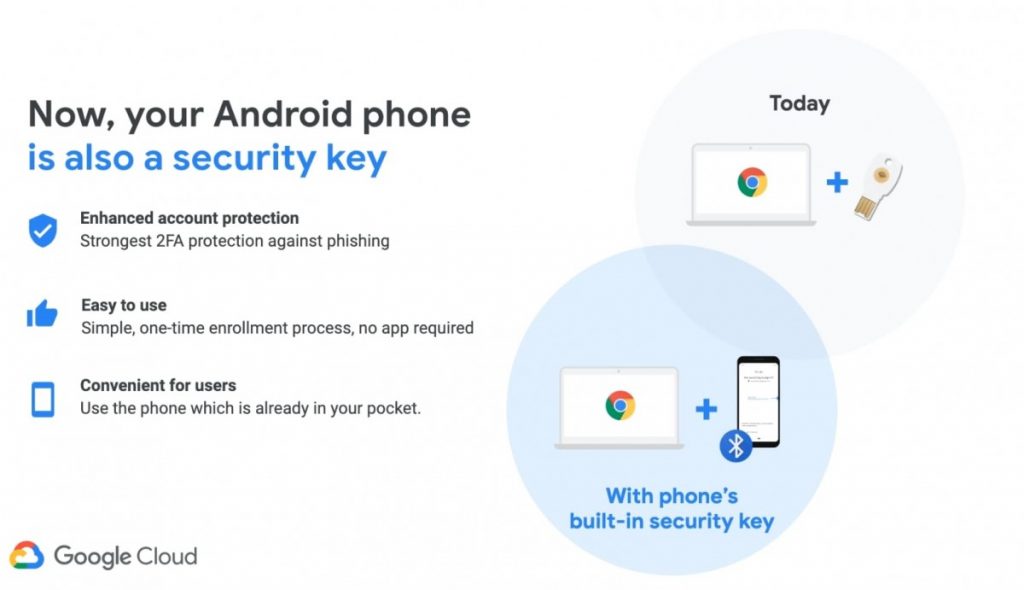
Google Android Phones as Security Keys
Google makes its Android phones as physical security keys for added cybersecurity, offering a novel approach to bolstering digital defenses. This innovative method leverages the familiar Android platform to create a robust security solution, promising enhanced protection against various cyber threats. By transforming everyday devices into secure authentication tools, this approach could revolutionize how we think about physical security keys and potentially make them more accessible to a wider range of users.
The technical details behind this integration, the security advantages and considerations, and the user experience implications are all crucial aspects of this groundbreaking advancement. Furthermore, the potential applications and use cases in various sectors, along with comparisons to existing security methods, are essential components to fully grasp the impact of this new paradigm.
Introduction to Android Phone Security Keys
Physical security keys are a crucial component of modern cybersecurity, offering a strong layer of protection against unauthorized access to sensitive data and systems. They function as a physical barrier, requiring a tangible object to be present for authentication. This eliminates reliance on easily compromised digital factors like passwords or security tokens, which are vulnerable to phishing, malware, or social engineering attacks.
The idea of using an Android phone as a physical security key leverages the increasing ubiquity and security features of smartphones.Using an Android phone as a physical security key offers a compelling approach to enhance security. It blends the convenience of a familiar device with the robust authentication capabilities of dedicated hardware security modules. This approach could significantly reduce the attack surface compared to traditional password-based systems.
This is particularly beneficial in scenarios where enhanced security is paramount, such as financial transactions or sensitive data access.
Potential Benefits of Android Phone Security Keys
This approach to security offers several advantages over traditional methods. By using a device already in frequent use, the friction of adopting a new security system is reduced. The user experience is enhanced because it integrates seamlessly with existing workflows. Furthermore, the physical nature of the security key eliminates the possibility of a compromised digital identity being used to gain unauthorized access.
