Enhancing Higher Education Security The Role of SSE
Enhancing higher education security the role of security service edge axis security – Enhancing higher education security: the role of security service edge (SSE) axis security is more critical than ever. Our universities and colleges are facing a rapidly evolving threat landscape, from sophisticated phishing attacks to data breaches targeting sensitive student and research information. Traditional network security solutions are often struggling to keep pace, leaving institutions vulnerable. This is where Security Service Edge (SSE) comes in, offering a modern, cloud-based approach to securing access to applications and data, regardless of location.
We’ll explore how SSE’s components – Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA) – can bolster higher education’s defenses.
This post will delve into the specific challenges faced by higher education institutions, showcasing how SSE can protect sensitive data, including student records, research findings, and financial information. We’ll examine best practices for implementation, address potential challenges, and look at the future of SSE in a zero-trust environment. Get ready to learn how SSE can significantly enhance your institution’s cybersecurity posture.
Defining the Higher Education Security Landscape
Higher education institutions face a unique and increasingly complex security landscape. The open nature of campuses, combined with the reliance on sophisticated IT infrastructure to support research, teaching, and administration, creates a vast attack surface vulnerable to a wide range of threats. Understanding this landscape is crucial for implementing effective security measures.The current threats facing higher education institutions are diverse and constantly evolving.
They range from relatively simple phishing attacks targeting students and staff to sophisticated state-sponsored cyber espionage targeting sensitive research data. The financial incentives for attackers are significant, with institutions holding valuable intellectual property, student data, and financial resources. Furthermore, the reputational damage from a successful cyberattack can be devastating.
Securing higher education networks is a huge challenge, demanding robust solutions like Security Service Edge (SSE). Efficient application development plays a key role; for instance, streamlining administrative tasks could be achieved through tools discussed in this insightful article on domino app dev, the low-code and pro-code future , which highlights how to build secure and user-friendly apps.
Ultimately, integrating such efficient development with a strong SSE framework is vital for comprehensive higher education security.
Key Vulnerabilities in Higher Education IT Infrastructure
Higher education IT infrastructures often present several key vulnerabilities. Outdated systems, a lack of centralized security management, and insufficient security awareness training among staff and students contribute significantly to the overall risk profile. The decentralized nature of many university networks, with numerous departments and research labs managing their own systems, can make it difficult to implement consistent security policies and practices.
Furthermore, the reliance on third-party vendors for various services introduces additional vulnerabilities into the ecosystem. The use of unpatched software, weak passwords, and insecure network configurations are common weaknesses that attackers readily exploit.
The Evolving Nature of Cyber Threats Targeting Universities and Colleges
Cyber threats against higher education are becoming increasingly sophisticated and targeted. Ransomware attacks, designed to encrypt sensitive data and demand a ransom for its release, are a growing concern. Advanced persistent threats (APTs), often state-sponsored, aim to steal intellectual property or sensitive research data over an extended period. Data breaches, resulting from compromised systems or insider threats, can expose sensitive student and faculty information, leading to significant legal and financial repercussions.
The rise of artificial intelligence (AI) is also influencing the nature of attacks, enabling attackers to automate previously manual processes and develop more effective phishing campaigns. For example, the use of AI-powered deepfakes to impersonate university officials in phishing emails is a rapidly emerging threat.
Legal and Regulatory Compliance Requirements for Higher Education Security
Higher education institutions are subject to a complex web of legal and regulatory requirements regarding data security and privacy. Regulations such as the Family Educational Rights and Privacy Act (FERPA) in the United States, and the General Data Protection Regulation (GDPR) in Europe, impose strict requirements on how student data is collected, stored, and protected. Non-compliance can lead to significant fines and reputational damage.
Furthermore, institutions must comply with industry best practices and security standards, such as those Artikeld by the National Institute of Standards and Technology (NIST). The specific requirements vary depending on the institution’s location, the type of data it handles, and the services it provides. For instance, institutions involved in research funded by government agencies often face additional compliance requirements related to data security and intellectual property protection.
