How to Balance Speed and Security in Your AppSec Program
How to balance speed and security in your application security program? It’s the million-dollar question for every developer and business owner. We all crave that lightning-fast development cycle, but security breaches can cost far more than just time; they can cripple your reputation and bottom line. This post dives deep into the strategies and tools you need to navigate this crucial balancing act, ensuring your application is both secure and swiftly delivered to market.
We’ll explore practical techniques for integrating security into every phase of development, from prioritizing critical risks and implementing secure coding practices to leveraging automated security tools and fostering a security-conscious team culture. We’ll also look at how different development methodologies, like Agile and DevOps, impact this delicate balance and how to adapt your approach accordingly. Get ready to learn how to build secure applications without sacrificing speed!
Defining Speed and Security in Application Development: How To Balance Speed And Security In Your Application Security Program
The modern software development landscape is a constant tug-of-war between the relentless pressure to deliver features quickly and the critical need to build secure applications. Speed, often driven by market demands and competitive pressures, frequently clashes with the meticulous processes required for robust security. Finding the right balance is crucial for success, as neglecting either aspect can lead to significant consequences.Speed in application development typically refers to the velocity of releasing new features, updates, and improvements.
This involves rapid iteration cycles, continuous integration and continuous delivery (CI/CD) pipelines, and a focus on minimizing time-to-market. Security, conversely, encompasses a wide range of practices aimed at protecting the application and its data from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes secure coding practices, vulnerability scanning, penetration testing, and incident response planning. The trade-off lies in the inherent tension between the agility of rapid development and the thoroughness demanded by comprehensive security measures.
Faster development cycles often mean less time for rigorous security reviews and testing, increasing the risk of vulnerabilities.
Trade-offs Between Rapid Development and Robust Security Measures
Prioritizing speed over security can significantly compromise the application’s resilience. Development teams under pressure to meet deadlines might cut corners, skipping crucial security steps like code reviews or penetration testing. This can lead to the introduction of various vulnerabilities, exposing the application and its users to significant risks. For instance, rushing the implementation of authentication mechanisms might result in weak password policies or the omission of multi-factor authentication, making the application susceptible to brute-force attacks.
Similarly, neglecting input validation can open the door to injection attacks (SQL injection, cross-site scripting), potentially allowing attackers to manipulate the application’s behavior or steal sensitive data. The cost of fixing security flaws discovered after release can be substantially higher than incorporating security measures early in the development lifecycle. This includes the financial cost of remediation, the reputational damage from a security breach, and the potential legal repercussions.
Examples of Security Vulnerabilities Introduced by Prioritizing Speed Over Security
Several real-world examples highlight the dangers of prioritizing speed over security. The infamous Equifax data breach of 2017, which exposed the personal information of millions of individuals, stemmed partly from the company’s failure to promptly patch a known vulnerability in its Apache Struts framework. This delay, driven by a focus on rapid deployment and cost-cutting, allowed attackers to exploit the vulnerability and gain access to sensitive data.
Another example is the Heartbleed bug, a critical vulnerability in the OpenSSL cryptographic library, which affected a vast number of applications and services. The bug, caused by a flaw in the library’s handling of heartbeat requests, allowed attackers to extract sensitive data, including private keys and passwords. These incidents demonstrate that the long-term costs of neglecting security far outweigh the short-term gains of faster development.
Best Practices for Integrating Security Considerations into the Agile Development Process
Integrating security into the agile development process is not about slowing down development; it’s about building security into every stage. This requires a shift in mindset, where security is not an afterthought but an integral part of the development lifecycle. One key strategy is “shifting left,” which involves incorporating security testing and reviews early in the development process, rather than waiting until the end.
This allows for the identification and remediation of vulnerabilities early on, when they are less expensive and easier to fix. Implementing secure coding practices, using static and dynamic application security testing (SAST and DAST) tools, and conducting regular penetration testing are also essential. Furthermore, establishing a strong security culture within the development team, providing security training, and fostering collaboration between developers and security professionals are crucial for success.
By embedding security into the development process from the outset, organizations can significantly reduce their risk exposure while maintaining a rapid pace of innovation.
