A Guide to Building a Cybersecurity Career in Pen Testing Post-COVID
A guide to building a cybersecurity career in pen testing post covid – A Guide to Building a Cybersecurity Career in Pen Testing Post-COVID: The pandemic dramatically shifted the digital landscape, creating a surge in remote work and, consequently, a massive increase in cyber threats. This opened up incredible opportunities for penetration testers, skilled professionals who ethically hack systems to identify vulnerabilities. This guide navigates the path to becoming one of these in-demand experts, exploring essential skills, training options, portfolio building, and ethical considerations in this exciting field.
We’ll delve into the crucial technical skills – networking, operating systems, scripting – and the equally important soft skills, like communication and teamwork. We’ll compare popular certifications like OSCP and CEH, examine various educational paths from bootcamps to self-study, and even guide you through building a killer portfolio to land your dream job. Beyond the technical aspects, we’ll cover the ethical responsibilities and legal frameworks that are paramount in this profession.
Finally, we’ll map out potential career progressions and specializations within penetration testing, ensuring you stay ahead of the curve in this rapidly evolving field.
The Evolving Landscape of Cybersecurity Post-COVID

The COVID-19 pandemic dramatically altered the global landscape, and the cybersecurity world was no exception. The rapid shift to remote work, spurred by lockdowns and social distancing measures, created a vastly expanded attack surface for cybercriminals. This surge in remote work also significantly increased the demand for skilled cybersecurity professionals, particularly penetration testers, to safeguard organizations’ increasingly vulnerable digital assets.
The pandemic acted as a catalyst, accelerating pre-existing trends and highlighting critical vulnerabilities in existing security infrastructures.The increased reliance on remote access technologies, such as VPNs and cloud services, introduced new entry points for malicious actors. Simultaneously, the rise in phishing and social engineering attacks, exploiting anxieties and uncertainties surrounding the pandemic, resulted in a significant increase in successful breaches.
This created a perfect storm, demanding a more proactive and sophisticated approach to cybersecurity. The need for skilled penetration testers to identify and mitigate these vulnerabilities became paramount.
The Rise of Remote Penetration Testing
The shift to remote work fundamentally changed how penetration testing is conducted. Traditional on-site assessments became less feasible, necessitating a shift towards remote testing methodologies. This includes utilizing virtual machines, cloud-based infrastructure, and remote access tools to simulate real-world attacks against an organization’s network and systems. This transition demanded a new set of skills for penetration testers, including proficiency in remote access tools, cloud security, and virtualized environments.
The demand for individuals skilled in these areas skyrocketed, making penetration testing a highly sought-after career path. For example, companies like CrowdStrike saw a massive increase in demand for their remote penetration testing services during the pandemic, illustrating the market’s rapid adaptation.
The Penetration Testing Career Path
A career in penetration testing typically begins with a strong foundation in computer science, networking, and operating systems. Many professionals start with a bachelor’s degree in a related field, though practical experience and certifications are often valued equally or even more highly. Entry-level positions might include security analyst roles, where individuals gain experience in vulnerability management and incident response.
From there, aspiring penetration testers can progress to more specialized roles, focusing on specific areas like web application security, network penetration testing, or mobile application security. Obtaining industry-recognized certifications, such as the Offensive Security Certified Professional (OSCP) or Certified Ethical Hacker (CEH), significantly enhances career prospects and demonstrates a commitment to professional development. Continued learning and adaptation are crucial, given the ever-evolving nature of cybersecurity threats and technologies.
Experience in scripting languages like Python or PowerShell is also increasingly important, allowing for automation and efficiency in testing processes.
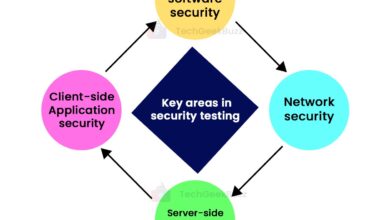
Essential Skills for a Penetration Tester
So, you’re thinking about a career in penetration testing? Fantastic! It’s a dynamic and rewarding field, but it demands a unique blend of technical prowess and interpersonal skills. This section breaks down the key elements you’ll need to master to succeed.
