How to Optimize a Secure DevOps Pipeline with Automation
How to optimize a secure DevOps pipeline with automation? It’s a question on every security-conscious developer’s mind. In today’s fast-paced world of software development, building a robust and secure pipeline isn’t just a best practice – it’s a necessity. This post dives deep into the strategies and tools you need to create a streamlined, automated process that prioritizes security at every stage, from code commit to deployment.
We’ll explore everything from secure coding practices and Infrastructure as Code (IaC) to continuous integration/continuous delivery (CI/CD) security and robust monitoring. Get ready to level up your DevOps game!
We’ll cover the fundamental principles of secure DevOps, highlighting the critical differences between a secure, automated pipeline and a more traditional, vulnerable approach. We’ll walk through practical examples, showing you how to implement security checks at each stage of your pipeline, and we’ll explore various tools and technologies to help you achieve this. By the end, you’ll have a clear roadmap for building a secure and efficient DevOps pipeline that minimizes risk and maximizes productivity.
Defining Secure DevOps and Automation
Secure DevOps represents a cultural shift and a set of practices that integrate security into every stage of the software development lifecycle (SDLC), from planning and coding to deployment and operations. It’s about building security in, not bolting it on as an afterthought. Automation plays a crucial role in achieving this, enabling speed, consistency, and reduced human error – all vital for robust security.The core principles of Secure DevOps revolve around shared responsibility, automation, continuous feedback, and collaboration.
Security is not solely the responsibility of a dedicated security team; it’s a collective effort involving developers, operations, and security professionals working together throughout the entire pipeline. This collaborative approach fosters a culture of security awareness and accountability, ensuring that security is considered at every step.
Benefits of Automating a DevOps Pipeline
Automating a DevOps pipeline offers significant advantages, particularly in enhancing security. Automation reduces the risk of human error, a common source of security vulnerabilities. Automated processes are consistent and repeatable, minimizing inconsistencies that could introduce security weaknesses. Furthermore, automation enables faster release cycles, allowing for quicker identification and remediation of vulnerabilities. This speed is crucial in today’s fast-paced software development environment.
The efficiency gains translate to cost savings and improved resource allocation.
Examples of Security Vulnerabilities in a Non-Automated DevOps Pipeline
