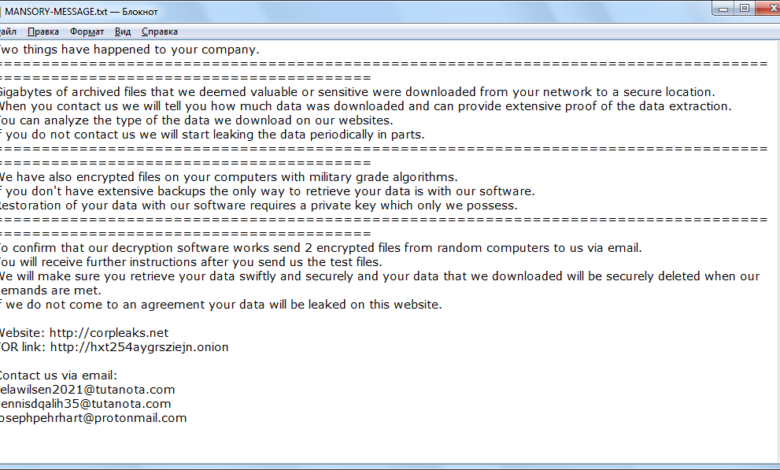
Nefilim Ransomware Hits Victorias Secret & Taiwan Refinery
Nefilim ransomware hits victoria secrets and taiwan oil refinery – Nefilim ransomware hits Victoria’s Secret and a major Taiwan oil refinery – talk about a one-two punch! This massive cyberattack raises serious questions about global cybersecurity vulnerabilities and the increasingly audacious tactics of ransomware gangs. We’re diving deep into the details of this incident, exploring the potential impact on both businesses and international relations. Get ready for a rollercoaster ride through the world of high-stakes cybercrime.
From the technical intricacies of the Nefilim ransomware itself to the potential for widespread data breaches and economic disruption, this story has it all. We’ll examine the likely motivations behind the attacks, the potential consequences for both victims, and what this all means for the future of cybersecurity. Buckle up, because this is a wild ride.
Nefilim Ransomware
The recent attacks on Victoria’s Secret and a Taiwanese oil refinery by the Nefilim ransomware highlight the escalating threat posed by sophisticated ransomware operations. While details remain scarce, analysis of available information paints a picture of a highly capable and potentially lucrative strain. Understanding its technical characteristics is crucial for developing effective mitigation strategies.
Nefilim Ransomware: Technical Characteristics
The specific technical details of Nefilim ransomware are currently limited due to the relatively recent emergence of this threat actor. However, based on reports and observed behaviors, we can infer some key characteristics. The ransomware likely employs advanced evasion techniques to bypass security software and remain undetected for an extended period. Its ability to successfully target high-profile organizations suggests a degree of sophistication in its development and deployment.
Further investigation is needed to fully understand its capabilities, including its command-and-control infrastructure and its resilience to various security measures.
Encryption Methods Used by Nefilim
Nefilim’s encryption method is unknown at this time, though it’s highly probable that it utilizes a robust, asymmetric encryption algorithm like RSA or ECC, coupled with a symmetric algorithm like AES for faster encryption of large files. This combination offers a balance between security and speed, making decryption difficult without the decryption key held by the attackers. The specific implementation details, including key lengths and modes of operation, would need further analysis of recovered samples.
Similar ransomware families often use variations of AES-256 or ChaCha20, algorithms known for their strength and computational efficiency.
Nefilim Ransomware: Attack Vectors
Initial reports suggest Nefilim may leverage multiple attack vectors. Phishing emails containing malicious attachments or links are a likely entry point, exploiting human error to gain initial access. Exploiting vulnerabilities in unpatched software, particularly in network devices or servers, is another probable vector. The success of the attacks against large organizations hints at the possibility of utilizing more advanced techniques, such as supply chain attacks or zero-day exploits.
A comprehensive security posture, encompassing robust endpoint protection, regular patching, and employee security awareness training, is essential to mitigate these risks.
