A Synopsis of WannaCry Ransomware Attack on 150 Countries
A synopsis of WannaCry ransomware attack on 150 countries – remember that terrifying Friday in 2017? The world woke up to a digital nightmare, a global ransomware attack crippling hospitals, businesses, and even entire national infrastructures. WannaCry wasn’t just another malware; it was a wake-up call, a stark reminder of our collective vulnerability in the face of sophisticated cyberattacks.
This post delves into the details of this unprecedented event, exploring its impact, the technology behind it, and the lessons learned.
From its initial deployment and rapid global spread, fueled by the infamous EternalBlue exploit, WannaCry’s impact was devastating. We’ll examine the technical intricacies of the malware, the various versions released, and the crippling effect it had on critical infrastructure across numerous sectors. We’ll also discuss the global response, the accidental discovery of a “kill switch,” and the long-term consequences for cybersecurity practices worldwide.
Overview of the WannaCry Ransomware Attack
The WannaCry ransomware attack, which unfolded in May 2017, serves as a stark reminder of the devastating potential of cyberattacks on a global scale. Exploiting a vulnerability in older versions of Microsoft Windows, this attack crippled hospitals, businesses, and critical infrastructure across the world, highlighting the interconnectedness of our digital systems and the vulnerability of outdated security practices. The speed and reach of the attack shocked many, prompting a global reassessment of cybersecurity protocols.The WannaCry ransomware attack began with the deployment of the malware on Friday, May 12, 2017.
Within hours, the ransomware rapidly spread across the globe, leveraging the EternalBlue exploit, a leaked National Security Agency (NSA) tool. This exploit allowed the malware to spread laterally across networks without requiring user interaction, making it particularly insidious. The attack’s rapid global spread was fueled by its worm-like capabilities, allowing it to self-propagate through vulnerable systems connected to the internet.
By the end of the weekend, the impact was felt worldwide, with reports of infections flooding in from various sectors and nations.
Initial Infection Vector and Propagation Method
The primary infection vector for WannaCry was the EternalBlue exploit, a vulnerability in the Server Message Block (SMB) protocol of older, unpatched Microsoft Windows operating systems. This exploit allowed the ransomware to bypass security measures and gain unauthorized access to vulnerable machines. Once a system was compromised, WannaCry would encrypt files on the hard drive, rendering them inaccessible until a ransom was paid in Bitcoin.
The malware then leveraged the same SMB vulnerability to scan and infect other vulnerable systems on the network, creating a cascading effect of infections. This self-propagating nature significantly amplified the attack’s reach and impact. The ease of propagation and the lack of user interaction required for infection contributed to the rapid global spread.
Countries Most Affected and Scale of Impact
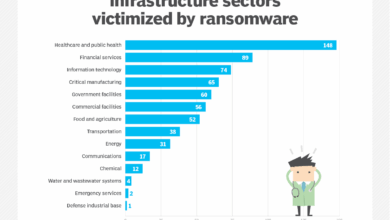
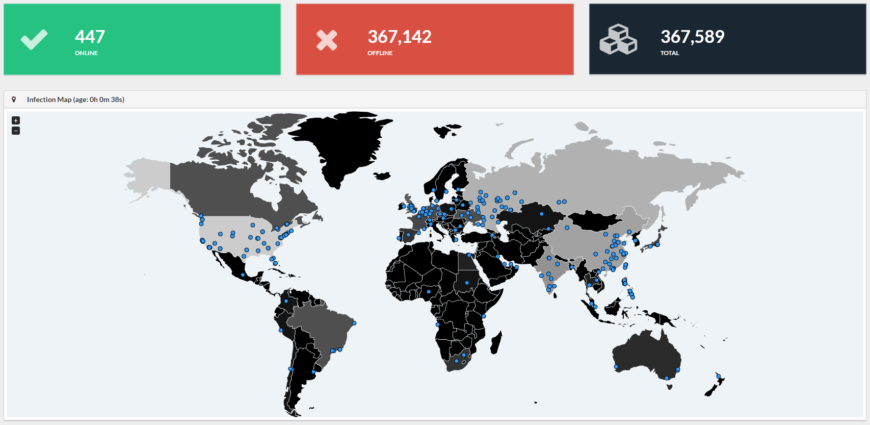
The WannaCry ransomware attack affected over 150 countries, demonstrating its truly global reach. While precise figures on the number of affected systems are difficult to ascertain, reports suggest hundreds of thousands of computers were infected. Hospitals in the UK’s National Health Service (NHS) were particularly hard hit, with disruptions to patient care and essential services. Other heavily impacted sectors included manufacturing, transportation, and financial institutions.
