Advancing API Security An Interview with Richard Bird of Traceable AI
Advancing api security an interview with richard bird of traceable ai – Advancing API Security: An Interview with Richard Bird of Traceable AI – In this insightful conversation, we delve into the critical world of API security with Richard Bird, a leading expert from Traceable AI. We explore the evolving landscape of API threats, the innovative solutions Traceable AI offers, and the best practices developers need to adopt. Get ready to uncover crucial strategies for protecting your organization’s valuable data and systems.
From identifying the top API security threats and vulnerabilities to understanding the future trends shaping this critical field, this interview offers a comprehensive overview of securing your APIs. We’ll explore how Traceable AI’s unique approach differs from traditional methods and uncover actionable insights you can implement today. Prepare to enhance your understanding of API security and learn how to stay ahead of emerging threats.
Introduction to Richard Bird and Traceable AI: Advancing Api Security An Interview With Richard Bird Of Traceable Ai
Richard Bird is a leading figure in the field of API security, bringing a wealth of experience and expertise to the forefront of this rapidly evolving landscape. His background encompasses years of hands-on experience in building and securing complex systems, giving him a unique perspective on the challenges and opportunities within API protection. This deep understanding informs his work at Traceable AI, where he leverages his knowledge to develop innovative solutions.Traceable AI is a company dedicated to solving the critical problem of securing APIs.
Their approach focuses on providing comprehensive visibility and automated threat detection for APIs, moving beyond traditional security methods that often fall short in the dynamic API environment. Traceable AI employs AI-powered analysis to identify and respond to threats in real-time, offering a proactive and efficient solution for organizations struggling to manage the increasing complexity and risk associated with APIs.
They aim to provide a security layer that adapts and learns alongside the evolving API landscape.
The Current API Security Landscape
The current API security landscape is characterized by a significant increase in both the number of APIs deployed and the sophistication of attacks targeting them. The widespread adoption of microservices architecture and cloud-native development has led to an explosion in the number of APIs, creating a larger attack surface. Simultaneously, attackers are becoming increasingly adept at exploiting vulnerabilities in APIs, using techniques like automated scanning and exploitation to identify and leverage weaknesses.
This results in data breaches, service disruptions, and significant financial losses for organizations. The challenge lies in effectively securing this expanding attack surface while maintaining agility and speed of development. Many traditional security solutions struggle to keep pace with the dynamic nature of APIs and the innovative attack vectors used by threat actors. This necessitates a new approach that leverages AI and automation to provide real-time protection and proactive threat detection.
API Security Threats and Vulnerabilities
The world of APIs, while enabling seamless data exchange and powering countless applications, presents a significant attack surface. Understanding the most prevalent threats and the vulnerabilities they exploit is crucial for organizations aiming to secure their digital assets. This section delves into the top three API security threats and explores the vulnerabilities they leverage.
Top Three API Security Threats
Organizations face a multitude of API security risks, but three consistently stand out due to their frequency and potential impact: Broken Authentication, Excessive Data Exposure, and Injection Flaws. These threats often stem from poor API design, inadequate security testing, and a lack of comprehensive security measures.
Broken Authentication, Advancing api security an interview with richard bird of traceable ai
Broken authentication is a top threat, exploiting weaknesses in the mechanisms designed to verify user identities and control access to API resources. Vulnerabilities include using easily guessable passwords, failing to implement multi-factor authentication (MFA), and neglecting proper session management. For example, an attacker might exploit a weak password policy to gain unauthorized access, potentially leading to data breaches or complete system compromise.
Another example is a lack of robust session timeouts, allowing attackers to maintain access even after the legitimate user has logged out.
Excessive Data Exposure
Excessive data exposure occurs when APIs return more data than necessary, exposing sensitive information to unauthorized users. This vulnerability often stems from inadequate input validation and output encoding. A common example is an API returning a user’s full address and credit card information in response to a simple profile request. Attackers can leverage this excessive data exposure to perform identity theft, financial fraud, or other malicious activities.
The lack of proper data masking or anonymization further exacerbates this risk.
Injection Flaws
Injection attacks, such as SQL injection or command injection, exploit vulnerabilities in how an API handles user-supplied data. Attackers inject malicious code into API requests, manipulating database queries or system commands to gain unauthorized access or modify data. For example, an attacker might inject SQL code into a search parameter, allowing them to bypass authentication mechanisms or retrieve sensitive data from the database.
Similarly, command injection can allow attackers to execute arbitrary commands on the server, potentially compromising the entire system. The lack of proper input sanitization and parameterized queries makes APIs particularly vulnerable to these attacks.
