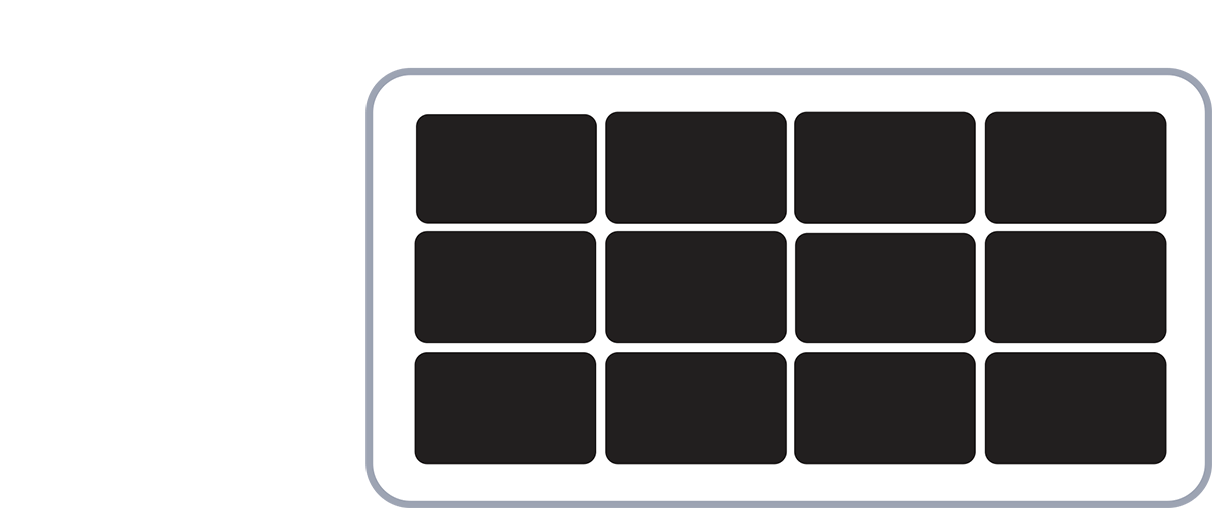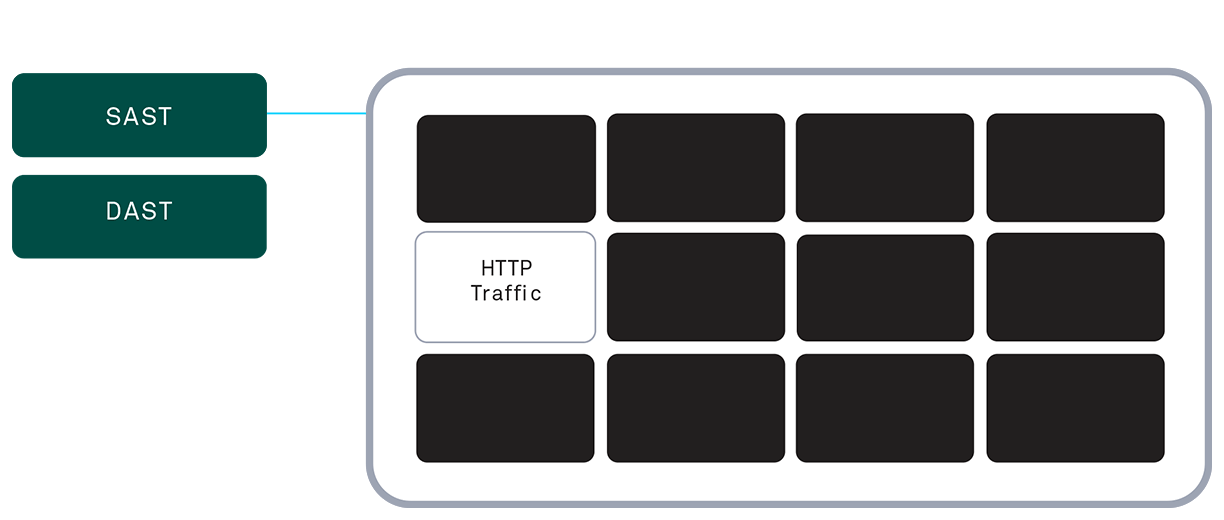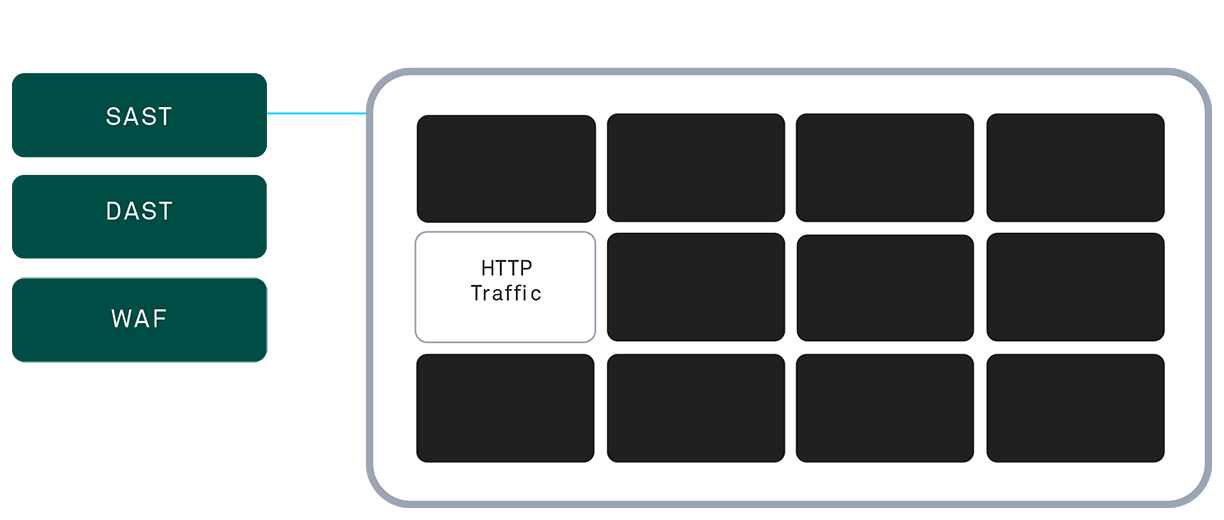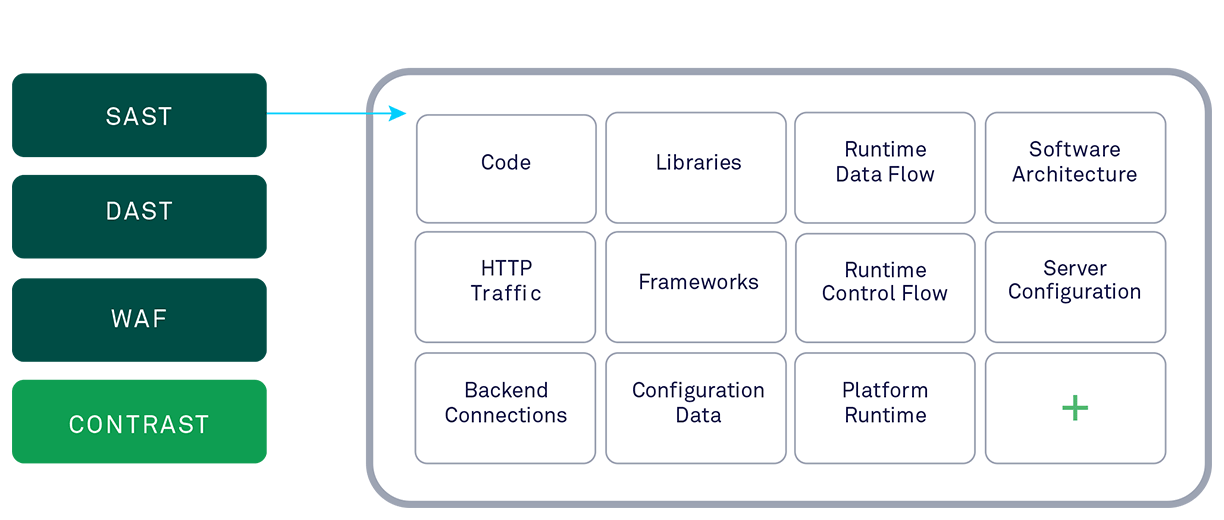
IAST, RASP, and Runtime Instrumentation Securing Apps
Iast rasp and runtime instrumentation – IAST, RASP, and runtime instrumentation are crucial for securing applications. This exploration delves into the intricacies of these methods, comparing them to traditional security approaches. We’ll cover core concepts, practical applications, potential challenges, and available tools.
