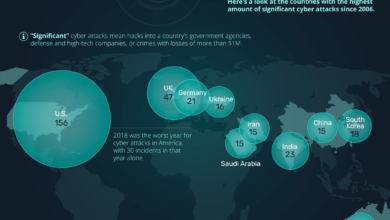
Addressing Financial Organizations Digital Demands Securely
Addressing financial organizations digital demands while avoiding cyber threats – Addressing financial organizations’ digital demands while avoiding cyber threats is a high-stakes balancing act. The rapid shift to digital banking has opened incredible opportunities for efficiency and customer experience, but it’s also created a vast, tempting landscape for cybercriminals. This post delves into the challenges and solutions, exploring everything from the latest threats to the most effective security measures.
We’ll uncover how financial institutions are navigating this complex world, striking a balance between innovation and security to protect themselves and their customers.
We’ll examine the key digital transformation initiatives reshaping the financial industry, highlighting the pressures driving this change and comparing traditional banking models to their modern, digital counterparts. Then, we’ll dive into the dark side, exploring the prevalent cyber threats—from phishing scams to sophisticated ransomware attacks—and their devastating consequences. This includes a look at the regulatory landscape and the crucial role of compliance.
Finally, we’ll unpack practical strategies for bolstering cybersecurity, emphasizing the importance of employee training, advanced security technologies, and proactive incident response planning. The goal? To paint a clear picture of how financial institutions can thrive in the digital age without compromising their security.
Understanding the Digital Demands of Financial Organizations
The financial services industry is undergoing a radical transformation, driven by rapid technological advancements and evolving customer expectations. This shift necessitates a deep understanding of the digital demands placed upon financial organizations, particularly in the context of mitigating ever-present cyber threats. Failure to adapt risks not only financial losses but also reputational damage and loss of customer trust.The Evolving Technological Landscape and Digital Transformation InitiativesThe financial landscape is being reshaped by several key technological trends.
Cloud computing offers scalability and cost-effectiveness, enabling institutions to process vast amounts of data and deploy new services rapidly. Artificial intelligence (AI) and machine learning (ML) are revolutionizing fraud detection, risk management, and personalized customer service. Big data analytics provide insights into customer behavior, enabling targeted marketing and improved product development. Blockchain technology offers the potential for enhanced security and transparency in transactions.
Finally, the rise of open banking APIs fosters innovation and competition by enabling third-party developers to access financial data and build new applications. Financial organizations are responding by implementing various digital transformation initiatives, including upgrading legacy systems, investing in cybersecurity infrastructure, adopting agile development methodologies, and fostering a data-driven culture.Pressure for Technological AdoptionThe pressure on financial organizations to adopt new technologies is immense.
Customers expect seamless, personalized digital experiences, mirroring those offered by other industries. Competition is fierce, with fintech companies disrupting traditional models and offering innovative products and services. Regulatory requirements, such as those related to data privacy and security, also necessitate technological upgrades. Furthermore, improving operational efficiency and reducing costs are crucial for maintaining profitability in a highly competitive environment.
Balancing the need for rapid digital transformation in financial organizations with robust cybersecurity is a constant challenge. To meet these demands efficiently, many are turning to innovative development approaches, such as those explored in this insightful article on domino app dev the low code and pro code future , which highlights how streamlined development can enhance security. Ultimately, faster development cycles, coupled with rigorous security protocols, are key to successfully navigating this complex landscape.
Adopting new technologies allows financial institutions to automate processes, reduce manual errors, and optimize resource allocation. This leads to improved efficiency and better allocation of resources. For example, the use of AI-powered chatbots can significantly reduce customer service costs while simultaneously improving response times and customer satisfaction.