Mitigation of Security Vulnerabilities
Android phones, when used as security keys, can effectively mitigate various security vulnerabilities. This includes:
- Phishing and Malware Attacks: These attacks often target user credentials to gain access to accounts. By relying on a physical security key, the attacker cannot simply steal the credentials. The physical presence of the Android phone is crucial. This approach significantly diminishes the impact of social engineering attacks.
- Password-based Compromises: Password-based systems are susceptible to numerous attacks. A leaked password can grant access to sensitive accounts. A physical security key prevents access without the physical device, greatly reducing the threat posed by stolen passwords or weak password choices.
- Man-in-the-Middle Attacks: These attacks intercept communications between two parties. A physical security key, like an Android phone, verifies the authenticity of the communicating parties through physical interaction with the device, negating the effect of man-in-the-middle attacks.
Technical Considerations for Implementation
The implementation of Android phones as security keys requires careful consideration of technical aspects. A secure key exchange protocol must be implemented. The Android phone’s security features must be leveraged to ensure the integrity of the authentication process. The protocol should be robust enough to withstand sophisticated attacks, including those designed to compromise the device’s security.
Technical Implementation Details
Integrating Android phones as security keys requires a sophisticated interplay of software and hardware components. This approach leverages the existing robust security features of Android, tailoring them for key-based authentication. The process involves careful design choices to ensure security and compatibility with various authentication protocols.This implementation hinges on establishing a secure channel between the Android device and the authentication service.
The Android device acts as a secure token, storing cryptographic keys and performing cryptographic operations. This method differs significantly from traditional security keys that rely on dedicated hardware, but it leverages the existing security architecture of Android.
Cryptographic Protocols and Algorithms
The chosen cryptographic protocols and algorithms are critical for the security of the system. Robust encryption and hashing algorithms are paramount for protecting the confidentiality and integrity of the authentication process. This includes the use of elliptic curve cryptography (ECC) for key generation and exchange. Secure key storage and management within the Android device are crucial.
Examples of suitable cryptographic algorithms include RSA, ECDSA, and SHA-256. These algorithms are commonly used in security key implementations and offer high levels of security.
Hardware Components
The Android device, itself, becomes the hardware component. Specific hardware features like the Secure Element (SE) are essential. The SE is a dedicated hardware module designed to securely store and manage cryptographic keys, protecting them from unauthorized access. The phone’s processor and memory also play a crucial role in the implementation. Efficient handling of cryptographic operations is vital for real-time authentication.
- The Secure Element (SE): This is a dedicated hardware component on the phone, often integrated with the Trusted Execution Environment (TEE). It acts as a protected enclave, storing and handling sensitive cryptographic keys, preventing malicious software from accessing them.
- Processor and Memory: The phone’s processor and RAM handle the cryptographic calculations required for authentication. Efficient handling of cryptographic operations is critical for responsiveness.
Differences from Traditional Security Keys
This approach differs from traditional security keys in several key ways. Traditional security keys are often dedicated hardware devices, whereas this method utilizes existing Android hardware and software. This leads to potentially lower cost and wider accessibility, as smartphones are already ubiquitous. However, maintaining the same level of security in a general-purpose device requires careful implementation. Furthermore, the software components in Android, if not properly implemented, can pose vulnerabilities.
Security Advantages and Considerations
Using Android phones as security keys offers a compelling approach to enhance cybersecurity, leveraging the ubiquity and familiarity of these devices. This method promises to streamline the authentication process for users, making it more convenient and user-friendly compared to traditional physical security keys. However, implementing this approach requires careful consideration of potential security risks and vulnerabilities.This section explores the security benefits and drawbacks of employing Android phones as security keys, examining the potential attack vectors and vulnerabilities.
It also highlights critical measures to secure the Android phone used as a key, ultimately aiming to provide a balanced perspective on the security advantages and considerations.
Security Enhancements
This approach provides a significant enhancement to traditional security key methods. By leveraging the already widespread adoption of Android phones, this method offers a more accessible and user-friendly authentication process. Furthermore, a strong and secure authentication process can mitigate unauthorized access to sensitive information and systems. This convenience factor is a key advantage for many users, especially in environments where traditional physical security keys are cumbersome or inconvenient.