Understanding IAST, RASP, and runtime instrumentation is vital for modern application security. These techniques offer a dynamic approach to identifying and preventing vulnerabilities, unlike static analysis methods that examine code without execution. This deep dive will illuminate how these tools work together to create a robust defense strategy.
Introduction to IAST, Rasp, and Runtime Instrumentation

Interactive Application Security Testing (IAST) is a dynamic application security testing method that analyzes application behavior during runtime. It observes the application’s execution flow and identifies vulnerabilities as they arise, offering a real-time perspective on potential weaknesses. This contrasts with static analysis, which examines code without execution, and dynamic analysis, which often requires separate testing environments.Runtime instrumentation is a crucial component of IAST and Rasp, enabling the observation and analysis of application behavior during execution.
It involves modifying the application’s code or binary to include monitoring points that record specific data, allowing security analysts to identify vulnerabilities and potential security risks. This process is often transparent to the end-user. Rasp, or Runtime Application Self-Protection, leverages runtime instrumentation to actively protect against attacks in real-time, whereas IAST primarily focuses on identifying vulnerabilities.
IAST Definition
IAST, or Interactive Application Security Testing, is a dynamic application security testing technique that examines the application’s behavior during runtime to detect vulnerabilities. It differs from static analysis, which analyzes the code without execution, and dynamic analysis, which often requires separate testing environments. IAST provides insights into the application’s execution flow, allowing security analysts to pinpoint potential weaknesses and vulnerabilities as they arise.
Rasp Definition
Runtime Application Self-Protection (Rasp) is a security approach that leverages runtime instrumentation to proactively prevent attacks. It actively monitors application behavior and reacts to suspicious activities, often mitigating threats before they can cause significant damage. Rasp goes beyond simply identifying vulnerabilities, actively defending against attacks.
Relationship Between IAST, Rasp, and Runtime Instrumentation
IAST utilizes runtime instrumentation to observe application behavior, identifying potential vulnerabilities. Rasp builds upon this, using runtime instrumentation to actively defend against attacks detected during the IAST process. The core concept underlying both is runtime instrumentation, the modification of an application to enable monitoring and analysis. This modification allows for the identification of security issues in IAST and the prevention of exploits in Rasp.
Differences from Other Testing Approaches
Traditional application security testing methods, like static analysis and dynamic analysis, have limitations compared to IAST and Rasp. Static analysis, which examines code without execution, can miss vulnerabilities that only appear during runtime. Dynamic analysis, while observing runtime behavior, often requires separate testing environments and might not capture all possible execution paths. IAST and Rasp, however, operate directly within the application’s runtime environment, providing a more accurate and comprehensive view of potential weaknesses.
Comparison Table
| Feature | IAST | Rasp | Static Analysis | Dynamic Analysis |
|---|---|---|---|---|
| Execution | Runtime | Runtime | Compile Time | Runtime |
| Focus | Identifying vulnerabilities | Preventing exploits | Identifying vulnerabilities | Identifying vulnerabilities |
| Data | Execution data | System data | Source code | Execution data |
Core Concepts of IAST, Rasp, and Runtime Instrumentation
Interactive Application Security Testing (IAST), Runtime Application Self-Protection (RASP), and runtime instrumentation are crucial components in modern application security. They work in concert to identify and mitigate vulnerabilities during the application’s execution, a stage where traditional static and dynamic analysis often fall short. This proactive approach is vital for protecting against sophisticated attacks that exploit vulnerabilities in the application’s code as it runs.IAST, RASP, and runtime instrumentation share a common goal: enhancing security by dynamically analyzing and modifying the application’s behavior during execution.
They each use different mechanisms and focus on distinct aspects of the application’s security posture, but all three play a critical role in a comprehensive security strategy.
Core Principles of IAST
IAST is fundamentally based on observing the application’s behavior during runtime to detect anomalies that could indicate vulnerabilities. It achieves this by injecting probes into the application code to monitor the flow of data and execution paths. These probes capture information about the application’s interactions with external resources and the internal logic, allowing for a deeper understanding of potential vulnerabilities.
