Exploring the Essence of Confidential Computing
Exploring the essence of confidential computing, we delve into a fascinating world where data security reaches unprecedented levels. Imagine a future where sensitive information, from medical records to financial transactions, is processed and analyzed without ever leaving its encrypted sanctuary. This is the promise of confidential computing, a revolutionary approach that’s transforming how we handle our most private data.
We’ll uncover the core technologies driving this transformation, explore its diverse applications, and examine the exciting possibilities and potential challenges that lie ahead.
This journey will take us through the fundamental principles of confidential computing, examining technologies like trusted execution environments and homomorphic encryption. We’ll see how it differs from traditional security methods and explore its practical applications across various industries, including healthcare, finance, and cloud computing. We’ll also grapple with the technical complexities of implementation, security considerations, and the ethical implications of this powerful technology.
Defining Confidential Computing
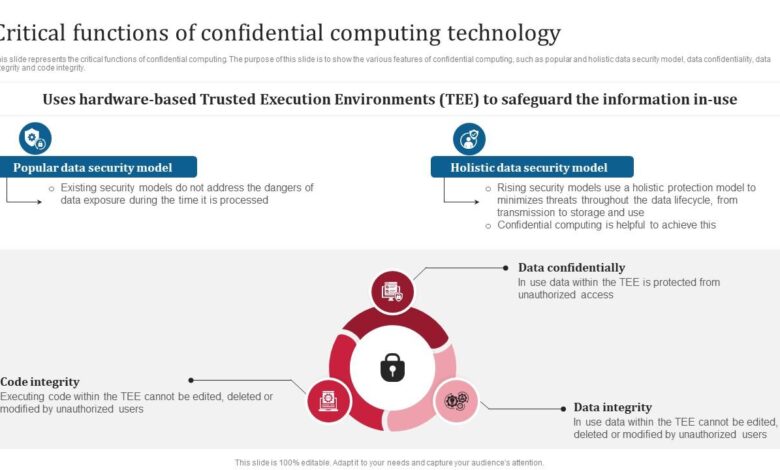
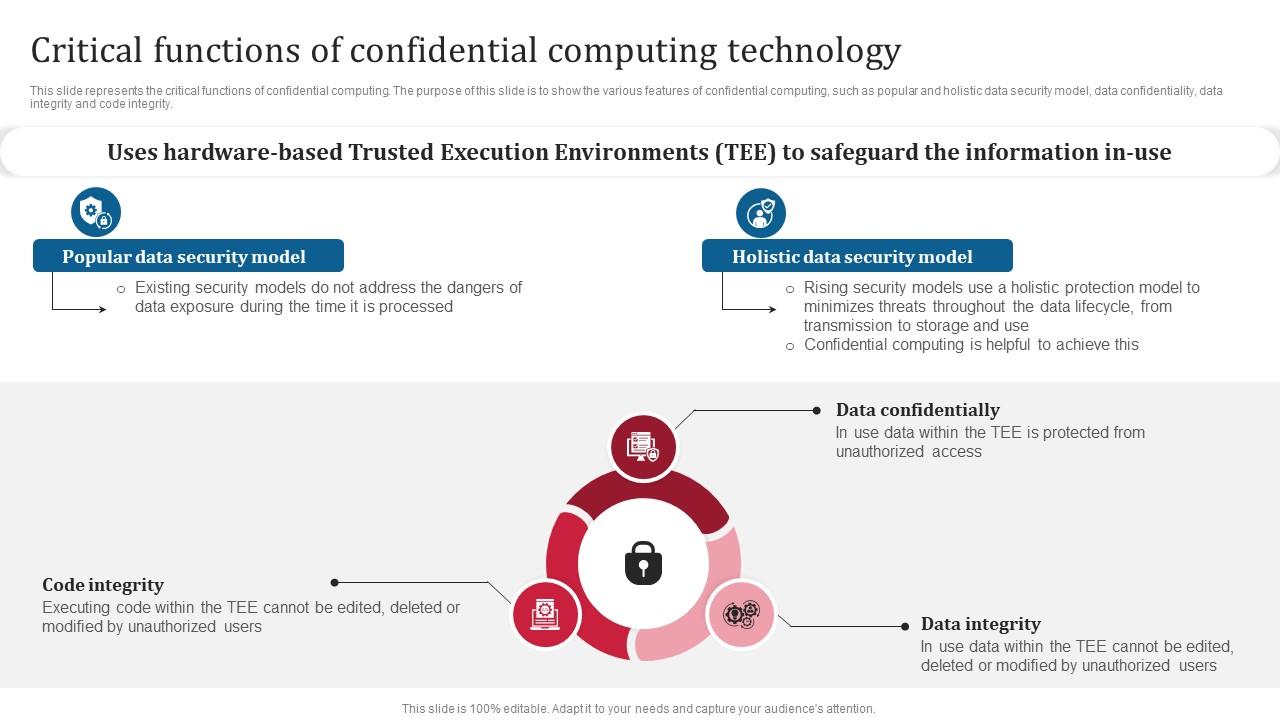
Confidential computing is a revolutionary approach to data security that protects sensitive information even from powerful attackers, including cloud providers and malicious insiders. It ensures data confidentiality throughout its lifecycle, offering a significant leap beyond traditional security methods. This is achieved by creating isolated, trusted execution environments where data remains encrypted and computations are performed securely, without ever exposing the data in its clear text form.Confidential computing relies on several core principles.
First, it emphasizes the importance of
- data isolation*, keeping sensitive data separate from the underlying hardware and software. Second, it focuses on
- secure processing*, ensuring that computations are performed within a trusted environment where only authorized parties can access the results. Third, it prioritizes
- integrity*, guaranteeing that the data and computations haven’t been tampered with. These principles combine to create a powerful shield against data breaches and unauthorized access.
Technologies Enabling Confidential Computing
Several technologies underpin the capabilities of confidential computing. Trusted Execution Environments (TEEs) are a crucial component. TEEs are isolated regions of memory within a processor that protect code and data from access by the operating system, hypervisor, or other software. Intel SGX, AMD SEV, and ARM TrustZone are examples of widely used TEE technologies. These technologies create a secure enclave where sensitive computations can occur.