Potential Security Risks
Employing Android phones as security keys introduces potential vulnerabilities. The very ubiquity of Android phones, while a strength in some respects, also means they are more susceptible to various attacks. A compromised Android device could potentially be used to gain unauthorized access to protected systems.
Attack Vectors and Vulnerabilities
The security of the Android phone used as a security key hinges on the integrity and security posture of the device itself. Several potential attack vectors could compromise the key’s security. These include:
- Malware and Viruses: Malicious software could gain control of the device, potentially enabling unauthorized access to the security key functionality. Examples include rootkits, Trojans, and ransomware, which could compromise the device’s integrity and use the security key to gain access to sensitive data. A compromised phone could then be used to generate fraudulent authentication tokens, thus allowing unauthorized access to the protected system.
- Phishing Attacks: Phishing attacks targeting the Android device could trick the user into revealing security key credentials. This could happen through fake login screens, malicious links, or other deceptive tactics.
- Physical Theft or Loss: The security of the key relies heavily on the security of the phone itself. If the phone is lost or stolen, the attacker gains immediate access to the key. Robust physical security measures are paramount.
- Weak Passwords or Biometric Security Measures: The effectiveness of the Android phone as a security key depends heavily on the user’s choice of passwords or biometrics. If weak or easily guessed, these measures can be circumvented by attackers.
Securing the Android Phone as a Key
To mitigate these risks, several security measures are crucial.
- Strong Passwords and Biometrics: Implementing strong passwords and robust biometric authentication (like fingerprint or facial recognition) is vital to protect against unauthorized access to the device.
- Regular Software Updates: Keeping the Android operating system and all applications updated is critical to patch known vulnerabilities and enhance the device’s overall security.
- Antivirus and Anti-malware Software: Installing and regularly updating antivirus and anti-malware software on the Android phone can provide a layer of protection against malicious software.
- Device Management Solutions: Utilizing device management solutions can help monitor the device’s activity and detect potential security breaches. This includes remote wipe capabilities in case of loss or theft.
- Secure Storage of Credentials: Storing and handling any credentials used to authenticate the security key should be done securely. This includes using strong encryption methods and secure storage protocols.
User Experience and Accessibility: Google Makes Its Android Phones As Physical Security Keys For Added Cybersecurity
Using Android phones as security keys presents a unique opportunity to integrate robust security into everyday workflows, but the user experience must be carefully considered. This approach offers a compelling alternative to traditional methods, promising a seamless and intuitive experience. However, effective implementation hinges on minimizing friction and ensuring accessibility for all users.
User Experience Implications
The user experience is paramount. A clunky or cumbersome process will discourage adoption, defeating the purpose of enhanced security. Users need to be able to seamlessly integrate the phone-as-key into their existing authentication routines, without significantly altering their workflow. This means minimizing the number of steps required for authentication and ensuring intuitive visual cues and prompts.
Comparison with Other Authentication Methods
Compared to traditional methods like passwords or security tokens, using an Android phone as a security key offers a potentially more convenient and secure alternative. Password-based systems are prone to breaches, while security tokens can be cumbersome to manage and sometimes require physical access to a separate device. The Android phone, if implemented effectively, could offer a more convenient experience while still maintaining high security standards.
Setup and Usage Procedures
A streamlined setup process is crucial for user adoption. The steps should be clear, concise, and easily navigable, with helpful visuals and prompts. For instance, a user should be able to quickly pair their Android phone with their target system and complete the initial setup through a guided interface.
- Initial Setup: Users should be guided through the pairing process. This includes installing necessary apps and configuring settings. The interface should be intuitive and avoid technical jargon. The setup should take minimal time, ideally less than 5 minutes.
- Authentication Process: After setup, authentication should be as simple as possible. Ideally, users would just need to unlock their phone to authenticate. Biometric authentication (fingerprint, face ID) can further streamline the process.
