GDPR Compliance Checklist 9 Step Guide
Gdpr compliance checklist 9 step guide – GDPR Compliance Checklist: 9 Step Guide – navigating the complexities of GDPR can feel like wandering through a maze. But fear not! This guide breaks down the process into nine manageable steps, helping you ensure your business is compliant and avoids hefty fines. We’ll cover everything from data mapping and subject rights to security measures and breach response, making GDPR compliance less daunting and more achievable.
This isn’t just another dry legal document; it’s a practical roadmap designed to empower you. We’ll use clear language, real-world examples, and actionable steps to help you understand and implement the necessary changes. Get ready to confidently navigate the world of data protection!
Introduction to GDPR Compliance
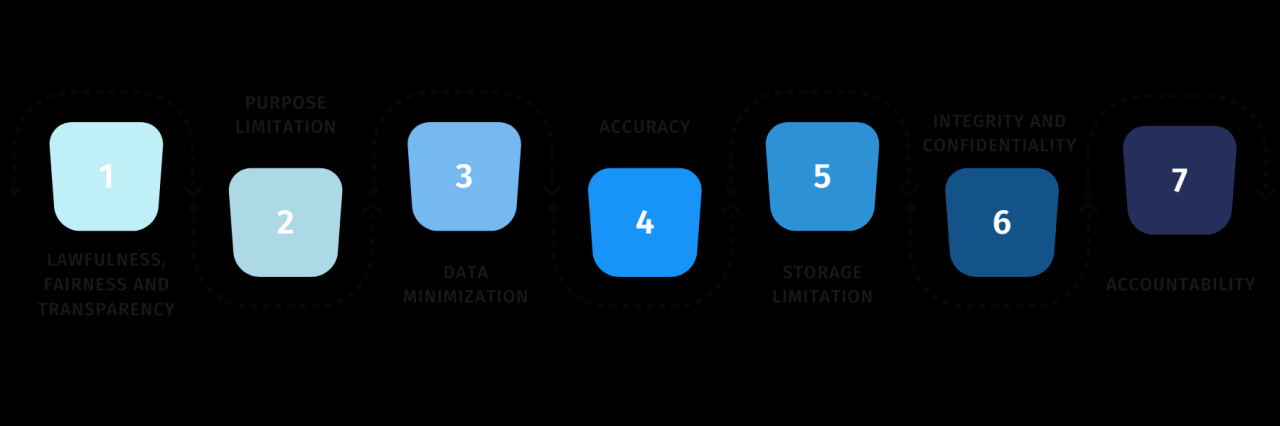
The General Data Protection Regulation (GDPR) is a landmark piece of legislation in the European Union that aims to protect the personal data of individuals within the EU. It establishes a comprehensive framework for the processing of personal data, granting individuals greater control over their information and holding organizations accountable for its proper handling. At its core, GDPR focuses on principles of lawfulness, fairness, and transparency; data minimization; accuracy; storage limitation; integrity and confidentiality; and accountability.Understanding and complying with GDPR is crucial for any business that processes the personal data of EU residents, regardless of the business’s location.
Failure to comply can result in significant financial penalties and reputational damage, impacting customer trust and potentially hindering business operations. The regulation applies to a broad range of organizations, from small businesses to multinational corporations, impacting how they collect, store, use, and share personal data.
GDPR Non-Compliance and its Consequences
Non-compliance with GDPR can lead to severe repercussions. For example, a company might face substantial fines, potentially reaching up to €20 million or 4% of annual global turnover – whichever is higher. Beyond financial penalties, data breaches resulting from non-compliance can severely damage a company’s reputation, leading to loss of customer trust and potential legal action from affected individuals.
A well-publicized example is the British Airways data breach in 2018, which resulted in a significant fine for failing to adequately protect customer data. The incident highlighted the importance of robust security measures and compliance with GDPR’s data protection requirements. This case serves as a stark reminder that the cost of non-compliance far outweighs the investment in implementing appropriate safeguards.
