
A New Tactic to Combat Cyber Warfare Diversity
A new tactic to combat cyber warfare diversity as digital defense cyberwarrior – A new tactic to combat cyber warfare diversity as digital defense cyberwarrior – that’s the exciting challenge we’re tackling today! The digital battlefield is a chaotic mess, a constantly shifting landscape of state-sponsored attacks, organized crime, and hacktivist groups. It’s not just about firewalls and antivirus anymore; it’s about understanding the
-why* behind the attacks, the motivations of the attackers, and leveraging that knowledge to build truly effective defenses.
We’ll dive into innovative strategies, the crucial role of the modern cyber defense professional, and how embracing diversity is key to winning this ever-evolving war.
This isn’t your grandpappy’s cybersecurity. We’re talking about proactive, adaptable defenses that anticipate the next threat, not just react to the last one. We need a new breed of cyber warrior – one that’s not just technically skilled, but also culturally aware, ethically sound, and ready to learn and adapt constantly. This post explores exactly how we build that defense, and what the future holds for this crucial battleground.
Defining Cyber Warfare Diversity
The digital battlefield is far from monolithic. Modern cyber warfare isn’t a simple clash between two armies; it’s a chaotic maelstrom of diverse actors, motivations, and attack methods, creating a constantly shifting landscape of threats. Understanding this diversity is crucial for developing effective defenses, as a one-size-fits-all approach is hopelessly inadequate. This complexity demands a nuanced understanding of the various players and their tactics to build truly resilient systems.The evolving nature of cyber threats presents a significant challenge to traditional security models.
The landscape is no longer dominated solely by nation-state actors. Instead, we see a complex interplay of state-sponsored groups, sophisticated criminal enterprises, and ideologically driven hacktivists, each with their own resources, capabilities, and objectives. This diverse range of actors employs a wide array of techniques, from highly targeted spear-phishing campaigns to large-scale distributed denial-of-service (DDoS) attacks, making comprehensive defense incredibly difficult.
The Multifaceted Nature of Cyber Warfare Actors, A new tactic to combat cyber warfare diversity as digital defense cyberwarrior
The actors involved in cyber warfare represent a spectrum of capabilities and motivations. State-sponsored actors, often backed by significant resources and advanced technology, may conduct espionage, sabotage critical infrastructure, or spread disinformation. Criminal enterprises, driven by financial gain, focus on data breaches, ransomware attacks, and the theft of intellectual property. Hacktivist groups, motivated by political or social agendas, may target organizations they perceive as unjust or harmful, often using disruptive tactics to raise awareness or inflict damage.
The motivations and capabilities of these actors vary significantly, demanding a tailored defensive approach for each threat type. For example, a defense against a state-sponsored APT (Advanced Persistent Threat) will differ vastly from a defense against a financially motivated ransomware attack.
Evolving Cyber Threat Vectors
The methods used to launch cyberattacks are constantly evolving, making it challenging to predict and defend against future threats. New vulnerabilities are constantly discovered, and attackers are continuously developing sophisticated techniques to exploit them. This includes the increasing use of artificial intelligence and machine learning by both attackers and defenders, creating an ongoing arms race. The rise of IoT (Internet of Things) devices also expands the attack surface, providing numerous potential entry points for malicious actors.
For instance, the exploitation of vulnerabilities in industrial control systems (ICS) can have catastrophic real-world consequences, as seen in past attacks on power grids and other critical infrastructure. The use of zero-day exploits, vulnerabilities unknown to the defender, further complicates the challenge.
Impact of Diversity on Defensive Strategies
The diversity of cyber warfare significantly impacts the development of effective defensive strategies. A single security solution is unlikely to be sufficient to address the wide range of threats. Instead, a layered approach is necessary, combining various security tools and techniques to create a robust defense-in-depth strategy. This requires a comprehensive understanding of the threat landscape, proactive threat hunting, and the ability to rapidly adapt to new and evolving threats.
Furthermore, effective collaboration and information sharing between organizations and governments are crucial to combating cyber threats effectively. The constant evolution of attack techniques demands continuous monitoring, adaptation, and improvement of defensive measures. Failure to adapt to this diverse threat landscape leaves organizations vulnerable to significant damage and disruption.
