Negotiating Ransomware Attacks A Guide
How to negotiate ransomware attacks a strategic guide sets the stage for understanding the complex world of ransomware. This guide delves into the intricacies of handling these cyberattacks, from proactive security measures to post-incident recovery strategies. We’ll explore various negotiation tactics, legal considerations, and the critical role of a well-defined incident response plan.
This guide will arm you with the knowledge to navigate the perilous landscape of ransomware, empowering you to minimize the impact and maximize your chances of a successful outcome.
Introduction to Ransomware Negotiation
Ransomware attacks are a significant cybersecurity threat, impacting organizations of all sizes and industries. These attacks involve malicious software that encrypts critical data, demanding a ransom payment in exchange for its release. The financial and reputational damage caused by these attacks can be devastating, and the decision of whether or not to negotiate is a complex one that requires careful consideration.The impact of ransomware extends beyond the immediate financial cost.
Loss of operational efficiency, disruption of business processes, and damage to customer trust are all potential consequences. Furthermore, the potential for data breaches and the exposure of sensitive information adds another layer of complexity to the situation.
Types of Ransomware
Ransomware attacks manifest in various forms, each with unique characteristics. Understanding these types is crucial for developing an effective incident response plan. Locker ransomware, for example, completely locks users out of their systems, rendering them unusable until the ransom is paid. Crypto-ransomware, on the other hand, encrypts files, making them inaccessible without the decryption key. More sophisticated variants, like double extortion ransomware, steal data before encrypting it, threatening to leak it publicly if the ransom isn’t paid.
Approaches to Ransomware Negotiation
Negotiation strategies for ransomware attacks are not a simple binary choice. Organizations need a multi-faceted approach that weighs the potential benefits against the risks. A direct negotiation approach involves contacting the attackers and negotiating the ransom amount. Alternatively, some organizations may decide to take a non-negotiation approach, opting instead to focus on incident response and recovery without engaging with the perpetrators.
The best course of action depends on the specifics of the attack, the organization’s resources, and the legal and regulatory environment.
Importance of a Well-Defined Incident Response Plan
A robust incident response plan is critical in mitigating the impact of a ransomware attack. This plan should Artikel procedures for detecting, containing, responding to, and recovering from a ransomware attack. The plan should address various scenarios, including the decision to negotiate. Having a pre-determined plan minimizes the chaos and ensures a more organized and effective response.
Key Stages of a Ransomware Incident Response Plan
A well-structured incident response plan provides a roadmap for managing a ransomware attack. The plan should be reviewed and updated regularly to reflect the evolving nature of ransomware threats.
Navigating ransomware attacks requires a strategic approach. Understanding vulnerabilities like those detailed in the Azure Cosmos DB Vulnerability Details is crucial. Knowing potential weaknesses in your systems allows for better defensive strategies and paves the way for a more robust negotiation process when an attack occurs. Ultimately, a strong security posture is key to successful negotiation.
| Stage | Description | Roles | Timeline |
|---|---|---|---|
| Preparation | Developing and maintaining the incident response plan, including procedures for identifying, containing, and recovering from ransomware attacks. This stage also involves training personnel on incident response procedures. | Security team, IT staff, legal counsel, senior management | Ongoing |
| Detection and Analysis | Identifying the ransomware attack, analyzing its characteristics, and determining the scope of the damage. | Security monitoring team, incident response team | Immediate |
| Containment and Eradication | Isolating infected systems to prevent further spread, removing the malware, and restoring affected systems. | IT staff, security team | Within 24-48 hours |
| Recovery and Post-Incident Activity | Restoring data and systems, conducting a thorough post-incident review to identify weaknesses and improve future resilience, and communicating with affected parties. | IT staff, security team, legal counsel | Days to weeks |
Understanding the Threat Landscape: How To Negotiate Ransomware Attacks A Strategic Guide
Ransomware attacks are no longer a niche problem; they’ve become a pervasive threat affecting organizations of all sizes and sectors. Understanding the intricate dynamics of these attacks is crucial for developing effective negotiation strategies. This involves recognizing the actors, their motivations, the diverse attack methods, and the ever-evolving nature of the threat itself. By delving into the threat landscape, we can better equip ourselves to counter these malicious activities and minimize their impact.Understanding the players, their motivations, and their tactics is vital for crafting effective negotiation strategies.
