How to Make 5 Million a Day in Cybercrime A Risky Proposition
How to make 5 million a day in cybercrime? This is a tempting question, but the reality is far more complex than any simple guide could convey. While the allure of such immense financial gain is undeniable, the path to achieving it is fraught with danger and ethical dilemmas. This exploration delves into the intricate world of cybercrime, examining the methods, motivations, and the extreme risks involved.
The landscape of cybercrime is constantly evolving, with new threats and opportunities emerging regularly. Understanding the techniques used by cybercriminals is essential for both preventing and combating these crimes. This article will cover the intricacies of various methods, including ransomware, phishing, and credit card fraud, while also discussing the massive scale and infrastructure required to generate such staggering daily profits.
Introduction to Cybercrime

Cybercrime encompasses a broad spectrum of illegal activities conducted using digital technologies and computer networks. It’s a constantly evolving threat landscape, fueled by technological advancements and the increasing reliance on online systems. These activities can range from relatively minor inconveniences to significant financial losses and severe damage to individuals and organizations. Understanding the various types, motivations, and evolving nature of cybercrime is crucial for developing effective prevention and mitigation strategies.
Defining Cybercrime
Cybercrime is defined as any criminal activity that involves a computer, computer network, or a related device. This encompasses a wide array of actions, from simple hacking to sophisticated financial fraud. It’s characterized by the use of technology as both the tool and the target of the crime.
Categories of Cybercrime
Cybercrime manifests in diverse forms. Understanding these categories provides a more comprehensive picture of the threats.
- Cybertheft: This category includes various forms of stealing digital assets, such as financial fraud, identity theft, and the unauthorized access and use of personal data. Cybertheft often involves sophisticated techniques to circumvent security measures and evade detection.
- Cybervandalism: This type of cybercrime focuses on disrupting or damaging digital infrastructure or data. Examples include website defacement, denial-of-service attacks, and the creation and dissemination of malicious code.
- Cyberespionage: This involves the unauthorized gathering of sensitive information from organizations or individuals. It can include stealing trade secrets, intellectual property, or government secrets. Nation-state actors often engage in cyberespionage to gain a strategic advantage.
- Cyberharassment: This involves using digital tools to cause distress or harm to individuals. Examples include cyberstalking, online harassment, and the spread of false information to damage reputation.
Motivations Behind Cybercriminal Activities
Cybercriminals are motivated by a diverse range of factors. Financial gain is often the primary driver, but other motivations include personal gratification, political agendas, and social causes.
- Financial Gain: This is arguably the most common motivation. Cybercriminals often target financial institutions and individuals to steal money, credit card details, and other valuable information.
- Personal Gratification: Some cybercriminals engage in activities such as hacking or data breaches simply to demonstrate their technical skills or gain recognition within online communities.
- Political Agendas: Certain cyberattacks are motivated by political ideologies or grievances. These attacks can range from disrupting online services to disseminating propaganda.
- Social Causes: In rare cases, cybercriminals may engage in activities to support specific social or political causes. These attacks are often more focused on disrupting systems than directly targeting individuals.
Evolving Landscape of Cyber Threats
The cyber threat landscape is constantly evolving, driven by new technologies, vulnerabilities, and attack methods. The sophistication of attacks is increasing, and cybercriminals are leveraging advanced techniques to bypass security measures.
- Sophistication of Attacks: Cybercriminals are constantly developing more sophisticated methods to breach security systems. This includes using artificial intelligence (AI) and machine learning (ML) to automate attacks and evade detection.
- Increased Use of AI and ML: AI and ML are being used to develop more sophisticated malware, automate attacks, and personalize phishing campaigns. This makes it more difficult for security systems to keep up.
- Rise of Ransomware: Ransomware attacks have become increasingly prevalent, targeting both individuals and organizations. Criminals encrypt data and demand payment in exchange for decryption keys.
