Adapting Cybersecurity Practices to Modern Threats
Adapting cybersecurity practices to modern threats is more crucial than ever. The digital landscape is constantly evolving, with cybercriminals employing increasingly sophisticated tactics. From AI-powered attacks to intricate supply chain compromises, the threat vectors are multiplying and becoming harder to predict. This post dives deep into the strategies needed to stay ahead of these evolving threats, ensuring your digital assets remain safe and secure in this ever-changing world.
We’ll explore how to build resilient security architectures, implement robust security controls, and empower your workforce with effective security awareness training. We’ll also touch upon the exciting – and sometimes daunting – influence of emerging technologies like AI and quantum computing on the future of cybersecurity. Get ready to bolster your defenses and navigate the complexities of the modern threat landscape!
Evolving Threat Landscape

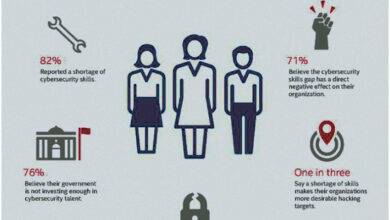
The cybersecurity landscape has undergone a dramatic transformation in the past five years, moving from primarily reactive defenses to a more proactive and predictive approach. This shift is driven by the increasing sophistication of cyberattacks, the rise of artificial intelligence (AI), and the expanding attack surface due to the proliferation of connected devices and cloud services. Understanding these changes is crucial for organizations seeking to effectively protect themselves.
Significant Shifts in Cyber Threats
Over the past five years, we’ve seen a marked increase in the frequency and severity of sophisticated cyberattacks. Ransomware attacks have become significantly more prevalent and damaging, often targeting critical infrastructure and demanding exorbitant ransoms. Phishing attacks have evolved, employing more convincing techniques and leveraging social engineering to bypass security measures. Supply chain attacks, which target vulnerabilities in software or hardware used by multiple organizations, have also gained traction, causing widespread disruption.
Furthermore, the use of readily available hacking tools and services on the dark web has lowered the barrier to entry for malicious actors, resulting in a surge in attacks from less technically skilled individuals. The shift from simple malware to more complex, multi-stage attacks designed to evade detection and exfiltrate sensitive data is also noteworthy.
The Impact of AI and Machine Learning on Cybersecurity
AI and machine learning (ML) are transforming both offensive and defensive cybersecurity strategies. On the offensive side, attackers leverage AI to automate tasks like identifying vulnerabilities, crafting phishing emails, and generating malicious code. AI-powered tools can analyze vast amounts of data to pinpoint weaknesses in systems and develop highly targeted attacks. Defensively, AI and ML are used to enhance threat detection, automate incident response, and improve security posture.
For instance, ML algorithms can analyze network traffic to identify anomalies and potential threats in real-time, allowing security teams to respond quickly. AI-powered security information and event management (SIEM) systems can correlate security alerts from various sources to provide a comprehensive view of security incidents.
Traditional vs. Modern Cyberattacks
Traditional threat vectors, such as viruses and worms, relied on exploiting known vulnerabilities in software. These attacks were often relatively simple to detect and mitigate using signature-based antivirus software. Modern attacks, however, are far more sophisticated. Ransomware, for example, often uses social engineering techniques to trick users into downloading malicious software or clicking on malicious links. Phishing attacks have become incredibly convincing, leveraging personalized information and exploiting human psychology to gain access to sensitive data.
Supply chain attacks are particularly insidious, as they compromise software or hardware used by many organizations, allowing attackers to gain access to a wide range of systems. These modern attacks often employ evasion techniques to bypass traditional security controls, requiring more advanced detection and response strategies.
Top Five Prevalent Cyber Threats and Mitigation Strategies
The following table Artikels five of the most prevalent cyber threats and their corresponding mitigation strategies:
| Threat | Description | Impact | Mitigation Strategies |
|---|---|---|---|
| Ransomware | Malicious software that encrypts files and demands a ransom for their release. | Data loss, financial losses, operational disruption. | Regular backups, strong endpoint protection, employee training, multi-factor authentication. |
| Phishing | Deceptive attempts to obtain sensitive information such as usernames, passwords, and credit card details. | Identity theft, financial fraud, data breaches. | Security awareness training, email filtering, multi-factor authentication, strong password policies. |
| Supply Chain Attacks | Attacks that target vulnerabilities in the supply chain of software or hardware. | Widespread disruption, data breaches, financial losses. | Vendor risk management, secure software development practices, vulnerability scanning. |
| Malware | Malicious software designed to damage, disrupt, or gain unauthorized access to computer systems. | Data loss, system damage, financial losses. | Antivirus software, regular software updates, strong firewalls. |
| Denial-of-Service (DoS) Attacks | Attacks that flood a network or server with traffic, making it unavailable to legitimate users. | Service disruption, financial losses, reputational damage. | Network security monitoring, intrusion detection systems, DDoS mitigation services. |
Adapting Security Architectures

The modern threat landscape demands a fundamental shift in how organizations design and implement their security architectures. Static, perimeter-based defenses are no longer sufficient. We need robust, adaptable systems that can withstand sophisticated attacks and accommodate the increasingly complex IT environments of today. This necessitates a move towards cloud-native security and the adoption of zero-trust principles.Building a robust and adaptable security architecture requires a multi-layered approach that incorporates various security controls and technologies.
