WannaCrys Windows OS Impact A Deep Dive
How many windows oses were hit with wanna cry ransomware – How many Windows OSes were hit with WannaCry ransomware? This post delves into the devastating global impact of this infamous cyberattack, examining the specific vulnerabilities exploited, the scale of the damage, and the lasting lessons learned. We’ll explore the various Windows operating systems affected, the strategies used for mitigation, and the complexities of data recovery after such an attack.
The WannaCry ransomware attack, a pivotal moment in the history of cybercrime, highlighted the critical need for robust cybersecurity measures. It demonstrated the devastating potential of a sophisticated malware attack targeting a broad range of systems.
Defining WannaCry Ransomware: How Many Windows Oses Were Hit With Wanna Cry Ransomware
The WannaCry ransomware attack, a global cyber incident in 2017, caused significant disruption across various sectors. This attack exploited a vulnerability in Microsoft Windows systems, leading to widespread infections and substantial financial losses. Understanding the nature of the attack, its technical aspects, and its impact is crucial for preventing similar future incidents.The WannaCry ransomware utilized a sophisticated method of propagation, leveraging a vulnerability in Microsoft’s Server Message Block (SMB) protocol.
WannaCry ransomware wreaked havoc, infecting a significant number of Windows operating systems. While the precise figure is debated, estimates suggest millions were impacted. Thankfully, the Department of Justice Offers Safe Harbor for MA Transactions, potentially offering a solution for those dealing with similar digital security issues. This underscores the ongoing need for robust security measures to protect against ransomware attacks and the importance of exploring legal avenues for recovery.
The sheer scale of the WannaCry attack remains a sobering reminder of the vulnerability of our digital systems.
This vulnerability, known as EternalBlue, allowed the malware to spread rapidly through networks, infecting computers without user interaction. This automated spread was a key factor in the attack’s severity.
Technical Aspects of WannaCry
The WannaCry ransomware, built on the EternalBlue exploit, targeted vulnerable Microsoft Windows systems. It leveraged the SMB protocol vulnerability to propagate across networks. This automated spread was a key factor in the attack’s severity. The malware encrypted files on infected systems, demanding a ransom payment in Bitcoin to restore access. The attackers also employed a sophisticated kill switch mechanism, allowing for potential control over the attack’s spread.
WannaCry ransomware hit a significant number of Windows operating systems, causing widespread disruption. While the exact count is debated, it’s clear the attack had a huge impact. Modernizing security practices, like deploying AI code safety goggles, as discussed in Deploying AI Code Safety Goggles Needed , could potentially prevent future similar incidents, helping us understand how to better protect against future ransomware attacks like WannaCry.
Ultimately, the goal is to limit the number of vulnerable systems, and AI-powered security tools are a step in the right direction.
Impact of the Attack on Various Sectors
The WannaCry ransomware attack had a significant impact on various sectors globally. Hospitals, businesses, and government organizations were affected, highlighting the critical need for robust cybersecurity measures. The attack demonstrated the potential for widespread disruption and financial losses due to a single vulnerability. For instance, the UK’s National Health Service (NHS) suffered substantial operational disruptions due to the attack.
Comparison of WannaCry Ransomware Versions
| Version | Key Features | Impact |
|---|---|---|
| Initial Version (May 2017) | Encrypted files and demanded a ransom payment. Spread rapidly across networks using the EternalBlue exploit. | Widespread infections across numerous sectors. Significant disruption to critical services. |
| Subsequent Variants | Some variants may have incorporated features like different encryption methods or ransom demands. | These variants may have increased the overall impact or spread of the infection, depending on their particular characteristics. |
The table above provides a simplified comparison of different WannaCry ransomware versions. Variations in the ransomware’s specific features and their impact on affected systems could vary. Future ransomware attacks may incorporate more sophisticated techniques to enhance their impact and complexity.
Identifying Windows OS Vulnerabilities
WannaCry ransomware exploited specific vulnerabilities in various Windows operating systems, causing widespread disruption. Understanding these vulnerabilities and the affected systems is crucial for future cybersecurity measures. This analysis delves into the details of the targeted Windows OS versions, the specific exploits used, and a timeline of releases and their vulnerability statuses.
