
Addressing the Human Element of Security Awareness Training
Addressing the human element of security awareness training programs – Addressing the human element of security awareness training programs is crucial for building a truly secure organization. It’s not enough to just tick boxes and deliver rote lectures; we need to understand
-why* people make security mistakes and tailor our training to overcome those hurdles. This isn’t about blame; it’s about recognizing the psychology behind our actions and building programs that actually stick.
We’ll delve into the psychological biases that trip us up, explore how to ditch fear-mongering for genuine engagement, and discover how to personalize training to resonate with diverse teams. We’ll cover practical strategies for boosting knowledge retention, measuring success, and ultimately, fostering a culture where security is everyone’s responsibility, not just the IT department’s.
Understanding the Psychology of Security Awareness

Security awareness training isn’t just about ticking boxes; it’s about changing behavior. To be truly effective, it needs to address the human element – our cognitive biases, motivations, and emotional responses. Understanding the psychology behind our actions is crucial to designing training that truly sticks.
Common Psychological Biases Hindering Security Practices
Several cognitive biases frequently undermine even the best-intentioned security efforts. Confirmation bias, for example, leads us to favor information confirming our pre-existing beliefs, even if that information is inaccurate or incomplete. This can manifest as ignoring security warnings that contradict our usual workflow. Similarly, the availability heuristic makes us overestimate the likelihood of events that are easily recalled, often leading to excessive worry about less probable threats while neglecting more common ones.
Another significant bias is normalcy bias, where we believe things will continue as they always have, leading us to underestimate the risk of a security breach. Finally, the anchoring bias can cause us to rely too heavily on the first piece of information we receive, even if it’s irrelevant or outdated, when making security decisions.
The Counterproductivity of Fear-Based Approaches in Security Training
While fear can be a motivator, fear-based security training often backfires. Instead of fostering careful consideration of security protocols, it can trigger a fight-or-flight response, leading to employees shutting down or ignoring the training altogether. Excessive fear can also lead to anxiety and stress, reducing productivity and potentially creating a hostile work environment. A more effective approach focuses on building confidence and empowering employees to make informed security decisions.
Fostering Intrinsic Motivation in Employees Regarding Security
Intrinsic motivation, driven by internal factors rather than external rewards or punishments, is key to long-term security behavior change. This can be achieved by framing security as a collaborative effort to protect the company and its data, emphasizing the value of their contributions. Clearly demonstrating how security measures directly benefit employees, such as protecting their personal information or ensuring business continuity, is crucial.
Providing employees with a sense of ownership and control over their security practices, allowing them to participate in the development and improvement of security protocols, can also significantly boost motivation.
A Training Module Leveraging Positive Reinforcement Techniques, Addressing the human element of security awareness training programs
This module uses gamification and positive reinforcement to encourage secure practices. Employees complete short, interactive modules focusing on specific security threats and best practices. Upon successful completion of each module, they earn points, badges, and leaderboard rankings. Regular feedback and recognition for demonstrating secure behaviors further reinforce positive actions. The module also includes scenario-based training where employees can practice identifying and responding to phishing attempts and other common threats in a safe environment.
The focus remains on building confidence and competence, not on instilling fear.
Illustrative Scenario: Cognitive Biases Leading to Security Breaches
Imagine Sarah, a marketing manager, receives an email seemingly from her CEO, requesting urgent access to sensitive client data. Due to anchoring bias, she focuses on the email’s apparent origin – the CEO’s email address – rather than scrutinizing the message’s content or tone. Confirmation bias leads her to ignore subtle inconsistencies because she wants to believe it’s legitimate, and normalcy bias makes her assume such requests are routine.
Ignoring the security protocols, she grants access, resulting in a significant data breach. This scenario highlights how cognitive biases, even in experienced professionals, can easily lead to security vulnerabilities.
Tailoring Training to Different Employee Personalities and Roles
Effective security awareness training isn’t a one-size-fits-all approach. Ignoring the diverse learning styles and responsibilities of your workforce can lead to low engagement and ultimately, a weaker security posture. A truly successful program recognizes and caters to these individual differences, ensuring everyone receives the information they need in a way they can understand and retain.Understanding that employees learn in different ways is crucial.
