Zero Trust for Active Directory A Practical Guide
A practical guide to applying zero trust principles to active directory for microsoft on premises and hybrid environment protection – A practical guide to applying zero trust principles to Active Directory for Microsoft on-premises and hybrid environment protection is more than just a security upgrade; it’s a fundamental shift in how we think about access control. In today’s threat landscape, traditional perimeter-based security simply isn’t enough. This guide dives deep into the practical steps needed to implement a robust Zero Trust framework, securing your Active Directory whether it’s entirely on-premises, in the cloud, or a hybrid mix.
We’ll cover everything from securing your Active Directory controllers and implementing multi-factor authentication (MFA) to leveraging powerful Microsoft security tools like Azure AD and Microsoft Defender for Identity. Get ready to transform your security posture and embrace a future-proof approach to protecting your valuable data.
We’ll explore the core principles of Zero Trust, highlighting the vulnerabilities of traditional Active Directory setups and contrasting them with the more secure Zero Trust model. This isn’t just theoretical; we’ll provide actionable strategies for both on-premises and hybrid environments, including step-by-step instructions, flowcharts, and practical examples to help you implement these changes effectively. We’ll also tackle advanced threats and discuss the critical role of continuous monitoring and logging in maintaining a strong Zero Trust posture.
Introduction to Zero Trust and Active Directory
Zero Trust, a security model built on the principle of “never trust, always verify,” is increasingly crucial in today’s complex IT landscape. This paradigm shift from traditional perimeter-based security is particularly relevant when securing Active Directory (AD), the backbone of many organizations’ on-premises and hybrid environments. Understanding the core principles of Zero Trust and the vulnerabilities inherent in traditional AD deployments is the first step towards bolstering your organization’s security posture.
Core Principles of Zero Trust Security
Zero Trust operates on the fundamental assumption that no user or device should be implicitly trusted, regardless of location (inside or outside the network perimeter). Verification is required at every access attempt, based on multiple factors, including user identity, device posture, and context. This multi-layered approach significantly reduces the attack surface compared to traditional models that rely on broad network access grants.
Key principles include least privilege access, micro-segmentation of networks, continuous monitoring and threat detection, and strong authentication mechanisms.
Vulnerabilities of Traditional Active Directory Deployments
Traditional Active Directory deployments often rely on a “trust-but-verify” model, where users and devices within the network perimeter are granted relatively broad access. This approach leaves organizations vulnerable to several threats. A compromised domain controller, for instance, can grant attackers complete control over the entire directory, leading to data breaches, lateral movement, and ransomware attacks. Furthermore, weak or easily guessed passwords, coupled with inadequate multi-factor authentication (MFA), provide easy entry points for malicious actors.
The inherent trust placed on users and devices within the network also enables lateral movement, allowing attackers to move freely through the network once they gain a foothold. Finally, a lack of granular access control and insufficient monitoring creates blind spots, making it difficult to detect and respond to threats in a timely manner.
Comparison of Traditional and Zero Trust Security Models
Traditional security models rely on a castle-and-moat approach, protecting a network perimeter. Once inside, users and devices are generally trusted. This model is increasingly ineffective against sophisticated attacks that bypass perimeter defenses. Zero Trust, in contrast, assumes no implicit trust, regardless of location. Every access request is verified, and access is granted only based on a comprehensive assessment of identity, device posture, and context.
This granular approach significantly reduces the impact of a breach, limiting the lateral movement of attackers and protecting sensitive data.
Key Differences Between Traditional and Zero Trust Approaches to Active Directory Security
| Feature | Traditional Approach | Zero Trust Approach |
|---|---|---|
| Trust Model | Implicit trust within the network perimeter | Explicit verification of every access request |
| Access Control | Broad access grants based on group membership | Granular access control based on least privilege and context |
| Authentication | Often relies on passwords alone | Employs multi-factor authentication (MFA) and strong authentication methods |
| Monitoring | Limited monitoring and logging | Continuous monitoring and advanced threat detection |
Implementing Zero Trust in On-Premises Active Directory
Transitioning your on-premises Active Directory to a Zero Trust model requires a fundamental shift in how you approach security. Instead of assuming trust based on network location, Zero Trust verifies every user and device before granting access to resources, regardless of their location. This approach significantly reduces your attack surface and strengthens your overall security posture. This section Artikels key strategies for implementing Zero Trust principles within your existing Active Directory infrastructure.