A key principle is to observe the application’s response to unexpected inputs and unusual conditions, which often expose vulnerabilities.
Core Principles of RASP
RASP’s core principle is to actively protect the application by intercepting and validating potentially dangerous operations. It acts as a “security layer” within the application, monitoring and controlling access to sensitive resources and preventing malicious code execution. Instead of passively observing, RASP actively intervenes to prevent exploitation attempts, offering a proactive defense mechanism.
How Runtime Instrumentation Works
Runtime instrumentation involves modifying the application’s code at runtime to add monitoring and analysis capabilities. This is achieved by inserting instrumentation probes into the application’s codebase. These probes collect data about the application’s execution flow, including inputs, outputs, and internal states. This data is then analyzed to identify vulnerabilities or suspicious behaviors.
Key Components of a Runtime Instrumentation System
A runtime instrumentation system typically consists of several key components:
- Instrumentation Engine: This engine is responsible for identifying and inserting probes into the application’s code. It dynamically modifies the bytecode or source code to include monitoring logic. This is crucial for seamlessly integrating the instrumentation without impacting the application’s performance.
- Probe Library: A set of probes tailored to different types of vulnerabilities and application interactions. These probes collect and record specific data points, such as method calls, data flows, and resource usage. These probes are vital for capturing relevant information during execution.
- Data Collection System: This component is responsible for collecting data from the probes and storing it in a format that can be analyzed. The data collected might include input values, output values, execution paths, and resource usage. Efficient storage and retrieval are essential.
- Analysis Engine: This engine processes the collected data to identify vulnerabilities and anomalies. It compares the data against predefined security rules and patterns to detect potential threats. A well-trained analysis engine is essential for accurate detection.
Demonstrating the Process of Instrumenting an Application for IAST
To instrument an application for IAST, you need to integrate the instrumentation engine into the application’s build pipeline. The engine will identify points in the application code where probes should be inserted. These probes will be placed in critical sections such as input validation, database interactions, and external API calls. This enables monitoring of potentially vulnerable areas.
I’ve been digging into IAST (Interactive Application Security Testing) and runtime instrumentation lately, and it’s fascinating how these tools work. They’re essentially like microscopic security inspectors, looking for vulnerabilities as code runs. This got me thinking about the Department of Justice Offers Safe Harbor for MA Transactions policy , and how robust security measures like this might help prevent potential issues.
Hopefully, these types of policies can help reduce vulnerabilities in real-world applications, which is directly applicable to how IAST and runtime instrumentation can be applied to detect and prevent similar problems.
Monitoring Application Behavior During Runtime
Monitoring application behavior during runtime involves using the instrumentation probes to collect data about the application’s interactions. This data includes parameters, return values, and execution paths. This monitoring process helps track and identify potential vulnerabilities in real-time.
IAST, RASP, and runtime instrumentation are crucial for identifying vulnerabilities in code, especially as AI models become more complex. Thinking about how to deploy AI code safety measures like those discussed in Deploying AI Code Safety Goggles Needed , it’s clear that these tools are essential. Stronger security measures, like those offered by robust IAST, RASP, and runtime instrumentation, are needed to ensure our AI applications are safe and reliable.
Vulnerabilities Detected by IAST, RASP, and Runtime Instrumentation
These technologies can detect a wide range of vulnerabilities, including:
- SQL Injection: Analyzing database queries and detecting suspicious patterns in input data.
- Cross-Site Scripting (XSS): Monitoring how user input is handled and identifying potential vulnerabilities.
- Cross-Site Request Forgery (CSRF): Observing the flow of requests and detecting unauthorized actions.
- Authentication and Authorization Issues: Monitoring user logins and access controls to detect potential weaknesses.
- Improper Error Handling: Analyzing the application’s response to errors and identifying potential vulnerabilities.
Preventing Vulnerabilities with These Technologies
By proactively identifying vulnerabilities, IAST, RASP, and runtime instrumentation contribute significantly to vulnerability prevention. The real-time feedback loop from these technologies enables immediate remediation efforts, reducing the window of exposure to attackers.