Comparison with Other Prominent Ransomware Families
While detailed comparisons require further analysis, Nefilim appears to share some characteristics with other high-profile ransomware families like Ryuk and REvil. These similarities might include sophisticated evasion techniques, the targeting of high-value organizations, and the use of double extortion tactics (data encryption coupled with data exfiltration). However, without access to the source code and detailed operational data, pinpointing precise similarities or unique features remains challenging.
Further research is needed to definitively place Nefilim within the ransomware landscape.
Hypothetical Mitigation Strategy Against Nefilim Infections
A multi-layered approach is necessary to effectively mitigate the risk of Nefilim infections. This strategy should include: robust endpoint detection and response (EDR) solutions to identify and contain malicious activity; regular patching and updates of all software and operating systems; strong network security measures, including firewalls and intrusion detection systems; employee security awareness training to prevent phishing attacks; regular backups of critical data stored offline or in an immutable storage solution; and incident response planning to ensure a swift and effective response in the event of an infection.
Furthermore, proactive threat hunting and vulnerability assessments can significantly reduce the attack surface. This layered approach aims to disrupt the attack at multiple stages, minimizing the potential impact of a successful breach.
Victoria’s Secret Data Breach Impact
A ransomware attack targeting a company like Victoria’s Secret, with its vast customer database and sensitive financial information, could have devastating consequences. The potential fallout extends far beyond immediate financial losses, impacting the brand’s reputation, customer trust, and legal standing. Understanding the breadth of this impact is crucial to assessing the long-term effects on the company and its stakeholders.
Types of Compromised Data
The potential data loss in a Victoria’s Secret breach is significant. Customer records could include names, addresses, email addresses, phone numbers, dates of birth, and potentially credit card information and purchase history. Beyond customer data, the attackers could also gain access to internal financial records, employee information, intellectual property related to designs and marketing strategies, and confidential supplier agreements.
The sheer volume and sensitivity of this data make the consequences exceptionally severe.
Financial and Reputational Damage
The financial damage from a Victoria’s Secret data breach would be multi-faceted. Immediate costs would include incident response, legal fees, credit monitoring services for affected customers, and potential fines and penalties. Beyond these direct costs, the long-term damage to the brand’s reputation could be far more significant. Loss of customer trust, decreased sales, and damage to the brand image could lead to substantial financial losses that extend for years.
Consider the impact on customer loyalty – a major breach could drive customers to competitors, causing irreversible damage to market share. The company might also face a decline in investor confidence, leading to a drop in stock value.
Legal Ramifications
Victoria’s Secret faces numerous legal ramifications following a data breach. Depending on the jurisdiction and the specific regulations violated, the company could face hefty fines under laws like GDPR (in Europe) or CCPA (in California). Class-action lawsuits from affected customers are almost certain, demanding compensation for damages, including identity theft and financial losses. Furthermore, regulatory investigations from bodies like the FTC (Federal Trade Commission) in the US are likely, potentially leading to further penalties and enforcement actions.
The company’s insurance coverage would be crucial in mitigating these costs, but the total financial burden could still be enormous.
Potential Data Loss Categories and Impact
| Data Category | Impact on Customers | Impact on Victoria’s Secret | Potential Legal Ramifications |
|---|---|---|---|
| Customer Personally Identifiable Information (PII) | Identity theft, fraud, harassment | Reputational damage, loss of customer trust, fines | Class-action lawsuits, regulatory fines (e.g., GDPR, CCPA) |
| Financial Data (Credit Card Information) | Financial loss, fraudulent transactions | Financial losses, chargeback fees, PCI DSS non-compliance fines | Class-action lawsuits, regulatory fines |
| Intellectual Property (Designs, Marketing Strategies) | N/A | Competitive disadvantage, loss of revenue | Civil lawsuits for intellectual property theft |
| Employee Data | N/A | Legal and reputational damage, potential for blackmail | Legal action from employees, potential regulatory fines |
Taiwan Oil Refinery Attack Implications
The Nefilim ransomware attack on a Taiwanese oil refinery presents a serious threat, not only to Taiwan’s domestic energy security but also with wider economic and geopolitical ramifications. The potential disruption to oil refining and distribution could ripple through the island’s economy and beyond, highlighting the vulnerability of critical infrastructure to cyberattacks.The attack’s impact on Taiwan’s oil supply depends heavily on the extent of the damage and the refinery’s capacity.
