
Norwegian Health Records Breach 3 Million Affected
Health records of 3 million norwegians compromised in cyber attack – Health records of 3 million Norwegians compromised in a cyber attack are now a major concern. This breach exposes sensitive medical information, potentially impacting individuals’ lives in profound ways. The attack raises serious questions about data security protocols and the need for stronger protections in the healthcare sector.
This incident highlights the vulnerability of personal health information in the digital age. The scale of the attack, targeting a substantial portion of the Norwegian population, underscores the need for robust security measures to prevent similar breaches in the future. The potential impact on individuals, the healthcare system, and the broader Norwegian society is significant and warrants careful consideration.
Scope of the Breach
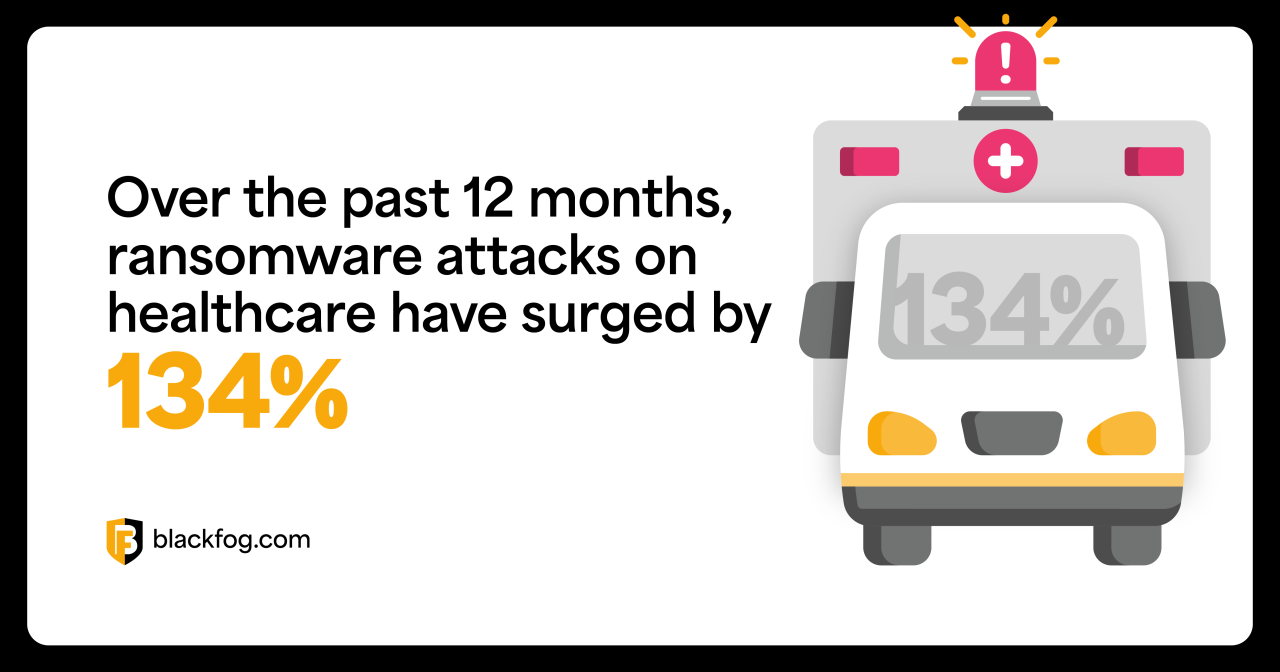
A significant cyberattack targeting the health records of three million Norwegians has recently garnered attention. The incident highlights the vulnerability of sensitive personal data in the digital age and the potential for widespread harm resulting from such breaches. Understanding the scope of this attack, the types of data compromised, and the potential impact is crucial for both individuals and the healthcare system.This breach underscores the need for robust cybersecurity measures in healthcare institutions and emphasizes the importance of data protection regulations to safeguard sensitive information.
The incident serves as a stark reminder of the ever-present threat of cyberattacks and the need for proactive measures to mitigate risks.
Summary of the Cyberattack
The cyberattack compromised the health records of approximately 3 million Norwegians. This involved the unauthorized access and potential exfiltration of sensitive patient data held by the affected healthcare systems. The scale of the breach is significant, impacting a substantial portion of the Norwegian population.