Core Technical Skills
A strong foundation in several technical areas is crucial for any aspiring penetration tester. These skills form the bedrock of your ability to identify and exploit vulnerabilities. Neglecting them will severely limit your effectiveness.
- Networking Fundamentals: Understanding TCP/IP, subnetting, routing protocols (like BGP and OSPF), and network topologies is essential. You need to know how networks function to effectively map them and find weaknesses. Think about tracing packets, identifying firewalls, and understanding how data flows. Without this, you’re essentially navigating a maze blindfolded.
- Operating System Expertise: Proficiency in both Windows and Linux is vital. You’ll be working with various operating systems, analyzing their security features, and identifying vulnerabilities. A deep understanding of their inner workings, including system calls, processes, and kernel modules, is crucial.
- Scripting and Programming: The ability to write scripts (Python, Bash, PowerShell) and potentially develop tools automates tasks, speeds up penetration testing, and allows you to create custom solutions for specific scenarios. This includes automating vulnerability scans, generating reports, and creating custom exploits.
- Database Management: Many applications rely on databases. Understanding SQL injection vulnerabilities and database security best practices is crucial. Knowing how to interact with different database systems (MySQL, PostgreSQL, MongoDB) is a significant asset.
- Web Application Security: This encompasses understanding common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). Familiarity with OWASP Top 10 is a must. You’ll need to know how to identify these vulnerabilities using both automated and manual techniques.
Essential Soft Skills
While technical skills are the foundation, soft skills are equally important, often determining whether a penetration tester is successful in their role or not. These skills ensure effective communication and collaboration within a team.
- Communication: Clearly articulating technical findings to both technical and non-technical audiences is critical. You need to explain complex vulnerabilities in a way that everyone can understand, from developers to executives.
- Teamwork: Penetration testing often involves collaboration. Effective teamwork ensures efficient task delegation and a shared understanding of the goals and findings.
- Problem-Solving: Penetration testing is all about problem-solving. You’ll encounter unexpected challenges and need to creatively find solutions. Analytical and critical thinking are essential for navigating these complexities.
- Time Management: Penetration tests are often conducted under strict deadlines. Effective time management is essential for delivering results on time and within budget.
- Ethical Considerations: Understanding and adhering to ethical guidelines is paramount. Penetration testers must always operate within legal and ethical boundaries.
Penetration Testing Certifications: A Comparison
Choosing the right certification can significantly impact your career trajectory. Several certifications demonstrate proficiency in penetration testing, each with its own strengths and weaknesses. Here’s a comparison:
| Certification | Cost (USD, approximate) | Difficulty | Job Market Value |
|---|---|---|---|
| OSCP (Offensive Security Certified Professional) | 1000-1500 | High (requires significant hands-on experience) | Very High (highly sought after by employers) |
| CEH (Certified Ethical Hacker) | 1000-1500 | Medium (more theoretical than OSCP) | High (widely recognized, good entry-level credential) |
| GPEN (GIAC Penetration Tester) | 2000-2500 | Medium-High (requires practical experience) | High (respected certification, often preferred for specific roles) |
| CPT (Certified Penetration Tester) | 500-1000 | Medium (balanced theory and practical application) | Medium-High (good for those starting their career) |
Educational Pathways and Training Resources
So, you’re ready to dive into the exciting world of penetration testing? Fantastic! But before you start probing networks, you need the right training and education. The path to becoming a pen tester isn’t a one-size-fits-all journey; it offers diverse routes, each with its own advantages and disadvantages. Let’s explore the different educational pathways available.