Another critical technology is homomorphic encryption, which allows computations to be performed on encrypted data without decryption. This means that even the service provider cannot see the underlying data, only the encrypted results. While still relatively immature compared to TEEs, homomorphic encryption holds significant promise for expanding the capabilities of confidential computing. Finally, secure multi-party computation (MPC) allows multiple parties to jointly compute a function over their private inputs without revealing anything beyond the output.
Confidential Computing vs. Traditional Security Measures
Traditional security measures, such as encryption at rest and in transit, focus on protecting data when it’s stored or being transmitted. However, they offer limited protection when data is being processed. Confidential computing goes a step further by protecting dataduring processing*, offering a more comprehensive approach to security. For example, encrypting data at rest prevents unauthorized access to a database, but once the data is decrypted for processing, it becomes vulnerable.
Confidential computing avoids this vulnerability by keeping the data encrypted even during computation. This fundamental difference significantly enhances security in environments where data is actively used and manipulated.
Real-World Applications of Confidential Computing
Confidential computing offers significant advantages in numerous real-world scenarios. Consider sensitive medical data analysis: Hospitals can use confidential computing to analyze patient records without revealing the identities or specific details of individual patients to the analytics provider. Similarly, financial institutions can leverage confidential computing to perform fraud detection on transaction data without exposing sensitive financial information to third-party service providers.
In the realm of supply chain management, confidential computing can help secure sensitive inventory and logistics data shared between multiple partners. Another promising application is secure remote computation, allowing users to perform complex computations on sensitive data without compromising its confidentiality, even on untrusted devices or cloud infrastructure. The possibilities are vast and continue to expand as the technology matures.
Exploring Use Cases
Confidential computing, with its ability to protect data even from the cloud provider, opens up exciting possibilities across various sectors. Let’s delve into some compelling real-world applications where this technology can significantly enhance security and privacy.
