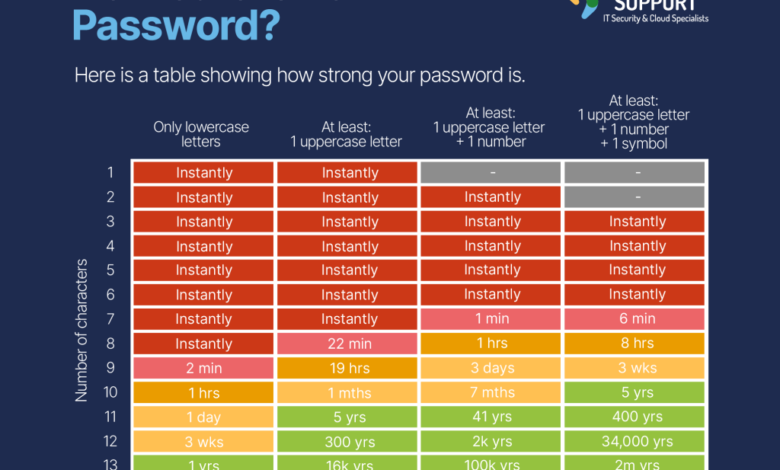
Why We Need to Make Passwords a Thing of the Past
Why we need to make passwords a thing of the past is a question that’s increasingly relevant in our hyper-connected world. We’re constantly bombarded with headlines about massive data breaches, highlighting the inherent weaknesses of password-based security. It’s exhausting trying to juggle countless complex passwords, and frankly, the whole system feels antiquated and insecure. This post dives into why passwords are failing us, explores better alternatives, and looks at a future where remembering a dozen different alphanumeric strings is a relic of the past.
From the frustration of forgotten passwords to the very real threat of identity theft, the current system is simply unsustainable. We’ll explore the vulnerabilities of passwords, the burden they place on users, and the exciting advancements in passwordless authentication that are finally offering a viable solution. Get ready to say goodbye to password fatigue and hello to a more secure and user-friendly digital experience.
The Inherent Weakness of Passwords

Passwords, the cornerstone of online security for decades, are fundamentally flawed. Their reliance on human memory and easily guessable combinations makes them vulnerable to a wide range of attacks, ultimately failing to provide the robust security we need in today’s digital landscape. This inherent weakness exposes individuals and organizations to significant risks, leading to data breaches, financial losses, and reputational damage.
Vulnerabilities of Password-Based Authentication
Password-based systems are susceptible to several attack vectors. Brute-force attacks involve systematically trying every possible password combination until a match is found. This is particularly effective against weak passwords or those using predictable patterns. Phishing attacks, on the other hand, trick users into revealing their credentials by disguising themselves as legitimate entities through deceptive emails or websites. Credential stuffing leverages stolen username and password combinations from one site and attempts to use them on other platforms, exploiting the common practice of users reusing passwords across multiple accounts.
These attacks, individually or in combination, pose a constant threat.
Examples of High-Profile Data Breaches
The consequences of password weaknesses are vividly illustrated by numerous high-profile data breaches. The 2017 Equifax breach, for example, exposed the personal information of nearly 150 million people due, in part, to the exploitation of a known vulnerability in their systems and weak password practices. Similarly, the Yahoo! data breaches in 2013 and 2014 resulted in the theft of billions of user accounts, highlighting the catastrophic impact of inadequate password security.
These incidents underscore the severe repercussions of relying on passwords as the primary defense against unauthorized access.
Statistics on Password-Related Security Incidents
The sheer volume of password-related security incidents highlights the urgency of finding alternatives. Reports from various cybersecurity firms consistently show millions of compromised accounts annually, with many breaches directly attributed to weak or stolen passwords. The financial and reputational costs associated with these incidents are staggering, impacting businesses and individuals alike. The frequency and impact of these events clearly demonstrate the inadequacy of passwords in securing sensitive information in the modern threat landscape.