Formal Degree Programs
A formal education, such as a Bachelor’s or Master’s degree in Cybersecurity, Computer Science, or a related field, provides a strong foundation in computer science principles, networking, and security concepts. These programs often include coursework in cryptography, network security, operating systems, and ethical hacking, preparing you for more advanced studies and certifications. However, these programs can be expensive and time-consuming, taking several years to complete.
Furthermore, the specific penetration testing skills might require supplemental training beyond the core curriculum. A strong academic background, however, can open doors to higher-paying positions and leadership roles in the long run. Examples include degrees offered at universities like SANS Institute, Carnegie Mellon University, and many others.
Bootcamps
Cybersecurity bootcamps offer a more intensive and accelerated learning experience, typically lasting several weeks or months. These programs focus on practical skills and hands-on experience, often culminating in capstone projects that simulate real-world penetration testing scenarios. Bootcamps are a quicker and potentially less expensive alternative to traditional degree programs, allowing students to enter the workforce faster. However, they might lack the theoretical depth of a formal degree, and the quality can vary significantly between different bootcamps.
Choosing a reputable bootcamp with experienced instructors and a strong track record is crucial. Several bootcamps specialize in cybersecurity, and research is vital to finding one that fits your learning style and career goals.
Self-Learning and Online Resources
Self-learning, using online resources and self-paced courses, offers the most flexible and potentially cost-effective path. Numerous online platforms, such as Cybrary, Udemy, Coursera, and SANS Institute’s online courses, provide a wide range of cybersecurity courses, including penetration testing specific modules. This route requires significant self-discipline and motivation, as you are responsible for structuring your learning and staying on track.
However, it allows you to learn at your own pace, focusing on areas of interest and filling in knowledge gaps as you progress. This approach, combined with hands-on practice and participation in Capture The Flag (CTF) competitions, can be a highly effective way to build a robust skillset.
Reputable Online Resources and Training Programs
Choosing the right resources is critical for success in self-directed learning. Here are some reputable online platforms and training programs for aspiring penetration testers:
A list of reputable online resources and training programs is crucial for aspiring penetration testers. This list should include both well-known platforms and specialized training programs. The selection should consider factors such as course content, instructor expertise, student reviews, and cost-effectiveness. For example, some platforms offer free introductory courses, while others offer comprehensive paid programs leading to certifications.
- SANS Institute: Offers various penetration testing courses and certifications, renowned for their high quality and industry recognition.
- Cybrary: Provides a wide range of cybersecurity courses, including penetration testing, many of which are free or offered at affordable prices.
- Udemy: Hosts numerous penetration testing courses, varying in quality and price, requiring careful selection based on reviews and instructor credentials.
- Coursera: Offers university-level cybersecurity courses, some focusing on penetration testing principles and techniques.
- Offensive Security: Known for its challenging and highly regarded penetration testing certifications, such as OSCP (Offensive Security Certified Professional).
Building a Portfolio and Gaining Experience
Landing your dream penetration testing role requires more than just certifications and skills; you need a compelling portfolio that showcases your abilities. In a competitive job market, a strong portfolio acts as your resume’s visual counterpart, providing tangible evidence of your expertise and problem-solving skills. It’s your opportunity to demonstrate your practical knowledge and impress potential employers with the quality of your work.A well-structured portfolio allows recruiters to quickly assess your capabilities and identify your suitability for specific roles.
It’s a chance to present your best work, highlighting projects that demonstrate your proficiency in various penetration testing methodologies and tools. Without a portfolio, you risk being overlooked, especially in the post-COVID landscape where remote work and online application processes are the norm.
Portfolio Project Examples
Building a robust penetration testing portfolio involves strategically selecting projects that showcase a range of skills and experience. It’s about demonstrating both breadth and depth in your capabilities. Simply listing skills isn’t enough; you need to show how you apply them.