Visual learners respond well to diagrams, videos, and infographics; auditory learners prefer podcasts, discussions, and presentations; while kinesthetic learners benefit from hands-on activities and simulations. Failing to consider these preferences means a significant portion of your workforce may not be absorbing the key security messages.
Learning Styles and Training Method Adaptation
To effectively address diverse learning styles, a multi-modal approach is necessary. For example, a module on phishing awareness could include a short animated video demonstrating common phishing tactics (visual), a narrated audio walkthrough of a realistic phishing email (auditory), and a hands-on exercise where employees identify and report simulated phishing attempts (kinesthetic). This layered approach ensures that regardless of an employee’s preferred learning style, they are exposed to the crucial information in a way that resonates with them.
Supplementing these methods with interactive quizzes and knowledge checks helps reinforce learning and identifies areas needing further attention.
Security Awareness Needs Across Departments
Different departments within an organization have varying security needs and vulnerabilities. The IT department, for instance, requires in-depth training on technical threats and security protocols, whereas the marketing department might need more focus on social engineering and data privacy. A finance department needs robust training on financial fraud prevention and compliance regulations. Tailoring training to these specific departmental needs ensures relevance and maximizes impact.
For example, a training module for the IT department could cover advanced persistent threats (APTs) and penetration testing methodologies, while a module for the marketing department could focus on protecting brand reputation and avoiding data breaches through social media.
Personalizing Training Content
Personalization goes beyond simply adjusting the format. It involves making the content relatable and relevant to individual employees. This can be achieved through scenario-based training that mirrors real-world situations employees might encounter. For instance, a scenario could involve a sales representative receiving a suspicious email from a supposed client requesting sensitive financial information. This makes the training more engaging and memorable.
Further personalization can be achieved by incorporating employee names or department-specific examples into training materials. Using familiar company examples of security incidents (without revealing sensitive information) can also increase engagement and highlight the real-world consequences of security lapses.
Training Materials for Various Technical Expertise Levels
The level of technical detail in training materials should align with the employee’s role and technical expertise. For non-technical staff, training should focus on clear, concise explanations of key concepts and avoid jargon. Visual aids and simple examples are crucial. Conversely, technical staff can benefit from more in-depth training that covers technical details, security protocols, and troubleshooting procedures.
For instance, a training module on password security for non-technical staff might emphasize the importance of strong passwords and password managers, while a similar module for IT staff could delve into password hashing algorithms and multi-factor authentication protocols.
Sample Training Schedule for Diverse Work Schedules
A flexible training schedule is essential to accommodate the varying work schedules of employees. Offering training modules in various formats—short videos, online courses, or in-person workshops—allows employees to access training at their convenience. Consider offering training sessions at different times of the day or week to cater to different shifts and work patterns. Microlearning modules, which deliver short bursts of information, are particularly effective for busy employees who may not have large blocks of time available for training.
A blended learning approach, combining online modules with occasional in-person workshops, can provide a comprehensive and flexible learning experience. This could involve scheduling online modules accessible 24/7, supplemented by monthly in-person sessions for Q&A and hands-on activities.
Improving Engagement and Knowledge Retention
Making security awareness training stick isn’t just about delivering information; it’s about creating a lasting impact. Employees need to understand and remember the crucial security practices to effectively protect themselves and the organization. This requires moving beyond passive lectures and embracing interactive, engaging methods that cater to different learning styles.
Effective security awareness training needs to be more than just another mandatory course. It should be an experience that resonates with employees, leaving them with practical knowledge and a genuine commitment to security best practices. This section will explore several techniques for improving engagement and knowledge retention.
Interactive Training Techniques
To combat passive learning, incorporate interactive elements. Instead of lengthy presentations, consider using short, focused modules with quizzes, interactive scenarios, and hands-on exercises. These active learning methods encourage participation and reinforce learning. For example, a simulated phishing email exercise where employees identify suspicious elements will be far more effective than a simple lecture on phishing.