- Error Handling: Clear error messages and guidance should be provided if an authentication attempt fails. These messages should be informative without being overly technical. Users should understand the reason for failure and how to rectify it.
Authentication and Access Control Methods
Various methods can be employed to ensure authentication and access control. These methods should be flexible and cater to different user needs and security requirements.
- Biometric Authentication: Leveraging fingerprint or facial recognition significantly reduces the cognitive load on the user, making the authentication process more seamless.
- Two-Factor Authentication (2FA): The Android phone can act as a second factor, adding an extra layer of security beyond the primary password or PIN.
- Conditional Access: Implement rules to limit access based on location, device, or time. This could prevent unauthorized access from unknown locations or devices.
- Role-Based Access Control (RBAC): Different users can be granted varying levels of access based on their roles within the system. This granular control enhances security and ensures appropriate permissions are granted.
Accessibility Considerations
Ensuring accessibility for users with disabilities is critical. The interface should be compatible with screen readers and other assistive technologies. Clear and concise instructions should be provided in multiple languages to cater to a diverse user base.
Potential Applications and Use Cases
Android phones, repurposed as physical security keys, open up exciting possibilities for enhanced cybersecurity across various sectors. This approach leverages existing infrastructure, offering a user-friendly and potentially cost-effective alternative to dedicated hardware security modules (HSMs). The flexibility of Android’s platform allows for seamless integration with existing systems, making this a potentially transformative technology.
Diverse Application Scenarios
The use of Android phones as security keys transcends individual user authentication. Its adaptability allows for application in numerous scenarios, from enterprise-level access control to securing sensitive online transactions.
Enterprise Access Control
Integrating Android phones as security keys into enterprise networks offers a compelling solution for access control. Instead of relying solely on passwords or multi-factor authentication tokens, employees can use their personal Android devices to authenticate, providing a familiar and convenient experience. This approach streamlines the authentication process and reduces the risk of compromised passwords. Imagine a scenario where employees need access to sensitive company data or specific resources.
A simple tap on their Android phone, acting as a security key, can grant them instant access, eliminating the need for separate hardware tokens.
Online Transaction Security
Android phones can significantly bolster online transaction security. Users can leverage their phones as a secondary factor during online payments, logins to banking applications, or other sensitive transactions. This enhances the security posture, making online financial activities less vulnerable to phishing attacks and unauthorized access attempts. For example, during online shopping, a user could authenticate their payment by using their Android phone as a security key.
This extra layer of security mitigates the risk of fraudulent activities.
Government and Public Sector Applications
In the government and public sector, Android phones can be used for accessing sensitive government databases, signing official documents, and handling classified information. By incorporating Android phones as security keys, government agencies can streamline access control and improve the overall security of their systems. Imagine a scenario where a government employee needs to access confidential documents. Using their Android phone as a security key ensures that only authorized personnel can access the information.
Integration with Existing Systems
The seamless integration of Android phones as security keys into existing systems is a key factor in its adoption. The ability to integrate with existing authentication protocols, such as OAuth 2.0, simplifies the transition for organizations. This integration process can be achieved through readily available APIs and SDKs, allowing for a smooth migration path. Existing infrastructure can be leveraged with minimal disruption to the existing workflow.
Real-World Implementation Examples (Hypothetical)
Numerous hypothetical examples showcase the potential of Android phones as security keys. For instance, a company could implement a system where employees use their Android phones to access sensitive company data. This system would integrate with existing access control protocols, requiring users to verify their identity with their Android phone before accessing protected resources. Another hypothetical example includes a secure online voting platform using Android phones as physical security keys for voter authentication, guaranteeing the integrity of the voting process.
The possibilities are truly vast.