This knowledge allows us to anticipate their behavior, understand their demands, and tailor our responses accordingly. By dissecting the methods they employ, we can anticipate their potential moves and fortify our defenses against future attacks.
Key Actors in Ransomware Attacks
Ransomware attacks are not conducted in a vacuum; various actors play distinct roles. These actors range from sophisticated criminal organizations to individuals, and their motivations and capabilities vary widely.
- Criminal Organizations: These groups often operate as highly organized cybercrime syndicates, employing advanced techniques to target vulnerable organizations and individuals. They typically focus on maximizing profit by demanding significant ransom payments. Examples include groups like REvil, Conti, and LockBit, who have carried out large-scale attacks, generating significant revenue.
- State-Sponsored Actors: Nation-states and their affiliated groups may also be involved in ransomware attacks. These attacks are frequently motivated by espionage, disruption, or political objectives, rather than solely financial gain. The targets are often critical infrastructure or political adversaries.
- Hacktivists: Hacktivist groups, driven by ideological or political agendas, may launch ransomware attacks against organizations they perceive as adversaries. Their attacks may be less focused on financial gain and more on achieving publicity or disrupting operations.
- Individuals: Individual hackers, sometimes motivated by financial gain or personal notoriety, may launch smaller-scale ransomware attacks, often using readily available tools and techniques.
Motivations and Tactics of Ransomware Groups
The motivations behind ransomware attacks vary significantly depending on the actors involved. Understanding these motivations is crucial to anticipating their behavior during negotiations.
- Financial Gain: This is the primary motivation for many criminal ransomware groups. They seek to maximize their financial returns through ransom demands and exploit vulnerabilities to achieve this goal.
- Political Objectives: State-sponsored actors and hacktivists may leverage ransomware attacks to disrupt operations or target political opponents. These attacks are less about financial gain and more about achieving specific political goals.
- Ideological Motivations: Hacktivist groups may utilize ransomware to target organizations they perceive as opposing their ideologies.
Comparison of Ransomware Attack Methodologies
Various methods are used in ransomware attacks, each with unique characteristics and implications for negotiation. Understanding these differences is essential to tailor responses appropriately.
- Double-Extortion: In double-extortion attacks, the attackers threaten to leak stolen data alongside encrypting systems. This tactic increases the pressure on victims to pay.
- Triple-Extortion: This tactic involves threats to leak data, disrupt operations, and threaten to target customers or partners.
- Supply Chain Attacks: Attackers target software or systems used by the victim’s vendors or suppliers, encrypting their data and potentially impacting multiple organizations.
Evolving Nature of Ransomware Threats
The ransomware threat landscape is constantly evolving, with new techniques and approaches emerging regularly. This requires continuous adaptation and vigilance.
- Rise of Ransomware-as-a-Service (RaaS): This model allows less-skilled actors to launch attacks by leveraging the infrastructure and tools of more sophisticated groups.
- Increased Sophistication: Attackers are employing more advanced techniques to bypass security measures and target vulnerabilities effectively.
- Focus on Critical Infrastructure: Attackers are increasingly targeting critical infrastructure sectors, highlighting the potential for widespread disruption and damage.
Ransomware Groups and Characteristics
This table summarizes key characteristics of various ransomware groups.
| Group Name | Tactics | Targets | Reputation |
|---|---|---|---|
| REvil | Double-extortion, data leaks | Large enterprises, software companies | High notoriety for leaks |
| LockBit | Data encryption, demanding high ransoms | Wide range of businesses | Known for sophisticated operations |
| Conti | Data exfiltration, targeting specific sectors | Large corporations, government agencies | High profile attacks and notoriety |
| BlackMatter | Data encryption, ransomware-as-a-service | Organizations across industries | Prominent in recent years |
Pre-Negotiation Strategies

Ransomware attacks are a significant threat to organizations of all sizes, impacting not only finances but also operational efficiency and reputation. Proactive measures are crucial in minimizing the risk and damage associated with such attacks. A robust pre-negotiation strategy should prioritize preventative measures, allowing organizations to respond effectively and swiftly if an attack does occur.Effective pre-negotiation strategies are fundamentally about reducing the attack surface and improving the organization’s resilience to ransomware.
