Dropbox Sign Witnesses Data Breach A Deep Dive
Dropbox Sign witnesses data breach – the very phrase sends shivers down your spine, doesn’t it? Imagine the sensitive information entrusted to this platform – legal documents, financial records, even personal health details – potentially exposed. This post explores the hypothetical yet chilling possibility of a data breach impacting witnesses using Dropbox Sign, examining the security measures in place, potential vulnerabilities, and the devastating consequences for both users and the platform itself.
We’ll dissect the legal implications, explore mitigation strategies, and delve into the crucial role of user education in preventing such a catastrophic event.
We’ll look at how Dropbox Sign handles witness data, from storage and retention policies to compliance with regulations like GDPR and CCPA. We’ll then build a hypothetical breach scenario, outlining the potential damage and exploring what steps Dropbox Sign, and its users, could take to prevent a similar situation. The goal isn’t to spread fear, but to foster awareness and encourage proactive measures to protect sensitive data.
Dropbox Sign Security Overview
Dropbox Sign prioritizes the security and privacy of its users’ data. They employ a multi-layered approach to protect sensitive information throughout its lifecycle, from creation to storage and eventual deletion. This involves robust security measures across various aspects of their platform, including authentication, authorization, encryption, and incident response.Dropbox Sign utilizes a comprehensive suite of security measures to safeguard user data.
These measures are continuously evaluated and updated to adapt to the ever-evolving threat landscape. The platform’s security posture is a key component of their service offering, aiming to provide a secure and reliable e-signature solution.
Authentication and Authorization Processes
Dropbox Sign employs strong authentication methods to verify user identities. This typically includes password-based authentication, often enhanced with multi-factor authentication (MFA) options such as one-time codes sent via email or SMS, or authenticator app verification. This layered approach makes it significantly more difficult for unauthorized individuals to access accounts. Authorization controls restrict access to specific features and data based on user roles and permissions, preventing unauthorized modification or disclosure of documents.
For example, only designated administrators might have access to certain system settings, while regular users only have access to their own documents and accounts.
Data Encryption Methods
Dropbox Sign employs robust encryption methods to protect data both at rest and in transit. Data at rest, meaning data stored on Dropbox Sign’s servers, is encrypted using strong encryption algorithms to prevent unauthorized access even if a server were compromised. Data in transit, meaning data transmitted between users’ devices and Dropbox Sign’s servers, is encrypted using HTTPS (TLS/SSL), ensuring confidentiality during transmission.
This protects the data from eavesdropping or interception during transfer. The specific encryption algorithms used are regularly reviewed and updated to reflect the latest security best practices and withstand emerging cryptographic attacks.
Dropbox Sign’s Incident Response Plan
Dropbox Sign has a well-defined incident response plan to address security breaches or incidents effectively and efficiently. This plan Artikels procedures for identifying, containing, and remediating security incidents, including data breaches. The plan includes protocols for notifying affected users, cooperating with law enforcement, and conducting thorough post-incident reviews to identify vulnerabilities and improve security measures. Regular security audits and penetration testing are also conducted to proactively identify and address potential weaknesses in the system.
Their plan incorporates best practices from industry standards like NIST Cybersecurity Framework, ensuring a structured and comprehensive approach to incident management. The goal is to minimize the impact of any security incidents and restore services as quickly and safely as possible.
Witness Data Handling in Dropbox Sign

Dropbox Sign prioritizes the secure handling of witness data throughout the e-signature process, recognizing the sensitive nature of this information. Their approach incorporates robust security measures and adherence to relevant data privacy regulations to ensure the confidentiality and integrity of witness details. This commitment extends from data collection to storage and eventual deletion.Witness data, including names, email addresses, and IP addresses (where applicable), is collected only when a witness is actively involved in the signing process.
This information is essential for authentication and verification purposes, ensuring the validity of the witnessed signature. Dropbox Sign employs various methods to minimize data collection, gathering only what is strictly necessary for the successful completion of the e-signature workflow.
Data Storage and Retention
Witness data is stored on secure servers utilizing industry-standard encryption methods, both in transit and at rest. The precise location of these servers may vary depending on factors such as user location and data residency requirements. Dropbox Sign adheres to a data retention policy that aligns with relevant legal and regulatory obligations. Generally, this policy dictates that witness data is retained for a specific period, after which it is securely deleted.