This approach prioritizes prevention, detection, and response capabilities to effectively neutralize threats. Furthermore, the architecture must be designed to be flexible and scalable, allowing for easy adaptation to changing business needs and evolving threats.
Cloud Security and Zero Trust Principles
A modern security architecture must embrace cloud security and zero trust principles. Cloud adoption offers scalability and cost-effectiveness, but also introduces new security challenges. Zero trust, on the other hand, assumes no implicit trust granted to any user, device, or network, regardless of location. It verifies every access request before granting access to resources. Implementing a zero-trust model requires strong identity and access management (IAM), micro-segmentation, and continuous monitoring.
For example, a company migrating to a cloud environment could implement multi-factor authentication (MFA) for all users, coupled with granular access control lists (ACLs) to restrict access to specific resources based on user roles and responsibilities. This approach reduces the blast radius of a potential compromise and limits the impact of a successful attack.
Micro-segmentation and Lateral Movement Mitigation
Micro-segmentation divides a network into smaller, isolated segments. This limits the impact of a breach by preventing lateral movement—the ability of an attacker to move from one compromised system to others within the network. By isolating sensitive data and applications, micro-segmentation reduces the attack surface and hinders an attacker’s ability to spread throughout the organization. For instance, a financial institution could micro-segment its network, isolating its core banking systems from other less critical applications.
If a breach occurs in a less critical segment, the attacker’s ability to reach sensitive banking data is significantly reduced.
Migrating Legacy Systems to the Cloud
Migrating legacy systems to the cloud presents both challenges and benefits from a security perspective. Legacy systems often lack the security features of modern applications, making them vulnerable to attacks. However, cloud migration offers the opportunity to modernize these systems and improve their security posture. Challenges include ensuring data security during migration, integrating legacy systems with cloud-native security tools, and addressing potential compliance issues.
Benefits include enhanced security through access controls, improved patching and vulnerability management, and increased resilience through redundancy and disaster recovery capabilities. A phased approach, with careful planning and risk assessment, is crucial for a successful and secure cloud migration.
Securing Remote Work Environments
The rise of remote work has significantly expanded the attack surface for organizations. Securing remote work environments requires a multi-faceted approach, including the use of Virtual Private Networks (VPNs) to encrypt traffic between remote devices and the corporate network, strong password policies, endpoint detection and response (EDR) solutions to monitor and protect endpoints, and regular security awareness training for employees.
For example, a company could implement a VPN with multi-factor authentication and regularly update its security awareness training to educate employees on phishing scams and other common threats. Furthermore, strong endpoint protection software can help detect and prevent malware infections on employee devices.
Enhancing Security Controls
Adapting to the ever-evolving threat landscape requires a robust and proactive approach to security. Simply patching vulnerabilities isn’t enough; we need to bolster our defenses with advanced security controls that can detect, respond to, and mitigate sophisticated attacks. This section delves into key enhancements crucial for modern cybersecurity.
SIEM System Components
A comprehensive Security Information and Event Management (SIEM) system is the cornerstone of a proactive security posture. It aggregates and analyzes security logs from various sources across the network, providing a unified view of security events. Key components include log collection agents that gather data from diverse sources like firewalls, servers, and endpoints; a central data repository for storing and indexing this data; a security information and event management (SIEM) engine that uses sophisticated analytics to detect patterns and anomalies; and a user interface that allows security analysts to visualize data, investigate alerts, and respond to incidents.
Furthermore, a robust SIEM system includes reporting and compliance features, providing valuable insights into security posture and assisting with regulatory compliance. Effective correlation of events from different sources is vital for accurate threat detection. For example, a SIEM might correlate a failed login attempt from an unusual location with a subsequent attempt to access sensitive data, indicating a potential breach.