Securing Active Directory Controllers
Protecting your Active Directory controllers is paramount. These servers are the heart of your domain, and compromising them grants attackers access to a wealth of sensitive information and control over your entire network. A multi-layered approach is essential. This includes deploying the latest security updates and patches, regularly auditing controller configurations, and implementing robust network segmentation to isolate them from less secure parts of your network.
Hardening the controllers themselves through restrictive firewall rules, disabling unnecessary services, and utilizing strong encryption are also critical. Regular vulnerability scans and penetration testing are also vital to proactively identify and mitigate potential weaknesses. Consider implementing read-only domain controllers (RODCs) in remote locations to reduce the attack surface of your primary DCs. These RODCs only hold a read-only copy of the directory, limiting the potential damage from a compromise.
Least Privilege Access Control
The principle of least privilege dictates that users and groups should only have the minimum necessary permissions to perform their job functions. Implementing this effectively within Active Directory involves carefully reviewing and refining user and group memberships. Regularly auditing group memberships, especially those with extensive permissions, is crucial to identify and remove unnecessary access rights. Employing granular permissions, such as using role-based access control (RBAC) to assign permissions based on specific job roles, is a more efficient way to manage access control than managing individual user permissions.
This significantly reduces the impact of a compromised account as the attacker will have limited privileges. Regularly reviewing and refining these assignments will ensure that permissions remain appropriately restricted.
Multi-Factor Authentication (MFA) Implementation
Implementing MFA for all Active Directory users is a critical step towards a Zero Trust environment. MFA adds an extra layer of security by requiring users to provide two or more forms of authentication, such as a password and a code from a mobile authenticator app. This significantly reduces the risk of unauthorized access, even if an attacker obtains a user’s password.
Microsoft Azure Multi-Factor Authentication (MFA) Server can be deployed on-premises to provide this capability for your Active Directory users. Integrating MFA with your existing login processes is relatively straightforward and provides a significant improvement in security. Consider prioritizing MFA for users with privileged access, such as domain administrators, to protect critical systems and data.
Strong Password Policies and Regular Rotations
Enforcing strong password policies and regular password rotations are fundamental security measures. This includes enforcing password complexity requirements (minimum length, character types), preventing password reuse, and setting a reasonable password expiration policy. For example, requiring passwords to be at least 12 characters long, containing uppercase and lowercase letters, numbers, and symbols, and enforcing a 90-day password expiration policy.
Regular password changes help limit the impact of compromised credentials. While password complexity requirements are important, consider educating users on the importance of unique and strong passwords and providing tools to help them manage complex passwords securely. Avoid overly aggressive password rotation policies, as frequent changes can lead to password fatigue and users resorting to weak, easily guessed passwords.
Extending Zero Trust to Hybrid Environments
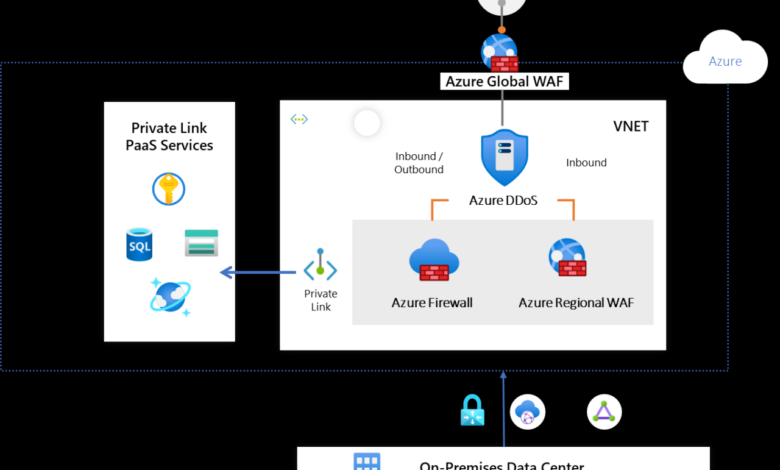
Securing a hybrid Active Directory environment presents a unique set of challenges. The blend of on-premises infrastructure and cloud-based services creates a complex attack surface, demanding a robust and adaptable security strategy. Zero Trust, with its principle of “never trust, always verify,” provides a powerful framework for mitigating these risks. This section explores how to extend Zero Trust principles to effectively secure your hybrid Active Directory deployment.Hybrid Active Directory environments inherently increase complexity due to the interaction between on-premises domain controllers and cloud-based identity services like Azure Active Directory (Azure AD).