Failure to adhere to these regulations can result in significant legal and financial penalties.
Introducing Security Service Edge (SSE)
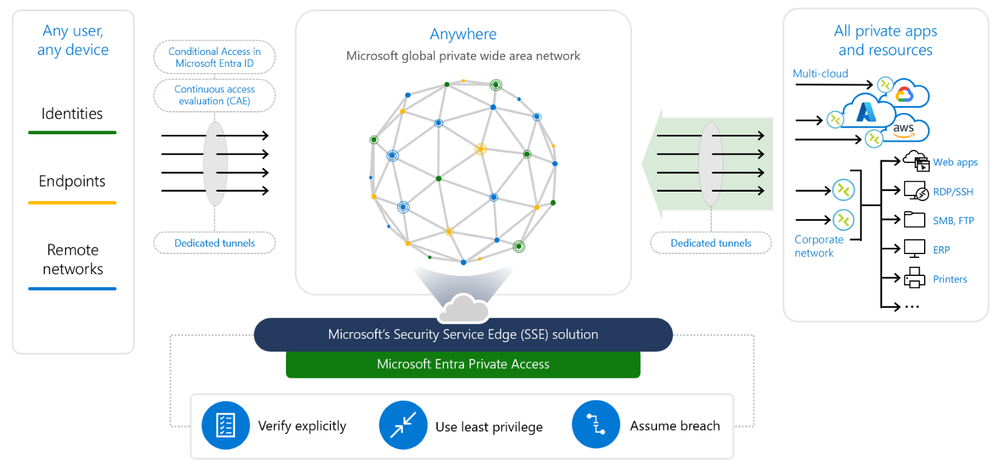
Higher education institutions face a unique set of security challenges, from protecting sensitive research data to safeguarding student information. Traditional network security approaches, often reliant on perimeter-based defenses, are increasingly inadequate in today’s cloud-first, mobile-first world. This is where Security Service Edge (SSE) comes in, offering a modern, cloud-delivered approach to securing access to applications and data regardless of location.SSE consolidates several security functions into a single, integrated platform, providing a more comprehensive and efficient security posture.
This contrasts sharply with the fragmented, often siloed, nature of traditional security solutions. The core benefit is simplified management and improved visibility across all access points, enhancing the overall security effectiveness.
SSE Core Functionalities and Components
SSE typically integrates three key components: Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA). The SWG filters web traffic, protecting against malware and phishing attacks. The CASB monitors and controls access to cloud applications, ensuring data security and compliance. Finally, ZTNA provides secure access to internal applications, only granting access to authorized users and devices based on granular policies.
This layered approach significantly strengthens security while improving user experience by eliminating the need for VPNs in many scenarios.
Comparison of SSE with Traditional Network Security
Traditional network security relies heavily on perimeter-based defenses, such as firewalls and VPNs. This approach becomes increasingly challenging to manage and maintain as institutions adopt cloud services and embrace remote work. SSE, on the other hand, adopts a zero-trust model, verifying every user and device before granting access, regardless of location. This shift from perimeter-based security to identity-based security significantly improves protection against sophisticated threats.
Traditional approaches often struggle with visibility into cloud traffic and application usage, whereas SSE provides comprehensive monitoring and control across all access points.
Addressing Higher Education Security Challenges with SSE
SSE can effectively address several key security challenges faced by higher education institutions. For example, it can prevent students from accessing malicious websites, protect sensitive research data stored in the cloud, and ensure secure access to internal systems for faculty and staff working remotely. The ability to enforce granular access control policies ensures that only authorized individuals can access specific data and applications, mitigating the risk of data breaches and unauthorized access.
Furthermore, the consolidated nature of SSE simplifies security management, reducing the burden on IT teams and allowing them to focus on more strategic initiatives.