Prioritizing Security Risks
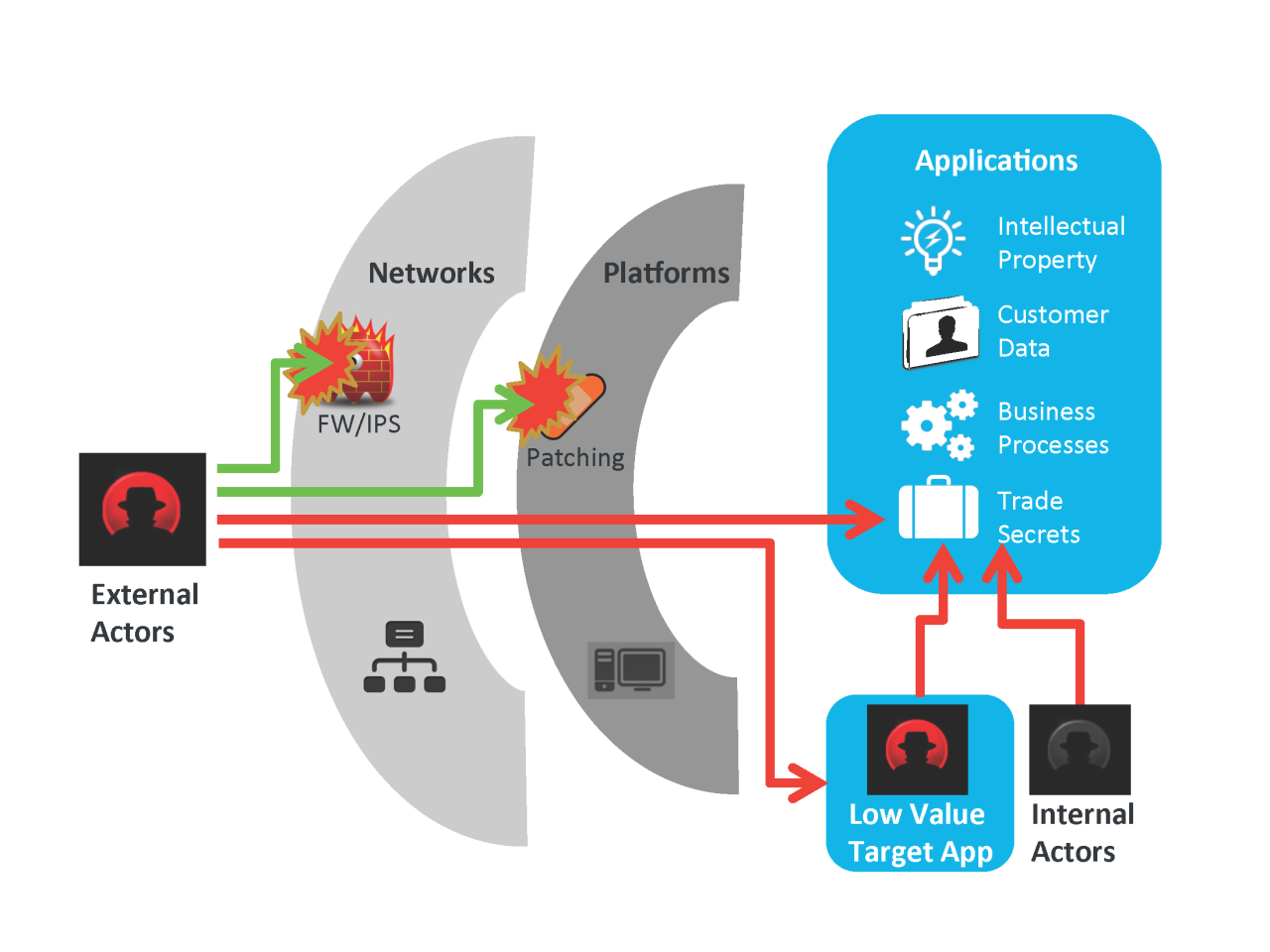
Balancing speed and security in application development requires a strategic approach to risk management. Instead of trying to address every potential vulnerability, focusing on the most critical risks allows for efficient resource allocation and faster development cycles without compromising essential security. This involves understanding the specific threats relevant to your industry and prioritizing mitigation efforts accordingly.Prioritizing security risks effectively involves identifying the most likely and impactful threats, understanding their potential consequences, and implementing cost-effective mitigation strategies.
This process is iterative and requires continuous monitoring and adaptation.
Top Three Critical Security Risks in the Fintech Industry
The Fintech industry, with its reliance on sensitive financial data and online transactions, faces unique security challenges. Three critical risks consistently emerge: data breaches, injection attacks (like SQL injection), and insecure APIs.
Data breaches, resulting from unauthorized access to sensitive customer information like account numbers, personal details, and transaction history, can lead to significant financial losses, regulatory penalties, and irreparable damage to reputation. The Equifax data breach of 2017, exposing the personal information of nearly 150 million people, serves as a stark example of the devastating consequences. The cost to Equifax included billions of dollars in fines, legal fees, and reputational damage.