Comparison of Traditional and Modern Digital Banking Models
| Feature | Traditional Banking Model | Modern Digital Banking Model |
|---|---|---|
| Service Delivery | Primarily branch-based, limited online access | Omni-channel approach, seamless integration of online, mobile, and branch services |
| Customer Interaction | Face-to-face interactions, limited self-service options | Personalized digital experiences, AI-powered chatbots, 24/7 online support |
| Product Offering | Limited range of standardized products | Diverse range of customized products and services, tailored to individual needs |
| Data Management | Manual processes, limited data analytics capabilities | Advanced data analytics, real-time insights into customer behavior and market trends |
Identifying Key Cyber Threats Facing Financial Organizations

The digital transformation of the financial sector has brought unparalleled efficiency and convenience, but it’s also opened the door to a wider range of sophisticated cyber threats. These threats, if successful, can lead to significant financial losses, reputational damage, and regulatory penalties for financial institutions of all sizes. Understanding the nature and impact of these threats is crucial for effective mitigation strategies.
Financial organizations face a constantly evolving threat landscape, making proactive cybersecurity a non-negotiable priority. The sheer volume and complexity of attacks demand a multi-layered defense, encompassing technological safeguards, robust security protocols, and well-trained personnel. Ignoring these threats can have catastrophic consequences.
Types of Cyber Threats Targeting Financial Institutions
Financial institutions are prime targets for various cyberattacks due to the sensitive data they hold and the significant financial resources they manage. These attacks can be broadly categorized, though often overlap in their methods and objectives.
- Phishing and Social Engineering: These attacks manipulate individuals into revealing sensitive information, such as usernames, passwords, and credit card details, often through deceptive emails, websites, or phone calls. The success of these attacks relies on human error, making employee training a critical component of defense.
- Malware: This encompasses a broad range of malicious software, including viruses, worms, Trojans, and spyware. Malware can steal data, disrupt operations, and encrypt files (ransomware). Sophisticated malware can evade detection for extended periods, causing significant damage before discovery.
- Ransomware: A particularly damaging form of malware that encrypts an organization’s data, rendering it inaccessible unless a ransom is paid. The impact extends beyond the financial cost of the ransom itself; it includes downtime, data loss, and reputational harm.
- Denial-of-Service (DoS) Attacks: These attacks flood a target system with traffic, making it unavailable to legitimate users. While not directly stealing data, DoS attacks can severely disrupt operations, leading to financial losses and customer dissatisfaction.
- Insider Threats: Malicious or negligent actions by employees or contractors can pose a significant risk. This includes theft of data, sabotage, or unintentional breaches due to poor security practices.
Financial and Reputational Impact of Cyberattacks
The consequences of a successful cyberattack on a financial organization can be devastating. Financial losses can be substantial, encompassing direct costs (ransom payments, investigation, remediation), indirect costs (lost business, legal fees), and the cost of restoring systems and data. Beyond the financial impact, reputational damage can be long-lasting, eroding customer trust and impacting the organization’s ability to attract and retain clients.
A damaged reputation can lead to decreased profitability and even insolvency.
Regulatory Landscape and Compliance Requirements
The financial sector is heavily regulated, with stringent cybersecurity requirements designed to protect customer data and maintain the stability of the financial system. Regulations such as GDPR (General Data Protection Regulation) in Europe and various state and federal laws in the US mandate specific security controls and data protection measures. Non-compliance can result in hefty fines and legal repercussions.
Staying abreast of these evolving regulations is paramount.
Hypothetical Cyberattack Scenario: Targeting a Retail Bank
Imagine a sophisticated phishing campaign targeting employees of a large retail bank. The attackers use a highly convincing email mimicking an internal communication, containing a malicious attachment. Employees who open the attachment unknowingly install malware that grants the attackers access to the bank’s internal network. The malware allows the attackers to steal customer data, including account numbers, social security numbers, and addresses.
They then use this data to conduct fraudulent transactions, leading to significant financial losses for the bank and its customers. The reputational damage from this breach could be substantial, impacting the bank’s customer base and its overall market standing. The subsequent investigation and remediation efforts would incur significant costs.
