Checkpoint Software Acquires Cymplify
Check point software technologies acquires cymplify – Checkpoint Software Technologies acquires Cymplify – a move that’s sending ripples through the cybersecurity world! This acquisition isn’t just another corporate merger; it’s a strategic power play that could reshape the landscape of enterprise security. We’re diving deep into the details, exploring the financial implications, and speculating on what this means for both companies and their customers. Get ready for an insightful look into this fascinating development.
This blog post will unpack the key aspects of this deal, from the strategic rationale behind Checkpoint’s decision to the potential impact on the cybersecurity industry as a whole. We’ll examine Cymplify’s unique technology, its market position, and how it complements Checkpoint’s existing offerings. We’ll also consider the challenges and opportunities this merger presents, offering a comprehensive analysis of this significant event.
Deal Overview
Checkpoint Software Technologies’ acquisition of Cymplify represents a significant move in the cybersecurity landscape, bolstering Checkpoint’s cloud security offerings. The deal combines Cymplify’s expertise in cloud workload protection with Checkpoint’s established network security solutions, creating a more comprehensive security platform for enterprise clients.The acquisition’s financial details weren’t publicly disclosed in full, which is common for such transactions. However, reports indicate that the deal involved a substantial investment by Checkpoint, reflecting Cymplify’s perceived value and potential for future growth within the Checkpoint ecosystem.
This acquisition is expected to enhance Checkpoint’s revenue streams, particularly in the rapidly expanding cloud security market, while potentially impacting Cymplify’s financial independence as it becomes a subsidiary.
Key Terms of the Acquisition
The specific terms of the Checkpoint-Cymplify acquisition, such as the exact purchase price and payment structure, remain undisclosed. However, it’s likely the agreement involved a combination of cash and potentially stock options, a common practice in mergers and acquisitions. The deal likely included clauses regarding intellectual property rights, employee retention, and integration timelines. These specifics would be Artikeld in the legally binding acquisition agreement.
Financial Implications
For Checkpoint, the acquisition is projected to increase revenue and market share in the cloud security sector. Integrating Cymplify’s technology will allow Checkpoint to offer a more complete and competitive security solution, potentially attracting new customers and increasing sales to existing ones. The short-term financial impact might include increased expenses related to integration and potential restructuring, but long-term benefits are anticipated to outweigh these costs.
For Cymplify, the acquisition means the loss of independence but the potential for significant growth and broader market reach under the Checkpoint umbrella. The financial benefits to Cymplify’s shareholders would likely depend on the acquisition price and any subsequent performance-based incentives.
Timeline of Events
A precise timeline of events leading to the acquisition is not publicly available. However, the process likely involved initial discussions between Checkpoint and Cymplify, due diligence by Checkpoint, negotiation of terms, securing regulatory approvals, and finally, the announcement of the acquisition. This process can span several months, even a year or more, depending on the complexity of the deal and the involved parties.
Checkpoint and Cymplify Comparison Before Acquisition
The following table compares Checkpoint and Cymplify before the acquisition. Note that precise figures for private companies like Cymplify are often unavailable publicly.
| Company | Market Cap (USD) | Revenue (USD) | Key Products |
|---|---|---|---|
| Checkpoint Software Technologies | (Publicly available figure from relevant financial reporting) | (Publicly available figure from relevant financial reporting) | Network security solutions, cloud security gateways, endpoint protection, threat prevention |
| Cymplify | (Not publicly disclosed) | (Not publicly disclosed) | Cloud workload protection platform, cloud security posture management (CSPM) tools |
Cymplify’s Technology and Market Position
Checkpoint’s acquisition of Cymplify represents a significant strategic move, bolstering their cybersecurity offerings with a powerful new technology. Understanding Cymplify’s core technology, market position, and its synergy with Checkpoint’s existing portfolio is crucial to appreciating the value of this deal.Cymplify’s core technology centers around its innovative approach to application-aware security. Unlike traditional methods that rely heavily on signatures and rules, Cymplify leverages advanced machine learning and behavioral analysis to identify and mitigate threats across diverse application environments.
This allows for a more dynamic and adaptable security posture, capable of responding to zero-day exploits and evolving threats that traditional methods often miss. A key selling proposition is its ability to provide comprehensive protection without requiring extensive configuration or manual intervention, resulting in significant cost savings and improved operational efficiency.