- Capture The Flag (CTF) Challenges: Participation in CTF competitions demonstrates your practical skills in vulnerability identification and exploitation. Document your approach, including the tools used, techniques applied, and the ultimate solution. Highlighting your problem-solving process is crucial. For example, detail your experience in a CTF involving a web application vulnerability, explaining how you identified the SQL injection flaw, exploited it, and documented the entire process.
- Personal Vulnerability Assessments: Conducting vulnerability assessments on your own websites or applications (with permission, of course!) allows you to showcase your ability to identify and report vulnerabilities. This could involve setting up a virtual machine with vulnerable applications, performing penetration testing, and documenting your findings in a professional report. Remember to clearly state the scope of your assessment and the limitations of your findings.
An example might be a vulnerability assessment of a custom-built web application you developed, focusing on common web application vulnerabilities like XSS or CSRF.
- Bug Bounty Programs: Participating in legitimate bug bounty programs provides real-world experience and demonstrates your ability to identify vulnerabilities in production systems. Successfully reported vulnerabilities, especially those with a financial reward, add significant weight to your portfolio. For example, detailing your participation in a bug bounty program for a well-known company, including the vulnerability you found, your methodology, and the eventual remediation, showcases your skills in a real-world context.
Creating a Compelling Portfolio Website
A well-designed website is essential for presenting your portfolio effectively. It should be professional, easy to navigate, and visually appealing. Think of it as your digital storefront – first impressions matter.
- Choose a Platform: Select a platform that suits your technical skills and budget. Options include website builders like Wix or Squarespace for ease of use, or GitHub Pages for a more technical approach.
- Structure and Design: Organize your projects logically, perhaps chronologically or by category (web application testing, network security, etc.). Use clear headings, concise descriptions, and high-quality images or screenshots to illustrate your work. Maintain a consistent design throughout the site for a professional look.
- Content is King: Each project description should include a brief overview, the tools and techniques used, the vulnerabilities identified, and the steps taken to exploit them (without compromising security). Include links to write-ups or reports whenever possible. Avoid overly technical jargon; focus on communicating your findings clearly and concisely.
- Showcase Your Skills: Highlight your key skills using s relevant to penetration testing roles. This helps recruiters easily find your portfolio and assess your suitability for their openings. Consider incorporating a skills section with a visual representation, like a progress bar, to emphasize your proficiencies.
- Call to Action: Include a clear call to action, such as your contact information or a link to your LinkedIn profile, making it easy for potential employers to reach out.
Job Search Strategies and Networking
Landing your dream penetration testing role requires a strategic approach that goes beyond simply applying online. The post-COVID landscape has shifted the way companies recruit, emphasizing networking and showcasing a strong online presence. This section Artikels effective strategies to navigate this competitive job market.Effective job searching involves a multi-pronged approach, leveraging both online resources and direct networking. Ignoring either aspect significantly reduces your chances of success.
A well-crafted resume and cover letter are also crucial for standing out from the competition.
Online Job Boards and Search Engines
Utilizing online job boards like LinkedIn, Indeed, Dice, and specialized cybersecurity job sites is essential. However, simply submitting your resume isn’t enough. Tailor your resume and cover letter to each specific job description, highlighting relevant skills and experience. Use s from the job posting to improve your chances of being noticed by Applicant Tracking Systems (ATS). Regularly search for new postings and proactively apply to positions that align with your skills and career goals.
Furthermore, expanding your search beyond specific “penetration tester” titles to include related roles like security analyst or ethical hacker can broaden your opportunities.
Networking within the Cybersecurity Community
Networking is paramount in the cybersecurity field. Attend online and in-person conferences, workshops, and meetups to connect with professionals. Engage in online communities and forums like Reddit’s r/netsec or participate in Capture The Flag (CTF) competitions to demonstrate your skills and build your network. LinkedIn is an invaluable tool for connecting with recruiters and professionals in the field.
