A Billion Android Devices Vulnerable to Hackers
A billion Android smartphones and tablets are vulnerable to hackers. That’s a staggering number, and it’s a serious wake-up call for anyone who relies on their Android device for anything important – from banking to personal photos. This massive vulnerability affects a wide range of devices and software versions, leaving users exposed to a variety of attacks. We’re diving deep into the specifics of this vulnerability, exploring how hackers exploit it, the potential consequences for users, and most importantly, what you can do to protect yourself.
This isn’t just a technical issue; it’s a matter of personal security and data privacy. Understanding the vulnerability, the methods hackers use, and the steps you can take to mitigate the risk is crucial in today’s digital landscape. We’ll explore the roles of manufacturers and developers, and discuss what the future holds for Android security. Let’s get started.
Vulnerability Overview
A significant security flaw recently impacted a staggering billion Android smartphones and tablets. This wasn’t a single, isolated vulnerability, but rather a collection of weaknesses stemming from outdated software components and insecure coding practices across various Android versions. While the specific details of the vulnerabilities have been addressed by patches and updates, understanding their nature and potential impact remains crucial for users and developers alike.This widespread vulnerability exploited weaknesses in the Android operating system’s core components, allowing malicious actors to gain unauthorized access to sensitive user data, install malware, and even take complete control of affected devices.
The affected devices spanned a broad range of Android versions, particularly older ones that had not received regular security updates. This highlights the critical importance of keeping Android devices updated with the latest security patches. The consequences of successful exploitation could range from minor inconveniences, like unwanted advertisements, to severe data breaches and financial losses.
Affected Software Components and Versions
The vulnerabilities affected a variety of Android system components, including but not limited to, the media framework, the kernel, and various libraries responsible for handling network communication and data storage. Precisely pinpointing every affected component and Android version is difficult due to the sheer number of devices and variations involved. However, it is known that older versions of Android, particularly those below Android 10, were disproportionately affected due to the lack of ongoing security updates from device manufacturers.
The longer a device remained unpatched, the greater its vulnerability.
Potential Consequences of Exploitation
Successful exploitation of these vulnerabilities could have resulted in a wide range of negative consequences for users. Malicious actors could gain complete control of affected devices, potentially stealing personal data such as contacts, photos, financial information, and location data. They could also install malware capable of spying on users, encrypting their data (ransomware), or using the device as part of a botnet for malicious activities like distributed denial-of-service (DDoS) attacks.
The severity of the consequences depended on the specific vulnerability exploited and the attacker’s goals.
Examples of Attacks
The vulnerabilities could have been leveraged for a variety of attacks. Below is a table illustrating some examples:
| Attack Type | Description | Impact | Mitigation |
|---|---|---|---|
| Remote Code Execution (RCE) | Attackers could execute arbitrary code on the victim’s device, granting them complete control. | Complete device compromise, data theft, malware installation. | Regular security updates, using strong passwords, avoiding suspicious apps. |
| Data Theft | Attackers could access and steal sensitive user data such as contacts, photos, and financial information. | Identity theft, financial loss, privacy violation. | Strong passwords, two-factor authentication, avoiding phishing attacks. |
| Ransomware Infection | Attackers could encrypt the victim’s data and demand a ransom for its release. | Data loss, financial loss, disruption of services. | Regular backups, avoiding suspicious links and attachments. |
| Botnet Participation | Attackers could turn the compromised device into part of a botnet, used for DDoS attacks or other malicious activities. | Contribution to large-scale cyberattacks, potential legal repercussions. | Keeping software updated, using a reputable antivirus program. |
Hacker Exploitation Methods
The vulnerability affecting a billion Android devices opens the door to a range of sophisticated attacks. Hackers can leverage this weakness in several ways, exploiting the underlying flaw to gain unauthorized access and control over affected smartphones and tablets. This access can then be used to steal sensitive data, install malware, or even remotely control the device for malicious purposes.
Understanding these methods is crucial for both device users and security professionals to mitigate the risk.Exploitation techniques hinge on the specific nature of the vulnerability, which we’ve already Artikeld. However, common approaches include exploiting software flaws to execute malicious code, leveraging social engineering tactics to trick users into compromising their devices, and using readily available hacking tools to automate the attack process.