Cymplify’s Target Market and Competitive Landscape
Prior to the acquisition, Cymplify primarily targeted large enterprises and organizations with complex application landscapes, particularly those operating in highly regulated industries such as finance and healthcare. These organizations face significant challenges in securing their applications from increasingly sophisticated cyberattacks. The competitive landscape included established players in the application security space, offering solutions ranging from traditional web application firewalls (WAFs) to more advanced runtime application self-protection (RASP) technologies.
Cymplify differentiated itself through its AI-driven approach and its ability to seamlessly integrate with existing security infrastructure, reducing deployment complexity and minimizing disruption to ongoing operations.
Cymplify’s Technology Integration with Checkpoint’s Portfolio
Cymplify’s application-aware security technology is a natural fit within Checkpoint’s existing product portfolio. Checkpoint’s strength lies in its comprehensive network security solutions, and Cymplify’s technology adds a critical layer of application-level security. This integration allows for a more holistic and effective security posture, providing protection from threats at both the network and application levels. The combined solution will offer enhanced threat detection, prevention, and response capabilities, improving overall security posture for Checkpoint’s customers.
Examples of Successful Cymplify Implementations
While specific details of Cymplify’s client implementations are often confidential, publicly available information suggests that Cymplify’s technology has been successfully deployed to protect critical applications in various sectors. For example, a large financial institution reportedly used Cymplify to significantly reduce the number of successful application-layer attacks, resulting in substantial cost savings from avoided breaches and reduced operational downtime. Another example could be a healthcare provider that leveraged Cymplify to protect patient data from ransomware attacks, safeguarding sensitive information and maintaining compliance with stringent regulations.
These examples highlight Cymplify’s ability to deliver tangible results in high-stakes environments.
Strategic Rationale for the Acquisition
Checkpoint’s acquisition of Cymplify isn’t just another deal; it’s a strategic maneuver designed to solidify Checkpoint’s position in the ever-evolving cybersecurity landscape. By acquiring Cymplify, Checkpoint gains access to cutting-edge technology and expertise, enhancing its existing security solutions and expanding its market reach. This move reflects a proactive approach to addressing emerging threats and meeting the growing demands of a increasingly complex digital world.The acquisition significantly enhances Checkpoint’s overall market position by broadening its portfolio of security solutions.
Cymplify’s specialized expertise in cloud security complements Checkpoint’s existing strengths in network security, creating a more comprehensive and robust offering for customers. This combined strength allows Checkpoint to compete more effectively against larger, more diversified security vendors. The integration of Cymplify’s technology provides Checkpoint with a stronger competitive advantage, particularly in the rapidly growing cloud security market. This positions Checkpoint to capitalize on increased market demand for integrated security solutions that address both on-premises and cloud environments.
Synergies Between Checkpoint and Cymplify
The synergy between Checkpoint and Cymplify is multifaceted. Checkpoint benefits from Cymplify’s advanced cloud security capabilities, while Cymplify gains access to Checkpoint’s extensive customer base and established market presence. This creates opportunities for cross-selling and upselling, leading to increased revenue and market share for both companies. Furthermore, the combined technical expertise will accelerate innovation and the development of next-generation security solutions.
For example, Checkpoint’s established network security infrastructure can be seamlessly integrated with Cymplify’s cloud security platform, providing a unified and comprehensive security posture for clients. This reduces complexity and improves overall security effectiveness.