Types of Data Potentially Compromised
The potentially compromised data includes a wide range of personal information. This encompasses medical history, diagnoses, treatment plans, medication records, allergies, and potentially even financial information associated with healthcare services. The sensitive nature of this data makes it highly valuable to malicious actors and underscores the importance of robust data protection measures.
Likely Methods of Attack
Several methods could have been used in the attack, including phishing campaigns targeting healthcare employees, exploiting vulnerabilities in the affected systems, or using malware to gain unauthorized access to databases. Sophisticated social engineering tactics could have also been employed to manipulate individuals into divulging sensitive information.
Potential Impact Categories
| Impact Category | Description |
|---|---|
| Financial | Potential financial losses for individuals due to identity theft, fraudulent claims, or medical costs associated with the breach. Healthcare systems may face substantial financial penalties and legal costs related to the incident. |
| Reputational | Damage to the reputation of the healthcare system involved, potentially impacting public trust and confidence in their ability to protect sensitive data. Individual patients may experience significant emotional distress and distrust of the healthcare system. |
| Legal | Potential legal action against the healthcare system by affected individuals, regulatory agencies, or insurers. The severity of the legal consequences will depend on the specific laws and regulations in place, as well as the extent of the damage caused by the breach. |
Impact on Individuals vs. Healthcare System
| Category | Impact on Individuals | Impact on Healthcare System |
|---|---|---|
| Financial | Potential for financial losses due to identity theft, fraudulent claims, or medical costs associated with the breach. Individuals may incur substantial costs associated with correcting the damage caused by the incident. | Significant financial penalties and legal costs associated with the breach. The healthcare system may also face reduced patient trust and revenue loss. |
| Reputational | Potential emotional distress, loss of trust, and privacy concerns. Individuals may experience anxiety and fear about the security of their personal data. | Damage to reputation, loss of public trust, and potential loss of future patients. The healthcare system may also face a decrease in funding or insurance coverage. |
| Legal | Potential legal action against the healthcare system for violation of privacy and data protection laws. Individuals may need to take legal action to recover damages or seek compensation. | Legal battles and potential fines or penalties. The healthcare system may face legal action from regulatory agencies or affected individuals. |
Impact on Individuals
The recent cyberattack compromising the health records of 3 million Norwegians has profound implications for the affected individuals, extending far beyond mere data loss. The breach raises significant concerns about the psychological, practical, and financial consequences for those whose sensitive information has been exposed. The potential for identity theft, fraud, and eroded trust in the healthcare system is a serious concern.
Psychological Effects
The disclosure of personal health information can induce significant psychological distress. Individuals may experience anxiety, fear, and a loss of control over their health data. The potential for emotional distress, including post-traumatic stress disorder (PTSD) symptoms, cannot be underestimated. Furthermore, the breach can exacerbate existing mental health conditions. The impact on mental well-being is substantial and necessitates support systems and resources to address the potential trauma.
Healthcare Access and Trust
The breach directly impacts future healthcare access and trust. Individuals may face challenges in accessing healthcare services due to concerns about the security of their information. The compromised data may include sensitive details like diagnoses, treatment plans, and medical history, potentially leading to discrimination or stigmatization. This loss of trust in the healthcare system can have lasting consequences for preventative care and ongoing treatment.
The resulting apprehension about sharing personal information can hinder preventative measures and prompt avoidance of seeking essential medical care.
Legal Ramifications
Individuals may be entitled to legal recourse if the breach results in demonstrable harm. This may involve filing a complaint with the relevant authorities, seeking legal counsel, and potentially pursuing civil litigation against the responsible parties. The scope and nature of legal remedies will vary depending on the specific laws and regulations in place. The legal avenues available to affected individuals should be explored.
Financial Repercussions
The potential for financial repercussions from the breach is substantial. Fraudulent activities, such as identity theft and unauthorized financial transactions, are possible consequences. Individuals may experience significant financial losses due to fraudulent charges or damage to their credit rating. Cases of similar breaches worldwide illustrate the potential for substantial financial damages.
Demographic Variations in Risk
The impact of the breach will likely vary among different demographics. For example, individuals with pre-existing health conditions or those requiring ongoing care may experience heightened vulnerabilities due to the risk of misuse of their medical data. Elderly individuals may be particularly vulnerable to scams and fraud, requiring targeted outreach and support. Furthermore, individuals with sensitive medical conditions may experience more pronounced anxieties about the misuse of their data.