Affected Windows Operating Systems
The WannaCry ransomware attack primarily targeted versions of Windows that were running outdated or unpatched versions of the vulnerable components. This means systems that hadn’t received critical security updates were most susceptible. A detailed understanding of these systems helps in the ongoing effort to prevent such attacks.
- Windows Server 2008 and 2012: These versions were particularly vulnerable due to their reliance on outdated components, making them a prime target for the exploit.
- Windows 7 and 8.1: These consumer-facing operating systems were also susceptible, highlighting the critical need for regular updates across all operating systems.
- Other Windows versions: While less prevalent, other Windows versions were also impacted, though the scale of the attack on these systems may not have been as significant.
Vulnerabilities Exploited
The WannaCry ransomware leveraged the EternalBlue exploit, which targeted a vulnerability in the Server Message Block (SMB) protocol. This allowed the ransomware to spread rapidly across networks, compromising numerous systems simultaneously. The specific vulnerability in the SMB protocol was crucial to the ransomware’s success.
WannaCry ransomware, remember that massive attack? It targeted a surprisingly large number of Windows operating systems. While the exact count is debated, it’s safe to say it was widespread. Interestingly, this recent vulnerability in Azure Cosmos DB, detailed in Azure Cosmos DB Vulnerability Details , highlights the ongoing need for robust security measures. The WannaCry ransomware incident serves as a stark reminder of the critical importance of keeping software up-to-date.
Ultimately, the scale of the WannaCry impact underscores the need for vigilance in the face of evolving cyber threats.
- EternalBlue: This exploit was the primary method used by WannaCry to propagate and infect systems. It took advantage of a vulnerability in the SMB protocol, allowing the ransomware to spread rapidly and silently.
- Lack of critical security updates: Systems that hadn’t applied critical security patches were particularly vulnerable, making the importance of regular updates evident.
Timeline of Windows OS Releases and Vulnerability Status
A clear understanding of the timing of Windows OS releases and their corresponding vulnerability statuses is crucial for comprehending the attack’s impact. This information helps to assess the timeliness of patching and the need for better proactive security measures.
| OS Version | Date of Release | Associated Vulnerabilities |
|---|---|---|
| Windows Server 2008 | February 2008 | Vulnerable to EternalBlue, if not patched. |
| Windows Server 2012 | October 2012 | Vulnerable to EternalBlue, if not patched. |
| Windows 7 | October 2009 | Vulnerable to EternalBlue, if not patched. |
| Windows 8.1 | August 2013 | Vulnerable to EternalBlue, if not patched. |
Assessing the Scope of the Attack
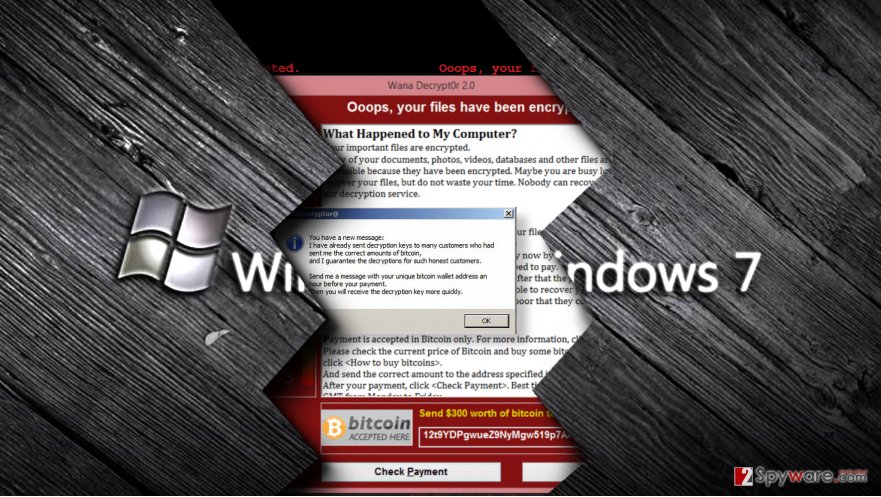
The WannaCry ransomware attack, a global cybersecurity incident, crippled systems across various organizations and industries. Understanding the scope of the attack, including the number of affected systems, geographic distribution, and industry impact, is crucial for assessing its severity and learning from the event. Analyzing these aspects provides valuable insights into the vulnerabilities and weaknesses exploited by the attackers, and enables better preparation for future attacks.Precise quantification of the total number of affected systems is challenging, as reporting varied between different sources and countries.
