Multi-Cloud Security How-to Guide
How to maintain security across multi cloud environments – How to maintain security across multi-cloud environments is crucial in today’s dynamic IT landscape. This guide delves into the complexities of securing diverse cloud platforms, highlighting the unique challenges and best practices for navigating this intricate territory. From defining multi-cloud security to implementing effective monitoring strategies, we’ll explore the entire spectrum of securing your multi-cloud infrastructure.
A multi-cloud environment, encompassing various cloud providers like AWS, Azure, and GCP, presents a unique set of security concerns. The sheer variety of services, data locations, and security postures across these platforms necessitates a tailored approach. This guide will provide actionable insights and practical strategies to address these challenges.
Defining Multi-Cloud Security: How To Maintain Security Across Multi Cloud Environments
Multi-cloud environments, where organizations leverage services from multiple cloud providers, are rapidly gaining traction. This approach offers greater flexibility, cost optimization, and resilience. However, this complexity introduces unique security challenges that demand careful consideration and proactive strategies. The seamless integration of different cloud platforms necessitates a comprehensive understanding of the security landscape in these environments.The security of a multi-cloud architecture is not simply the sum of the security measures applied to individual clouds.
It’s a fundamentally different paradigm, requiring a holistic approach that addresses the intricacies of data movement, access control, and compliance across diverse platforms. This includes the integration of different security tools and protocols, the management of various access controls, and ensuring consistent security policies across different cloud providers.
Multi-Cloud Environment Components
Multi-cloud architectures involve the deployment of applications and data across various cloud providers, often with specific workloads residing on specific platforms. This intricate setup necessitates careful consideration of data location, service configurations, and security measures for each environment. Different cloud providers offer varying services, leading to diverse security features and implementations. Understanding these differences is crucial for maintaining consistent security policies.
For instance, data encryption methods and access control mechanisms may differ across AWS, Azure, and GCP.
Key Security Differences Across Cloud Providers
Cloud providers, such as AWS, Azure, and GCP, each have unique security postures. These differences stem from the specific services offered, their respective architectures, and their approaches to security. Security features, while generally robust, differ in implementation details. For instance, the configuration of Identity and Access Management (IAM) may vary significantly between the providers.
Security Features Comparison
Understanding the security features offered by different cloud providers is crucial for a comprehensive multi-cloud security strategy. The following table illustrates the core security features available from major cloud providers.
| Feature | AWS | Azure | GCP |
|---|---|---|---|
| Identity and Access Management (IAM) | Highly configurable IAM system with fine-grained access control | Robust IAM system with built-in role-based access control | IAM system offering granular control over access to resources |
| Data Encryption | Comprehensive encryption options for data at rest and in transit | Supports various encryption options for data storage and transfer | Provides a range of encryption options, including encryption at rest and in transit |
| Security Monitoring and Logging | Extensive logging and monitoring capabilities for security events | Comprehensive logging and monitoring tools for security events | Provides a comprehensive security logging and monitoring service |