Comparison of API Attack Types
Comparing different types of API attacks highlights their unique characteristics and the varying impacts they have on organizations. Injection attacks, as discussed above, directly manipulate the API’s internal logic. Data breaches, often facilitated by broken authentication or excessive data exposure, result in the unauthorized access and exfiltration of sensitive information. Denial-of-service (DoS) attacks, while not directly exploiting vulnerabilities in the API’s logic, overwhelm the API with requests, making it unavailable to legitimate users.
Each attack type requires a different set of mitigation strategies. For instance, preventing injection attacks relies heavily on input validation and parameterized queries, while mitigating data breaches requires robust authentication, authorization, and data masking techniques. DoS attacks often necessitate infrastructure-level defenses, such as rate limiting and distributed denial-of-service (DDoS) mitigation solutions.
Traceable AI’s Solutions for Advancing API Security

Traceable AI offers a comprehensive platform designed to proactively identify and mitigate API security risks. Unlike traditional approaches that often rely on reactive measures after a breach, Traceable AI employs a proactive, AI-powered approach to continuously monitor and analyze API traffic, identifying vulnerabilities and anomalous behavior in real-time. This allows organizations to address potential threats before they can be exploited.Traceable AI’s core functionality centers around its ability to provide complete visibility into API activity.
This visibility allows for the identification of both known and unknown threats, a key differentiator from traditional methods that often struggle with the detection of zero-day exploits. The platform analyzes vast amounts of data, correlating different events to identify patterns and anomalies indicative of malicious activity or vulnerabilities.
Core Functionalities of Traceable AI’s Platform
The Traceable AI platform offers several key functionalities to bolster API security. It utilizes machine learning algorithms to establish a baseline of normal API behavior and then detects deviations from this baseline, flagging potential security incidents. Furthermore, the platform provides comprehensive API inventory management, automatically discovering and mapping APIs within an organization’s infrastructure. This automated discovery significantly reduces the manual effort required for API security management.
Finally, the platform offers detailed reporting and analytics, providing organizations with actionable insights into their API security posture.
Differentiation from Traditional API Security Approaches
Traditional API security solutions often rely on static analysis, penetration testing, and Web Application Firewalls (WAFs). While these methods are valuable, they are often reactive and struggle to keep pace with the evolving threat landscape. Traceable AI differentiates itself through its proactive, AI-powered approach. Instead of simply reacting to known threats, Traceable AI continuously monitors API traffic, learning normal behavior and identifying anomalies that might indicate an attack or vulnerability, even if it’s a previously unknown threat.
This continuous monitoring and anomaly detection provides a significant advantage in identifying and mitigating zero-day exploits and other sophisticated attacks.
Identifying and Mitigating API Security Risks with Traceable AI
Traceable AI helps organizations identify and mitigate API security risks through several key mechanisms. The platform’s real-time monitoring capabilities provide immediate alerts on suspicious activity, allowing for swift responses to potential threats. Its detailed analytics provide insights into the root cause of security incidents, facilitating faster remediation. The platform’s automated API discovery and inventory management features streamline the process of identifying and securing all APIs within an organization’s ecosystem.
Finally, Traceable AI’s integration with existing security tools allows for a cohesive and comprehensive security posture.
Comparison of Traceable AI with a Competitor
The following table compares Traceable AI’s features with those of a fictional competitor, “SecureAPI.” Note that this is a simplified comparison and the actual feature sets may vary.
| Feature | Traceable AI | SecureAPI |
|---|---|---|
| AI-Powered Anomaly Detection | Yes, real-time detection of unknown threats | No, relies primarily on signature-based detection |
| Automated API Discovery | Yes, automatic mapping of APIs across the infrastructure | No, requires manual configuration and updates |
| Real-time Threat Alerts | Yes, immediate notifications on suspicious activity | No, relies on scheduled scans and reporting |
| Comprehensive Reporting and Analytics | Yes, detailed insights into API security posture | Limited reporting, focusing mainly on known vulnerabilities |
Best Practices for Securing APIs
Building secure APIs is paramount in today’s interconnected world. A single vulnerability can expose sensitive data, disrupt services, and severely damage an organization’s reputation. Implementing robust security measures from the initial design phase is crucial, not an afterthought. This requires a multifaceted approach encompassing secure coding practices, rigorous testing, and a proactive security mindset.
The following best practices provide a strong foundation for developers to build and maintain secure APIs.
Five Essential API Security Best Practices
Implementing these five best practices significantly reduces the risk of API-related security breaches. They cover crucial aspects of API design, development, and deployment, ensuring a more secure and resilient system.
