Hackers Target UnityPoint Health Phishing Scam
Hackers target UnityPoint Health with email phishing scam, a concerning incident that highlights the vulnerability of healthcare organizations to cyberattacks. This attack used deceptive emails to potentially steal sensitive patient data, raising significant concerns about the security measures in place. The potential impact on patient privacy and the organization’s reputation is substantial, necessitating a thorough understanding of the methods employed and potential remedies.
The phishing emails likely contained malicious links or attachments designed to trick recipients into revealing personal information or downloading malware. UnityPoint Health’s response and preventative measures will be crucial in mitigating future attacks. This incident serves as a stark reminder of the ongoing threat of cybercrime and the importance of robust security protocols.
Introduction to the UnityPoint Health Phishing Incident: Hackers Target Unitypoint Health With Email Phishing Scam
UnityPoint Health, a significant healthcare provider, recently faced a concerning email phishing scam. Malicious actors attempted to compromise sensitive data through deceptive emails designed to trick employees into revealing personal information or clicking on malicious links. This attack highlights the persistent threat of phishing in the healthcare sector and the potential for substantial damage to both operations and reputation.The impact of this attack extends beyond immediate financial loss.
Compromised patient data could lead to identity theft, fraud, and severe reputational damage for UnityPoint Health. Furthermore, operational disruptions, including system downtime or data breaches, can negatively impact patient care and create significant administrative burdens for the organization. The meticulous planning behind such attacks often indicates a targeted effort, suggesting a potential threat to sensitive information held by the institution.
Characteristics of the Phishing Emails
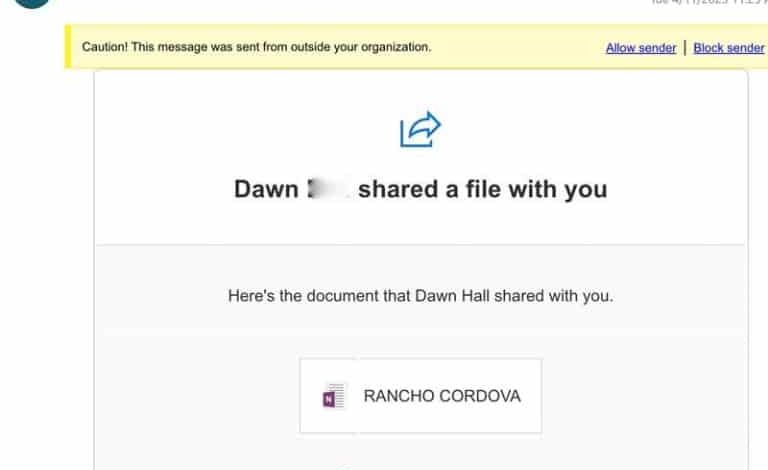
The phishing emails employed various tactics to deceive recipients. Common characteristics included a sense of urgency, a professional tone mimicking legitimate communications, and the use of official-looking logos and branding. The emails often contained hyperlinks disguised as legitimate websites, which led to fraudulent login pages or malicious downloads.
Methods of Distribution
The phishing emails were likely distributed through various channels. These included bulk email campaigns targeting a wide range of employees, potentially using compromised email accounts to send messages from seemingly trusted sources. Sophisticated social engineering techniques, such as spear phishing (targeting specific individuals), were likely used to enhance the effectiveness of the attack.
Specific Examples of Phishing Email Techniques
Phishing emails often employ several techniques to manipulate victims. These include impersonating trusted individuals or organizations, creating a sense of urgency or fear, and manipulating emotions to encourage clicks on malicious links. The emails may appear to come from a senior executive or a trusted colleague, which can add to their deceptive nature.
Types of Data Potentially Compromised
The UnityPoint Health phishing incident highlights the serious risk of data breaches in healthcare settings. Cybercriminals targeting healthcare organizations often seek access to sensitive patient information, which can have severe consequences for individuals and the institution. Understanding the types of data at risk and the potential impact is crucial for mitigating the effects of such attacks.