Cybercrime Examples and Impacts
| Crime Type | Description | Example | Potential Impact |
|---|---|---|---|
| Phishing | Tricking individuals into revealing sensitive information, such as passwords and credit card details, by pretending to be a legitimate entity. | Receiving an email claiming to be from a bank asking for account details. | Financial loss, identity theft, compromise of personal information. |
| Malware | Software designed to damage or disable a computer system. | Downloading a seemingly harmless file that contains a virus. | Data loss, system damage, financial loss, operational disruption. |
| Denial-of-Service (DoS) Attacks | Overwhelming a system with traffic, making it unavailable to legitimate users. | Launching an attack on a website to disrupt its operations. | Loss of revenue, disruption of services, reputational damage. |
| Social Engineering | Manipulating individuals into performing actions or divulging information that compromises security. | A cybercriminal posing as a technical support representative to gain access to a user’s system. | Unauthorized access to sensitive data, financial loss, reputational damage. |
Financial Gain Through Cybercrime
The digital age has created a new frontier for criminal activity, with cybercrime offering lucrative opportunities for financial gain. This shift in criminal landscape has led to sophisticated techniques and diverse targets, demanding a careful understanding of the methods employed and their potential profitability. This section delves into the common methods of financial gain through cybercrime, outlining the mechanics, steps, and potential returns of each.
Common Methods of Financial Gain
Various tactics are employed by cybercriminals to extract financial resources. These methods often exploit vulnerabilities in systems and human behavior. Understanding the mechanics behind each method is crucial to understanding the potential for harm.
Ransomware
Ransomware attacks involve encrypting a victim’s data and demanding payment for its release. The mechanics are often complex, involving sophisticated encryption algorithms and techniques to ensure data is inaccessible without the decryption key. The process typically starts with gaining unauthorized access to a system, followed by the deployment of the ransomware. Once the data is encrypted, a ransom demand is presented to the victim.
The steps involved often include identifying potential targets, deploying malware, encrypting data, and demanding payment. The profitability of ransomware attacks can vary greatly depending on the target’s resources and willingness to pay.
Dreaming of making $5 million a day in cybercrime? It’s a pipe dream, frankly. While exploiting vulnerabilities like those detailed in the Azure Cosmos DB Vulnerability Details might seem tempting, the reality is far more complex and fraught with risk. The pursuit of such quick riches in cybercrime is often a dead end. Focus on ethical hacking and secure practices instead.
Phishing
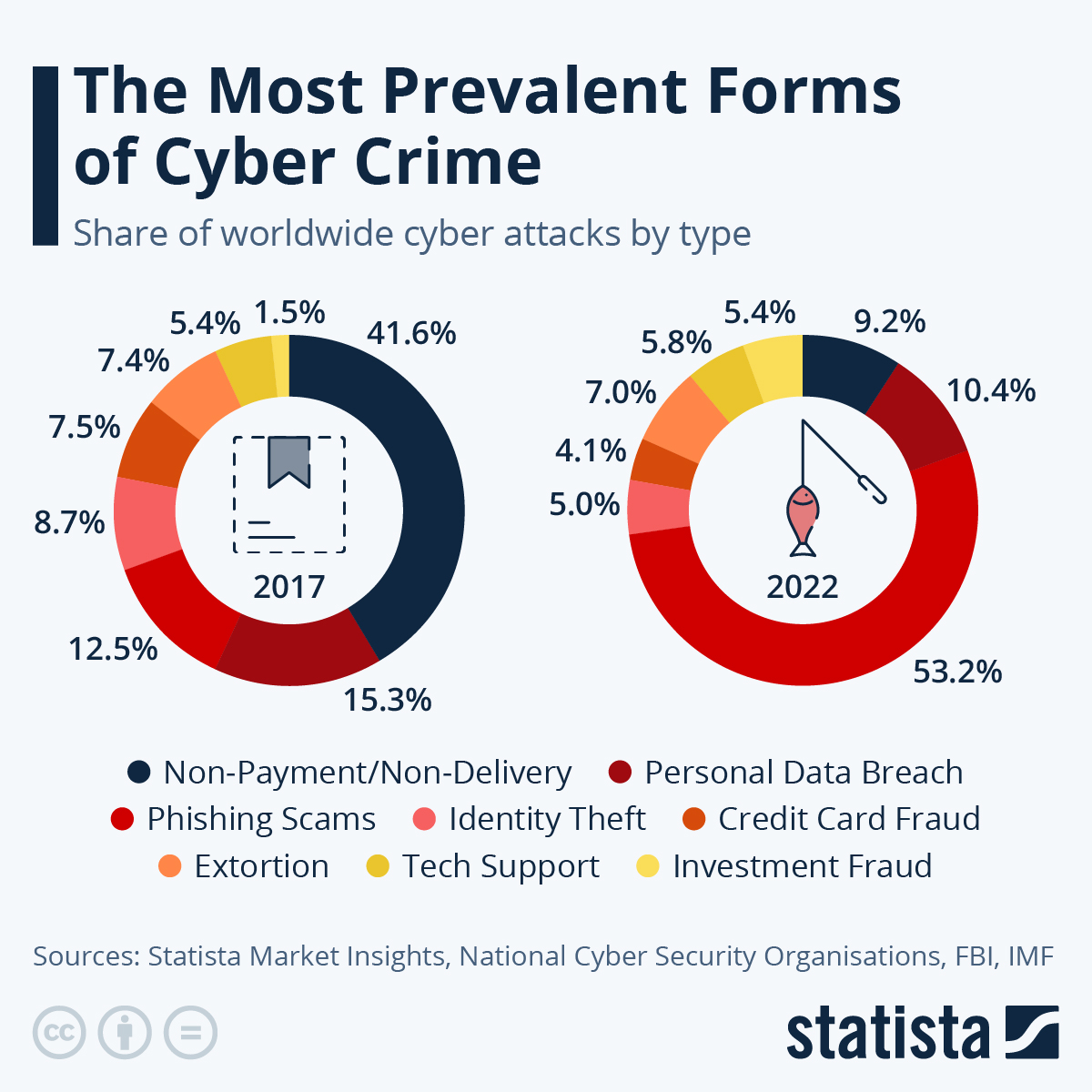