Secure Data Analytics System Design
Imagine a system for analyzing sensitive customer data, such as purchasing habits and demographics, to improve marketing strategies. Traditional approaches store this data in a centralized database, vulnerable to breaches. A confidential computing-based system would encrypt the data at rest and in use. The analytics would be performed within secure enclaves, isolated environments where only authorized code can access the decrypted data.
This ensures that even the cloud provider or any malicious actor cannot access the sensitive information, maintaining complete data confidentiality while still allowing for valuable insights. The system could use technologies like Intel SGX or AMD SEV to create these secure enclaves, and the results of the analysis could be securely returned to authorized personnel. This approach minimizes the risk of data breaches and complies with stringent privacy regulations.
Confidential Computing in Healthcare
The healthcare industry deals with highly sensitive patient data, subject to strict regulations like HIPAA. Confidential computing offers a robust solution for protecting this data. For example, researchers could analyze medical records within secure enclaves to identify trends and develop new treatments without ever directly accessing the unencrypted patient data. Similarly, hospitals could securely share patient information with other healthcare providers for consultations or collaborative research, ensuring patient privacy throughout the process.
The use of federated learning, where models are trained across multiple datasets without sharing the raw data, is also significantly enhanced by confidential computing, allowing for better medical insights while protecting patient confidentiality. This approach allows for collaborative research and improved healthcare outcomes while strictly adhering to privacy regulations.
Confidential Computing in Financial Transactions
Financial transactions require the highest levels of security. Confidential computing can significantly enhance the security of online banking and payment systems. Sensitive data, such as account numbers and transaction details, can be processed within secure enclaves, protecting them from unauthorized access even if the system is compromised. This technology could be used to improve the security of point-of-sale systems, reducing the risk of credit card fraud.
Furthermore, confidential computing can enable more secure and private blockchain implementations, safeguarding sensitive financial data on the distributed ledger. The added layer of security provided by confidential computing can significantly increase consumer trust and reduce the risk of financial fraud.
Challenges and Opportunities in Cloud Environments
While confidential computing offers significant advantages, challenges remain, particularly in cloud environments. The performance overhead associated with creating and managing secure enclaves can be substantial, impacting the efficiency of applications. Furthermore, integrating confidential computing technologies with existing cloud infrastructure requires significant effort and expertise. However, the opportunities are substantial. As the technology matures and becomes more efficient, its adoption in cloud environments will accelerate, leading to more secure and private cloud services.
The development of standardized APIs and tools will also simplify integration and reduce the complexity of deploying confidential computing solutions in the cloud. The growing demand for data privacy and security will drive further innovation and adoption, making confidential computing a key technology for the future of cloud computing.
Technical Aspects of Implementation
Confidential computing, while offering significant security advantages, presents unique challenges in implementation. Successfully integrating it requires a careful understanding of the underlying technologies and a methodical approach to deployment. This section delves into the practical aspects of setting up and using confidential computing environments.
Setting Up a Confidential Computing Environment
Establishing a confidential computing environment involves several key steps. First, you need to choose a suitable hardware platform that supports trusted execution environments (TEEs), such as Intel SGX, AMD SEV, or ARM TrustZone. Next, you’ll need to select a suitable software framework, such as Intel SGX SDK, or a higher-level abstraction like Open Enclave. This framework provides the necessary APIs and tools to interact with the TEE.
Finally, you need to configure the environment, including setting up secure communication channels and managing keys. This often involves integrating with existing infrastructure, such as virtual machines or containers, and configuring network security policies. The complexity of this setup depends significantly on the chosen technology and the specific security requirements of the application.
Integrating Confidential Computing into an Existing Application
Integrating confidential computing into an existing application requires a phased approach. The first step involves identifying the sensitive data and operations that need to be protected within the application. This is followed by refactoring the application code to encapsulate these sensitive components within an enclave. This often involves significant code changes, requiring careful planning and testing. Next, you’ll need to adapt the application’s communication protocols to securely transfer data to and from the enclave.
Exploring the essence of confidential computing means understanding how to protect sensitive data, no matter where it resides. This is especially crucial in the cloud, which is why the rise of tools like cloud security posture management is so important. Check out this great article on bitglass and the rise of cloud security posture management to see how it all fits together.