Data Mapping and Inventory
Creating a comprehensive data map is the foundational step in achieving GDPR compliance. It provides a clear picture of what personal data your organization holds, where it’s stored, and how it’s used. This allows you to identify potential risks and implement appropriate safeguards. Without a thorough data map, you’re essentially navigating in the dark, making it difficult to comply with data subject requests and respond effectively to data breaches.A robust data mapping methodology involves a systematic review of all data processing activities within your organization.
This goes beyond simply listing databases; it requires a deep dive into the various systems, applications, and processes that handle personal data.
Data Mapping Methodology
The process of creating a comprehensive data map involves several key stages. First, identify all systems and applications that process personal data. This includes databases, spreadsheets, CRM systems, email servers, and any other technology that stores or processes personal information. Second, for each system, identify the specific types of personal data being processed. This might include names, addresses, email addresses, phone numbers, financial information, or other sensitive data.
Third, determine the source of each data category. Where did this information originate? Was it collected directly from individuals, obtained from third parties, or generated internally? Finally, pinpoint the storage location of the data. Is it stored on-premises, in the cloud, or both?
Documenting these aspects thoroughly is crucial for a complete and accurate data map.
Data Categories, Sources, and Storage Locations
The following table illustrates a sample data map. Remember, your own data map will need to be tailored to your specific organization and the types of data you process.
| Data Category | Source | Storage Location | Data Retention Policy |
|---|---|---|---|
| Customer Name | Website registration forms, sales orders | CRM Database (Cloud-based) | 7 years after last interaction |
| Customer Email Address | Website registration forms, marketing opt-ins | Email Marketing Platform (Cloud-based), CRM Database (Cloud-based) | Until customer unsubscribes |
| Customer Address | Website registration forms, shipping information | CRM Database (Cloud-based), Order Management System (On-premises) | 7 years after last order |
| Employee Contact Information | HR onboarding process | HR Database (On-premises) | Until employment ends + 2 years |
Identifying Personal Data
Identifying personal data processed by your organization requires a thorough and meticulous approach. This involves reviewing all data processing activities, including those performed manually and automatically. Consider all possible sources of personal data, such as customer interactions, employee records, marketing campaigns, and third-party data integrations. Remember that personal data encompasses a broad range of information, including identifiers like names and addresses, but also less obvious data like IP addresses, online identifiers, and location data.
A systematic review of all systems and processes, coupled with consultation with relevant departments, is essential to ensure a comprehensive identification of all personal data. It’s also vital to consider the context in which data is processed. Data that may not be personally identifiable in isolation could become so when combined with other information.
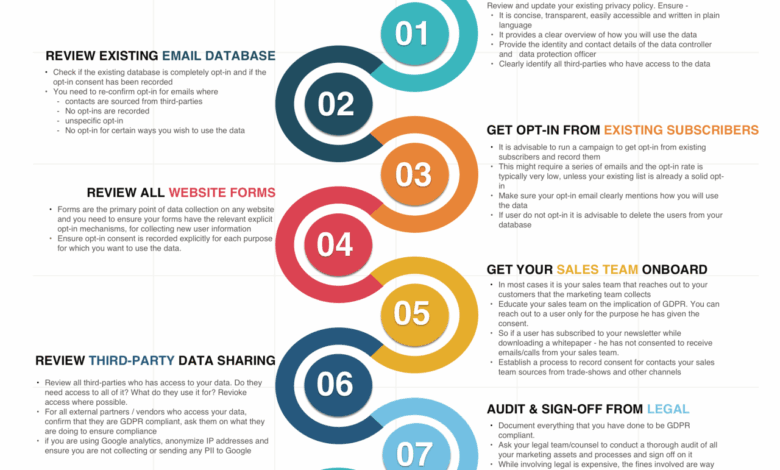
So you’re tackling a GDPR compliance checklist – a 9-step guide can be a lifesaver! Building apps that respect user data is crucial, and that’s where development choices come in. For instance, consider the powerful options explored in this article on domino app dev the low code and pro code future , which can significantly impact how easily you integrate robust data protection measures.
Getting back to that GDPR checklist, remember to thoroughly document your data handling processes – it’s a key step for compliance.
Data Subject Rights

Understanding and respecting data subject rights is fundamental to GDPR compliance. These rights empower individuals to control their personal data and ensure its responsible handling. Failing to properly address data subject requests can lead to significant fines and reputational damage.