Manual processes are inherently prone to errors, leading to security risks in a non-automated DevOps pipeline. For instance, misconfiguration of servers during manual deployment is a common occurrence, potentially exposing sensitive data or creating access points for attackers. Lack of standardized security checks at each stage can also lead to vulnerabilities slipping through the cracks. Inconsistent application of security policies across different environments increases the attack surface.
Imagine a scenario where a developer manually installs a library with known vulnerabilities because they missed a security update notice; this could easily compromise the entire application. Finally, the absence of automated testing for security flaws significantly increases the likelihood of deploying insecure code into production.
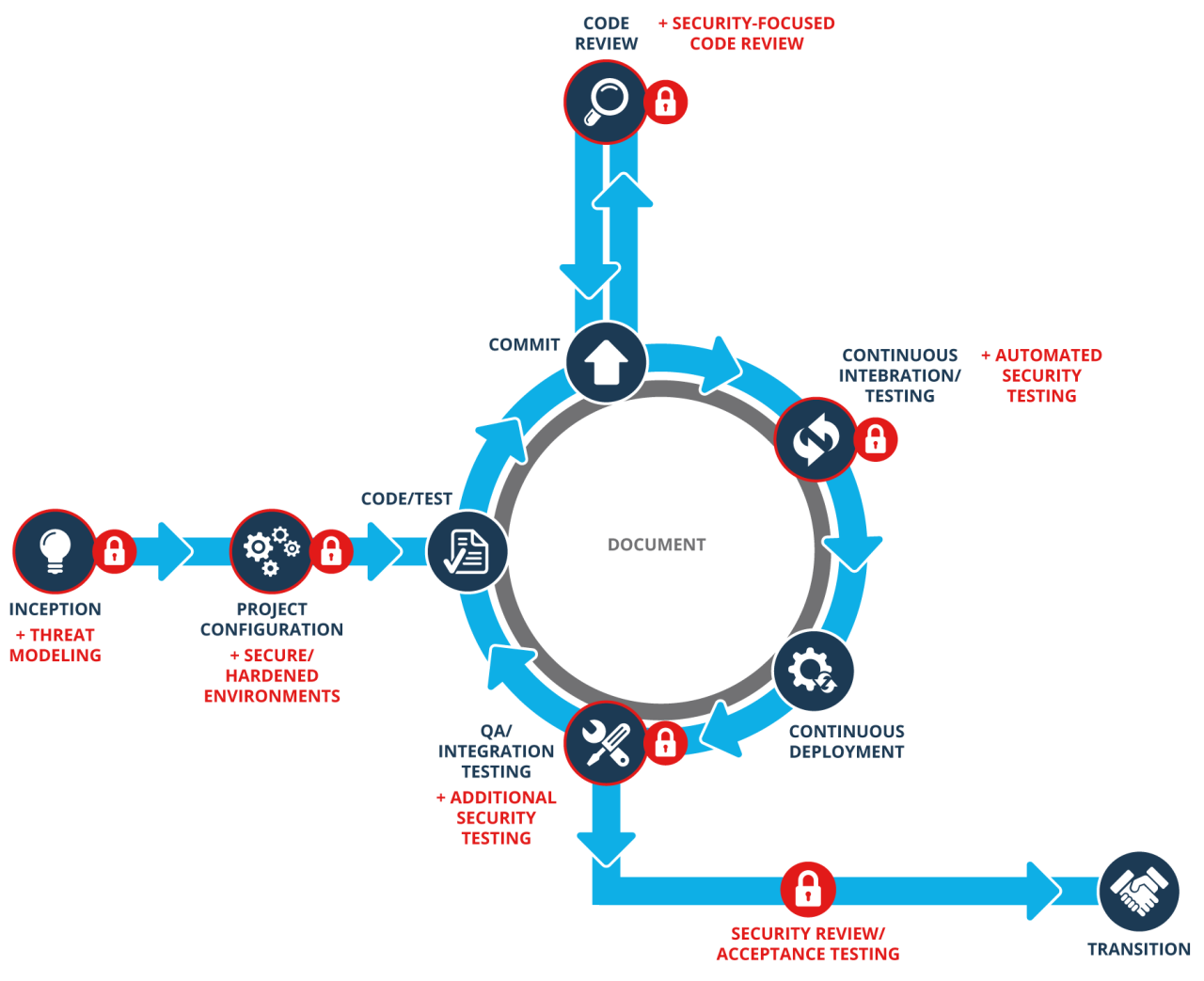
Conceptual Model of a Secure, Automated DevOps Pipeline
Imagine a pipeline visualized as a series of interconnected stages. It begins with code commits, which trigger automated security scans (static and dynamic analysis) to identify potential vulnerabilities early in the development process. Successful scans move the code to an automated build and integration stage. Automated testing, including security testing, ensures functionality and identifies security flaws before deployment.
Next, the code is deployed to a staging environment, where further automated security checks and penetration testing are performed. Upon successful completion, the code is automatically deployed to production. Continuous monitoring and logging throughout the pipeline provide real-time visibility into system health and security posture, enabling immediate response to threats. This entire process is orchestrated by automated tools and workflows, minimizing manual intervention and human error.
The feedback loop from each stage is crucial; any security issue detected triggers immediate action, preventing insecure code from reaching production. This model emphasizes continuous integration, continuous delivery (CI/CD), and continuous security (Sec).
Implementing Secure Coding Practices
Secure coding is the cornerstone of a robust and secure DevOps pipeline. Without secure code practices, even the most sophisticated automation tools will be ineffective against vulnerabilities. This section delves into best practices for writing secure code, leveraging static and dynamic analysis tools, and provides a practical checklist for developers.
Best Practices for Writing Secure Code
Secure coding involves proactively preventing vulnerabilities rather than reacting to them after deployment. This requires a shift in mindset, focusing on security from the initial design phase. Key principles include input validation (sanitizing all user inputs to prevent injection attacks), output encoding (preventing cross-site scripting or XSS attacks by properly encoding data before displaying it), secure authentication and authorization mechanisms (using strong passwords, multi-factor authentication, and least privilege principles), and error handling (preventing information leakage through error messages).