Actively participate in discussions, share insightful content, and connect with individuals working in penetration testing roles. Don’t hesitate to reach out to professionals for informational interviews; these conversations can provide valuable insights into the industry and potential job opportunities. Building genuine relationships takes time and effort, but the rewards are significant.
Resume and Cover Letter Optimization
Your resume and cover letter are your first impression on potential employers. For penetration testing roles, highlight your technical skills, certifications (like OSCP, CEH, GPEN), and experience with penetration testing tools and methodologies. Quantify your accomplishments whenever possible. For example, instead of saying “Performed penetration testing,” say “Successfully identified and reported 15 critical vulnerabilities in a client’s network infrastructure, resulting in a 20% reduction in security risks.” Your cover letter should expand on your resume, demonstrating your passion for cybersecurity and highlighting your relevant experience.
Tailor your resume and cover letter to each specific job application, emphasizing the skills and experiences most relevant to the particular role. Use a clean, professional format that is easy to read and understand. Proofread carefully for any grammatical errors or typos. Consider using a professional resume writing service if you need assistance.
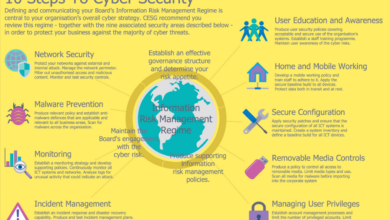
Ethical Considerations and Legal Frameworks
Penetration testing, while crucial for bolstering cybersecurity defenses, operates within a delicate ethical and legal landscape. Navigating this terrain responsibly is paramount for both the tester’s career and the security of the organizations they assess. A strong ethical compass, coupled with a thorough understanding of relevant laws and regulations, is essential for success in this field.The ethical implications of penetration testing stem from the inherent power to access and potentially disrupt systems.
Testers handle sensitive data, and their actions, even within a legally sanctioned engagement, could have unintended consequences if not carefully managed. Adherence to legal frameworks, such as the Computer Fraud and Abuse Act (CFAA) in the US or the Data Protection Act in the UK, is non-negotiable. Violating these laws can lead to severe penalties, including hefty fines and imprisonment.
Furthermore, a breach of trust with a client, even if unintentional, can severely damage a tester’s reputation and career prospects.
Legal Pitfalls and Mitigation Strategies
Understanding potential legal issues is crucial for preventing costly mistakes. One major pitfall is exceeding the scope of a signed contract. A tester must strictly adhere to the agreed-upon terms, which explicitly define the systems and data that can be accessed. Unauthorized access, even if done with good intentions, constitutes a violation. Another risk is failing to obtain proper authorization.
Penetration testing without explicit written consent from the organization’s owner is illegal and unethical. To mitigate these risks, always have a clear, detailed contract that Artikels the scope of work, permitted actions, and liabilities. Regularly review the contract throughout the testing process to ensure compliance. Maintain meticulous documentation of all activities, including timestamps, accessed systems, and any vulnerabilities discovered.
This documentation serves as a vital record for legal defense if needed. Finally, seek legal counsel when dealing with complex or ambiguous situations. This proactive approach minimizes legal risks and ensures responsible conduct.
Responsible Vulnerability Disclosure
Responsible disclosure is a cornerstone of ethical penetration testing. It involves privately reporting discovered vulnerabilities to the affected organization, allowing them time to remediate the issues before public disclosure. This coordinated approach prevents malicious actors from exploiting the vulnerabilities and protects the organization’s reputation and data. The timeline for disclosure varies depending on the severity of the vulnerability and the organization’s responsiveness.
However, the general principle remains consistent: prioritize the organization’s security and work collaboratively towards a solution. Many organizations have established vulnerability disclosure programs (VDPs) outlining their preferred disclosure methods and timelines. Familiarizing yourself with these programs is essential. If an organization is unresponsive or fails to address critical vulnerabilities within a reasonable timeframe, ethical guidelines may permit public disclosure, often after a final attempt at private notification.