The GDPR grants several key rights to individuals concerning their personal data. These rights aren’t isolated but often intertwine, requiring a holistic approach to handling requests.
Right of Access
Individuals have the right to obtain confirmation from a data controller whether or not personal data concerning them is being processed, and, where that is the case, access to the personal data and certain supplementary information. This includes the purposes of processing, the categories of data processed, the recipients of the data, and the retention period. For example, if a customer requests access to their order history from an online retailer, the retailer must provide a copy of this data within one month.
This should include details such as order dates, items purchased, delivery addresses, and payment information. The response should be clear, concise, and easily understandable for the individual.
Right to Rectification
Data subjects have the right to have inaccurate personal data concerning them rectified without undue delay. If a customer’s address is incorrect on file, they have the right to have it updated. The process should involve verifying the accuracy of the correction request and implementing the change swiftly and securely, notifying relevant parties if necessary. The organization should maintain a record of all rectification requests and actions taken.
Right to Erasure (“Right to be Forgotten”)
Under certain circumstances, individuals can request the erasure of their personal data. This right isn’t absolute and doesn’t apply if the data is necessary for legal compliance or other legitimate purposes. For example, a user might request the deletion of their account from a social media platform. The platform should then delete the user’s profile and associated data, unless legally obligated to retain it (e.g., for legal proceedings).
Right to Restriction of Processing
Individuals can request the restriction of processing their personal data under specific conditions, such as when the accuracy of the data is contested or the processing is unlawful. For instance, if a customer disputes the accuracy of their billing information, the company might restrict processing of that data until the accuracy is verified. This means limiting further processing of the disputed data until the issue is resolved.
Right to Data Portability
Data subjects have the right to receive their personal data in a structured, commonly used, and machine-readable format and have the right to transmit that data to another controller. This is particularly relevant for online services. Imagine a user wanting to switch email providers; they should be able to easily download their emails and contacts in a format that can be imported into the new provider’s system.
Right to Object
Individuals have the right to object to the processing of their personal data, particularly in cases of direct marketing. For example, a customer can object to receiving marketing emails from a company. The company must cease processing the data for that purpose unless they demonstrate compelling legitimate grounds for the processing which override the interests, rights and freedoms of the data subject, or for the establishment, exercise or defence of legal claims.
Automated Individual Decision-Making, Including Profiling
Individuals have the right not to be subject to a decision based solely on automated processing, including profiling, which produces legal effects concerning him or her or similarly significantly affects him or her. This means that individuals have a right to human intervention in decisions that significantly impact them. For example, if a loan application is automatically rejected based solely on an algorithmic assessment, the individual has the right to challenge that decision and request a human review.
Handling Data Subject Requests Efficiently
Efficiently handling data subject requests requires a well-defined process. This includes designating a point of contact, establishing clear internal procedures, using a secure system for managing requests, and ensuring timely responses. Regular training for staff on data subject rights and procedures is crucial. Using a centralized system for tracking requests and responses is also vital for maintaining compliance.
Best Practices for Responding to Data Subject Access Requests
Responding to data subject access requests within the legally mandated timeframe (one month) is paramount. This involves promptly acknowledging receipt of the request, verifying the identity of the requester (through secure methods), locating and retrieving the relevant data, and providing the data in a clear and accessible format. If an extension is necessary (up to two months), the individual must be informed promptly and provided with a justification.
Keeping detailed records of all requests and responses is essential for demonstrating compliance.
Lawful Basis for Processing
Navigating the GDPR’s requirements for processing personal data can feel like wading through a dense legal jungle. One of the most crucial aspects is understanding and correctly identifying the lawful basis for your data processing activities. Getting this wrong can lead to hefty fines and reputational damage. This section clarifies the six lawful bases, helping you choose the right one for your specific needs.The GDPR Artikels six lawful bases for processing personal data.
Each basis represents a different justification for collecting and using someone’s information. It’s vital to choose the basis that most accurately reflects your reason for processing the data, ensuring transparency and compliance. Misrepresenting the lawful basis is a serious breach.