- Interactive Scenarios: Present realistic scenarios where employees make decisions about security incidents, receiving immediate feedback on their choices.
- Short Quizzes and Polls: Regularly assess understanding with short quizzes and polls throughout the training, providing immediate feedback and highlighting areas needing further attention.
- Hands-on Activities: Include activities like configuring multi-factor authentication on their personal devices or practicing password management techniques.
Gamification and Storytelling in Security Awareness
Gamification and storytelling can significantly boost engagement. These techniques tap into intrinsic motivation, making learning more enjoyable and memorable. Think of points, badges, leaderboards, and challenges to motivate participation. Storytelling helps to make abstract concepts relatable and memorable.
Effective security awareness training needs to go beyond dry facts; it’s about fostering a security-conscious culture. To achieve this, we need intuitive tools that empower users, and that’s where the advancements in domino app dev the low code and pro code future come into play. These platforms can help create engaging, user-friendly security apps that reinforce training and make security protocols easier to understand and follow, ultimately boosting the effectiveness of our human element focus.
- Points and Badges: Award points for completing modules, quizzes, and challenges. Badges can be earned for achieving certain milestones or demonstrating proficiency.
- Leaderboards: Introduce friendly competition through leaderboards, motivating employees to improve their security knowledge and scores.
- Storytelling: Use real-world examples and case studies to create engaging narratives that illustrate the consequences of security breaches and the importance of best practices.
Real-World Examples and Case Studies
Abstract concepts often fail to resonate with learners. Incorporating real-world examples and case studies makes the training relevant and impactful. Discuss recent data breaches, illustrating how they occurred and the devastating consequences. Showcase successful security initiatives and best practices from other organizations.
- Data Breach Case Studies: Analyze well-known data breaches, highlighting the vulnerabilities exploited and the resulting impact on individuals and organizations (e.g., Equifax breach, Yahoo data breach).
- Success Stories: Share examples of organizations that have successfully implemented security awareness programs and achieved significant improvements in their security posture.
- Industry Best Practices: Highlight best practices from security frameworks like NIST Cybersecurity Framework or ISO 27001.
Post-Training Knowledge Retention Quiz
A short quiz after the training helps assess immediate knowledge retention. This allows for immediate feedback and identification of areas requiring further reinforcement.
| Question | Correct Answer | User Answer | Result |
|---|---|---|---|
| What is phishing? | A deceptive attempt to obtain sensitive information such as usernames, passwords, and credit card details | [User’s Answer] | [Correct/Incorrect] |
| What is a strong password? | A password that is long, complex, and unique | [User’s Answer] | [Correct/Incorrect] |
| What is multi-factor authentication (MFA)? | A security measure requiring multiple methods of authentication to verify a user’s identity | [User’s Answer] | [Correct/Incorrect] |
| What should you do if you receive a suspicious email? | Do not click any links or open any attachments. Report it to your IT department. | [User’s Answer] | [Correct/Incorrect] |
Mitigating the Forgetting Curve
The forgetting curve illustrates how quickly we forget information if not reinforced. To mitigate this, incorporate spaced repetition and regular refreshers. The visual representation would be a graph showing a steep decline in retention immediately after learning, followed by a gradual decrease over time. Strategies to flatten the curve include regular quizzes, refresher training, and on-the-job reinforcement.
Imagine a graph with “Retention Percentage” on the Y-axis and “Time Since Training” on the X-axis. The curve starts high immediately after training, then rapidly drops in the first few days, before leveling off at a much lower percentage over weeks and months. Strategies to mitigate this are depicted as lines or arrows intersecting the curve, indicating how regular reinforcement (e.g., short quizzes, refresher modules, reminders) increases knowledge retention over time, preventing the steep drop and keeping retention closer to the initial level.
Measuring the Effectiveness of Security Awareness Training Programs
Measuring the success of a security awareness training program isn’t just about ticking boxes; it’s about demonstrably improving your organization’s security posture. Effective measurement provides crucial feedback, allowing you to refine your training and justify its ongoing investment. Without concrete data, you risk running programs that are ineffective or even counterproductive.