Furthermore, developers should minimize the attack surface by using only necessary libraries and frameworks and keeping them updated. Regular security training and code reviews are essential to reinforce these practices.
Static and Dynamic Code Analysis Tools
Static analysis tools examine code without executing it, identifying potential vulnerabilities based on coding patterns and known weaknesses. They provide immediate feedback, helping developers catch problems early in the development lifecycle. Examples include SonarQube, FindBugs, and PMD. Dynamic analysis tools, conversely, examine the code during runtime, identifying vulnerabilities that only appear during execution. These tools are often used for penetration testing and can reveal runtime errors and security flaws missed by static analysis.
Examples include OWASP ZAP and Burp Suite. Both types of analysis are crucial for a comprehensive security approach; they offer complementary perspectives on code security.
Secure Coding Guidelines Checklist for Developers
Before initiating any coding, developers should review and follow a comprehensive checklist. This checklist should cover several key areas:
- Input Validation: Always validate and sanitize all user inputs to prevent injection attacks (SQL injection, cross-site scripting, command injection).
- Output Encoding: Properly encode all data before displaying it to prevent cross-site scripting (XSS) vulnerabilities.
- Authentication and Authorization: Implement robust authentication and authorization mechanisms using strong passwords, multi-factor authentication, and the principle of least privilege.
- Session Management: Use secure session management techniques to prevent session hijacking.
- Error Handling: Handle errors gracefully and avoid revealing sensitive information in error messages.
- Data Protection: Protect sensitive data using encryption, access control, and data loss prevention (DLP) techniques.
- Secure Libraries and Frameworks: Use only necessary libraries and frameworks, and keep them updated to the latest versions.
- Regular Security Updates: Regularly update software and dependencies to patch known vulnerabilities.
- Code Reviews: Conduct regular code reviews to identify potential security flaws.
- Security Testing: Regularly perform security testing (static and dynamic analysis, penetration testing) to identify and remediate vulnerabilities.
Comparison of Popular Secure Coding Tools
The choice of security tool depends on specific needs and budget. Here’s a comparison of some popular options:
| Tool | Type | Features | Limitations |
|---|---|---|---|
| SonarQube | Static | Comprehensive code analysis, supports multiple languages, integrates with CI/CD pipelines. | Can generate false positives, requires configuration and expertise. |
| FindBugs | Static | Focuses on Java code, identifies common bugs and vulnerabilities. | Limited language support compared to SonarQube. |
| OWASP ZAP | Dynamic | Open-source penetration testing tool, supports various attack vectors. | Requires expertise to use effectively, can be time-consuming. |
| Burp Suite | Dynamic | Powerful penetration testing tool with a wide range of features, both free and professional versions. | Professional version is expensive, requires significant expertise. |
Infrastructure as Code (IaC) and Security
Infrastructure as Code (IaC) is a revolutionary approach to managing and provisioning infrastructure. Instead of manually configuring servers and networks, IaC uses code to define and manage these resources. This automated approach offers significant advantages in terms of speed, consistency, and repeatability, but it also introduces new security considerations that must be carefully addressed. Ignoring these can lead to significant vulnerabilities in your systems.IaC significantly improves security when implemented correctly.
By defining infrastructure in code, we establish a single source of truth, making it easier to track changes, enforce consistency, and audit configurations. This reduces human error, a primary cause of many security breaches. The ability to version control IaC code also allows for rollback to previous, known-good states in case of misconfigurations or attacks.
IaC Security Risks and Mitigation Strategies
Several security risks are inherent to IaC if not properly managed. These risks stem from the nature of code itself, its accessibility, and the potential for misconfigurations. Understanding these risks and implementing appropriate mitigation strategies is crucial for a secure DevOps pipeline.
- Risk: Unsecured Code Repositories: Storing IaC code in publicly accessible repositories or without proper access controls exposes sensitive information like API keys, passwords, and network configurations. This can lead to unauthorized access and compromise of your infrastructure.