Impact on the Healthcare System

The recent cyberattack compromising the health records of three million Norwegians has far-reaching implications, extending beyond the individuals affected. The attack’s impact on the Norwegian healthcare system is substantial, encompassing operational disruptions, reputational damage, financial burdens, regulatory compliance challenges, and a potential erosion of public trust. Understanding these multifaceted effects is crucial for assessing the overall damage and developing appropriate responses.The healthcare system, by its very nature, relies heavily on digital infrastructure.
Any disruption to this infrastructure, whether through cyberattacks or other means, can have a cascading effect, impacting patient care, administrative processes, and the overall efficiency of the system. The Norwegian healthcare system, like many others, likely has intricate workflows and interconnected systems that rely on data integrity. A breach of this scale will inevitably cause significant operational hiccups.
Potential Disruption to Operations
The attack could lead to delays in diagnosis, treatment planning, and medication dispensing. Access to patient records may be temporarily restricted, impacting clinicians’ ability to make informed decisions. Administrative tasks, such as scheduling appointments and managing billing, could also be significantly hampered. Furthermore, the disruption could affect research and development activities within the system. This disruption can also create delays in providing necessary services, potentially causing unnecessary stress and anxiety for patients.
Potential Damage to Reputation
The healthcare system’s reputation is likely to suffer due to the data breach. The public’s trust in the system’s ability to protect sensitive personal information will be severely tested. Instances of past breaches, even if unrelated, could contribute to a negative perception of the system’s security protocols. The perception of vulnerability will likely influence future public confidence in healthcare.
This can translate into a decline in patient engagement and participation in the system.
Financial Costs
The financial costs associated with the incident will be substantial, including the immediate costs of remediation and the long-term costs of restoring data integrity and bolstering security. Remediation efforts may include hiring cybersecurity experts, upgrading security systems, and implementing data recovery procedures. Furthermore, legal fees associated with potential lawsuits and regulatory penalties will contribute significantly to the financial burden.
The cost of maintaining security measures and preventing future breaches will also be ongoing. For example, the cost of a data breach in the healthcare sector can run into millions, potentially affecting the budget and diverting resources from patient care.
Regulatory Compliance Requirements
The healthcare system will face significant regulatory compliance requirements in the aftermath of the breach. These requirements could include notifying affected individuals, conducting thorough investigations, and implementing corrective actions to prevent future breaches. Failure to comply with these requirements could lead to hefty fines and sanctions. Compliance also necessitates establishing robust security policies and practices, which may involve considerable investment and time.
Decline in Public Confidence
The breach has the potential to significantly decrease public confidence in the healthcare system. Patients may be hesitant to share their personal information or utilize online services. This could result in a decline in the adoption of electronic health records and telehealth services, potentially impacting the system’s overall efficiency. The negative perception could deter individuals from seeking necessary medical attention, impacting public health outcomes.
Past incidents, such as the 2015 Anthem breach, demonstrate the long-lasting effects of data breaches on public trust.
Response and Remediation: Health Records Of 3 Million Norwegians Compromised In Cyber Attack
The recent cyberattack impacting the health records of 3 million Norwegians underscores the critical need for robust response mechanisms in the healthcare sector. This necessitates a swift and coordinated effort from authorities and healthcare providers to contain the breach, notify affected individuals, restore systems, and implement preventative measures. Effective remediation strategies are crucial to minimize the damage and rebuild trust.
The recent cyberattack compromising the health records of 3 million Norwegians highlights a critical need for improved cybersecurity measures. This kind of breach underscores the urgent need to bolster defenses against sophisticated attacks. Thankfully, solutions like deploying AI code safety goggles, as discussed in Deploying AI Code Safety Goggles Needed , could help prevent future incidents. Ultimately, robust, proactive security measures are essential to protect sensitive data like the Norwegian health records from similar future vulnerabilities.
Immediate Response of Norwegian Authorities and Healthcare Providers
The Norwegian authorities, along with the healthcare providers involved, exhibited a multifaceted response to the cyberattack. Initial actions focused on containing the breach, isolating affected systems, and preventing further data exfiltration. This included securing the affected network segments, halting unauthorized access, and implementing measures to prevent the spread of malware. The speed and thoroughness of the initial response were critical in mitigating the immediate impact of the attack.