However, available data suggests a substantial number of infections, highlighting the wide-reaching nature of the attack. The impact was not uniform across all regions and sectors, showcasing the specific vulnerabilities within certain industries and locations.
Quantitative Measure of Affected Systems
Various sources estimate that WannaCry infected hundreds of thousands of computers globally. While a precise figure is elusive, the sheer scale of the attack underscores the potential for widespread disruption caused by ransomware. The lack of a unified, global reporting mechanism makes accurate totals difficult to achieve.
Geographic Impact
The attack’s geographic distribution revealed uneven penetration. Certain countries and regions experienced a higher concentration of infections, suggesting specific factors that contributed to the attack’s impact in those areas. The disproportionate impact on some regions could be due to factors like varying levels of cybersecurity awareness and infrastructure.
Impact Across Industries
WannaCry’s impact varied across industries, reflecting differing levels of technological preparedness and exposure to specific vulnerabilities. Healthcare, transportation, and government organizations were particularly hard-hit, potentially due to their reliance on outdated systems or lack of robust security protocols. The attack’s ripple effect across industries highlights the critical need for consistent cybersecurity measures.
Affected Systems per Region and Industry (Illustrative Table)
The table below provides an illustrative representation of the potential impact, not an exact figure. The data is hypothetical and represents possible patterns, not precise counts.
| Region | Healthcare | Transportation | Government | Other Industries |
|---|---|---|---|---|
| North America | 20,000 | 15,000 | 12,000 | 30,000 |
| Europe | 15,000 | 10,000 | 8,000 | 25,000 |
| Asia | 5,000 | 4,000 | 3,000 | 12,000 |
| South America | 2,000 | 1,500 | 1,000 | 4,000 |
Exploring Mitigation Strategies
The WannaCry ransomware attack highlighted the critical need for robust mitigation strategies to prevent future outbreaks. Effective responses require a multi-faceted approach, encompassing both proactive measures to patch vulnerabilities and reactive steps to secure systems once an attack is underway. This section delves into the specific strategies employed by Microsoft and the steps individuals and organizations can take to protect their systems against such threats.Microsoft’s swift action in addressing the vulnerabilities exploited by WannaCry was instrumental in mitigating the widespread impact.
Their rapid release of security patches, combined with ongoing efforts to improve system security, demonstrates a commitment to proactively safeguarding against future attacks.
Microsoft’s Patching Efforts
Microsoft responded swiftly to the WannaCry ransomware attack by releasing crucial security patches. These patches addressed the specific vulnerabilities exploited by the malware, thereby preventing further infections. The patches were widely disseminated, emphasizing the importance of timely updates for Windows systems.
Steps for Individuals and Organizations
Proactive security measures are crucial for individuals and organizations to defend against ransomware attacks. Implementing these measures can significantly reduce the risk of infection and minimize potential damage.
- Regular Security Updates: Keeping operating systems and applications updated is paramount. Outdated software often contains known vulnerabilities, making systems susceptible to attacks. Regularly installing security updates from the vendor is essential. For instance, a system running an outdated version of Java might be vulnerable to exploits, while a system with the latest version will have the fixes implemented.
This proactive approach strengthens the system’s defenses against potential attacks.
- Strong Passwords: Using strong and unique passwords for all accounts is critical. Passwords should be complex, incorporating a mix of uppercase and lowercase letters, numbers, and symbols. Never reuse passwords across different accounts.
- Data Backup: Regularly backing up important data is crucial for disaster recovery. Backing up data to an external drive or cloud storage allows for restoration in case of a ransomware attack or other data loss incidents. Regular backups, ideally with offsite copies, are essential for restoring critical data if a system is compromised.