The exact retention period is determined by legal requirements and Dropbox Sign’s internal policies, ensuring compliance with regulations such as GDPR and CCPA. For example, if a legal hold is placed on a document, the associated witness data will be retained until the hold is released.
The Dropbox Sign witnesses data breach really highlights the importance of robust security in digital document workflows. Thinking about solutions, I’ve been exploring more secure development options, and learning about the exciting advancements in domino app dev, the low-code and pro-code future , which could offer a more controlled environment for sensitive data. Ultimately, the Dropbox breach underscores the need for better security measures across all digital signing platforms.
Data Privacy and Confidentiality Measures
Dropbox Sign implements several security measures to safeguard witness data privacy. These include access controls limiting data access to authorized personnel only, regular security audits to identify and address vulnerabilities, and encryption protocols to protect data during transmission and storage. Furthermore, Dropbox Sign employs robust intrusion detection and prevention systems to monitor for and mitigate potential security threats.
The platform undergoes regular penetration testing and vulnerability assessments to proactively identify and address potential weaknesses in its security posture. For instance, multi-factor authentication is encouraged for all users, adding an extra layer of security to protect account access and the sensitive data within.
Compliance with Data Privacy Regulations
Dropbox Sign actively works to ensure compliance with various data privacy regulations globally. This includes adherence to the General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA) in California, and other relevant jurisdictional laws. They provide users with control over their data through features such as data subject access requests and the ability to download or delete their data.
Dropbox Sign maintains comprehensive documentation outlining its data privacy practices and security measures, readily available to users upon request. For example, Dropbox Sign’s data processing agreements clearly articulate the responsibilities of both the platform and its users regarding data handling and privacy. The platform also participates in industry best practices and regularly updates its security measures to reflect the evolving threat landscape.
Hypothetical Data Breach Scenario
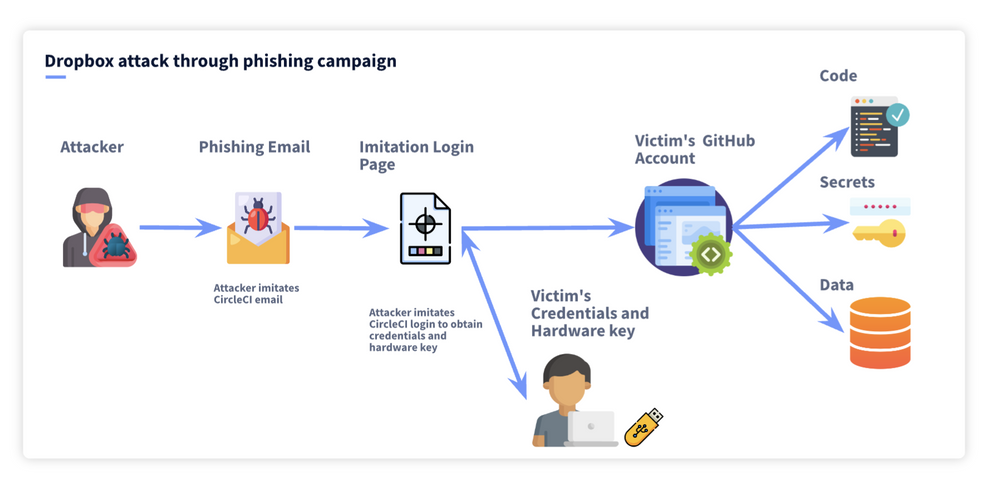
Imagine a sophisticated phishing attack targeting employees of a large multinational corporation using Dropbox Sign for crucial legal and financial documents. The attackers successfully compromise employee credentials, gaining unauthorized access to the Dropbox Sign platform. This breach isn’t a simple password grab; it involves exploiting a previously unknown vulnerability in the platform’s security protocols, allowing for sustained access and data exfiltration.This breach goes beyond simply accessing document content.
The attackers focus on witness data, specifically targeting documents involving sensitive financial transactions, property transfers, and legal agreements. The breach remains undetected for several weeks, allowing the attackers to download a significant amount of witness information.
Sensitive Information Exposed in the Breach
The compromised witness data includes names, email addresses, IP addresses at the time of witnessing, physical addresses (in some cases), and potentially even partial or full copies of government-issued identification documents that were uploaded as part of the witnessing process. The sheer volume of data, coupled with the sensitive nature of the information, creates a substantial risk for both the witnesses and Dropbox Sign itself.