- Mitigation: Implement robust access control mechanisms to limit access to your code repositories. Utilize private repositories and employ strong authentication and authorization methods. Regularly audit access permissions and revoke unnecessary privileges. Consider using secrets management tools to store sensitive data outside of the codebase.
- Risk: Insecure IaC Configurations: Misconfigurations in IaC templates can lead to vulnerabilities in the provisioned infrastructure. For example, leaving default passwords, exposing ports unnecessarily, or failing to implement proper security groups can create significant security holes.
- Mitigation: Employ rigorous code review processes to identify and rectify insecure configurations. Utilize static analysis tools to automatically scan IaC code for potential vulnerabilities. Implement automated security testing and validation as part of your CI/CD pipeline to catch errors before deployment.
- Risk: Supply Chain Attacks: Compromised modules or libraries used in your IaC code can introduce malicious code into your infrastructure. This attack vector can be difficult to detect and mitigate.
- Mitigation: Use only trusted and vetted modules and libraries. Regularly update dependencies to patch known vulnerabilities. Employ dependency scanning tools to identify and address potential threats in your IaC code.
Secure IaC Implementation with Terraform
Terraform, a popular IaC tool, provides several features to enhance security. By implementing best practices, we can minimize the risks associated with IaC.Let’s consider a simple example of creating an AWS EC2 instance with Terraform, incorporating security best practices: resource "aws_instance" "example" ami = "ami-0c55b31ad2299a701" # Replace with a suitable AMI ID instance_type = "t2.micro" key_name = "my-key-pair" # Replace with your key pair name vpc_security_group_ids = [aws_security_group.allow_ssh.id]resource "aws_security_group" "allow_ssh" name = "allow_ssh" description = "Allow SSH inbound traffic" ingress description = "SSH" from_port = 22 to_port = 22 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] #Restrict this to specific IP addresses in production egress from_port = 0 to_port = 0 protocol = "-1" cidr_blocks = ["0.0.0.0/0"] This example demonstrates the creation of a security group that only allows SSH traffic on port 22 (although in production, this should be restricted to specific IP addresses).
The EC2 instance is then configured to use this secure security group. Remember to replace placeholder values with your actual credentials and resources. This is a simplified example; more complex deployments will require more sophisticated security measures.
Continuous Integration/Continuous Delivery (CI/CD) Security
Integrating security into your CI/CD pipeline isn’t just a best practice; it’s a necessity in today’s threat landscape. By automating security checks throughout the software development lifecycle, you significantly reduce vulnerabilities and improve the overall security posture of your applications. This approach shifts security left, addressing potential issues early in the development process when they are cheaper and easier to fix.Security testing integrated into the CI/CD pipeline ensures that security is not an afterthought but a core component of the software development process.
This proactive approach allows for the identification and mitigation of vulnerabilities before they reach production, minimizing the risk of security breaches and data loss. The automation of these checks speeds up the development process and reduces the manual effort required for security testing.
Integrating Security Testing into the CI/CD Pipeline
Integrating security testing involves strategically placing various security checks at different stages of the CI/CD pipeline. This might include static application security testing (SAST) early in the development cycle, followed by dynamic application security testing (DAST) and penetration testing later in the process. The specific tools and techniques will depend on the project’s needs and complexity, but the goal remains consistent: to identify and remediate security flaws as early as possible.
A well-designed pipeline ensures that only secure code makes it to production.
Implementation of Security Scanning Tools within the CI/CD Process
Numerous security scanning tools are available to automate security checks. For example, SAST tools like SonarQube analyze source code for vulnerabilities without executing the code. DAST tools, such as OWASP ZAP, test running applications to identify vulnerabilities. These tools can be integrated into CI/CD platforms like Jenkins, GitLab CI, or Azure DevOps through plugins or APIs. The output from these scans can be integrated into the CI/CD pipeline, automatically failing builds that exceed a defined threshold of vulnerabilities.
This ensures that developers are immediately alerted to security issues and can address them before the code moves further down the pipeline. For example, a build might be automatically stopped if more than five critical vulnerabilities are detected.