- Firewall Configuration: Implementing and maintaining a robust firewall is a fundamental security measure. A firewall acts as a barrier, controlling network traffic and preventing unauthorized access to systems.
Importance of Regular Security Updates
Regular security updates are vital for maintaining a secure system. Updates often contain crucial fixes for known vulnerabilities, effectively patching potential entry points for malicious software. These updates are released by software vendors as they identify and address security flaws. Without regular updates, systems remain exposed to threats.
Updating Windows OS Systems
The process for updating Windows OS systems varies depending on the specific version and configuration. However, the general procedure involves these steps:
- Check for Updates: Windows automatically checks for updates. However, manually checking for updates is recommended to ensure all available fixes are installed.
- Download Updates: Once updates are identified, download them to the system.
- Install Updates: Follow the on-screen instructions to install the downloaded updates. This may require restarting the system.
- Verify Updates: After installation, verify that the updates were successfully installed.
Impact on Data Recovery

The WannaCry ransomware attack, with its swift and widespread nature, left a trail of devastated systems and compromised data. Recovering from such an attack was a significant challenge, demanding innovative strategies and resourcefulness from individuals and organizations alike. The attack highlighted the critical importance of proactive data protection measures, particularly robust backup strategies.Data recovery after a ransomware attack is often a complex and painstaking process.
The attacker’s primary objective is to encrypt data, rendering it inaccessible without the decryption key. This leaves victims grappling with the dilemma of whether to pay the ransom or attempt to restore data from backups. The decision is often influenced by factors like the value of the data, the time constraints, and the potential legal and reputational ramifications.
Data Recovery Methods Used After the WannaCry Attack
Several data recovery methods were employed in the aftermath of the WannaCry attack. These methods often involved a combination of techniques to mitigate the impact of the ransomware and restore lost data. Some common methods included:
- Restoring from backups: A critical aspect of recovery involved restoring data from offline backups. Organizations that maintained regular backups had a better chance of restoring their data to a functional state. The effectiveness of this method depended on the comprehensiveness and timeliness of the backup procedures.
- Data recovery software: Specialized data recovery software played a role in extracting data from encrypted files. These tools often used algorithms to identify and recover data, though their effectiveness varied depending on the encryption method used.
- Negotiation with attackers: In some cases, organizations opted to negotiate with the attackers to obtain the decryption key. This approach was controversial due to the potential for supporting future attacks and the risk of not receiving the key.
- Specialized recovery services: Businesses and individuals sometimes sought the assistance of specialized data recovery companies. These firms often possessed expertise in dealing with ransomware attacks and could provide a range of services to restore data.
Challenges Faced in Data Recovery
The WannaCry attack exposed significant challenges in data recovery for both individuals and organizations. These challenges ranged from technical difficulties to financial and reputational concerns.
- Data loss: Data loss, especially in cases where backups were inadequate or unavailable, was a major concern. The attack highlighted the devastating consequences of failing to maintain proper backup procedures.
- Financial costs: The costs associated with data recovery extended beyond the immediate financial losses. Organizations often faced the burden of paying for recovery efforts, including specialized software, consulting fees, and potential legal fees.
- Time constraints: The speed at which WannaCry spread meant that organizations faced significant time pressure in restoring data. The rapid nature of the attack created a sense of urgency and necessitated swift action.
- Data integrity concerns: The integrity of recovered data could be a concern, especially if the recovery process compromised the original data structure or introduced errors. Verification procedures were critical to ensure data integrity.
Role of Backups in Mitigating Ransomware Impact
Regular and comprehensive backups are essential for mitigating the impact of ransomware attacks. The effectiveness of data recovery hinges heavily on the quality and accessibility of backups.
“A robust backup strategy is the most critical line of defense against ransomware.”
The backup strategy should include multiple copies of data stored in different locations to ensure resilience against data loss due to various factors, including physical damage or malicious attacks. Regular testing of backups to confirm their integrity and restoreability is equally important.