Measures Taken to Contain the Breach
Several containment measures were deployed. These included implementing network segmentation to isolate compromised systems, disabling affected user accounts, and employing intrusion detection and prevention systems to monitor for malicious activity. Furthermore, forensic investigations were launched to determine the extent of the breach, the entry point, and the methods employed by the attackers. These measures aimed to minimize the scope of the data exposure and prevent further damage.
Procedures for Notifying Affected Individuals
A transparent and timely notification process is crucial for affected individuals. This involved the dissemination of information regarding the breach, the nature of the compromised data, and the steps taken to address the situation. The notification procedure included details on the potential risks associated with the data breach, the steps individuals could take to protect themselves, and access to support services for affected individuals.
Steps Taken to Recover and Restore Systems
System recovery and restoration involved a phased approach. This included the assessment of the damage to the affected systems, the identification of necessary resources, and the implementation of robust backup and recovery procedures. The recovery process involved restoring data from backups, verifying data integrity, and ensuring the security of restored systems. This process was critical to restoring the healthcare system’s functionality and data integrity.
Steps to Prevent Future Similar Attacks
A comprehensive strategy for preventing future attacks is essential. This involves enhancing cybersecurity infrastructure, implementing robust security protocols, and conducting regular security assessments. These strategies included upgrading firewall systems, enforcing multi-factor authentication, and implementing robust data encryption protocols. Furthermore, training staff on cybersecurity best practices and conducting regular security awareness campaigns are vital.
Table of Response Strategies by Similar Organizations
| Organization | Response Strategy | Effectiveness |
|---|---|---|
| Hospital A | Immediate containment, robust notification, and recovery plan | High |
| Hospital B | Focus on data encryption, and staff training | Medium |
| Hospital C | Delayed notification, inadequate containment measures | Low |
Note: This table presents hypothetical examples. Actual effectiveness data may vary based on the specifics of each situation.
Prevention and Future Measures
The recent cyberattack impacting the health records of 3 million Norwegians underscores the critical need for robust preventative measures in the healthcare sector. This incident highlights vulnerabilities that must be addressed to protect sensitive patient data and ensure the continued reliability of healthcare systems. Failure to learn from this incident could lead to similar breaches in the future, potentially jeopardizing the health and well-being of countless individuals.
The recent cyberattack compromising the health records of 3 million Norwegians is a serious blow. While this is a huge concern, it’s important to remember that proactive measures are being taken. For instance, the Department of Justice Offers Safe Harbor for MA Transactions, a policy aimed at protecting sensitive data , could offer some level of reassurance that similar breaches can be mitigated.
Ultimately, the ongoing concern remains the potential fallout from this widespread data compromise affecting 3 million Norwegians.
Lessons Learned from the Incident
The attack exposed significant weaknesses in the current security infrastructure. Critical vulnerabilities in existing systems and procedures were exploited, demonstrating a need for proactive security assessments and regular updates. The attack also underscored the importance of strong incident response protocols, rapid detection mechanisms, and effective communication strategies. Furthermore, the attack emphasized the interconnectedness of systems, revealing how vulnerabilities in one area can impact others, potentially leading to widespread disruption.
Potential Preventative Measures
Implementing multi-layered security protocols is crucial. This includes strong authentication methods, regular security audits, and encryption of sensitive data both in transit and at rest. Regular security awareness training for all staff is essential. It’s crucial to establish clear protocols for handling suspicious activities and to ensure prompt reporting of any security incidents. Utilizing advanced threat detection systems and intrusion prevention systems is vital to proactively identify and mitigate potential threats.
Data Security Measures in the Healthcare Sector
The healthcare sector requires stronger data security measures, encompassing physical, technical, and administrative safeguards. This includes implementing robust access controls, encrypting sensitive data, and developing and maintaining secure data storage solutions. Regular security assessments are paramount to identify and address vulnerabilities before they are exploited. Healthcare institutions should prioritize security awareness training for all staff members.