Injection attacks, particularly SQL injection, exploit vulnerabilities in database interactions to manipulate data or gain unauthorized access. Successful attacks can compromise entire databases, leading to data theft, modification, or deletion. The impact can range from minor data inconsistencies to complete system failure and significant financial losses, depending on the sensitivity of the compromised data. A well-known example is the 2011 Sony PlayStation Network breach, which resulted from an SQL injection vulnerability and affected millions of users.
Insecure APIs, often used for communication between different systems and applications, can expose sensitive data and functionality to unauthorized access. Exploiting vulnerabilities in APIs can allow attackers to bypass security controls, steal data, or disrupt services. A compromised API can lead to data breaches, service disruptions, and financial losses. The 2017 Uber data breach, partly attributed to insecure APIs, exposed the personal information of millions of users.
Mitigation Strategies for Prioritized Risks
Effective mitigation doesn’t require a complete halt to development. Instead, focus on implementing practical, efficient safeguards.
For data breaches, robust data encryption both in transit and at rest is crucial. This minimizes the impact of a successful breach by rendering stolen data unusable. Regular security audits and penetration testing identify vulnerabilities before attackers can exploit them. Implementing multi-factor authentication adds an extra layer of security, making unauthorized access significantly more difficult. Furthermore, robust access control mechanisms ensure that only authorized personnel can access sensitive data.
Mitigating injection attacks requires implementing parameterized queries and input validation. These techniques prevent attackers from injecting malicious code into database queries. Regular security training for developers emphasizes secure coding practices, reducing the likelihood of introducing vulnerabilities. Employing a web application firewall (WAF) can provide an additional layer of protection by filtering malicious traffic before it reaches the application.
Securing APIs involves implementing robust authentication and authorization mechanisms, such as OAuth 2.0 or OpenID Connect. Regular security testing of APIs helps identify and address vulnerabilities before they can be exploited. Rate limiting and input validation prevent abuse and mitigate denial-of-service attacks. Proper API documentation and secure design principles contribute to minimizing potential vulnerabilities from the outset.
Implementing Secure Coding Practices
Secure coding practices are the bedrock of a robust application security program. They represent a proactive approach, aiming to prevent vulnerabilities from ever appearing in the codebase, rather than relying solely on reactive measures like penetration testing. By integrating security into the development lifecycle from the outset, we can significantly reduce the risk of costly breaches and reputational damage.
This section delves into practical guidelines, techniques, and processes for implementing secure coding effectively.
Secure Coding Guidelines
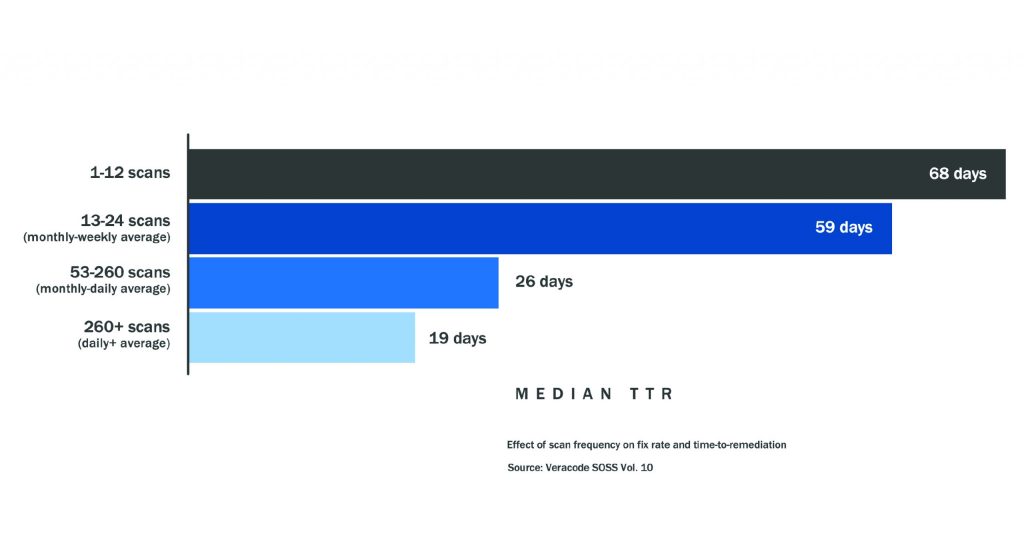
Implementing secure coding requires a disciplined approach and a deep understanding of common vulnerabilities. The following table Artikels key guidelines, providing examples and illustrating the potential impact of neglecting them.