This interconnectedness introduces vulnerabilities if not properly secured. Maintaining a consistent security posture across both environments is paramount, requiring careful integration of on-premises and cloud-based security solutions. Failure to address this adequately leaves organizations susceptible to breaches and data loss.
Challenges of Securing Hybrid Active Directory
Securing a hybrid Active Directory environment involves several key challenges. Maintaining consistent security policies across on-premises and cloud environments is crucial. This includes ensuring consistent password policies, multi-factor authentication (MFA) enforcement, and access control lists. Another significant challenge is managing the trust relationship between on-premises Active Directory and Azure AD. Misconfigurations in this trust relationship can create security loopholes.
Finally, monitoring and logging across both environments is critical for detecting and responding to security incidents. A comprehensive security information and event management (SIEM) system is necessary to aggregate and analyze logs from both on-premises and cloud resources.
Key Components Requiring Zero Trust Protection in a Hybrid Setup
Several critical components in a hybrid Active Directory environment require specific Zero Trust protection. These include on-premises domain controllers, which are essential for authentication and authorization within the on-premises network. Azure AD Connect, the synchronization service connecting on-premises Active Directory with Azure AD, requires strong security to prevent unauthorized access and modification. Azure AD itself, the cloud-based identity and access management service, needs robust security controls to protect user accounts and applications.
Finally, all applications and resources accessed by users, regardless of their location (on-premises or cloud), must be protected with granular access controls and continuous monitoring.
Integrating Cloud-Based Security Solutions with On-Premises Active Directory
Integrating cloud-based security solutions with on-premises Active Directory requires a phased approach. First, implement MFA for all users, both on-premises and cloud-based. This significantly enhances security by requiring multiple authentication factors. Next, leverage Azure AD Conditional Access policies to enforce granular access controls based on user location, device posture, and other risk factors. This ensures that only authorized users can access specific resources under specific conditions.
Then, integrate cloud-based security tools like Azure Sentinel for security information and event management (SIEM) to monitor both on-premises and cloud environments. This provides a unified view of security events and enables proactive threat detection and response. Finally, implement continuous monitoring and automated threat response capabilities to quickly identify and address security breaches.
Data Flow and Security Measures in a Hybrid Zero Trust Environment
The following flowchart illustrates the data flow and security measures in a typical hybrid Zero Trust environment. Imagine a user attempting to access a cloud-based application from their laptop. First, the user authenticates using MFA through Azure AD. Azure AD then verifies the user’s identity and device posture. If the verification is successful, Azure AD issues a temporary access token.
This token is then used to access the cloud-based application. The application verifies the token before granting access. Meanwhile, the user’s access is monitored continuously by Azure Sentinel. Any suspicious activity triggers alerts and automated responses. For on-premises access, a similar process occurs, with authentication happening through on-premises Active Directory and access controlled by conditional access policies.
All access attempts are logged and monitored. The trust relationship between on-premises Active Directory and Azure AD is carefully managed and audited regularly. This comprehensive approach ensures that only authorized users and devices can access resources, regardless of their location.
Imagine a diagram here showing a user’s laptop (with MFA authentication) connecting to Azure AD, which then verifies the identity and device health before granting access to a cloud application (e.g., Office 365). The access is continuously monitored by Azure Sentinel. A separate, but similar, path would exist for on-premises applications, with authentication occurring via on-premises Active Directory.
Both paths would funnel logging data to a central SIEM system for monitoring and analysis. The connection between on-premises AD and Azure AD is clearly represented as a secured and monitored trust relationship.
Leveraging Microsoft Security Tools for Zero Trust
Implementing Zero Trust in Active Directory effectively requires leveraging the robust security tools offered by Microsoft. These tools, when properly configured and integrated, provide a layered approach to securing your on-premises and hybrid environments, minimizing the attack surface and enhancing overall security posture. This section details how key Microsoft technologies contribute to a robust Zero Trust architecture.