The Six Lawful Bases for Processing Personal Data
The six lawful bases are: Consent, Contract, Legal Obligation, Vital Interests, Public Task, and Legitimate Interests. Understanding the nuances between them is critical for compliance.
| Lawful Basis | Description | Example | Considerations |
|---|---|---|---|
| Consent | The data subject freely gives clear, informed, and unambiguous indication of their agreement to the processing of their personal data. | Subscribing to a newsletter after explicitly checking a box indicating agreement. | Must be freely given, specific, informed, and unambiguous. Easy to withdraw. |
| Contract | Processing is necessary for a contract with the data subject or to take steps at the request of the data subject before entering into a contract. | Processing customer data to fulfill an order placed online. | Clearly defined contractual obligations must exist. |
| Legal Obligation | Processing is necessary for compliance with a legal obligation to which the controller is subject. | Processing payroll data to comply with tax regulations. | Specific legal requirement must be identified. |
| Vital Interests | Processing is necessary to protect the vital interests of the data subject or another person. | Processing medical data in an emergency situation. | Must be a life-threatening situation. |
| Public Task | Processing is necessary for the performance of a task carried out in the public interest or in the exercise of official authority vested in the controller. | Processing data by a government agency for census purposes. | Clearly defined public interest or official authority must be present. |
| Legitimate Interests | Processing is necessary for the purposes of the legitimate interests pursued by the controller or by a third party, except where such interests are overridden by the interests or fundamental rights and freedoms of the data subject. | Using customer data to improve products or services. | Requires a careful balancing of interests. Must not override data subject’s rights. |
Selecting the Appropriate Lawful Basis
Choosing the correct lawful basis is crucial. For example, using “legitimate interests” for marketing emails without providing a clear and simple opt-out mechanism could be problematic. Similarly, relying on consent for processing data required by law would be incorrect. Each situation requires careful consideration of the specific facts and the relevant legal requirements. If unsure, seeking legal advice is recommended.
Navigating GDPR compliance can be tricky, and my recent 9-step guide helps break it down. A key aspect of data protection, especially with the increasing reliance on cloud services, is robust security. Understanding cloud security posture management is crucial, and check out this great article on bitglass and the rise of cloud security posture management to see how it helps.
Ultimately, strong cloud security directly supports your GDPR compliance checklist goals.
Data Security Measures
Protecting your data is paramount under GDPR. This step focuses on identifying potential threats and implementing robust security measures to prevent data breaches and maintain compliance. Failing to adequately secure personal data can lead to significant fines and reputational damage. This section will guide you through identifying vulnerabilities and implementing effective safeguards.Data security isn’t a one-time task; it’s an ongoing process requiring continuous monitoring and improvement.
Regular assessments and audits are crucial to ensure the effectiveness of your security measures and to adapt to evolving threats.
Common Data Security Threats and Vulnerabilities
Understanding the types of threats your organization faces is the first step towards effective protection. Common threats include unauthorized access, accidental data loss, malware attacks, phishing scams, and insider threats. Vulnerabilities often arise from weak passwords, outdated software, inadequate access controls, and lack of employee training. A comprehensive risk assessment should identify specific threats and vulnerabilities relevant to your organization’s context and data processing activities.
Consider the potential impact of each threat, both financially and reputationally.
Technical and Organizational Security Measures
Implementing a combination of technical and organizational measures is vital for robust data security. These measures should be proportionate to the risk involved and the sensitivity of the data being processed.
- Data Encryption: Encrypting data both in transit and at rest protects it from unauthorized access, even if a breach occurs. This involves using strong encryption algorithms and key management practices.
- Access Control: Implementing strong access controls, including role-based access control (RBAC), ensures that only authorized personnel can access specific data. This minimizes the risk of unauthorized disclosure or modification.
- Regular Software Updates: Regularly updating software and systems patches vulnerabilities that malicious actors could exploit. This includes operating systems, applications, and security software.
- Firewall and Intrusion Detection Systems: Firewalls act as barriers, preventing unauthorized access to your network. Intrusion detection systems monitor network traffic for suspicious activity, alerting you to potential threats.
- Security Awareness Training: Educating employees about data security best practices, including phishing awareness and password management, reduces the risk of human error leading to breaches. Regular training should be provided and reinforced.
