Cyber Attack to Impact 1.5 Billion Apple Devices
Cyber attack to impact 1 5 billion apple devices – Cyber attack to impact 1.5 billion Apple devices? Whoa. That’s a headline that instantly grabs your attention, right? Imagine the chaos: millions of iPhones, iPads, and Macs potentially compromised, Apple services crippled, and personal data exposed on a massive scale. This isn’t a far-fetched sci-fi scenario; it’s a chilling possibility highlighting the vulnerabilities even the most secure tech giants face.
We’ll dive into the potential attack vectors, the devastating consequences, and what steps can be taken to mitigate this nightmare scenario.
This post explores the potential for a catastrophic cyberattack targeting Apple’s massive user base. We’ll examine how such an attack could unfold, focusing on potential entry points like software vulnerabilities, hardware flaws, and sophisticated social engineering techniques. We’ll also assess the impact on critical Apple services like iCloud, the App Store, and Apple Pay, and discuss the potential for widespread data breaches and their far-reaching economic consequences.
Finally, we’ll explore response strategies for both Apple and individual users, emphasizing the importance of proactive security measures and the long-term implications for trust in Apple’s security infrastructure.
Potential Vectors of a Widespread Apple Device Attack

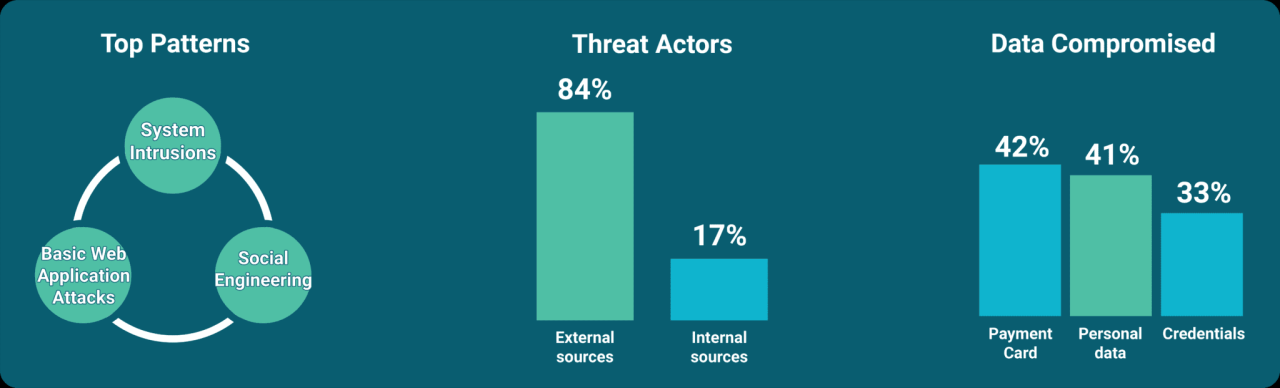
A hypothetical attack targeting 1.5 billion Apple devices would require a multifaceted approach, exploiting vulnerabilities across software, hardware, and user behavior. The sheer scale necessitates leveraging multiple attack vectors simultaneously to achieve significant impact. Understanding these vectors is crucial for developing effective mitigation strategies.
Likely Entry Points for a Widespread Attack
The following table Artikels potential attack vectors, their vulnerabilities, impact, and suggested mitigations. This is not an exhaustive list, but it highlights some of the most critical areas of concern.