Comparison with Existing Security Methods
Google’s proposal to use Android phones as physical security keys presents an intriguing alternative to traditional security key methods. While existing solutions like USB-based security keys and hardware security modules (HSMs) have their strengths, the integration of this technology with a ubiquitous platform like Android opens up new possibilities and challenges. This approach requires a careful analysis of its advantages, disadvantages, and potential impact on the security landscape.The existing security key landscape is diverse, with various approaches catering to different needs and security requirements.
Comparing Google’s proposal against these established methods allows for a nuanced understanding of its potential position in the market. The accessibility and user-friendliness of Android phones are significant factors, while the inherent security of the device itself needs robust evaluation.
Advantages of Using Android Phones as Security Keys
The ubiquitous nature of Android phones offers a substantial advantage over dedicated security keys. Many users already possess Android devices, minimizing the need for additional hardware purchases. This accessibility can significantly increase the adoption rate compared to traditional solutions. Furthermore, the potential integration with existing Android ecosystems and services provides an attractive feature set.
Disadvantages of Using Android Phones as Security Keys
Security relies heavily on the overall security of the Android device itself. Compromised devices can potentially compromise the entire security system. This inherent vulnerability is a significant concern that needs careful mitigation. Maintaining the security posture of the Android phone becomes paramount for the success of this approach. Also, the potential for malware or compromised applications poses a threat to the security of the key.
Further, the security of the operating system itself and its updates is crucial.
Analysis of Potential Market Impact
The potential market impact of this technology is substantial. The integration with Android’s massive user base could drive significant adoption, potentially disrupting the existing security key market. This could lead to increased competition, driving innovation and potentially lowering the cost of security solutions. The potential for integration with other Google services, such as cloud storage, could further expand its reach.
An example of market impact is the significant increase in smartphone usage that has transformed communication and personal computing.
Comparison Table of Security Key Types
| Security Key Type | Strengths | Weaknesses |
|---|---|---|
| USB-based Security Keys | High security, dedicated hardware | Limited accessibility, higher initial cost, potential for physical loss |
| Hardware Security Modules (HSMs) | High security, robust encryption, enterprise-grade security | Specialized hardware, often high cost, limited accessibility to non-enterprise users |
| Android Phone Security Keys | High accessibility, integration with existing ecosystem, potential for lower cost | Reliance on Android OS security, potential for device compromise, need for strong security measures |
Future Directions and Research
Android phones as security keys open exciting avenues for future research and development. The integration of physical security into everyday devices like smartphones presents opportunities for enhanced user security and potentially lower overall security costs compared to traditional methods. This section will explore potential future developments, open challenges, and a roadmap for research and development in this evolving field.
Potential Developments in Hardware Integration
Hardware advancements will play a critical role in shaping the future of Android phone security keys. Increased processing power and specialized hardware for cryptographic operations can significantly boost performance and security. Furthermore, the incorporation of advanced sensor technologies like biometric authentication alongside the security key function can create a more comprehensive and user-friendly security framework. For example, the integration of fingerprint sensors or facial recognition could enhance the security and convenience of authentication processes.
Usability and Accessibility Enhancements
Improving user experience and accessibility is crucial for widespread adoption. Future research should focus on designing intuitive interfaces for secure key interactions, minimizing friction points, and making the system usable by a broad range of users, including those with disabilities. This includes creating more seamless integration with existing Android functionalities and exploring alternative input methods to suit diverse user needs.
For instance, a voice-activated authentication system could make the security key more accessible to users with limited mobility.
Enhanced Security Protocols and Algorithms
Continuously evolving threats necessitate the development of robust security protocols and algorithms. Future research should explore the use of advanced cryptography techniques, like post-quantum cryptography, to safeguard against future threats. It’s also important to analyze and address potential vulnerabilities in the existing security architecture, aiming for a layered approach to defense. By proactively anticipating potential weaknesses and incorporating stronger security mechanisms, the security key can adapt to evolving attack vectors.