A prolonged shutdown could lead to fuel shortages, impacting transportation, manufacturing, and power generation. This scenario would be particularly challenging given Taiwan’s reliance on imported oil and its limited domestic reserves. The speed and effectiveness of the refinery’s recovery efforts, as well as the government’s response, will be crucial in mitigating the severity of the disruption.
Economic Consequences of Refinery Shutdown
A shutdown of a major Taiwanese oil refinery would have significant economic consequences. Increased fuel prices are inevitable, impacting consumers and businesses alike. The cost of transportation would rise, affecting the prices of goods and services across the board. Manufacturing industries, heavily reliant on energy, would face production slowdowns or even shutdowns, leading to job losses and decreased economic output.
The overall impact could be substantial, potentially affecting Taiwan’s GDP growth and investor confidence. We can look at similar incidents, such as the Colonial Pipeline ransomware attack in the US in 2021, which caused significant fuel shortages and economic disruption, as a case study for potential impacts. The resulting economic losses in that instance ran into hundreds of millions of dollars.
Geopolitical Ramifications of the Attack
The attack could have significant geopolitical ramifications, particularly given Taiwan’s strained relationship with China. China might attempt to exploit the situation for political gain, potentially exacerbating tensions across the Taiwan Strait. International concern regarding the vulnerability of critical infrastructure to cyberattacks would increase, leading to discussions about international cooperation in cybersecurity and the need for enhanced protective measures.
The incident could also highlight the importance of energy security and diversification strategies for Taiwan and other nations. Furthermore, the incident could serve as a case study for other countries facing similar geopolitical pressures, emphasizing the need for robust cybersecurity defenses.
Strategies for Preventing Similar Attacks
Preventing similar attacks requires a multi-pronged approach. This includes investing in robust cybersecurity infrastructure, implementing stringent access controls and network segmentation, and regularly conducting penetration testing and vulnerability assessments. Employee training on cybersecurity awareness is crucial to mitigate the risk of phishing attacks and social engineering. Collaboration between government agencies, private sector companies, and international organizations is vital for sharing threat intelligence and developing effective countermeasures.
Furthermore, the development and implementation of incident response plans is critical to minimize the impact of successful attacks. The establishment of clear communication channels between stakeholders is also crucial to facilitate rapid response and coordinated efforts.
Short-Term and Long-Term Consequences
The potential consequences of the attack can be categorized as short-term and long-term impacts.
It’s important to note that these are potential consequences and the actual impact will depend on several factors, including the extent of the damage, the speed of recovery efforts, and the effectiveness of government response.
- Short-Term Consequences: Fuel shortages, price increases, transportation disruptions, manufacturing slowdowns, potential social unrest, increased political tensions.
- Long-Term Consequences: Increased investment in cybersecurity infrastructure, changes in energy policies, potential shifts in geopolitical alliances, long-term economic damage, lasting impact on investor confidence, increased insurance premiums for businesses in the energy sector.
Cybersecurity Response and Recovery
The Nefilim ransomware attacks on Victoria’s Secret and the Taiwan oil refinery highlight the critical need for robust cybersecurity preparedness and swift response mechanisms. Both incidents, while differing in scale and industry, underscore the devastating consequences of successful ransomware deployments and the importance of proactive security measures. Understanding the response and recovery efforts of these organizations provides valuable insights into best practices and areas for improvement.Victoria’s Secret’s response likely involved several key steps, beginning with immediate containment of the attack.
This would have included isolating affected systems from the network to prevent further lateral movement of the ransomware. Simultaneously, a thorough investigation would have commenced to determine the extent of the breach, identifying compromised data and systems. Forensic analysis would have been crucial to understand the attack vector and the ransomware variant used. Notification of relevant authorities, such as law enforcement and potentially credit reporting agencies depending on the nature of the compromised data, would have followed.