Phishing scams exploit human psychology to trick individuals into revealing sensitive information, such as usernames, passwords, and credit card details. The mechanics often involve creating convincing fraudulent emails or websites mimicking legitimate entities. The process typically starts with researching potential victims, crafting convincing phishing emails or messages, and distributing them to target individuals. Victims who fall for the scam provide their sensitive information, which the attackers then use for financial gain.
The profitability of phishing depends on the scale of the attack and the number of successful targets.
Credit Card Fraud
Credit card fraud involves stealing credit card information to make unauthorized purchases or withdraw funds. The mechanics often involve stealing data from compromised systems, skimming data from physical terminals, or exploiting vulnerabilities in online payment systems. The process typically involves identifying potential targets, acquiring credit card information, and using the information to make fraudulent purchases. The profitability depends on the volume of stolen information and the ability to successfully use it.
Comparison of Profitability
The profitability of different cybercrime methods is highly variable. Ransomware, while potentially lucrative for large-scale attacks, can also lead to significant exposure. Phishing, with its ease of execution, can yield substantial gains when targeting many individuals. Credit card fraud, if conducted on a large scale, can result in significant financial gains.
Potential Financial Gains
| Cybercrime Method | Average Successful Targets | Potential Financial Gain (USD) |
|---|---|---|
| Ransomware | 50-200 per year (per attacker group) | $10,000 – $1,000,000+ per attack |
| Phishing | Thousands per campaign | $100 – $10,000+ per campaign |
| Credit Card Fraud | Hundreds per month (per attacker group) | $100 – $100,000+ per month |
Note: The figures presented are estimates and can vary significantly depending on the specific attack, the target, and the success rate.
The Feasibility of $5 Million Daily in Cybercrime: How To Make 5 Million A Day In Cybercrime
Achieving a daily profit of $5 million through cybercrime is an extremely ambitious goal, bordering on the fantastical. While individual attacks and sophisticated campaigns can generate substantial sums, the scale required for such consistent high-volume income is unprecedented and likely unsustainable. This level of profitability demands a sophisticated, highly organized operation, and is fraught with immense risks.
Hypothetical Case Study: A Massive Ransomware Campaign
A hypothetical cybercriminal organization aiming for $5 million daily revenue would need a highly advanced ransomware operation. This operation wouldn’t rely on a single, large attack, but rather a highly automated system targeting hundreds, if not thousands, of vulnerable systems daily. The organization would need to develop a highly sophisticated ransomware strain, capable of quickly encrypting data and demanding a significant ransom.
This strain would need to be highly adaptable to evolving security measures. Furthermore, a robust infrastructure for payment collection and communication is crucial, employing techniques to evade law enforcement tracking. The cybercriminals would need a dedicated team to identify and exploit vulnerabilities, manage the infected systems, and handle the ransom payments, as well as a robust support system for victims.