| Vector Type | Vulnerability | Impact | Mitigation Strategy |
|---|---|---|---|
| Software Vulnerability | Zero-day exploit in iOS or macOS kernel | Complete system compromise, data theft, device control | Regular software updates, robust security auditing, vulnerability disclosure programs |
| Software Vulnerability | Vulnerability in a widely used third-party app | Data breach, malware installation, user tracking | Careful app selection from trusted sources, app sandboxing, regular app updates |
| Hardware Flaw | Compromised hardware component (e.g., in a specific chip model) | Data theft, persistent backdoor access | Hardware security modules, rigorous supply chain security, firmware updates |
| Social Engineering | Phishing emails, malicious websites, SMS scams | Credential theft, malware installation | User education, multi-factor authentication, robust spam filters |
| Social Engineering | Fake Apple support calls | Remote access to devices, data theft | User awareness campaigns, verification of support contacts |
Supply Chain Compromises
A compromised component within the Apple supply chain, even a seemingly insignificant one, could have devastating consequences on a scale of 1.5 billion devices. Imagine a malicious actor gaining access to the manufacturing process of a crucial chip, embedding a backdoor into every device using that chip. The resulting impact could be catastrophic, leading to widespread data theft, device control, and significant financial losses for Apple and its users.
This is analogous to the SolarWinds attack, where malicious code was inserted into the software update process of a widely used IT management tool.
The news about a potential cyberattack impacting 1.5 billion Apple devices is seriously unsettling. Thinking about the scale of such a breach got me pondering the future of app development and how secure platforms need to be, which is why I’ve been reading up on domino app dev, the low-code and pro-code future , to see how these advancements might help mitigate future risks.
Hopefully, robust development practices like those explored in the article can help prevent similar catastrophes from happening again. This whole situation highlights the urgent need for improved security across the board.
Comparison of Attack Effectiveness
Phishing attacks, while relatively simple to execute, rely on user error. Their effectiveness is limited by user awareness and security practices. Malware disguised as legitimate apps can bypass some security measures, but detection mechanisms are constantly improving. Zero-day exploits are the most dangerous, as they target previously unknown vulnerabilities. Their impact is potentially far-reaching and devastating due to the lack of immediate defenses.
A successful large-scale attack would likely combine multiple strategies; for instance, a zero-day exploit could be delivered through a phishing email, exploiting the vulnerability to install persistent malware. This layered approach maximizes the chances of success and complicates the response.
Impact Assessment
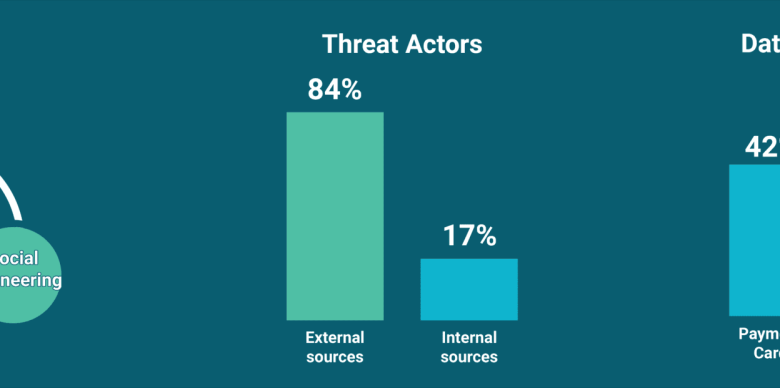
A successful cyberattack impacting 1.5 billion Apple devices would have catastrophic consequences, rippling across numerous systems and services, and causing significant economic and social disruption. The sheer scale of such an attack necessitates a detailed assessment of its potential impact, considering both the immediate effects and long-term repercussions. This analysis will focus on the critical services affected, the potential for data breaches, and the resulting economic costs.
Critical Apple Services Affected
The interconnected nature of Apple’s ecosystem means that a widespread attack could cripple multiple services simultaneously. The following list details the most vulnerable services and their potential consequences.
- iCloud: A successful attack could lead to the exposure of billions of users’ personal data, including photos, emails, documents, and backups. This would represent a massive privacy violation and could expose users to identity theft and financial fraud. Recovery would be extremely complex and time-consuming.
- App Store: Disruption to the App Store would prevent users from downloading updates and new applications, potentially leaving devices vulnerable to further attacks or rendering existing apps unusable. This would also severely impact app developers, leading to revenue loss and disruption to their businesses.