Azure AD Connect Capabilities in Hybrid Environments
Azure AD Connect acts as the bridge between your on-premises Active Directory and Azure AD. Its crucial role in a Zero Trust implementation lies in its ability to synchronize user identities, groups, and other attributes, enabling seamless single sign-on (SSO) and conditional access policies. This synchronization allows for consistent identity management across both environments, a cornerstone of effective Zero Trust.
Features like password hash synchronization, pass-through authentication, and federation provide different approaches to authentication, each offering various levels of security and complexity. Careful consideration of your specific environment and security requirements is key when choosing the optimal synchronization method. For example, organizations with stricter security needs might opt for pass-through authentication to avoid storing passwords in the cloud.
Leveraging Azure AD Conditional Access Policies
Azure AD Conditional Access provides granular control over access to resources based on various signals, including user location, device state, application, and risk level. By defining policies that require multi-factor authentication (MFA), device compliance, or risk assessment before granting access, organizations can significantly reduce the risk of unauthorized access. For instance, a policy might require MFA for all users accessing sensitive applications from unmanaged devices, while allowing password-only authentication for trusted users accessing less sensitive resources from compliant devices within the corporate network.
This context-aware approach is central to the Zero Trust philosophy of “never trust, always verify.”
Best Practices for Utilizing Microsoft Defender for Identity
Microsoft Defender for Identity (formerly Azure ATP) provides advanced threat protection for your on-premises Active Directory environment. Its capabilities include detecting and responding to suspicious activities like brute-force attacks, lateral movement, and privileged account abuse. Best practices include ensuring comprehensive coverage of all your domain controllers, regularly reviewing alerts and security recommendations, and integrating Defender for Identity with other security tools for a holistic view of your security posture.
Proactive monitoring and timely responses to alerts are crucial in mitigating potential threats before they escalate. For example, immediate investigation of a flagged privileged account access attempt from an unusual location can prevent a significant breach.
Relevant Microsoft Security Tools for Zero Trust in Active Directory
Implementing a comprehensive Zero Trust strategy necessitates a multi-layered approach. Several Microsoft security tools play crucial roles in achieving this goal:
- Azure Active Directory (Azure AD): Provides identity and access management services, including single sign-on (SSO), multi-factor authentication (MFA), and conditional access policies.
- Azure AD Connect: Synchronizes identities and other attributes between on-premises Active Directory and Azure AD, enabling hybrid identity management.
- Microsoft Defender for Identity: Detects and responds to threats within your on-premises Active Directory environment.
- Microsoft Intune: Manages and secures mobile devices, ensuring compliance before granting access to corporate resources.
- Microsoft Endpoint Manager: A unified platform for managing and securing endpoints, including PCs, laptops, and mobile devices.
- Microsoft Defender for Endpoint: Provides endpoint detection and response (EDR) capabilities, protecting devices from malware and other threats.
- Azure Sentinel: A cloud-native SIEM solution for collecting, analyzing, and visualizing security data from various sources, providing a centralized view of your security posture.
User and Device Access Control
Implementing robust user and device access control is paramount in a Zero Trust model for Active Directory. This goes beyond simple username and password authentication; it requires a granular approach that considers both user roles and the security posture of the devices accessing your network resources. This layered approach minimizes the attack surface and limits the potential damage from compromised accounts or insecure devices.This section details strategies for achieving granular access control, including device registration, compliance checks, network segmentation, and leveraging Group Policy Objects (GPOs) to enforce Zero Trust principles.
Granular Access Control Based on User Roles and Device Posture
A successful Zero Trust strategy requires moving away from broad access permissions. Instead, access should be granted based on the principle of least privilege. Users should only have access to the resources absolutely necessary for their roles. This requires careful mapping of user roles to specific permissions within Active Directory. Simultaneously, device posture assessment plays a crucial role.
Only compliant devices, meeting specific security criteria (e.g., up-to-date antivirus, firewall enabled, operating system patched), should be granted access to sensitive resources. This dual-layered approach significantly reduces the risk of unauthorized access and lateral movement within the network. For example, a help desk technician might need access to specific user accounts for troubleshooting but not to financial data, while a finance manager would need access to financial systems but not to user account management tools.