Key Metrics for Evaluating Training Success
Choosing the right metrics is critical for accurately assessing the impact of your security awareness training. These metrics should directly reflect the program’s objectives and align with your overall security goals. Focusing on a range of metrics provides a more holistic understanding of the training’s effectiveness.
- Pre- and Post-Training Assessments: Measuring knowledge gained through pre- and post-training assessments helps quantify the improvement in employee understanding of security concepts. A significant increase in scores demonstrates effective knowledge transfer.
- Phishing Simulation Results: Tracking the success rate of phishing simulations, both before and after training, is a powerful indicator of behavioral change. A decrease in the number of employees clicking on malicious links shows improved vigilance.
- Security Incident Reduction: The ultimate measure of success is a reduction in security incidents attributable to human error. This could include fewer instances of password breaches, malware infections, or social engineering attacks.
- Employee Feedback Scores: Gathering feedback on training satisfaction, clarity, and relevance helps identify areas for improvement and ensures the training resonates with employees.
- Training Completion Rates: Monitoring the percentage of employees who complete the training indicates engagement levels and identifies potential barriers to participation.
Tracking Employee Behavior Changes Post-Training
Simply measuring knowledge gained isn’t enough; you need to see if that knowledge translates into changed behavior. This requires ongoing monitoring and analysis beyond the initial training period.
Continuous monitoring can involve several strategies. For example, regularly scheduled phishing simulations provide ongoing assessments of employee vigilance. Analyzing security logs for suspicious activity can reveal patterns of behavior indicative of vulnerabilities. Furthermore, regular quizzes or short knowledge checks can reinforce learning and identify areas where refresher training might be needed. Tracking these metrics over time provides valuable insights into the long-term effectiveness of the program and helps pinpoint areas needing improvement.
Assessing the Impact of Training on Reducing Security Incidents
The most compelling evidence of successful security awareness training is a demonstrable reduction in security incidents caused by human error. This requires careful analysis of security incident reports, correlating them with training completion data.
For instance, if a company implemented a new security awareness training program focusing on phishing attacks and subsequently experienced a significant drop in phishing-related incidents, this provides strong evidence of the training’s effectiveness. Analyzing the types of incidents reduced and the specific training modules related to those incidents can help refine future training efforts and highlight areas where further education is needed.
This requires a robust incident response system capable of accurately categorizing and analyzing security events.
Examples of Effective Training Outcome Reports
Effective reports should be concise, visually appealing, and focus on key findings. They should avoid overwhelming the reader with unnecessary detail.
A successful report will include:
- Executive Summary: A brief overview of the training program and its key results.
- Key Metrics and Results: Clear presentation of data illustrating the program’s impact on key metrics (e.g., phishing simulation success rates, security incident reduction).
- Visualizations: Charts and graphs to effectively communicate complex data in an easily digestible format.
- Recommendations: Suggestions for improvements based on the findings, including areas for future training focus.
- Appendix (Optional): Detailed data tables and supporting documentation.
Methods for Collecting Employee Feedback
Gathering employee feedback is essential for continuous improvement. Multiple methods can be employed to capture a wide range of perspectives.
Several methods can be used to gather feedback, each with its own advantages and disadvantages. These include:
- Post-Training Surveys: These provide quantitative and qualitative data on employee satisfaction, understanding, and suggestions for improvement. Online survey tools offer easy distribution and analysis.
- Focus Groups: These allow for in-depth discussions and exploration of specific issues. Focus groups provide rich qualitative data, but can be more time-consuming to conduct and analyze.
- Individual Interviews: These offer a more personalized approach and can uncover nuanced perspectives. However, individual interviews are more time-intensive than surveys or focus groups.
- Informal Feedback Mechanisms: Establishing channels for employees to provide informal feedback, such as suggestion boxes or online forums, can encourage ongoing communication and identify emerging issues.