- Data Loss Prevention (DLP) Tools: DLP tools monitor data movement and prevent sensitive data from leaving the organization’s control without authorization. This is crucial for protecting data both inside and outside the network.
- Regular Backups and Disaster Recovery Plan: Having regular backups and a robust disaster recovery plan ensures business continuity and data availability in case of a data loss event. This plan should detail procedures for restoring data and systems.
Security Assessments and Audits
Regular security assessments and audits are essential to identify weaknesses and ensure the effectiveness of your security measures. These assessments should cover all aspects of your data security infrastructure and processes. Audits can be internal or external, conducted by qualified professionals.
- Penetration Testing: Simulates real-world attacks to identify vulnerabilities in your systems and processes. This helps proactively identify weaknesses before malicious actors can exploit them.
- Vulnerability Scanning: Automatically identifies known vulnerabilities in your systems and software. This provides a comprehensive overview of potential security weaknesses.
- Security Audits: Independent assessments of your security controls and processes to ensure compliance with relevant regulations and best practices. This provides an objective evaluation of your security posture.
- Incident Response Plan: A well-defined incident response plan Artikels procedures to follow in the event of a data breach or security incident. This ensures a coordinated and effective response to minimize damage and ensure compliance with notification requirements.
Data Breaches and Notifications
Navigating data breaches is a critical aspect of GDPR compliance. A robust response plan is essential not only to minimize damage but also to fulfill legal obligations and maintain public trust. Understanding the process, from internal reporting to external notifications, is crucial for any organization handling personal data.A data breach, under GDPR, is defined as a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored or otherwise processed.
The severity of a breach can range from minor incidents to significant compromises of sensitive information. Regardless of scale, a well-defined response plan is vital.
Internal Reporting Procedures
Effective internal reporting is the cornerstone of a successful breach response. This involves establishing clear channels for reporting suspected breaches, designating responsible personnel, and implementing a standardized procedure for investigation and assessment. A dedicated team, perhaps including IT security specialists, legal counsel, and data protection officers, should be readily available to handle such events. The reporting process should be documented, easily accessible, and regularly reviewed to ensure its effectiveness.
The goal is to identify and contain the breach as quickly as possible to limit further damage. For example, a company might use a dedicated online form or a secure email address for breach reporting, with automated alerts sent to the relevant team members.
Notification Requirements to Supervisory Authorities
GDPR mandates notification of the supervisory authority (the data protection authority in the affected EU member state) within 72 hours of becoming aware of a data breach, unless the breach is unlikely to result in a risk to the rights and freedoms of individuals. This notification must include details of the breach, the measures taken to mitigate the impact, and the estimated number of individuals affected.
Failure to comply with these notification requirements can result in significant fines. For instance, a company experiencing a phishing attack resulting in the unauthorized access of customer email addresses would be obligated to report this to the relevant data protection authority within the 72-hour timeframe.
Notification Requirements to Data Subjects
Notification to affected individuals is also required unless certain conditions are met (e.g., the controller has implemented appropriate technical and organizational protection measures, making the risk to the rights and freedoms of data subjects unlikely). This notification should inform individuals of the nature of the breach, the types of personal data affected, and the measures taken to address the breach.
The notification should be clear, concise, and easy to understand. For example, a company might send a personalized email to affected customers, explaining the breach, the data involved, and steps taken to protect their information, along with advice on how to safeguard themselves.
Example Breach Response Plan
An effective breach response plan should include the following stages:
- Incident Identification and Reporting: Clear procedures for reporting suspected breaches.
- Containment and Investigation: Steps to isolate the breach and investigate its cause and extent.
- Impact Assessment: Determining the number of affected individuals and the type of data compromised.
- Notification: Procedures for notifying supervisory authorities and affected individuals.
- Remediation: Steps to repair the vulnerability and prevent future breaches.
- Post-Incident Review: Analysis of the breach to identify areas for improvement in security and response procedures.
Regular testing and updating of this plan are vital to ensure its effectiveness in responding to diverse breach scenarios. For example, a tabletop exercise simulating a phishing attack can help a team practice its response and identify potential weaknesses in the plan.