Device Registration and Compliance Checks
Device registration and compliance checks are the cornerstones of secure device access. Microsoft Intune or other Mobile Device Management (MDM) solutions can be leveraged to enforce compliance policies. These policies can mandate software updates, secure configurations, and the installation of security agents. Upon registration, devices undergo a compliance check against these policies. Only compliant devices are granted access to resources.
Non-compliant devices might be placed in a quarantined state, allowing limited access or no access until they meet the required security standards. This prevents compromised or misconfigured devices from accessing sensitive data. For example, a policy might require devices to have a specific version of antivirus software installed and up-to-date, a strong password policy enforced, and regular security updates applied.
Network Segmentation to Isolate Sensitive Resources
Network segmentation is a critical element in limiting the impact of a security breach. By segmenting the network into smaller, isolated zones, you can restrict lateral movement. Sensitive resources, such as domain controllers or financial applications, should reside in highly secure segments, accessible only by authorized users and devices. This prevents a compromise in one segment from impacting other parts of the network.
For example, the domain controllers could be placed in a separate VLAN with strict access controls, while less sensitive resources, like shared drives for non-critical data, could be placed in a different, less restricted segment.
Using Group Policies to Enforce Zero Trust Principles
Group Policy Objects (GPOs) provide a powerful mechanism for enforcing Zero Trust principles. GPOs can be used to configure various security settings across the network, such as password complexity, account lockout policies, and restricting access to specific resources based on user group membership or device compliance status. For example, a GPO can be created to enforce multi-factor authentication (MFA) for all users accessing sensitive resources, or to restrict access to certain network shares based on user role.
Another GPO could be configured to prevent the execution of unauthorized scripts or applications on managed devices.
Securing your Active Directory, especially in hybrid environments, requires a robust approach like implementing zero trust principles. This means moving beyond traditional perimeter security and focusing on granular access control. For application development, consider the innovative approaches discussed in this article on domino app dev the low code and pro code future , which could help streamline your security processes.
Returning to our core topic, a well-defined zero trust strategy for Active Directory is crucial for protecting your on-premises and cloud-based infrastructure.
Monitoring and Auditing
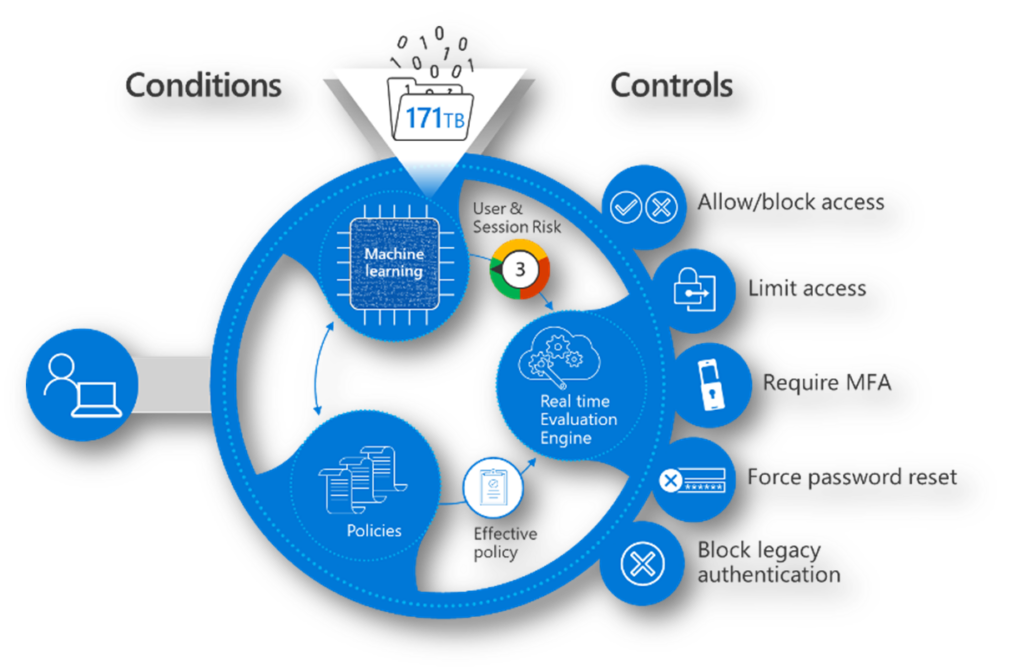
Implementing Zero Trust in Active Directory requires a robust monitoring and auditing strategy. Continuous monitoring provides real-time visibility into your environment, allowing for immediate detection and response to potential threats. Comprehensive logging helps in post-incident analysis, enabling security teams to understand attack vectors and improve their defenses. Without consistent monitoring and detailed logging, your Zero Trust implementation will be significantly weakened.Security auditing for Active Directory events is crucial for maintaining a Zero Trust posture.
