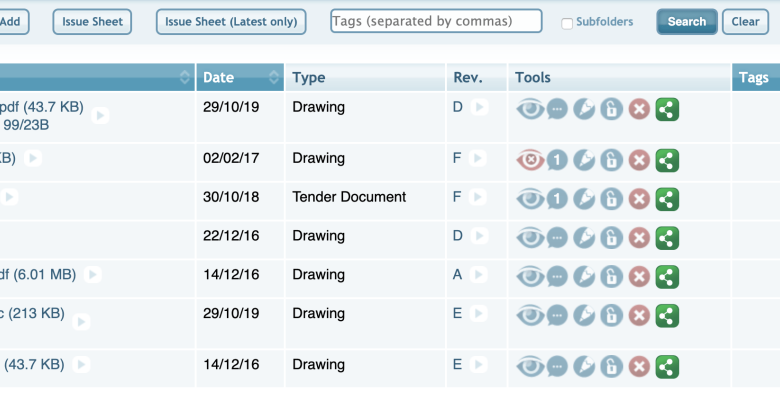
Software Bill of Materials VersionVault Auditing
Software Bill of Materials VersionVault auditing: Navigating the complex world of software security often feels like untangling a Gordian knot. But what if there was a way to systematically understand and manage the components within your software, ensuring its integrity and compliance? That’s where Software Bill of Materials (SBOMs) and VersionVault come in. This powerful combination allows for a detailed inventory of your software’s building blocks, making vulnerability identification and remediation far more efficient.
This post dives deep into how to leverage VersionVault for creating, managing, and auditing your SBOMs, ultimately strengthening your software supply chain security.
We’ll explore the creation and management of SBOMs within VersionVault, examining the practical steps involved in integrating this powerful tool into your existing workflows. We’ll cover best practices for maintaining accuracy, identify potential vulnerabilities, and delve into both manual and automated auditing techniques. We’ll also touch upon compliance requirements and how visualizing SBOM data can significantly improve your understanding of complex software dependencies.
Get ready to unlock a new level of control and visibility over your software’s composition!
Software Bill of Materials (SBOM) Definition and Importance
In today’s interconnected world, software is the lifeblood of countless systems, from critical infrastructure to everyday applications. Understanding the components that make up this software is paramount, and that’s where the Software Bill of Materials (SBOM) comes in. An SBOM is essentially an inventory of all the software components used in a piece of software, much like a traditional bill of materials lists the parts in a physical product.
This seemingly simple concept is revolutionizing how we approach software security and supply chain management.An SBOM provides a comprehensive list of all the software components, including their versions, licenses, and dependencies. This detailed inventory allows developers, security teams, and other stakeholders to understand the entire software ecosystem, identify potential vulnerabilities, and manage risks more effectively. It’s not just about the code you write; it’s about the vast network of open-source libraries, frameworks, and other components that underpin modern software development.
SBOM Core Components
An SBOM typically includes information such as the name and version of each component, the component’s source (e.g., a specific repository URL), its license, and a description of its function within the software. It also often includes details about relationships between components, creating a dependency graph. This graph helps visualize how components interact and pinpoint potential points of failure or vulnerability.
For instance, if a vulnerability is discovered in a specific library, the SBOM allows you to quickly identify all the applications that rely on that library, enabling rapid mitigation efforts.
Benefits of Using SBOMs in Software Development
The benefits of using SBOMs extend far beyond simple inventory management. They significantly enhance security by enabling proactive vulnerability detection and remediation. SBOMs also improve compliance with industry regulations and standards, such as those related to data security and privacy. Furthermore, they facilitate better software maintenance and upgrades by providing a clear understanding of the software’s architecture and dependencies.
This clarity streamlines the process of patching vulnerabilities and updating components, minimizing disruption and downtime. The ability to quickly identify and manage licensing requirements is another significant advantage, reducing the risk of compliance violations.