Comparison of Password-Based Authentication with Alternatives
| Method | Strengths | Weaknesses | Security Level |
|---|---|---|---|
| Password-Based | Simple to implement, familiar to users | Vulnerable to brute-force, phishing, and credential stuffing; relies on user memory and security practices | Low |
| Multi-Factor Authentication (MFA) | Adds multiple layers of security, significantly reducing the risk of unauthorized access | Can be more complex to implement and use; may require additional hardware or software | Medium to High |
| Biometric Authentication | Highly secure, difficult to replicate or steal | Privacy concerns; potential for errors or malfunctions; requires specialized hardware | High |
| Passwordless Authentication | Eliminates the need for passwords entirely, removing a major vulnerability | Requires robust infrastructure and user education; potential for reliance on other vulnerable factors | Medium to High |
The User Experience Burden of Passwords
Let’s face it: managing passwords in the digital age is a monumental pain. The sheer number of accounts we need passwords for, coupled with the ever-increasing complexity requirements, creates a frustrating and often insecure experience for the average user. This burden impacts not only our daily lives but also poses significant security risks.The constant juggling act of creating, remembering, and securely storing countless passwords is a significant source of stress and inconvenience.
This frustration stems from the inherent limitations of passwords as a security mechanism, leading to compromises and security vulnerabilities. We’ll explore the various facets of this user experience burden below.
Password Management Challenges
The average internet user has dozens, if not hundreds, of online accounts, each requiring a unique and complex password. Remembering these passwords, especially when they must adhere to stringent length and character requirements (including uppercase letters, lowercase letters, numbers, and symbols), is a near-impossible task for most people. This leads to common practices like password reuse, writing passwords down (often in insecure locations), or relying solely on easily guessable passwords.
All these practices significantly increase vulnerability to hacking and data breaches.
Security Risks of Password Reuse and Password Managers
While password managers aim to alleviate the burden of remembering multiple passwords, they introduce their own set of security concerns. If a password manager is compromised, access to all the user’s accounts is potentially exposed. Similarly, password reuse, a common coping mechanism for the password burden, represents a significant security risk. If one account is compromised using a reused password, attackers can potentially gain access to multiple accounts.
Consider a scenario where a user reuses the same password for their email, banking, and social media accounts. A breach on any one platform could grant an attacker access to all three.
Impact of Password Complexity Requirements on User Productivity
The constant pressure to create ever-more complex passwords negatively impacts user productivity and satisfaction. The time spent creating, remembering, and managing these passwords could be used for more productive tasks. Furthermore, the frustration associated with resetting passwords, dealing with lockout mechanisms, and navigating complex password recovery processes detracts from the overall user experience. The trade-off between security and usability is often skewed heavily towards security, resulting in a frustrating experience for the end-user.
A User Scenario: The Password Predicament
Imagine Sarah, a busy professional with accounts on various platforms: email, banking, social media, online shopping, streaming services, and more. She’s diligently trying to follow best practices by using unique and complex passwords for each account. However, she struggles to keep track of them all. She resorts to writing down some passwords, which feels insecure, and uses password reuse for others, increasing her vulnerability to attacks.
She frequently spends time resetting passwords, gets locked out of accounts, and feels overwhelmed by the sheer number of passwords she needs to manage. This constant struggle diminishes her productivity and leaves her feeling stressed and frustrated. This scenario is far from unique; it’s a common experience for millions of internet users.
Exploring Passwordless Authentication Methods
So, passwords are out – but what’s in? The good news is that several robust and user-friendly alternatives are already available, promising a future where security and convenience go hand-in-hand. Let’s delve into some of the most promising passwordless authentication methods.
The shift away from passwords requires a multifaceted approach, leveraging various technologies to enhance security and streamline user experience. The following methods offer compelling alternatives, each with its strengths and weaknesses.
Biometric Authentication
Biometric authentication uses unique biological traits to verify identity. This could include fingerprint scanning, facial recognition, iris scanning, or even voice recognition. These methods offer a high degree of security, as they’re difficult to replicate or steal. For instance, fingerprint scanners are increasingly common on smartphones and laptops, providing a convenient and secure way to unlock devices. However, the accuracy and reliability of biometric systems can vary depending on the technology and environmental factors.
Concerns around privacy and data security also need to be addressed, ensuring that biometric data is stored and handled securely. Furthermore, some users may have reservations about the use of their biometric data for security purposes.
One-Time Passwords (OTPs)
OTPs are temporary passwords generated and delivered via SMS, email, or authenticator apps. These passwords are valid for a limited time, typically a few minutes, making them highly secure. Google Authenticator and Authy are popular examples of authenticator apps that generate time-based OTPs. The user experience is generally good, offering a simple and secure alternative to traditional passwords.