By configuring detailed auditing, you gain a granular record of all significant activities within your Active Directory environment. This includes account creations and modifications, group membership changes, login attempts, and access control list (ACL) modifications. This detailed logging allows for the identification of suspicious activities that might indicate a compromise.
Configuring Security Auditing for Active Directory
To configure security auditing for Active Directory, you’ll need to utilize the Group Policy Management Console (GPMC). Navigate to the domain controllers and modify the relevant Group Policy Objects (GPOs) to enable detailed auditing for specific events. Focus on auditing events related to account management, access control, and authentication. Remember to configure both success and failure audits, as failure audits often reveal attempted attacks.
The specific settings will depend on your organizational needs and risk profile. For example, auditing changes to sensitive group memberships should be prioritized. Regularly review and refine your auditing configuration to ensure it remains effective against emerging threats. Incorrectly configured auditing can lead to excessive log volume, making analysis difficult.
Analyzing Security Logs to Identify and Respond to Threats
Analyzing security logs requires specialized tools and expertise. Security Information and Event Management (SIEM) systems are invaluable for collecting, correlating, and analyzing logs from various sources, including Active Directory. These systems can identify patterns indicative of malicious activity, such as brute-force attacks, unauthorized access attempts, or privilege escalation. The analysis should focus on identifying anomalies, unusual login times or locations, and access to sensitive resources by unauthorized users.
Effective analysis requires a clear understanding of normal activity within your environment to distinguish it from malicious behavior. When a threat is detected, a rapid response is crucial. This may involve disabling compromised accounts, blocking malicious IP addresses, or initiating a full-scale incident response process.
Key Security Events to Monitor
The following table Artikels key security events to monitor and their corresponding actions. Remember that this is not an exhaustive list and should be adapted to your specific environment and risk profile.