For instance, a witness’s home address, combined with their name, could lead to identity theft. Exposure of financial transaction details could lead to fraudulent activities.
Consequences for Affected Witnesses
The consequences for affected witnesses are severe and multifaceted. Identity theft is a primary concern, with potential for financial loss, damaged credit scores, and the emotional distress associated with such crimes. Furthermore, the exposure of sensitive personal data could lead to phishing attacks targeting witnesses directly, attempting to exploit their compromised information. Depending on the specific nature of the documents witnessed, witnesses may face legal ramifications, particularly if the compromised data is used in fraudulent activities.
The reputational damage stemming from such a breach could also have significant personal consequences.
Legal and Reputational Risks for Dropbox Sign
Dropbox Sign faces significant legal and reputational risks following such a breach. Class-action lawsuits from affected witnesses are highly probable, leading to substantial financial liabilities. Regulatory fines from data protection authorities (like the GDPR in Europe or CCPA in California) are also likely, adding to the financial burden. Beyond the financial penalties, the damage to Dropbox Sign’s reputation could be catastrophic, leading to a loss of customer trust and impacting their market share.
The company would likely experience a significant drop in stock value and face intense scrutiny from investors and the media. The long-term consequences could involve significant restructuring and investment in enhanced security measures to regain public confidence. The impact would be similar to what other companies have experienced in major data breaches, with potential for long-term legal battles and brand damage.
Mitigation Strategies and Best Practices

Protecting witness data in e-signature platforms is paramount. A data breach can have severe consequences, including legal penalties, reputational damage, and loss of customer trust. Implementing robust security measures and educating users about best practices are crucial for mitigating risks. This section Artikels strategies to safeguard witness information within Dropbox Sign and similar platforms.
User best practices are vital in preventing data breaches. Even the most secure system is vulnerable if users don’t follow safe practices.
The Dropbox Sign witnesses data breach really highlights the urgent need for robust cloud security. It makes you wonder how many other platforms are vulnerable. Learning more about solutions like Bitglass, and the rise of cloud security posture management as discussed in this excellent article, bitglass and the rise of cloud security posture management , is crucial.
Understanding these advancements is key to preventing future incidents like the Dropbox Sign breach.
Best Practices for Users Protecting Witness Data in Dropbox Sign, Dropbox sign witnesses data breach
Following these practices will significantly reduce the risk of compromised witness information.
- Strong Passwords: Use unique, complex passwords for your Dropbox Sign account, incorporating a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable passwords or reusing passwords across multiple accounts.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security by requiring a second verification method, such as a code from your phone or email, in addition to your password. This significantly hinders unauthorized access, even if your password is compromised.
- Regular Password Changes: Change your Dropbox Sign password regularly, at least every three months, to minimize the window of vulnerability if a breach occurs.
- Secure Devices: Only access your Dropbox Sign account from trusted and secure devices. Avoid using public Wi-Fi networks or unsecured computers.
- Software Updates: Keep your operating system, web browser, and other software updated to patch security vulnerabilities.
- Phishing Awareness: Be wary of suspicious emails or links that claim to be from Dropbox Sign. Never click on links or open attachments from unknown senders.
- Review Access Permissions: Regularly review and revoke access permissions for any applications or individuals that no longer require access to your Dropbox Sign account.
- Report Suspicious Activity: Immediately report any suspicious activity, such as unauthorized login attempts or unusual account behavior, to Dropbox Sign’s support team.
Data Protection Strategies Comparison
Several strategies can be employed to protect witness data. This table compares their effectiveness and drawbacks.
| Strategy | Description | Pros | Cons |
|---|---|---|---|
| Data Encryption | Encrypting witness data both in transit and at rest using strong encryption algorithms. | Protects data even if a breach occurs; complies with data privacy regulations. | Can add overhead; requires careful key management. |
| Access Control Lists (ACLs) | Restricting access to witness data based on roles and permissions. | Granular control over data access; improves security posture. | Can be complex to manage; requires careful planning and implementation. |
| Multi-Factor Authentication (MFA) | Requiring multiple forms of authentication to access the system. | Significantly reduces the risk of unauthorized access, even with stolen credentials. | Can be inconvenient for users; requires user education and adoption. |
| Regular Security Audits | Periodically reviewing security controls and identifying vulnerabilities. | Proactive identification and mitigation of risks; improves overall security. | Requires resources and expertise; can be time-consuming. |
Dropbox Sign Security Enhancements
Dropbox Sign can enhance its security posture through several improvements.