Comparison of SBOM Formats
Several standardized formats exist for representing SBOMs, each with its strengths and weaknesses. Two of the most widely adopted are SPDX (Software Package Data Exchange) and CycloneDX. SPDX, developed by the Linux Foundation, is a well-established standard with broad industry support. It’s known for its flexibility and rich feature set, allowing for detailed descriptions of software components and their relationships.
CycloneDX, on the other hand, is designed for machine readability and ease of automation. Its XML-based structure makes it particularly well-suited for integration into automated security tools and workflows. The choice of format often depends on the specific needs of the organization and its existing tooling.
Examples of SBOMs Improving Software Supply Chain Security
Imagine a scenario where a critical vulnerability is discovered in a widely used open-source library. Without an SBOM, identifying which applications are affected could be a time-consuming and complex process, potentially leaving systems exposed for an extended period. With an SBOM, however, you can quickly scan your software inventory and pinpoint all instances of the vulnerable library. This allows for immediate remediation efforts, minimizing the window of vulnerability and reducing the risk of exploitation.
This rapid response is critical in today’s fast-paced threat landscape. Another example involves compliance audits. An SBOM can streamline the process of demonstrating compliance with regulations that require disclosure of software components and their licenses, saving time and resources.
VersionVault and SBOM Integration
VersionVault, a robust software configuration management system, offers powerful capabilities that significantly enhance the creation and management of Software Bills of Materials (SBOMs). Its integrated version control and comprehensive audit trail provide a solid foundation for maintaining accurate and reliable SBOMs throughout the software development lifecycle. By leveraging VersionVault’s features, organizations can streamline their SBOM processes, improve security posture, and meet compliance requirements more effectively.VersionVault facilitates SBOM creation and management by tightly linking software components with their versions and dependencies.
This traceability is crucial for understanding the composition of a software product and identifying potential vulnerabilities. The system’s inherent version control ensures that SBOMs accurately reflect the current state of the software, preventing discrepancies and ensuring that security analyses are performed on the correct build. This eliminates the guesswork often associated with manually maintained SBOMs, leading to more reliable and actionable insights.
VersionVault Features Relevant to SBOM Generation
VersionVault’s core functionalities directly support SBOM generation. Its robust version control system tracks every change made to source code, libraries, and dependencies, creating a complete history. This history is essential for generating accurate SBOMs that reflect the specific components used in each release. The system’s ability to manage multiple branches and releases ensures that SBOMs are tailored to each specific version of the software.
Further, VersionVault’s granular access control ensures only authorized personnel can modify the software components and SBOMs, preserving data integrity and security. Built-in reporting features can be customized to generate SBOMs in various formats (e.g., SPDX, CycloneDX), enabling seamless integration with vulnerability scanning tools and other security systems.
Workflow for Integrating VersionVault into an Existing SBOM Process
Integrating VersionVault into an existing SBOM process involves a structured approach. First, identify the existing SBOM generation process and its pain points. Next, map the VersionVault features to address these pain points. For instance, if manual SBOM updates are a problem, VersionVault’s automated version tracking can be leveraged. A crucial step is defining a clear process for associating components with their respective versions within VersionVault.
This involves establishing naming conventions and tagging strategies to ensure consistent identification of components throughout the development lifecycle. Regularly scheduled SBOM generation using VersionVault’s reporting capabilities, ideally automated through scripting, should be implemented. Finally, establish a review and approval process for generated SBOMs before they are disseminated. This ensures accuracy and consistency. This integrated approach minimizes manual effort and ensures SBOMs are consistently updated and readily available.
Best Practices for Maintaining Accurate SBOMs within VersionVault
Maintaining accurate SBOMs within VersionVault requires adherence to best practices. Consistent use of VersionVault’s tagging and branching mechanisms is paramount for tracking component versions across different software releases. Regularly scheduled automated SBOM generation reduces the risk of outdated information. Implementing a robust change management process, ensuring all modifications to components are tracked within VersionVault, is crucial. Furthermore, integrating VersionVault with automated vulnerability scanning tools enables proactive identification and remediation of security risks.