Instrumentation Probes: A Detailed Explanation
Instrumentation probes are small code snippets inserted into the application’s source or bytecode. They act as sensors, monitoring specific events and collecting relevant data. These probes are strategically placed at critical points in the application’s logic to observe the flow of data and execution paths. They capture the context of each event, including input parameters, method calls, and return values.
These detailed observations allow for in-depth analysis and identification of vulnerabilities.
Practical Applications of IAST, Rasp, and Runtime Instrumentation: Iast Rasp And Runtime Instrumentation
IAST, RASP, and runtime instrumentation are powerful tools for proactively identifying and mitigating software vulnerabilities. Understanding their practical applications is crucial for integrating them effectively into a comprehensive security strategy. These techniques move beyond static analysis, examining code in execution, thereby revealing vulnerabilities that might otherwise remain hidden.
Real-World Use Cases for IAST
IAST tools analyze applications during runtime, allowing for the detection of vulnerabilities that might not be apparent during static analysis. They are particularly useful in identifying vulnerabilities in complex, dynamic applications. For example, IAST can be used to detect SQL injection vulnerabilities in web applications by monitoring how the application interacts with the database. A real-world use case is identifying flaws in a banking application where sensitive financial data is involved.
IAST (Interactive Application Security Testing) and runtime instrumentation are crucial for identifying vulnerabilities like those found in Azure systems. For example, understanding the specifics of a recent Azure Cosmos DB Vulnerability is key to proactively bolstering security. Azure Cosmos DB Vulnerability Details provide critical insight, helping to refine our IAST and runtime instrumentation strategies for comprehensive security checks.
IAST can simulate attacks on the application, monitoring the responses and identifying potential weaknesses.
Real-World Use Cases for RASP
Runtime Application Self-Protection (RASP) tools actively protect applications from attacks during execution. They act as a shield, intercepting malicious requests and preventing exploits from succeeding. A practical example includes protecting e-commerce platforms from cross-site scripting (XSS) attacks. RASP tools can monitor user input and prevent malicious scripts from being executed. This proactive approach can prevent attackers from gaining access to sensitive data.
Examples of How Runtime Instrumentation is Applied in Different Software Contexts
Runtime instrumentation involves modifying the application’s code to add monitoring and analysis capabilities. This technique is valuable in various contexts, from monitoring performance to detecting vulnerabilities. For instance, in a web server, runtime instrumentation can track user interactions, such as requests and responses, to identify unusual patterns that could indicate a potential attack. In a distributed system, it can be used to trace the flow of data between different components, aiding in the identification of bottlenecks or security breaches.
Specific Vulnerabilities Detected by IAST, Rasp, or Runtime Instrumentation
IAST, RASP, and runtime instrumentation have detected various vulnerabilities in real-world applications. Examples include cross-site scripting (XSS) vulnerabilities in web applications, insecure deserialization issues in APIs, and buffer overflows in network services. Runtime instrumentation has been instrumental in detecting race conditions in multithreaded applications, ensuring data consistency and preventing unexpected behavior.
Integrating IAST into Existing CI/CD Pipelines
Integrating IAST into CI/CD pipelines allows for automated vulnerability scanning. This ensures that security testing is performed consistently throughout the development lifecycle. The process involves integrating the IAST tool with the CI/CD pipeline, allowing for automated scanning of code changes. This can be achieved by setting up the IAST tool to run on specific branches or triggers.
Identifying Effectiveness of IAST, Rasp, and Runtime Instrumentation, Iast rasp and runtime instrumentation
The effectiveness of IAST, RASP, and runtime instrumentation can be evaluated by analyzing the number of vulnerabilities detected, the severity of the identified vulnerabilities, and the time taken to remediate them. Metrics like vulnerability detection rate, false positive rate, and remediation time can be used to quantify their effectiveness.
Creating a Comprehensive Security Testing Strategy Using IAST, Rasp, and Runtime Instrumentation
A comprehensive security testing strategy should incorporate IAST, RASP, and runtime instrumentation. The strategy should define the scope of testing, the tools to be used, and the metrics to be monitored. It should also define how the results will be analyzed and used to improve the security posture of the application. A strategy can involve phased implementation of these tools, starting with IAST for initial vulnerability scanning and gradually adding RASP for real-time protection and runtime instrumentation for deeper analysis.