- Enhanced Encryption: Implement stronger encryption algorithms and key management practices to protect witness data more effectively.
- Improved Access Controls: Refine access control mechanisms to ensure only authorized personnel can access sensitive witness information.
- Regular Penetration Testing: Conduct regular penetration testing and vulnerability assessments to identify and address security weaknesses proactively.
- Security Information and Event Management (SIEM): Implement a SIEM system to monitor security events and detect anomalies in real-time.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to handle security breaches effectively.
- Employee Training: Provide regular security awareness training to employees to educate them about best practices and potential threats.
Implementing Multi-Factor Authentication (MFA)
MFA adds a crucial layer of security by requiring users to provide multiple forms of authentication before gaining access to their accounts. This significantly reduces the risk of unauthorized access, even if an attacker obtains a user’s password.
For example, if an attacker gains access to a Dropbox Sign user’s password through phishing, they would still need to provide a second factor, such as a one-time code from a mobile authenticator app or an email code, to log in. This makes it considerably more difficult for attackers to access witness data.
Implementing MFA can involve various methods, including time-based one-time passwords (TOTP), push notifications, security keys, and biometrics. Dropbox Sign should offer users a range of MFA options to cater to different preferences and security needs. Clear and concise instructions on how to enable and use MFA should be readily available to users.
Legal and Regulatory Compliance
A Dropbox Sign data breach involving witness data carries significant legal and regulatory implications, potentially exposing the company and its clients to substantial fines and legal action. The severity of the consequences depends on various factors, including the nature and extent of the breach, the type of data compromised, and the applicable laws and regulations in the affected jurisdictions.
Understanding these legal frameworks is crucial for mitigating risk and ensuring compliance.The legal landscape surrounding data breaches is complex and constantly evolving. However, several key regulations consistently emerge as paramount in protecting witness data.
Data Privacy Regulations Applicable to Witness Data
Witness data, which may include personally identifiable information (PII) like names, addresses, and potentially sensitive information depending on the document being witnessed, falls under the purview of numerous data privacy regulations globally. Key regulations include the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in California, USA. These laws establish strict rules regarding the collection, processing, storage, and protection of personal data, including the requirement to implement appropriate security measures to prevent data breaches.
Other regional and national laws, like the Brazilian LGPD, also apply depending on the location of the data subjects and the company’s operations.
Consequences of Non-Compliance
Non-compliance with data privacy regulations like GDPR and CCPA can result in severe penalties. GDPR, for example, can levy fines of up to €20 million or 4% of annual global turnover, whichever is higher, for serious breaches. The CCPA, while not as financially punitive, allows for private right of action, meaning individuals can sue companies for violations, potentially leading to substantial legal costs and reputational damage.
In the case of a Dropbox Sign witness data breach, non-compliance could lead to class-action lawsuits from affected witnesses, further compounding the financial and reputational risks. For instance, a hypothetical breach exposing the PII of thousands of witnesses in Europe could trigger a GDPR investigation and significant fines, while a similar breach in California could result in numerous CCPA lawsuits.
Data Breach Notification Laws
Data breach notification laws mandate that organizations promptly inform affected individuals and relevant authorities about data breaches involving personal information. The specifics of notification requirements vary by jurisdiction. For example, some jurisdictions require notification within a specific timeframe (e.g., 72 hours), while others stipulate that notification must occur without undue delay. Failure to comply with these notification laws can result in additional penalties and fines.
In the context of a Dropbox Sign breach, the company would be legally obligated to notify affected witnesses about the breach, outlining the nature of the compromised data and the steps being taken to mitigate the harm. Failure to do so could expose Dropbox Sign to further legal action and erode public trust.
User Education and Awareness
Effective user education is paramount in preventing data breaches and ensuring the responsible handling of sensitive witness information within Dropbox Sign. A comprehensive program that combines proactive training, clear communication, and readily accessible resources is crucial for mitigating risk. Ignoring user education leaves a significant vulnerability in your security posture.
A well-designed user education program not only reduces the likelihood of accidental data breaches but also fosters a culture of security awareness within your organization. This proactive approach empowers users to become active participants in protecting sensitive data, ultimately strengthening your overall security posture.
Key Information for Dropbox Sign Users
The following bullet points highlight essential information that all Dropbox Sign users should understand to protect witness data and maintain the security of the platform.