Designing a CI/CD Pipeline Incorporating Automated Security Checks at Various Stages
A secure CI/CD pipeline should incorporate security checks at multiple stages. This could involve:
- Code Analysis (Pre-Commit/Pre-Merge): SAST tools analyze code for common vulnerabilities during code review. This prevents insecure code from even entering the repository.
- Build Stage: Dependency checks identify known vulnerabilities in third-party libraries. Software Composition Analysis (SCA) tools are crucial here.
- Testing Stage: DAST tools scan running applications for vulnerabilities. Unit and integration tests should also include security-focused test cases.
- Deployment Stage: Security scanning of deployed applications and infrastructure is performed before releasing to production. This could include vulnerability scans and configuration checks.
Failing any of these checks should automatically halt the pipeline, requiring remediation before proceeding.
Comparison of Different Approaches to Securing a CI/CD Pipeline
Different organizations may adopt varying approaches to securing their CI/CD pipelines, depending on factors such as their size, budget, and technical expertise. Some may opt for a phased approach, gradually incorporating more security checks over time. Others may prioritize a comprehensive, fully automated system from the outset. The choice between using commercial or open-source tools will also impact the overall approach.
The key is to find a balance between thoroughness and efficiency, ensuring that security doesn’t become a bottleneck in the development process. A well-documented and regularly reviewed security policy is essential for consistent and effective implementation.
Secret Management and Access Control
Protecting sensitive information is paramount in any DevOps pipeline. A breach can have devastating consequences, from financial losses to reputational damage and legal repercussions. Effective secret management and robust access control are crucial for mitigating these risks and ensuring the overall security of your systems. This section will explore best practices for securely handling secrets and managing access throughout your DevOps workflow.
Secure Secret Management Techniques
Secure secret management involves employing strategies and tools to protect sensitive information like API keys, database credentials, and certificates. Simply storing these secrets in plain text within configuration files is unacceptable. Instead, dedicated secret management solutions offer features like encryption at rest and in transit, access control, and auditing capabilities. These solutions often integrate directly with CI/CD pipelines, allowing for secure retrieval and rotation of secrets during deployment.
Examples include HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault. These services typically offer features such as versioning, allowing for easy rollback in case of errors, and automated rotation, minimizing the window of vulnerability associated with compromised secrets. Choosing a solution that aligns with your organization’s infrastructure and security policies is key.
Access Control Models in DevOps
Different access control models govern how users and systems interact with sensitive information. The most common models are Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). RBAC assigns permissions based on roles within an organization, simplifying management and ensuring consistency. For example, a “developer” role might have access to read secrets, while a “deployment” role might have access to read and use them.
ABAC, on the other hand, is more granular, allowing for fine-grained control based on various attributes such as user identity, time of day, and location. This model is beneficial for complex environments requiring highly customized access restrictions. Choosing the right model depends on the complexity of your infrastructure and the level of granularity required. A hybrid approach, combining aspects of both RBAC and ABAC, is often the most effective solution.
Secure Storage and Management of Sensitive Information
Storing API keys, database credentials, and other sensitive information requires a multi-layered approach. Never hardcode these credentials directly into your code or configuration files. Instead, leverage dedicated secret management solutions mentioned previously. These services encrypt secrets at rest and in transit, ensuring confidentiality even if the underlying infrastructure is compromised. For example, when deploying an application to a cloud environment, the CI/CD pipeline can retrieve the necessary database credentials from the secret management service, decrypt them securely, and use them only during the deployment process.
After deployment, these credentials are not stored within the application itself. Regular auditing and logging of access attempts are essential to detect and respond to potential security incidents. The principle of least privilege should be strictly enforced, ensuring that users and systems only have access to the minimum necessary secrets.
Implementing Least Privilege Access Control
The principle of least privilege dictates that users and systems should only have the necessary permissions to perform their tasks. This minimizes the impact of a potential compromise. In a DevOps pipeline, this translates to granting specific roles only the access needed for each stage. For instance, a build server might only need read access to the source code repository and the necessary secrets for building the application, but it should not have write access to the production environment.