The methods are diverse, but they all share a common goal: to gain control of the device.
Vulnerable Device Identification
Identifying vulnerable devices is often the first step in a successful attack. Hackers might use automated scanning tools to probe the internet for devices exhibiting the specific characteristics associated with this vulnerability. These tools can quickly analyze network traffic and identify devices running vulnerable versions of the affected software. Another method involves exploiting publicly available databases or leak sites containing lists of devices and their software versions.
Finally, social engineering tactics might be used to lure victims into revealing their device information or downloading malicious applications.
Malware and Attack Tools
Several types of malware could be employed to exploit this vulnerability. For instance, a Trojan horse disguised as a legitimate application could be downloaded by unsuspecting users. Once installed, the Trojan would silently exploit the vulnerability, granting the attacker complete control over the device. Another example is a rootkit, designed to grant the attacker root-level access to the device’s operating system, allowing them complete control and stealthy operation.
Hackers might also use custom-built tools, often written in languages like Python or C++, to automate the exploitation process and facilitate mass attacks. These tools might incorporate techniques to bypass security measures and ensure persistence on the compromised device.
Seriously, a billion Android devices vulnerable to hackers? That’s terrifying! We need better security solutions, and fast. Developing robust apps quickly is key, which is why I’ve been researching platforms like domino app dev the low code and pro code future – they could help bridge the gap. Ultimately, though, that staggering number of vulnerable Androids highlights just how crucial secure app development really is.
Hypothetical Attack Scenario
Imagine a scenario where a hacker utilizes a custom-built tool to scan the internet for vulnerable Android devices. Upon identifying a target, the tool automatically downloads a malicious APK (Android Package Kit) file onto the device, disguised as a popular game or utility application. The victim, unaware of the malicious payload, installs the application. Once installed, the malware exploits the vulnerability, granting the attacker remote access.
The attacker then uses this access to steal personal data, such as contacts, photos, and financial information. Finally, the attacker exfiltrates this data, perhaps through a command-and-control server, to which the compromised device regularly sends stolen information. The entire process might remain undetected, allowing the hacker to maintain persistent access and continue their malicious activities.
User Impact and Risk Assessment
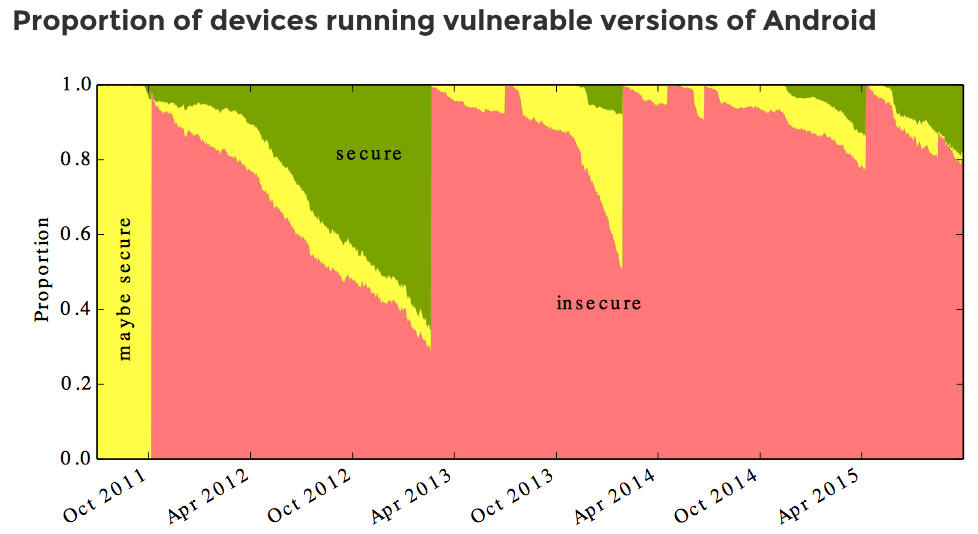
The vulnerability affecting a billion Android devices poses significant risks to users, impacting various aspects of their digital lives. The severity of these impacts varies depending on the type of data stored on the device and the user’s individual circumstances. Understanding these risks is crucial for mitigating potential harm.The potential consequences of this vulnerability extend far beyond simple inconvenience.