However, OTPs rely on a secondary device or service (phone, email, authenticator app), which could become a single point of failure if compromised. Also, reliance on mobile network connectivity for SMS-based OTPs can be a limitation in areas with poor network coverage.
Public Key Cryptography, Why we need to make passwords a thing of the past
Public key cryptography, also known as asymmetric cryptography, uses a pair of keys: a public key and a private key. The public key is shared openly, while the private key remains secret. This system allows for secure communication and authentication without the need for passwords. For example, the FIDO2 standard leverages public key cryptography to enable passwordless logins on websites and applications.
This method offers strong security and is resistant to many common password-related attacks. However, the technical complexity can make it challenging for some users to understand and implement. Furthermore, the management of cryptographic keys needs to be carefully considered to ensure security and prevent loss or compromise.
Here’s a summary comparing these methods:
- Biometrics:
- Strengths: High security, convenient user experience.
- Weaknesses: Accuracy can vary, privacy concerns, potential for spoofing.
- UX Improvement: Eliminates the need to remember and type passwords, offering a seamless login experience.
- One-Time Passwords (OTPs):
- Strengths: High security, relatively easy to implement.
- Weaknesses: Reliance on secondary device, vulnerable to SIM swapping or email compromise.
- UX Improvement: More secure than static passwords, reduces the risk of credential stuffing attacks.
- Public Key Cryptography:
- Strengths: Very strong security, resistant to many attacks.
- Weaknesses: Technically complex, requires careful key management.
- UX Improvement: Provides a secure and seamless login experience, often integrated directly into browsers or operating systems.
The Economic and Societal Impact of Password Dependence

The reliance on passwords as our primary security mechanism carries a significant, often underestimated, economic and societal burden. The costs extend far beyond the inconvenience of forgotten passwords; they encompass substantial financial losses for businesses and individuals, alongside a pervasive erosion of trust and security in our increasingly digital world. The sheer scale of the problem necessitates a critical examination of its impact and a proactive search for more robust alternatives.The economic consequences of password-related security breaches are staggering.
Data breaches resulting from compromised passwords lead to direct financial losses through theft of sensitive information, including credit card details, personal data, and intellectual property. Beyond the immediate costs, businesses face significant expenses related to incident response, legal fees, regulatory fines, and reputational damage. A 2021 IBM study estimated the average cost of a data breach to be $4.24 million.
This figure includes costs associated with detection and response, lost business, and regulatory penalties – many of which are directly attributable to weak or stolen passwords. Recovery efforts, including notifying affected users, credit monitoring services, and system upgrades, further inflate these costs.
Financial Losses from Password-Related Breaches
The Ponemon Institute’s research consistently reveals the high costs associated with data breaches, with a significant portion directly linked to compromised passwords. Their reports frequently highlight the escalating financial burden on organizations, emphasizing the need for more secure authentication methods. For example, a breach impacting a large retailer could lead to millions of dollars in losses due to stolen credit card information, customer refunds, and legal action.
Smaller businesses might face bankruptcy following a significant data breach, highlighting the vulnerability of organizations reliant on passwords for security. These financial losses ripple through the economy, impacting consumers, businesses, and the overall financial stability of industries.
Societal Impact of Password-Related Identity Theft and Fraud
Beyond the economic consequences, password-related security breaches have profound societal implications. Identity theft and fraud, facilitated by compromised passwords, lead to significant personal distress and financial hardship for individuals. Victims may face difficulties obtaining credit, securing employment, and restoring their good name. The emotional toll of such events is substantial, leading to anxiety, stress, and a loss of trust in online systems.
Furthermore, the widespread prevalence of password-related security breaches erodes public confidence in online services and institutions, potentially hindering the adoption of beneficial technologies and services. The increased scrutiny and regulations aimed at mitigating these risks also place an added burden on businesses and individuals.
Broader Implications of Password Dependence in an Interconnected World
Our increasing reliance on interconnected digital systems amplifies the risks associated with password-based security. The interconnected nature of our digital infrastructure means that a single breach can have cascading effects, compromising multiple systems and impacting a vast number of individuals and organizations. This vulnerability is further exacerbated by the growing prevalence of Internet of Things (IoT) devices, many of which lack robust security measures and rely on weak, easily guessable passwords.