Scale of Resources and Infrastructure
Maintaining a $5 million daily income requires substantial resources. The organization needs a large team of skilled hackers, coders, and payment processors. Servers with immense processing power are essential for executing the attacks and managing the massive influx of data. The infrastructure would also need advanced encryption methods, sophisticated evasion techniques to bypass security measures, and multiple geographically distributed servers to mask their location and avoid detection.
Furthermore, a secure and reliable payment infrastructure is critical for receiving ransoms in untraceable digital currencies. This operation likely requires a large office space, and a substantial amount of capital to purchase and maintain all the necessary equipment and software.
Potential Risks and Challenges
The risks associated with such a large-scale operation are significant. Law enforcement agencies are constantly improving their detection and response capabilities. The risk of being caught and prosecuted, or even facing cyber warfare from targeted nations, is substantial. Furthermore, the reliability of the payment infrastructure, and the potential for payment disputes or non-payment from victims, is a major concern.
Dreaming of making $5 million a day in cybercrime? Well, forget about it. The reality is, attempts to profit from cybercrime are almost always met with severe consequences. Thankfully, the Department of Justice Offers Safe Harbor for MA Transactions here , providing a framework for legitimate transactions in the state. So, while fantasizing about illicit gains is fun, focusing on legal and ethical business practices is a much safer bet for long-term financial success.
The operation’s success relies heavily on the resilience and security of their infrastructure. Maintaining secrecy and avoiding detection are paramount, requiring constant adaptation and vigilance.
Comparison to Other Criminal Enterprises
Comparing this level of income to other criminal enterprises reveals the extreme scale involved. While organized crime groups may generate significant revenue from various activities, reaching $5 million daily through cybercrime is exceptional. Drug trafficking and other criminal enterprises typically involve physical resources, manpower, and geographical limitations that don’t translate to the same scale of profit and risk in cybercrime.
The flexibility and potential for massive scale in cybercrime makes it uniquely challenging to compare it to traditional criminal enterprises.
Daily Revenue Generated Through Various Cybercrime Methods (Estimated)
| Cybercrime Method | Estimated Daily Revenue (USD) | Description |
|---|---|---|
| Ransomware | $1,000,000 – $5,000,000+ | Encrypting data and demanding a ransom. |
| Distributed Denial-of-Service (DDoS) Attacks | $50,000 – $500,000 | Overloading a target’s servers with traffic, causing them to crash. |
| Data Breaches | $100,000 – $1,000,000+ | Stealing sensitive data and selling it on the dark web. |
| Phishing and Social Engineering | $10,000 – $100,000+ | Tricking individuals into revealing sensitive information. |
This table provides a general overview of potential daily revenue for various cybercrime methods. These estimates are highly variable and depend on the sophistication of the attack, the target’s vulnerability, and the effectiveness of the criminal operation.
Technical Aspects of High-Value Cybercrime
High-value cybercrime operations demand a sophisticated understanding of technology and a willingness to exploit vulnerabilities. This isn’t about clicking a few links; it’s about deep technical knowledge and meticulous planning. Successful attacks are meticulously crafted, leveraging weaknesses in systems and networks to achieve significant financial gain. This section delves into the essential technical skills and tools required for such operations.The digital landscape is constantly evolving, demanding continuous adaptation and learning for cybercriminals.
This constant adaptation fuels the need for specialized expertise and a keen understanding of emerging technologies. Successfully exploiting these systems requires a deep understanding of how they function and where their weaknesses lie.
Technical Skills Required
Cybercrime operations necessitate a diverse skillset. From network penetration to code manipulation, a deep understanding of computer systems and software is essential. Proficient programmers, network engineers, and security analysts are highly sought after. Knowledge of operating systems, programming languages (like Python, C++, and Assembly), and networking protocols is critical for developing and deploying malicious code.
Technologies and Tools Used in Sophisticated Attacks
Sophisticated attacks utilize a wide range of tools and technologies. These include exploit kits, ransomware, phishing kits, and custom-developed malware. Exploit kits automate the process of identifying and exploiting vulnerabilities in software, often targeting a wide range of systems. Ransomware encrypts victim data, demanding payment for its release. Phishing kits are used to trick individuals into revealing sensitive information, such as login credentials or financial details.