Ultimately, understanding these security measures is key to truly grasping the implications of confidential computing.
This typically involves using secure channels and authenticated encryption. Finally, thorough testing is crucial to ensure that the integration is secure and doesn’t introduce performance bottlenecks or other issues. A gradual rollout, starting with a small subset of users, can help mitigate risks.
Performance Overhead Comparison of Confidential Computing Techniques
Different confidential computing techniques offer varying levels of security and performance. The choice depends on the specific application needs and security requirements. The table below provides a comparison of the performance overhead of several techniques. Note that these figures are estimates and can vary significantly depending on the hardware, software, and application workload.
| Technique | CPU Overhead (%) | Memory Overhead (%) | Latency Overhead (ms) |
|---|---|---|---|
| Intel SGX | 5-20 | 1-5 | 1-10 |
| AMD SEV | 1-5 | <1 | <1 |
| ARM TrustZone | 2-10 | <1 | 1-5 |
Implementing a Simple Confidential Computing Protocol using Intel SGX
A simple example using Intel SGX could involve a secure computation of a shared secret. Two parties, Alice and Bob, each have a secret value (a and b respectively). They want to compute a + b without revealing their individual secrets. Using Intel SGX, they could each create an enclave that contains their secret and a function to perform the addition.
The enclaves would then exchange intermediate values through a secure channel, ensuring that neither party reveals their individual secret. The final result, a + b, would be returned securely. This is a simplified example; real-world applications would require more sophisticated techniques to handle more complex computations and security considerations. The specific implementation would involve using the Intel SGX SDK to create and manage the enclaves, and implementing secure communication protocols to exchange data between them.
The code would involve creating remote attestation mechanisms to verify the integrity of the enclaves before computation.
Security and Privacy Considerations
Confidential computing, while promising enhanced data protection, isn’t a silver bullet. It introduces its own set of security and privacy challenges that need careful consideration. Understanding these vulnerabilities and implementing robust mitigation strategies is crucial for realizing the full potential of this technology while minimizing risks.
The inherent complexity of confidential computing systems creates potential attack vectors. While the data itself might be protected within a trusted execution environment (TEE), the software running within the TEE, the communication channels to and from the TEE, and the surrounding infrastructure all present points of vulnerability. A compromised hypervisor, for instance, could potentially bypass the security mechanisms of the TEE, granting unauthorized access to confidential data.
Similarly, side-channel attacks could leak information about the computations performed within the TEE, compromising the confidentiality of the processed data. Furthermore, poorly designed or implemented confidential computing applications can introduce vulnerabilities that attackers could exploit.
Potential Vulnerabilities and Threats
Several vulnerabilities and threats are associated with confidential computing. These include, but are not limited to, software vulnerabilities within the TEE, side-channel attacks exploiting timing or power consumption differences, attacks targeting the hypervisor or other parts of the system infrastructure, and supply chain attacks compromising the hardware or software components used in confidential computing systems. The reliance on trusted hardware also raises concerns about potential backdoors or weaknesses in the hardware itself.
For example, a flaw in the design or manufacturing process of a trusted platform module (TPM) could compromise the security of the entire system.
Mitigation Strategies for Confidential Data Integrity
Mitigating risks and ensuring data integrity requires a multi-layered approach. This includes rigorous software development practices to minimize vulnerabilities in the code running within the TEE, the use of robust hardware security modules (HSMs) for key management, and the implementation of strong access control mechanisms to limit access to sensitive data and resources. Regular security audits and penetration testing are crucial to identify and address potential weaknesses.
Furthermore, employing techniques to defend against side-channel attacks, such as using countermeasures to mask timing variations or power consumption patterns, is essential. Finally, rigorous supply chain security practices are necessary to ensure the integrity of the hardware and software components used in confidential computing systems.
Security Implications of Different Approaches
Different confidential computing approaches, such as Intel SGX, AMD SEV, and ARM TrustZone, have varying security implications. Each technology has its own strengths and weaknesses in terms of security features, performance overhead, and attack surface. For example, Intel SGX relies on memory encryption and isolation, while AMD SEV focuses on virtual machine security. The choice of technology should be based on a thorough assessment of the specific security requirements and risk tolerance of the application.