Implementing Robust Cybersecurity Measures

The digital transformation of financial organizations has brought unprecedented opportunities, but it has also amplified the risk of cyberattacks. Implementing robust cybersecurity measures is no longer a luxury; it’s a fundamental necessity for survival and maintaining customer trust. A multi-layered approach, encompassing technology, processes, and people, is crucial for effective protection.
Financial institutions face a constantly evolving threat landscape. Therefore, a proactive and adaptive cybersecurity strategy is paramount. This involves continuous monitoring, regular updates, and a commitment to staying ahead of emerging threats. This section will delve into the key components of a comprehensive cybersecurity plan for financial organizations.
Cybersecurity Best Practices for Financial Institutions
A robust cybersecurity posture requires a multifaceted approach. The following best practices are essential for minimizing vulnerabilities and protecting sensitive data:
- Strong Authentication and Authorization: Implement multi-factor authentication (MFA) for all systems and access points. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access, even if they obtain usernames and passwords.
- Data Encryption: Encrypt sensitive data both in transit and at rest. This ensures that even if data is compromised, it remains unreadable to unauthorized individuals. Encryption standards like AES-256 should be employed.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities before attackers can exploit them. This proactive approach helps to strengthen defenses and prevent breaches.
- Vulnerability Management: Establish a robust vulnerability management program to identify, assess, and remediate security vulnerabilities in a timely manner. This includes patching systems regularly and using vulnerability scanners.
- Network Security: Implement firewalls, intrusion detection/prevention systems (IDS/IPS), and other network security controls to monitor and protect against malicious network traffic. This creates a perimeter defense against external threats.
- Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving the organization’s control. This includes monitoring data transfers and blocking unauthorized access attempts.
- Access Control: Implement the principle of least privilege, granting users only the access they need to perform their jobs. This limits the damage that can be caused if an account is compromised.
- Security Information and Event Management (SIEM): Utilize SIEM systems to collect and analyze security logs from various sources, providing real-time visibility into security events and enabling faster incident response.
Advanced Security Technologies
Beyond traditional security measures, advanced technologies offer enhanced protection against sophisticated cyber threats:
- AI-powered Threat Detection: AI and machine learning algorithms can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, enabling faster detection and response to threats that traditional methods might miss. For example, an AI system might detect unusual login attempts from unfamiliar locations or identify subtle variations in network traffic patterns that signal a potential attack.
- Blockchain for Secure Transactions: Blockchain technology can enhance the security and transparency of financial transactions by providing an immutable record of transactions. This makes it more difficult for attackers to alter or tamper with transaction data, reducing the risk of fraud.
- Zero Trust Security: Zero trust security models assume no implicit trust, verifying every user and device before granting access to resources. This approach minimizes the impact of breaches by limiting lateral movement within the network.
Employee Training and Awareness Programs, Addressing financial organizations digital demands while avoiding cyber threats
Human error remains a significant vulnerability in cybersecurity. Comprehensive employee training and awareness programs are crucial to mitigate this risk:
Regular training sessions should cover topics such as phishing awareness, password security, social engineering tactics, and safe browsing practices. Simulated phishing attacks can help employees identify and report suspicious emails. Furthermore, clear policies and procedures should be established for reporting security incidents.
Incident Response Planning
A well-defined incident response plan is essential for minimizing the impact of a cyberattack. The plan should Artikel the steps to be taken in case of a security breach:
- Preparation: Identify potential threats, establish communication protocols, and designate roles and responsibilities.
- Detection and Analysis: Implement monitoring tools to detect security incidents promptly and analyze the nature and scope of the attack.
- Containment: Isolate affected systems and prevent further damage. This might involve disconnecting infected machines from the network or shutting down services.
- Eradication: Remove malware and restore affected systems to a secure state. This may involve reinstalling software, restoring backups, and patching vulnerabilities.