Patient Records
Patient records are a primary target for attackers. These records contain highly sensitive information, including medical history, diagnoses, treatment plans, and personal identifiers. A breach can expose patients to identity theft, medical fraud, and emotional distress. For instance, unauthorized access to medical records could allow attackers to impersonate patients for fraudulent purposes or to blackmail them. Moreover, the release of sensitive information could violate patient privacy, potentially damaging the reputation of the healthcare provider.
Financial Information
Financial details, such as payment information, insurance details, and billing records, are also vulnerable. Compromised financial data could lead to fraudulent charges, identity theft, and financial losses for patients. The potential for unauthorized access to bank account information or credit card details is significant, and the resulting financial burden on patients can be substantial. Examples of real-world breaches involving financial data in healthcare settings demonstrate the devastating consequences of such compromises.
Other Confidential Details
Beyond patient records and financial information, attackers might target other confidential details. This includes information about medications, allergies, family history, and even social security numbers. These details, when misused, can lead to serious implications for patients, potentially compromising their well-being and financial stability. For instance, attackers could use this data to target individuals for targeted phishing campaigns or to create fraudulent insurance claims.
The wide range of data that can be accessed underscores the importance of robust security measures to protect patient confidentiality.
Vulnerabilities Exploited
Attackers often leverage social engineering tactics, exploiting human weaknesses to gain access to sensitive data. This includes crafting convincing phishing emails that mimic legitimate communications from the organization, thereby tricking employees into divulging credentials or clicking malicious links. Technical vulnerabilities in the organization’s systems, such as outdated software or weak passwords, can also be exploited by attackers. The combination of social engineering and technical vulnerabilities makes healthcare organizations particularly vulnerable to cyberattacks.
Comparison of Data Types and Impact
| Type of Data | Potential Impact of Compromise |
|---|---|
| Patient Records | Identity theft, medical fraud, emotional distress, reputational damage |
| Financial Information | Fraudulent charges, identity theft, financial losses, potential for blackmail |
| Other Confidential Details | Targeted phishing campaigns, fraudulent insurance claims, compromising well-being |
The table above highlights the potential impact of each data type being compromised. The consequences can range from financial losses and reputational damage to serious emotional distress and potential harm to physical health. Protecting all these data types requires a multi-faceted approach, including strong security protocols, employee training, and regular system updates.
Cybersecurity Implications for Healthcare Organizations
The UnityPoint Health incident highlights a critical vulnerability in healthcare’s digital landscape. Phishing attacks, leveraging deceptive emails, are a pervasive threat, and the healthcare sector, with its sensitive patient data, is particularly vulnerable. Understanding the specific cybersecurity challenges and appropriate defenses is crucial for protecting patient information and maintaining public trust.Healthcare organizations face a unique set of cybersecurity threats.
Beyond the general risks of data breaches, they must contend with stringent regulations like HIPAA, which mandate the protection of protected health information (PHI). Non-compliance can result in significant financial penalties and reputational damage. This makes robust security measures not just a best practice, but a legal and ethical imperative.
General Cybersecurity Threats to Healthcare
Healthcare organizations are prime targets for cybercriminals due to the high value of the sensitive patient data they possess. These threats include not only phishing attacks, but also malware infections, ransomware attacks, and denial-of-service (DoS) attacks. The consequences can range from data breaches and financial losses to disruptions in critical operations and potential harm to patients.
Security Measures UnityPoint Health Might Have in Place
UnityPoint Health, like other healthcare providers, likely employs a multi-layered security approach. This includes firewalls, intrusion detection systems, and anti-malware software to prevent unauthorized access. They likely also have access controls and user authentication protocols in place. The effectiveness of these measures, however, depends heavily on the implementation and ongoing maintenance of the system. A key aspect of security is consistent staff training, highlighting the importance of recognizing phishing attempts and reporting suspicious emails.
Importance of Robust Email Security Protocols
Email security is a cornerstone of any effective cybersecurity strategy. Robust email security protocols should include spam filters, email encryption, and authentication measures such as DKIM, SPF, and DMARC. These protocols help identify and block malicious emails, reducing the risk of successful phishing attacks.