Google’s move to make Android phones physical security keys is a smart way to boost cybersecurity. While this is great, it’s worth remembering that vulnerabilities like those found in Microsoft Azure Cosmos DB, detailed in Azure Cosmos DB Vulnerability Details , highlight the ever-present need for robust security measures across all platforms. This underscores the importance of continued innovation in security technologies, even with seemingly secure devices like Android phones.
Cost-Effectiveness and Scalability
Cost-effectiveness and scalability are essential for widespread adoption. Future research should focus on optimizing the manufacturing process for security keys to reduce production costs without compromising security. Additionally, the design should consider how to implement a cost-effective solution for the widespread deployment and maintenance of the system. This could involve exploring cloud-based infrastructure to reduce hardware dependency and potentially lower the cost for users.
Roadmap for Future Research and Development
A phased approach is recommended for future research and development.
- Phase 1: Focus on enhancing the usability and accessibility of the security key, with specific attention to user interface design, and support for diverse input methods. This phase will include extensive user testing to ensure the system is intuitive and usable for various user demographics.
- Phase 2: Prioritize the exploration of advanced security protocols, including post-quantum cryptography, and incorporate rigorous security audits to identify and mitigate vulnerabilities. This phase will require collaborations with security experts to ensure robust security measures are in place.
- Phase 3: Investigate cost-effective manufacturing processes and scalable deployment strategies, exploring cloud-based solutions and optimized hardware designs. This phase will focus on achieving a balance between cost-effectiveness and security robustness.
- Phase 4: Expand research to include the integration of advanced sensors and biometric authentication, alongside exploring the potential of decentralized authentication and blockchain technologies. This phase will aim to create a secure, user-friendly, and versatile authentication system for diverse applications.
Security Best Practices
Using an Android phone as a physical security key introduces a new layer of security, but proper implementation is crucial. Neglecting best practices can compromise the security benefits and potentially expose sensitive data. This section Artikels critical steps for securing both the Android device and the associated security key functionality.
Physical Security of the Android Device
Proper physical security of the Android device is paramount. A compromised device can lead to unauthorized access to the security key’s cryptographic functions. Therefore, safeguarding the physical device is as vital as the security key itself.
Google’s move to make Android phones physical security keys is a smart step towards boosting cybersecurity. However, simply relying on hardware isn’t enough in today’s complex digital landscape. We also need to focus on the software side of things, like deploying AI code safety tools, like those discussed in Deploying AI Code Safety Goggles Needed.
Ultimately, a multi-layered approach, combining strong hardware security keys with advanced software security analysis, will be key to maintaining robust security against evolving threats, and Google’s approach is a great first step in this direction.
- Secure Storage: Store the Android device in a secure location, preferably one that restricts unauthorized access. Consider a locked cabinet or a secure room with restricted access. Avoid leaving the device in easily accessible areas where it could be stolen or compromised.
- Physical Protection: Protect the device from physical damage or tampering. Use a protective case, screen protector, and other physical safeguards to deter potential attacks.
- Anti-theft Measures: Enable anti-theft features on the device. These features often include remote locking, location tracking, and data wiping capabilities, which can aid in recovering a lost or stolen device and preventing unauthorized access.
- Password Protection: Implement strong passwords or biometric authentication methods (like fingerprint or facial recognition) for the device’s lock screen to prevent unauthorized access when the device is in use.
Software Security Measures
Securing the software environment is critical to maintaining the integrity of the Android device as a security key. Vulnerabilities in the software can be exploited to compromise the cryptographic operations or access sensitive data.
- Regular Software Updates: Keep the Android operating system and all installed applications up-to-date. Updates often include security patches that address vulnerabilities and strengthen the device’s defenses.
- Trusted Sources: Only install applications from trusted sources (like the Google Play Store) to mitigate the risk of malware or malicious code.
- Disable Unnecessary Features: Disable any unnecessary or potentially risky features on the device, like Bluetooth or Wi-Fi when not in use, to minimize exposure to potential threats.
- Security Apps: Consider using security apps that provide extra layers of protection. These can scan for malware, detect suspicious activity, and offer additional security features.