The lack of a secure, universal authentication system creates a fragmented and vulnerable landscape, hindering the development of a truly secure and interconnected digital world.
Visual Representation of a Cascading Password Breach
Imagine a network diagram. At the center is a large circle representing a major company’s database, compromised due to a massive password breach. From this central circle radiate numerous smaller circles, representing various interconnected systems – banks, social media platforms, online retailers, and even individual user accounts. Lines connecting the circles illustrate the data flow and interdependencies. As the breach spreads, the smaller circles become increasingly shaded, indicating the expanding impact of the compromised data.
The diagram visually demonstrates how a single point of failure (a weak password system) can trigger a chain reaction, impacting numerous organizations and individuals across the entire network.
The Future of Authentication Beyond Passwords
The shift away from passwords is not merely a technological upgrade; it’s a fundamental reimagining of how we secure our digital lives. This transition requires a multi-pronged approach, encompassing technological innovation, user education, and regulatory frameworks to ensure a smooth and secure future for online authentication. The path forward necessitates a collaborative effort between developers, policymakers, and users themselves.
A Roadmap for Passwordless Transition
A successful transition to passwordless systems requires a phased approach. Initial stages will focus on integrating strong passwordless options into existing systems, alongside password-based authentication, allowing users to choose their preferred method. This parallel approach minimizes disruption and allows for gradual user adoption. Subsequent phases will involve the progressive phasing out of password-based logins, prioritizing passwordless methods across all platforms and services.
This will necessitate significant investment in infrastructure upgrades and widespread user education initiatives. Finally, the ultimate goal is a passwordless ecosystem where password-based logins become obsolete. This will require universal adoption of standardized and interoperable passwordless technologies.
Challenges and Obstacles to Widespread Adoption
Several obstacles hinder the widespread adoption of passwordless solutions. One key challenge is the diverse range of existing systems and legacy infrastructure. Migrating these systems to passwordless authentication can be expensive and time-consuming, requiring significant technical expertise and resources. Another hurdle is user education and acceptance. Many users are accustomed to passwords and may be hesitant to adopt new authentication methods, requiring clear and concise educational campaigns to build trust and understanding.
Furthermore, ensuring the security and privacy of passwordless systems is paramount. Robust security measures must be implemented to prevent vulnerabilities and protect user data. Finally, the interoperability of different passwordless systems needs to be addressed to create a seamless user experience across various platforms and services.
The Role of Legislation and Regulation
Legislation and regulation play a vital role in accelerating the shift away from passwords. Governments and regulatory bodies can incentivize the adoption of passwordless solutions through various measures. For example, regulations could mandate the use of passwordless authentication for certain high-security applications, such as government services or financial transactions. Furthermore, standards and guidelines can be established to ensure the interoperability and security of passwordless systems.
Legislation can also address liability issues and provide a clear legal framework for passwordless authentication. By creating a supportive regulatory environment, governments can foster innovation and accelerate the transition to a more secure and user-friendly digital landscape. The European Union’s General Data Protection Regulation (GDPR) serves as an example of legislation that indirectly encourages stronger authentication methods, though it doesn’t explicitly mandate passwordless solutions.
Timeline for the Evolution of Authentication Technology
Predicting a precise timeline is challenging, but a reasonable projection suggests significant progress within the next decade. Within the next 2-3 years, we can anticipate widespread adoption of passwordless options alongside traditional passwords in many major online services. In the next 5-7 years, passwordless authentication is likely to become the default or preferred method for many applications, particularly those involving sensitive data.
Within the next 10-15 years, we might see a significant decline in password-based systems, with passwordless authentication becoming the dominant method across most platforms. This timeline, however, is contingent upon successful technological advancements, widespread user acceptance, and supportive regulatory frameworks. The rapid advancements in biometric authentication, such as facial recognition and fingerprint scanning, combined with the increasing sophistication of phishing detection, are likely to significantly impact this trajectory.
The success of initiatives like FIDO2, a passwordless authentication standard, will also play a crucial role in shaping the timeline.