User Awareness Training
User awareness training is essential to mitigate the impact of phishing attempts. Training programs should educate employees on identifying phishing emails, recognizing suspicious links and attachments, and reporting suspicious activity to the appropriate channels. The training must be regular, comprehensive, and relevant to the evolving threats. Regular refresher courses can reinforce the importance of vigilance.
Recommended Cybersecurity Measures for Future Prevention
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring multiple verification steps before granting access to sensitive systems. This significantly reduces the risk of unauthorized access, even if a password is compromised. Consider enforcing MFA for all employees and external access.
- Regular Security Audits and Penetration Testing: Regular security audits and penetration testing help identify vulnerabilities in systems and processes. These audits can highlight weaknesses that attackers might exploit, allowing for proactive remediation. Regular evaluations are essential to ensure the effectiveness of security measures.
- Endpoint Detection and Response (EDR): Implementing EDR solutions allows for the monitoring of endpoints for suspicious activity. This proactive approach enables the detection and response to potential threats in real-time, reducing the impact of any breach.
- Data Loss Prevention (DLP) Tools: Implementing DLP tools helps prevent sensitive data from leaving the organization’s control. This is crucial for healthcare organizations handling PHI, as it safeguards against accidental or malicious data breaches. DLP tools can help regulate the sharing and transmission of data, ensuring compliance with regulations.
Potential consequences and remedies

The UnityPoint Health phishing incident highlights the severe consequences of cybersecurity breaches in healthcare. Beyond the immediate disruption, reputational damage and financial losses can be substantial, impacting patient trust and long-term sustainability. Understanding the potential ramifications and implementing effective mitigation strategies are crucial for organizations like UnityPoint Health to bounce back stronger.The consequences of a successful phishing attack extend beyond just the immediate financial impact.
The erosion of patient trust and the potential for legal repercussions can have a long-lasting effect on the organization’s reputation and future operations.
Financial Repercussions
The financial impact of a data breach can be substantial. Direct costs include forensic analysis, notification procedures, and legal fees. Indirect costs, such as lost revenue due to patient attrition, decreased insurance rates, and reputational damage, can be significantly higher. For example, a 2020 study by IBM found that the average cost of a data breach in the healthcare sector was well over $9 million.
These figures underscore the critical need for proactive cybersecurity measures.
Reputational Damage
A data breach can severely damage a healthcare organization’s reputation. Patients may lose trust in the organization’s ability to protect their sensitive information, potentially leading to a decline in patient enrollment and referrals. The negative publicity associated with a breach can tarnish the organization’s image and impact its standing within the community. The healthcare industry relies heavily on public trust; a breach can severely erode this trust, leading to long-term consequences.
Examples of reputational damage can be seen in other high-profile healthcare breaches, where patients lost faith in the organization’s ability to maintain confidentiality.
Mitigation Strategies
UnityPoint Health can employ various strategies to mitigate the impact of the breach. These include implementing robust security measures, conducting thorough incident response planning, and establishing clear communication channels for affected parties. These steps can reduce the severity of the breach and minimize the potential harm to patients, employees, and the organization.
UnityPoint Health recently fell victim to a nasty email phishing scam, highlighting the ongoing threat of cyberattacks. Fortunately, measures like those outlined in the Department of Justice’s Safe Harbor policy for Massachusetts transactions Department of Justice Offers Safe Harbor for MA Transactions could potentially help mitigate such risks in other regions. This underscores the importance of proactive security measures in healthcare and other sectors to prevent similar incidents from occurring.
Containing the Phishing Attack
Immediate action is critical to contain the spread of a phishing attack. This involves identifying the source of the attack, blocking malicious emails, and educating employees on recognizing phishing attempts. The organization needs to promptly investigate the source of the attack to prevent future occurrences. Implementing robust email filtering systems and employee training programs can significantly reduce the risk of similar attacks.
Patient and Employee Notification Procedure
A transparent and timely notification process is essential for maintaining patient and employee trust. UnityPoint Health should develop a detailed procedure outlining the steps to notify affected individuals, providing clear explanations of the breach, and offering support resources. The procedure should include specific timelines for notification, methods of communication, and contact information for support. Transparency and proactive communication are key to maintaining trust and minimizing the negative impact on affected individuals.