Custom-developed malware can be tailored to specific targets and environments.
Network Security and Vulnerability Exploitation
Understanding network security is paramount for effective cybercrime. Identifying vulnerabilities in a network’s architecture and security protocols is crucial. This requires meticulous research and analysis of the target’s defenses. Cybercriminals need to exploit these weaknesses to gain unauthorized access to systems and data. This knowledge is vital for navigating firewalls, intrusion detection systems, and other security measures.
Thinking about making $5 million a day in cybercrime? Forget the fantasies; it’s a dangerous path. Instead, consider the crucial need for enhanced code security, like deploying AI Code Safety Goggles Needed here. This proactive approach is way more productive than chasing ill-gotten gains. Focusing on secure coding practices is the real key to success, not illegal activities.
Evasion Techniques to Remain Undetected
Evasion techniques are critical for successful attacks. These methods are designed to bypass security measures and remain undetected. Techniques such as encrypting communications, using proxy servers, and employing obfuscation techniques can mask malicious activity. The ability to avoid detection is crucial for sustaining a high-volume operation.
Technical Requirements and Skill Sets
| Cybercrime Method | Technical Requirements | Skill Set |
|---|---|---|
| Ransomware Attacks | Strong programming skills (Python, C++), cryptography knowledge, understanding of encryption algorithms, knowledge of operating systems (Windows, Linux). | Software development, cryptography, security analysis, network administration. |
| Distributed Denial-of-Service (DDoS) Attacks | Deep understanding of network protocols, ability to create and manage botnets, knowledge of network infrastructure, and tools to manage large-scale attacks. | Network engineering, security analysis, scripting, system administration. |
| Phishing Attacks | Social engineering skills, ability to create convincing phishing emails or messages, knowledge of web development and email protocols. | Social engineering, web development, email protocols, psychology. |
| Data Breaches | Advanced knowledge of database systems, network security, and vulnerability exploitation. | Database administration, network security, penetration testing, ethical hacking. |
Legal and Ethical Considerations
The allure of substantial financial gain often overshadows the crucial considerations of legality and ethics in cybercrime. While the potential for significant returns exists, the associated risks are immense, ranging from severe legal penalties to the erosion of personal integrity. This section will explore the multifaceted nature of these considerations, providing a balanced perspective on the dangers involved.Understanding the legal landscape surrounding cybercrime is essential for anyone considering such activities.
Navigating this complex web of laws and regulations requires a deep comprehension of both national and international legal frameworks. The penalties for cybercrime are substantial, varying based on the severity of the offense and the jurisdiction involved. This includes imprisonment, substantial fines, and a permanent criminal record that can impact future opportunities.
Legal Ramifications of Cybercrime
Cybercrime encompasses a broad spectrum of illegal activities, from unauthorized access to sensitive data to sophisticated financial fraud. These actions often violate numerous laws, including those related to data protection, intellectual property, and financial transactions. The legal ramifications can extend beyond national borders, requiring international cooperation and coordination among legal systems to address cross-border cybercrimes.
Ethical Implications of Cybercrime
The ethical implications of cybercrime are profound and far-reaching. Engaging in such activities can lead to significant harm to individuals, organizations, and society as a whole. The violation of trust, the theft of personal information, and the disruption of critical systems are just a few examples of the potential harm. Ethical considerations should always outweigh the potential financial rewards when evaluating any action.
Penalties and Consequences for Cybercrime
Penalties for cybercrime vary considerably based on the nature of the crime and the jurisdiction. Crimes like unauthorized access to computer systems or financial fraud can lead to imprisonment, substantial fines, and other severe penalties. The severity of the penalties is often tied to the extent of the damage caused and the intent behind the criminal act.
Comparison of Different Legal Frameworks
Different legal frameworks and jurisdictions have varying approaches to cybercrime. Some countries have more robust laws and regulations aimed at protecting digital assets and data. Others may be lagging behind in the development of comprehensive cybercrime legislation. These differences in legal frameworks can create significant challenges for law enforcement agencies and individuals involved in cross-border cybercrime investigations.