- Apple Pay: A compromise of Apple Pay could result in widespread financial fraud, with attackers potentially gaining access to users’ credit card and banking information. The resulting financial losses for both users and financial institutions would be substantial.
- iMessage and FaceTime: Disruption or compromise of these communication services would severely impact users’ ability to communicate, potentially hindering emergency response and causing significant social disruption.
- Apple Music and other Streaming Services: Disruption to these services would impact users’ entertainment and could result in revenue loss for Apple and content providers.
Potential Data Breaches and Sensitive User Data
The potential for data breaches in a large-scale attack is extremely high. The sensitive nature of the data stored on Apple devices and within Apple’s services makes this a particularly serious concern. The following table categorizes the types of sensitive data at risk and their relative sensitivity.
| Data Category | Examples | Sensitivity Level |
|---|---|---|
| Financial | Credit card details, banking information, Apple Pay transaction history | High |
| Personal | Names, addresses, phone numbers, email addresses, contact lists | Medium |
| Health | Medical records, fitness data, health app information (if applicable) | High |
| Location | GPS data, location history | Medium |
| Communications | iMessages, emails, FaceTime calls | Medium to High (depending on content) |
Economic Consequences, Cyber attack to impact 1 5 billion apple devices
The economic impact of such an attack would be far-reaching, affecting Apple, its users, and the global economy.
| Affected Party | Type of Impact | Estimated Cost (Illustrative Example) |
|---|---|---|
| Apple | Loss of revenue, legal costs, damage to reputation, cost of remediation | Billions of USD (comparable to the cost of major data breaches like Equifax) |
| Users | Financial losses due to fraud, identity theft, loss of productivity, emotional distress | Millions to billions of USD (depending on the scale of fraud and identity theft) |
| Wider Economy | Disruption to businesses reliant on Apple services, loss of consumer confidence, impact on financial markets | Potentially trillions of USD (considering the global reach of Apple’s ecosystem) |
Response and Mitigation Strategies
A widespread cyberattack affecting 1.5 billion Apple devices would be catastrophic, requiring a multi-pronged, rapid response. The scale of such an attack necessitates a meticulously planned incident response plan, proactive user education, and a robust patching strategy. This section Artikels strategies for effective response and mitigation, focusing on Apple’s role and the actions individual users can take.
Apple’s Incident Response Plan
A successful response hinges on a well-defined incident response plan. The plan must be activated immediately upon detection of the attack and must cover all stages, from initial detection to post-incident analysis. This plan needs to be regularly tested and updated to reflect evolving threat landscapes.
- Detection: Implement advanced threat detection systems across Apple’s infrastructure, including intrusion detection systems (IDS), security information and event management (SIEM) tools, and threat intelligence platforms. This includes monitoring for unusual network activity, suspicious login attempts, and anomalous device behavior.
- Containment: Isolate affected devices and networks to prevent further spread of the malware. This may involve temporarily disabling certain services or features. Prioritize critical systems and data, implementing network segmentation to limit the impact.
- Eradication: Develop and deploy a comprehensive malware removal tool, potentially utilizing a combination of signature-based and heuristic detection methods. This tool needs to be thoroughly tested before widespread deployment to avoid causing further damage.
- Recovery: Restore affected systems and data from backups, prioritizing critical services and data. Implement robust data recovery procedures, ensuring data integrity and availability. This phase will likely require significant resources and coordination.
- Post-Incident Activity: Conduct a thorough post-mortem analysis to identify the root cause of the attack, vulnerabilities exploited, and weaknesses in existing security measures. Implement corrective actions to prevent future incidents, including software updates, security enhancements, and employee training.
Individual User Preventative Measures
While Apple will play a crucial role in mitigating the attack, individual users can significantly reduce their risk through proactive security measures. These actions, while seemingly small, collectively contribute to a stronger defense against widespread attacks.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain passwords.
- Keep Software Updated: Regularly install the latest operating system updates and security patches. These updates often contain crucial security fixes that address known vulnerabilities.
