
A New Age of Threats in Online Shopping Cybersecurity Tips
A new age of threats in online shopping cybersecurity tips is crucial now more than ever! Online shopping has become an undeniable part of our lives, but with this convenience comes a growing number of sophisticated cyber threats. From cleverly disguised phishing scams to devastating data breaches, the digital landscape is a minefield for unsuspecting shoppers. This post dives into the evolving threats, exploring how technology is both the cause and the potential solution to keeping your online transactions safe.
We’ll unpack the latest tactics used by cybercriminals, examining everything from the increasingly realistic phishing emails that bypass even the most cautious eyes to the vulnerabilities lurking within popular e-commerce platforms. We’ll also delve into the importance of strong passwords, the benefits of multi-factor authentication, and the necessity of keeping your software updated. This isn’t just about protecting your credit card; it’s about safeguarding your personal information and peace of mind.
Evolving Online Shopping Threats
Online shopping has become an integral part of modern life, offering unparalleled convenience and choice. However, this convenience comes at a cost: a constantly evolving landscape of security threats that target both shoppers and retailers. The traditional risks, such as phishing and malware, persist, but are now augmented by sophisticated attacks leveraging advancements in artificial intelligence and the Internet of Things (IoT).
Understanding these evolving threats is crucial for navigating the digital marketplace safely.
The digital shopping experience is no longer confined to desktop computers. The proliferation of mobile devices and smart home technologies has expanded the attack surface significantly. Traditional threats, like phishing emails designed to steal login credentials, are still prevalent. However, these scams are becoming increasingly sophisticated, incorporating AI-powered personalization and exploiting vulnerabilities in less secure mobile apps and IoT devices used for online transactions.
Comparison of Traditional and Emerging Online Shopping Security Risks
Traditional online shopping security risks primarily focused on protecting user credentials and financial information through secure websites and payment gateways. These methods, while still important, are insufficient against the newer threats. AI-powered attacks can automate phishing campaigns at scale, creating highly personalized and convincing lures. IoT devices, while offering convenience, can introduce vulnerabilities if not properly secured, potentially allowing hackers to access network information and even manipulate smart home systems to compromise online shopping activities.
For example, a compromised smart speaker could potentially intercept voice commands used for online purchases. The increasing use of biometric authentication, while enhancing security in some ways, also introduces new vulnerabilities if the biometric data itself is compromised.
The Impact of Social Engineering on Online Shoppers
Social engineering remains a highly effective attack vector. Scammers are increasingly leveraging social media, messaging apps, and even fake online reviews to build trust and manipulate shoppers into revealing sensitive information or making fraudulent purchases. These scams often involve creating a sense of urgency or exploiting emotional vulnerabilities. For example, a scammer might impersonate a customer service representative to obtain credit card details under the guise of resolving a payment issue.
The sophistication of these tactics is constantly increasing, making them difficult to detect for even the most tech-savvy users.
Top Five Prevalent Online Shopping Security Threats
The following table highlights five of the most prevalent online shopping security threats currently impacting consumers. Understanding these threats is the first step towards mitigating the risks.
| Threat | Description | Impact | Mitigation |
|---|---|---|---|
| Phishing | Deceptive emails or websites designed to steal login credentials or financial information. | Identity theft, financial loss. | Verify website legitimacy, avoid suspicious links, use strong passwords. |
| Malware | Malicious software that can steal data, monitor activity, or disrupt systems. | Data breaches, financial loss, system damage. | Install reputable antivirus software, update software regularly. |
| Man-in-the-Middle Attacks | Interception of communication between the shopper and the website. | Stolen credentials, financial loss. | Use secure Wi-Fi networks, look for HTTPS. |
| Fake Websites | Websites designed to mimic legitimate online stores to steal information. | Identity theft, financial loss. | Verify website legitimacy, check for secure connections (HTTPS). |
| Social Engineering Scams | Manipulative tactics to trick users into revealing sensitive information. | Identity theft, financial loss. | Be wary of unsolicited contacts, verify information independently. |
Phishing and Social Engineering Attacks
The digital landscape of online shopping has become a prime target for sophisticated phishing and social engineering attacks. These attacks leverage increasingly advanced techniques to deceive unsuspecting consumers and steal their personal and financial information. Understanding the methods employed by these attackers is crucial for protecting yourself in the ever-evolving world of e-commerce.Modern phishing attempts are far more convincing than their predecessors.