Data recovery efforts would have ranged from restoring backups (if available and untainted) to potentially negotiating with the attackers (a highly risky strategy with uncertain outcomes). Finally, Victoria’s Secret would have implemented enhanced security measures to prevent future attacks, including patching vulnerabilities, improving network segmentation, and bolstering employee security awareness training.
Victoria’s Secret’s Response
The retail giant likely prioritized data recovery and minimizing reputational damage. Given the sensitive nature of customer data potentially compromised, Victoria’s Secret would have faced intense pressure to manage the situation effectively and transparently, communicating promptly with affected customers and regulatory bodies. The recovery process likely involved a complex interplay of technical expertise, legal counsel, and public relations management.
The costs associated with such a response – including forensic investigations, data recovery, legal fees, and potential regulatory fines – would be substantial. The incident likely prompted a comprehensive review of their existing security posture, leading to significant investments in enhanced security infrastructure and employee training.
Taiwan Oil Refinery’s Recovery
The Taiwan oil refinery’s recovery process would have been significantly different, given the critical infrastructure nature of the operation. The primary focus would have been on restoring operational functionality as quickly as possible to minimize disruption to oil production and distribution. This likely involved a combination of restoring systems from backups, deploying temporary solutions, and potentially even manually operating certain aspects of the refinery until full system restoration was achieved.
Given the potential for physical damage or sabotage alongside the cyberattack, a thorough physical security assessment would also have been conducted. The refinery would have faced significant economic losses due to production downtime, and the incident would have likely spurred investment in more resilient and robust cybersecurity systems. Collaboration with government agencies and cybersecurity experts would have been crucial in the recovery effort.
The Nefilim ransomware attack on Victoria’s Secret and a Taiwanese oil refinery highlights the urgent need for robust cybersecurity. Building resilient systems requires efficient development, and that’s where exploring options like domino app dev, the low-code and pro-code future , becomes crucial. Faster development cycles could help organizations patch vulnerabilities quicker, potentially mitigating the impact of future ransomware attacks like the one targeting these high-profile targets.
Comparison of Cybersecurity Responses
While both Victoria’s Secret and the Taiwan oil refinery faced the disruptive impact of a ransomware attack, their responses differed significantly based on their industry, criticality, and the nature of the data at risk. Victoria’s Secret likely focused heavily on data recovery and reputational management, while the oil refinery prioritized operational restoration and minimizing the impact on energy supply. Both organizations, however, shared the common goal of containing the attack, investigating the incident, and implementing improved security measures to prevent future occurrences.
Importance of Proactive Cybersecurity Measures
The Nefilim ransomware attacks serve as a stark reminder of the importance of proactive cybersecurity measures. Reactive responses, while crucial in mitigating the immediate impact of an attack, are inherently more costly and less effective than a robust preventive strategy. Proactive measures, such as regular security assessments, vulnerability patching, employee training, and incident response planning, significantly reduce the likelihood and impact of ransomware attacks.
Investing in advanced security technologies, such as endpoint detection and response (EDR) and security information and event management (SIEM) systems, can also enhance an organization’s ability to detect and respond to threats effectively.
Ransomware Response Flowchart
The following describes a typical ransomware response flowchart. Imagine a visual representation, a flowchart with boxes and arrows connecting the stages. The first box would be “Incident Detection.” This is followed by “Containment,” isolating infected systems. Next, “Eradication” focuses on removing the malware. Then, “Recovery” involves restoring data from backups or other means.
“Investigation” analyzes the attack to identify vulnerabilities. Finally, “Post-Incident Activities” encompass improved security measures and lessons learned. This process highlights the importance of a well-defined and practiced incident response plan.
Attribution and Motivation
The Nefilim ransomware attacks against Victoria’s Secret and the Taiwanese oil refinery raise crucial questions about the perpetrators and their motives. While definitive attribution remains challenging in the absence of publicly available forensic evidence, analyzing the targets and attack methods allows us to speculate on potential actors and their motivations. The sophistication of the attacks suggests a well-resourced and experienced threat actor.The choice of targets – a major retailer and a critical infrastructure component – hints at a multifaceted strategy.