The Concept of the “Digital Defense Cyberwarrior”: A New Tactic To Combat Cyber Warfare Diversity As Digital Defense Cyberwarrior
The term “Digital Defense Cyberwarrior” evokes images of elite hackers battling sophisticated threats in the digital realm. While the imagery is dramatic, the reality is far more nuanced. It’s about highly skilled professionals possessing a unique blend of technical expertise, strategic thinking, and ethical awareness, constantly adapting to the ever-evolving landscape of cyber warfare. This isn’t about lone wolves; it’s about collaborative teams working together to protect critical infrastructure and data.The modern cyber defense professional needs a diverse skill set, going far beyond simple coding proficiency.
This necessitates a multifaceted approach to training and continuous professional development. The following table Artikels the key skill categories, specific skills, expertise levels, and practical applications for a successful Digital Defense Cyberwarrior.
Required Skills and Attributes of a Digital Defense Cyberwarrior
| Skill Category | Specific Skill | Required Expertise Level | Example Application |
|---|---|---|---|
| Technical Skills | Network Security | Advanced | Analyzing network traffic for malicious activity, implementing intrusion detection systems, and responding to network breaches. |
| Technical Skills | Security Auditing | Intermediate | Conducting regular vulnerability assessments and penetration testing to identify and mitigate security weaknesses. |
| Technical Skills | Programming/Scripting | Advanced | Developing custom security tools, automating security tasks, and analyzing malware samples. |
| Technical Skills | Cloud Security | Intermediate | Securing cloud-based infrastructure and applications, implementing cloud security controls, and responding to cloud-based security incidents. |
| Analytical Skills | Incident Response | Advanced | Investigating security incidents, containing threats, and recovering systems after a breach. |
| Analytical Skills | Threat Intelligence | Intermediate | Gathering and analyzing information about emerging cyber threats to proactively mitigate risks. |
| Analytical Skills | Data Analysis | Intermediate | Analyzing security logs and other data sources to identify patterns and anomalies indicative of malicious activity. |
| Soft Skills | Communication | Advanced | Clearly communicating technical information to both technical and non-technical audiences. |
| Soft Skills | Teamwork | Advanced | Collaborating effectively with other security professionals to address complex security challenges. |
| Soft Skills | Problem-Solving | Advanced | Quickly and effectively identifying and resolving complex security issues under pressure. |
Adaptability and Continuous Learning
The cyber threat landscape is constantly evolving. New vulnerabilities are discovered daily, and attackers are constantly developing new techniques. Therefore, adaptability and continuous learning are not merely desirable traits for a Digital Defense Cyberwarrior; they are essential for survival. Staying abreast of the latest threats, technologies, and best practices requires consistent engagement with industry news, participation in training programs, and active involvement in professional communities.
For example, the rise of AI-powered attacks necessitates a deeper understanding of machine learning and its application in both offensive and defensive cybersecurity. Similarly, the increasing reliance on cloud computing requires specialized knowledge of cloud security architectures and best practices.
Ethical Considerations
Digital Defense Cyberwarriors face complex ethical dilemmas. The line between defense and offense can be blurred, particularly when dealing with sophisticated adversaries. Ethical considerations must be at the forefront of every decision, ensuring that actions are legal, proportionate, and necessary. For instance, the use of offensive techniques, even in a defensive context, requires careful consideration of potential unintended consequences.
Maintaining strict adherence to legal and ethical frameworks, such as those Artikeld in national and international laws governing cybersecurity, is paramount. Transparency and accountability are also crucial, ensuring that actions are documented and justified.
Exploring Novel Defensive Tactics
The increasing sophistication and diversity of cyber warfare necessitate a move beyond traditional cybersecurity measures. We need innovative approaches that can adapt to the ever-evolving threat landscape. This section explores three novel defensive tactics designed to combat the multifaceted nature of modern cyberattacks, focusing on their mechanisms, potential impact, and comparison to existing strategies.
Traditional cybersecurity often relies on reactive measures like firewalls and antivirus software. While crucial, these are often insufficient against highly targeted, sophisticated attacks that exploit zero-day vulnerabilities or leverage the human element. The tactics presented here aim for a more proactive and adaptive defense.