Hardware Security Considerations
Hardware components of the Android device play a critical role in its security as a key. Physical tampering with the device’s hardware could expose sensitive cryptographic data.
- Hardware Integrity: Regularly inspect the device for any signs of physical damage or tampering. Any suspicious changes or damage should immediately prompt a security review.
- Secure Boot: Ensure that the device utilizes secure boot to verify the integrity of the operating system at startup. This prevents malicious code from loading during boot.
- Device Integrity Verification: Use device integrity verification tools to detect any modifications to the device’s hardware or software components that could compromise its security.
- Secure Storage for Cryptographic Keys: Use secure storage mechanisms for storing cryptographic keys related to the security key functionality to prevent unauthorized access.
Mitigating Threats and Vulnerabilities
Implementing robust security practices minimizes potential threats and vulnerabilities. A multi-layered approach is essential to address potential attacks from different vectors.
- Security Audits: Conduct periodic security audits to identify and address potential weaknesses in the device’s security configuration.
- Regular Security Awareness Training: Educate users about the importance of security practices and the potential risks associated with neglecting these practices.
- Incident Response Plan: Develop and test an incident response plan to handle security breaches or vulnerabilities effectively.
- Penetration Testing: Consider conducting penetration testing on the Android device to simulate potential attacks and identify vulnerabilities before they are exploited by malicious actors.
Illustrative Examples
Android phones as security keys offer a compelling new approach to digital security. Imagine a world where your phone, a ubiquitous device, doubles as your primary authentication method, eliminating the need for separate, often forgotten or misplaced physical security keys. This concept unlocks exciting possibilities, enhancing security while streamlining the user experience.
Hypothetical Scenario
A user, Sarah, needs to access her online banking account. Traditionally, she would use a separate security key, but with this new approach, her Android phone serves as the key. When attempting to log in, the banking application prompts Sarah’s phone for authentication. The phone, recognizing the legitimate request from the banking app, performs a secure authentication process, verifying Sarah’s identity through biometrics or a PIN.
Successful authentication grants access to her account. This scenario highlights the ease and efficiency of this technology, integrating seamlessly into existing workflows.
Implementing Security Key Functionality
To implement the security key functionality on an Android device, developers would integrate a dedicated security module within the operating system. This module would handle all authentication requests from external applications, ensuring secure communication and data handling. The module will be designed with robust encryption and access controls. It would securely store and manage the user’s credentials and authentication keys.
Setting Up and Using the Approach
Setting up the security key functionality would involve a few steps. First, the user would install a specific app or update their existing banking app to utilize the new functionality. Then, the user would configure the desired authentication methods (biometrics or PIN). This process would involve secure setup procedures to ensure the user’s credentials are protected. Once set up, every authentication attempt to the protected applications would utilize the phone’s security key.
Illustrative Diagram
The following diagram illustrates the authentication flow:
+-----------------+ +-----------------+
| User's Android | --> | Banking App |
| Phone | | (on Server) |
+-----------------+ +-----------------+
| ^
| |
| Authentication Request |
| (via secure channel) |
| |
v v
+-----------------+ +-----------------+
| Security Module | --> | Authentication |
| (on Android Phone)| | Mechanism |
+-----------------+ +-----------------+
| ^
| |
| Verification & | +-----------------+
| Authentication | | Response |
| (using Biometrics/PIN) | | (access granted)|
| | +-----------------+
v v
+-----------------+ +-----------------+
| Access Granted | <-- | Banking App |
| (to Account) | | (on Server) |
+-----------------+ +-----------------+
The diagram depicts the secure communication channel between the user's phone, the security module, and the banking application.
The data flows securely, and the security module plays a critical role in ensuring authentication integrity. The authentication mechanism verifies the user's identity using configured methods, enabling access to the account.
Potential Impact on Existing Systems
Integrating Android phone security keys into existing systems presents a compelling opportunity to bolster security, but careful consideration is needed. The transition will require assessing existing infrastructure, identifying potential compatibility issues, and designing strategies for seamless implementation across various environments. This process must prioritize user experience and minimize disruption to existing workflows.