- Use Strong Passwords: Employ strong, unique passwords for all Apple accounts and services, using a password manager to help manage them securely.
- Be Wary of Phishing Attempts: Exercise caution when clicking links or opening attachments from unknown sources. Phishing emails are a common vector for malware distribution.
- Install Reputable Security Software: Consider using reputable antivirus and anti-malware software to provide an additional layer of protection against threats.
- Regularly Back Up Data: Regularly back up important data to a secure location, such as an external hard drive or cloud storage service. This allows for quick recovery in case of data loss.
Patching Vulnerability Across a Massive Number of Devices
Patching 1.5 billion devices presents a significant logistical challenge. Apple will need to employ a multi-faceted approach combining software updates, remote management tools, and user cooperation. The success of this effort will depend on efficient deployment mechanisms and effective user communication.
- Software Updates: Apple’s existing software update mechanism is a primary tool. However, optimizing delivery to handle this scale requires careful planning, potentially prioritizing updates based on device type and criticality.
- Remote Management Tools: Apple’s MDM (Mobile Device Management) solutions can be leveraged to remotely deploy patches to managed devices. This is particularly effective for corporate or institutional deployments.
- User Cooperation: Effective communication with users is paramount. Clear, concise instructions and incentives for prompt updates are essential to maximize user participation in the patching process. Apple’s reputation and user trust will heavily influence this cooperation.
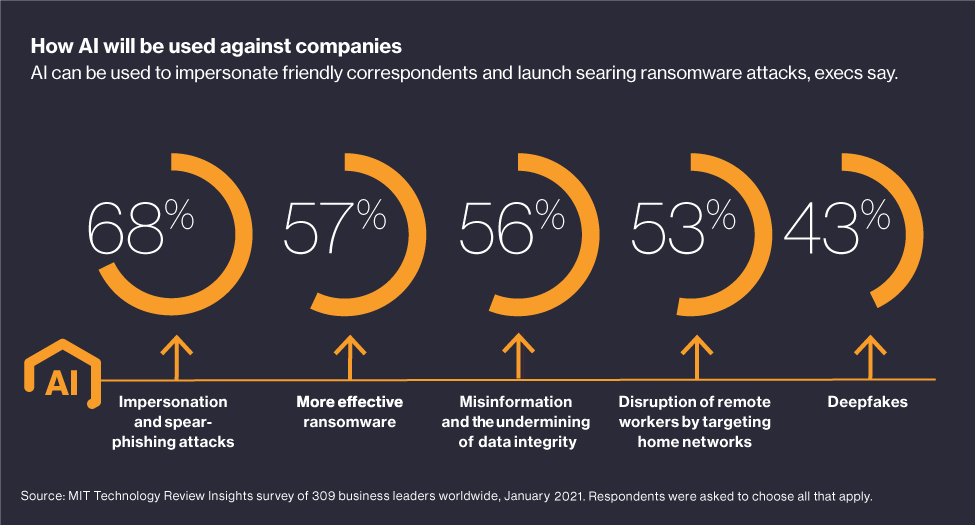
Long-Term Security Implications: Cyber Attack To Impact 1 5 Billion Apple Devices
A hypothetical cyberattack impacting 1.5 billion Apple devices would have profound and long-lasting consequences, extending far beyond the immediate disruption and data breaches. The ripple effects on user trust, Apple’s brand reputation, and the broader tech landscape would be significant and require substantial effort to mitigate. This event would serve as a stark reminder of the ever-evolving nature of cybersecurity threats and the need for continuous vigilance.The scale of such an attack would severely erode user confidence in Apple’s vaunted security infrastructure.
Many users choose Apple products precisely because of their reputation for robust security. A massive breach would shatter this perception, potentially driving users towards competing platforms, even if those platforms have their own vulnerabilities. The resulting loss of market share could be substantial, forcing Apple to invest heavily in regaining user trust through enhanced security measures and transparent communication.