Step-by-Step Guide to Implementing Runtime Instrumentation in a Java Application
Implementing runtime instrumentation in a Java application involves several steps. First, identify the areas of the application that require instrumentation. Next, use a suitable library (e.g., bytebuddy) to instrument the identified code segments. The library will intercept method calls, allowing the collection of data and analysis. Finally, process the collected data to identify potential vulnerabilities or performance bottlenecks.
This process can be automated using scripting or tools, significantly increasing efficiency.
Challenges and Considerations
Implementing IAST, RASP, and runtime instrumentation, while powerful for security, presents various challenges. These methods, while effective in identifying vulnerabilities, introduce complexities related to performance overhead, false positives, and the need for careful consideration in their selection and implementation. Understanding these challenges is crucial for successful application security.The effectiveness of IAST, RASP, and runtime instrumentation is directly influenced by their accuracy and reliability.
Misconfigurations or inappropriate application contexts can lead to inaccuracies, impacting the quality and usability of the results. Understanding the potential sources of errors and implementing strategies for minimizing them is essential.
Performance Impacts of Runtime Instrumentation
Runtime instrumentation, by its very nature, introduces performance overhead. The act of monitoring and modifying application behavior during execution inevitably slows down the application. This slowdown can be significant, particularly for computationally intensive tasks. Mitigation strategies include optimizing instrumentation techniques, focusing on critical paths, and utilizing caching mechanisms to reduce the impact on overall application responsiveness.
Choosing Between IAST, RASP, and Runtime Instrumentation
The choice between IAST, RASP, and runtime instrumentation depends on specific use cases and the characteristics of the application being protected. IAST is suitable for finding vulnerabilities in the application’s external interface and behavior, but does not directly alter the application’s execution flow. RASP, on the other hand, actively intercepts and modifies the application’s execution flow, offering more precise vulnerability detection and prevention.
Runtime instrumentation provides granular control, but with a higher potential for performance impact.
Strategies for Mitigating Performance Bottlenecks
Various strategies can mitigate performance bottlenecks associated with runtime instrumentation. Profiling the application to identify performance-critical sections is vital. Selective instrumentation, focusing only on the most crucial parts of the code, can reduce the instrumentation’s impact on performance. Additionally, using efficient data structures and algorithms for storing and processing the instrumentation data can improve overall efficiency.
Ensuring Accuracy and Reliability of Results
Ensuring the accuracy and reliability of results is critical for effective vulnerability detection. Rigorous testing and validation, including comparing results against known vulnerabilities and using various test cases, are necessary. Proper configuration and calibration of the instrumentation tools are essential to minimize false positives and ensure accurate reporting.
False Positives in IAST, RASP, and Runtime Instrumentation
False positives, results indicating a vulnerability that does not actually exist, are a common issue with these techniques. False positives can stem from various factors, including complex application logic, unexpected inputs, or limitations in the instrumentation’s ability to accurately interpret the application’s behavior. This necessitates careful analysis and verification of the reported vulnerabilities.
Handling False Positives in Runtime Instrumentation
Strategies for handling false positives in runtime instrumentation involve thorough analysis of the reported vulnerabilities. Detailed code review, comparing against known good practices, and utilizing various testing methods can help to identify false positives. Implementing a filtering mechanism to prioritize genuine vulnerabilities and suppress false positives is crucial for improving the effectiveness of the instrumentation. Furthermore, developing a clear process for validating results and incorporating feedback from developers is essential for ongoing improvement.
Tools and Technologies
IAST, RASP, and runtime instrumentation tools are crucial for identifying and mitigating software vulnerabilities. These tools empower developers to proactively address potential weaknesses before they are exploited. The choice of the right tool depends heavily on the specific needs of the project and the type of vulnerabilities being targeted. This section delves into the various tools available, highlighting their features and functionalities.
IAST Tools
Several tools are available for performing IAST analysis. They differ in their approaches, features, and target platforms. Choosing the right tool is critical for effectively identifying vulnerabilities.
- SonarQube: SonarQube, a widely used platform, integrates IAST scanning capabilities. It offers a comprehensive set of static and dynamic analysis features, covering various programming languages. It excels in identifying vulnerabilities, code smells, and security issues within projects. SonarQube can be configured to scan code repositories and provide reports on potential vulnerabilities.