The attack underscored the significant economic and societal costs associated with large-scale ransomware attacks. The disruption caused by WannaCry highlighted the critical need for robust cybersecurity measures and the importance of timely software patching to mitigate such threats. The sheer scale of the attack served as a wake-up call for organizations and governments worldwide, emphasizing the need for proactive cybersecurity strategies and international collaboration in combating cybercrime.
Technical Analysis of the WannaCry Malware

WannaCry wasn’t just a simple ransomware; it was a sophisticated piece of malware leveraging several cutting-edge techniques to achieve unprecedented global impact. Understanding its technical underpinnings is crucial to comprehending the scale and severity of the attack. This section delves into the specific technical components that made WannaCry so effective.WannaCry employed a combination of robust encryption and aggressive network propagation mechanisms to maximize its reach and impact.
The encryption used was AES-128, a symmetric-key algorithm considered strong, making decryption difficult without the decryption key. This key was unique for each victim, further complicating any mass decryption efforts. The ransomware encrypted numerous file types, including documents, images, and databases, rendering them unusable until a ransom was paid. The propagation relied heavily on exploiting vulnerabilities in older, unpatched systems.
Remember the WannaCry ransomware attack? It crippled systems in 150 countries, highlighting the urgent need for robust cybersecurity. Thinking about how to build more resilient systems quickly brings to mind the advancements in application development, like what’s discussed in this article on domino app dev the low code and pro code future , which could help organizations respond faster to such threats.
Ultimately, the WannaCry attack serves as a stark reminder of the importance of secure, efficiently-built applications.
EternalBlue Exploit
The success of the WannaCry attack was largely attributable to the exploitation of a vulnerability known as EternalBlue. This exploit, leaked from the NSA’s hacking arsenal, targeted a critical vulnerability (MS17-010) in Microsoft’s Server Message Block (SMB) protocol, specifically affecting older versions of Windows. EternalBlue allowed WannaCry to spread laterally across networks without requiring user interaction, essentially turning infected machines into self-propagating agents.
This “worm-like” behavior significantly amplified the attack’s reach, allowing it to rapidly infect thousands of computers worldwide. The vulnerability’s prevalence and the ease of exploitation via EternalBlue were key factors in WannaCry’s rapid dissemination. Many organizations and individuals failed to patch their systems, leaving them vulnerable to this devastating attack.
WannaCry Versions and Key Differences
Understanding the evolution of WannaCry requires examining its different versions. These variations showcased the attackers’ adaptation and attempts to improve the ransomware’s capabilities.
| Version | Release Date (Approximate) | Key Features | Notable Differences |
|---|---|---|---|
| WannaCry (original) | May 12, 2017 | AES-128 encryption, EternalBlue exploit, ransom note | Initial release; lacked a kill switch |
| WannaCry (with kill switch) | May 12, 2017 (shortly after original) | AES-128 encryption, EternalBlue exploit, ransom note, kill switch domain | Incorporated a kill switch; propagation halted when a specific domain was registered |
| Variants and subsequent modifications | May 12, 2017 onwards | Variations in ransom amounts, command and control (C&C) servers, and other minor tweaks | These were minor modifications often aimed at evading detection or altering ransom demands. Some included attempts to improve stealth or persistence. |
Impact and Consequences of the WannaCry Attack
The WannaCry ransomware attack, while relatively short-lived, left a significant and lasting impact across the globe. Its exploitation of a critical vulnerability in older Windows systems resulted in widespread disruption and substantial financial losses for numerous organizations and individuals. The sheer scale of the attack – affecting over 150 countries – highlighted the interconnectedness of global infrastructure and the devastating potential of large-scale cyberattacks.