The financial impact, including legal repercussions and compensation for affected users, could also be staggering.
Impact on User Behavior and Apple’s Brand Reputation
The immediate impact would be a widespread panic among Apple users. Many would likely change their passwords, delete sensitive data, or even switch to alternative devices and operating systems. The long-term impact could be a shift in user behavior, with increased skepticism towards Apple’s security claims and a greater emphasis on personal security practices like two-factor authentication and robust password management.
Apple’s brand reputation, built on a foundation of security and privacy, would suffer significant damage, requiring a sustained and comprehensive public relations campaign to repair. This could involve significant investments in security research and development, improved communication with users, and potentially even legal settlements to address the fallout. The impact could be comparable to the Equifax data breach, which significantly damaged consumer trust and resulted in ongoing legal and financial repercussions.
Potential Future Attacks Targeting Apple’s Ecosystem
This hypothetical attack would provide valuable intelligence to malicious actors, highlighting potential vulnerabilities in Apple’s ecosystem. The lessons learned from this scenario would undoubtedly inform future attacks, potentially leading to more sophisticated and targeted campaigns.This event would underscore the importance of proactively identifying and addressing potential vulnerabilities.
- Exploitation of zero-day vulnerabilities in iOS and macOS.
- Phishing attacks targeting Apple ID credentials and iCloud accounts.
- Supply chain attacks compromising the manufacturing or distribution process of Apple devices.
- Malware targeting specific Apple services, such as iMessage or FaceTime.
- Exploitation of vulnerabilities in third-party apps available on the App Store.
Influence on Future Security Practices
This hypothetical attack would necessitate a significant reevaluation of security practices within Apple and across the broader technology industry. The following table Artikels potential areas for improvement, proposed solutions, and their expected outcomes.
| Area of Improvement | Proposed Solution | Expected Outcome |
|---|---|---|
| Zero-day vulnerability management | Increased investment in bug bounty programs and enhanced vulnerability detection systems. | Reduced incidence of zero-day exploits and improved overall system security. |
| Enhanced user authentication | Implementation of stronger authentication methods, such as biometric authentication and hardware security keys. | Increased resistance to phishing attacks and unauthorized access to user accounts. |
| Improved supply chain security | Stricter vetting processes for suppliers and enhanced security measures throughout the manufacturing and distribution process. | Reduced risk of compromised devices and supply chain attacks. |
| Strengthened app store security | More rigorous app review process and improved detection of malicious apps. | Reduced number of malicious apps available on the App Store and enhanced user protection. |
| Increased transparency and communication | Proactive communication with users about security incidents and improved transparency regarding security practices. | Increased user trust and improved response to future security incidents. |
End of Discussion
The potential for a cyberattack impacting 1.5 billion Apple devices is a stark reminder of the ever-evolving threat landscape. While the sheer scale of such an attack is daunting, understanding the potential vectors, impact, and mitigation strategies is crucial. Both Apple and its users need to remain vigilant, proactively adopting robust security practices and staying informed about emerging threats.
The future of digital security depends on collective action and a continuous commitment to improving our defenses against increasingly sophisticated cyberattacks. Let’s hope this hypothetical scenario remains just that – a hypothetical.
FAQ Overview
What types of data are most at risk in a large-scale Apple attack?
Financial information (credit card details, Apple Pay data), personal data (contacts, photos, location history), health data (from Apple Health), and potentially even sensitive business data stored on devices are all at risk.
Could a hardware flaw be the root cause of such a widespread attack?
Absolutely. A vulnerability in Apple’s hardware, especially one present across multiple device models, could provide a backdoor for attackers to compromise a vast number of devices simultaneously.
What is Apple’s responsibility in preventing such a massive attack?
Apple has a responsibility to implement robust security measures throughout its supply chain, in its software and hardware, and to provide users with clear and effective security advice and tools. Regular security updates and proactive vulnerability patching are key.