Multi-Factor Authentication (MFA) and its Effectiveness
Multi-factor authentication (MFA) significantly enhances security by requiring users to provide multiple forms of authentication before gaining access to systems or data. This typically involves a combination of something the user knows (password), something the user has (security token or mobile device), and something the user is (biometrics). The effectiveness of MFA lies in its layered approach; even if one factor is compromised, attackers still need to overcome the others.
For instance, if a user’s password is stolen, an attacker would still need access to the user’s authenticator app or a physical security key to gain access. MFA dramatically reduces the risk of unauthorized access, especially in the face of phishing attacks and credential stuffing. Its widespread adoption across organizations and services demonstrates its crucial role in modern cybersecurity.
Implementing Endpoint Detection and Response (EDR) Solutions
Endpoint Detection and Response (EDR) solutions provide advanced threat detection and response capabilities at the endpoint level (computers, laptops, mobile devices). Implementing an EDR solution involves several steps. First, a thorough assessment of the existing security infrastructure is crucial to identify gaps and ensure compatibility. Second, selecting an appropriate EDR solution based on specific needs and budget considerations is essential.
Third, deployment involves installing the EDR agent on all endpoints, configuring settings, and integrating with existing security tools. Fourth, ongoing monitoring and management are critical for ensuring the solution’s effectiveness, including reviewing alerts, investigating incidents, and updating the system. Finally, regular training for security personnel on using the EDR system is vital for maximizing its potential. For example, an organization might start with a pilot deployment of EDR on a small subset of machines before rolling it out across the entire network.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are network security tools that monitor network traffic for malicious activity. IDS passively monitors network traffic and alerts administrators to suspicious activity, while IPS actively blocks or mitigates threats. Network-based IDPS monitor network traffic at a specific point, like a router or firewall. Host-based IDPS monitor traffic on individual systems.
Signature-based IDPS look for known attack patterns, while anomaly-based IDPS detect deviations from established baselines. IPS offers more proactive protection by actively blocking malicious traffic, whereas IDS only alerts. The choice between IDS and IPS depends on the specific security needs and risk tolerance. A layered approach, using both IDS and IPS, provides comprehensive protection. For example, a network-based IPS might block known malware, while a host-based IDS might detect unusual process activity indicating a zero-day exploit.
Security Awareness Training and Education

In today’s interconnected world, a robust cybersecurity posture relies heavily on informed and vigilant employees. Security awareness training isn’t just a box to tick; it’s a continuous process of education and reinforcement, crucial for mitigating the ever-evolving threats targeting organizations. A comprehensive program empowers employees to become the first line of defense, significantly reducing the risk of successful attacks.A multi-faceted approach is key to effective security awareness training.
It shouldn’t be a single, one-off session but rather an ongoing cycle of learning and reinforcement, tailored to the specific needs and roles within the organization. This includes regular updates to reflect the latest threat landscape and best practices.
Phishing, Social Engineering, and Password Security Training
This module focuses on practical skills to identify and avoid common threats. Employees will learn to recognize phishing emails, SMS messages, and other social engineering tactics. This includes understanding the techniques used by attackers to manipulate individuals into revealing sensitive information or compromising systems. Training will also cover the importance of strong, unique passwords, the risks of password reuse, and the benefits of multi-factor authentication (MFA).
Interactive simulations and real-world examples of phishing attempts will be used to reinforce learning and build practical skills. For instance, trainees will participate in simulated phishing exercises, analyzing suspicious emails and identifying key indicators of compromise (IOCs). Successful completion of these exercises will be a requirement for certification.
Regular Security Audits and Penetration Testing, Adapting cybersecurity practices to modern threats
Regular security audits and penetration testing are vital for identifying vulnerabilities before attackers can exploit them. Security audits provide a comprehensive assessment of an organization’s security posture, reviewing policies, procedures, and technical controls. Penetration testing, on the other hand, simulates real-world attacks to identify exploitable weaknesses. The results of these assessments are used to prioritize remediation efforts and improve the overall security architecture.
For example, a recent penetration test at a financial institution revealed a vulnerability in their web application that could have allowed attackers to steal customer data. This vulnerability was promptly addressed after the penetration test, preventing a potential data breach. The frequency of these assessments should be determined based on risk assessment and regulatory requirements.
Adapting cybersecurity practices to modern threats is crucial, especially with the rise of sophisticated attacks. Building secure applications requires careful consideration, and understanding the development process is key; check out this insightful article on domino app dev the low code and pro code future to see how development methodologies impact security. Ultimately, strong security needs to be baked into every stage, from design to deployment, to effectively combat evolving threats.