| Vulnerability Management | Offers services to identify and remediate security vulnerabilities | Provides tools and services to identify and address security vulnerabilities | Provides security tools and services for vulnerability detection and mitigation |
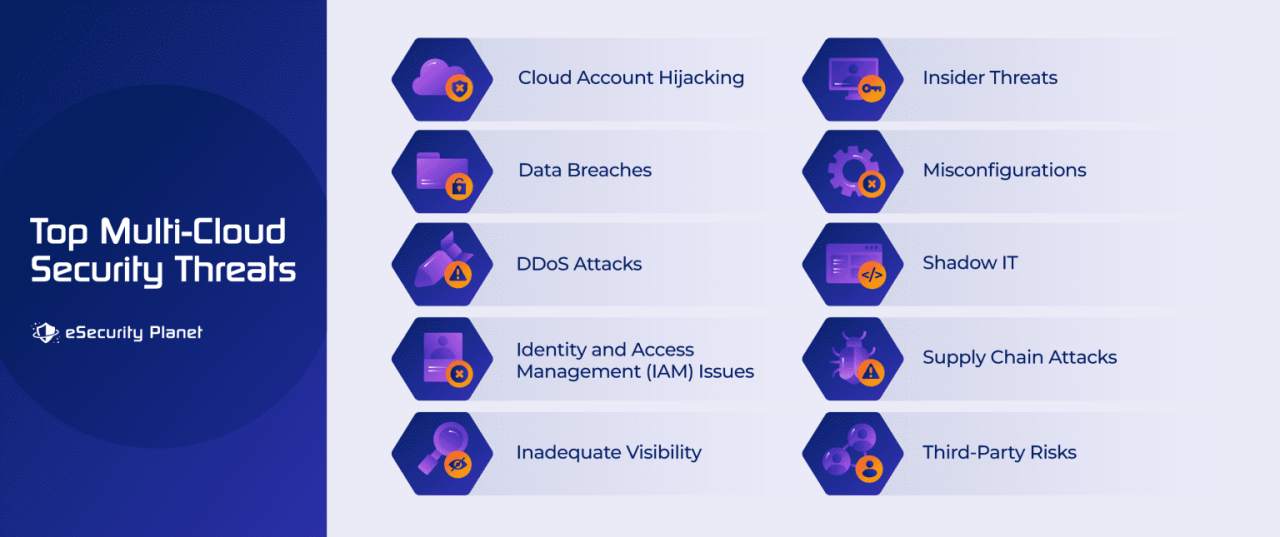
Identifying Security Risks in Multi-Cloud
Navigating the complexities of multiple cloud environments introduces a unique set of security challenges. The very nature of deploying applications and data across various cloud providers creates a more intricate attack surface, demanding a multifaceted approach to risk assessment and mitigation. This involves understanding the specific vulnerabilities inherent in multi-cloud deployments and proactively addressing potential issues related to data breaches, misconfigurations, and access control.The increasing reliance on multi-cloud strategies for business continuity and scalability necessitates a comprehensive understanding of the security risks associated with each cloud platform and the interconnected data flows between them.
A unified security posture across different cloud providers is crucial to maintain overall system integrity and avoid potential vulnerabilities.
Data Breach Vulnerabilities in Multi-Cloud
Data breaches pose a significant threat in multi-cloud environments. The distributed nature of data across multiple clouds makes it more challenging to detect and respond to breaches. Compromising one cloud can potentially expose data stored in other environments if appropriate security measures are not implemented. This necessitates robust data encryption and access control policies throughout the entire multi-cloud infrastructure.
Moreover, the potential for data breaches is amplified by the complexity of managing multiple cloud accounts, user permissions, and configurations.
Misconfigurations Across Cloud Providers
Misconfigurations are a significant source of vulnerability in multi-cloud deployments. Different cloud providers have varying interfaces and management tools, leading to potential errors in security settings. A misconfigured firewall, storage bucket, or virtual machine in one cloud can compromise data stored across other clouds. Manual errors, lack of automation, and inadequate monitoring of security configurations in each cloud environment increase the likelihood of vulnerabilities.
Access Control Issues Across Clouds
Maintaining consistent access control policies across multiple cloud providers is challenging. Variations in access control mechanisms, user permissions, and authentication methods across different cloud environments can create gaps in security. A weak access control in one cloud could expose sensitive data in other connected clouds, demanding consistent and granular access management policies across all cloud platforms. This necessitates strong authentication methods and rigorous access control policies to prevent unauthorized access to resources in any cloud environment.
Data Sovereignty and Compliance Risks
Data sovereignty and compliance regulations are critical considerations in multi-cloud deployments. Different jurisdictions have varying data privacy and security regulations. Storing data in multiple clouds may require compliance with multiple sets of regulations. Failure to adhere to these regulations can lead to legal repercussions and reputational damage. Ensuring that data is stored and processed in accordance with the applicable data sovereignty and compliance regulations in each jurisdiction is essential.
Attack Vectors Specific to Cloud Providers
- AWS (Amazon Web Services): Common attack vectors include misconfigured S3 buckets (allowing public access to sensitive data), insecure IAM roles (granting excessive permissions), and vulnerabilities in EC2 instances. For example, failing to apply security patches to EC2 instances can expose them to known exploits.