Seriously, remembering countless passwords is a nightmare! We need a better, more secure system, and I think the future lies in exploring innovative authentication methods. This is where advancements like those discussed in this article on domino app dev the low code and pro code future become crucial; building secure, passwordless apps is a key step towards a more streamlined and safer digital experience for everyone.
Let’s ditch the passwords and embrace a more secure tomorrow!
Final Review: Why We Need To Make Passwords A Thing Of The Past
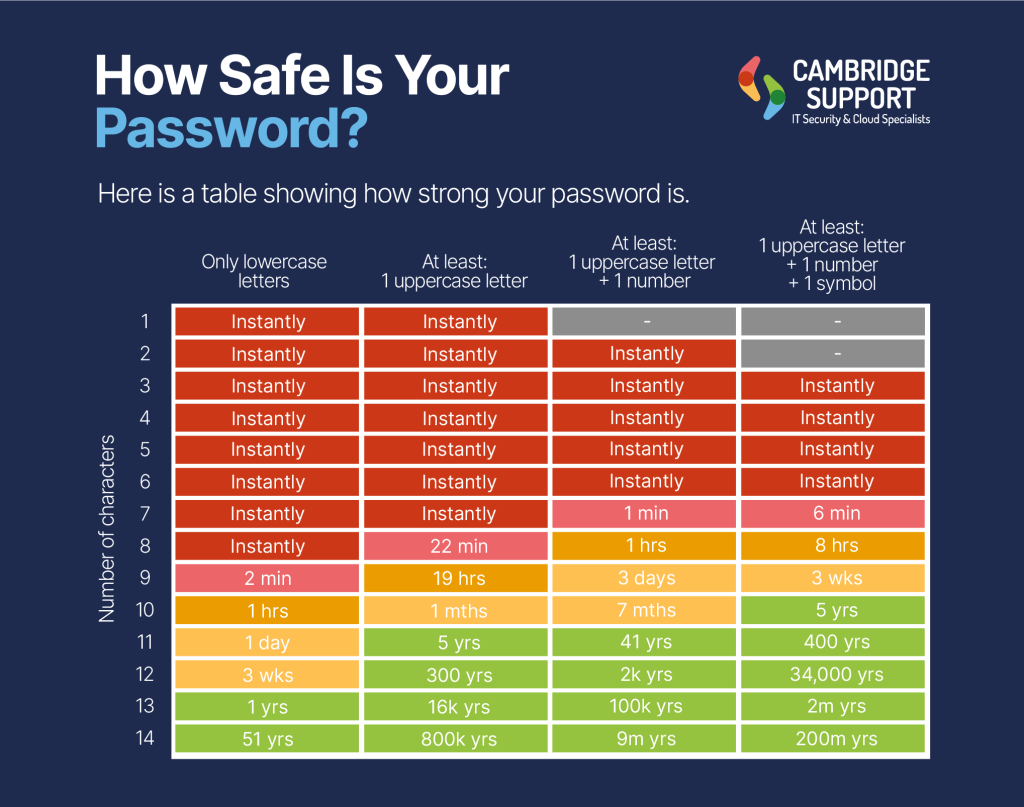
The move away from passwords isn’t just a technological upgrade; it’s a fundamental shift in how we approach online security. By embracing passwordless authentication methods, we can significantly reduce the risk of data breaches, improve user experience, and create a safer digital landscape for everyone. While challenges remain in widespread adoption, the benefits are undeniable, paving the way for a future where security is seamless and intuitive, not a constant source of stress and frustration.
Let’s ditch the passwords and embrace a more secure tomorrow!
Detailed FAQs
What are the biggest risks associated with password reuse?
Reusing passwords means that if one account is compromised, all your accounts are at risk. Hackers can use stolen credentials to access multiple services, leading to widespread identity theft and financial loss.
How secure are biometric authentication methods?
Biometric authentication, like fingerprint or facial recognition, offers strong security, but it’s not foolproof. Sophisticated attacks can still compromise biometric data, so a multi-layered approach is often best.
What is public key cryptography and how does it relate to passwordless logins?
Public key cryptography uses a pair of keys – a public key for encryption and a private key for decryption. Passwordless systems can use this to verify your identity without requiring a password.
Are password managers truly a safe solution?
Password managers can be helpful for managing many passwords, but they are not without risk. If the password manager itself is compromised, all your passwords are at risk. Choose a reputable manager with strong security features.