Data Transfers and International Transfers
Navigating the world of data transfers, especially those that cross borders, is a crucial aspect of GDPR compliance. The regulations surrounding the movement of personal data outside the European Economic Area (EEA) are stringent, designed to protect individuals’ privacy rights even when their data travels internationally. Understanding these rules and implementing appropriate safeguards is essential for any organization processing personal data.The GDPR strictly regulates the transfer of personal data outside the EEA.
Simply put, transferring personal data to a country outside the EEA that doesn’t offer an adequate level of data protection is prohibited unless specific safeguards are in place. This is because the data protection laws in non-EEA countries might not be as robust as those within the EEA, potentially leaving individuals’ data vulnerable.
Adequacy Decisions
The European Commission regularly assesses the data protection laws of non-EEA countries. If a country’s laws are deemed to provide an adequate level of protection comparable to that within the EEA, the Commission issues an “adequacy decision.” This decision allows for the free flow of personal data to that country without the need for additional safeguards. However, the list of countries with adequacy decisions is constantly evolving, and it’s crucial to stay updated on the latest decisions.
For example, at the time of writing, some countries with adequacy decisions include Canada, Japan, and certain parts of the US under the Privacy Shield framework (though the validity of this framework is subject to change).
Appropriate Safeguards for Data Transfers, Gdpr compliance checklist 9 step guide
When an adequacy decision doesn’t exist for the recipient country, organizations must implement appropriate safeguards to ensure the lawful transfer of personal data. These safeguards aim to replicate the level of protection offered within the EEA. Common mechanisms include:
The most frequently used mechanism is the use of Standard Contractual Clauses (SCCs). These are pre-approved contractual clauses developed by the European Commission that both the data exporter (the organization transferring the data) and the data importer (the organization receiving the data) must sign. The SCCs Artikel the obligations of both parties to ensure the data is protected according to GDPR standards.
They cover various aspects, including data security, data subject rights, and breach notification.
Another option is the use of Binding Corporate Rules (BCRs). These are internal policies adopted by multinational organizations to govern the transfer of personal data within their corporate group. BCRs must be approved by a supervisory authority in an EEA member state and provide a consistent level of data protection across the entire organization.
Other mechanisms include certified codes of conduct and certification mechanisms, which provide a framework for data protection and compliance. These are often used in specific industries or sectors.
Scenarios Requiring Specific Consideration
Several scenarios necessitate careful consideration for international data transfers:
Cloud service providers: Using cloud services based outside the EEA requires careful scrutiny of the provider’s data protection measures and the contractual arrangements in place to ensure compliance with GDPR. This often involves relying on SCCs or other appropriate safeguards.
Data transfers to law enforcement agencies: Transferring data to law enforcement agencies in non-EEA countries requires careful assessment of the legal basis for the transfer and the level of protection afforded to the data. This often involves a detailed analysis of the legal framework in the recipient country and potentially requires additional safeguards.
Mergers and acquisitions: In the case of mergers and acquisitions involving organizations that process personal data, careful consideration must be given to the transfer of data across borders as part of the transaction. This might involve the use of SCCs or other appropriate safeguards to ensure compliance with GDPR throughout the process.
Data Retention Policy: Gdpr Compliance Checklist 9 Step Guide
Establishing a clear and comprehensive data retention policy is crucial for GDPR compliance. It demonstrates your organization’s commitment to data minimization and responsible data handling, reducing the risk of breaches and fines. A well-defined policy Artikels how long you keep different types of data, ensuring you only retain what’s necessary for legitimate business purposes and complying with legal obligations.
Failure to do so can lead to hefty penalties.A robust data retention policy isn’t just about avoiding legal trouble; it’s about efficient data management. By proactively deleting or archiving data that’s no longer needed, you streamline your operations, reduce storage costs, and minimize the risk of data breaches.
Data Retention Schedules
Creating a schedule involves categorizing your data and assigning appropriate retention periods. This should consider factors such as legal requirements, contractual obligations, and business needs. Remember, the principle of data minimization dictates that you should only retain data for as long as necessary.
- Customer Data (e.g., names, addresses, purchase history): Retention period might be determined by the applicable statute of limitations for contracts or legal claims (e.g., 7 years for tax purposes in some jurisdictions), plus a reasonable buffer period for potential audits or disputes.