| Guideline | Description | Example | Potential Impact of Violation |
|---|---|---|---|
| Input Validation | Always validate and sanitize all user inputs before using them in your application. This prevents malicious data from causing unexpected behavior or security flaws. | Instead of directly using user-supplied data in an SQL query (SELECT
), use parameterized queries or prepared statements ( SELECT
, with the username provided as a parameter). |
SQL injection, Cross-Site Scripting (XSS), command injection, and other vulnerabilities leading to data breaches, unauthorized access, or application crashes. |
| Output Encoding | Encode all data before displaying it to the user. This prevents malicious code from being executed in the user’s browser. | Before displaying user-supplied data on a web page, encode it using appropriate encoding methods (e.g., HTML encoding for HTML context, URL encoding for URL context). For example, instead of directly displaying <script>alert('XSS')</script>. |
Cross-Site Scripting (XSS) attacks, allowing attackers to steal session cookies, redirect users to malicious websites, or inject malicious code into the application. |
| Authentication and Authorization | Implement robust authentication and authorization mechanisms to verify user identities and control access to resources. | Use strong password policies, multi-factor authentication, and role-based access control (RBAC) to restrict access to sensitive data and functionalities. | Unauthorized access to sensitive data, account takeover, privilege escalation, and data breaches. |
| Session Management | Use secure session management techniques to prevent session hijacking and other attacks. | Use HTTPS, regenerate session IDs regularly, implement appropriate session timeouts, and avoid storing sensitive data in sessions. | Session hijacking, unauthorized access, and data breaches. |
| Error Handling | Handle errors gracefully and avoid revealing sensitive information in error messages. | Instead of displaying error messages containing detailed stack traces or database information, provide generic error messages to users and log detailed information for debugging purposes. | Information leakage, allowing attackers to gain insights into the application’s architecture and vulnerabilities. |
| Data Protection | Protect sensitive data at rest and in transit using encryption and other security measures. | Encrypt sensitive data stored in databases, use HTTPS for all communication, and implement data loss prevention (DLP) measures. | Data breaches, unauthorized access, and non-compliance with data privacy regulations. |
Input Validation and Output Encoding, How to balance speed and security in your application security program
Input validation and output encoding are crucial for preventing common vulnerabilities like SQL injection and cross-site scripting (XSS). Input validation ensures that data received from untrusted sources conforms to expected formats and constraints. Output encoding converts data into a safe format for display in a specific context, preventing malicious code from being executed.For example, consider a web form where users enter their username.
Without input validation, a malicious user could enter a specially crafted string like ' OR '1'='1, which could lead to an SQL injection vulnerability if the input is directly incorporated into an SQL query. Proper input validation would ensure that the username only contains alphanumeric characters and does not contain SQL s. Similarly, output encoding protects against XSS attacks by converting special characters in user-supplied data into their HTML entities before displaying them on a web page.
Code Reviews for Security Flaws
Code reviews are a critical step in identifying and addressing security flaws before they reach production. A systematic approach to code reviews should involve multiple developers examining the code for potential vulnerabilities, adherence to coding standards, and overall security best practices. Tools like static analysis scanners can also assist in automating the process and identifying potential issues. The review process should focus on areas such as input validation, output encoding, authentication and authorization, session management, error handling, and data protection.
The goal is to catch vulnerabilities early in the development lifecycle, when they are easier and less expensive to fix. Documentation of findings and remediation steps is crucial for continuous improvement and learning.
Utilizing Automated Security Tools
Automating security testing is crucial for balancing speed and security in application development. Manual testing is time-consuming and prone to human error, especially as applications grow in complexity. Leveraging automated tools allows for faster feedback loops, earlier vulnerability detection, and ultimately, more secure software releases. This approach shifts the security focus from a gatekeeping function to an integral part of the development process.
Several automated security testing tools exist, each with its strengths and weaknesses. Choosing the right combination depends on your specific development environment, budget, and risk tolerance. Effective integration of these tools into your development pipeline is key to realizing their full potential.