Building a Culture of Security Awareness: Addressing The Human Element Of Security Awareness Training Programs
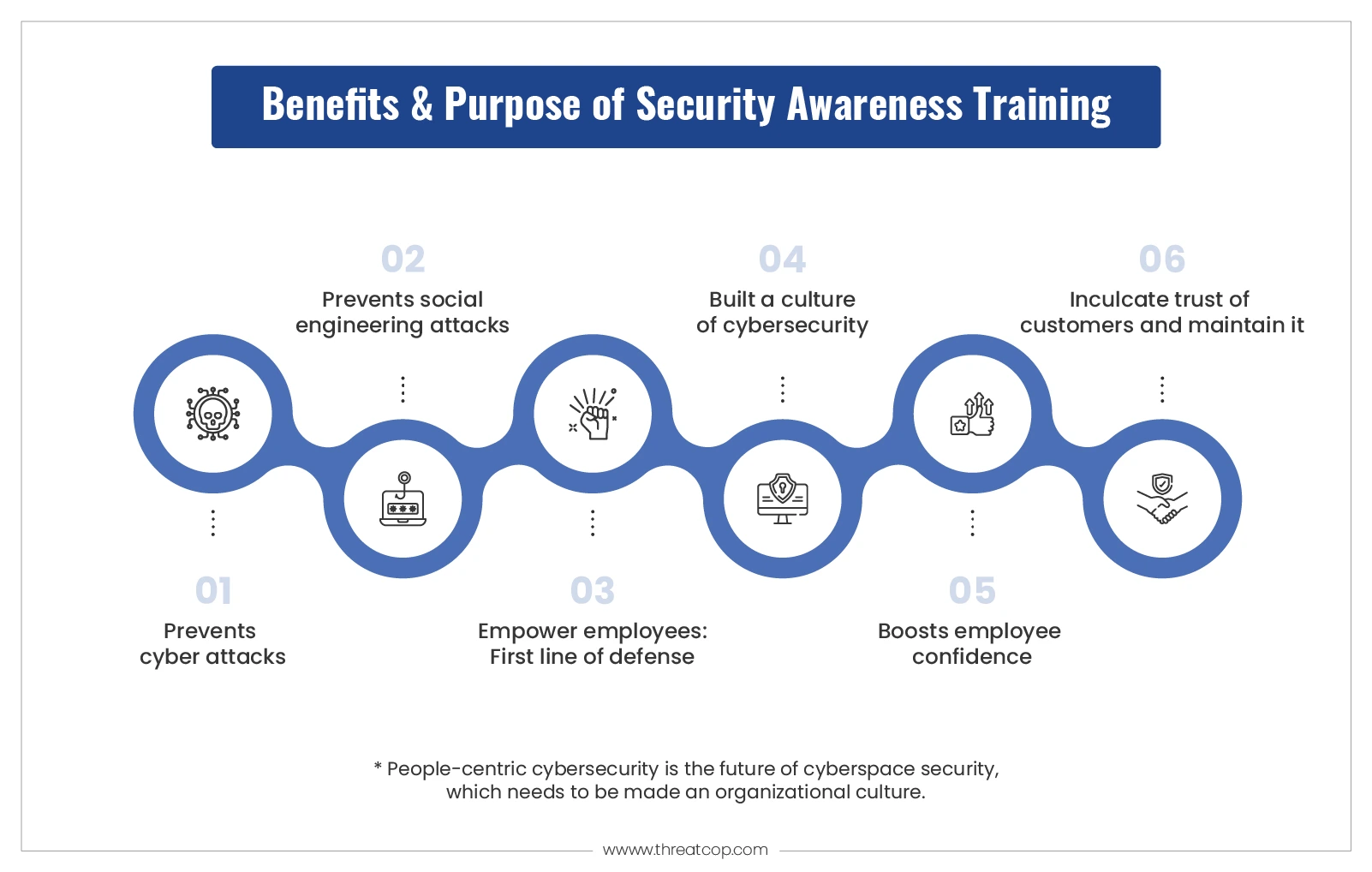
Creating a truly secure organization isn’t just about implementing the latest technology; it’s about fostering a culture where security is everyone’s responsibility. This involves a top-down approach, engaging leadership, empowering employees, and consistent communication. A strong security culture reduces vulnerabilities, improves response times to incidents, and ultimately strengthens the organization’s resilience against cyber threats.