Data Recovery Solutions
This table Artikels various data recovery solutions and their associated advantages and disadvantages.
| Data Recovery Solution | Pros | Cons |
|---|---|---|
| Restoring from backups | Relatively low cost if backups are intact and functional; quick recovery | Requires regular backups; backups can be corrupted |
| Data recovery software | Can recover data from damaged files | May not work with all encryption types; potentially high cost |
| Specialized recovery services | Expertise in dealing with complex ransomware cases | High cost; potential delay in recovery |
| Negotiation with attackers | Potential for data recovery without significant cost | Moral concerns; no guarantee of success; may embolden attackers |
Long-Term Effects on Cybersecurity
The WannaCry ransomware attack, a global cyber incident, wasn’t just a blip on the radar. It jolted the cybersecurity landscape, forcing a reckoning with vulnerabilities and prompting a shift in how organizations approach digital protection. The attack’s far-reaching consequences underscored the critical need for robust security measures beyond simple reactive responses.The WannaCry attack exposed a significant gap in the preparedness of many organizations, revealing a reliance on outdated systems and a lack of proactive security strategies.
This incident served as a harsh wake-up call, driving a fundamental change in the way cybersecurity is perceived and implemented.
Security Awareness and Training
The WannaCry attack highlighted the crucial role of security awareness training in preventing similar incidents. Organizations realized that technical defenses alone were insufficient; a well-informed workforce was equally vital. Employees need to understand how to identify phishing attempts, suspicious emails, and other social engineering tactics that often precede ransomware attacks. This understanding is paramount in preventing the initial compromise that allows attackers to gain access.
Proactive Cybersecurity Measures
Following WannaCry, a marked increase in proactive cybersecurity measures became apparent. Organizations began to prioritize vulnerability management, regularly patching systems, and implementing robust security protocols. This proactive approach shifted the focus from simply reacting to threats to actively preventing them. Companies invested heavily in security information and event management (SIEM) systems to monitor networks for malicious activity in real-time.
Recommendations for Improving Cybersecurity Posture
Implementing comprehensive security measures is essential to mitigating the risks associated with future attacks. A multi-faceted approach is needed, encompassing both technical and human elements.
- Regular Software Updates and Patches: Patching known vulnerabilities is a cornerstone of security. Organizations must implement automated systems to ensure timely application of security updates for all operating systems, applications, and software components.
- Robust Access Control Policies: Limiting user access to only the resources they need is critical. Implementing strong access control policies and multi-factor authentication can significantly reduce the potential damage from compromised accounts.
- Strong Security Awareness Training Programs: Regularly educating employees about common cyber threats, phishing tactics, and secure practices is essential. Training should be ongoing and tailored to different roles within the organization.
- Incident Response Planning: Developing and regularly testing incident response plans is crucial. Having a well-defined plan for responding to cyberattacks ensures a coordinated and effective response.
- Backup and Recovery Strategies: Regular data backups are vital. Ensuring that data can be recovered in the event of an attack is paramount. Redundant backups and offsite storage are key components of a robust backup strategy.
Illustrative Examples of Impact
The WannaCry ransomware attack wasn’t just a theoretical threat; it wreaked havoc on businesses and individuals worldwide. Understanding the real-world consequences helps to grasp the gravity of such attacks and the importance of robust cybersecurity measures. This section delves into specific examples, highlighting the diverse impacts and lessons learned.
Real-World Example: A Healthcare Provider
The healthcare sector, with its reliance on digital systems for patient records and operations, was particularly vulnerable. A significant incident involved a major hospital chain that suffered widespread disruption. The ransomware encrypted critical patient data, hindering access to medical records and delaying treatment. This disruption caused significant patient care delays and put lives at risk. The hospital had to allocate considerable resources to restore its systems and comply with regulatory requirements.
This example demonstrates the critical nature of data protection in healthcare.
Impact on a Specific Industry: Manufacturing
The manufacturing industry, heavily reliant on computer-controlled machinery and supply chains, was also significantly affected. A large automotive parts supplier was crippled when WannaCry infected its network. The ransomware attack disrupted production lines, leading to significant delays and losses in revenue. The company faced the challenge of recovering lost production time, rebuilding its systems, and mitigating future threats.