Comparison of Automated Security Testing Tools
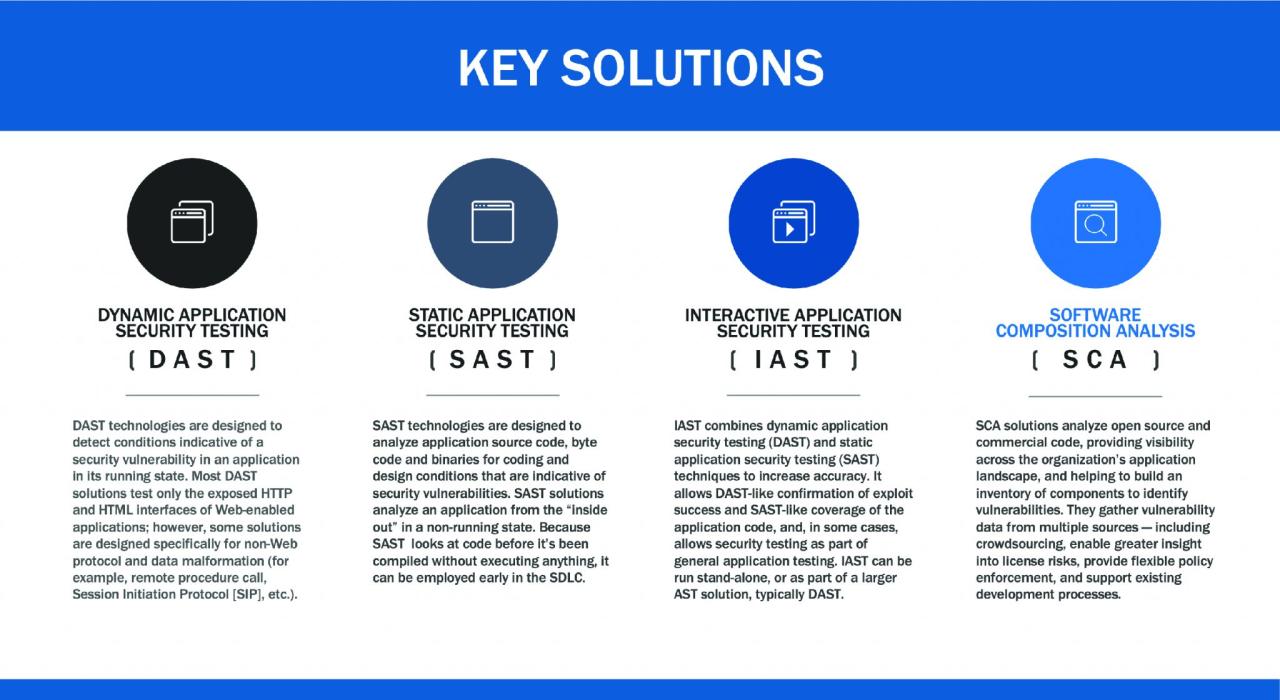
Different automated tools offer unique approaches to security testing. Understanding their differences is key to selecting the best tools for your needs. The three main categories are Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST).
- SAST: SAST tools analyze the application’s source code without actually executing it. They identify vulnerabilities by looking for patterns and known weaknesses in the code itself. Think of it as a code grammar check, but for security. Strengths include early detection of vulnerabilities and a relatively low false positive rate. Weaknesses include a limited ability to detect runtime vulnerabilities and the need for access to source code.
- DAST: DAST tools test the application from the outside, simulating real-world attacks. They analyze the application’s behavior during runtime, identifying vulnerabilities in the application’s response to different inputs. Think of it as a penetration test, but automated. Strengths include the ability to detect runtime vulnerabilities and a wider range of vulnerabilities than SAST. Weaknesses include a higher false positive rate and the inability to pinpoint the exact location of the vulnerability in the code.
- IAST: IAST tools combine the strengths of both SAST and DAST. They instrument the application during runtime, analyzing both the code and the application’s behavior. They provide detailed information about vulnerabilities, including their location in the code and the context in which they occur. Strengths include high accuracy, precise vulnerability location, and fewer false positives. Weaknesses include the need for instrumentation, potential performance overhead, and the complexity of setup and integration.
Integrating Automated Security Tools into the Development Pipeline
A successful integration strategy requires careful planning and execution. The goal is to seamlessly incorporate security testing into each stage of the development lifecycle, providing continuous feedback and enabling rapid remediation.
- Selection of Tools: Based on the comparison above, choose the appropriate SAST, DAST, and potentially IAST tools that align with your project’s needs and resources.
- Pipeline Integration: Integrate the chosen tools into your CI/CD pipeline. This might involve using plugins or APIs to trigger automated scans at specific points in the process, such as after code commits or before deployments.
- Thresholds and Reporting: Establish clear thresholds for acceptable vulnerability levels. Configure automated reporting to alert developers to new or unresolved issues. This ensures that security issues are addressed promptly and efficiently.