AI-Driven Threat Hunting and Response
This approach utilizes advanced artificial intelligence and machine learning algorithms to proactively hunt for and respond to threats. Unlike traditional signature-based detection, AI-driven systems can identify anomalies and suspicious patterns in network traffic and system behavior, even if they haven’t been encountered before. This allows for the early detection of advanced persistent threats (APTs) and other sophisticated attacks.
The system would continuously learn and adapt, improving its accuracy and effectiveness over time. For example, an AI system could analyze network logs to detect unusual communication patterns indicative of data exfiltration, even if the malicious code itself is obfuscated or unknown. Compared to traditional methods, this approach offers faster response times and a greater ability to detect novel attacks.
However, it requires significant computational resources and expertise to develop and maintain. A disadvantage is the potential for false positives, requiring careful tuning and human oversight.
Decentralized Defense Architecture
This tactic shifts from a centralized security model to a decentralized one, distributing security functions across multiple nodes and systems. This makes the system more resilient to attacks because compromising one node doesn’t necessarily compromise the entire network. Imagine a network where each device has its own local security agent that can autonomously detect and respond to threats.
Building a diverse digital defense requires creative new tactics to combat cyber warfare. One promising avenue is leveraging rapid application development; check out this article on domino app dev, the low code and pro code future , to see how streamlined development can accelerate the creation of crucial security tools. This faster development cycle allows for quicker response times to emerging threats, a key element in a diverse and agile cyber defense strategy.
These agents communicate with each other to share information and coordinate their actions, creating a robust, self-healing system. Compared to traditional centralized architectures, this approach offers increased resilience and reduced single points of failure. However, managing and coordinating a decentralized system can be complex, and ensuring consistent security policies across all nodes requires careful planning and implementation.
Behavioral Biometrics for Authentication
This approach goes beyond traditional password-based authentication by incorporating behavioral biometrics. This involves analyzing user behavior patterns such as typing rhythm, mouse movements, and scrolling habits to verify their identity. Combining this with multi-factor authentication creates a more robust defense against credential theft and phishing attacks. For example, if a user’s typing rhythm suddenly changes significantly, the system could flag this as suspicious activity and trigger an authentication challenge.
Compared to traditional methods, this offers stronger protection against credential compromise. However, implementing behavioral biometrics requires sophisticated algorithms and careful consideration of privacy concerns. The accuracy of behavioral biometrics can also be affected by factors such as stress or fatigue.
Scenario: AI-Driven Threat Hunting Against a Supply Chain Attack
Imagine a scenario where a sophisticated APT group is attempting a supply chain attack targeting a major software company. They have compromised a third-party vendor’s systems and introduced malicious code into a widely used software library. An AI-driven threat hunting system, constantly monitoring the company’s network and software repositories, detects unusual patterns in the library’s code, such as unexpected function calls or unusual network connections.
The system flags this as a potential threat and automatically quarantines the affected library, preventing its deployment and mitigating the potential impact of the attack. The AI system then analyzes the malicious code to identify the attack vector and the attackers’ infrastructure, allowing for proactive measures to be taken to secure other vulnerable systems.
Leveraging Diversity in Defense Strategies
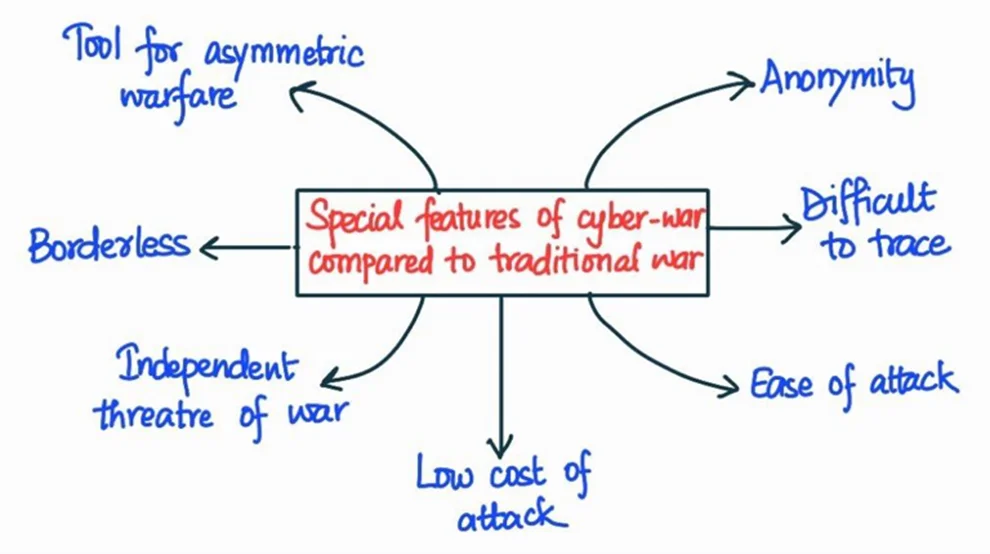
The fight against cyber warfare is a complex and ever-evolving battle. To effectively defend against increasingly sophisticated attacks, we must move beyond traditional approaches and embrace a more holistic strategy. A crucial component of this strategy is leveraging the power of diversity within our digital defense teams. By incorporating diverse perspectives – in terms of cultural background, technical expertise, and personal experiences – we can significantly enhance our ability to anticipate, detect, and respond to cyber threats.Building diverse cybersecurity teams isn’t just about meeting quotas; it’s about building a stronger, more resilient defense.