Victoria’s Secret, with its vast customer database and sensitive financial information, represents a lucrative target for data extortion. Simultaneously, attacking a Taiwanese oil refinery disrupts supply chains, potentially causing significant economic damage and impacting geopolitical stability. This suggests a group capable of both financially motivated and potentially state-sponsored or politically motivated attacks.
Potential Actors
Several actors could be responsible. State-sponsored groups, known for their advanced capabilities and willingness to engage in disruptive attacks, are a strong possibility. China, given the refinery attack, is a prime suspect, though this should be treated as speculation without concrete evidence. Alternatively, financially motivated ransomware-as-a-service (RaaS) groups could be behind the attacks, leveraging their affiliates to target high-value organizations for maximum profit.
These groups often operate with a degree of anonymity, making attribution difficult. Another possibility is a financially motivated group with a secondary agenda, such as causing disruption to a specific industry or region.
Motivations Behind Target Selection
Victoria’s Secret was likely targeted for financial gain. The potential for data extortion – demanding a ransom for the return of stolen customer data and intellectual property – is substantial. A successful attack could yield millions of dollars in ransom payments. The Taiwanese oil refinery, however, presents a more complex picture. The attack could have been purely financially motivated, aiming to disrupt operations and extract a significant ransom.
Alternatively, it could have been politically motivated, aiming to destabilize Taiwan’s economy or send a geopolitical message. The simultaneous attacks suggest a coordinated effort, perhaps to maximize the impact and the potential ransom yield.
Potential Links Between Attacks
The connection between the two attacks is currently unclear. They could be entirely coincidental attacks by separate groups. However, the similar use of Nefilim ransomware suggests a possible link. The attackers may have employed a common infrastructure or shared resources, suggesting a potential collaboration or a connection between the groups. A more sinister possibility is that the attacks are part of a larger, coordinated campaign targeting critical infrastructure and high-value businesses across different sectors.
Further investigation is needed to definitively establish a connection.
Likely Ransom Demands
The ransom demands would likely be substantial, reflecting the value of the stolen data and the potential impact of the disruption. For Victoria’s Secret, the ransom could be in the millions of dollars, considering the volume of sensitive customer data and the potential for reputational damage. The ransom for the oil refinery attack would likely be even higher, reflecting the significant economic disruption caused by the outage and the potential for long-term consequences.
The attackers might demand payment in untraceable cryptocurrencies to maintain anonymity. They would likely threaten to leak the stolen data or further disrupt operations if the ransom is not paid.
Hypothetical Attacker Profile
Based on the available information, the attackers likely possess a high level of technical expertise in ransomware deployment and data exfiltration. They are likely well-organized and capable of conducting coordinated attacks across different sectors. Their motivation appears to be a blend of financial gain and potentially geopolitical or ideological goals. The attackers likely operate from a location that allows them to evade law enforcement easily, possibly in a country with lax cybersecurity regulations or a history of supporting cybercrime.
Their use of Nefilim ransomware suggests a preference for well-established tools that are known to be effective in achieving their objectives. The group may consist of several individuals with specialized skills, working together to execute and maintain the attacks.
Illustrative Example: Data Exfiltration
Let’s imagine a plausible scenario of data exfiltration during the hypothetical Nefilim ransomware attack on Victoria’s Secret. The attackers, having gained initial access perhaps through a phishing email or exploited vulnerability, wouldn’t immediately encrypt everything. A sophisticated attack like this would likely involve a phased approach, prioritizing valuable data for exfiltration before the encryption phase to maximize their leverage.The attackers likely employed a multi-pronged approach to exfiltration.
This would include using several techniques to avoid detection and ensure data transfer success. They might have leveraged compromised internal credentials to access network shares and databases, then used a combination of techniques including covert channels, steganography (hiding data within other files), and encrypted communication tunnels to transfer the data. They would choose methods based on the size and sensitivity of the data being stolen.