The consequences extended far beyond immediate data loss, revealing vulnerabilities in critical infrastructure and prompting a global reassessment of cybersecurity practices.The economic repercussions of WannaCry were felt acutely across various sectors. The attack’s indiscriminate nature meant that organizations of all sizes and in various industries suffered. The disruption to operations, the costs of recovery, and the reputational damage caused significant financial strain.
Economic Impact Across Sectors
The healthcare sector was particularly hard hit. Hospitals and clinics in several countries experienced significant disruption to their operations, with some forced to divert ambulances and postpone surgeries due to compromised systems. The impact on patient care was substantial, demonstrating the severe consequences of ransomware attacks on essential services. The automotive industry also faced challenges, with some manufacturers reporting temporary production halts due to infected systems impacting their supply chains.
Beyond these specific sectors, the attack caused ripple effects across the global economy, impacting businesses reliant on international trade and digital infrastructure. Estimates of the total economic damage vary widely, but the cost undoubtedly ran into hundreds of millions, if not billions, of dollars globally. The costs included not only direct financial losses from ransom payments (although many victims did not pay), but also the expense of recovery, including hiring cybersecurity experts, replacing hardware, and restoring data.
Furthermore, the long-term damage to reputation and customer trust represented a significant, and difficult-to-quantify, cost.
Critical Infrastructure Disruption
The WannaCry attack highlighted the vulnerability of critical infrastructure systems to ransomware. The attack demonstrated that even systems believed to be well-protected could be compromised. Transportation networks, including railways and airports, experienced some disruptions, though the extent varied greatly by location and system resilience. Energy companies also reported some infections, underscoring the potential for catastrophic consequences if such attacks were more widespread or targeted.
The vulnerability of healthcare systems, with their reliance on interconnected devices and often outdated software, was starkly revealed. The attack exposed the need for improved security protocols and robust disaster recovery plans for critical infrastructure, especially given the potential for cascading failures if multiple interconnected systems are compromised. The attack served as a wake-up call for governments and private organizations alike to invest more heavily in cybersecurity measures to protect essential services.
Long-Term Consequences for Affected Organizations
The long-term consequences of the WannaCry attack for affected organizations were multifaceted and significant.
- Increased Cybersecurity Investments: Many organizations significantly increased their cybersecurity budgets and implemented enhanced security measures, including improved endpoint protection, vulnerability patching, and employee training programs.
- Improved Disaster Recovery Planning: The attack underscored the importance of robust disaster recovery plans and prompted organizations to invest in more sophisticated backup and recovery systems.
- Enhanced Network Segmentation: Organizations implemented network segmentation strategies to limit the impact of future attacks by isolating critical systems from less secure networks.
- Reputational Damage: Some organizations experienced lasting reputational damage, impacting their customer trust and business relationships.
- Regulatory Scrutiny: The attack led to increased regulatory scrutiny of cybersecurity practices, with some organizations facing fines or other penalties for failing to meet regulatory requirements.
- Legal Liabilities: Some organizations faced legal action from customers or partners affected by the attack.
Response and Mitigation Efforts
The WannaCry ransomware attack triggered a swift and multifaceted global response, involving governments, cybersecurity firms, and individual users. The sheer scale and speed of the attack highlighted the vulnerability of interconnected systems and the urgent need for improved cybersecurity practices. While the response was largely reactive, it showcased the potential for international collaboration in tackling major cyber threats.The immediate response focused on containment and mitigation.
Cybersecurity firms raced to analyze the malware, identify vulnerabilities, and develop patches. Governments issued public warnings, providing guidance to individuals and organizations on how to protect themselves. Many countries established emergency response teams to coordinate efforts and assist affected entities. The effectiveness of these strategies varied, however, depending on factors such as the level of preparedness of individual organizations and the speed of patch deployment.