- Recovery: Restore normal operations and implement measures to prevent future attacks. This might involve reviewing security policies, strengthening controls, and conducting employee training.
- Post-Incident Activity: Conduct a post-incident review to identify lessons learned and improve the organization’s security posture.
Balancing Innovation and Security
The rapid pace of technological advancement in the financial sector presents a constant challenge: how to embrace innovation while simultaneously safeguarding sensitive data and maintaining operational resilience. This delicate balancing act requires a strategic approach that prioritizes security without stifling progress. Finding the right equilibrium demands a comprehensive understanding of the risks involved and a commitment to proactive security measures.Different approaches to balancing innovation and security exist, each with its own strengths and weaknesses.
A purely security-focused approach might prioritize robust firewalls and strict access controls, but this can hinder agility and the adoption of new technologies. Conversely, an innovation-first approach, while fostering creativity, might leave critical vulnerabilities exposed. The optimal strategy lies in finding a middle ground, integrating security considerations into every stage of the innovation lifecycle.
Security-First vs. Innovation-First Approaches
A “security-first” approach emphasizes rigorous security testing and validation before deploying new technologies. This reduces the risk of introducing vulnerabilities, but it can slow down the development process and increase costs. A “innovation-first” approach prioritizes rapid development and deployment, often relying on iterative updates and patching to address security issues as they arise. This approach is faster and more adaptable, but it may leave systems vulnerable for extended periods.
Many organizations now adopt a “DevSecOps” model, integrating security practices throughout the software development lifecycle, striking a balance between speed and security.
Challenges of Integrating New Technologies While Maintaining a Strong Security Posture
Integrating new technologies, such as AI-powered fraud detection systems or blockchain-based payment platforms, presents significant security challenges. These technologies often introduce new attack surfaces and require specialized security expertise to manage effectively. For example, the use of cloud-based services introduces dependencies on third-party providers, necessitating rigorous due diligence and robust security agreements. Moreover, integrating these technologies requires careful consideration of data privacy regulations and compliance requirements.
The complexity of modern IT infrastructures further complicates this challenge, requiring robust security information and event management (SIEM) systems to monitor and respond to threats effectively.
Trade-offs Between Security and User Experience in Digital Banking Solutions
Balancing security with a positive user experience is crucial for the success of digital banking solutions. Strong security measures, such as multi-factor authentication and biometric verification, can enhance security but may also create friction for users. For instance, overly complex authentication processes can lead to user frustration and abandonment of digital banking services. Finding the right balance requires careful consideration of user needs and preferences, as well as the development of user-friendly security features that are both effective and convenient.
A good example is the use of intuitive mobile applications with built-in security features, minimizing the need for complex passwords or security questions.
Agile Development Methodologies and Adapting to Evolving Cyber Threats
Agile development methodologies, with their iterative and incremental approach, offer a significant advantage in adapting to evolving cyber threats. The ability to quickly respond to emerging vulnerabilities and integrate new security features is critical in the face of constantly evolving threat landscapes. By incorporating security testing and feedback loops into each iteration, organizations can identify and address vulnerabilities early in the development process, reducing the risk of significant security breaches.
For instance, the rapid adoption of agile methodologies by financial institutions allowed them to quickly adapt to the increased threat of ransomware attacks by incorporating more robust data backup and recovery strategies.
The Role of Data Security and Privacy
In today’s digital financial landscape, data security and privacy are not just best practices—they’re absolute necessities. The sheer volume of sensitive customer information handled by financial organizations makes them prime targets for cyberattacks. A breach can lead to significant financial losses, reputational damage, and legal repercussions. Protecting this data is paramount, requiring a multi-faceted approach encompassing robust security measures and a deep understanding of relevant regulations.Data encryption and access control are foundational elements of a strong data security posture.