Finally, establish clear roles and responsibilities for SBOM management, ensuring accountability and efficient workflow. Regular audits of the SBOM generation process and VersionVault data ensure ongoing accuracy and compliance.
Auditing SBOMs Generated by VersionVault: Software Bill Of Materials Versionvault Auditing
So, you’ve integrated VersionVault into your software development lifecycle and are now generating SBOMs. Fantastic! But the real power of an SBOM lies not just in its creation, but in its thorough auditing. This process helps identify potential vulnerabilities and ensures the accuracy and completeness of your software’s component inventory. Let’s dive into how to effectively audit the SBOMs produced by VersionVault.
Regular SBOM audits are crucial for mitigating security risks and maintaining compliance. By identifying outdated or vulnerable components, you can proactively address potential threats before they exploit weaknesses in your software. This proactive approach minimizes the impact of security breaches and strengthens the overall security posture of your application.
Potential Vulnerabilities Revealed Through SBOM Auditing
SBOM auditing can uncover a range of vulnerabilities. For example, an audit might reveal the presence of components with known Common Vulnerabilities and Exposures (CVEs). It could also highlight licenses that conflict with your organization’s policies or identify components that are no longer maintained, leaving your software vulnerable to future exploits. A thorough audit will also uncover inconsistencies in the SBOM itself, such as missing components or inaccurate version numbers, all of which can impact the reliability of the information.
Consider a scenario where an older version of a widely used library, known to have several critical CVEs, is identified. The audit would immediately flag this as a significant risk requiring immediate attention.
SBOM Audit Checklist for Completeness and Accuracy
A comprehensive checklist ensures a thorough audit. This checklist should cover various aspects, including:
Before beginning the audit, it is essential to establish clear criteria for evaluating the SBOM. These criteria should align with your organization’s security policies and compliance requirements. This ensures that the audit focuses on the most critical aspects of your software’s composition.
- Component Identification: Verify that all components are accurately identified and listed, including their names, versions, and unique identifiers.
- Version Numbers: Check that version numbers are accurate and consistent with the actual components used in the software.
- License Compliance: Confirm that all licenses are compliant with your organization’s policies and any applicable regulations.
- CVE Checks: Cross-reference components against known vulnerability databases (like the National Vulnerability Database) to identify any known CVEs.
- Dependency Analysis: Analyze dependencies to ensure that all direct and transitive dependencies are included in the SBOM.
- Data Integrity: Verify the integrity of the SBOM itself to ensure it hasn’t been tampered with.
- Metadata Completeness: Check for completeness of metadata, such as component origin, build date, and other relevant information.
Step-by-Step Guide for Conducting a VersionVault SBOM Audit
Auditing an SBOM generated by VersionVault is a systematic process.
The following steps provide a structured approach to conducting a thorough audit. Remember that the specific tools and techniques used might vary based on the complexity of your software and the chosen SBOM format. However, the fundamental principles remain consistent.
- Retrieve the SBOM: Export the SBOM from VersionVault in the desired format (e.g., SPDX, CycloneDX).
- Choose an Auditing Tool: Select an appropriate tool for analyzing the SBOM. Many open-source and commercial tools are available.
- Perform Vulnerability Scanning: Use the chosen tool to scan the SBOM for known vulnerabilities, cross-referencing against vulnerability databases.
- License Compliance Check: Analyze the SBOM to ensure license compliance with your organization’s policies.
- Review for Completeness: Manually review the SBOM for missing components or inconsistencies.
- Document Findings: Record all findings, including vulnerabilities, license issues, and inconsistencies, along with their severity and remediation steps.
- Remediation: Address identified vulnerabilities and inconsistencies by updating components, resolving license conflicts, or correcting errors in the SBOM.
Utilizing VersionVault Features to Support the Auditing Process
VersionVault’s features significantly aid the auditing process.
VersionVault’s robust tracking and management capabilities directly support a streamlined audit process. By leveraging these features, organizations can significantly reduce the time and effort involved in identifying and addressing vulnerabilities.