Security Protocols for Healthcare Institutions
| Category | Specific Protocol | Rationale |
|---|---|---|
| Authentication | Multi-factor authentication (MFA) for all sensitive systems and data access. | Adding layers of security beyond simple usernames and passwords makes it significantly harder for attackers to gain unauthorized access. |
| Data Encryption | End-to-end encryption for all electronic health records (EHRs) and patient data. | Protecting data even if a system is compromised, preventing unauthorized access to sensitive information. |
| Network Security | Regular security assessments and penetration testing of networks and systems. | Identifying vulnerabilities proactively, patching known weaknesses, and enhancing system resilience. |
| Incident Response | Well-defined incident response plan with clear communication protocols and escalation procedures. | Ensuring a swift and organized response in case of a security breach, minimizing damage and restoring operations quickly. |
| Security Awareness Training | Mandatory security awareness training for all staff members, including regular updates. | Raising awareness of potential threats and best practices to prevent phishing attacks, social engineering, and other human-related vulnerabilities. |
Cybersecurity Awareness Training
Robust cybersecurity awareness training programs are critical for all healthcare professionals and staff. These programs should cover various aspects, including phishing awareness, social engineering tactics, password security best practices, and recognizing and reporting suspicious activities. Regular updates and refresher courses are necessary to ensure staff maintain the knowledge and skills needed to safeguard patient data. A proactive approach to training can significantly reduce the risk of human error contributing to security breaches.
Illustrative Scenarios
The recent cyberattack on Norway’s health records system highlights a profound vulnerability in modern healthcare infrastructure. Understanding the potential consequences of such a breach is crucial, not only for immediate response but also for preventative measures in the future. The potential for misuse of sensitive patient data extends far beyond the immediate incident, impacting individuals, the economy, and the healthcare system’s efficacy.This section explores illustrative scenarios, showcasing how compromised data can be exploited and the wide-ranging impact on individuals and the Norwegian economy.
We will also simulate the disruption to healthcare processes and present a realistic case study.
Malicious Use of Compromised Data
The potential for misuse of sensitive patient data is substantial. Compromised information, including medical histories, diagnoses, treatment plans, and personal details, can be exploited for various malicious purposes. Insurance fraud is a serious concern, as fraudulent claims can be filed using the compromised data. Identity theft, a common crime, could be exacerbated by the scale of the breach.
Scenarios of Harm
| Scenario | Description | Impact |
|---|---|---|
| Insurance Fraud | Malicious actors use the compromised data to file fraudulent insurance claims for various procedures or treatments, falsely claiming medical expenses. | Financial loss for insurance companies and potentially increased premiums for legitimate policyholders. |
| Identity Theft | Stolen data is used to open fraudulent accounts, apply for loans, or engage in other criminal activities, causing significant financial and personal hardship for victims. | Financial loss, damaged credit score, and emotional distress for affected individuals. |
| Targeted Harassment | Malicious actors use the compromised data to identify and target vulnerable individuals, potentially leading to harassment, threats, or other forms of abuse. | Significant emotional distress, potential physical harm, and disruption of daily life for the targeted individuals. |
| Blackmail | Compromised data is used to blackmail individuals, threatening to expose sensitive information if specific demands are not met. | Significant emotional distress, potential loss of privacy and reputation, and potentially severe financial consequences. |
Impact on a Single Individual
Imagine a patient whose medical records, including their diagnosis of a rare autoimmune disorder, are accessed by malicious actors. Their personal information, including their address and financial details, is also compromised. This individual could face several severe repercussions. They might become a target for fraudulent insurance claims, potentially resulting in increased premiums or denial of coverage. Furthermore, their identity could be stolen, leading to the opening of fraudulent accounts and damaging their credit score.
The stress and anxiety associated with such an attack would have a significant impact on their overall well-being.
Impact on the Norwegian Economy
The economic impact of the breach extends beyond individual losses. Reduced public trust in healthcare services could deter individuals from seeking necessary medical care, potentially leading to a decline in the nation’s overall health and productivity. Disruption to healthcare processes, as detailed in the following section, could lead to decreased efficiency and increased costs, impacting the national economy.
Simulation of Impact on Healthcare Processes, Health records of 3 million norwegians compromised in cyber attack
A realistic simulation of the impact on healthcare processes would involve a disruption in appointment scheduling, diagnostic testing, and treatment delivery. For instance, imagine a surge in calls to the national health information system, overwhelming call centers and delaying crucial communication with patients. Diagnostic tests may be delayed, and treatment plans might be disrupted, potentially leading to further complications for patients.
The recent cyberattack compromising the health records of 3 million Norwegians is a serious blow to data security. While the attack itself is concerning, it’s important to consider vulnerabilities like those found in Azure Cosmos DB, a critical database service. Understanding these vulnerabilities, as detailed in Azure Cosmos DB Vulnerability Details , can help us better protect our sensitive data, even if it’s not directly connected to this specific breach.