Table Comparing Legal and Ethical Implications of Different Cybercrime Methods
| Cybercrime Method | Legal Implications | Ethical Implications |
|---|---|---|
| Unauthorized Access to Data | Violation of data protection laws, potential fines and imprisonment. | Violation of privacy and trust, potential for significant harm to individuals. |
| Distributed Denial of Service (DDoS) Attacks | Violation of service disruption laws, potential fines and imprisonment. | Disruption of services and access for legitimate users, significant financial and reputational harm to victims. |
| Phishing Scams | Violation of fraud laws, potential fines and imprisonment. | Deception and exploitation of individuals, leading to financial loss and emotional distress. |
| Malware Distribution | Violation of software licensing and intellectual property laws, significant fines and imprisonment. | Infliction of harm to individuals and organizations, damage to reputation, and financial loss. |
Countermeasures and Prevention

The pursuit of financial gain through cybercrime is a complex and ever-evolving threat. Effective countermeasures require a multifaceted approach that goes beyond simply reacting to attacks. Proactive measures, coupled with robust security practices, are essential to deterring high-volume cybercrime. This section delves into strategies for preventing such crimes, highlighting security measures and best practices, and emphasizing the importance of cybersecurity awareness training.A comprehensive strategy for combating cybercrime requires a multi-layered defense.
This includes strong technical safeguards, robust security policies, and a culture of cybersecurity awareness. Preventing significant financial losses necessitates a proactive approach to risk management and threat intelligence.
Strategies for Preventing High-Volume Cybercrime
Preventing large-scale cybercrime involves a multi-faceted approach, focusing on both technical security and human factors. This includes implementing strong security protocols, investing in advanced threat detection systems, and fostering a culture of cybersecurity awareness within the organization. Regular security audits and vulnerability assessments are crucial for identifying and addressing potential weaknesses.
Security Measures and Best Practices
Robust security measures are fundamental to preventing high-volume cybercrime. These include:
- Strong Password Policies: Enforcing complex password requirements, regular password changes, and the use of multi-factor authentication (MFA) significantly reduce the risk of unauthorized access. Password managers and strong, unique passwords for each account are critical.
- Network Segmentation: Isolating sensitive data and systems on separate networks limits the impact of a breach. This isolates critical data, hindering attackers from accessing sensitive data.
- Endpoint Security: Implementing robust endpoint security software that detects and prevents malware, ransomware, and other threats is essential. Regular software updates are vital for patching known vulnerabilities.
- Data Loss Prevention (DLP): Implementing DLP tools and policies to control the movement and access of sensitive data is a critical security measure. DLP systems prevent sensitive data from leaving a protected environment, reducing the risk of data breaches.
Examples of Successful Cybercrime Prevention Efforts
Numerous organizations have implemented successful cybercrime prevention strategies. These range from small businesses proactively implementing strong password policies to large corporations investing heavily in advanced security technologies. The success of these initiatives underscores the importance of a holistic approach that combines technical measures with human training.
Importance of Cybersecurity Awareness Training
Employee training programs are crucial in fostering a culture of cybersecurity awareness. Such training should focus on recognizing phishing attempts, understanding secure password practices, and recognizing potential social engineering tactics.
Security Measures and Effectiveness
| Security Measure | Effectiveness Against Cybercrime | Explanation |
|---|---|---|
| Strong Password Policies | High | Strong passwords and MFA make unauthorized access significantly harder. |
| Network Segmentation | Medium to High | Limits the impact of a breach to a contained network segment. |
| Endpoint Security Software | High | Proactively detects and prevents malware, ransomware, and other threats. |
| Data Loss Prevention (DLP) | High | Controls the movement and access of sensitive data, preventing breaches. |
| Cybersecurity Awareness Training | Medium to High | Reduces the risk of human error and social engineering attacks. |
Illustrative Case Studies
Cybercrime, especially large-scale operations targeting organizations, often leaves a trail of significant damage. Understanding these operations through case studies provides valuable insights into motivations, methods, and the broader impact on victims and society. This section delves into real-world examples, highlighting the devastating consequences and prompting a critical examination of security measures.Analyzing past incidents offers crucial lessons for developing and implementing effective preventative measures.
By studying the tactics, techniques, and procedures (TTPs) used in successful attacks, organizations can bolster their defenses against similar threats in the future.
Large-Scale Cyberattacks on Organizations
Large-scale cyberattacks on organizations, unlike individual targeting, often involve sophisticated techniques and significant financial motivations. These attacks exploit vulnerabilities in systems and networks to steal sensitive data, disrupt operations, or cause financial damage. They are often conducted by organized crime groups or state-sponsored actors.