Encryption transforms sensitive data into an unreadable format, rendering it useless to unauthorized individuals even if a breach occurs. Access control mechanisms, such as multi-factor authentication and role-based access, limit who can view and modify specific data, minimizing the potential impact of a compromised account. These measures work in tandem to create a layered defense against data breaches.
Data Encryption and Access Control Mechanisms
Data encryption involves converting readable data into an unreadable format, called ciphertext, using an encryption algorithm and a key. Only those possessing the correct decryption key can access the original data. There are various encryption methods, including symmetric encryption (using the same key for encryption and decryption) and asymmetric encryption (using separate keys for encryption and decryption, like with RSA).
Access control, on the other hand, focuses on restricting access to sensitive data based on user roles and permissions. This might involve assigning different levels of access to employees based on their job functions, limiting access to specific systems or databases, or implementing strong authentication measures like multi-factor authentication (MFA) to verify user identities. For example, a bank teller might only have access to customer account details, while a system administrator would have broader access for maintenance purposes.
The combination of robust encryption and granular access control significantly reduces the risk of data exposure.
Legal and Ethical Considerations of Data Privacy
The financial sector is heavily regulated, with numerous laws and regulations designed to protect customer data privacy. These regulations, such as GDPR in Europe and CCPA in California, mandate specific security measures, data handling practices, and procedures for handling data breaches. Beyond legal compliance, ethical considerations demand that financial institutions treat customer data with the utmost respect and transparency.
Building and maintaining customer trust is crucial, and data privacy is a cornerstone of that trust. Failure to comply with regulations or uphold ethical standards can lead to significant fines, reputational damage, and loss of customer confidence. For instance, a failure to properly secure customer data leading to a breach could result in significant legal action and loss of customer trust, potentially leading to business failure.
Best Practices for Managing and Protecting Customer Data
Managing and protecting customer data requires a proactive and comprehensive approach. This includes regular security assessments and penetration testing to identify vulnerabilities, employee training programs to raise awareness of security risks and best practices, and the implementation of robust incident response plans to effectively manage and mitigate data breaches. Data minimization—collecting only the necessary data and retaining it only for as long as needed—is also a critical best practice.
Regular data backups and disaster recovery planning ensure business continuity in the event of a data loss incident. Finally, strong data governance policies and procedures are essential for establishing clear accountability and ensuring compliance with relevant regulations.
Strategies for Complying with Data Privacy Regulations
Implementing these strategies requires a dedicated team and ongoing investment in security infrastructure and personnel. Regular audits and assessments are crucial to ensure compliance and adapt to evolving threats.
- Conduct regular risk assessments and vulnerability scans.
- Implement robust data encryption and access control mechanisms.
- Develop and maintain comprehensive data privacy policies and procedures.
- Provide regular employee training on data security and privacy best practices.
- Establish a data breach response plan and regularly test its effectiveness.
- Implement strong data governance policies and procedures.
- Regularly review and update security measures to address emerging threats.
- Maintain detailed records of data processing activities and security incidents.
- Ensure compliance with all relevant data privacy regulations.
- Engage in regular audits and assessments to verify compliance.
Future Trends in Financial Cybersecurity
The financial landscape is constantly evolving, driven by digital transformation and increasing reliance on interconnected systems. This creates a dynamic threat environment, requiring financial institutions to proactively anticipate and adapt to emerging cybersecurity challenges. Understanding these future trends is crucial for maintaining the integrity and security of financial data and operations.The next decade will witness a significant escalation in the sophistication and scale of cyberattacks targeting financial organizations.
This necessitates a proactive, multi-layered approach to cybersecurity, incorporating advanced technologies and strategic partnerships.
Emerging Cyber Threats and Vulnerabilities
Financial institutions face a growing number of sophisticated cyber threats. These include advanced persistent threats (APTs), leveraging increasingly complex malware and exploiting zero-day vulnerabilities. Supply chain attacks, targeting third-party vendors and service providers, pose a significant risk, as do the exploitation of vulnerabilities in cloud-based infrastructure and the rise of cryptojacking, where attackers secretly use a victim’s computing resources to mine cryptocurrency.