This involves implementing a comprehensive approach that encompasses proactive security measures, robust backup and recovery strategies, employee training, and strong access controls. These strategies, while not guaranteeing complete immunity, significantly reduce the potential damage and recovery time if a ransomware incident occurs.
Proactive Security Measures
Proactive security measures are the cornerstone of a strong defense against ransomware attacks. These measures encompass a wide range of technologies and processes aimed at preventing the initial compromise that allows attackers to deploy ransomware. Stronger security measures reduce the likelihood of an attack in the first place. Implementing multi-layered security protocols, including firewalls, intrusion detection systems, and endpoint protection, is vital.
Regular security assessments and penetration testing help identify vulnerabilities and address them before they can be exploited. Staying up-to-date with the latest security patches and software updates is also crucial.
Data Backups and Recovery Strategies
Data backups are a critical element of ransomware mitigation. Regular, automated backups of critical data, both on-site and off-site, ensure that even if ransomware encrypts data, organizations can restore systems and data quickly and effectively. A well-defined recovery plan, outlining the steps to follow in the event of an attack, is essential for minimizing downtime and data loss.
Cloud-based backups, for instance, can offer a secure and readily available repository for data recovery.
Employee Training and Awareness Programs
Employee training plays a vital role in preventing ransomware attacks. Educating employees about the various types of ransomware threats, phishing techniques, and safe online practices can significantly reduce the risk of successful attacks. Regular awareness programs, including simulated phishing exercises, can reinforce the importance of vigilance and help employees recognize and report suspicious emails or links. Employees should be instructed on the importance of verifying the authenticity of emails and attachments before opening them.
Strong Access Controls and Security Protocols
Strong access controls and security protocols are essential to limit the potential damage from ransomware attacks. Implementing strict access controls, such as least privilege principles and multi-factor authentication, can restrict the level of access granted to users and prevent unauthorized access to sensitive data. Regularly reviewing and updating security protocols can help keep pace with evolving threats.
Navigating ransomware attacks requires a strategic approach, and understanding legal frameworks is key. Recent developments like the Department of Justice’s new Safe Harbor policy for Massachusetts transactions, Department of Justice Offers Safe Harbor for MA Transactions , are crucial for businesses. This policy, while specific to MA, highlights the evolving landscape of legal protections surrounding these attacks, which, in turn, informs a broader strategy for negotiation.
Ultimately, a robust strategy for negotiating ransomware attacks involves anticipating and responding to the latest legal developments.
Data Backup Strategies Comparison
Regular, comprehensive backups are crucial in ransomware mitigation. This table contrasts different data backup strategies, highlighting their recovery time objectives (RTO), recovery point objectives (RPO), and associated costs.
| Strategy | Recovery Time Objective (RTO) | Recovery Point Objective (RPO) | Cost |
|---|---|---|---|
| Full Backup (Daily) | Hours to days | 24 hours or less | High |
| Incremental Backup (Daily) | Hours to days | Few hours | Medium |
| Differential Backup (Daily) | Hours to days | Few hours to a day | Medium |
| Cloud-based Backup (Daily) | Minutes to hours | Minutes to hours | Variable, often medium to high |
Note that RTO and RPO values vary depending on the specific data and the recovery plan. The cost of each strategy also depends on the infrastructure and technology involved.
Negotiation Strategies
Navigating the treacherous waters of ransomware negotiations requires a delicate balance of firmness, flexibility, and strategic thinking. A well-defined strategy can significantly influence the outcome, potentially minimizing financial losses and reputational damage. This section delves into various negotiation tactics, communication strategies, and crucial legal and ethical considerations, offering a practical framework for organizations facing this critical challenge.
Demonstrating Negotiation Tactics
Effective negotiation tactics involve a multifaceted approach. These tactics aim to establish a clear position, while simultaneously recognizing the adversary’s perspective. Understanding the adversary’s motivations and potential vulnerabilities can prove instrumental in achieving a favorable outcome. A proactive and calculated approach is key, emphasizing controlled communication and data recovery strategies.