- Azure (Microsoft Azure): Potential attack vectors include misconfigured storage accounts (similar to S3 buckets in AWS), weak passwords for Azure Active Directory accounts, and unpatched virtual machines. For example, neglecting to implement network security groups can lead to unauthorized access to Azure resources.
- GCP (Google Cloud Platform): Attack vectors include insecurely configured Cloud Storage buckets, weak passwords for Google Cloud accounts, and unpatched virtual machines. An example is the improper use of service accounts leading to elevated privileges.
Comparison of Security Risks Across Cloud Providers
| Cloud Provider | Common Security Risks | Example Vulnerabilities |
|---|---|---|
| AWS | Misconfigured S3 buckets, insecure IAM roles, EC2 instance vulnerabilities | Publicly accessible S3 buckets, weak IAM permissions, outdated EC2 security patches |
| Azure | Misconfigured storage accounts, weak AD passwords, unpatched VMs | Publicly accessible storage accounts, compromised AD credentials, outdated VM security patches |
| GCP | Insecure Cloud Storage buckets, weak GCP account passwords, unpatched VMs | Publicly accessible Cloud Storage buckets, weak service account credentials, outdated VM security patches |
Implementing Security Strategies
Maintaining consistent security across multiple cloud platforms is crucial for a robust multi-cloud strategy. This requires a proactive approach, encompassing policies, procedures, and tools tailored to the unique characteristics of each cloud provider. Effective security management in a multi-cloud environment goes beyond simply replicating security measures; it demands a holistic, integrated approach.
Creating Consistent Security Policies
Establishing a centralized security policy framework is vital. This framework should define security standards, procedures, and controls applicable across all cloud environments. This includes defining access levels, data encryption requirements, and incident response protocols. The policy should be adaptable to the specific needs of each cloud platform while adhering to a core set of security principles. A well-defined policy acts as a blueprint for security implementation and ensures a uniform level of protection across the entire multi-cloud ecosystem.
Enforcing Security Best Practices
Enforcing security best practices across diverse cloud providers necessitates a standardized approach. This involves using security tools and automation to consistently monitor and enforce security policies. Implementing automated security scans and vulnerability assessments across all cloud platforms is critical. Integration with cloud provider security services, like AWS Security Hub or Azure Security Center, can streamline the enforcement process.
Regular audits and reviews of security controls are also essential to ensure ongoing compliance and effectiveness.
Maintaining Data Encryption and Access Control
Data encryption and access control are fundamental aspects of multi-cloud security. Implementing strong encryption mechanisms across all data stored in various cloud environments is essential to protect sensitive information. This includes both data at rest and data in transit. Centralized access control management is key to regulating user permissions and access rights to data residing in different cloud providers.
This approach ensures that only authorized personnel can access specific data sets, regardless of the cloud platform involved. Implementing least privilege access principles is vital to reduce the impact of potential security breaches.
Security Tools and Technologies
A range of security tools and technologies can bolster multi-cloud security. These tools should address the unique characteristics of each cloud platform while enabling consistent security management. Cloud security information and event management (SIEM) solutions can provide comprehensive visibility into security events across multiple cloud environments. Identity and access management (IAM) tools are crucial for managing user access and permissions.
Using a centralized security orchestration, automation, and response (SOAR) platform can streamline security operations across the entire multi-cloud environment.
Recommended Security Tools and Functionalities
| Security Tool | Functionality in Multi-Cloud |
|---|---|
| Cloud Security Posture Management (CSPM) | Identifies and remediates security misconfigurations across various cloud platforms. |
| Security Information and Event Management (SIEM) | Centralized logging and analysis of security events from multiple cloud environments. |
| Cloud Access Security Broker (CASB) | Enforces security policies and controls for data access and usage across various cloud providers. |
| Identity and Access Management (IAM) | Manages user identities, permissions, and access controls in all cloud environments. |
| Data Loss Prevention (DLP) | Prevents sensitive data from leaving the cloud environment or being accessed by unauthorized users. |
| Vulnerability Management | Identifies and mitigates vulnerabilities across all cloud environments. |
Monitoring and Auditing Multi-Cloud Security

Maintaining security across multiple cloud environments requires a robust monitoring and auditing strategy. A reactive approach to security issues is insufficient in this complex landscape. Continuous monitoring and proactive auditing are crucial for identifying vulnerabilities and threats before they escalate into significant incidents. This proactive approach minimizes downtime, data breaches, and financial losses.Proactive security monitoring and auditing in a multi-cloud environment are essential to maintain a strong security posture.