- Financial Records (e.g., invoices, bank statements): Often subject to longer retention periods due to legal and auditing requirements (e.g., 7-10 years, depending on the jurisdiction and specific regulations).
- Employee Data (e.g., payroll information, performance reviews): Retention periods vary depending on employment laws and internal policies (e.g., several years after termination for tax and legal reasons).
- Marketing Data (e.g., email subscriptions, website activity): Retention is often tied to the consent period or until the individual unsubscribes, with a reasonable grace period for processing unsubscribes.
- Website Log Files (e.g., IP addresses, browsing history): Retention periods are typically shorter, often ranging from a few weeks to a few months, unless needed for security or legal investigations.
Secure Data Deletion and Archiving
Once the retention period expires, data must be securely deleted or archived. Secure deletion ensures data is irretrievable, while archiving involves storing data in a manner that maintains its integrity and accessibility, should it be needed for legal or auditing purposes.The process should include:
- Data Identification: Accurately identify data that has reached the end of its retention period.
- Data Sanitization: Use secure deletion methods to overwrite or destroy data, rendering it unrecoverable. This may involve specialized software or hardware.
- Verification: Confirm that data has been successfully deleted or archived, potentially through audit trails or verification reports.
- Documentation: Maintain detailed records of the deletion or archiving process, including dates, methods used, and individuals involved. This provides an audit trail for compliance purposes.
- Archiving Considerations: If archiving, ensure the archive is secure, accessible only to authorized personnel, and compliant with data protection regulations. Consider encryption and access controls.
Step 8: Documentation and Records
Maintaining meticulous records is not merely a box-ticking exercise for GDPR compliance; it’s the cornerstone of demonstrating your organization’s commitment to data protection. Comprehensive documentation allows you to proactively manage data, respond effectively to requests, and readily prove your adherence to regulations in the event of an audit. Failing to maintain proper documentation can lead to significant penalties.The GDPR requires organizations to maintain detailed records of their data processing activities.
This isn’t just about having a single document; it’s about a systematic approach to recording and updating information across various aspects of your data handling processes. This comprehensive approach allows for easier tracking, analysis, and demonstration of compliance.
Essential GDPR Documentation
Effective documentation proves your organization’s commitment to data protection. It provides a clear audit trail, allowing you to demonstrate your compliance efforts to supervisory authorities. It also aids in responding to data subject requests and managing potential data breaches efficiently. Without thorough documentation, demonstrating compliance becomes significantly more challenging.
GDPR Documentation Checklist
Regularly reviewing and updating this checklist is crucial. Remember, data processing activities and associated risks evolve, so your documentation must reflect these changes.
Following a GDPR compliance checklist, like my 9-step guide, is crucial for protecting user data. The recent news about facebook asking bank account info and card transactions of users highlights why robust data protection measures are essential. Understanding and implementing a thorough GDPR checklist helps avoid such potentially damaging breaches and ensures your business remains compliant.
- Records of Processing Activities (ROPAs): A central register detailing all data processing activities, including the purpose, categories of data, lawful basis, data retention periods, and security measures.
- Data Mapping and Inventory: A comprehensive inventory of all personal data processed, including its location, format, and purpose.
- Data Subject Access Requests (DSAR) Log: A record of all DSARs received, actions taken, and timelines adhered to.
- Data Breach Register: A log of all data breaches, including the date, nature, affected individuals, and remedial actions taken.
- Data Security Policies and Procedures: Documentation outlining the organization’s security measures to protect personal data, including access controls, encryption, and incident response plans.
- Data Retention Policy: A clear policy outlining how long personal data is stored and the criteria for deletion or archiving.
- Consent Records: Records of all consents obtained from data subjects, including the date, method of obtaining consent, and the specific purpose of processing.
- Contracts with Data Processors: Copies of contracts with data processors, outlining their responsibilities and obligations under the GDPR.
- Employee Training Records: Evidence of employee training on GDPR compliance, including the date, content, and participants.
Best Practices for Maintaining Accurate Records
Accuracy and up-to-dateness are paramount. Outdated or inaccurate records negate the value of documentation and can hinder your ability to demonstrate compliance. A proactive approach is key.