Attackers no longer rely on crudely crafted emails with obvious grammatical errors. Instead, they employ highly personalized messages, often mimicking legitimate websites and brands with remarkable accuracy. This level of sophistication makes it incredibly difficult for even tech-savvy individuals to distinguish between genuine and fraudulent communications. The attackers invest significant resources in creating realistic-looking websites, emails, and even SMS messages, making their attacks increasingly effective.
Examples of Real-World Phishing Attacks Targeting E-commerce
Phishing attacks against e-commerce platforms and payment gateways are constantly evolving. One common tactic involves creating fake websites that closely resemble popular online stores like Amazon or eBay. These sites often include convincing logos, product listings, and even customer reviews, designed to lure unsuspecting shoppers. Once a user enters their credentials, the attacker gains access to their account and potentially their payment information.
Another example involves phishing emails that appear to be from a shipping company, requesting users to update their delivery address or payment details by clicking on a malicious link. These emails often contain tracking numbers and other details that seem legitimate, adding to their credibility. There have also been instances where attackers compromised legitimate email accounts and sent phishing emails from compromised addresses, making it harder for recipients to detect the fraud.
Techniques Used to Bypass Multi-Factor Authentication (MFA)
While multi-factor authentication (MFA) provides a significant layer of security, determined attackers are constantly finding ways to circumvent it. One common method involves using social engineering tactics to trick users into revealing their one-time passwords (OTPs) or other authentication codes. This might involve a phone call pretending to be from the bank or online store, claiming there’s a problem with the account and requesting the OTP for verification.
Another technique focuses on exploiting vulnerabilities in the MFA system itself, such as using compromised or stolen credentials to access the user’s account. Additionally, attackers may target weaker MFA methods, such as SMS-based authentication, which can be susceptible to SIM swapping attacks. Advanced persistent threats (APTs) might even involve malware that silently intercepts and steals OTPs before the user even sees them.
Lifecycle of a Typical Phishing Attack
Imagine a visual representation: a flowchart starting with the attacker crafting a convincing phishing email or creating a fake website. This is followed by the attacker sending the email or directing traffic to the fake website. The next stage shows the unsuspecting user receiving the communication and clicking the malicious link. The user is then redirected to a fake login page or website, where they enter their credentials.
The attacker then captures these credentials and proceeds to access the user’s online shopping account. Finally, the attacker can then access financial information or make unauthorized purchases. This whole process, from initial contact to unauthorized access, can happen very quickly.
Data Breaches and Privacy Violations
The digital age has brought unprecedented convenience to online shopping, but it’s also ushered in a new era of security risks. Data breaches, the unauthorized access and disclosure of sensitive customer information, are a significant threat to both e-commerce businesses and their customers. Understanding the vulnerabilities, implementing robust security measures, and educating consumers about responsible online behavior are crucial steps in mitigating these risks.E-commerce platforms, despite their security measures, are vulnerable to various attacks.
Weak passwords, outdated software, insecure payment gateways, and insufficient employee training are all potential entry points for malicious actors. Furthermore, third-party integrations, often used for features like shipping and payment processing, can introduce additional vulnerabilities if not properly vetted and secured. A single point of weakness can compromise an entire system, leading to the exposure of vast amounts of personal data, including names, addresses, credit card details, and even medical information.
Vulnerabilities in E-commerce Platforms Leading to Data Breaches
Several factors contribute to data breaches in e-commerce. Poorly configured databases, lacking encryption or proper access controls, are prime targets. SQL injection attacks, where malicious code is injected into database queries, can grant unauthorized access to sensitive information. Cross-site scripting (XSS) vulnerabilities allow attackers to inject malicious scripts into websites, potentially stealing cookies and session IDs. Unpatched software and outdated security protocols leave systems vulnerable to known exploits.
Finally, human error, such as phishing scams targeting employees with access to sensitive data, can be a significant contributing factor.
Best Practices for Mitigating Data Breach Risk
E-commerce businesses must adopt a multi-layered approach to security. This includes regularly updating software and security patches, implementing robust access controls and authentication mechanisms (such as multi-factor authentication), and encrypting sensitive data both in transit and at rest. Regular security audits and penetration testing can identify and address vulnerabilities before they are exploited. Employee training programs focused on cybersecurity awareness and phishing prevention are also critical.