- Negotiating from a Position of Strength: Demonstrating a firm commitment to not paying the ransom, backed by clear legal and security protocols, can often deter attackers. This includes having robust backups and incident response plans in place.
- Offering Incentives: This may involve offering a specific sum of money or the provision of certain data, in exchange for a reduced ransom demand or the return of encrypted data. This strategy requires careful consideration to avoid incentivizing future attacks.
- Employing Delay Tactics: Prolonging negotiations can give organizations time to assess the situation, strengthen their defenses, and potentially uncover weaknesses in the attacker’s demands or operations. This approach can be crucial in managing pressure.
- Leveraging Third-Party Mediation: Engaging a neutral third party, such as a cybersecurity firm or legal expert, can help facilitate communication and potentially bridge the gap between the organization and the attackers.
Effective Communication Strategies
Maintaining clear and consistent communication with ransomware actors is crucial, yet fraught with risk. Maintaining a professional, but firm, demeanor is vital to avoid escalating the situation.
- Formal Communication Channels: Using established channels, such as email or encrypted messaging platforms, for communication can enhance transparency and traceability. Documentation of all interactions is essential.
- Understanding Attacker Demands: Careful analysis of the attackers’ demands, motivations, and previous actions can provide valuable insights into their intentions and potential vulnerabilities. Identifying patterns and anomalies is vital.
- Establishing Clear Expectations: Clearly outlining expectations regarding data recovery, payment timelines, and security guarantees can help ensure that the negotiation proceeds in a predictable and controlled manner.
- Employing Professional Negotiators: Engaging specialized negotiators with experience in ransomware incidents can improve the chances of a positive outcome. This is particularly important for complex negotiations.
Legal and Ethical Considerations
Navigating ransomware negotiations demands a deep understanding of legal and ethical principles. Organizations must prioritize their legal obligations and maintain a strong ethical framework throughout the process.
- Compliance with Legal Regulations: Understanding and adhering to relevant laws and regulations regarding data privacy, financial transactions, and reporting requirements is paramount.
- Ethical Considerations: Organizations should prioritize ethical decision-making and avoid actions that could potentially incentivize future attacks. This includes resisting pressure to pay ransoms under duress.
- Seeking Legal Counsel: Consulting with legal experts is essential to ensure that all actions are compliant with applicable laws and regulations. This includes both domestic and international laws.
Potential Risks and Pitfalls
Negotiating with ransomware actors is inherently risky. Organizations must carefully weigh the potential benefits against the potential drawbacks.
- Escalation of Demands: Attackers may increase their demands during the negotiation process, leading to further financial and operational losses.
- Non-Compliance: Attackers may fail to comply with agreed-upon terms, leaving organizations with unrecovered data and a lack of assurance.
- Reputational Damage: Public disclosure of negotiations or payment of ransoms can damage an organization’s reputation and erode public trust.
Negotiation Tactics Table
| Negotiation Stage | Tactics | Potential Outcomes | Risks |
|---|---|---|---|
| Initial Contact | Establish clear communication channels, document all interactions, assess attacker demands. | Establish a baseline for negotiation, gain understanding of attacker motives. | Potential escalation of demands, lack of trust. |
| Negotiation Phase | Offer incentives, employ delay tactics, leverage third-party mediation. | Potential reduction in ransom demands, increased likelihood of data recovery. | Risk of non-compliance, increased negotiation time, potential for reputational damage. |
| Resolution | Finalize agreements, ensure data recovery, implement security improvements. | Data recovery, payment resolved, incident mitigated. | Risk of unresolved issues, attacker failure to uphold commitments. |
Post-Negotiation Strategies
Successfully negotiating a ransomware attack is a significant step, but it’s only half the battle. The true test lies in the meticulous steps taken afterward. Post-negotiation strategies ensure a swift return to normalcy and prevent future vulnerabilities. These strategies include thorough system restoration, robust security enhancements, and diligent incident reporting and analysis.A successful post-negotiation strategy minimizes the long-term impact of the attack and builds resilience against future threats.