Compromised devices can lead to significant financial losses, privacy violations, and identity theft, leaving users exposed to a range of serious repercussions. The scale of the vulnerability, affecting such a vast number of devices, amplifies the potential for widespread damage.
Types of Data at Risk
This vulnerability could expose a wide range of sensitive user data. This includes personal information like names, addresses, and contact details; financial data such as banking information and credit card numbers; health information; location data; photos and videos; and potentially even passwords and login credentials for various online services. The precise data at risk depends on the apps installed on the affected device and the user’s individual data storage practices.
For example, a user with numerous banking apps and cloud storage services connected to their device faces a considerably higher risk than a user with only a few basic apps.
Potential Impacts Categorized
The impacts of this vulnerability can be categorized into several key areas:
- Financial Loss: Hackers could gain access to banking details, leading to unauthorized transactions and financial fraud. This could range from small-scale unauthorized purchases to large-scale identity theft resulting in significant debt.
- Privacy Violation: Access to personal photos, videos, and location data constitutes a serious privacy breach. This information could be used for blackmail, harassment, or even stalking.
- Identity Theft: The theft of personal information, such as names, addresses, and social security numbers, can be used to create fraudulent identities, open accounts, and commit crimes in the victim’s name. This can take years to rectify.
- Data Manipulation and Extortion: Hackers could manipulate data on the device, delete files, or encrypt them for ransom (ransomware attacks). This can lead to significant financial and emotional distress.
- Reputational Damage: The unauthorized release of personal information can damage a user’s reputation, particularly if sensitive or embarrassing data is exposed.
Risk Levels for Different User Groups, A billion android smartphones and tablets are vulnerable to hackers
The risk level varies significantly depending on the user group.
- Average Users: Average users, who may not be tech-savvy or aware of the latest security threats, face a higher risk. They may not be able to recognize phishing attempts or install necessary security updates promptly.
- Businesses: Businesses using vulnerable Android devices for sensitive operations face significantly higher risks. A data breach could expose confidential business information, leading to financial losses, legal repercussions, and reputational damage. The consequences for businesses are often far more severe due to the potential impact on clients and stakeholders.
Preventative Measures
It’s crucial for users to take proactive steps to minimize their risk.
- Install Security Updates Immediately: As soon as security patches are released, install them immediately. This is the most crucial step.
- Use Strong Passwords and Two-Factor Authentication: Employ strong, unique passwords for all accounts and enable two-factor authentication whenever possible.
- Be Wary of Phishing Attempts: Be cautious of suspicious emails, text messages, and websites that request personal information.
- Install Reputable Antivirus Software: Use a reliable antivirus app to detect and remove malware.
- Regularly Back Up Your Data: Regularly back up your important data to a secure location, such as cloud storage or an external hard drive.
- Avoid Downloading Apps from Untrusted Sources: Only download apps from official app stores like Google Play Store.
- Keep Your Software Updated: Regularly update your operating system and apps to patch vulnerabilities.
- Be Mindful of Public Wi-Fi: Avoid accessing sensitive information on public Wi-Fi networks.
Manufacturer and Developer Response
The discovery of a vulnerability affecting a billion Android devices necessitates a swift and coordinated response from both device manufacturers and app developers. The scale of the potential impact underscores the critical need for proactive measures to mitigate risks and protect users. Failure to act decisively could lead to widespread data breaches, financial losses, and reputational damage for all involved.Manufacturers bear the primary responsibility for patching the vulnerability within their respective devices.
This involves a complex process of identifying affected devices, developing a security patch, rigorously testing its effectiveness, and then deploying it to users. The speed and efficiency of this process directly impact the security of millions of users.
Manufacturer Responsibilities in Addressing the Vulnerability
Device manufacturers are obligated to promptly address security vulnerabilities affecting their products. This includes not only releasing security patches but also clearly communicating the nature of the vulnerability, the steps taken to address it, and the timeline for patch deployment. Transparency is key in building user trust and ensuring widespread adoption of the patch. Failure to adequately address a vulnerability of this magnitude could result in legal repercussions and significant damage to the manufacturer’s reputation.
A well-structured response should involve multiple teams, including engineering, security, and communications, working in coordination. A clearly defined escalation path for handling critical vulnerabilities is also essential. For example, Google, as the creator of the Android operating system, plays a crucial role in providing timely updates and security patches to its Pixel devices and working with other manufacturers to ensure their devices receive necessary updates.