- Feedback Loops: Create clear communication channels to ensure developers receive timely feedback on identified vulnerabilities. This often involves integrating the security scanning results into your issue tracking system.
- Regular Updates: Keep your security tools updated with the latest vulnerability databases and signatures. This ensures that your scans remain effective against the latest threats.
Examples of Early Vulnerability Identification
Automated tools can significantly improve the speed and efficiency of vulnerability detection. Let’s consider some real-world examples.
- SQL Injection: A SAST tool could detect vulnerable SQL queries in the code before the application even runs, preventing a potential database compromise. For example, if a developer uses string concatenation to build SQL queries, a SAST tool would flag this as a potential SQL injection vulnerability.
- Cross-Site Scripting (XSS): A DAST tool, during a runtime scan, might discover an XSS vulnerability by injecting malicious scripts into input fields and observing the application’s response. This could expose sensitive user data or allow attackers to take control of user sessions.
- Broken Authentication: An IAST tool, by monitoring the application’s behavior, could detect weaknesses in the authentication mechanism, such as easily guessable passwords or lack of proper session management, even before the application is released to users.
Security Training and Awareness
Building a robust application security program isn’t just about tools and processes; it’s about people. A skilled and security-conscious team is your best defense against vulnerabilities. This section focuses on the critical role of security training and awareness in bolstering your application’s defenses. Investing in training is an investment in the long-term security of your applications and your organization.A comprehensive security training program is essential for developers and all team members to understand and implement secure coding practices and recognize potential threats.
Regular security awareness training reinforces best practices and keeps everyone informed about evolving threats.
Developer Security Training Program
This program aims to equip developers with the knowledge and skills necessary to write secure code. The curriculum will be delivered through a combination of online modules, hands-on workshops, and regular knowledge checks.
- Module 1: Introduction to Application SecurityThis module provides a foundational understanding of common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It will also cover the OWASP Top 10 vulnerabilities and their impact.
- Module 2: Secure Coding PracticesThis module focuses on practical secure coding techniques, including input validation, output encoding, and secure authentication and authorization mechanisms. Real-world examples of insecure code and their remediation will be demonstrated.
- Module 3: Vulnerability Analysis and Penetration TestingThis module covers the principles of vulnerability analysis and penetration testing, including static and dynamic analysis tools. Participants will learn to identify and mitigate vulnerabilities in their own code.
- Module 4: Secure Development Lifecycle (SDLC) IntegrationThis module demonstrates how to integrate security into each phase of the SDLC, from requirements gathering to deployment and maintenance. Emphasis will be placed on shifting security left.
- Module 5: Continuous Learning and UpdatesThis module encourages ongoing learning and staying current with emerging threats and best practices through resources like OWASP and SANS Institute publications. Regular updates and refresher training will be provided.
Importance of Regular Security Awareness Training
Regular security awareness training is crucial for all team members, not just developers. This training should go beyond technical details and focus on the human element of security. It should cover topics such as phishing awareness, social engineering tactics, password management, and the importance of reporting security incidents. The goal is to create a security-conscious culture where everyone understands their role in protecting the organization’s assets.
Real-World Security Incidents Caused by Human Error
Many security breaches are caused by human error, often stemming from a lack of awareness or training. For example, a phishing email might trick an employee into revealing sensitive credentials, leading to a data breach. Another example is an employee accidentally clicking on a malicious link, resulting in malware infection. In both cases, proper security awareness training could have significantly reduced the risk.
A well-designed training program would cover these scenarios, providing employees with the skills to identify and report such threats effectively. For instance, training on identifying suspicious emails (unfamiliar senders, grammatical errors, urgent requests for action) and practicing safe browsing habits could have mitigated the risk in these examples.
Continuous Monitoring and Improvement
Building a truly secure application isn’t a one-time event; it’s an ongoing process. Continuous monitoring and improvement are crucial for identifying and mitigating emerging threats, ensuring your application remains resilient against evolving attack vectors. This involves establishing a robust system for tracking security posture, responding effectively to incidents, and proactively adapting security measures.A well-designed system for continuous monitoring provides real-time visibility into your application’s security health.
This allows for proactive identification of vulnerabilities before they can be exploited. Ignoring this aspect can lead to significant breaches and reputational damage.
Continuous Application Security Monitoring System Components
A comprehensive application security monitoring system requires several key components working in concert. These components provide a layered approach to security, enhancing detection capabilities and minimizing blind spots. Effective integration between these components is paramount.