This decision should be made carefully, considering the potential consequences and adhering to responsible disclosure best practices. The goal is always to protect users and systems while holding organizations accountable for their security posture.
Career Progression and Specialization

Penetration testing, while offering a thrilling entry point into cybersecurity, is far from a dead-end job. The field is dynamic, constantly evolving with new technologies and attack vectors, providing ample opportunities for growth and specialization. This means that a career in pen testing isn’t just about breaking into systems; it’s about continuously learning and adapting to the ever-changing threat landscape.The beauty of a penetration testing career lies in its diverse specialization options.
As you gain experience, you can focus on specific areas that align with your interests and skills, leading to higher earning potential and increased job satisfaction. This section explores potential career paths and specializations, along with illustrating possible career progressions.
Specializations within Penetration Testing
Penetration testing isn’t a monolithic field. Instead, it branches into various specializations, each requiring a unique skillset and knowledge base. These specializations allow professionals to develop expertise in specific areas, increasing their value in the job market.
So, you’re thinking about a cybersecurity career in pen testing post-COVID? It’s a hot field, but you need the right skills. Interestingly, understanding application development, especially the evolving landscape described in this article on domino app dev the low code and pro code future , can actually give you a significant edge. Knowing how apps are built helps you find vulnerabilities, making you a more effective pen tester.
Ultimately, a strong foundation in both security and development is key to success in this field.
- Web Application Security: This specialization focuses on identifying vulnerabilities in web applications, encompassing everything from SQL injection and cross-site scripting (XSS) to authentication flaws and insecure session management. Professionals in this area need a strong understanding of web technologies, programming languages (like Python, JavaScript), and OWASP Top 10 vulnerabilities.
- Mobile Application Security: With the proliferation of mobile devices, securing mobile applications has become paramount. This specialization requires expertise in mobile operating systems (Android and iOS), reverse engineering techniques, and understanding the unique vulnerabilities present in mobile apps.
- Cloud Security: As more organizations migrate to cloud platforms, the demand for cloud security experts has skyrocketed. This specialization involves assessing the security posture of cloud environments, including Infrastructure as a Code (IaC) security, configuration management, and identifying vulnerabilities within cloud services like AWS, Azure, and GCP.
- Network Security Penetration Testing: This traditional area focuses on identifying vulnerabilities within network infrastructure, including routers, switches, firewalls, and servers. It requires a strong understanding of networking protocols, TCP/IP, and common network attacks.
- Red Teaming: Red teaming goes beyond traditional penetration testing, simulating real-world attacks against an organization’s entire security posture. It requires advanced skills in social engineering, malware development, and advanced persistent threat (APT) simulations. Red teamers often work closely with blue teams (defensive security teams) to enhance overall security.
Career Progression Flowchart
The following describes a potential career progression path, represented visually as a flowchart. Note that this is just one possible path; many other routes are equally valid.Imagine a flowchart with the following stages:* Entry Level Penetration Tester: This is the starting point, requiring foundational knowledge and certification (like CompTIA Security+ or Certified Ethical Hacker (CEH)).
Specialized Penetration Tester
After gaining experience, testers often specialize (e.g., Web App Security, Cloud Security). This stage might involve obtaining vendor-specific certifications (e.g., AWS Certified Security – Specialty).
Senior Penetration Tester/Team Lead
With more experience and proven skills, testers can lead teams, mentor junior testers, and manage projects.
Security Consultant/Manager
This involves a broader scope, advising clients on security strategies and managing security projects. Often requires strong communication and leadership skills.
Chief Information Security Officer (CISO)
This is a top-level executive position responsible for an organization’s overall security strategy. This requires extensive experience and leadership skills.
Advanced Penetration Testing Techniques and Methodologies
Advanced penetration testing often involves techniques beyond basic vulnerability scanning. These methods require a deeper understanding of systems and networks and often involve custom tools and scripts.