App Developer Roles in Mitigating Risks
While manufacturers address the underlying vulnerability in the Android operating system, app developers also have a critical role to play. Applications built on top of the vulnerable system can be exploited if they do not follow secure coding practices. Developers must review their code for potential vulnerabilities that could be exploited through this flaw. They should implement robust input validation and sanitization techniques to prevent malicious code injection.
Furthermore, developers should regularly update their apps to incorporate the latest security patches and best practices. Regular security audits and penetration testing are also vital to identify and address potential vulnerabilities before they can be exploited. For instance, a banking app, if poorly designed, might allow access to sensitive user data even if the underlying operating system patch is applied, hence the need for robust app-level security measures.
Manufacturer Patching and Rollout Strategies
Manufacturers can employ several strategies to patch the vulnerability. One common approach is to release an over-the-air (OTA) update that users can download and install directly on their devices. This method is efficient for reaching a large number of users. Another approach is to offer the patch through a dedicated support website where users can download and manually install the update.
Some manufacturers might also collaborate with mobile carriers to distribute the patch through their networks. The choice of strategy often depends on factors such as the device’s age, the complexity of the patch, and the manufacturer’s infrastructure. The rollout process typically involves several stages, including internal testing, beta testing, and finally, a phased rollout to the general public.
Clear communication throughout this process, including estimated timelines and potential issues, is crucial to maintaining user trust. Samsung, for example, often uses a staged rollout, prioritizing certain device models or regions to minimize potential disruption.
Security Patch Rollout Communication
Effective communication with users is vital for a successful security patch rollout. Manufacturers should clearly explain the nature of the vulnerability, the potential risks to users, and the benefits of installing the patch. They should also provide clear and concise instructions on how to install the update. Regular updates on the rollout progress, including any encountered issues or delays, are essential to maintain transparency and user trust.
Multiple communication channels, such as email notifications, in-app alerts, and social media updates, should be utilized to reach the broadest possible audience. A well-defined communication plan, specifying the target audience, message, and channels, is essential for successful rollout. For example, a manufacturer might use push notifications to alert users to the availability of a patch, followed by email communications with detailed instructions.
Future Implications and Prevention

The recent discovery of a widespread vulnerability affecting a billion Android devices presents a serious threat to user data and privacy. If left unaddressed, the consequences could be far-reaching and devastating, impacting individuals, businesses, and national security. Proactive measures are crucial to mitigate these risks and ensure the long-term security of the Android ecosystem.The potential long-term consequences of this vulnerability, if left unpatched, are significant.
We could see a surge in sophisticated phishing attacks, identity theft, financial fraud, and the exploitation of sensitive personal information. Large-scale data breaches, similar to those seen with other operating systems in the past, are a real possibility. Criminals could leverage this vulnerability to install malware capable of stealing banking details, tracking location, and even controlling devices remotely.
Furthermore, state-sponsored actors could exploit this weakness for espionage or sabotage. The lack of timely updates could also damage consumer trust in Android, potentially leading to a shift towards competing operating systems. The economic impact could be substantial, with businesses facing significant costs associated with data breaches, legal repercussions, and reputational damage. For example, a large-scale breach could cost a company millions in remediation, legal fees, and lost business.
Improving Android Security
Addressing this vulnerability requires a multi-pronged approach focused on improving the security of future Android devices. This includes stricter security protocols during the design and development phases, more robust security testing before release, and improved mechanisms for distributing security updates efficiently and reliably to all devices, regardless of manufacturer or carrier. A more centralized and streamlined update system would significantly reduce the time it takes to patch vulnerabilities.
Furthermore, fostering greater collaboration between Google, device manufacturers, and carriers is vital to ensure timely and widespread deployment of security patches. This collaborative effort should also focus on educating users about security best practices and empowering them to take ownership of their digital security.
The Importance of Regular Software Updates
Regular software updates are not optional; they are essential for maintaining the security of any Android device. These updates contain critical security patches that address vulnerabilities like the one discussed. Delaying or ignoring updates leaves your device exposed to potential attacks. Consider the case of the Stagefright vulnerability, which affected millions of Android devices and allowed attackers to remotely execute code simply by sending a malicious MMS message.