They enable organizations to identify and address potential threats and vulnerabilities before they cause damage. This approach is significantly more effective than reacting to security incidents after they occur.
Continuous Monitoring of Security Posture
Continuous monitoring of security posture in a multi-cloud environment necessitates the use of various tools and techniques. These methods should track key metrics, detect anomalies, and provide real-time insights into potential threats. This constant vigilance helps organizations identify and respond to security events quickly, reducing the impact of any potential breaches.
Importance of Proactive Security Auditing and Reporting
Proactive security auditing and reporting mechanisms are critical for identifying vulnerabilities and compliance gaps. Regular audits help organizations ensure that their security controls are effective and up-to-date, reducing the risk of unauthorized access and data breaches. Automated reporting enables organizations to track security performance over time, identifying trends and areas needing improvement. Regular reports highlight security posture, compliance status, and potential risks.
Identifying and Responding to Security Incidents, How to maintain security across multi cloud environments
Identifying and responding to security incidents in a multi-cloud setup requires a well-defined incident response plan. This plan should Artikel procedures for detecting, containing, and resolving security incidents, minimizing the impact on business operations. The plan should be regularly tested and updated to reflect changes in the environment and threat landscape. A clear incident response framework enables organizations to effectively handle and mitigate security incidents.
Implementing and Automating Security Alerts and Notifications
Implementing and automating security alerts and notifications is vital for timely incident response. Automated systems can be configured to send alerts based on predefined criteria, such as unusual network activity or suspicious login attempts. This automation ensures that security teams are notified immediately of potential threats, allowing for swift response and mitigation. Early detection and response is critical to minimizing damage from security incidents.
Monitoring Tools for Multi-Cloud Environments
Implementing an effective monitoring strategy necessitates the selection of appropriate tools. Different tools cater to various needs, and understanding their strengths and weaknesses is crucial for proper selection. This organized approach to tool selection ensures optimal protection for the multi-cloud environment.
- Security Information and Event Management (SIEM) tools: These tools collect and analyze security logs from various sources, providing a centralized view of security events across the multi-cloud environment. Their strength lies in correlating events to identify patterns indicative of malicious activity. Weaknesses can include complexity in configuration and management, and potential performance bottlenecks if not properly tuned.
- Cloud-native security tools: These tools are specifically designed for cloud environments, offering features such as real-time threat detection and response. They provide a more streamlined approach for monitoring and managing cloud-specific security threats. However, they might not be as versatile as SIEM tools when dealing with data from non-cloud sources.
- Network monitoring tools: These tools provide visibility into network traffic and activity, helping identify suspicious connections or unusual patterns. They can be useful in detecting malicious traffic or unauthorized access attempts. However, they may not be sufficient for comprehensive security monitoring without integrating with other tools.
- Vulnerability scanners: These tools identify and report security vulnerabilities in applications and infrastructure, helping proactively address potential threats. They are crucial for maintaining a strong security posture. Weaknesses include false positives and the need for regular updates to stay effective against the ever-evolving threat landscape.
Compliance and Governance in Multi-Cloud
Navigating the complex landscape of multi-cloud deployments requires a robust framework for compliance and governance. Simply deploying applications across different cloud providers doesn’t automatically ensure adherence to regulations or maintain consistent security posture. Effective governance ensures that security policies and procedures are consistently applied across all environments, regardless of the cloud provider. This proactive approach minimizes risk and protects sensitive data.Meeting regulatory requirements in a multi-cloud environment demands a granular understanding of each cloud provider’s compliance certifications and frameworks.
A comprehensive approach is essential, encompassing policies, processes, and technologies that address the unique security challenges presented by the diverse environments. This involves implementing consistent controls and monitoring mechanisms across all clouds, which is critical for maintaining a unified security posture.