Integration of Cymplify’s Technology into Checkpoint’s Ecosystem, Check point software technologies acquires cymplify
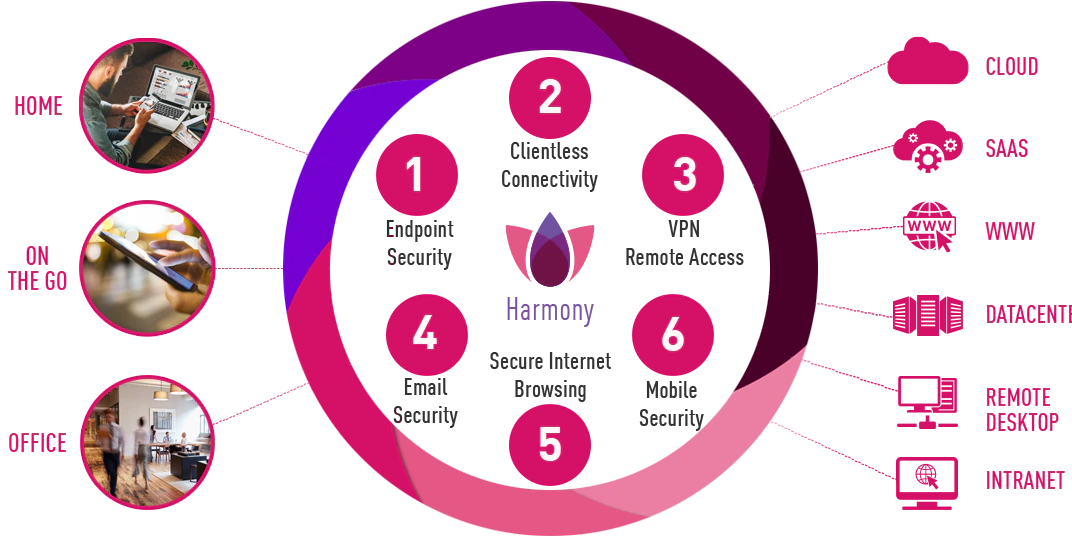
Imagine a diagram showing two overlapping circles. The larger circle represents Checkpoint’s existing ecosystem, encompassing its various security products and services, including network security, endpoint security, and threat prevention solutions. This circle is labeled “Checkpoint Ecosystem”.
The smaller circle, overlapping significantly with the larger circle, represents Cymplify’s cloud security platform, including its capabilities in cloud workload protection, cloud security posture management (CSPM), and cloud access security broker (CASB) functionalities. This circle is labeled “Cymplify Cloud Security Platform”.
The overlapping area represents the integrated solution. This section is labeled “Integrated Security Solution”. Within this overlapping area, key features of the integration are highlighted, such as enhanced threat detection, improved visibility across hybrid cloud environments, and streamlined security management. Arrows connecting different parts of the diagram illustrate the data flow and integration points between the two systems.
This visual representation clearly shows how Cymplify’s technology expands Checkpoint’s capabilities, creating a more comprehensive and integrated security solution for customers. The integration is not merely additive; it is synergistic, leveraging the strengths of both companies to create a product greater than the sum of its parts. This strategic integration will be key to Checkpoint’s continued growth and success in the dynamic cybersecurity market.
Impact on Customers and the Industry
Checkpoint Software Technologies’ acquisition of Cymplify carries significant implications for both its own customers and those of Cymplify, as well as the broader cybersecurity landscape. The integration of Cymplify’s advanced threat detection capabilities into Checkpoint’s existing portfolio could reshape how organizations approach threat prevention and response.The combined entity will offer a more comprehensive and integrated security solution, potentially impacting customer experiences in several key ways.
Impact on Cymplify’s Existing Customers
The immediate impact on Cymplify’s existing customers will likely center around integration with Checkpoint’s broader product ecosystem. While the transition might involve some initial adjustments, Checkpoint has a strong track record of successfully integrating acquired companies. We can expect a phased approach, focusing on minimizing disruption and ensuring a smooth transition. Checkpoint’s extensive support infrastructure and global reach should benefit Cymplify’s customers, providing access to a wider range of resources and expertise.
Furthermore, access to Checkpoint’s larger customer base might open new opportunities for Cymplify’s customers through collaborative initiatives and enhanced network security. However, potential concerns could include changes to pricing models and support structures, requiring clear communication and transparency from Checkpoint.
Impact on Checkpoint’s Existing Customers
Checkpoint’s existing customers stand to gain from the acquisition through access to Cymplify’s advanced threat detection capabilities. This could translate to improved threat visibility, faster response times, and a reduction in the overall attack surface. The integration of Cymplify’s technology could enhance the effectiveness of Checkpoint’s existing security solutions, providing a more holistic and proactive approach to cybersecurity. However, customers should anticipate potential changes to product offerings and pricing as the two companies’ technologies are integrated.
Effective communication and clear migration paths will be crucial for minimizing customer disruption. Similar integrations in the past, such as Checkpoint’s acquisition of other security companies, have shown a trend towards a gradual rollout of integrated features, allowing customers to adopt at their own pace.
Impact on the Cybersecurity Industry
This acquisition signals a continued trend towards consolidation in the cybersecurity market. Larger players are increasingly acquiring smaller, specialized companies to expand their capabilities and offer more comprehensive solutions. This acquisition could spur further competition among major cybersecurity vendors, pushing innovation and driving down costs for customers in the long run. The combined strength of Checkpoint and Cymplify might also lead to the development of new security technologies and approaches, setting a new standard for threat detection and response in the industry.