Incident Response Planning and Security Breach Handling
A well-defined incident response plan is crucial for minimizing the impact of a security breach. This plan should Artikel clear roles, responsibilities, and procedures for handling various types of security incidents. It should include steps for containment, eradication, recovery, and post-incident activity. Regular drills and simulations help ensure that the plan is effective and that employees are prepared to respond appropriately in a real-world scenario.
For instance, the plan might detail steps for isolating infected systems, collecting forensic evidence, and communicating with stakeholders. A post-incident review will analyze the event to identify areas for improvement in the future.
Communicating Security Incidents to Stakeholders and the Public
Effective communication is critical during a security incident. A pre-defined communication plan should Artikel the process for informing stakeholders, including employees, customers, partners, and regulatory bodies. This plan should specify the information to be communicated, the channels to be used, and the timing of communications. Transparency and honesty are key to maintaining trust and minimizing reputational damage.
For example, a company experiencing a data breach should promptly notify affected individuals and regulatory authorities, providing clear and concise information about the incident and the steps being taken to address it. The communication should also include information on how affected individuals can protect themselves.
Emerging Technologies and Cybersecurity
The rapid advancement of technology presents both incredible opportunities and significant challenges for cybersecurity. Emerging technologies like blockchain, AI, and quantum computing are fundamentally reshaping the threat landscape, demanding equally innovative approaches to security. Understanding the impact of these technologies is crucial for building robust and future-proof security systems.
Blockchain Technology and Data Security
Blockchain’s decentralized and immutable nature offers significant potential for enhancing data security and integrity. By distributing data across a network of nodes, blockchain makes it extremely difficult for attackers to alter or delete information without detection. This is particularly relevant for sensitive data like medical records or financial transactions. The cryptographic hashing and consensus mechanisms used in blockchain ensure that any tampering is immediately identified, providing a high level of trust and transparency.
For example, the use of blockchain in supply chain management can provide verifiable provenance of goods, reducing the risk of counterfeiting and fraud. Furthermore, blockchain-based digital identity systems can enhance user authentication and privacy, reducing reliance on centralized, vulnerable databases.
Artificial Intelligence in Cyber Threat Detection and Response
Artificial intelligence is revolutionizing cybersecurity by enabling faster and more accurate detection and response to cyber threats. AI algorithms can analyze vast amounts of data from various sources, identifying patterns and anomalies that might indicate malicious activity. This includes detecting phishing emails, malware infections, and intrusion attempts. AI-powered security information and event management (SIEM) systems can correlate events across different systems, providing a comprehensive view of the security landscape.
Moreover, AI can automate incident response, such as isolating infected systems or blocking malicious traffic, significantly reducing the time it takes to contain a breach. For instance, AI is already being used to detect and prevent zero-day exploits, where vulnerabilities are unknown until they are exploited.
Extended Detection and Response (XDR) for Improved Threat Visibility
Extended Detection and Response (XDR) represents a significant advancement in threat detection and response capabilities. Unlike traditional security solutions that focus on individual endpoints or network segments, XDR provides a unified view of the entire security landscape by integrating data from various sources, including endpoints, networks, cloud environments, and security tools. This holistic approach allows security teams to correlate events across different systems, identify complex attacks that might otherwise go undetected, and respond more effectively to threats.
For example, XDR can detect lateral movement within a network, identifying attackers who have already compromised one system and are attempting to access other systems. This improved visibility and context enables faster incident response and reduces the impact of cyberattacks.
Quantum Computing’s Impact on Cybersecurity
Quantum computing, while still in its early stages, presents both significant opportunities and challenges for cybersecurity. On the offensive side, quantum computers have the potential to break widely used encryption algorithms, such as RSA and ECC, which are currently used to secure sensitive data and communications. This would have catastrophic consequences for online security. However, quantum computing also offers the potential for developing new, more robust cryptographic techniques, resistant to attacks from both classical and quantum computers.
For example, post-quantum cryptography (PQC) algorithms are currently under development and are being standardized to replace existing algorithms vulnerable to quantum attacks. The race is on to develop both quantum-resistant cryptography and quantum-based security solutions before malicious actors can exploit the power of quantum computing to break existing security measures. The development of quantum key distribution (QKD) offers a promising path towards secure communication, leveraging the principles of quantum mechanics to guarantee secure key exchange.