| Event Type | Description | Action | Severity |
|---|---|---|---|
| Account Lockout | Multiple failed login attempts for a user account. | Investigate potential brute-force attack. Review account lockout threshold settings. | High |
| Group Membership Change | Addition or removal of users from sensitive groups (e.g., Domain Admins). | Verify legitimacy of change. Review audit logs for suspicious activity. | High |
| Failed Logon Attempt | Failed authentication attempts from unusual IP addresses or times. | Investigate potential unauthorized access attempt. Block malicious IP addresses if necessary. | Medium |
| Privilege Escalation Attempt | Attempt to elevate user privileges beyond their assigned roles. | Investigate potential compromise. Review access control lists (ACLs). | High |
Addressing Advanced Threats: A Practical Guide To Applying Zero Trust Principles To Active Directory For Microsoft On Premises And Hybrid Environment Protection
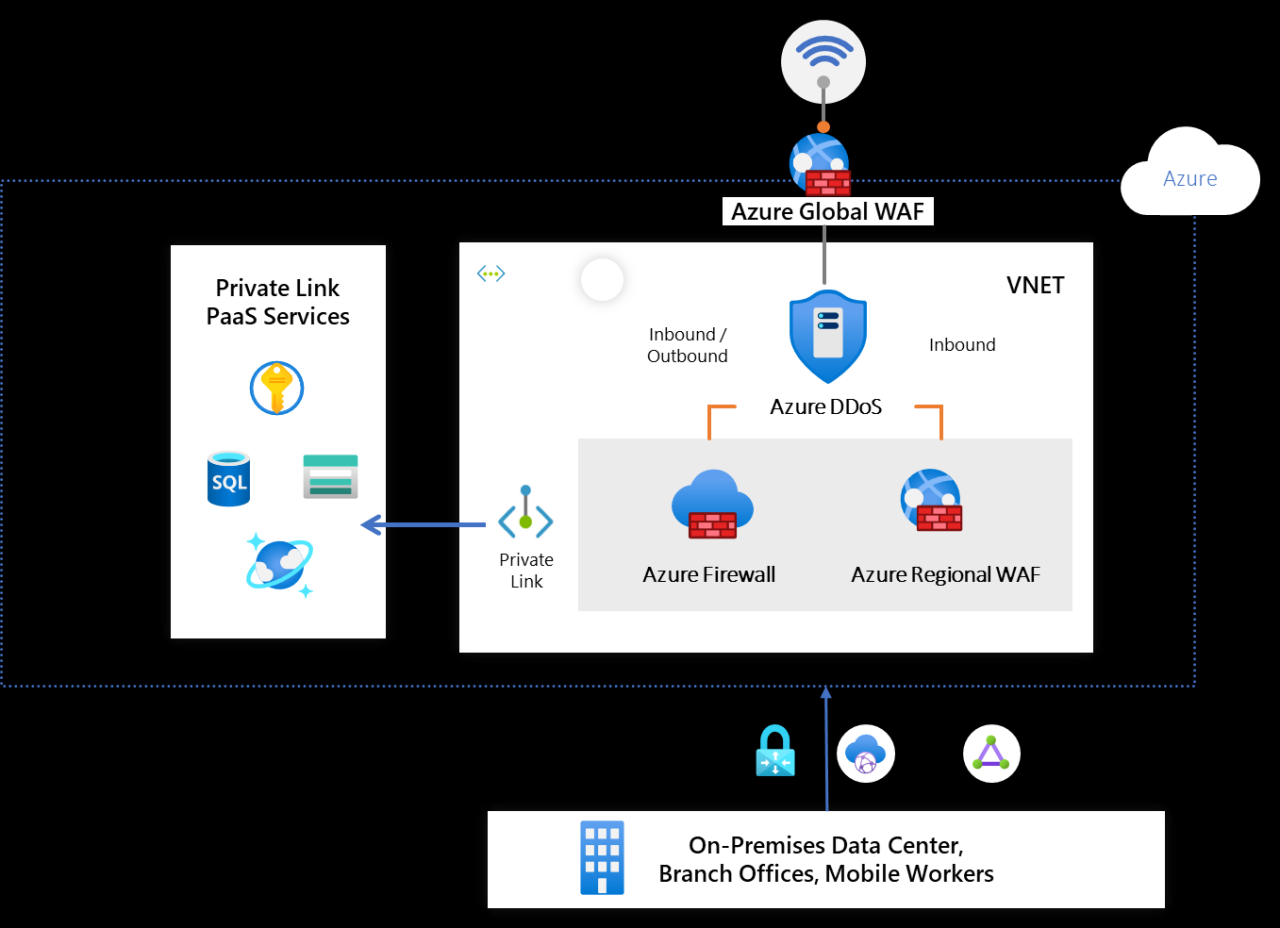
Zero Trust’s inherent assumption of no implicit trust extends to the threat landscape. A robust Zero Trust strategy for Active Directory, especially in hybrid environments, must proactively address advanced threats that can bypass traditional security perimeters. This requires a multi-layered approach combining threat intelligence, advanced detection mechanisms, and robust monitoring.Threat intelligence plays a crucial role in preemptively identifying and mitigating advanced threats.
By leveraging threat feeds, vulnerability databases, and security research, organizations can anticipate potential attacks and proactively strengthen their defenses. This proactive approach allows for timely patching, configuration adjustments, and the deployment of specific security controls to counter emerging threats.
Threat Intelligence Integration
Effective threat intelligence integration involves several key steps. First, organizations must identify and subscribe to reputable threat intelligence feeds that align with their specific risk profile. These feeds can provide early warnings of new malware variants, attack techniques, and targeted campaigns. Secondly, this intelligence needs to be processed and correlated with existing security logs and data to identify potential threats within the organization’s own environment.