Smaller, high-value data sets, like customer credit card information or sensitive marketing strategies, might be exfiltrated via encrypted email or through a command-and-control server using a custom protocol. Larger datasets, such as customer databases or product design documents, would likely be moved more slowly using more robust, but potentially slower, methods like a compromised FTP server or even a cloud storage service that they had previously compromised.
Data Exfiltration Methods
The attackers likely utilized a combination of techniques for data exfiltration. This would involve initial reconnaissance to identify valuable data stores, followed by careful selection of methods based on data size and sensitivity. For example, smaller, sensitive files such as customer credit card information might be exfiltrated piecemeal through an encrypted email account or using a compromised cloud storage service.
Larger datasets like customer databases could be transferred via a compromised FTP server, using techniques to fragment the data for increased stealth and to make detection more difficult. The attackers might also employ steganography, embedding the stolen data within seemingly innocuous image files to evade detection by standard security tools.
Types of Data Stolen
The stolen data would likely include a variety of sensitive information. This could encompass customer Personally Identifiable Information (PII), including names, addresses, phone numbers, email addresses, and credit card details. Financial information related to transactions, internal financial documents, and intellectual property relating to product designs, marketing strategies, and business plans would also be high-value targets. Furthermore, employee data, including payroll information and internal communications, could also be compromised.
Visual Representation of Data Exfiltration
Imagine a visual representation as a complex network map. At the center is Victoria’s Secret’s internal network, depicted as a brightly lit node. From this central node, numerous dark, thin lines radiate outwards, representing the various data exfiltration channels. Some lines are thick and slow, representing the transfer of large datasets via compromised FTP servers, perhaps to a remote server in a different country.
Other lines are thinner and faster, representing the rapid exfiltration of smaller, high-value data sets through encrypted email or cloud storage. The destination points of these lines are depicted as darker, shadowy nodes, representing the attacker’s command-and-control servers and data storage locations. The entire network is overlaid with a faint, flickering red glow, symbolizing the constant monitoring and countermeasures deployed by Victoria’s Secret’s security team, highlighting the ongoing struggle between attacker and defender.
The success of the exfiltration is represented by the steady flow of data along these lines, a constant trickle or even a torrent, depending on the chosen method.
Illustrative Example: Refinery Operational Disruption
The Nefilim ransomware attack on a Taiwanese oil refinery could have devastating consequences, far exceeding simple data theft. Imagine a scenario where the attackers successfully infiltrate the refinery’s control systems, crippling its ability to process crude oil and distribute refined products. This wouldn’t just be a matter of lost data; it would be a real-world catastrophe with wide-ranging economic and societal impacts.The immediate impact would be felt across multiple systems.
Critical infrastructure, including the refinery’s control systems (SCADA), process monitoring systems, and potentially even safety systems, could be compromised. This compromise could lead to a cascade of failures.
Specific Systems Affected and Consequences, Nefilim ransomware hits victoria secrets and taiwan oil refinery
The SCADA system, responsible for monitoring and controlling the various stages of oil refining – from crude oil intake to product distribution – would be a prime target. Successful ransomware deployment here could lead to the immediate shutdown of processing units, resulting in a halt to the production of gasoline, diesel, jet fuel, and other crucial petroleum products. Simultaneously, the process monitoring systems, which provide real-time data on the refinery’s operations, would be rendered useless, preventing operators from understanding the status of the equipment and making informed decisions.
A further concern would be the impact on safety systems. If these systems were compromised, the risk of explosions, fires, or toxic spills would dramatically increase, posing a severe threat to personnel and the surrounding environment. The resulting disruption to the supply chain would have far-reaching economic consequences. Fuel shortages would impact transportation, industries reliant on petroleum products, and ultimately, consumers.
Visual Representation of Disrupted Operations
Imagine the sprawling refinery complex, usually a hive of activity with towering distillation columns, intricate pipework gleaming under the sun, and the constant hum of machinery. Now, picture this scene frozen in time. Flames from the refinery stacks would be significantly reduced or extinguished altogether, indicating a halt in processing. The usual flurry of tanker trucks loading and unloading would cease, leaving a silent, almost eerie stillness.