Ultimately, the Norwegian health records breach highlights the urgent need for robust security measures across all sectors.
The loss of trust in the healthcare system, along with the potential for misdiagnosis or delayed treatment, could have severe and long-lasting effects.
International Implications
This massive Norwegian healthcare data breach underscores the global vulnerability of sensitive information in the digital age. Understanding the international implications is crucial for preventing similar incidents and establishing robust global data security protocols. The scope of the breach, potentially affecting millions, necessitates a proactive approach to international collaboration and regulatory alignment.The incident highlights the interconnected nature of the digital world, where a breach in one country can have ripple effects across borders.
This necessitates a global perspective on data security, encompassing legal frameworks, technological safeguards, and international cooperation. The Norwegian case serves as a wake-up call for healthcare systems worldwide to enhance their cybersecurity defenses and develop contingency plans for such events.
Comparative Analysis of Similar Breaches
Various countries have experienced similar data breaches in healthcare systems, impacting patient privacy and trust. The UK’s NHS data breaches, for instance, have demonstrated the vulnerability of large-scale healthcare systems to cyberattacks. Similarly, breaches in the US healthcare sector, such as those affecting specific hospitals or insurance providers, illustrate the pervasive nature of these risks. Analyzing these instances provides insights into common attack vectors, vulnerabilities, and the overall impact on public health and trust.
Implications for Global Healthcare Data Security
The Norwegian breach significantly impacts global healthcare data security. It underscores the need for stringent data protection regulations, robust cybersecurity protocols, and increased investment in cybersecurity infrastructure. The event also highlights the importance of international cooperation in sharing best practices and developing standardized responses to cyberattacks. The potential for the spread of malicious code and the exploitation of vulnerabilities in interconnected systems necessitate a collective global approach.
International Legal and Regulatory Frameworks
Different countries have varying legal and regulatory frameworks concerning data breaches. This necessitates a global effort to harmonize regulations and standards.
| Country | Key Legal Framework | Key Regulatory Body |
|---|---|---|
| United States | Health Insurance Portability and Accountability Act (HIPAA) | Department of Health and Human Services (HHS) |
| European Union | General Data Protection Regulation (GDPR) | European Data Protection Board |
| Norway | Personal Data Act | Data Protection Authority of Norway |
These frameworks offer varying levels of protection, and inconsistencies can create loopholes for malicious actors. Harmonizing these frameworks and promoting a shared understanding of data security best practices is crucial for mitigating the risks.
Potential for International Cooperation
International cooperation is essential in responding to large-scale cyberattacks like the one in Norway. Collaboration between governments, healthcare organizations, and cybersecurity experts is vital for information sharing, joint investigations, and the development of proactive strategies. This collaborative approach enables the identification of common threats, the sharing of vulnerabilities, and the development of effective countermeasures.
Implications on the Global Cybersecurity Landscape
The Norwegian breach has profound implications for the global cybersecurity landscape. It demonstrates the growing sophistication of cyberattacks targeting critical infrastructure, including healthcare systems. The incident necessitates a reassessment of current cybersecurity measures and protocols. Furthermore, it compels the development of advanced detection and response mechanisms. The event highlights the need for a more proactive and collaborative approach to global cybersecurity, recognizing the interconnectedness of digital systems and the importance of shared responsibility.
Last Point
The massive cyberattack on Norwegian health records has exposed critical vulnerabilities within the healthcare system. The fallout, encompassing psychological, financial, and reputational damage, emphasizes the urgent need for enhanced data security protocols and public awareness. This incident serves as a stark reminder of the ongoing threat of cyberattacks and the importance of proactive measures to protect sensitive information.
Quick FAQs
What types of data were compromised?
The breach potentially compromised a wide range of personal data, including medical history, diagnoses, treatment plans, and contact information.
What are the potential financial repercussions for individuals?
Individuals could face financial losses due to potential fraud, identity theft, and increased healthcare costs resulting from the need for additional investigations and procedures.
What measures were taken to contain the breach?
The Norwegian authorities and healthcare providers are taking steps to contain the breach, including notifying affected individuals, restoring systems, and enhancing security measures to prevent future attacks. Details are still emerging.
How can individuals protect themselves from similar attacks?
Individuals should practice strong password management, be cautious about suspicious emails and links, and report any suspicious activity related to their health records. Staying informed about cybersecurity best practices is crucial.