Governmental Responses
Governments worldwide played a crucial role in responding to the WannaCry attack. Some governments, like the UK’s National Cyber Security Centre (NCSC), proactively disseminated information and provided technical support to affected organizations. Others, such as the United States’ Cybersecurity and Infrastructure Security Agency (CISA), issued emergency directives and collaborated with international partners to share threat intelligence. The response varied in its intensity and effectiveness, reflecting differences in national cybersecurity capabilities and priorities.
For example, some countries with more robust cybersecurity infrastructure were better equipped to handle the crisis than others with limited resources or expertise. The speed and effectiveness of government responses often correlated with pre-existing national cybersecurity strategies and investment in cyber infrastructure.
Mitigation Strategies and Their Effectiveness
Several mitigation strategies proved effective in containing the spread of WannaCry. The most crucial was the rapid development and deployment of security patches by Microsoft. Organizations that promptly updated their systems were largely protected. Network segmentation, isolating vulnerable systems from the internet, also played a vital role in limiting the impact of the attack. The use of robust endpoint detection and response (EDR) solutions allowed some organizations to detect and contain the ransomware before it could encrypt significant amounts of data.
However, many organizations, particularly smaller businesses and individuals, lacked the resources or expertise to implement these measures effectively. This disparity in preparedness led to a significant variation in the severity of the impact across different sectors and geographical regions.
International Collaboration and Information Sharing
The WannaCry attack underscored the importance of international cooperation in cybersecurity. The rapid sharing of threat intelligence and analysis among governments and cybersecurity firms played a critical role in the response. This collaborative effort enabled researchers to quickly identify the malware’s vulnerabilities and develop effective countermeasures. However, challenges remained in terms of coordinating responses across different jurisdictions and overcoming legal and regulatory obstacles to information sharing.
The attack highlighted the need for improved mechanisms for international collaboration in the face of future cyber threats, including better standardized protocols for sharing threat intelligence and coordinated responses.
Lessons Learned and Future Implications

The WannaCry ransomware attack served as a stark reminder of the vulnerabilities inherent in interconnected systems and the devastating consequences of neglecting cybersecurity best practices. The attack exposed critical weaknesses in both organizational security protocols and the broader global digital infrastructure, highlighting the urgent need for proactive and comprehensive security measures. The lessons learned from this event extend far beyond immediate remediation; they underscore the need for a fundamental shift in how we approach cybersecurity in the age of increasingly sophisticated cyber threats.The WannaCry attack primarily exploited the EternalBlue exploit, a vulnerability in older versions of Microsoft’s Windows operating system.
This vulnerability allowed attackers to remotely execute code on affected machines without user interaction. The widespread impact demonstrated the significant risk posed by unpatched software and the critical importance of timely updates. Furthermore, the attack’s rapid propagation across networks highlighted the vulnerability of organizations with insufficient network segmentation and inadequate monitoring capabilities. The reliance on outdated systems and the lack of robust security protocols allowed the ransomware to spread exponentially, causing widespread disruption and financial losses.
The implications are far-reaching, affecting not only individual users but also critical infrastructure like hospitals and transportation systems.
Vulnerabilities Exposed and Their Implications
The WannaCry attack exposed several critical vulnerabilities. The most significant was the EternalBlue exploit, which targeted the Server Message Block (SMB) protocol. This protocol, used for file sharing and other network communication, was vulnerable to remote code execution, allowing attackers to install malware without user interaction. The widespread use of outdated Windows systems and the slow patching process by many organizations exacerbated the problem.
This highlighted the critical need for robust patch management systems and proactive vulnerability scanning to identify and address security weaknesses before they can be exploited. The attack also revealed the dangers of relying on legacy systems and the importance of a comprehensive approach to cybersecurity that encompasses both technology and organizational processes. Failure to implement strong access controls, network segmentation, and robust security monitoring systems allowed the ransomware to spread rapidly and cause significant damage.
Recommendations for Improving Cybersecurity Defenses
Improving cybersecurity defenses requires a multi-faceted approach. First and foremost, organizations must implement a robust patch management system to ensure that all software, including operating systems and applications, is updated with the latest security patches. This requires not only the technical capability to deploy updates but also the organizational discipline to prioritize and schedule updates effectively. Regular vulnerability scanning and penetration testing are also essential to identify and address potential weaknesses in the system before they can be exploited.