This proactive approach, which involves a clear understanding of the incident, swift remediation, and the implementation of improved security protocols, is crucial for organizational recovery and maintaining business continuity.
Restoring Systems and Data, How to negotiate ransomware attacks a strategic guide
Effective restoration is paramount to recovering from a ransomware attack. It involves meticulously recovering encrypted files, restoring backups, and re-establishing critical systems. The chosen restoration method should prioritize data integrity and minimize the risk of reinfection. This might involve a phased approach, starting with essential systems and gradually restoring others. A comprehensive data recovery plan, developed and tested before an incident, is essential.
This plan should detail specific procedures for restoring different data types and prioritize critical systems.
Long-Term Security Improvements
Preventing future attacks is crucial. A thorough review of existing security protocols is essential, identifying weaknesses exploited by the attackers. Implementing enhanced security measures is paramount, such as robust intrusion detection systems, multi-factor authentication, and security awareness training for employees. Patching vulnerabilities promptly and regularly is vital to fortifying the defenses against emerging threats. Consider implementing zero-trust architecture, where every access request is verified, reducing the attack surface.
Investing in a Security Information and Event Management (SIEM) system can provide valuable insights into potential threats.
Incident Reporting and Analysis
Thorough incident reporting and analysis are vital for learning from the attack and preventing similar incidents in the future. Reporting to authorities, regulatory bodies, and stakeholders is often mandatory and essential for transparency and accountability. A detailed incident report should Artikel the attack vector, the impact, the remediation process, and lessons learned. This report becomes a valuable resource for future security improvements.
The analysis should identify vulnerabilities, gaps in security protocols, and areas for improvement in response strategies.
Post-Incident Actions Summary
| Action | Description | Responsible Party | Timeline |
|---|---|---|---|
| Data Recovery | Restore encrypted files and critical systems from backups. | IT/Security Team | Within 24-72 hours (depending on backup frequency and complexity) |
| Security Review | Identify vulnerabilities exploited in the attack. | Security Team, IT | Immediately following restoration |
| Security Enhancement | Implement enhanced security measures (e.g., intrusion detection, MFA). | Security Team, IT | Within 1-2 weeks |