Leadership’s Role in Promoting Security Best Practices
Leadership sets the tone for security within an organization. Visible and active participation from executives is crucial. This means more than just issuing mandates; it involves actively participating in security training, publicly endorsing security initiatives, and consistently demonstrating a commitment to best practices. For instance, a CEO visibly using strong passwords and practicing safe browsing habits sends a powerful message that security isn’t just a concern for the IT department, but for everyone at every level.
Regular communication from leadership, highlighting security successes and addressing breaches transparently, builds trust and reinforces the importance of security. When leaders are seen prioritizing and actively engaging with security, employees are far more likely to follow suit.
Encouraging Secure Reporting of Security Concerns
Establishing a safe and anonymous reporting system is vital. Employees need to feel comfortable reporting potential security issues without fear of repercussions. This can be achieved through anonymous reporting channels, clear communication about the lack of retribution for good-faith reporting, and regular reminders of the importance of reporting. The organization should actively promote a culture of open communication where mistakes are seen as learning opportunities, not grounds for punishment.
A successful reporting system might include a dedicated, secure online portal, a confidential email address, or even a suggestion box – the key is to offer multiple, accessible options. Regular communication campaigns emphasizing the importance of reporting, and showcasing how reported issues have led to positive outcomes, can further encourage this behavior.
A Communication Plan for Reinforcing Security Awareness
Consistent reinforcement is key to maintaining security awareness. A multi-faceted communication plan is essential, incorporating various methods to reach all employees. This could involve regular email newsletters with security tips, short training videos, interactive quizzes, posters in common areas, and inclusion of security messages in internal communications. The messaging should be tailored to different departments and roles, ensuring relevance and avoiding information overload.
For example, the marketing department might receive training on phishing scams, while the IT department might focus on secure coding practices. Regular security awareness campaigns, themed around specific threats or best practices, can help maintain employee engagement and knowledge retention. A successful communication plan regularly evaluates its effectiveness and adapts its approach based on feedback and results.
Guidelines for Establishing Clear Security Policies and Procedures
Clear, concise, and easily accessible security policies and procedures are essential for building a culture of security awareness. These guidelines should be regularly reviewed and updated to reflect evolving threats and best practices.
- Policy Clarity: Policies should be written in plain language, avoiding technical jargon, and should clearly Artikel expectations and consequences of non-compliance.
- Accessibility: Policies should be readily available to all employees, ideally through an easily accessible online portal or intranet.
- Regular Review and Updates: Policies should be reviewed and updated at least annually, or more frequently if significant changes occur in the threat landscape or organizational structure.
- Training and Communication: Employees should receive training on the policies and procedures, and regular communication should reinforce their importance.
- Enforcement: Consistent enforcement of policies is crucial. Consequences for non-compliance should be clearly defined and consistently applied.
- Feedback Mechanism: A mechanism for employees to provide feedback on the policies and procedures should be established.
Conclusive Thoughts

Ultimately, effective security awareness training isn’t about compliance; it’s about empowering individuals. By understanding the human element – our biases, motivations, and learning styles – we can create training programs that truly resonate, fostering a culture of security that’s not just enforced, but embraced. Let’s move beyond the checklist mentality and build a security-conscious workforce, one engaging training session at a time.
Top FAQs
How do I know if my training is actually effective?
Track key metrics like phishing test success rates, reported security incidents, and employee feedback. Look for a reduction in security breaches and an increase in proactive security behavior.
What if my employees find the training boring?
Incorporate interactive elements like games, simulations, and real-world case studies. Personalize the content to make it relevant to their roles and responsibilities.
How can I encourage employees to report security concerns?
Establish a clear, anonymous reporting system and assure employees there will be no retribution for reporting genuine concerns. Promote a culture of open communication and feedback.
What’s the best way to deal with employees who consistently ignore security protocols?
Address the issue privately, understanding the reasons behind their behavior. Offer additional training or mentoring, and consider adjusting training methods based on their learning style. If the problem persists, escalate to HR.