Importance of Compliance and Governance
Effective compliance and governance strategies are paramount for mitigating risks in multi-cloud environments. They ensure that sensitive data is protected, regulatory requirements are met, and business operations remain consistent with legal and industry standards. Robust governance minimizes the risk of security breaches and data loss, while compliance demonstrates a commitment to responsible data handling.
Meeting Regulatory Requirements Across Cloud Providers
A crucial aspect of multi-cloud compliance is understanding and implementing the specific compliance requirements for each cloud provider. This requires meticulous research and detailed documentation to ensure that all environments are aligned with the necessary standards. Organizations must maintain detailed records of their compliance posture across all clouds, enabling easy auditing and reporting. A centralized policy management system can enforce consistent compliance across all providers.
Maintaining Compliance with Industry Regulations
Industry regulations like HIPAA, GDPR, and PCI DSS often dictate specific security measures. Organizations must identify the relevant regulations for their industry and ensure that their multi-cloud strategy aligns with these requirements. For instance, HIPAA requires specific measures for protecting patient data. This necessitates a comprehensive approach to data security across all cloud environments, including encryption, access controls, and audit trails.
Regular audits are vital to ensure compliance is maintained.
Maintaining security across multiple cloud environments is a real challenge, especially when dealing with the complexities of different providers. Fortunately, the Department of Justice Offers Safe Harbor for MA Transactions here offers valuable insights into handling sensitive data. Understanding these legal frameworks is crucial for building robust security policies that span your entire multi-cloud setup.
Data Sovereignty and Privacy in a Multi-Cloud Context
Data sovereignty and privacy are critical considerations in multi-cloud environments. Regulations often dictate where data must be stored, and organizations need a strategy to ensure compliance with these rules. A multi-cloud strategy must include mechanisms for ensuring data resides in compliant regions and that access controls are in place to maintain data privacy. This includes adhering to data residency policies and employing encryption techniques to protect data in transit and at rest.
Maintaining security across multiple cloud environments is a real challenge, requiring careful planning and robust tools. One crucial aspect is ensuring the code you’re deploying is secure, which is why deploying AI Code Safety Goggles Needed here is so important. Ultimately, a layered approach, combining these advanced security tools with strong cloud infrastructure policies, is key to maintaining that security posture.
Compliance Requirements and Solutions by Cloud Provider
| Cloud Provider | Compliance Requirements | Solutions |
|---|---|---|
| AWS | SOC 2, HIPAA, GDPR | AWS Security Hub, IAM, encryption services, managed services |
| Azure | SOC 2, HIPAA, GDPR, ISO 27001 | Azure Security Center, Azure Active Directory, encryption, key management |
| Google Cloud | SOC 2, HIPAA, GDPR, ISO 27001 | Google Cloud Security Command Center, IAM, encryption, data loss prevention |
This table provides a high-level overview. Specific compliance requirements and solutions will vary based on the specific needs and regulations of the organization.
Best Practices for Multi-Cloud Security

Securing a multi-cloud environment requires a holistic approach that transcends individual cloud provider security measures. Best practices go beyond simply replicating security controls across different platforms. They demand a unified strategy that accounts for the unique characteristics of each cloud and the interconnected nature of the entire infrastructure. This approach ensures consistent security posture and resilience across all environments.Effective multi-cloud security necessitates a shift in mindset, moving away from a siloed approach towards a centralized, integrated strategy.
Maintaining security across multiple cloud environments is a real challenge, and understanding specific vulnerabilities like those in Azure Cosmos DB is crucial. For example, checking out the Azure Cosmos DB Vulnerability Details can highlight potential weak points. Ultimately, robust security strategies need to account for these details to prevent breaches and maintain a strong multi-cloud posture.
This requires a deep understanding of the nuances of each cloud platform and a robust framework for managing security across all environments. It’s crucial to recognize that security in one cloud isn’t automatically transferable to another; tailored strategies are essential for optimal protection.
Secure Configuration Management Practices
Proper configuration management is fundamental to multi-cloud security. It ensures consistent security settings across all cloud environments. This includes defining and enforcing standardized configurations for virtual machines, networks, and storage.
- AWS: Employ AWS CloudFormation templates for automating infrastructure provisioning and configuration. Utilize security best practices Artikeld in the AWS Security Whitepaper to define security groups, access controls, and network configurations.