| Incident Reporting | Report the incident to relevant authorities, regulatory bodies, and stakeholders. | Compliance Officer, Legal Team | Within 72 hours of incident discovery |
| Post-Incident Analysis | Analyze the incident to identify lessons learned and areas for improvement. | Security Team, IT | Ongoing, as needed |
Case Studies and Examples
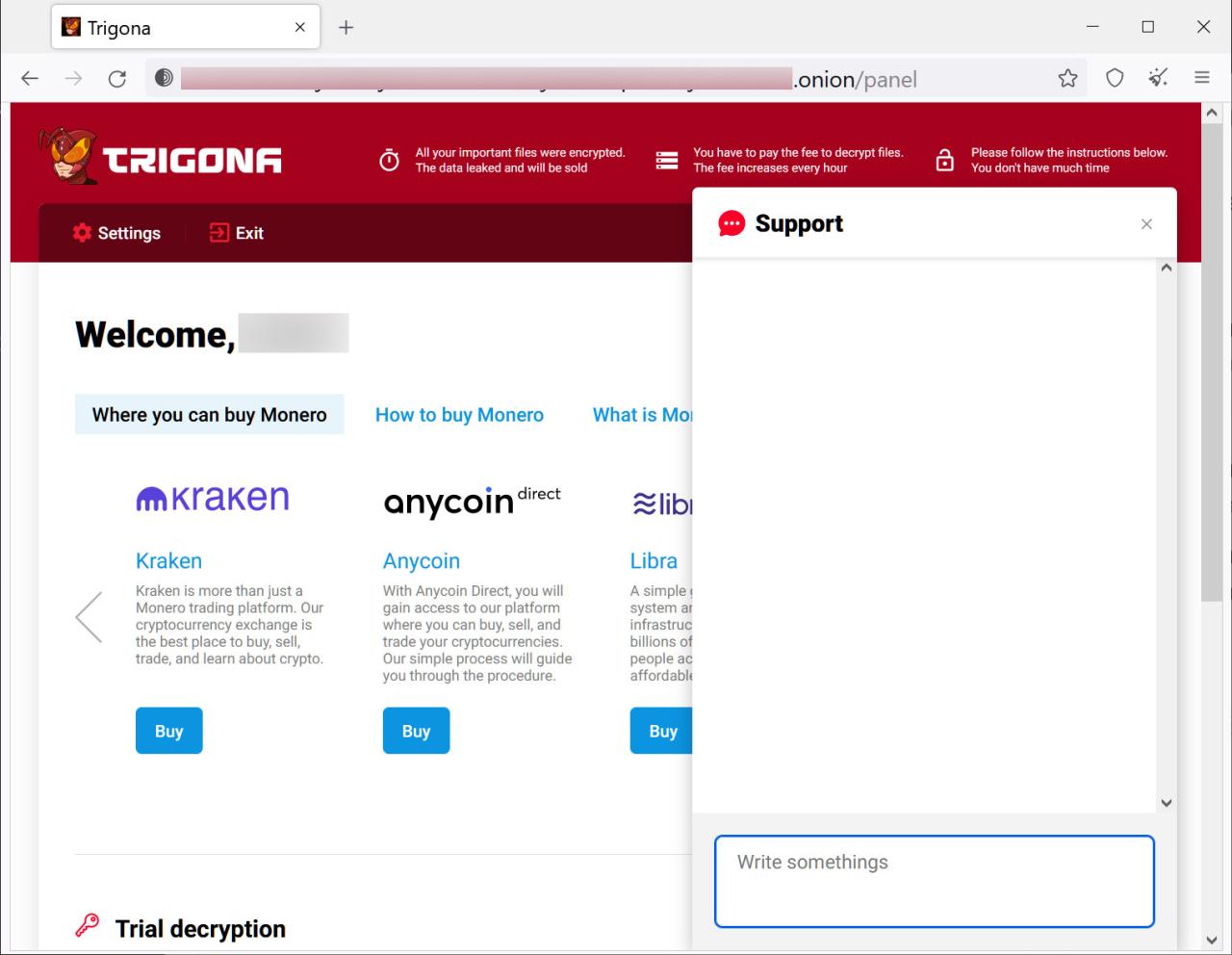
Ransomware attacks are a growing threat, and understanding how previous negotiations have unfolded is crucial for developing effective strategies. Analyzing successful and unsuccessful cases provides valuable insights into the factors influencing outcomes and highlights the importance of a well-defined negotiation approach. This section will delve into real-world examples, dissecting the strategies employed and the results achieved.Analyzing successful and unsuccessful ransomware negotiations offers invaluable lessons.
Negotiating ransomware attacks requires a strategic guide, focusing on swift response and calculated risk assessment. A critical component of this strategy involves proactively deploying AI-powered tools like those discussed in Deploying AI Code Safety Goggles Needed , to identify and mitigate vulnerabilities in your systems before they’re exploited. This approach ensures a more resilient posture against future attacks, ultimately strengthening your negotiation position and reducing the likelihood of a successful ransomware campaign.
By understanding the intricacies of past incidents, organizations can refine their approaches to enhance their chances of a positive outcome. The impact of various negotiation tactics on the final result will be examined, revealing the significance of preparedness and a strategic plan.
Successful Ransomware Negotiation Examples
Successful negotiations often involve a blend of proactive measures and calculated concessions. A common theme in successful cases is the establishment of clear communication channels and adherence to a well-defined negotiation strategy. Companies that prioritized data backups and had robust incident response plans often saw positive results. This proactive approach demonstrates the importance of preparedness.
Unsuccessful Ransomware Negotiation Examples and Lessons Learned
Conversely, unsuccessful negotiations often highlight the pitfalls of a lack of preparedness and a lack of clear communication. A common thread in unsuccessful cases is the failure to prioritize data backups or the absence of a comprehensive incident response plan. This illustrates the critical role of proactive measures in mitigating the impact of ransomware attacks. Often, hasty or poorly considered decisions lead to unfavorable outcomes.
Companies must avoid making decisions under pressure, instead, relying on a structured process.