- Input Validation and Sanitization: Always validate and sanitize all inputs received by your API. Never trust data from external sources. This prevents injection attacks (SQL injection, cross-site scripting, etc.) by ensuring that all data conforms to expected formats and data types before being processed. For example, check string lengths, validate email addresses using regular expressions, and escape special characters before using data in database queries.
- Authentication and Authorization: Implement strong authentication mechanisms, such as OAuth 2.0 or OpenID Connect, to verify the identity of clients accessing your API. Authorization ensures that only authenticated clients have access to specific resources and functionalities. Use granular access control to limit privileges based on user roles and permissions. For instance, a read-only user should not have the ability to modify data.
- Rate Limiting and Throttling: Protect your API from denial-of-service (DoS) attacks by implementing rate limiting and throttling. This limits the number of requests a client can make within a specific timeframe. This prevents malicious actors from overwhelming your API and disrupting service for legitimate users. Consider using sliding windows or token bucket algorithms for effective rate limiting.
- Secure Communication: Always use HTTPS to encrypt communication between clients and your API. This protects sensitive data in transit from eavesdropping and tampering. Ensure that your certificates are properly configured and regularly updated. Consider using TLS 1.3 or later for the strongest encryption.
- Regular Security Audits and Updates: Conduct regular security audits and penetration testing to identify vulnerabilities in your API. Stay updated with the latest security patches and best practices. Use automated security scanning tools to detect potential issues early in the development lifecycle. Regularly update your API’s dependencies and libraries to address known vulnerabilities.
API Security Testing Methodologies
Thorough testing is essential to identify and mitigate API security vulnerabilities before deployment. A multi-layered approach incorporating various testing methodologies is highly recommended.
- Static Application Security Testing (SAST): SAST tools analyze the source code to identify potential security flaws without actually executing the code. They can detect vulnerabilities such as SQL injection, cross-site scripting, and insecure authentication mechanisms. Examples include SonarQube and Checkmarx.
- Dynamic Application Security Testing (DAST): DAST tools test the running application to identify vulnerabilities by simulating attacks. They can detect vulnerabilities that are not apparent in the source code, such as insecure configurations and improper input handling. Examples include OWASP ZAP and Burp Suite.
- Interactive Application Security Testing (IAST): IAST combines the benefits of SAST and DAST by instrumenting the application to detect vulnerabilities in real-time. It provides detailed information about the location and nature of vulnerabilities. Examples include Contrast Security and AppDetective.
- Penetration Testing: Penetration testing involves simulating real-world attacks to identify vulnerabilities. Ethical hackers attempt to breach the API’s security to identify weaknesses. This provides a realistic assessment of the API’s security posture.
The Future of API Security

The API economy is booming, and with it, the attack surface for malicious actors is expanding exponentially. Predicting the future of API security requires understanding current trends and extrapolating their likely impact. While crystal balls are unreliable, analyzing current vulnerabilities and emerging technologies allows us to reasonably forecast the key challenges and solutions that will shape the landscape in the coming years.
Three Significant Trends Shaping the Future of API Security
The next five years will witness a convergence of factors significantly impacting API security. These trends will force organizations to adapt and innovate their security strategies to remain resilient against increasingly sophisticated threats.
- AI-Powered Threat Detection and Response: The use of artificial intelligence and machine learning (AI/ML) in API security will move beyond simple anomaly detection. We’ll see more sophisticated systems capable of predicting attacks, proactively identifying vulnerabilities, and automatically responding to threats in real-time. This is driven by the increasing volume and complexity of API traffic, making manual analysis impractical. For example, AI could learn to identify subtle patterns in API calls indicative of a specific type of attack, such as a data exfiltration attempt, even before it becomes a full-blown breach.