Furthermore, choosing reputable and secure third-party vendors and regularly reviewing their security practices is essential. Finally, having a comprehensive incident response plan in place is crucial to minimize the damage in the event of a breach.
Legal and Ethical Implications of Data Breaches
Data breaches carry significant legal and ethical consequences. Businesses face potential fines and lawsuits under regulations like the GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act). Reputational damage can also be devastating, leading to loss of customer trust and business. Ethically, businesses have a responsibility to protect the personal information entrusted to them. Failing to do so is a breach of trust and can have severe consequences for consumers, including identity theft, financial loss, and emotional distress.
Consumers, too, have ethical responsibilities in protecting their own data, such as using strong passwords and being cautious about phishing attempts.
Steps Consumers Can Take to Protect Personal Information During Online Shopping
Protecting personal information during online shopping requires vigilance and proactive measures.
It’s crucial to be aware of the risks and take appropriate precautions. Here are some key steps consumers can take:
- Use strong, unique passwords for each online account.
- Enable two-factor authentication whenever possible.
- Shop only on secure websites (look for “https” in the URL).
- Be wary of suspicious emails and links; avoid clicking on them.
- Use a credit card or virtual credit card for online purchases rather than debit cards.
- Monitor your bank and credit card statements regularly for unauthorized activity.
- Be cautious about sharing personal information on social media.
- Regularly review your privacy settings on all online accounts.
- Consider using a reputable VPN for added security when shopping online.
Malware and Ransomware Attacks
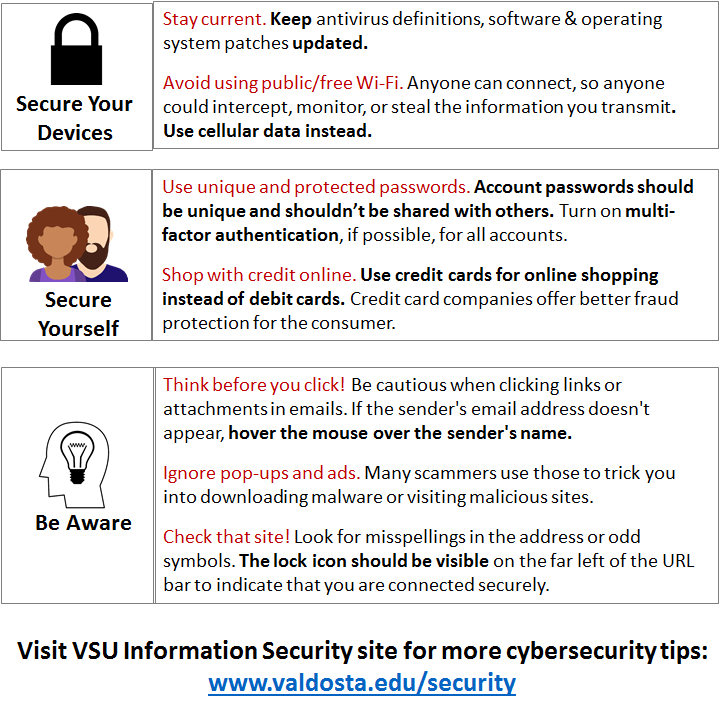
Online shopping, while incredibly convenient, exposes us to a range of cyber threats. Malware and ransomware are particularly insidious, capable of stealing financial information, hijacking accounts, and crippling devices, all while you’re trying to snag that perfect pair of shoes or that must-have gadget. Understanding these threats and how to protect yourself is crucial for safe online shopping.Malware and ransomware attacks can compromise online shopping transactions in several ways.
Malware can secretly record keystrokes (keyloggers), capturing login credentials and credit card details as you enter them. Ransomware can encrypt your entire system, holding your data hostage until a ransom is paid, potentially including sensitive information related to your online purchases. This can lead to identity theft, financial losses, and significant inconvenience. The impact extends beyond just the immediate transaction; compromised systems can be used to launch further attacks or spread malware to other devices.
Types of Malware and Ransomware Targeting Online Shoppers
Various types of malware and ransomware pose threats to online shoppers. Some examples include trojans, which disguise themselves as legitimate software, often downloaded through seemingly harmless links or attachments. Spyware monitors your online activity, collecting data like browsing history and login details. Adware bombards you with unwanted advertisements, potentially leading you to malicious websites. Ransomware, as mentioned earlier, encrypts your files and demands a ransom for their release.