Finally, actionable insights derived from the intelligence should trigger automated responses, such as blocking malicious IP addresses or isolating compromised systems. This automated response significantly reduces the window of opportunity for attackers.
Advanced Threat Detection and Response, A practical guide to applying zero trust principles to active directory for microsoft on premises and hybrid environment protection
Implementing advanced threat detection and response requires a layered approach involving multiple technologies. Next-generation antivirus (NGAV) solutions provide advanced malware detection capabilities beyond traditional signature-based approaches. Endpoint Detection and Response (EDR) tools offer real-time monitoring of endpoint activity, enabling the detection of suspicious behavior and rapid response to incidents. Furthermore, Security Information and Event Management (SIEM) systems play a critical role in centralizing and correlating security logs from various sources, facilitating threat detection and incident response.
By combining these technologies, organizations can achieve a comprehensive approach to detecting and responding to advanced threats.
Security Information and Event Management (SIEM) Systems
SIEM systems act as the central nervous system for security monitoring and analysis within a Zero Trust framework. They aggregate logs from various sources, including Active Directory, firewalls, endpoints, and cloud services, providing a holistic view of security events. SIEMs leverage advanced analytics and machine learning to identify patterns indicative of malicious activity, such as unusual login attempts, data exfiltration attempts, and lateral movement within the network.
Real-time alerting capabilities enable rapid response to security incidents, minimizing their impact. Effective SIEM deployment requires careful planning, configuration, and ongoing tuning to optimize alert accuracy and reduce false positives. Furthermore, effective incident response playbooks are crucial to ensure efficient handling of detected threats.
Examples of Advanced Threats and Zero Trust Mitigation
Understanding how advanced threats operate is critical to effectively mitigating them within a Zero Trust architecture.
- Phishing Attacks: Zero Trust mitigates phishing by enforcing multi-factor authentication (MFA) and limiting access based on context (e.g., device posture, location). Even if a user falls for a phishing attempt, MFA prevents unauthorized access.
- Malware Infections: EDR and NGAV solutions, integrated within a Zero Trust framework, detect and contain malware infections quickly, limiting their lateral movement and impact. Micro-segmentation and least privilege access further restrict the malware’s reach.
- Insider Threats: Zero Trust principles, such as least privilege access and granular access control, limit the damage an insider can inflict, even if malicious intent is present. Continuous monitoring and auditing of user activity can detect suspicious behavior early on.
- Credential Stuffing Attacks: MFA and robust password policies, combined with anomaly detection within the SIEM, can effectively detect and block credential stuffing attacks.
- Supply Chain Attacks: Zero Trust mitigates the impact of supply chain attacks by enforcing strict verification of software and hardware components before deployment. Regular vulnerability scanning and patching are also essential.
Final Review
Implementing Zero Trust in your Active Directory environment is a journey, not a destination. It requires a proactive approach, continuous monitoring, and a willingness to adapt to evolving threats. This guide has provided a solid foundation, equipping you with the knowledge and practical steps needed to begin your Zero Trust transformation. Remember, the key is to continuously assess your security posture, adapt your strategies, and leverage the powerful tools available to ensure your Active Directory remains secure in the face of ever-increasing cyber threats.
Start small, focus on critical assets, and gradually expand your Zero Trust implementation. The result will be a significantly more secure and resilient IT infrastructure.
Questions and Answers
What are the biggest challenges in implementing Zero Trust for Active Directory?
The biggest challenges often involve integrating existing systems with new Zero Trust technologies, managing the complexity of granular access control, and ensuring user experience isn’t negatively impacted. Proper planning and phased implementation are crucial.
How much will implementing Zero Trust cost?
Costs vary greatly depending on your existing infrastructure, the tools you choose, and the level of expertise required. Some solutions are relatively inexpensive, while others require significant investment in hardware, software, and professional services.
Can I implement Zero Trust gradually?
Absolutely! A phased approach is recommended. Start with high-value assets and gradually expand your Zero Trust implementation across your entire Active Directory environment.
What happens if I experience a security breach after implementing Zero Trust?
While Zero Trust significantly reduces the impact of a breach, it doesn’t eliminate the possibility entirely. Continuous monitoring and robust incident response plans are essential to minimize damage and recovery time.