- Checkmarx: Checkmarx is another prominent IAST tool. It is known for its robust analysis engine, offering comprehensive security checks for a wide range of applications and programming languages. Checkmarx often boasts advanced features, such as integrating with CI/CD pipelines, to provide seamless security checks within development workflows.
- Fortify: IBM Fortify offers a comprehensive suite of security tools, including IAST. It typically provides deep code analysis, resulting in a high degree of accuracy in vulnerability detection. Integration with other development tools is a common feature in the Fortify platform.
RASP Tools
RASP tools offer a different approach, implementing security checks directly within the application’s runtime environment. This allows for real-time detection and prevention of vulnerabilities.
- OWASP-ModSecurity Core Rule Set (CRS): A widely adopted open-source RASP solution, the CRS provides a comprehensive set of rules to identify and block malicious requests. It acts as a filter, examining incoming requests for malicious patterns and preventing attacks.
- Veracode: Veracode’s RASP solution is known for its extensive functionality and ability to detect vulnerabilities in various applications. It is often integrated with development pipelines for efficient security checks.
- Imperva SecureSphere: This solution offers advanced RASP features, including comprehensive detection of various types of attacks and detailed reporting on vulnerabilities. Imperva’s solutions are often tailored to specific application needs and often involve detailed configuration options.
Runtime Instrumentation Libraries and Frameworks
Runtime instrumentation is a technique that modifies the execution flow of a program to collect data or execute specific actions at various points.
- Java Instrumentation API: This API allows Java applications to be instrumented at runtime. It enables modification of class loading and bytecode manipulation, enabling the insertion of monitoring or security checks.
- Aspect-Oriented Programming (AOP) Libraries (e.g., Spring AOP): These libraries facilitate the addition of cross-cutting concerns, including security checks, into an application without modifying the core code. AOP frameworks can enhance the efficiency and maintainability of security implementations.
- OpenTelemetry: OpenTelemetry is a standardized framework for collecting and exporting telemetry data, including performance and security metrics. It is increasingly used for runtime instrumentation, offering flexibility and compatibility across various programming languages.
Features of Popular IAST, RASP, and Runtime Instrumentation Tools
These tools often provide detailed reporting capabilities, allowing developers to pinpoint specific vulnerabilities and understand the context of the issues. Integration with CI/CD pipelines is also common, automating the security testing process.
Comparison Table of IAST Tools
| Tool | Features | Pricing | Target Platforms |
|---|---|---|---|
| SonarQube | Static and dynamic analysis, vulnerability detection, code quality analysis | Various licensing options available | Multi-platform |
| Checkmarx | Robust analysis engine, comprehensive security checks, wide range of programming languages | Typically a subscription-based model | Multi-platform |
| Fortify | Deep code analysis, high accuracy in vulnerability detection | Typically a subscription-based model | Multi-platform |
Example of Vulnerability Analysis
Using SonarQube, a developer might identify a SQL injection vulnerability in a web application. The tool would pinpoint the specific line of code susceptible to the vulnerability and provide recommendations for remediation. This allows developers to quickly address the vulnerability and enhance the application’s security posture.
Last Point
In conclusion, IAST, RASP, and runtime instrumentation provide a powerful suite of tools for bolstering application security. While challenges like performance overhead exist, the benefits in terms of vulnerability detection and prevention often outweigh these considerations. Choosing the right tools and implementing a comprehensive strategy are key to maximizing their effectiveness. This exploration has hopefully provided a solid foundation for understanding and implementing these techniques.
FAQ Section
What are the key differences between IAST and static analysis?
IAST analyzes applications during runtime, whereas static analysis examines the code without execution. This runtime analysis allows IAST to detect vulnerabilities that might not be apparent in static code reviews.
How does runtime instrumentation impact application performance?
Runtime instrumentation can introduce performance overhead. However, careful selection of instrumentation points and tools can mitigate these impacts significantly.
What are some common false positives in IAST?
False positives can arise from complex code structures or unexpected interactions. Careful analysis and filtering are necessary to ensure accurate vulnerability detection.
Which tools are commonly used for RASP?
Popular RASP tools include, but are not limited to, AppArmor, and others, each with their own strengths and weaknesses.