VersionVault’s integration with various development tools allows for seamless data flow, simplifying the SBOM generation and subsequent auditing. This integration reduces the likelihood of errors and inconsistencies, resulting in a more accurate and reliable audit process.
- Version Control Integration: VersionVault’s tight integration with version control systems allows for tracing components back to their origins, aiding in vulnerability analysis.
- Dependency Tracking: VersionVault’s ability to track dependencies simplifies the identification of transitive dependencies, ensuring comprehensive SBOM generation.
- Reporting Capabilities: VersionVault’s reporting features can provide summaries of SBOM contents, facilitating easier auditing.
SBOM Auditing Methods and Tools
SBOM auditing is crucial for understanding and mitigating security risks within software supply chains. Effective auditing involves a combination of manual inspection and automated analysis, each with its own strengths and weaknesses. The choice of method often depends on the size and complexity of the SBOM, available resources, and the level of risk tolerance.
Manual and automated SBOM auditing techniques offer distinct advantages. Manual reviews allow for in-depth analysis of specific components and relationships, potentially uncovering subtle vulnerabilities missed by automated tools. However, manual audits are time-consuming, prone to human error, and struggle to scale effectively with increasingly complex SBOMs. Automated tools, conversely, offer speed and scalability, allowing for rapid analysis of large datasets.
They can identify common vulnerabilities and exposures (CVEs) and other potential issues, but may require significant configuration and expertise to achieve optimal results and may miss context-dependent vulnerabilities.
Automated SBOM Analysis Tools
Automated tools significantly accelerate the SBOM auditing process, enabling efficient identification of potential vulnerabilities and compliance issues. These tools leverage various techniques, including vulnerability databases and dependency analysis, to pinpoint potential risks. The selection of a suitable tool depends on factors such as the SBOM format, the specific vulnerabilities being targeted, and the level of integration required with existing development workflows.
Several tools provide automated SBOM analysis capabilities. Examples include Grype, Trivy, and CycloneDX. Grype, for example, is an open-source vulnerability scanner that integrates well with various container registries and CI/CD pipelines. Trivy is another popular option, known for its speed and ease of use, while CycloneDX offers a robust platform for SBOM creation, management, and analysis. These tools can scan SBOMs, compare them against vulnerability databases, and report potential security risks, allowing developers to address vulnerabilities proactively.
Challenges of Auditing Large and Complex SBOMs
Auditing large and complex SBOMs presents significant challenges. The sheer volume of data involved can overwhelm manual processes, making automated tools almost essential. Further complications arise from the nested dependencies within software projects. Tracing vulnerabilities through multiple layers of indirect dependencies can be incredibly difficult, even with automated assistance. Inconsistent SBOM formats and metadata also pose significant obstacles, making data aggregation and analysis more complex.
Finally, the constant evolution of software and its dependencies requires ongoing monitoring and re-auditing to ensure accuracy and relevance of findings.
Remediating SBOM Audit Vulnerabilities
Once vulnerabilities are identified during an SBOM audit, a systematic remediation process is essential. This process typically involves several key steps. First, the identified vulnerabilities must be prioritized based on their severity and potential impact. Then, the root cause of each vulnerability must be investigated and verified. Appropriate patches or updates should then be identified and applied, followed by thorough testing to ensure that the remediation was effective.
Finally, the updated SBOM should be generated and re-audited to verify that the vulnerabilities have been successfully addressed. This iterative process ensures ongoing security and compliance.