Similarly, deployment servers should only have the permissions required for deployment and not for modifying the underlying infrastructure. Implementing least privilege requires careful planning and configuration, but it is a crucial step in enhancing the security of your DevOps pipeline. Regular reviews of access rights are essential to ensure that permissions remain appropriate and that unnecessary access is revoked promptly.
Monitoring and Logging for Security
Robust monitoring and logging are the cornerstones of a secure DevOps pipeline. Without them, identifying and responding to security breaches becomes a near-impossible task, leaving your organization vulnerable to significant damage. Effective monitoring and logging provide the visibility needed to detect suspicious activity, analyze trends, and ultimately, prevent future attacks.A comprehensive monitoring and logging strategy proactively identifies and mitigates security risks.
This involves collecting detailed logs from various sources, analyzing them for anomalies, and implementing automated responses to detected threats. This proactive approach significantly reduces the impact of security incidents and allows for faster remediation.
Centralized Log Management
A centralized log management system aggregates logs from diverse sources—servers, applications, databases, network devices, and cloud platforms—into a single, searchable repository. This consolidated view provides a holistic understanding of system activity, simplifying security analysis and incident response. Effective systems often employ technologies like Elasticsearch, Logstash, and Kibana (ELK stack) or similar solutions, offering features like real-time log analysis, advanced search capabilities, and customizable dashboards.
Without a centralized system, tracking down the root cause of a security incident becomes a time-consuming and often frustrating exercise.
Real-Time Threat Detection
Real-time threat detection involves using advanced analytics to identify malicious activity as it happens. This typically involves analyzing log data for patterns indicative of attacks, such as unusual login attempts, unauthorized access, or data exfiltration. Security Information and Event Management (SIEM) systems are frequently used for this purpose, correlating events from multiple sources to identify complex threats that might be missed by individual systems.
For example, a SIEM might detect a suspicious login attempt from an unfamiliar location, combined with an unusual amount of data being accessed, triggering an alert and potentially initiating an automated response such as account lockout.
Security Dashboards and Alerts
Effective security dashboards provide a visual representation of key security metrics and alerts. These dashboards should display critical information such as the number of security events, the severity of threats, and the status of remediation efforts. Customizable dashboards allow security teams to focus on the most relevant information. Alerts should be configured to notify security personnel of critical events in real-time, enabling prompt response and minimizing the impact of incidents.
For instance, an alert could be triggered when a large number of failed login attempts originate from a specific IP address, indicating a potential brute-force attack. A well-designed dashboard might display a heatmap showing the geographic location of login attempts, allowing security teams to quickly identify suspicious activity.
Log Analysis and Threat Identification
Analyzing security logs requires a systematic approach to identify potential threats. This involves searching for specific patterns, anomalies, and known indicators of compromise (IOCs). Regular reviews of security logs, coupled with automated analysis tools, help detect suspicious activity that might otherwise go unnoticed. For example, the detection of a large number of failed login attempts from a single IP address could indicate a brute-force attack.
Similarly, unusual access patterns to sensitive data or the presence of known malware signatures in logs can signal a security breach. Analyzing log data in conjunction with other sources of intelligence, such as threat feeds, can improve the accuracy of threat identification.
Automation Tools and Technologies

Automating your Secure DevOps pipeline is crucial for efficiency and security. The right tools can significantly reduce human error, accelerate deployment cycles, and strengthen your overall security posture. Choosing and integrating these tools effectively is key to a robust and secure system. This section explores popular automation tools, their features, integration strategies, and the role of scripting languages in automating security tasks.
The landscape of DevOps automation tools is vast and constantly evolving. Selecting the right tools depends heavily on your specific needs, existing infrastructure, and team expertise. However, several tools consistently stand out for their capabilities in secure DevOps.
Popular Automation Tools for Secure DevOps
Several tools excel in different aspects of secure DevOps automation. Understanding their strengths and weaknesses allows for strategic selection and integration.
- Jenkins: A widely adopted open-source automation server, Jenkins excels in CI/CD pipeline orchestration. It offers a vast plugin ecosystem for integrating various security tools and automating tasks like code analysis, testing, and deployment.