A comparative analysis considering the level of protection offered against different attack vectors is crucial in determining the suitability of each approach for a specific use case. This analysis should also include the impact of each technology on performance and resource utilization.
Legal and Ethical Considerations
The use of confidential computing raises several legal and ethical considerations. Data protection regulations, such as GDPR, require organizations to implement appropriate technical and organizational measures to ensure the security and privacy of personal data. Confidential computing can help meet these requirements, but it also introduces new challenges regarding data access, control, and accountability. The use of confidential computing may also raise questions about the potential for misuse, such as using it to circumvent surveillance or to conceal illegal activities.
Furthermore, the development and deployment of confidential computing technologies require careful consideration of the potential impact on human rights and societal well-being. Clear guidelines and regulations are needed to ensure responsible innovation and adoption of this technology.
Exploring the essence of confidential computing is fascinating, especially when considering how it impacts application development. The security implications are huge, and building secure apps requires careful consideration, which is why understanding platforms like those discussed in this great article on domino app dev the low code and pro code future is crucial. Ultimately, secure development practices are key to ensuring that the benefits of confidential computing are fully realized.
Future Trends and Developments: Exploring The Essence Of Confidential Computing
Confidential computing is rapidly evolving, driven by increasing concerns about data privacy and security in a world increasingly reliant on cloud services and interconnected devices. The future of this field promises significant advancements, reshaping how we approach data protection and processing across various sectors. We’ll explore key trends, predictions, and a vision for next-generation systems.
The next few years will see a dramatic expansion in the adoption and capabilities of confidential computing. Research efforts are focused on improving performance, expanding functionality, and simplifying implementation, making it more accessible to a wider range of users and applications. This will lead to a significant shift in how organizations handle sensitive data, fostering greater trust and innovation.
Homomorphic Encryption Advancements
Significant breakthroughs in fully homomorphic encryption (FHE) are anticipated. Current FHE schemes are computationally expensive, limiting their practical application. However, ongoing research into improved algorithms and hardware acceleration is paving the way for more efficient and widely deployable FHE solutions. This would allow computations to be performed directly on encrypted data without decryption, a game-changer for privacy-preserving data analysis and machine learning.
For example, a financial institution could analyze aggregated, encrypted transaction data to detect fraud patterns without ever accessing the underlying sensitive financial information.
Hardware-Software Co-design for Enhanced Performance
The performance bottleneck in confidential computing often stems from the cryptographic operations involved. Future systems will leverage hardware-software co-design approaches, optimizing both the hardware acceleration of cryptographic primitives and the software architecture for efficient data flow and management within trusted execution environments (TEEs). This integrated approach will dramatically reduce latency and improve throughput, making confidential computing viable for real-time applications like autonomous vehicles or high-frequency trading.
Imagine a self-driving car leveraging confidential computing to process sensor data and make critical decisions while ensuring the privacy of the location and sensor readings.
Decentralized Confidential Computing Architectures, Exploring the essence of confidential computing
The integration of confidential computing with decentralized technologies like blockchain is a promising avenue. This combination could create secure and transparent data sharing platforms, empowering individuals and organizations with greater control over their data. For instance, a healthcare system could utilize a blockchain-based platform with confidential computing to securely share patient medical records, allowing authorized researchers to access and analyze data without compromising patient privacy.
This architecture would ensure data integrity and provenance while protecting sensitive information.
AI and Confidential Computing Synergy
The convergence of AI and confidential computing will unlock significant opportunities in various fields. Confidential computing can enable the development of privacy-preserving AI models, allowing organizations to train and deploy AI algorithms on sensitive data without compromising confidentiality. Consider a financial institution training a fraud detection model on encrypted transaction data. The model can learn patterns and make predictions without ever accessing the raw, sensitive data.
This approach promotes responsible AI development while safeguarding privacy.
Conceptual Framework for a Next-Generation Confidential Computing System
A next-generation system should focus on a modular and extensible architecture. This architecture would allow for seamless integration of various cryptographic techniques, hardware accelerators, and software components. The system would support diverse TEE implementations and allow for flexible policy management to cater to different security and privacy requirements. A key component would be a robust attestation mechanism to verify the integrity and trustworthiness of the execution environment.