Integration Strategies
Implementing Android phone security keys within existing systems necessitates a strategic approach. One strategy is to leverage existing authentication protocols, such as those based on username/password combinations or multi-factor authentication (MFA) systems. A phased rollout, beginning with pilot programs in specific departments or locations, can help assess the impact and identify potential challenges before widespread adoption.
Infrastructure Modifications
The introduction of Android phone security keys will likely require modifications to existing infrastructure. This includes updating software and hardware components to support the new authentication method. For instance, systems may need to be upgraded to handle the additional authentication steps required by the security keys. Furthermore, existing network configurations might need adjustments to ensure secure communication between the security keys and the system.
Google's move to make Android phones physical security keys is a smart play for boosting cybersecurity. This innovative approach directly addresses the need for stronger authentication methods, but it's also worth noting that parallel developments like the Department of Justice Offers Safe Harbor for MA Transactions Department of Justice Offers Safe Harbor for MA Transactions highlight a broader push for secure transactions.
Ultimately, these advancements create a more robust and reliable digital ecosystem, pushing us toward a future where our online interactions are more secure and trustworthy, and that's good news for all of us.
Compatibility Considerations
Compatibility issues are a potential concern during the transition. Older systems might not be compatible with the new authentication method, requiring either upgrades or workarounds. Compatibility testing is crucial to identify and resolve these issues. For example, legacy applications might need modifications to accommodate the security keys. Solutions include developing wrapper applications to bridge the gap between legacy systems and the new authentication standard.
Implementation in Diverse Environments
The versatility of Android phone security keys allows for implementation in various environments. From enterprise networks to cloud-based applications, the adaptability of the technology facilitates integration. Consider a hospital setting where patient data is highly sensitive. The use of Android phone security keys could enhance security by requiring authentication for accessing sensitive medical records. Another example is in financial institutions, where implementing the keys could add another layer of security to transactions, safeguarding customer data and preventing fraud.
These varied environments necessitate customized strategies for integration, taking into account specific security requirements and user workflows.
User Experience Considerations, Google makes its android phones as physical security keys for added cybersecurity
The user experience is paramount. Any new security method must be intuitive and user-friendly to avoid hindering productivity. Intuitive setup and use instructions are crucial to avoid user frustration. Training programs for employees can facilitate a smooth transition and minimize disruptions to their daily work. Clear instructions and support materials should be provided to guide users through the implementation process.
Summary

Google's initiative to integrate Android phones as security keys signifies a significant leap forward in cybersecurity. By blending the convenience of smartphones with the rigor of physical security keys, this approach has the potential to drastically improve security postures across numerous applications and industries. While the transition to this new paradigm will likely require careful consideration and user education, the long-term benefits are substantial and worth exploring.
FAQ Summary
What are the potential security risks associated with using Android phones as security keys?
While Android phones offer a convenient security key option, potential risks include device loss or theft, compromised device software, and vulnerabilities in the underlying cryptographic implementation. Robust security measures for the phone itself and secure management of the keys are essential to mitigate these risks.
How does this method differ from traditional security key approaches?
Traditional security keys are often dedicated hardware devices. This approach leverages the existing infrastructure of Android phones, potentially increasing accessibility and reducing the need for separate physical devices. However, it also introduces the need for robust software and security measures within the Android OS itself.
What steps are required for users to set up and use this system?
The setup process would likely involve specific configuration within the Android OS and possibly a dedicated application. Users would need to establish a secure connection to the system and potentially utilize multi-factor authentication methods to ensure access.
What are some illustrative examples of how this technology could be applied in different sectors?
Potential use cases span various sectors, including finance, healthcare, and government. In finance, secure access to accounts could be significantly improved, while in healthcare, secure access to patient records is a critical application. Government agencies could utilize this method for enhanced data protection and security.