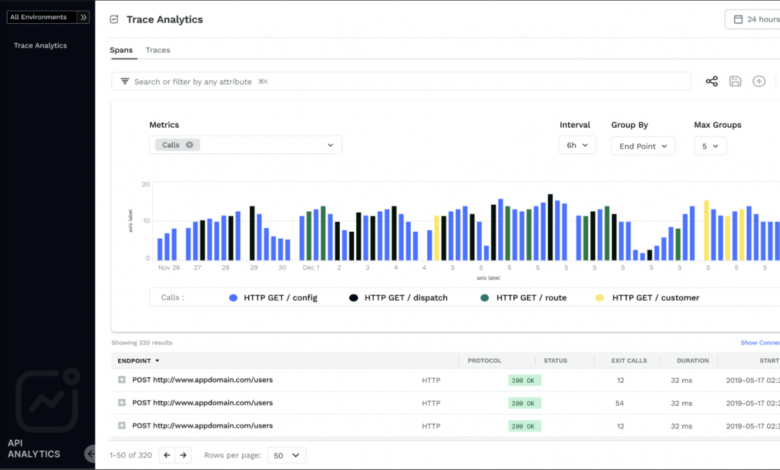
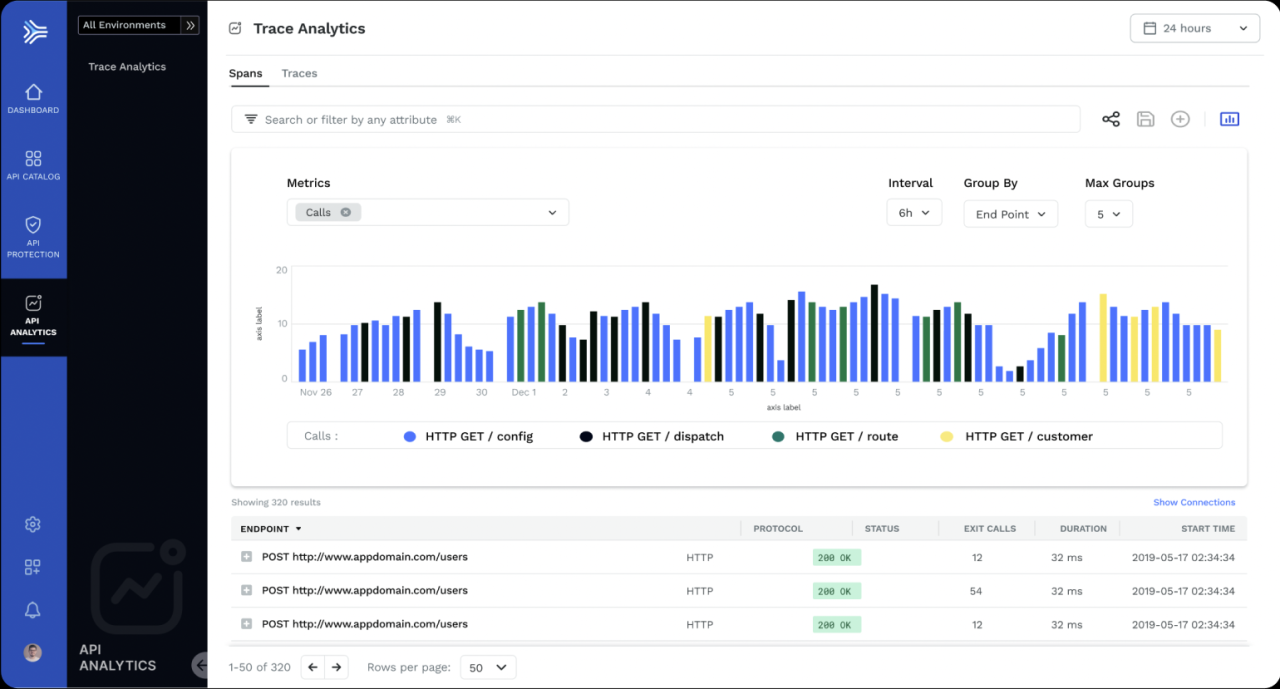
- Increased Focus on API Observability and Runtime Protection: Traditional security measures often fall short in the dynamic environment of APIs. The emphasis will shift towards runtime protection, enabling organizations to monitor API behavior in real-time and react to threats as they emerge. This includes detailed tracing of API calls, robust logging, and advanced threat intelligence integration to provide comprehensive visibility and control. Imagine a scenario where a compromised internal API is used to leak sensitive data.
Runtime protection allows for immediate detection and mitigation, limiting the damage.
- Shift-Left Security and DevSecOps Integration: Integrating security practices throughout the entire software development lifecycle (SDLC) will become paramount. This “shift-left” approach emphasizes proactively embedding security into the design and development phases, rather than addressing vulnerabilities after deployment. DevSecOps methodologies will be crucial for automating security testing, vulnerability scanning, and continuous monitoring of APIs. This proactive approach reduces the likelihood of vulnerabilities ever reaching production, minimizing the potential for breaches.
Impact on Businesses and Organizations
These trends will significantly impact businesses and organizations in several ways. The adoption of AI-powered security will require investments in new technologies and expertise, but it will also lead to more efficient and effective security operations. Increased observability and runtime protection will enable faster response times to threats, reducing the potential financial and reputational damage from breaches. Finally, the shift-left approach will streamline development processes while strengthening overall security posture, potentially reducing development costs in the long run by preventing costly fixes later in the cycle.