Furthermore, the system should incorporate automated tools for managing and monitoring the security and performance of confidential computing deployments. This framework would allow for a more adaptable and scalable solution capable of handling the increasing complexity of data protection needs.
Illustrative Examples
Let’s delve into concrete scenarios showcasing the power and practical applications of confidential computing. These examples will illustrate how this technology protects sensitive data in various contexts, moving beyond theoretical discussions.
Confidential computing offers a powerful way to safeguard data, even in untrusted environments. By leveraging hardware-based security features, it ensures data remains encrypted and protected throughout its lifecycle, from storage to processing. This is particularly critical in scenarios involving collaboration or data sharing where complete trust in all parties isn’t always possible.
Secure Data Sharing Scenario
Imagine a collaborative research project involving multiple institutions. Each institution possesses sensitive patient data which they want to analyze collectively to discover new insights without compromising patient privacy. Using confidential computing, each institution can encrypt its data before uploading it to a central, shared server. The server, equipped with trusted execution environments (TEEs), only allows computation on the encrypted data.
The research algorithms run within the TEE, decrypting the data only temporarily and within the secure enclave. The results of the analysis are then returned to the participating institutions, still encrypted, ensuring no intermediary, including the server administrator, can access the raw patient data. This architecture relies on homomorphic encryption, allowing computations on encrypted data without decryption, and secure multi-party computation (MPC) protocols to manage the interactions between the different parties involved.
The entire process ensures data confidentiality, integrity, and availability while allowing for collaborative research.
Confidential Computing System Architecture for Protecting Sensitive Data
This architecture focuses on a system designed to protect sensitive financial data. The system incorporates several layers of security to protect data both in transit and at rest. Client applications encrypt sensitive data using a strong encryption algorithm (e.g., AES-256) before transmission. Data is transmitted over a secure channel (e.g., HTTPS) to a server equipped with a TEE.
The server uses a key management system (KMS) to manage the encryption keys, ensuring only authorized parties can access the data. Within the TEE, the data is processed securely, maintaining its encrypted state throughout the computation. The processed data is then re-encrypted before being stored in a secure database, which is itself encrypted at rest using strong encryption.
Access to the database is strictly controlled through access control lists and regular security audits. The system further incorporates intrusion detection and prevention systems to monitor for and respond to any potential security threats. Regular security assessments and penetration testing are performed to identify and address vulnerabilities. This layered approach ensures that sensitive financial data remains protected at every stage, from input to storage and processing, minimizing the risk of data breaches and unauthorized access.
Outcome Summary
Confidential computing isn’t just about adding another layer of security; it’s about fundamentally changing how we approach data privacy and security. By enabling computation on encrypted data, it unlocks possibilities that were previously unimaginable. While challenges remain – particularly concerning performance overhead and potential vulnerabilities – the potential benefits are too significant to ignore. As the technology matures and adoption increases, we can expect to see a profound shift in how sensitive data is handled across various sectors, leading to a more secure and privacy-respecting digital world.
The future of confidential computing is bright, promising innovative solutions to the ever-evolving landscape of data protection.
Questions and Answers
What are the main limitations of confidential computing?
While powerful, confidential computing isn’t a silver bullet. Performance overhead can be significant depending on the chosen techniques, and there’s always the risk of vulnerabilities in the underlying hardware or software.
How does confidential computing compare to other security measures like encryption at rest and in transit?
Traditional encryption protects data while it’s stored or transmitted, but confidential computing goes further by protecting it
-during processing*. This allows computations to be performed on sensitive data without ever decrypting it.
Is confidential computing suitable for all types of data and applications?
No, the suitability depends on the sensitivity of the data and the computational requirements of the application. It’s particularly well-suited for applications requiring complex computations on sensitive data, but might be overkill for simpler tasks.
What are the regulatory compliance implications of using confidential computing?
The use of confidential computing can help organizations meet various data privacy regulations (like GDPR, HIPAA) by providing strong data protection mechanisms, but specific compliance requirements need careful consideration.