- GitLab CI/CD: Tightly integrated with GitLab’s version control system, GitLab CI/CD streamlines the process from code commit to deployment. It offers built-in security features like vulnerability scanning and SAST/DAST integration.
- GitHub Actions: Similar to GitLab CI/CD, GitHub Actions provides a platform for automating workflows directly within GitHub. It allows for seamless integration with other GitHub services and offers extensive customization options for security automation.
- Ansible: Ansible is a powerful configuration management and automation tool. It simplifies infrastructure provisioning, configuration management, and application deployment, all crucial aspects of a secure DevOps pipeline. Its agentless architecture enhances security.
- Terraform: Terraform is an Infrastructure as Code (IaC) tool that allows you to define and manage your infrastructure in a declarative manner. This ensures consistency and repeatability, reducing the risk of misconfigurations and security vulnerabilities.
Comparing Automation Tool Features and Capabilities, How to optimize a secure devops pipeline with automation
The choice between these tools often comes down to specific needs and existing infrastructure. Here’s a comparison based on key features:
| Feature | Jenkins | GitLab CI/CD | GitHub Actions | Ansible | Terraform |
|---|---|---|---|---|---|
| CI/CD Orchestration | Excellent | Excellent | Excellent | Good | Limited (Focus on IaC) |
| Integration with Version Control | Excellent (Plugins) | Excellent (Built-in) | Excellent (Built-in) | Good (via scripts) | Good (via providers) |
| Security Features | Extensive (Plugins) | Good (Built-in) | Good (Built-in) | Moderate (via modules) | Good (via providers and modules) |
| Ease of Use | Moderate (Steeper learning curve) | Good | Good | Good | Moderate (Requires IaC understanding) |
| Scalability | Excellent | Excellent | Excellent | Excellent | Excellent |
Integrating Automation Tools into a Cohesive Pipeline
Effective integration is key. A typical pipeline might involve Jenkins orchestrating the overall process, GitLab CI/CD handling build and test stages, Ansible managing infrastructure, and Terraform provisioning resources. Tools communicate through APIs, shared configuration files, and standardized output formats.
Automating Security Tasks with Scripting Languages
Scripting languages like Python and Bash are invaluable for automating repetitive security tasks. These scripts can integrate with various tools and APIs to enhance security.
For example, a Python script could automate vulnerability scanning using a tool like Nessus, analyzing the results, and generating reports. A Bash script could automate the deployment of security configurations to servers using Ansible.
Example (Python snippet for checking file permissions):
import osimport statdef check_permissions(filepath, expected_permissions): permissions = stat.S_IMODE(os.stat(filepath).st_mode) return permissions == expected_permissions#Example Usagefilepath = "/path/to/file"expected_permissions = 0o640 #Example permissionsif check_permissions(filepath, expected_permissions): print(f"File filepath has correct permissions.")else: print(f"File filepath has incorrect permissions.")
Security Audits and Compliance: How To Optimize A Secure Devops Pipeline With Automation

Regular security audits and adherence to compliance standards are critical for maintaining the integrity and trustworthiness of your DevOps pipeline. A robust security posture isn’t just about preventing breaches; it’s about demonstrating due diligence and building confidence with stakeholders. This involves proactively identifying vulnerabilities, addressing weaknesses, and ensuring your processes meet regulatory requirements.Regular security audits are a systematic process for evaluating the security controls and practices within your DevOps pipeline.
These audits provide a snapshot of your current security posture, identifying potential weaknesses and areas for improvement. They help to ensure that your security measures are effective and up-to-date, protecting your organization from potential threats. The frequency of these audits depends on factors such as your risk tolerance, industry regulations, and the complexity of your pipeline.
Conducting Regular Security Audits
A structured approach is crucial for effective security audits. This typically involves defining the scope of the audit, identifying key security controls to assess, and selecting appropriate auditing methodologies. The process involves reviewing code, infrastructure configurations, security policies, and the overall CI/CD process. This often involves manual code reviews, automated vulnerability scans, penetration testing, and compliance checks against relevant standards.