Impact of Negotiation Approaches on Outcomes
Different negotiation approaches yield varied outcomes. A collaborative approach, where both parties work towards a mutually beneficial resolution, often results in a favorable outcome for the victim. In contrast, a confrontational approach can often escalate the situation, hindering a positive resolution. The choice of negotiation approach hinges on several factors, including the nature of the attack, the involved parties, and the desired outcome.
Furthermore, understanding the motivations and objectives of the attackers can significantly impact the negotiation process. A clear understanding of the attacker’s objectives can guide negotiators towards a more effective strategy.
Table Summarizing Key Takeaways from Case Studies
| Case Study | Negotiation Approach | Outcome | Key Lessons |
|---|---|---|---|
| Company A | Collaborative, involving legal counsel and security experts | Successful recovery of data with minimal financial loss | Proactive measures like data backups and robust incident response plans are crucial. |
| Company B | Confrontational, refusing to pay ransom | Data loss and significant financial impact | Avoidance of confrontation, without clear backups, often leads to negative outcomes. |
| Company C | Negotiation via intermediaries | Successful negotiation of reduced ransom payment | Using intermediaries can be effective in establishing trust and communication. |
| Company D | Negotiation through a third-party negotiator | Successful resolution without financial loss | External assistance can often facilitate smoother negotiations. |
Legal and Regulatory Considerations
Navigating a ransomware attack isn’t just about technical prowess; it’s a complex legal and regulatory minefield. Understanding the specific laws and regulations in your jurisdiction is crucial. Non-compliance can lead to severe penalties, potentially crippling your organization. This section dives into the critical legal considerations for effectively handling ransomware incidents.Legal frameworks and regulations related to ransomware attacks vary significantly by jurisdiction, often reflecting broader cybersecurity and data protection laws.
This section details the crucial legal aspects of responding to a ransomware attack.
Legal Frameworks and Regulations
Ransomware attacks trigger a cascade of legal obligations depending on the type of data compromised, the location of the affected parties, and the specific industry the victim operates in. These obligations often relate to data protection, cybersecurity, and reporting requirements.
Implications of Non-Compliance
Failing to comply with these regulations can lead to substantial penalties. These penalties can range from hefty fines to criminal prosecution, depending on the severity of the violation and the specific regulations involved. For example, in cases of data breaches involving personally identifiable information (PII), penalties can be substantial. Furthermore, reputational damage can be equally devastating, eroding trust and impacting future business operations.
Importance of Legal Counsel During Ransomware Incidents
Engaging legal counsel promptly during a ransomware incident is paramount. Legal experts can advise on the specific legal requirements applicable to the situation, helping organizations navigate the complex regulatory landscape and mitigate potential liabilities. Their insights can guide decision-making processes, ensure compliance, and ultimately help minimize the impact of the attack. Legal counsel can also advise on the best strategies for handling negotiations with the attackers.
Examples of Regulatory Requirements in Different Jurisdictions
Regulations vary widely across different jurisdictions. The General Data Protection Regulation (GDPR) in the European Union, for instance, places strict requirements on organizations handling personal data. Similar regulations exist in the United States, like the Health Insurance Portability and Accountability Act (HIPAA) for healthcare data, and the California Consumer Privacy Act (CCPA) for consumer data. Understanding these specific requirements is vital for avoiding legal pitfalls.
Key Legal Requirements for Handling Ransomware Attacks
| Jurisdiction | Law/Regulation | Requirement | Penalties |
|---|---|---|---|
| United States (HIPAA) | Health Insurance Portability and Accountability Act | Report breaches to affected individuals and authorities within a specified timeframe. | Fines, civil penalties, potential criminal charges. |
| European Union (GDPR) | General Data Protection Regulation | Implement appropriate technical and organizational measures to protect personal data; notify authorities of breaches promptly. | Significant fines, potential criminal charges. |
| California (CCPA) | California Consumer Privacy Act | Provide consumers with specific rights regarding their personal data; comply with breach notification requirements. | Fines, potential lawsuits. |
| United Kingdom (Data Protection Act) | Data Protection Act | Comply with breach notification requirements; demonstrate appropriate security measures. | Fines, potential criminal charges. |
Developing a Robust Response Plan

A well-defined ransomware response plan is crucial for minimizing damage and accelerating recovery. A comprehensive plan acts as a roadmap, guiding organizations through the complex and often stressful process of handling a cyberattack. This plan should not be a static document; it needs to be regularly reviewed and updated to reflect evolving threats and the organization’s changing infrastructure.A robust response plan goes beyond simply identifying the problem; it anticipates potential challenges and Artikels specific actions for each stage of the incident.