Emergency lights would likely flash intermittently, signaling a state of alert. The normally bustling control room, a hub of monitoring and decision-making, would be a scene of controlled chaos, with technicians frantically trying to assess the damage and implement contingency plans. The normally clear, concise data displays on the monitoring screens would be replaced with error messages or blank screens, reflecting the ransomware’s impact.
The overall atmosphere would be one of tension and uncertainty, a stark contrast to the controlled, predictable environment of normal operations. The surrounding area might experience a noticeable drop in the characteristic refinery smell, further evidence of the disruption.
Final Thoughts
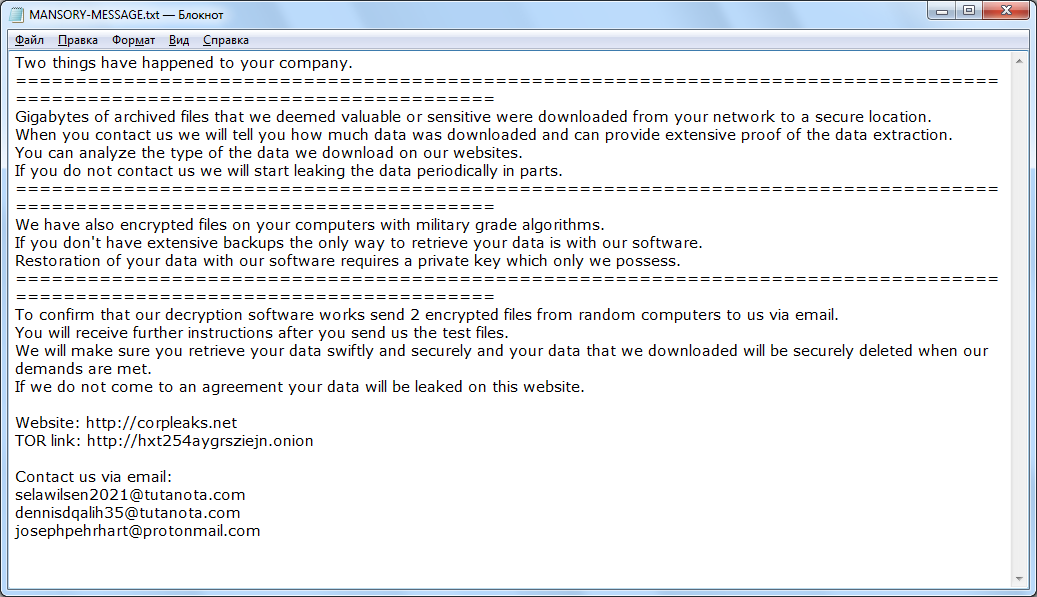
The Nefilim ransomware attacks on Victoria’s Secret and the Taiwan oil refinery serve as a stark reminder of the ever-evolving threat landscape in cyberspace. The scale and audacity of these attacks highlight the urgent need for robust cybersecurity measures across all sectors, from retail giants to critical infrastructure. While the immediate consequences are significant, the long-term implications for global security and economic stability remain to be seen.
One thing’s for sure: this isn’t the last we’ll hear about Nefilim, or the next big ransomware threat.
FAQ Section: Nefilim Ransomware Hits Victoria Secrets And Taiwan Oil Refinery
What type of data might have been stolen from Victoria’s Secret?
Potentially sensitive customer data including names, addresses, credit card information, and potentially even more personal details depending on the extent of the breach.
What are the potential geopolitical implications of the Taiwan refinery attack?
Disruption to Taiwan’s oil supply could impact its economy and potentially create regional instability, depending on the duration and severity of the outage.
How much ransom was demanded by the attackers?
The exact ransom demand isn’t publicly known, but ransomware demands can range from hundreds of thousands to millions of dollars depending on the target and the data compromised.
What makes Nefilim ransomware different from other ransomware families?
Further investigation is needed to fully understand Nefilim’s unique characteristics. Initial analysis would likely compare its encryption methods, attack vectors, and overall functionality to known ransomware strains to identify any unique features.