- Azure: Leverage Azure Resource Manager templates for consistent deployments and configuration. Implement Azure Policy definitions to enforce security standards and compliance requirements.
- Google Cloud Platform (GCP): Utilize GCP Deployment Manager for automated infrastructure provisioning. Leverage the security best practices available in GCP documentation to configure appropriate access controls, logging, and monitoring.
Importance of Identity and Access Management (IAM)
Effective Identity and Access Management (IAM) is critical for controlling access to resources in a multi-cloud environment. It’s not enough to simply replicate IAM solutions; a unified access management strategy is essential.
- Centralized Identity Provider: Using a centralized identity provider (IdP) for authentication and authorization across all clouds enables consistent access policies and simplifies management.
- Least Privilege Principle: Applying the principle of least privilege to all user accounts and roles minimizes the potential impact of security breaches by restricting access only to necessary resources.
- Multi-Factor Authentication (MFA): Implementing MFA across all cloud environments enhances security by requiring additional verification steps beyond simple passwords.
Incident Response Strategies
A robust incident response strategy is vital for a multi-cloud environment. It must address the unique challenges of detecting, containing, and recovering from security incidents across multiple clouds.
- Unified Incident Management Platform: Implement a centralized platform for monitoring and managing security incidents across all clouds. This facilitates rapid response and streamlined communication.
- Playbook Development: Create detailed incident response playbooks for different types of security incidents. These playbooks should be specific to each cloud environment, considering the unique characteristics and vulnerabilities of each platform.
- Automated Threat Detection and Response: Leverage security information and event management (SIEM) tools and security orchestration, automation, and response (SOAR) platforms to automate incident detection and response.
Recommended Security Tools
Selecting the right security tools is crucial for a multi-cloud environment. These tools should be chosen based on their capabilities and compatibility across different cloud platforms.
| Tool | Application |
|---|---|
| Cloud Security Posture Management (CSPM) tools | Automated assessment and remediation of security misconfigurations across multiple cloud platforms. |
| Security Information and Event Management (SIEM) tools | Centralized logging and analysis of security events from various cloud environments. |
| Security Orchestration, Automation, and Response (SOAR) platforms | Automation of security tasks, including incident response and threat hunting. |
| Network Security Tools | Protecting network traffic between cloud environments and on-premises infrastructure. |
Case Studies and Real-World Examples
Multi-cloud environments, while offering flexibility and resilience, introduce complex security challenges. Real-world case studies provide invaluable insights into successful implementations and common pitfalls, enabling organizations to learn from others’ experiences and avoid costly mistakes. Understanding how various industries have tackled multi-cloud security is crucial for developing effective strategies.Effective multi-cloud security implementations require a holistic approach, encompassing not only technical solutions but also organizational policies and procedures.
A key element is a strong security information and event management (SIEM) system that can correlate events across different cloud platforms.
Successful Multi-Cloud Security Strategies
Implementing effective multi-cloud security strategies involves careful planning and execution. Organizations must establish clear security policies that apply consistently across all cloud environments. This often requires a centralized security team or a dedicated security architect to oversee and coordinate security initiatives. Crucially, this team needs access to all cloud environments’ data to manage risks effectively.
- Financial Services: A leading financial institution successfully migrated to a multi-cloud environment while maintaining strict compliance with regulatory mandates like PCI DSS and GDPR. Their strategy involved a phased approach to migration, securing each environment before merging them into a unified multi-cloud platform. Security measures included robust access controls, encryption at rest and in transit, and regular security audits to maintain compliance across all cloud providers.
- Retail: A large e-commerce company utilized a multi-cloud approach to support its global operations. Their multi-cloud strategy focused on high availability and disaster recovery, with a dedicated security team responsible for managing security policies and incident response across all cloud platforms. They employed automated security scanning tools to identify vulnerabilities in real-time and implemented zero-trust network access (ZTNA) to control network access to sensitive data.
- Healthcare: A healthcare provider leveraged a multi-cloud strategy to manage sensitive patient data securely. Key to their success was a centralized security information and event management (SIEM) system that monitored events across all cloud environments. Regular security assessments and penetration testing were performed to proactively identify and mitigate potential threats. Strict adherence to HIPAA regulations was a top priority throughout the implementation.