Network segmentation can limit the impact of a breach by preventing malware from spreading throughout the entire network. Implementing strong access controls, such as multi-factor authentication, can help prevent unauthorized access to sensitive systems and data. Finally, robust security information and event management (SIEM) systems are crucial for monitoring network activity, detecting malicious behavior, and responding to security incidents effectively.
The investment in employee training and awareness programs is also critical, as human error remains a major factor in many security breaches.
Best Practices for Preventing Ransomware Infections
A proactive approach to cybersecurity is paramount to prevent ransomware infections. The following best practices are essential:
- Regular Software Updates: Implement a robust patch management system to ensure all software is up-to-date with the latest security patches.
- Network Segmentation: Segment the network to limit the impact of a breach and prevent malware from spreading throughout the entire system.
- Strong Access Controls: Implement strong passwords, multi-factor authentication, and access control lists to restrict access to sensitive systems and data.
- Regular Backups: Regularly back up critical data to an offline location to ensure data recovery in case of a ransomware attack.
- Security Awareness Training: Provide regular security awareness training to employees to educate them about phishing scams, malicious emails, and other social engineering techniques.
- Antivirus and Endpoint Detection and Response (EDR): Implement robust antivirus software and EDR solutions to detect and prevent malware infections.
- Vulnerability Scanning and Penetration Testing: Regularly scan for vulnerabilities and conduct penetration testing to identify and address potential weaknesses in the system.
- Incident Response Plan: Develop and regularly test an incident response plan to effectively handle security incidents.
The Role of the NSA and the EternalBlue Exploit
The WannaCry ransomware attack, which crippled systems across 150 countries in 2017, serves as a stark reminder of the potential consequences of irresponsible handling of cybersecurity vulnerabilities. A key factor in the attack’s widespread success was the exploitation of EternalBlue, a powerful exploit developed by the National Security Agency (NSA). This section delves into the NSA’s role and the ethical and security implications surrounding the use and storage of zero-day exploits.The NSA’s EternalBlue exploit targeted a critical vulnerability in Microsoft’s SMB (Server Message Block) protocol.
This vulnerability allowed attackers to remotely execute code on affected systems without any user interaction, essentially giving them complete control. The NSA, as part of its intelligence gathering operations, had likely developed and stored EternalBlue as a zero-day exploit – a vulnerability unknown to the software vendor and thus unpatched. The leak of this exploit, however, through the Shadow Brokers hacking group, allowed malicious actors to weaponize it, unleashing the devastating WannaCry ransomware.
The ease with which the ransomware spread, exploiting this single vulnerability, highlighted the catastrophic potential of such powerful exploits falling into the wrong hands.
Ethical and Security Implications of Storing and Using Zero-Day Exploits
The ethical debate surrounding the development and storage of zero-day exploits is complex. While the argument for their use in national security operations is often presented, the potential for misuse and catastrophic consequences is undeniable. Storing such powerful tools creates an inherent risk of leakage, as evidenced by the EternalBlue case. The potential for these exploits to fall into the hands of criminal organizations, state-sponsored actors, or even individual hackers with malicious intent, presents a significant threat to global cybersecurity.
The lack of transparency surrounding the NSA’s zero-day exploit program only exacerbates these concerns, hindering effective risk assessment and mitigation strategies. The balance between national security interests and the potential for widespread harm needs careful reconsideration in light of events like WannaCry.
Potential Consequences of Irresponsible Handling of Zero-Day Exploits
Imagine a scenario where a highly sophisticated zero-day exploit, capable of compromising critical infrastructure systems such as power grids or financial institutions, is leaked. The consequences could be devastating. A coordinated attack using such an exploit could lead to widespread power outages, crippling financial markets, disrupting essential services, and causing significant economic and social disruption. Furthermore, the loss of sensitive data, the disruption of critical infrastructure, and the potential for physical harm could lead to long-term instability and widespread panic.