- Security Information and Event Management (SIEM): This centralizes security logs from various sources – servers, applications, network devices – providing a unified view of security events. A SIEM system allows for correlation of events, facilitating the identification of potential threats and attacks. For example, a SIEM might detect unusual login attempts from unusual geographical locations, flagging a potential brute-force attack.
- Runtime Application Self-Protection (RASP): RASP agents reside within the application itself, providing real-time insights into application behavior. They can detect and block attacks in progress, such as SQL injection or cross-site scripting attempts, before they cause damage. This provides an inside-out perspective on security threats.
- Vulnerability Scanners: Regular automated vulnerability scans identify known weaknesses in your application’s code and configuration. These scans, conducted both internally and externally, provide a comprehensive overview of potential entry points for attackers. Tools like Nessus or OpenVAS can be used for this purpose.
- Threat Intelligence Feeds: Staying informed about emerging threats is crucial. Subscribing to threat intelligence feeds provides valuable context for interpreting security alerts and prioritizing responses. These feeds often highlight newly discovered vulnerabilities and attack patterns.
Incident Response and Vulnerability Remediation
A well-defined incident response plan is essential for effectively handling security breaches. This plan should Artikel clear steps for identifying, containing, eradicating, recovering from, and learning from security incidents. Speed and efficiency are paramount in minimizing the impact of an attack.
- Detection: The first step involves detecting a security incident through monitoring systems or user reports. This may involve alerts from a SIEM system or unusual activity noticed by an employee.
- Analysis: Once an incident is detected, a thorough analysis is needed to understand its nature, scope, and impact. This involves investigating logs, network traffic, and affected systems.
- Containment: The goal is to isolate the affected systems or applications to prevent further damage or compromise. This might involve shutting down affected servers or blocking malicious network traffic.
- Eradication: The next step is to remove the root cause of the incident. This could involve patching vulnerabilities, removing malware, or resetting compromised accounts.
- Recovery: Once the threat is eliminated, systems need to be restored to their operational state. This may involve restoring data from backups or reinstalling applications.
- Post-Incident Activity: After recovery, a post-incident review should be conducted to identify weaknesses in security procedures and improve future responses. This includes documenting lessons learned and updating security policies.
Regular Security Policy and Procedure Review
Security policies and procedures are not static documents; they require regular review and updates to remain effective. The frequency of these reviews should depend on the evolving threat landscape and changes within the organization. Outdated policies can leave your application vulnerable to attack.Regular reviews should encompass all aspects of your application security program, including access controls, incident response procedures, and security awareness training.
Changes in technology, regulatory requirements, or internal processes may necessitate policy updates. For example, the adoption of new cloud services might require revisions to access control policies. The review process should involve key stakeholders across different departments, ensuring comprehensive coverage and buy-in.
Balancing Speed and Security in Different Development Methodologies
The inherent tension between rapid development and robust security is amplified by the choice of development methodology. Different approaches prioritize speed and security in varying ways, demanding tailored security strategies for optimal results. Understanding these nuances is crucial for building secure and scalable applications.Agile and Waterfall methodologies present contrasting challenges in balancing speed and security. DevOps, however, offers a powerful framework to bridge this gap, promoting both rapid iteration and a strong security posture.
Agile vs. Waterfall Development: Security Considerations
Agile’s iterative nature, with its emphasis on rapid feedback loops and continuous integration, can sometimes lead to security being treated as an afterthought. Waterfall’s sequential approach, on the other hand, offers more structured opportunities for security assessments but can be slower to adapt to emerging threats. In Agile, security needs to be integrated into each sprint, requiring a shift-left approach where security is considered from the very beginning.
Waterfall projects benefit from thorough upfront security planning and risk assessments but may struggle to address vulnerabilities discovered late in the development lifecycle. Effective security practices must be tailored to the specific methodology to avoid compromising either speed or security.
DevOps Practices for Enhanced Speed and Security
DevOps emphasizes automation and collaboration between development and operations teams. This collaborative environment is instrumental in improving both speed and security. Automated security testing integrated into the CI/CD pipeline allows for early detection and remediation of vulnerabilities, preventing them from reaching production. Infrastructure as Code (IaC) allows for consistent and secure infrastructure provisioning, minimizing human error. Furthermore, continuous monitoring and logging provide real-time visibility into application security, enabling rapid response to threats.
For example, automated penetration testing integrated into the CI/CD pipeline can identify and flag security issues before they are deployed to production, saving time and resources. This automated approach, a cornerstone of DevOps, ensures security is not a bottleneck but a seamlessly integrated aspect of the development process.