This proactive approach is vital for containing the damage, mitigating reputational harm, and ensuring swift restoration of operations. It also significantly reduces the time it takes to restore operations and minimizes the financial impact.
Need for a Comprehensive and Adaptable Incident Response Plan
A comprehensive incident response plan is essential for effectively handling a ransomware attack. It should encompass all aspects of the attack, from initial detection to post-incident recovery. The plan must be adaptable to various attack vectors and evolving threat landscapes. This adaptability ensures that the plan remains relevant and effective even as ransomware techniques and targets shift.
Organizations should recognize that ransomware attacks are not static events; they often involve sophisticated tactics that necessitate a flexible and up-to-date response strategy.
Roles and Responsibilities of Different Teams in a Response Plan
Clearly defined roles and responsibilities within the incident response team are critical for efficient action. This clarity ensures that everyone knows their specific tasks and who to report to during a crisis. This structured approach streamlines communication and decision-making, preventing confusion and delays. A well-defined chain of command is vital to ensure that critical decisions are made swiftly and accurately.
Communication Protocols for Handling a Ransomware Attack
Effective communication is paramount during a ransomware attack. Establish clear communication protocols to ensure that critical information is shared promptly and accurately with stakeholders, including affected personnel, legal counsel, and the authorities. This structured approach ensures that everyone is informed and prepared to handle their assigned responsibilities effectively. A communication plan should detail who is responsible for communicating with whom, and the channels to use for various types of communication.
Importance of Regular Plan Reviews and Updates
Regular reviews and updates of the incident response plan are crucial for maintaining its effectiveness. Cybersecurity threats evolve rapidly, and new vulnerabilities emerge frequently. Therefore, the plan must be updated to reflect these changes. Regular exercises, simulations, and drills can help identify weaknesses and refine the response strategy. This ongoing refinement ensures that the plan remains relevant and effective in responding to emerging threats and the evolving threat landscape.
Roles and Responsibilities Table
| Role | Responsibilities | Communication Channels | Reporting Structure |
|---|---|---|---|
| Incident Commander | Overall direction and coordination of the response; decision-making; resource allocation. | Email, phone, secure communication channels | CEO/Executive Leadership |
| Security Analyst | Identifying the scope of the attack; analyzing the malware; monitoring network activity. | Email, secure communication tools, internal ticketing system | Incident Commander |
| Legal Counsel | Advising on legal implications of the attack; compliance with regulatory requirements. | Dedicated communication channels; secure video conferencing | Incident Commander |
| Public Relations | Managing external communication; mitigating reputational damage. | Email, phone, press releases, social media | Incident Commander |
End of Discussion
In conclusion, effectively negotiating ransomware attacks requires a multi-faceted approach that combines proactive security, strategic planning, and a deep understanding of the evolving threat landscape. This guide provides a comprehensive framework for navigating these challenges, ensuring that you are prepared to respond to and recover from ransomware incidents. Remember, the key to success lies in preparedness, clear communication, and a steadfast commitment to long-term security improvements.
Detailed FAQs
What are the most common types of ransomware?
Common ransomware types include encrypting ransomware, which encrypts files, and locker ransomware, which locks the user out of their system. Other types target specific industries or exploit vulnerabilities.
What are the key stages of a ransomware incident response plan?
Key stages include preparation, identification, containment, eradication, recovery, and lessons learned. Each stage involves specific roles and timelines to ensure a swift and effective response.
What are some proactive security measures to prevent ransomware attacks?
Proactive measures include strong passwords, multi-factor authentication, regular software updates, employee training, and strong access controls.
What are the potential risks of negotiating with ransomware attackers?
Potential risks include the attackers demanding more than originally asked for, the attacker not following through with the agreement, or the attacker using the negotiation process to gain more information. It’s critical to weigh the risks carefully against the potential benefits of recovery.