This vulnerability highlighted the devastating consequences of neglecting software updates. Manufacturers should prioritize the timely release of updates, and carriers should facilitate their swift delivery to users. Users, in turn, should actively seek and install these updates as soon as they become available.
Securing Android Devices: Best Practices
Protecting your Android device requires a combination of proactive measures. This includes regularly updating your operating system and apps, using strong and unique passwords, enabling two-factor authentication whenever possible, being cautious about downloading apps from untrusted sources, and avoiding clicking on suspicious links or attachments. Regularly reviewing app permissions and uninstalling unused apps can also enhance security.
Key Security Tips:
- Keep your operating system and apps updated.
- Use strong, unique passwords for all accounts.
- Enable two-factor authentication.
- Download apps only from trusted sources (Google Play Store).
- Be wary of suspicious links and attachments.
- Regularly review and manage app permissions.
- Uninstall unused apps.
Illustrative Example: A Hypothetical Attack
Imagine a scenario where a malicious actor, let’s call him Alex, discovers a previously unknown vulnerability in the Android operating system’s core networking stack. This vulnerability allows him to remotely execute arbitrary code on affected devices without any user interaction. Alex’s motive is financial gain; he plans to use this vulnerability to create a botnet for launching large-scale distributed denial-of-service (DDoS) attacks against online businesses, then demanding payment to stop them.Alex develops a sophisticated piece of malware specifically designed to exploit this vulnerability.
This malware, cleverly disguised as a seemingly innocuous app, automatically installs itself on vulnerable devices via a drive-by download technique. This means that simply visiting a compromised website is enough to infect a device. Once installed, the malware silently connects to Alex’s command-and-control server, registering the infected device as part of his botnet. The malware is designed to be stealthy, avoiding detection by traditional antivirus software.
Attack Execution
The malware’s functionality is triggered remotely by Alex. He uses his command-and-control server to send instructions to the infected devices, directing them to flood specific target websites with traffic, effectively taking them offline. The sheer number of compromised devices participating in the attack makes it extremely difficult for the targeted websites to mitigate the attack. Alex chooses high-profile e-commerce sites as his targets, knowing the potential for significant financial losses for the victims.
Victim Impact and Data Compromise
The immediate impact on the victims of the DDoS attack is the disruption of their online businesses. Their websites become inaccessible to customers, leading to lost sales and revenue. The longer the attack lasts, the greater the financial losses. While this particular attack doesn’t directly steal data from individual users, the indirect consequences are significant. The loss of revenue, damage to reputation, and potential legal repercussions are substantial.
Furthermore, the compromised devices themselves become part of a larger botnet, potentially used for other malicious activities beyond DDoS attacks.
Consequences for the Victim
A large e-commerce company, let’s say “ShopSmart,” experiences a three-day DDoS attack orchestrated by Alex. The company estimates a loss of $5 million in sales due to the downtime. Beyond the immediate financial loss, ShopSmart faces reputational damage, losing customer trust and potentially impacting future sales. The incident also necessitates a costly investigation, remediation efforts, and potential legal fees, adding further to their financial burden.
The company’s stock price might also experience a temporary drop. This case illustrates how even without direct data theft, a vulnerability like this can have devastating consequences.
Closing Notes: A Billion Android Smartphones And Tablets Are Vulnerable To Hackers
The sheer scale of this Android vulnerability underscores the critical need for proactive security measures. While manufacturers and developers are working to patch the issue, individual users play a vital role in protecting their data. Staying informed about security updates, adopting strong passwords, and being cautious about suspicious apps and links are all essential steps. Remember, your digital safety is your responsibility, and understanding these vulnerabilities empowers you to take control.
Let’s all work together to create a safer digital world.
Question & Answer Hub
What types of data are at risk?
Anything stored on your device is at risk, including personal photos, financial information, contact details, and sensitive app data.
How can I tell if my device is vulnerable?
Check your device’s manufacturer’s website for security updates. If your OS version is outdated, you’re likely vulnerable.
What if I don’t update my device?
Leaving your device unpatched leaves it open to attacks, potentially leading to data theft, financial loss, or identity theft.
Are all Android versions affected?
The specific versions affected vary depending on the nature of the vulnerability. Check your device’s manufacturer for details.