- Understand Data Sensitivity: Recognize that witness information is sensitive and requires careful handling. This includes names, addresses, email addresses, and any other personally identifiable information.
- Strong Password Practices: Use strong, unique passwords for your Dropbox Sign account and regularly update them. Avoid reusing passwords across multiple platforms.
- Recognize Phishing Attempts: Be vigilant against phishing emails and suspicious links. Never click on links or open attachments from unknown senders.
- Report Suspicious Activity: Immediately report any suspicious activity, such as unauthorized access attempts or unusual logins, to your organization’s IT department or Dropbox Sign support.
- Secure Device Management: Use updated anti-malware software and keep your devices (computers, mobile phones) secure with strong passwords and up-to-date operating systems.
- Privacy Settings: Familiarize yourself with Dropbox Sign’s privacy settings and ensure they align with your organization’s security policies.
- Document Security: Understand the document access controls within Dropbox Sign and use them appropriately to restrict access to sensitive documents.
Sample User Education Program
A multi-faceted approach is necessary for effective user education. This sample program incorporates various methods to reach and engage users.
- Initial Training: Mandatory online training modules covering data security best practices, phishing awareness, and responsible data handling within Dropbox Sign. This should include interactive elements and quizzes to reinforce learning.
- Regular Refresher Courses: Short, regular refresher courses to reinforce key concepts and address emerging threats. These could be delivered via email newsletters, short videos, or quick online quizzes.
- Security Awareness Campaigns: Periodic campaigns using posters, emails, and internal communications to highlight security best practices and raise awareness of potential threats.
- Interactive Workshops: Hands-on workshops to provide practical training on using Dropbox Sign securely and addressing common security challenges.
- Accessible Resources: Provide easily accessible resources, such as FAQs, cheat sheets, and video tutorials, that users can refer to as needed.
Importance of User Training in Preventing Data Breaches
User training is not merely a compliance exercise; it is a critical component of a robust security strategy. Neglecting user education significantly increases the risk of data breaches stemming from human error. Comprehensive training empowers users to identify and avoid phishing attempts, use strong passwords, and handle sensitive data responsibly. This proactive approach reduces the likelihood of accidental data exposure and strengthens the overall security posture of the organization.
For example, a recent study showed that 88% of data breaches involved a human element, highlighting the critical role of user education in preventing such incidents.
Effective Communication Strategies
Effective communication is key to successful user education. Employing a variety of channels ensures the message reaches all users.
- Clear and Concise Messaging: Use plain language and avoid technical jargon. Focus on the “why” behind security practices to encourage user buy-in.
- Multiple Communication Channels: Utilize emails, internal newsletters, posters, intranet articles, and even short video tutorials to reach a broader audience.
- Interactive Training: Engage users with interactive elements such as quizzes, games, and scenarios to make learning more engaging and memorable.
- Regular Feedback and Updates: Solicit feedback from users and regularly update training materials to reflect evolving threats and best practices.
- Gamification: Incorporate gamification elements, such as points, badges, and leaderboards, to motivate users and encourage participation in security training.
Conclusive Thoughts: Dropbox Sign Witnesses Data Breach
The potential for a Dropbox Sign witnesses data breach underscores the critical need for robust security measures and user awareness. While Dropbox Sign employs various security protocols, the human element remains a significant vulnerability. By understanding the risks, implementing best practices, and staying informed about evolving threats, we can collectively strive towards a safer digital environment where sensitive data remains protected.
Remember, vigilance and proactive security measures are our best defense against data breaches. Let’s prioritize data security and ensure that the trust placed in e-signature platforms like Dropbox Sign remains well-founded.
FAQs
What types of witness data are most at risk in a Dropbox Sign breach?
Witness names, addresses, email addresses, IP addresses, and potentially even the content of the signed document itself are all vulnerable.
What is Dropbox Sign’s responsibility if a data breach occurs?
Their responsibility would depend on applicable laws and their own terms of service. This likely includes notifying affected users, cooperating with investigations, and potentially offering credit monitoring or other remediation services.
Can I opt out of having witnesses on my Dropbox Sign documents?
Depending on the document and its purpose, you may be able to forgo witnesses, though this might impact the legal validity in certain situations.
How often does Dropbox Sign update its security protocols?
Dropbox Sign regularly updates its security protocols; however, specific update frequencies aren’t publicly available. Checking their security page for announcements is recommended.