Legal and Regulatory Compliance: Adapting Cybersecurity Practices To Modern Threats
Navigating the complex world of cybersecurity is no longer just about protecting data; it’s about adhering to a growing web of legal and regulatory requirements. Failure to comply can lead to hefty fines, reputational damage, and even criminal charges. Understanding and implementing the necessary safeguards is crucial for any organization, regardless of size or industry.
Key Requirements of GDPR, CCPA, and HIPAA
These three regulations – the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA) – represent different but equally important facets of data protection. GDPR, a European Union regulation, focuses on the protection of personal data of EU citizens. CCPA, a California state law, grants California residents similar rights regarding their personal information.
HIPAA, a US federal law, specifically protects the privacy and security of Protected Health Information (PHI). Key requirements often overlap, focusing on data minimization, purpose limitation, data security, and individual rights (such as the right to access, rectification, and erasure). For example, all three require organizations to implement appropriate technical and organizational measures to ensure the security of personal data, including encryption, access controls, and regular security assessments.
The specific requirements, however, vary based on the type of data handled and the jurisdiction.
Data Loss Prevention (DLP) and Regulatory Compliance
Data loss prevention (DLP) plays a vital role in meeting regulatory compliance. DLP solutions employ various techniques, including data classification, monitoring, and prevention mechanisms, to identify and prevent sensitive data from leaving the organization’s control. This includes preventing unauthorized access, copying, or transmission of data. For example, a DLP system might block an attempt to email a file containing PHI outside the organization’s network or flag a user attempting to copy sensitive customer data to a USB drive.
Effective DLP is essential for demonstrating compliance with regulations like GDPR, CCPA, and HIPAA, which all mandate robust data security measures to prevent unauthorized data breaches.
Implications of Data Breaches and Legal Consequences
Data breaches can have devastating consequences for organizations. Beyond the financial costs of remediation and notification, organizations face significant legal repercussions. Depending on the nature and scope of the breach, penalties can range from substantial fines (as seen with GDPR’s potential fines of up to €20 million or 4% of annual global turnover) to lawsuits from affected individuals and regulatory investigations.
Reputational damage can also be severe, leading to loss of customer trust and business opportunities. For instance, Equifax’s 2017 data breach resulted in billions of dollars in fines, legal settlements, and reputational harm.
Checklist for Ensuring Compliance with Cybersecurity Regulations
Implementing a robust cybersecurity program is crucial for compliance. A checklist can aid in this process. This is not exhaustive and should be adapted to the specific requirements of each regulation and the organization’s context.
- Data Inventory and Classification: Conduct a thorough inventory of all personal data and classify it according to sensitivity.
- Risk Assessment: Regularly assess the risks to personal data and implement appropriate security controls.
- Data Security Controls: Implement technical and organizational security measures, including access controls, encryption, and data backups.
- Data Loss Prevention (DLP): Implement DLP solutions to prevent unauthorized data exfiltration.
- Incident Response Plan: Develop and regularly test an incident response plan to handle data breaches effectively.
- Employee Training: Provide regular security awareness training to employees.
- Data Subject Rights: Establish processes for handling data subject requests (e.g., access, rectification, erasure).
- Vendor Management: Implement due diligence when selecting and managing third-party vendors that handle personal data.
- Regular Audits and Monitoring: Conduct regular audits and monitoring to ensure ongoing compliance.
- Documentation: Maintain comprehensive documentation of all security policies, procedures, and activities.
Final Review
Staying secure in today’s digital world requires a proactive and adaptable approach. By understanding the evolving threat landscape, implementing robust security architectures, enhancing security controls, and investing in comprehensive security awareness training, organizations can significantly reduce their vulnerability to cyberattacks. Remember, cybersecurity isn’t a destination, it’s an ongoing journey that demands continuous learning, adaptation, and a commitment to staying ahead of the curve.
The future of cybersecurity is dynamic, and so must our defenses be!
Question Bank
What is the biggest cybersecurity threat facing organizations today?
It’s difficult to pinpoint one single biggest threat, as the landscape is constantly shifting. However, ransomware, phishing attacks, and supply chain compromises consistently rank among the most prevalent and damaging.
How can I improve my employees’ cybersecurity awareness?
Regular security awareness training, phishing simulations, and clear communication about security policies are crucial. Make it engaging and relatable, and reinforce good habits consistently.
What is the role of AI in cybersecurity?
AI plays a dual role: it can be used by attackers to automate attacks, but also by defenders to detect and respond to threats more effectively through anomaly detection and threat prediction.
How often should I update my security software?
Security software updates should be applied as soon as they are released. These updates often contain critical patches that address newly discovered vulnerabilities.