Example Notification Process
A well-defined notification process should include:
- Identification of Affected Parties: Precisely identify patients and employees whose data may have been compromised.
- Notification Timeline: Establish a clear timeline for notification, adhering to legal and regulatory requirements.
- Communication Channels: Utilize various communication channels, such as email, phone calls, and/or letters, depending on the specific situation.
- Content of Notifications: Provide clear and concise information about the breach, including what data was compromised, what steps are being taken to remediate the situation, and the available support resources.
- Post-Notification Support: Provide ongoing support for affected individuals through dedicated phone lines, online portals, or counseling services, if needed.
Prevention Strategies for Future Attacks

The UnityPoint Health incident highlights the critical need for proactive security measures to mitigate the risk of future cyberattacks. A multifaceted approach, encompassing employee education, robust technical controls, and a culture of security awareness, is essential for building a resilient defense against phishing and other sophisticated threats.Effective prevention requires a comprehensive strategy that goes beyond simply reacting to incidents.
Organizations must adopt a proactive stance, focusing on identifying vulnerabilities, implementing preventative measures, and fostering a culture of security vigilance among all employees. This includes not only technical safeguards but also fostering a mindset of skepticism and caution towards suspicious communications.
Employee Training Programs
Employee training is paramount in preventing phishing attacks. A robust training program should equip employees with the knowledge and skills to recognize and avoid phishing scams. These programs should be ongoing, not a one-time event, and should include simulated phishing exercises to reinforce learning.Training should cover various aspects of phishing attacks, including:
- Identifying suspicious email characteristics, such as poor grammar, urgent requests, and unfamiliar senders.
- Recognizing the subtle cues of malicious links and attachments.
- Understanding the importance of verifying information before clicking on links or downloading attachments.
- Knowing the appropriate channels for reporting suspicious emails.
- Practicing good password hygiene and avoiding reuse of passwords across multiple accounts.
Security Measures and Effectiveness
Implementing strong security measures is critical to fortifying defenses against phishing attacks. A layered approach, combining multiple security controls, is more effective than relying on a single measure.
| Security Measure | Effectiveness in Preventing Phishing Attacks |
|---|---|
| Multi-Factor Authentication (MFA) | Significantly increases the difficulty for attackers to gain access to accounts even if credentials are compromised. |
| Email Filtering and Spam Blocking | Reduces the likelihood of phishing emails reaching employee inboxes. |
| Antivirus and Anti-malware Software | Detects and blocks malicious software, including those disguised as attachments. |
| Regular Security Audits | Identifies vulnerabilities and gaps in security posture that could be exploited in phishing attacks. |
| Data Loss Prevention (DLP) Tools | Reduces the risk of sensitive data falling into the wrong hands via phishing attacks. |
| Security Information and Event Management (SIEM) Systems | Collects and analyzes security logs to detect suspicious activities and potential threats, including phishing campaigns. |
Secure Email Protocols and Procedures
Robust email protocols and procedures are vital components of a comprehensive security strategy.
- Implement strong password policies. Enforce password complexity requirements, and mandate regular password changes.
- Establish clear email communication protocols. Define procedures for how sensitive information should be transmitted, and encourage the use of secure channels.
- Verify sender authenticity. Implement measures to verify the authenticity of email senders and avoid accepting emails from unknown sources.
- Use secure email gateways. Employ email gateways to filter out spam and malicious content before it reaches employees’ inboxes.
- Enable email authentication protocols. Employ mechanisms such as DMARC, SPF, and DKIM to authenticate email senders and prevent spoofing.
“A multi-layered approach to security is crucial, combining technical controls with employee education and awareness.”
Illustrative Case Study
Phishing attacks are a persistent threat, particularly in the healthcare sector. Understanding how these attacks unfold and the tactics employed can help organizations better protect themselves. A closer look at similar incidents reveals common patterns and helps anticipate future strategies.Healthcare organizations, due to the sensitive data they handle, are frequent targets for malicious actors. Criminals leverage phishing scams to gain unauthorized access to patient records, financial information, and intellectual property.