Comparison of SBOM Auditing Tools
Choosing the right SBOM auditing tool is crucial for effective vulnerability management. The following table compares four popular tools, highlighting their strengths and weaknesses.
| Name | Features | Strengths | Weaknesses |
|---|---|---|---|
| Grype | Vulnerability scanning, SBOM parsing (various formats), integration with container registries and CI/CD pipelines | Open-source, widely adopted, good community support, strong integration capabilities | Can be complex to configure, requires some technical expertise |
| Trivy | Vulnerability scanning, SBOM parsing (various formats), image scanning, dependency analysis | Fast, easy to use, supports multiple languages and package managers | Limited advanced features compared to some other tools |
| CycloneDX | SBOM creation, management, and analysis, vulnerability scanning (through integrations), various formats supported | Comprehensive platform, strong focus on SBOM lifecycle management, flexible and extensible | Can be more resource-intensive than some other tools, requires more setup |
| Snyk | Vulnerability scanning, SBOM analysis, remediation guidance, integration with development workflows | User-friendly interface, strong remediation capabilities, good integration with various development tools | Proprietary software (paid subscription required), potentially more expensive than open-source alternatives |
SBOM and Compliance Requirements
Software Bill of Materials (SBOMs) are no longer a nice-to-have; they’re rapidly becoming a must-have for organizations striving for robust security and compliance. The increasing complexity of software supply chains, coupled with heightened regulatory scrutiny, necessitates a thorough understanding of how SBOMs contribute to meeting various compliance obligations.SBOMs significantly aid organizations in achieving compliance by providing a comprehensive inventory of all software components within a system.
This detailed view allows for better vulnerability management, license compliance tracking, and overall risk reduction. This transparency is crucial in demonstrating due diligence to auditors and regulators, minimizing potential penalties and reputational damage.
Relevant Industry Regulations and Standards, Software bill of materials versionvault auditing
Several industry regulations and standards explicitly or implicitly mandate the use of SBOMs, or at least require a level of software transparency that SBOMs effectively address. For example, the National Institute of Standards and Technology (NIST) strongly recommends the use of SBOMs, and various government contracts now often include requirements for their provision. Furthermore, initiatives like the Open Source Software Security Foundation (OpenSSF) actively promote SBOM adoption and standardization, pushing for wider industry acceptance.
Specific regulations like the EU’s Cybersecurity Act and the proposed Software Supply Chain Security legislation in the United States are driving this trend further, highlighting the growing importance of SBOMs in securing software supply chains.
How SBOMs Facilitate Compliance
SBOMs act as a central repository of information about the components comprising a software system. This detailed inventory enables organizations to:
- Identify and mitigate vulnerabilities: By knowing precisely which components are included, organizations can proactively address known vulnerabilities in those components, minimizing their exposure to attacks.
- Ensure license compliance: SBOMs provide a clear picture of the licenses associated with each component, facilitating compliance with open-source licensing requirements and avoiding potential legal issues.
- Track component origins and provenance: This transparency helps in identifying potentially malicious or compromised components early in the development cycle.
- Demonstrate due diligence: In the event of a security incident or audit, the SBOM serves as demonstrable proof of the organization’s efforts to understand and manage its software supply chain.
Consequences of SBOM Non-Compliance
Failure to adhere to SBOM requirements can lead to a variety of serious consequences:
- Financial penalties: Non-compliance with government regulations or contractual obligations can result in significant fines.
- Reputational damage: Security breaches linked to unmanaged software components can severely damage an organization’s reputation and erode customer trust.
- Legal liabilities: Issues with open-source licensing compliance can lead to costly legal battles.
- Delayed product releases: The discovery of vulnerabilities late in the development cycle can cause significant delays in product releases.
For example, a hypothetical medical device manufacturer failing to provide an SBOM could face severe penalties if a vulnerability in a component leads to a malfunction causing patient harm. Similarly, a company failing to comply with a government contract’s SBOM requirements might lose the contract and face reputational damage.
Steps to Ensure SBOM Compliance
Implementing a robust SBOM program requires a multi-faceted approach. The following steps are crucial for achieving and maintaining SBOM compliance:
- Establish a clear SBOM policy: Define the scope, format, and frequency of SBOM generation within the organization.
- Integrate SBOM generation into the software development lifecycle (SDLC): Automate SBOM generation as part of the build process to ensure consistency and accuracy.
- Select appropriate SBOM tools and technologies: Choose tools that align with your organization’s needs and integrate seamlessly with your existing infrastructure.