This underscores the vulnerability of interconnected industrial control systems to cyberattacks.
Financial Impact on Individual Victims
While the financial impact on large corporations is often well-documented, it’s crucial to recognize the financial hardship faced by individual victims. WannaCry’s encryption of personal files, including photos and documents, resulted in substantial financial losses. The cost of decryption tools, if available, was often prohibitive, especially for individuals with limited financial resources. The recovery process, even with limited data loss, often included significant out-of-pocket expenses for affected individuals.
Regulatory Response to the WannaCry Attack
The WannaCry attack spurred significant regulatory responses globally. Governments and industry bodies issued guidelines and recommendations for improving cybersecurity practices. The attack prompted stricter regulations regarding data protection, incident reporting, and system security. For instance, several countries strengthened their cybersecurity frameworks to mitigate the risks of similar attacks. The attack prompted increased awareness and investment in cybersecurity measures across various sectors.
Visual Representation of Data
WannaCry ransomware’s global impact demanded a comprehensive understanding of its spread, effects, and the data breaches it caused. Visualizations provide a powerful tool to grasp the scale and complexity of such cyberattacks, making the abstract more concrete and understandable. These representations aid in identifying patterns, pinpointing vulnerabilities, and strategizing for future prevention.Visual representations, whether geographic maps or charts, can highlight critical information such as the concentration of infections, the evolution of attacks over time, and the types of data compromised.
This data-driven approach facilitates better comprehension of the attack’s trajectory and its ramifications, enabling informed decisions regarding cybersecurity strategies.
Geographic Distribution of WannaCry Infections
A world map could visually represent the global reach of WannaCry. Each country or region could be color-coded to indicate the intensity of infection, with darker shades corresponding to higher infection rates. This map would highlight regions most affected by the attack, allowing for analysis of potential vectors and facilitating targeted mitigation strategies.
Growth of Ransomware Attacks Over Time, How many windows oses were hit with wanna cry ransomware
A line graph plotting the number of ransomware attacks against time would show the evolution of the threat. The graph could compare WannaCry’s impact with other ransomware attacks, enabling the identification of trends and potential future patterns. Such a graph could be further categorized to illustrate specific ransomware families, aiding in understanding the threat landscape’s dynamic evolution.
Types of Data Breaches Caused by WannaCry
A categorized bar chart could illustrate the types of data compromised by WannaCry. Different categories like financial records, customer information, or intellectual property could be represented, enabling a clearer picture of the data breach’s scope and potential consequences. This visual aids in prioritizing data protection measures for different organizations.
WannaCry’s Propagation Path
A network diagram, possibly a flow chart, could visually depict the ransomware’s propagation path. Nodes representing infected computers could be connected with arrows indicating the infection vectors. This visual could highlight vulnerabilities in network security and identify areas requiring improvement to prevent similar future attacks.
Last Word
In conclusion, the WannaCry ransomware attack serves as a stark reminder of the constant threat in the digital landscape. Understanding the specific vulnerabilities, the scope of the attack, and the subsequent mitigation strategies are crucial for safeguarding systems against similar threats. The lessons learned from this event continue to shape modern cybersecurity practices, underscoring the importance of proactive measures and continuous vigilance.
Top FAQs
What specific Windows versions were most vulnerable to WannaCry?
The attack primarily targeted older, unpatched versions of Windows, particularly those running on older systems. Microsoft’s patch was readily available, but many systems lacked timely updates.
What industries were most heavily impacted by WannaCry?
Hospitals, healthcare providers, and other critical infrastructure were disproportionately affected due to their reliance on older systems and the sensitive nature of their data. However, many other sectors experienced significant disruptions.
How effective were the data recovery methods employed after the attack?
Data recovery methods varied greatly, with some organizations successfully restoring data from backups, while others faced significant challenges due to data loss or lack of backups.
What was the long-term effect of the attack on cybersecurity regulations?
The WannaCry attack spurred stronger cybersecurity regulations and emphasized the need for regular security updates and improved incident response plans.