The increasing prevalence of deepfakes, capable of creating realistic but fraudulent audio and video recordings, presents a new challenge for authentication and fraud prevention. Furthermore, the Internet of Things (IoT) devices, while offering convenience, introduce new attack vectors if not properly secured.
The Role of Artificial Intelligence and Machine Learning in Enhancing Cybersecurity Defenses
Artificial intelligence (AI) and machine learning (ML) are transforming cybersecurity. AI-powered systems can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, significantly improving threat detection and response times. ML algorithms can adapt to evolving attack techniques, providing more robust and proactive security. For instance, AI can be used to detect fraudulent transactions in real-time by identifying unusual spending patterns or geographic locations, preventing financial losses.
Similarly, ML can enhance security information and event management (SIEM) systems, automating the analysis of security logs and alerts to prioritize and address critical threats efficiently.
The Potential Impact of Quantum Computing on the Future of Cybersecurity in Finance
Quantum computing, while still in its early stages, poses a significant long-term threat to current cryptographic methods. Quantum computers, with their immense processing power, could potentially break widely used encryption algorithms, compromising sensitive financial data. Financial institutions need to begin planning for a post-quantum cryptography era, exploring and implementing quantum-resistant algorithms to protect against future attacks. This requires collaboration with researchers and technology providers to develop and deploy these new cryptographic techniques.
The transition will be complex and require substantial investment in infrastructure and expertise.
Visual Representation of the Evolution of Cybersecurity Threats in the Financial Sector Over the Past Decade
Imagine a graph charting the evolution of cyber threats over the past decade. The X-axis represents the years (2013-2023), and the Y-axis represents the complexity and sophistication of attacks. The graph starts with a relatively low and steady line in 2013, representing common attacks like phishing and malware. Around 2015, the line begins to rise sharply, reflecting the increasing prevalence of advanced persistent threats (APTs) and data breaches.
Around 2017-2018, the line becomes steeper and more erratic, indicating the rise of ransomware attacks, cryptojacking, and the exploitation of cloud vulnerabilities. From 2020 onwards, the line shows a significant increase in complexity and frequency, reflecting the emergence of AI-powered attacks, deepfakes, and the growing threat of quantum computing. The overall trend is a steep upward curve, illustrating the exponential growth in the sophistication and scale of cyber threats facing the financial sector.
Different colors could represent different types of attacks (e.g., phishing in blue, ransomware in red, APT in purple), making the visualization more informative.
Closure: Addressing Financial Organizations Digital Demands While Avoiding Cyber Threats

The journey to secure digital transformation in finance is an ongoing one, requiring constant vigilance and adaptation. While the challenges are significant, the solutions are within reach. By embracing a proactive security posture, leveraging cutting-edge technologies, and prioritizing employee training, financial organizations can confidently navigate the digital landscape, fostering innovation while safeguarding their valuable assets and maintaining customer trust.
The future of finance is digital, and with the right strategies, it can also be secure.
Top FAQs
What are the most common types of phishing attacks targeting financial institutions?
Spear phishing (highly targeted attacks), whaling (targeting high-level executives), and clone phishing (mimicking legitimate websites) are particularly common and dangerous.
How can AI and machine learning help improve financial cybersecurity?
AI and ML can analyze vast amounts of data to detect anomalies, predict potential threats, and automate responses, significantly enhancing threat detection and prevention.
What is the role of blockchain in enhancing financial security?
Blockchain’s decentralized and immutable nature can improve the security and transparency of transactions, reducing the risk of fraud and data breaches.
What are some practical steps financial institutions can take to improve employee cybersecurity awareness?
Regular security awareness training, phishing simulations, and clear security policies are crucial. Promoting a security-conscious culture is key.