The NotPetya Ransomware Incident (2017)
The NotPetya ransomware attack, a devastating cyberattack in 2017, serves as a prime example of a large-scale cybercrime operation. This wasn’t just a ransomware attack; it was a wiper malware designed to inflict maximum disruption and damage. Its propagation was exceptionally effective, causing significant disruptions across various industries, including shipping, manufacturing, and government agencies. The attack demonstrated the devastating impact of highly sophisticated and rapidly spreading malware.
The SolarWinds Supply Chain Attack (2020)
The SolarWinds Orion platform supply chain attack in 2020 highlights the vulnerabilities of seemingly secure systems. Attackers exploited a trusted software provider to compromise numerous organizations’ networks. This case demonstrates the potential for widespread damage through seemingly benign supply chains. The attack showcased the potential for a sophisticated, long-term campaign that was hard to detect and eradicate.
Impact on Victims and Society
These incidents result in significant financial losses for organizations. Beyond financial costs, reputational damage and operational disruption can have long-term effects. Trust in organizations and the overall stability of the digital infrastructure can be compromised. The incident’s effect on society often ripples through various sectors, affecting industries dependent on uninterrupted operations.
Summary Table of Major Cybercrime Incidents
| Incident | Target | Methods | Outcomes |
|---|---|---|---|
| NotPetya | Global organizations | Wiping malware, exploiting vulnerabilities | Significant financial losses, operational disruption |
| SolarWinds | Multiple organizations | Supply chain compromise | Widespread network compromise, espionage |
| WannaCry | Global organizations | Ransomware | Significant financial losses, operational disruption |
Visual Representations of Cybercrime
Visual representations are crucial for understanding and combating cybercrime. They transform complex data flows and attack vectors into easily digestible formats, aiding in threat identification, incident response, and preventative measures. By visualizing the intricate web of cybercrime, security professionals can more effectively pinpoint vulnerabilities and implement targeted solutions.
Visualizing Attack Paths and Network Structures
Network diagrams are fundamental in visualizing the intricate pathways cybercriminals utilize. These diagrams illustrate the interconnectedness of systems, highlighting vulnerabilities and attack points. They depict how malicious actors exploit network structures to gain unauthorized access. Furthermore, these diagrams facilitate a better understanding of the attacker’s modus operandi, enabling proactive security measures to be implemented.
Data Flow Diagrams and Their Importance
Data flow diagrams provide a clear picture of how data moves through a system. These diagrams are invaluable in understanding data vulnerabilities and potential attack points. They visually represent data flows, identifying where data is vulnerable to interception, modification, or destruction. This visualization is critical for security professionals to assess the risk and prioritize protection measures.
Presenting Complex Cybercrime Information Visually
Visualizations are essential for conveying complex cybercrime information to diverse audiences. Utilizing charts, graphs, and diagrams simplifies intricate details, enabling stakeholders to grasp the essence of the threat without being overwhelmed by technical jargon. Using clear and concise visual aids promotes effective communication and understanding. For instance, a Sankey diagram can visually represent the flow of funds in a money laundering scheme.
Heatmaps can highlight areas of high vulnerability within a network.
Examples of Visual Representations in Cybersecurity
| Visual Representation | Application in Cybersecurity |
|---|---|
| Network Diagrams | Identifying attack paths, visualizing network infrastructure, pinpointing vulnerabilities, planning incident response |
| Data Flow Diagrams | Understanding data movement, identifying data vulnerabilities, assessing risk, implementing security controls |
| Attack Trees | Structuring possible attack scenarios, identifying critical vulnerabilities, assessing the potential impact of attacks |
| Threat Maps | Visualizing cyber threats across geographical areas, understanding threat trends, prioritizing security measures |
| Timeline Charts | Tracking events during a cyberattack, identifying critical points, enabling better incident response |
Visual Representation of a Typical Cybercrime Attack Process
A typical cybercrime attack process, visually represented, can be displayed as a flowchart. The flowcharts start with reconnaissance, followed by the exploitation phase, gaining access, and finally, data exfiltration or other malicious activities. Each step can be represented with a different shape, color, or symbol. For instance, the reconnaissance phase could be represented by a magnifying glass icon, the exploitation phase by a hacking tool icon, and data exfiltration by a data transfer icon.