Hypothetical SSE Architecture for a Medium-Sized University
A medium-sized university could implement an SSE architecture consisting of a cloud-based SSE platform from a reputable vendor. This platform would integrate SWG, CASB, and ZTNA functionalities. The university’s existing identity provider (IdP) would be integrated with the SSE platform to enable seamless authentication and authorization. All university-owned devices would be enrolled in the platform’s mobile device management (MDM) system for enhanced security and control.
The SSE platform would monitor all network traffic and application usage, generating detailed logs and reports to aid in security monitoring and incident response. This architecture would provide a robust and scalable solution for securing the university’s network and applications, while improving the overall security posture and simplifying management.
SSE’s Role in Enhancing Higher Education Security: Enhancing Higher Education Security The Role Of Security Service Edge Axis Security
Higher education institutions face a unique set of security challenges. They manage vast amounts of sensitive student data, support a diverse range of devices and users (students, faculty, staff, and guests), and often operate on limited budgets. Security Service Edge (SSE) offers a compelling solution to these challenges by consolidating various security functions into a single, cloud-delivered platform.
This approach simplifies security management, improves protection, and can even lead to cost savings in the long run.SSE offers a comprehensive approach to securing access to applications and data, regardless of location. This is particularly beneficial for higher education institutions, which often have geographically dispersed campuses, remote learners, and a diverse range of devices accessing their network and data.
By centralizing security policies and enforcement, SSE significantly reduces the complexity of managing security across a distributed environment.
Protecting Student Data with SSE
Student data is incredibly valuable, yet also incredibly vulnerable. SSE protects this data through various mechanisms, including secure web gateways (SWGs) that filter malicious traffic, zero trust network access (ZTNA) that restricts access based on user identity and context, and data loss prevention (DLP) tools that prevent sensitive information from leaving the network unauthorized. For example, an SSE solution could prevent a student from accidentally uploading a file containing personally identifiable information (PII) to an unapproved cloud storage service.
The granular control offered by SSE allows institutions to tailor their security policies to the specific needs of different user groups, ensuring that only authorized individuals have access to sensitive data.
Integrating SSE with Existing Security Systems
Successful SSE integration requires careful planning and execution. It’s crucial to assess existing security infrastructure to identify potential overlaps and conflicts. Many institutions already have firewalls, intrusion detection systems, and other security tools in place. A phased approach, starting with a pilot project, can help minimize disruption and ensure smooth integration. The key is to leverage the strengths of both existing systems and the new SSE solution to create a layered security architecture that provides comprehensive protection.
For example, an institution might integrate SSE with its existing identity provider (IdP) to enable seamless single sign-on (SSO) and centralized user authentication.
Challenges and Limitations of SSE Adoption in Higher Education
While SSE offers significant benefits, several challenges exist. Budget constraints are a major factor, as implementing and maintaining an SSE solution requires investment in both software and expertise. Another challenge is the complexity of integrating SSE with legacy systems, which may require significant effort and time. Finally, ensuring adequate training for staff and faculty is essential to maximize the effectiveness of the SSE solution.
Proper training helps users understand the new security policies and procedures, which is crucial for overall success. Without sufficient training, the benefits of SSE might be undermined.
Cost-Effectiveness of SSE vs. Traditional Security Solutions
| Feature | SSE | Traditional Security Solutions | Notes |
|---|---|---|---|
| Initial Investment | Potentially higher upfront cost | Lower upfront cost, but higher ongoing costs | Depends on the scale and complexity of the deployment. |
| Ongoing Costs | Subscription-based, potentially lower long-term costs | Higher ongoing costs for maintenance, updates, and staff training | SSE often includes automatic updates and centralized management. |
| Scalability | Highly scalable to accommodate growth | Scaling can be complex and expensive | SSE is designed to handle increasing user numbers and data volumes efficiently. |
| Management Complexity | Centralized management, simplified administration | Decentralized management, requiring more staff and resources | SSE reduces the need for managing multiple disparate security tools. |
Securing Specific Higher Education Assets with SSE
SSE, or Security Service Edge, offers a comprehensive approach to securing higher education institutions’ diverse digital assets. By consolidating various security functions into a single platform, SSE simplifies management and strengthens protection against evolving threats targeting sensitive university data and systems. This approach is particularly crucial given the increasing reliance on cloud services and remote access in modern higher education.