Adapting Security Practices to Different Frameworks
Different development frameworks necessitate different security approaches. For example, when developing a microservices architecture, each service requires independent security considerations. This might involve implementing service-to-service authentication and authorization mechanisms, like OAuth 2.0 or JWT, and securing communication channels using TLS. In contrast, a monolithic application requires a more holistic security approach, focusing on input validation, output encoding, and database security.
Frameworks like React, Angular, or Vue.js require securing the frontend through techniques like Content Security Policy (CSP) and protecting against Cross-Site Scripting (XSS) attacks. Regardless of the framework, implementing a robust security testing strategy, encompassing static and dynamic application security testing (SAST and DAST), is essential for identifying and mitigating vulnerabilities. Regular security audits and penetration testing should also be part of the ongoing security program, regardless of the development framework used.
Illustrating the Impact of Security Breaches
The consequences of a security breach can be devastating, extending far beyond the immediate technical issues. A seemingly small vulnerability can trigger a chain reaction of events with significant financial and reputational repercussions for a business. Let’s examine a hypothetical scenario to illustrate these impacts.Imagine “GreenThumb Gardens,” a rapidly growing online retailer of gardening supplies, experienced a data breach.
A malicious actor exploited a vulnerability in their e-commerce platform, gaining access to customer databases containing names, addresses, credit card information, and order history.
The Breach and its Immediate Impact
The breach went undetected for several weeks. During this time, the attacker systematically exfiltrated sensitive data, resulting in thousands of customers having their credit cards compromised. GreenThumb Gardens immediately faced a wave of angry customer calls, emails, and social media posts. They were forced to shut down their online store to investigate and implement emergency security measures, resulting in a complete loss of sales for a crucial period encompassing peak gardening season.
This immediate loss of revenue was substantial, estimated at approximately $500,000.
Financial Consequences
Beyond the loss of sales, GreenThumb Gardens faced significant financial burdens. They had to engage a cybersecurity firm to investigate the breach, costing them $75,000 for forensic analysis and incident response. They also incurred substantial legal fees from responding to customer lawsuits and regulatory inquiries, amounting to an additional $150,000. Furthermore, they had to cover the costs associated with credit monitoring services provided to affected customers, estimated at $25,000.
The total financial cost of the breach, including lost revenue, exceeded $750,000.
Reputational Damage and Long-Term Effects
The reputational damage proved even more enduring than the financial losses. News of the breach spread rapidly, impacting GreenThumb Gardens’ brand image and customer trust. Many customers vowed never to shop with them again, leading to a long-term decline in sales and market share. The negative publicity also made it more difficult to attract new customers and secure future investment.
This intangible loss is difficult to quantify but is arguably more damaging than the immediate financial impact. It could take years for GreenThumb Gardens to fully recover its reputation.
Preventing the Breach
This hypothetical breach could have been largely prevented through several proactive security measures. Regular security audits and penetration testing would have identified the vulnerability in the e-commerce platform before it could be exploited. Implementing robust multi-factor authentication would have significantly increased the difficulty for attackers to gain unauthorized access. Furthermore, employee security awareness training could have prevented a potential insider threat or reduced the chances of employees falling for phishing scams that could have led to the compromise.
Finally, keeping the software updated with the latest security patches is crucial for mitigating known vulnerabilities. A proactive approach to security, encompassing all these elements, is significantly more cost-effective than reacting to a breach after it has occurred.
Last Recap
Ultimately, balancing speed and security isn’t about choosing one over the other; it’s about finding the optimal synergy. By adopting a proactive approach that integrates security into every stage of the development lifecycle, utilizes automated tools effectively, and fosters a culture of security awareness, you can significantly reduce your risk profile without sacrificing the velocity of your development process. Remember, a secure application is a successful application, and with the right strategies, you can have both speed and security working in perfect harmony.
Helpful Answers
What are the biggest security risks for web applications today?
SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) remain prevalent threats. Additionally, vulnerabilities related to authentication and authorization, insecure data storage, and lack of input validation continue to pose significant risks.
How can I convince my team to prioritize security?
Highlight the potential financial and reputational damage of a security breach. Show them how integrating security early saves time and money in the long run. Frame security as a business enabler, not a roadblock.
What’s the difference between SAST, DAST, and IAST?
SAST (Static Application Security Testing) analyzes code without execution. DAST (Dynamic Application Security Testing) analyzes a running application. IAST (Interactive Application Security Testing) combines aspects of both, providing real-time feedback during development.
How often should I update my security policies?
Regularly review and update your security policies at least annually, or more frequently if there are significant changes in your technology stack or regulatory environment. Consider using a change management process.