Examining past cases highlights the methods used and provides insights into how to improve security protocols.
Similar Email Phishing Scam Against a Healthcare Organization
The Community Health System (CHS) faced a significant phishing attack in 2022. Criminals sent emails mimicking legitimate CHS communications, prompting employees to click on malicious links. The links led to fake login pages designed to steal credentials. This type of attack, leveraging social engineering, is common in healthcare.
Successful Phishing Campaigns: Tactics and Methods
Phishing campaigns often utilize deceptive emails, creating a sense of urgency or legitimacy. The CHS attack exemplified this by including false claims of system updates or critical security alerts. The attackers crafted emails that mimicked official communications, employing branding and language consistent with CHS’s communications. Furthermore, they used techniques to make the emails appear authentic, like spoofing email addresses.
A key element is the use of psychological manipulation to trick recipients into taking action.
Methods Used to Spread the Attack
The spread of the attack typically involved a chain reaction. Once an employee clicked on the malicious link, their credentials were harvested. Attackers then used these credentials to access further systems or to spread the attack to other employees. Email chains, often with automated or targeted messaging, can amplify the attack’s reach. In the CHS incident, the attackers exploited the existing email infrastructure for wider dissemination.
Comparison and Contrast with the UnityPoint Health Case, Hackers target unitypoint health with email phishing scam
While the UnityPoint Health incident focused on a specific type of data, such as employee information, the CHS case highlights the potential impact on patient records. Both instances demonstrate the effectiveness of social engineering techniques in bypassing security measures. A key difference lies in the targets; UnityPoint Health aimed for employees, while CHS aimed for both employees and possibly patients.
Both cases underscore the need for robust security measures, including email authentication and employee training, to mitigate such attacks. Stronger email security protocols, such as multi-factor authentication, can significantly reduce the effectiveness of these attacks.
Recommendations for enhanced security
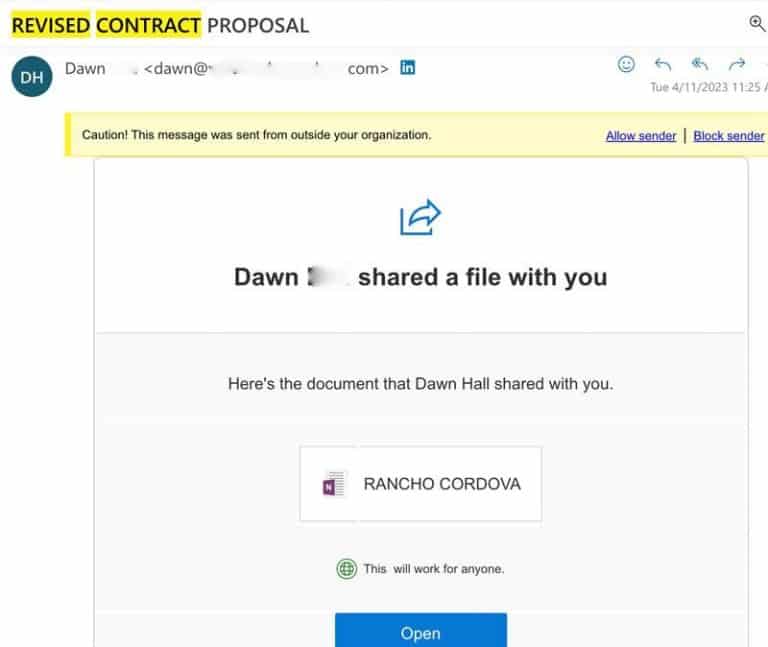
UnityPoint Health needs a multi-faceted approach to email security, encompassing both technological solutions and user education. This involves implementing robust security measures to prevent future phishing attacks and cultivating a culture of security awareness among employees. A layered approach, combining technical controls with human factors, is crucial for creating a strong defense against evolving cyber threats.This section details specific recommendations for enhancing email security and user awareness at UnityPoint Health, outlining crucial technologies and user training strategies to mitigate future phishing attempts.