A homogenous team, while potentially efficient in a limited context, lacks the breadth of experience and perspective necessary to counter the wide range of attacks we face. A diverse team, however, brings together a wealth of knowledge and skills, leading to more robust and innovative solutions.
Benefits of Diverse Cybersecurity Teams
The advantages of a diverse cybersecurity team are numerous and impactful. A truly diverse team, encompassing a variety of backgrounds and skillsets, is better equipped to handle the complex challenges of modern cyber warfare. The benefits extend beyond simple problem-solving; they influence the entire team’s approach to cybersecurity, creating a more proactive and adaptable organization.
- Enhanced Problem-Solving: Diverse teams bring multiple viewpoints and approaches to problem-solving, leading to more creative and effective solutions. Different cultural backgrounds can offer unique perspectives on potential threats and vulnerabilities.
- Improved Threat Detection: A broader range of experiences allows for the identification of threats that might otherwise be missed. Individuals with backgrounds in different industries or geographical locations can bring unique insights into potential attack vectors.
- Increased Innovation: Diverse teams foster a more innovative environment, leading to the development of new and improved cybersecurity technologies and strategies. The cross-pollination of ideas leads to creative solutions and better adaptation to evolving threats.
- Better Communication and Collaboration: Teams with diverse communication styles and backgrounds are better equipped to communicate effectively with a wider range of stakeholders, including clients, partners, and government agencies.
- Stronger Reputation and Trust: Organizations known for their commitment to diversity and inclusion are often viewed as more trustworthy and reliable, attracting top talent and strengthening relationships with clients and partners.
Understanding Diverse Attacker Motivations and Tactics
Understanding the motivations and tactics of diverse cyber attackers is crucial for developing effective defenses. Cybercriminals come from various backgrounds, with diverse motivations ranging from financial gain to political activism or state-sponsored espionage. Their tactics also vary widely, reflecting their skills, resources, and objectives. By studying these differences, we can develop more targeted and effective defenses.For example, a financially motivated attacker might focus on exploiting vulnerabilities in financial systems, while a politically motivated attacker might target critical infrastructure or government agencies.
Understanding these differences allows us to prioritize our defenses and allocate resources more effectively. This involves not just technical analysis but also understanding the socio-political context surrounding cyberattacks. Analyzing the geopolitical landscape, for example, can reveal potential sources of state-sponsored attacks and help anticipate their strategies.
Examples of Successful Diversity-Driven Cybersecurity Initiatives
While specific examples of initiatives often involve confidential information, the general principle is demonstrably successful. Many organizations are now actively promoting diversity within their cybersecurity teams, recognizing the crucial role it plays in enhancing their defenses. The success of these initiatives isn’t always publicly documented due to security concerns, but the trend towards greater diversity in the field is undeniable.
The increased focus on diversity and inclusion within major tech companies and government agencies reflects a growing understanding of its importance in combating cyber threats. For instance, initiatives focusing on outreach programs to attract women and underrepresented minorities into the cybersecurity field demonstrate a commitment to building more diverse and effective teams. The measurable outcome, although not always publicly quantifiable due to security concerns, is a demonstrably more resilient and adaptable cybersecurity posture.