Each type presents a unique risk, impacting the security of your online transactions in different ways. For instance, a keylogger will directly steal your credentials, while ransomware renders your system unusable, preventing you from accessing your online accounts or purchased items.
Identifying and Removing Malware
Identifying and removing malware requires a multi-faceted approach. Firstly, be vigilant about suspicious activity. This includes unexpected pop-ups, slow system performance, unusual browser behavior, and unexplained charges on your credit card statements. Secondly, run a full system scan with a reputable anti-malware program. Ensure your antivirus software is up-to-date and regularly scan your system for threats.
Thirdly, if malware is detected, follow the instructions provided by your anti-malware software to remove it. This often involves quarantining or deleting the malicious files. If you’re unable to remove the malware yourself, consider seeking professional help from a cybersecurity expert. Remember to always back up your important data regularly to mitigate the impact of a ransomware attack.
Malware Types and Their Impact on Online Shopping Security
| Malware Type | Description | Impact on Online Shopping | Example |
|---|---|---|---|
| Keylogger | Records keystrokes, capturing login credentials and payment information. | Direct theft of sensitive data during online transactions. | A user unknowingly installs a keylogger while downloading a cracked software. Their banking details are subsequently stolen. |
| Trojan | Disguises itself as legitimate software, often used to install other malware. | Installation of additional malware that can compromise online transactions. | A user clicks a link in a phishing email, downloading a trojan that installs ransomware. |
| Spyware | Monitors online activity, collecting browsing history, login details, and other personal information. | Potential theft of sensitive data and tracking of online shopping behavior. | A user visits a compromised website, unknowingly installing spyware that tracks their online purchases. |
| Ransomware | Encrypts files and demands a ransom for their release. | Loss of access to important files, including purchase confirmations and digital receipts. Potential financial loss due to ransom payment. | A user’s system is encrypted by ransomware after clicking a malicious link in an online advertisement. |
Payment Security and Fraud: A New Age Of Threats In Online Shopping Cybersecurity Tips

Online shopping offers unparalleled convenience, but this ease comes with inherent risks. Protecting your financial information during online transactions is paramount, and understanding the vulnerabilities of different payment methods, as well as the security measures employed by businesses and innovative technologies, is crucial for safe online shopping.Payment security hinges on multiple layers of protection, from the methods we use to pay to the systems in place to detect and prevent fraud.
The vulnerabilities vary greatly depending on the chosen payment method and the security practices of both the merchant and the payment processor.
Vulnerabilities of Different Payment Methods
Credit cards, while widely used, are susceptible to data breaches if a retailer’s systems are compromised. Stolen credit card information can be used for unauthorized purchases. Digital wallets, while often perceived as more secure due to tokenization (replacing actual card numbers with unique identifiers), still rely on the security of the wallet provider and can be vulnerable to phishing attacks targeting user credentials.
Direct bank transfers, while seemingly secure, can be vulnerable to scams where fraudulent websites mimic legitimate payment gateways. Each method presents unique challenges and vulnerabilities requiring different security considerations.
Robust Payment Security Measures for Businesses
Businesses must implement robust security measures to protect customer financial data. This includes using secure sockets layer (SSL) certificates to encrypt data transmitted between the customer’s browser and the merchant’s server. PCI DSS (Payment Card Industry Data Security Standard) compliance is essential for businesses handling credit card information, ensuring they adhere to strict security guidelines. Regular security audits and penetration testing help identify vulnerabilities before malicious actors can exploit them.
Employing multi-factor authentication (MFA) adds an extra layer of security, requiring more than just a password to access accounts. Furthermore, data encryption at rest and in transit protects sensitive information even if a breach occurs.
The Role of Fraud Detection Systems
Fraud detection systems are critical in preventing fraudulent transactions. These systems use algorithms and machine learning to analyze transaction data in real-time, identifying patterns and anomalies indicative of fraudulent activity. Factors such as unusual purchase amounts, locations, or patterns of activity are flagged for review. Real-time monitoring and analysis of transactions allows for immediate blocking of suspicious activity, minimizing losses.