The WannaCry attack, while significant, offers only a glimpse of the potential scale of damage that could result from the irresponsible handling of zero-day exploits. The incident underscores the urgent need for a more responsible approach to the development, storage, and use of such powerful tools, prioritizing global cybersecurity over narrow national security interests. The development of robust vulnerability disclosure programs and a greater emphasis on proactive cybersecurity measures are crucial steps in mitigating these risks.
The Kill Switch and its Impact
The WannaCry ransomware attack, while devastating in its scope, could have been far worse. A crucial factor in limiting its impact was the accidental discovery and activation of a “kill switch,” a feature inadvertently built into the malware itself. This seemingly insignificant detail played a pivotal role in containing the global ransomware outbreak.The kill switch was a domain name hardcoded into the malware.
Its intended purpose remains unclear, perhaps for testing or future control by the attackers. However, a security researcher, accidentally registered the domain name, effectively activating the kill switch. This simple act prevented further infections by halting the malware’s propagation mechanism. The malware checked this domain name; if it resolved, the ransomware would not encrypt files. This unintentional act demonstrated the unpredictable nature of cybersecurity and the critical role of seemingly minor details in large-scale cyberattacks.
The Kill Switch Mechanism
The kill switch functioned as a simple check within the WannaCry malware code. Before encrypting a victim’s files, the malware attempted to connect to a specific domain name. If the connection was successful (meaning the domain was registered), the encryption process would be halted. The accidental registration of this domain, by a researcher who had no prior knowledge of its significance, essentially deactivated the ransomware’s ability to spread further.
This unexpected outcome highlights the importance of proactive security measures, even those that seem insignificant at the time.
The Limitation of the Attack’s Extent
The kill switch’s activation significantly limited the WannaCry attack’s geographic reach and the number of affected systems. While millions of computers were infected before the kill switch was activated, its deployment prevented a far more widespread catastrophe. It’s difficult to quantify precisely how many more systems would have been compromised without the kill switch, but the difference was undoubtedly substantial.
The speed at which the ransomware spread before the kill switch’s activation underscores the potential for catastrophic damage had it remained dormant. The speed and efficiency of the malware’s propagation before the kill switch’s activation showcased the vulnerability of interconnected systems and the potential for rapid and widespread damage.
The Significance of the Accidental Discovery, A synopsis of wannacry ransomware attack on 150 countries
The accidental discovery and activation of the kill switch serve as a potent reminder of the unpredictable nature of cybersecurity incidents. It underscores the crucial role of chance and serendipity in mitigating large-scale cyberattacks. While proactive security measures are essential, this incident highlights the importance of researchers’ vigilance and the unexpected ways in which vulnerabilities can be discovered and exploited—or, in this case, inadvertently neutralized.
The event also brought to light the importance of rigorous code analysis and the potential for unintended consequences in malware design. The accidental nature of the kill switch’s activation should not overshadow the importance of robust security practices and incident response plans.
Final Review
The WannaCry ransomware attack wasn’t just a technological event; it was a societal one, exposing deep vulnerabilities in global cybersecurity infrastructure and highlighting the ethical dilemmas surrounding the use and storage of zero-day exploits. While the accidental activation of the kill switch ultimately limited the damage, the attack served as a crucial lesson. It underscored the need for proactive cybersecurity measures, improved international cooperation, and a renewed focus on responsible disclosure of vulnerabilities.
The shadow of WannaCry remains a potent reminder of the ever-evolving threat landscape and the importance of constant vigilance.
Question & Answer Hub: A Synopsis Of Wannacry Ransomware Attack On 150 Countries
What was the estimated financial cost of the WannaCry attack?
The exact financial cost is difficult to pinpoint, with estimates varying widely depending on the sources and methods of calculation. However, it’s widely accepted that the attack caused billions of dollars in damages worldwide.
Were there any arrests made in connection with the WannaCry attack?
While several individuals were suspected of involvement, confirmed arrests and convictions related directly to the initial WannaCry attack remain limited and publicly available information is scarce.
How did the WannaCry attack affect healthcare systems specifically?
The National Health Service (NHS) in the UK was significantly impacted, with numerous hospitals forced to cancel appointments and divert patients. This highlighted the vulnerability of healthcare systems, which often rely on older, less secure technology.