The arrows connecting these shapes visually illustrate the progression of the attack.
The Evolving Nature of Cybercrime
The digital landscape is constantly shifting, and cybercriminals are quick to adapt. This dynamic environment necessitates a constant vigilance and proactive approach to cybersecurity. Understanding the evolving nature of cybercrime is crucial for organizations and individuals to stay ahead of potential threats.Cybercrime is not a static entity; it adapts and evolves with advancements in technology. New vulnerabilities are constantly emerging, and cybercriminals are constantly developing new tactics to exploit them.
This necessitates a proactive approach to security, encompassing both technical measures and a keen awareness of emerging trends.
Cybercrime Trends, How to make 5 million a day in cybercrime
The realm of cybercrime is characterized by a constant flux of new methods and targets. Phishing attacks, once relatively straightforward, are now increasingly sophisticated, employing social engineering tactics tailored to specific individuals and organizations. Ransomware attacks, once primarily targeting large corporations, have expanded to encompass small businesses and even individuals. Cryptocurrency, with its anonymity and decentralized nature, has become a crucial component in many cybercriminal operations.
Impact of New Technologies
The emergence of new technologies has both amplified existing cybercrime threats and created entirely new avenues for attacks. The increasing use of the Internet of Things (IoT) devices, for instance, has opened up a vast network of potential entry points for malicious actors. The rise of artificial intelligence (AI) has the potential to both enhance cybercrime defenses and facilitate new attack vectors, including the creation of highly realistic deepfakes.
The proliferation of mobile devices has made users vulnerable to targeted attacks through SMS phishing or malware disguised as legitimate apps.
Staying Updated on Emerging Threats
The speed at which cyber threats evolve necessitates a commitment to ongoing learning and adaptation. Cybersecurity professionals, businesses, and individuals must stay informed about the latest vulnerabilities, attack vectors, and trends in the cybercrime landscape. This includes subscribing to cybersecurity newsletters, attending relevant conferences, and engaging in continuous professional development.
Adapting Security Measures
Security measures must be proactive and adaptable to effectively counter evolving cybercrime trends. Organizations should implement robust multi-factor authentication (MFA) systems, regularly update software and hardware, and educate employees about the latest threats. The focus should be on implementing layered security approaches, combining technical controls with human awareness training.
Evolution of Cybercrime Methods
| Era | Primary Method | Key Characteristics |
|---|---|---|
| Early Internet (1990s-2000s) | Email-based phishing, simple viruses | Limited sophistication, focused on exploiting basic vulnerabilities. |
| Social Media Era (2010s) | Social engineering, targeted phishing | Exploiting social media platforms for information gathering and attacks. |
| IoT & Mobile Age (2020s) | Ransomware-as-a-service, IoT device exploitation | Increased sophistication, targeting diverse devices and networks. |
| AI-Powered Attacks (Present & Future) | Automated attacks, AI-generated phishing | Highly automated and targeted attacks, potentially leading to widespread damage. |
Final Wrap-Up
In conclusion, the pursuit of making millions daily through cybercrime is not only highly improbable but also ethically reprehensible and carries severe legal consequences. The sheer scale of resources and technical expertise needed, coupled with the inherent risks and challenges, make this goal an unattainable fantasy for most. The article has thoroughly examined the methods, feasibility, and ethical implications of such endeavors, emphasizing the importance of robust cybersecurity measures and ethical conduct.
Detailed FAQs
What are the most common types of cybercrime targeting financial gain?
Common methods include ransomware attacks, phishing scams, and various forms of credit card fraud. Each method exploits vulnerabilities in systems and individuals to gain financial benefits.
What are the legal consequences of cybercrime?
Penalties for cybercrime vary significantly depending on the specific crime and jurisdiction. They can range from substantial fines to lengthy prison sentences.
What are some effective security measures against cybercrime?
Implementing strong passwords, using multi-factor authentication, keeping software updated, and practicing cautious online behavior are crucial steps in preventing cyberattacks.
Is there a way to track and identify the perpetrators of high-profile cybercrime operations?
Law enforcement agencies utilize sophisticated forensic techniques and international collaborations to track down cybercriminals, but successful prosecution often hinges on the complexity of the operation and the digital footprints left behind.