Future Trends and Challenges
The rapid evolution of cyber warfare, fueled by increasing technological sophistication and the expanding diversity of actors, presents a constantly shifting landscape for digital defense. Predicting the future is inherently challenging, but by analyzing current trends and emerging technologies, we can anticipate key challenges and opportunities for the digital defense cyberwarrior. Understanding these factors is crucial for developing proactive and adaptable defense strategies.The interconnected nature of modern systems and the increasing reliance on artificial intelligence (AI) magnify the potential impact of cyberattacks.
This complexity, combined with the ever-growing sophistication of adversarial tactics, necessitates a forward-looking approach to cybersecurity. Failing to adapt to these changes risks leaving critical infrastructure and national security vulnerable.
Significant Future Challenges Related to Cyber Warfare Diversity and Defense
Three significant future challenges are the rise of AI-driven attacks, the increasing sophistication of nation-state actors, and the blurring lines between cybercrime and state-sponsored operations. AI is rapidly changing the nature of cyberattacks, enabling automated, large-scale, and highly targeted campaigns that are difficult to detect and defend against. Nation-state actors are continuously developing more advanced cyber weapons and tactics, often leveraging zero-day exploits and advanced persistent threats (APTs).
The convergence of cybercrime and state-sponsored operations makes attribution difficult, hindering effective response and deterrence. For example, criminal groups might be unknowingly used as proxies by nation-states, creating a complex web of accountability and responsibility.
Potential Technological Advancements Reshaping the Cyber Defense Landscape
Several technological advancements hold the potential to reshape the cyber defense landscape. Quantum computing, while posing significant threats in terms of code-breaking, also offers opportunities for developing more robust cryptographic techniques and faster threat detection systems. Blockchain technology, known for its security and transparency, could be used to create immutable audit trails and enhance the security of critical infrastructure.
Advanced AI and machine learning algorithms can be employed for proactive threat detection, predictive analysis, and automated incident response, potentially outpacing the capabilities of attackers. For instance, AI-powered systems could analyze network traffic in real-time, identifying anomalies and potential threats before they escalate into full-blown attacks, mimicking the human expertise of a seasoned cyberwarrior but at a vastly increased scale and speed.
Vision for the Future of Digital Defense Cyberwarriors
The future digital defense cyberwarrior will be a highly skilled, adaptable professional, deeply versed in both offensive and defensive cybersecurity techniques. They will leverage advanced AI and machine learning tools to analyze vast amounts of data, anticipate threats, and automate responses. Collaboration and information sharing will be paramount, fostering a global network of cyber defense experts working together to counter evolving threats.
Imagine a team of cyberwarriors, seamlessly integrating human intuition with AI-powered predictive analytics, proactively neutralizing threats before they can even reach their targets. They operate within a globally interconnected network, sharing intelligence and resources in real-time, creating a formidable shield against the ever-evolving landscape of cyber warfare. These individuals will be not just technical experts, but also strategic thinkers, capable of understanding the geopolitical context of cyberattacks and developing effective countermeasures.
Final Wrap-Up

The fight against cyber warfare is far from over, but by embracing a diverse approach, fostering a culture of continuous learning, and implementing innovative defensive tactics, we can significantly strengthen our digital defenses. The future of digital defense cyberwarriors hinges on adaptability, ethical awareness, and a deep understanding of the ever-evolving threat landscape. It’s a challenging but ultimately rewarding mission, and one that requires a collective effort to secure our digital world.
Let’s build a stronger, more resilient future, together.
FAQs
What are some examples of “diverse” cyber attackers?
Diverse attackers include nation-state actors, organized crime syndicates, hacktivist groups, lone wolves, and even disgruntled insiders. Each has unique motivations and attack methods.
How does cultural diversity improve cybersecurity?
Different cultural perspectives bring varied problem-solving approaches and a wider understanding of potential vulnerabilities, leading to more robust defenses.
What are the ethical dilemmas faced by digital defense cyberwarriors?
Ethical dilemmas include balancing national security with individual privacy, the potential for unintended consequences of defensive actions, and the responsible use of offensive capabilities.
What technological advancements are most likely to impact cyber defense in the future?
AI and machine learning, quantum computing, and advancements in blockchain technology will all significantly reshape the cyber defense landscape.