Securing University Learning Management Systems (LMS) with SSE, Enhancing higher education security the role of security service edge axis security
Learning Management Systems (LMS) are central to the educational experience, housing sensitive student data, course materials, and grades. SSE protects LMS platforms by applying a range of security measures. For example, SSE can provide secure access control, ensuring only authorized users can access the system. It can also implement robust data loss prevention (DLP) policies, preventing sensitive information from leaving the LMS environment unauthorized.
Enhancing higher education security requires a robust approach, especially with the increasing reliance on cloud services. A key component is implementing a strong Security Service Edge (SSE) architecture. Understanding cloud security posture management is crucial here, and a great resource to check out is this article on bitglass and the rise of cloud security posture management , which helps illustrate the importance of proactive cloud security.
Ultimately, a comprehensive SSE strategy, informed by best practices in cloud security, is vital for protecting our educational institutions.
Furthermore, SSE’s capabilities in threat prevention and detection actively monitor for malicious activity, such as malware or unauthorized attempts to breach the system, alerting administrators to potential threats in real-time. This proactive approach minimizes disruption and protects the integrity of the LMS and its data.
Securing Research Data and Intellectual Property with SSE
Universities are hubs of research and innovation, generating valuable intellectual property and sensitive research data. SSE plays a critical role in protecting these assets. By integrating with existing data storage and collaboration platforms, SSE enforces access control policies, ensuring that only authorized researchers can access specific data sets. Data encryption, both in transit and at rest, further protects sensitive information from unauthorized access.
SSE’s advanced threat detection capabilities also monitor for data breaches and insider threats, providing early warnings and enabling rapid responses to potential security incidents. This protection is essential for maintaining the confidentiality, integrity, and availability of research data and intellectual property.
Enhancing the Security of Administrative Systems and Financial Data with SSE
Administrative and financial systems within universities manage sensitive student and employee information, as well as substantial financial resources. SSE strengthens the security posture of these systems through various mechanisms. For instance, SSE can implement multi-factor authentication (MFA) to enhance access control and prevent unauthorized login attempts. It can also enforce robust security policies, ensuring compliance with relevant regulations such as FERPA and HIPAA.
Furthermore, SSE’s integrated security functions provide comprehensive protection against malware, phishing attacks, and other cyber threats that could compromise sensitive data and disrupt operations. The centralized management capabilities of SSE streamline security administration, reducing complexity and improving overall efficiency.
Implementing SSE for Remote Access to Campus Resources
Implementing SSE for secure remote access requires a phased approach:
- Assessment and Planning: Conduct a thorough assessment of existing infrastructure and identify critical resources requiring remote access. Define clear security policies and access control rules.
- SSE Deployment: Deploy the SSE platform, integrating it with existing network infrastructure and security tools. Configure the necessary security policies and rules, including authentication, authorization, and data encryption.
- User Onboarding: Provide users with the necessary training and tools to access campus resources securely through the SSE platform. This includes setting up secure credentials and familiarizing users with the new access procedures.
- Monitoring and Management: Continuously monitor the SSE platform for security events and anomalies. Regularly review and update security policies and configurations to adapt to evolving threats and user needs. Implement a robust incident response plan to handle any security breaches effectively.
Future Trends and Considerations
The higher education landscape is rapidly evolving, driven by technological advancements and shifting threat vectors. Understanding these changes and their impact on security is crucial for universities to maintain a robust and adaptable defense. The integration of emerging technologies, alongside the refinement of existing security architectures like SSE, will be pivotal in shaping the future of higher education cybersecurity.The convergence of artificial intelligence (AI), the Internet of Things (IoT), and increasingly sophisticated cyberattacks presents both opportunities and challenges.
