Imagine a registry editor window. Ransomware often modifies registry keys to achieve persistence, ensuring that it runs automatically upon system startup. It might add itself to the Run key or other startup locations. It could also create new registry keys or modify existing ones to disable security software or modify system settings. These changes would need to be carefully examined by a forensic expert to understand the extent of the intrusion.
Last Recap
Facing a ransomware attack is a serious situation, but by taking swift and informed action, you can significantly improve your chances of recovery. Remember, the key is to remain calm, follow the steps Artikeld above, and prioritize data preservation. Don’t restart your computer! Instead, focus on isolating the affected system, creating a disk image, and seeking professional help if needed.
Taking these steps will not only protect your data but also help you understand how the attack happened and prevent future incidents. Stay safe and proactive!
Frequently Asked Questions: Dont Restart Your Computer After A Ransomware Attack
What if I accidentally restarted my computer?
Unfortunately, restarting often overwrites crucial data, making recovery significantly harder. Data recovery may still be possible, but your chances are greatly reduced. Contact a cybersecurity professional immediately.
Should I pay the ransom?
Paying the ransom is generally not recommended. There’s no guarantee you’ll get your data back, and you’ll be encouraging further criminal activity. Focus on data recovery and reporting the incident to authorities.
How long can I safely leave my computer off before attempting recovery?
The sooner you start the recovery process, the better. However, leaving the computer off while you prepare your recovery strategy is generally fine. The longer you wait, the higher the risk of data loss or further compromise if the malware is still active.
Can I use my regular antivirus software after a ransomware attack?
Using your regular antivirus software might not be effective, as the ransomware may have already disabled or bypassed it. Focus on creating a disk image and using specialized forensic tools for analysis.