UnityPoint Health recently fell victim to a nasty email phishing scam, highlighting the ongoing threat of cyberattacks. This underscores the critical need for robust security measures, particularly in healthcare. Protecting sensitive patient data requires more than just reactive measures; proactive steps like deploying AI Code Safety Goggles Needed are essential. Deploying AI Code Safety Goggles Needed can help identify and mitigate vulnerabilities before hackers exploit them.
This proactive approach is crucial for organizations like UnityPoint Health to avoid future phishing scams and protect patient information.
These recommendations are grounded in best practices and lessons learned from similar incidents.
So, hackers are targeting UnityPoint Health with a nasty email phishing scam. This highlights the ever-present threat of social engineering tactics. Interestingly, a similar vulnerability exists within the Azure Cosmos DB ecosystem, as detailed in Azure Cosmos DB Vulnerability Details , which could be exploited in a much broader attack. This further emphasizes the need for robust security measures in healthcare systems, like UnityPoint Health, to combat these increasingly sophisticated phishing attempts.
Email Security Enhancements
Email security requires a layered approach, combining technological solutions with user awareness training. Strengthening the defenses at various points of the email lifecycle is vital. This involves filtering potentially malicious emails, educating users on identifying phishing attempts, and implementing robust authentication mechanisms.
- Advanced Threat Protection (ATP): Implementing advanced email security solutions that employ sophisticated filtering and analysis techniques can significantly reduce the likelihood of phishing emails reaching employee inboxes. ATP systems use machine learning, heuristic analysis, and behavioral analysis to identify and block suspicious emails, preventing malicious content from entering the network. This proactive approach reduces the attack surface.
- Spam Filters and Anti-Phishing Tools: Modern spam filters utilize sophisticated algorithms to identify and block known phishing patterns and malicious content. Supplementing these filters with anti-phishing tools that employ reputation databases, URL scanning, and content analysis further bolsters the defense. This ensures a layered approach that proactively identifies and prevents the delivery of suspicious emails.
User Awareness Training
Educating employees about phishing tactics is a critical component of a robust security posture. Regular training programs should cover various phishing techniques, enabling employees to identify and report suspicious emails effectively. This proactive measure equips employees with the knowledge and tools to resist social engineering attacks.
- Simulated Phishing Campaigns: Regular simulated phishing campaigns are vital for testing user awareness and identifying vulnerabilities in employee training. These campaigns provide a safe environment to practice identifying phishing emails, and the results can be used to refine training materials. A feedback loop ensures continuous improvement in user awareness.
- Comprehensive Training Modules: Training materials should be comprehensive, covering various types of phishing attacks, including spear phishing, whaling, and CEO fraud. Training should also include practical exercises and examples to demonstrate how to recognize suspicious emails and the importance of reporting them immediately.
Security Technology Summary
The table below summarizes various security technologies and their effectiveness in detecting and blocking phishing emails. It provides a comparative overview of different solutions and their potential to mitigate threats.
| Security Technology | Detection Capabilities | Blocking Capabilities | Effectiveness |
|---|---|---|---|
| Advanced Threat Protection (ATP) | High | High | Excellent |
| Spam Filters | Moderate to High | Moderate to High | Good |
| Anti-Phishing Tools | High | High | Excellent |
| Multi-Factor Authentication (MFA) | N/A | High | Excellent |
Multi-Factor Authentication and Password Policies
Multi-factor authentication (MFA) adds an extra layer of security by requiring multiple verification methods. This significantly reduces the risk of unauthorized access, even if a password is compromised. Secure password policies, including complexity requirements and regular password changes, also contribute to a robust security framework.
- Multi-Factor Authentication (MFA): Implementing MFA across all critical systems is essential to prevent unauthorized access. This mandates users to provide multiple forms of verification, making it harder for attackers to gain access, even with compromised credentials. This proactive measure strengthens the security posture.
- Strong Password Policies: Enforcing strong password policies, including minimum length, complexity requirements, and regular password changes, is crucial. These policies minimize the risk of password breaches, significantly reducing the potential impact of a successful phishing attack.