- Regular Reviews: Schedule regular reviews of all documentation to ensure accuracy and completeness. This could be monthly, quarterly, or annually, depending on the volume and complexity of your data processing activities.
- Version Control: Implement a version control system to track changes and revisions to documents. This allows you to easily trace updates and identify the current, valid version.
- Centralized Repository: Store all documentation in a secure, centralized repository that is easily accessible to authorized personnel. Consider using a secure cloud-based system or a dedicated server.
- Designated Data Protection Officer (DPO): Assign a DPO or a dedicated team to oversee the management and maintenance of GDPR documentation. This ensures consistency and accountability.
- Automated Processes: Where possible, utilize automated processes to streamline data collection and record-keeping. This can reduce manual errors and improve efficiency.
Ongoing Monitoring and Review
GDPR compliance isn’t a one-time fix; it’s an ongoing process. Think of it like regular car maintenance – you wouldn’t just get your car serviced once and expect it to run perfectly forever. Similarly, your organization’s data protection practices need consistent attention to remain compliant and effective. Regular reviews and updates are crucial to adapt to evolving regulations, technological changes, and your organization’s own growth.Regular reviews and updates to your GDPR compliance procedures are vital for maintaining compliance and mitigating risks.
Failing to do so can lead to significant fines and reputational damage. A proactive approach ensures your organization stays ahead of potential issues and demonstrates a commitment to data protection. This includes staying informed about changes in legislation, technological advancements in data security, and best practices within your industry.
Periodic Audits and Assessments
A structured plan for periodic audits and assessments is essential. These audits shouldn’t be a rushed, once-a-year event; instead, they should be integrated into your organization’s operational rhythm. Consider conducting internal audits at least annually, with more frequent reviews of specific high-risk areas. These audits should encompass all aspects of your GDPR compliance program, including data mapping, data security measures, incident response plans, and employee training.
External audits, conducted by independent experts, can provide an objective assessment of your compliance posture and identify areas for improvement that internal reviews might miss. For example, a financial institution might schedule a comprehensive GDPR audit every year, with quarterly reviews of their data breach response procedures. A smaller business might conduct a less frequent, but still thorough, annual audit and supplement it with regular internal checks on data security measures.
Addressing Compliance Gaps
Identifying gaps or deficiencies in your compliance program is inevitable. The key is to have a robust process for addressing them promptly and effectively. This process should involve:
- Identifying the gap: Clearly define the nature and extent of the non-compliance.
- Assessing the risk: Evaluate the potential impact of the gap on your organization and data subjects.
- Developing a remediation plan: Create a detailed plan to address the gap, including timelines, responsibilities, and resources.
- Implementing the plan: Execute the remediation plan and monitor its effectiveness.
- Documenting the process: Maintain records of the identified gap, the remediation plan, and the outcome.
For instance, if an audit reveals insufficient employee training on data protection, the remediation plan might include mandatory training sessions, updated training materials, and a system for tracking employee completion. Regular follow-up assessments will ensure the training’s effectiveness in changing employee behavior and improving data protection practices. Documentation of this entire process, from the initial gap identification to the final assessment of the remediation’s success, is crucial for demonstrating accountability and proactive compliance.
Last Word
So, there you have it – a nine-step guide to conquering GDPR compliance. Remember, it’s an ongoing process, not a one-time fix. Regular reviews, updates, and a commitment to data protection are key to long-term compliance. By following these steps, you’re not just ticking boxes; you’re building a culture of responsible data handling that benefits both your business and your customers.
Now go forth and be GDPR-compliant!
FAQ Summary
What happens if I don’t comply with GDPR?
Non-compliance can lead to significant fines, reputational damage, and loss of customer trust.
How often should I review my GDPR compliance?
Regular reviews, ideally annually, are recommended to ensure ongoing compliance and address any changes in legislation or your business practices.
Do I need a lawyer to help with GDPR compliance?
While not always mandatory, legal counsel can be beneficial, especially for complex scenarios or larger organizations. Many resources are available to help you understand the basics, though.
Can I use a GDPR compliance checklist template?
Yes, many templates are available online, but be sure to tailor them to your specific business needs and data processing activities.