Sophisticated systems can also learn from past fraudulent attempts, adapting and improving their ability to detect new types of fraud.
Innovative Technologies Enhancing Payment Security
Biometric authentication, using fingerprints, facial recognition, or voice recognition, adds another layer of security beyond passwords. Blockchain technology offers potential for secure and transparent transactions, recording transactions immutably on a distributed ledger. Tokenization replaces sensitive data with non-sensitive substitutes, reducing the impact of a data breach. Advanced encryption techniques, such as homomorphic encryption, allow computations to be performed on encrypted data without decryption, further enhancing security.
These technologies represent the forefront of payment security, constantly evolving to combat emerging threats.
Cybersecurity Tips for Online Shoppers

Online shopping offers incredible convenience, but it also exposes us to a range of cyber threats. Protecting yourself requires vigilance and proactive measures. This guide Artikels practical steps to ensure your online shopping experience remains safe and secure. Remember, a little precaution can go a long way in preventing significant problems.
Strong Passwords and Password Management
Creating strong, unique passwords for each online account is crucial. Weak passwords are easily guessed or cracked, leaving your accounts vulnerable. A strong password is typically at least 12 characters long, combines uppercase and lowercase letters, numbers, and symbols, and avoids easily guessable information like names or birthdays. For example, “P@$$wOrd123!” is stronger than “password1”. Using a password manager is highly recommended.
These tools generate strong, unique passwords for each site and securely store them, eliminating the need to remember countless complex passwords. Popular password managers include LastPass, 1Password, and Bitwarden.
Software Updates and Antivirus Protection, A new age of threats in online shopping cybersecurity tips
Regularly updating your operating system, web browser, and other software is essential. Updates often include security patches that fix vulnerabilities hackers can exploit. Think of it as patching holes in your digital defenses. Similarly, using reputable antivirus software provides real-time protection against malware and other threats. Ensure your antivirus software is always active and up-to-date, regularly scanning your system for threats.
Popular options include Norton, McAfee, and Bitdefender. Remember to choose a reputable provider with a good track record.
Before, During, and After Online Purchase Checklist
Before making a purchase, verify the website’s legitimacy. Look for secure connections (HTTPS) indicated by a padlock icon in the browser address bar. Check online reviews and ensure the site is reputable before entering any personal information. During the purchase, pay close attention to the checkout process. Be wary of unexpected pop-ups or redirects.
Online shopping’s booming, but so are the scams! We’re facing a new age of sophisticated phishing and malware attacks targeting unsuspecting shoppers. Building robust security systems is crucial, and that’s where the power of efficient development comes in; check out this article on domino app dev, the low-code and pro-code future , to see how faster development cycles can help create better security solutions.
Ultimately, staying ahead of these threats requires innovation in both security and development practices.
After completing your purchase, review your transaction history and bank statements for any unauthorized charges. Change your passwords if you suspect any compromise.
- Before Purchase: Verify website legitimacy (HTTPS), check reviews, and only use trusted payment methods.
- During Purchase: Pay close attention to the checkout process, avoid suspicious links or pop-ups, and double-check billing information.
- After Purchase: Review transaction history and bank statements, change passwords if necessary, and keep records of your purchase.
Final Review
Navigating the digital world of online shopping requires vigilance and awareness. While the threats are constantly evolving, so are the tools and techniques to protect yourself. By understanding the risks and implementing the cybersecurity tips Artikeld above, you can significantly reduce your vulnerability to online shopping scams and data breaches. Remember, staying informed and proactive is your best defense in this ever-changing online landscape.
Stay safe, and happy shopping!
FAQ Corner
What is multi-factor authentication (MFA), and why is it important?
MFA adds an extra layer of security beyond just a password. It typically involves verifying your identity through a second method, such as a code sent to your phone or email, a biometric scan, or a security key. This makes it significantly harder for hackers to access your accounts, even if they obtain your password.
How can I spot a phishing email?
Look for suspicious email addresses, grammatical errors, urgent or threatening language, requests for personal information, and unusual links. Hover over links without clicking to see the actual URL – it might be different from what’s displayed.
What should I do if I think my account has been compromised?
Immediately change your passwords, contact the relevant websites or banks to report the breach, and monitor your accounts for suspicious activity. Consider freezing your credit to prevent fraudulent transactions.