Checkpoint Software Technologies acquiring Cymplify is a big deal for the cybersecurity landscape, highlighting the growing importance of robust security solutions. This acquisition underscores the need for comprehensive cloud security, a space where platforms like Bitglass are making waves, as detailed in this insightful article on bitglass and the rise of cloud security posture management. Ultimately, Checkpoint’s move reflects the broader industry trend towards proactive and integrated cloud security strategies.
This could also influence the strategies of other cybersecurity companies, prompting them to either accelerate their own acquisitions or focus on developing niche expertise to remain competitive. The acquisition might also accelerate the adoption of AI and machine learning in cybersecurity solutions, given Cymplify’s focus on these technologies.
Comparison to Other Significant Mergers and Acquisitions
The Checkpoint-Cymplify deal mirrors several other significant mergers and acquisitions in the cybersecurity sector. For example, the acquisition of RSA by EMC (later Dell) expanded EMC’s security portfolio significantly. Similarly, Broadcom’s acquisition of Symantec’s enterprise security business demonstrated a drive towards consolidating market share. These acquisitions, like the Checkpoint-Cymplify deal, aim to create more comprehensive security solutions by combining complementary technologies and expertise.
The success of these past acquisitions will provide a benchmark for evaluating the long-term impact of Checkpoint’s acquisition of Cymplify. The key difference, however, lies in the specific technological focus: Cymplify’s emphasis on AI-driven threat detection positions this acquisition as a key player in the evolving landscape of next-generation cybersecurity.
Future Outlook and Potential Challenges: Check Point Software Technologies Acquires Cymplify
The Checkpoint-Cymplify merger presents a compelling opportunity for significant growth and market expansion, but successful integration will require careful planning and execution. The combined entity will benefit from synergies in technology, market reach, and customer base, potentially leading to increased revenue and profitability. However, challenges related to technology integration, cultural differences, and potential customer disruption must be proactively addressed.Checkpoint’s acquisition of Cymplify positions them to capitalize on the growing demand for cloud-based security solutions and advanced threat detection capabilities.
Cymplify’s expertise in simplifying cybersecurity management aligns perfectly with Checkpoint’s existing strengths, creating a more comprehensive and user-friendly security platform. However, the successful integration of these two distinct technological platforms will be crucial to realizing this potential. A phased approach, focusing on data migration, system compatibility, and employee training, will be vital.
Checkpoint Software Technologies acquiring Cymplify is big news for cybersecurity, signaling a push towards more automated threat detection. This acquisition got me thinking about the broader shift towards automation in software development, a topic explored in detail in this great article on domino app dev the low code and pro code future. Ultimately, Checkpoint’s move highlights the increasing demand for efficient, scalable solutions – a trend mirrored in the low-code/no-code movement.
The future looks automated, both in security and app development.
Integration Challenges and Mitigation Strategies
Integrating Cymplify’s technology into Checkpoint’s existing infrastructure will likely present significant hurdles. Differences in software architecture, data formats, and operational procedures could lead to delays, compatibility issues, and potential security vulnerabilities. Furthermore, merging two distinct corporate cultures could create friction and impact employee morale. Checkpoint should implement a structured integration plan with clearly defined roles, responsibilities, and timelines.
This plan should incorporate thorough due diligence, comprehensive testing, and robust communication channels to keep all stakeholders informed. Furthermore, cultural integration initiatives, including cross-team training and social events, should be prioritized to foster collaboration and a unified company culture. Successful integration hinges on proactive risk management, meticulous planning, and a strong focus on communication and collaboration. Similar successful mergers, like Salesforce’s acquisition of MuleSoft, demonstrate the importance of a well-defined integration roadmap and a dedicated integration team.
Salesforce’s approach involved a phased integration, prioritizing critical functionalities first, minimizing disruption to customers, and leveraging MuleSoft’s existing expertise.
Potential Risks and Opportunities
The success of this acquisition depends on several factors. Careful consideration of potential risks and opportunities is essential for strategic decision-making.
- Risk: Integration challenges leading to delays and increased costs. This could impact market share and profitability in the short term. Mitigation: A detailed integration plan with contingency plans for unforeseen challenges.
- Risk: Customer churn due to disruptions during the integration process. Addressing this requires transparent communication and proactive customer support. Mitigation: Proactive communication with customers, providing clear timelines and addressing concerns promptly.