Incident Response Plan
A robust incident response plan is crucial for healthcare organizations like UnityPoint Health to mitigate the impact of cyberattacks and ensure business continuity. A well-defined plan Artikels procedures for detecting, containing, eradicating, recovering, and learning from security incidents. This plan acts as a roadmap for swift and coordinated action during a crisis, minimizing damage and maximizing the chances of a swift recovery.A comprehensive incident response plan details the steps necessary to handle a cyberattack effectively.
This includes clear roles and responsibilities for personnel, specific procedures for containment and eradication, and mechanisms for communication and reporting. This plan needs to be regularly reviewed and updated to reflect evolving threats and technological advancements.
Incident Response Team Structure
A dedicated and well-trained incident response team is paramount. This team should consist of personnel with diverse skills and experience, capable of handling different aspects of an incident. A rapid and effective response is critical, minimizing the time it takes to detect, contain, and eradicate a threat.
- The incident response team should be multi-disciplinary, encompassing information security, IT operations, legal, and public relations personnel. This ensures a holistic approach to the crisis, addressing various facets of the incident.
- Roles and responsibilities within the team should be clearly defined and documented. This ensures accountability and minimizes ambiguity during a crisis. For example, a dedicated incident commander should be designated to direct and oversee the response efforts.
- Team members should be trained regularly on incident response procedures, best practices, and emerging threats. This includes simulating real-world scenarios to enhance their preparedness and refine their responses.
Key Personnel and Roles
A clear delineation of roles and responsibilities for key personnel is essential. This ensures accountability and avoids confusion during a crisis.
| Personnel | Role |
|---|---|
| Incident Commander | Oversees and directs the incident response activities, ensuring coordination among all involved parties. |
| Security Analyst | Identifies and assesses the scope and impact of the incident, providing technical expertise. |
| Network Administrator | Contains the attack by isolating compromised systems, and restoring essential services. |
| Legal Counsel | Provides legal guidance and advice regarding compliance and regulatory requirements. |
| Public Relations | Manages communication with external stakeholders, addressing any concerns and maintaining public trust. |
| IT Operations | Supports the recovery process by restoring critical systems and data. |
Incident Response Plan Template
A template for an incident response plan should be comprehensive and adaptable. It should cover all potential scenarios, from phishing attacks to ransomware attacks.
“A well-structured plan includes procedures for incident detection, containment, eradication, recovery, and lessons learned. It should detail the roles and responsibilities of personnel, communication protocols, and escalation procedures.”
The template should include sections on:
- Incident Detection and Analysis: Procedures for identifying and analyzing security incidents, including indicators of compromise.
- Incident Containment: Strategies for isolating affected systems and preventing further damage.
- Incident Eradication: Methods for removing the threat and restoring affected systems.
- Recovery and Restoration: Processes for recovering data and restoring systems to their pre-incident state.
- Post-Incident Activities: Actions for evaluating the response, identifying improvements, and preventing future incidents.
Final Wrap-Up
The email phishing scam targeting UnityPoint Health underscores the critical need for enhanced cybersecurity measures within the healthcare sector. Robust security protocols, user awareness training, and a proactive incident response plan are essential to protect sensitive patient data and maintain public trust. This incident will hopefully spark broader conversations and encourage the adoption of best practices to safeguard against future attacks.
Popular Questions
What types of data were potentially compromised?
The attack potentially targeted patient records, financial information, and other confidential details. The specific data compromised depends on the success of the attack.
What steps can UnityPoint Health take to prevent future attacks?
Implementing stronger email security protocols, providing more comprehensive user awareness training, and investing in advanced cybersecurity technologies are key preventative measures.
How can individuals protect themselves from phishing scams?
Be cautious of unsolicited emails, verify sender addresses, avoid clicking suspicious links, and report any suspicious activity to the appropriate authorities.
What is the importance of a rapid and effective incident response team?
A swift response to a cyberattack is crucial to minimize damage, contain the spread, and implement effective remediation strategies.