Challenges and Lessons Learned
Multi-cloud deployments present unique challenges in security management. Lack of visibility across disparate cloud environments often leads to blind spots in security posture. Maintaining consistent security policies across different cloud providers can be complex and require significant effort. The lack of a unified security management platform is often a major hurdle.
- Interoperability issues: Different cloud platforms may have varying security features and functionalities, leading to interoperability challenges. Integrating security tools across different clouds can be complex and costly. Organizations need to carefully evaluate the capabilities of each cloud platform and choose tools that work seamlessly across all environments.
- Data sprawl: Data sprawl across multiple cloud environments can complicate data governance and security management. A lack of centralized data management can result in security gaps and compliance violations. Developing a clear data classification and labeling scheme, coupled with a robust data access control system, is crucial.
- Compliance complexity: Meeting compliance requirements across various cloud environments can be challenging. Different regulations may apply to different cloud platforms and data locations, creating a complex compliance landscape. Implementing a standardized compliance framework that is applicable across all cloud environments can help.
Security Breach Scenario and Recovery
A hypothetical scenario involves a cloud storage provider experiencing a security breach impacting a multi-cloud deployment. The attacker exploited a vulnerability in a third-party application used across all cloud environments. The breach led to sensitive customer data being compromised.The recovery process involved several steps:
- Immediate containment: The organization immediately isolated the affected systems and suspended access to the compromised data.
- Vulnerability remediation: The vulnerability was promptly addressed, patching the affected applications across all cloud platforms.
- Data recovery: A detailed forensic analysis was conducted to assess the extent of the breach and recover any affected data. This often involves working with the cloud provider and external security experts.
- Enhanced security protocols: The organization implemented new security protocols and procedures to prevent future breaches. These included enhanced access controls, intrusion detection systems, and regular security audits.
Success Factors and Common Pitfalls
The success of multi-cloud security depends on several factors. Careful planning, consistent security policies, and a centralized security team are critical. The table below Artikels key success factors and common pitfalls:
| Success Factors | Common Pitfalls |
|---|---|
| Unified Security Management Platform | Lack of Visibility Across Clouds |
| Centralized Security Policies | Inconsistent Security Policies |
| Strong Access Controls | Insufficient Access Controls |
| Regular Security Assessments | Inadequate Security Monitoring |
| Proactive Threat Hunting | Lack of Proactive Security Measures |
Concluding Remarks
In conclusion, securing a multi-cloud environment demands a holistic approach that considers diverse security risks, compliance requirements, and best practices. This guide has Artikeld key strategies for maintaining a robust security posture across multiple clouds, enabling organizations to leverage the benefits of multi-cloud deployments while mitigating potential vulnerabilities. Continuous monitoring, proactive auditing, and a strong understanding of the specific security features of each cloud provider are paramount for success.
Remember, security in a multi-cloud environment is an ongoing process, requiring constant adaptation and vigilance.
Questions Often Asked
What are some common misconfigurations that can compromise security in a multi-cloud environment?
Insufficient access controls, insecure API keys, and improperly configured storage buckets are common misconfigurations that can expose sensitive data. Different cloud providers have varying approaches to configuration, requiring careful attention to detail and consistent policies.
How does data sovereignty impact security strategies in a multi-cloud setup?
Data sovereignty regulations often mandate that data be stored within specific geographical boundaries. This necessitates understanding the regulations of each region and selecting cloud providers that comply with these requirements. Proper data encryption and access controls are also crucial to maintaining data sovereignty.
What are some key considerations when choosing monitoring tools for a multi-cloud environment?
Monitoring tools should be able to seamlessly integrate with various cloud platforms. They should provide real-time visibility into security events, allowing for quick detection and response. Consider factors like scalability, ease of use, and reporting capabilities when selecting monitoring tools.
How can I ensure consistent security policies across different cloud platforms in a multi-cloud environment?
Centralized security management tools and policies can help enforce consistent security protocols across all cloud platforms. This approach involves defining standard configurations, enforcing access controls, and ensuring that all environments adhere to established security guidelines.