- Train personnel on SBOM best practices: Ensure developers and security teams understand the importance of SBOMs and how to use them effectively.
- Regularly audit and update SBOMs: Maintain up-to-date SBOMs to reflect changes in the software components and their associated vulnerabilities.
- Establish a process for vulnerability remediation: Develop a clear process for addressing identified vulnerabilities in software components.
Visualizing SBOM Data
Understanding the complex web of dependencies within a software project can be challenging. A Software Bill of Materials (SBOM) provides a structured representation of these dependencies, but simply reading a text-based SBOM can be overwhelming. Visualizing this data is crucial for effective analysis and risk management. This allows for quicker identification of vulnerabilities and simplifies the understanding of the software’s composition.Visual representations significantly improve the understanding of software components and their relationships.
By transforming the raw data of an SBOM into a graphical format, we can easily identify critical dependencies, potential vulnerabilities, and areas of concern. This visual approach allows for faster identification of patterns and anomalies that might be missed in a textual representation.
Dependency Graph Representation
A common and effective way to visualize SBOM data is through a dependency graph. This type of graph uses nodes to represent software components (libraries, frameworks, etc.) and edges to represent the dependencies between them. The size of the nodes can be proportional to the size or importance of the component, and the color can indicate the risk level associated with that component based on known vulnerabilities.
A directed edge indicates the direction of the dependency. For instance, if library A depends on library B, an arrow would point from A to B. This immediately clarifies which components are reliant on others.
Example of a Hypothetical SBOM Visualization
Imagine a hypothetical application with the following components: Application Core, Database Library, UI Framework, and Logging Library. The Application Core depends on the Database Library and the UI Framework. The UI Framework depends on the Logging Library. A dependency graph would show the Application Core as a central node with arrows pointing to the Database Library and UI Framework nodes.
The UI Framework node would have an arrow pointing to the Logging Library node. The size of the Application Core node could be larger than the others to represent its central role. If a known vulnerability exists within the Logging Library, that node could be highlighted in red to quickly draw attention to the potential risk. This visual representation instantly clarifies the flow of dependencies and highlights potential points of vulnerability.
Benefits of Different Visualization Techniques
Different visualization techniques offer unique advantages depending on the specific needs. For instance, a hierarchical tree structure can be useful for displaying nested dependencies, while a network graph can highlight clusters of interconnected components. Heatmaps can be used to visualize the distribution of vulnerabilities across different components. The choice of visualization method depends on the specific information that needs to be emphasized and the audience’s familiarity with different graph types.
Choosing the right technique significantly impacts the ease of understanding and the speed of analysis.
Conclusive Thoughts
Mastering software bill of materials VersionVault auditing is crucial in today’s complex software landscape. By effectively utilizing VersionVault’s capabilities for SBOM creation, management, and auditing, you gain a significant advantage in identifying and mitigating security risks. Remember, a well-structured SBOM, regularly audited, is not just a compliance requirement; it’s a cornerstone of robust software security. This empowers you to build more secure, reliable, and compliant software, ultimately protecting your organization and your users.
User Queries
What are the limitations of automated SBOM auditing tools?
Automated tools excel at identifying known vulnerabilities based on existing databases. However, they may miss novel or zero-day vulnerabilities, requiring manual review for comprehensive analysis. They also struggle with highly customized or proprietary components.
How often should I audit my SBOMs?
The frequency of SBOM audits depends on your risk tolerance and the frequency of software updates. For critical systems, regular audits (e.g., monthly or even weekly) are recommended. Less critical systems may require less frequent audits.
Can VersionVault integrate with other SBOM tools?
VersionVault’s integration capabilities will vary depending on the specific version and available plugins. Check the VersionVault documentation for details on supported integrations with other SBOM tools and formats.
What happens if my SBOM audit reveals vulnerabilities?
Identifying vulnerabilities through SBOM auditing initiates a remediation process. This involves prioritizing vulnerabilities based on severity, developing and implementing patches, and retesting to ensure the fixes are effective. Documentation of the entire process is crucial.