- Exploit Development: Creating custom exploits to leverage newly discovered vulnerabilities. This requires strong programming skills and a deep understanding of operating systems and software.
- Binary Analysis: Reverse engineering malware and applications to understand their functionality and identify vulnerabilities. This often involves using tools like IDA Pro and Ghidra.
- Social Engineering Attacks: Advanced social engineering techniques involve manipulating individuals to gain access to sensitive information or systems. This requires psychological understanding and exceptional interpersonal skills.
- Advanced Persistent Threat (APT) Simulation: Simulating sophisticated, long-term attacks to test an organization’s ability to detect and respond to advanced threats. This requires a high level of expertise in various attack vectors and techniques.
Maintaining Skills and Keeping Up-to-Date
The cybersecurity landscape is in constant flux. New threats emerge daily, tools and techniques are constantly refined, and the regulatory environment evolves. To remain competitive and relevant as a penetration tester, continuous learning and professional development are not just beneficial—they’re essential for long-term success. Stagnation in this field can quickly lead to obsolescence.Continuous learning ensures you remain proficient in the latest tools and techniques, allowing you to effectively identify and exploit vulnerabilities.
It also helps you stay ahead of the curve, adapting to emerging threats and developing innovative solutions. This proactive approach to skill development not only enhances your technical abilities but also boosts your marketability and career progression.
Resources for Staying Current, A guide to building a cybersecurity career in pen testing post covid
Staying abreast of the latest threats, tools, and techniques requires a multi-faceted approach. Relying on a single source is insufficient; a combination of resources is crucial for a comprehensive understanding.
Several reputable online platforms offer valuable resources. Websites like SANS Institute, Cybrary, and OWASP provide extensive training courses, webinars, and research papers covering a wide range of cybersecurity topics. These resources often feature hands-on labs and exercises, allowing you to practice your skills in a safe and controlled environment. Furthermore, subscribing to security newsletters and following industry influencers on social media platforms like Twitter and LinkedIn provides a constant stream of up-to-date information and insights.
Benefits of Professional Organizations and Conferences
Joining professional organizations like (ISC)² or ISACA offers several advantages. Membership provides access to exclusive resources, such as training materials, certifications, and networking opportunities. These organizations often host conferences and workshops where you can learn from leading experts, network with peers, and stay informed about the latest trends. Attending industry conferences such as Black Hat, DEF CON, and RSA Conference offers invaluable opportunities to learn about the newest threats and techniques directly from researchers and practitioners.
Networking with professionals at these events can lead to valuable mentorship opportunities and potential job prospects. The insights gained from these conferences are often far more insightful and practical than those obtained from online resources alone, offering a direct line to the cutting edge of the field.
Ultimate Conclusion
Breaking into the world of penetration testing post-COVID requires dedication, skill, and a proactive approach. By mastering the technical skills, developing a strong portfolio, understanding the ethical implications, and consistently updating your knowledge, you can successfully navigate this exciting career path. This guide provides a roadmap; your ambition and perseverance will determine your destination. Remember, the cybersecurity landscape is constantly evolving, so continuous learning is key to long-term success.
Embrace the challenge, and you’ll find yourself in a rewarding and impactful career helping organizations secure their digital assets in an increasingly vulnerable world.
FAQ Corner: A Guide To Building A Cybersecurity Career In Pen Testing Post Covid
What’s the average salary for a penetration tester?
Salaries vary widely based on experience, location, and certifications. Expect a competitive salary, generally above average for tech roles.
How long does it take to become a penetration tester?
It depends on your background and learning style. Bootcamps might take a few months, while self-study could take longer. Consistent effort is key.
Is a college degree necessary?
No, a degree isn’t always mandatory, but relevant experience and certifications are crucial. Many successful pen testers are self-taught.
What if I don’t have any prior experience?
Start with Capture The Flag (CTF) competitions to build skills and showcase your abilities in a portfolio. Volunteer work or personal projects can also help.