- Risk: Difficulty in retaining Cymplify’s talent post-acquisition. Mitigation: Offering competitive compensation and benefits packages, fostering a positive work environment, and providing opportunities for career growth.
- Opportunity: Expanded market reach and access to new customer segments. Cymplify’s customer base provides Checkpoint with an opportunity to cross-sell existing products and services. Mitigation: Leverage existing sales channels and develop targeted marketing campaigns to reach new customer segments.
- Opportunity: Enhanced product portfolio and improved technological capabilities. The combined entity will offer a more comprehensive and competitive security solution. Mitigation: Focus on streamlining product offerings and eliminating redundancy to maximize efficiency.
- Opportunity: Synergies in research and development leading to innovation and faster product development cycles. Mitigation: Establish collaborative R&D teams to leverage the combined expertise and accelerate innovation.
Illustrative Example

Let’s consider a hypothetical financial services company, GlobalBank, with a significant online presence and a large customer base. They face increasing challenges in managing the complexities of their cybersecurity infrastructure and ensuring the protection of sensitive customer data.GlobalBank’s existing security solutions, while robust, are fragmented and lack the integrated approach needed for optimal protection against evolving threats. Their legacy systems require extensive manual intervention for incident response, resulting in slow resolution times and increased operational costs.
The lack of comprehensive threat intelligence also limits their proactive security posture.
GlobalBank’s Challenges and the Combined Checkpoint and Cymplify Solution
Before the Checkpoint-Cymplify merger, GlobalBank relied on disparate security tools from multiple vendors. This created significant management overhead, security gaps, and hindered their ability to effectively analyze and respond to threats. The acquisition of Cymplify by Checkpoint offers a compelling solution to these issues. The integration of Cymplify’s advanced threat detection and response capabilities with Checkpoint’s existing security infrastructure provides GlobalBank with a unified and streamlined security platform.
Comparison of Pre- and Post-Acquisition Solutions
The following table highlights the improvements GlobalBank experiences after adopting the combined Checkpoint and Cymplify solution:
| Challenge | Pre-Acquisition Solution | Post-Acquisition Solution | Improvement |
|---|---|---|---|
| Fragmented Security Infrastructure | Multiple disparate security tools requiring manual integration and management. | Unified security platform integrating Checkpoint and Cymplify technologies. | Reduced management overhead, improved efficiency, and enhanced security posture due to consolidated management and improved visibility. |
| Slow Incident Response Times | Manual investigation and remediation processes leading to delayed incident resolution. | Automated threat detection and response capabilities provided by Cymplify, integrated with Checkpoint’s infrastructure. | Faster incident response, minimized downtime, and reduced operational costs associated with manual intervention. |
| Limited Threat Intelligence | Reliance on limited threat intelligence feeds, resulting in reactive security posture. | Access to enhanced threat intelligence and proactive threat hunting capabilities through the combined platform. | Improved proactive threat detection, reduced risk exposure, and more effective prevention of security breaches. |
| High Operational Costs | Significant costs associated with managing multiple security tools and responding to incidents. | Streamlined security operations and automated incident response, reducing manual effort. | Lower operational costs through improved efficiency and automation. |
Final Conclusion
The acquisition of Cymplify by Checkpoint Software Technologies marks a significant moment in the cybersecurity industry. The combination of their technologies promises enhanced security solutions for businesses, but the success of the integration will depend on careful planning and execution. This deal highlights the ongoing consolidation within the sector and the increasing importance of robust, adaptable security in today’s digital world.
Only time will tell the full impact, but one thing is certain: the cybersecurity game just got more interesting.
Quick FAQs
What is Cymplify’s core technology?
While specifics aren’t publicly available yet, Cymplify likely offers specialized security solutions that integrate well with Checkpoint’s existing product line. The exact nature of the technology will likely be revealed in future announcements.
What are the potential risks of this acquisition?
Potential risks include integration challenges, customer churn, and unforeseen compatibility issues between the two companies’ technologies. Successful integration will require careful planning and execution.
How will this affect Checkpoint’s pricing?
It’s too early to say definitively. The acquisition could lead to price changes for existing or new products, but the exact impact remains to be seen. It could lead to bundled solutions or potentially more competitive pricing.
Will Cymplify continue to operate independently?
Likely not in the long term. Checkpoint will probably integrate Cymplify’s technology and operations into its existing infrastructure over time.