The results are documented, prioritized, and remediated in a timely manner. For example, a monthly audit might focus on a specific component of the pipeline, while a yearly audit offers a more comprehensive overview.
Ensuring Compliance with Security Standards and Regulations
Compliance with industry standards and regulations is paramount. Different industries have specific requirements, such as HIPAA for healthcare, PCI DSS for payment card processing, and GDPR for data privacy in Europe. These regulations often mandate specific security controls and auditing practices. Maintaining compliance requires a deep understanding of the relevant regulations and implementing the necessary controls within your DevOps pipeline.
This might involve integrating security scanners that specifically target vulnerabilities related to these regulations, maintaining detailed audit trails, and regularly reviewing and updating your security policies to reflect changes in the regulatory landscape. For instance, a company handling sensitive financial data must adhere strictly to PCI DSS standards, requiring regular audits and vulnerability assessments.
Security Audit Checklist for a DevOps Pipeline
A comprehensive security audit requires a systematic approach. The following checklist provides a framework:
- Code Security: Review code for vulnerabilities using static and dynamic analysis tools. Check for secure coding practices and adherence to coding standards.
- Infrastructure Security: Assess the security of infrastructure components, including servers, networks, and databases. Verify proper configuration, patching, and access controls.
- CI/CD Security: Examine the security of the CI/CD pipeline itself, ensuring secure integration of tools and processes. Check for vulnerabilities in the pipeline tools and configurations.
- Secret Management: Evaluate the security of secret management practices, including the storage, access, and rotation of sensitive information. Ensure secrets are encrypted at rest and in transit.
- Access Control: Verify the effectiveness of access control mechanisms, ensuring that only authorized personnel have access to sensitive resources. Review user permissions and roles.
- Monitoring and Logging: Assess the adequacy of monitoring and logging mechanisms, ensuring that security events are properly recorded and analyzed. Verify the integrity and security of logs themselves.
- Compliance: Check compliance with relevant security standards and regulations (e.g., ISO 27001, SOC 2, HIPAA, PCI DSS).
Reporting Mechanisms for Security Audit Findings
Effective reporting is essential for communicating audit results and driving remediation efforts. Reports should clearly Artikel identified vulnerabilities, their severity, and recommended remediation steps. They should also include a timeline for addressing the identified issues. Different reporting mechanisms can be used, including:
- Formal reports: Detailed documents summarizing audit findings, including evidence and recommendations.
- Dashboards: Interactive dashboards providing a visual overview of security posture and key metrics.
- Automated alerts: Real-time alerts notifying security teams of critical vulnerabilities.
- Issue tracking systems: Integration with issue tracking systems to manage and track remediation efforts.
For example, a formal report might use a standardized vulnerability scoring system (like CVSS) to prioritize findings, while a dashboard could display the number of open vulnerabilities and their severity levels.
Closing Summary
Optimizing a secure DevOps pipeline with automation is a journey, not a destination. It requires ongoing vigilance, adaptation, and a commitment to continuous improvement. By embracing the principles and practices Artikeld in this post, you can significantly reduce your security vulnerabilities, accelerate your release cycles, and build a more reliable and robust software delivery process. Remember that security is everyone’s responsibility, so fostering a culture of security within your team is crucial for long-term success.
Start building that secure pipeline today – your future self will thank you!
Detailed FAQs
What are the biggest risks of NOT automating security in a DevOps pipeline?
Manual processes are error-prone, slow down releases, and leave significant gaps in security coverage. This increases the likelihood of vulnerabilities being missed, leading to breaches and compliance issues.
How do I choose the right automation tools for my needs?
Consider your existing infrastructure, team expertise, and the specific security needs of your application. Start with a small pilot project to test different tools and find the best fit.
How often should I conduct security audits of my DevOps pipeline?
Regular audits, ideally quarterly or semi-annually, are crucial. The frequency should depend on your risk tolerance and the complexity of your pipeline.
What are some common compliance regulations impacting DevOps security?
Common regulations include GDPR, HIPAA, PCI DSS, and SOC 2, depending on your industry and the data you handle. Ensure your pipeline complies with all relevant standards.