AI can enhance threat detection and response capabilities, automating tasks like anomaly detection and incident triage. However, AI-powered attacks are also becoming more prevalent, requiring sophisticated countermeasures. Similarly, the proliferation of IoT devices on campus, while offering convenience and efficiency, expands the attack surface, creating new vulnerabilities that need careful management. The role of SSE in this dynamic environment is to provide a unified, adaptable security layer that can address these evolving threats.
The Evolving Role of SSE in a Zero Trust Model
Zero trust security, a model that assumes no implicit trust, is gaining traction in higher education. This approach requires continuous verification of every user and device attempting to access university resources, regardless of location. SSE plays a critical role in implementing zero trust by providing secure access to applications and data, regardless of where users are located – on campus, remotely, or using personal devices.
By enforcing granular access control policies and employing technologies like micro-segmentation and data loss prevention, SSE helps universities enforce the zero-trust principle, ensuring only authorized users and devices can access sensitive information. This approach significantly reduces the impact of breaches, as even if one system is compromised, the attacker’s lateral movement is significantly restricted. For example, a compromised student laptop would not automatically grant access to the university’s research database due to the enforced access controls within the SSE framework.
Future Threats and SSE Adaptation
Future threats will likely be more targeted, sophisticated, and persistent. State-sponsored actors, organized crime groups, and even individual malicious actors are becoming increasingly adept at exploiting vulnerabilities. We can expect to see more advanced phishing attacks, leveraging AI-generated content and social engineering techniques to bypass traditional security measures. Ransomware attacks targeting critical university systems, such as student records or research data, will also likely continue to increase.
SSE can adapt to these threats by integrating advanced threat intelligence feeds, leveraging machine learning for anomaly detection, and implementing robust multi-factor authentication (MFA) to prevent unauthorized access. Continuous monitoring and proactive threat hunting will also be crucial. Furthermore, SSE can incorporate automated incident response capabilities, enabling quicker containment and mitigation of security incidents.
SSE Protection Against a Sophisticated Phishing Attack
Imagine a sophisticated phishing campaign targeting faculty members. The attackers craft highly realistic emails mimicking legitimate university communications, complete with embedded malicious links or attachments. Traditional email security might miss these sophisticated attacks. However, with SSE, the malicious link would be intercepted before it reaches the faculty member’s device. The SSE gateway would analyze the URL, identify it as malicious based on threat intelligence, and block access.
Even if the faculty member were to bypass the initial block and attempt to access the link from a different device, SSE’s consistent policy enforcement across all access points would prevent access to the malicious website. Furthermore, the SSE platform could automatically quarantine the email, preventing further dissemination within the university network. This multi-layered approach, combined with user education and awareness training, significantly reduces the risk of successful phishing attacks.
Summary
In conclusion, enhancing higher education security requires a modern, adaptable approach. Security Service Edge (SSE) offers a powerful solution, providing comprehensive protection across various attack vectors. By implementing SSE and embracing a zero-trust model, institutions can significantly reduce their risk profile, protect sensitive data, and ensure the ongoing safety and security of their digital environment. The future of higher education security hinges on embracing innovative technologies like SSE, and proactive strategies are essential for navigating the ever-changing threat landscape.
FAQ Compilation
What are the biggest risks to higher education institutions today?
Major risks include ransomware attacks, phishing campaigns targeting faculty and students, data breaches compromising sensitive personal information, and insider threats.
How much does SSE cost compared to traditional solutions?
The cost varies depending on the size of the institution and specific needs. However, SSE can often be more cost-effective in the long run by reducing the need for extensive on-premise infrastructure and specialized personnel.
Is SSE difficult to integrate with existing systems?
Integration can vary, but many SSE solutions are designed for seamless integration with existing infrastructure. Careful planning and collaboration with vendors are key to a smooth transition.
How does SSE protect against sophisticated phishing attacks?
SSE’s SWG component can filter malicious links and attachments before they reach users, while its CASB component monitors cloud applications for suspicious activity, significantly reducing the success rate of phishing attempts.