Failure to adapt to these trends will leave organizations vulnerable to increasingly sophisticated attacks and potentially crippling consequences.
Hypothetical API Security Breach Scenario and Traceable AI’s Role
Imagine a large e-commerce company relying heavily on APIs for its operations. A malicious actor gains access to a poorly secured internal API used for inventory management. This API lacks robust authentication and authorization mechanisms, and the actor uses automated tools to exploit a known vulnerability. The attacker can manipulate inventory data, creating fake orders and diverting shipments.
Traditional security measures miss this attack due to its subtlety and the high volume of legitimate API traffic.However, Traceable AI’s platform, with its advanced AI-powered anomaly detection and runtime protection capabilities, identifies the suspicious activity. The system flags the unusual patterns in API calls, such as an abnormally high volume of orders from a single IP address and the modification of inventory levels without proper authorization.
Traceable AI automatically alerts the security team, providing detailed insights into the attack, including the source, the affected APIs, and the potential impact. The security team can then quickly respond, blocking the malicious actor, restoring the integrity of the inventory data, and preventing further damage. This scenario illustrates how a proactive, AI-driven approach to API security can effectively mitigate the risk of significant breaches and protect businesses from substantial financial and reputational losses.
Case Studies and Real-World Examples
Illustrating the effectiveness of API security solutions requires looking at both hypothetical scenarios and considering how real-world organizations have benefited. Below, we’ll explore a fictional case study highlighting the success of Traceable AI and then examine a visualization of the positive impact of robust API security.
Successful Implementation of Traceable AI: Global Retail Giant
Imagine a large global retail company, “ShopWorld,” facing increasing API attack surface due to rapid expansion of their online services and microservices architecture. They struggled with detecting and responding to sophisticated attacks targeting their APIs, leading to data breaches and significant financial losses. Their existing security measures proved insufficient against advanced threats. ShopWorld implemented Traceable AI’s solution, which provided comprehensive API visibility, anomaly detection, and automated response capabilities.
So, I was just reading this fascinating interview with Richard Bird of Traceable AI about advancing API security – seriously insightful stuff! It got me thinking about how crucial robust security is, especially as we see more low-code/no-code development taking off, like what’s discussed in this great article on domino app dev the low code and pro code future.
The ease of app creation needs to be matched by equally simple, yet powerful, security measures. Getting back to Richard’s interview, his points on proactive API protection really resonated with me in light of this increasing accessibility.
The solution helped them identify and mitigate numerous vulnerabilities, including unauthorized access attempts, data exfiltration attempts, and injection attacks. The key challenges were integrating the solution with their existing infrastructure and training their security team to effectively utilize the platform’s advanced features. The results were dramatic: a 75% reduction in API-related security incidents within six months, a significant improvement in mean time to resolution (MTTR) for security incidents, and a substantial increase in overall security posture, leading to a boost in customer trust and reduced regulatory compliance costs.
Traceable AI Preventing a Major API Security Incident: The Fintech Narrative
“FinTechForward,” a rapidly growing fintech startup, relied heavily on APIs for its core banking operations. A malicious actor gained access to one of their less-secure APIs. They began a stealthy data exfiltration operation, slowly transferring sensitive customer data. FinTechForward’s security team, however, had implemented Traceable AI. The AI-powered anomaly detection system immediately flagged the unusual activity patterns.
The system’s automated response capabilities promptly blocked the attacker’s access, preventing a massive data breach. The incident response team was able to quickly assess the situation, contain the breach, and minimize the potential damage. This prevented a significant financial loss, reputational damage, and potential legal ramifications. The quick response, enabled by Traceable AI, allowed FinTechForward to maintain customer trust and avoid a major crisis.
Visual Representation: Impact of Successful API Security Implementation
Imagine a diagram depicting an organization’s infrastructure. Before the implementation of Traceable AI, the API gateway is shown as a vulnerable point, with numerous red arrows indicating various attack vectors (SQL injection, unauthorized access, data breaches, etc.), leading to a central data repository depicted as a heavily guarded vault, yet visibly stressed and under attack. After implementation, the same diagram shows a reinforced API gateway, with a robust shield around it, deflecting most of the red arrows.
Green arrows now represent secure API calls, flowing smoothly into the data repository. The vault is now depicted as calm and secure, with minimal stress. The overall image suggests a significant reduction in the attack surface and an improved security posture, reflecting increased resilience and reduced vulnerability. This visual representation showcases the tangible impact of a successful API security implementation on an organization’s overall security landscape.
Ending Remarks
Our conversation with Richard Bird provided invaluable insights into the ever-evolving world of API security. We learned about the critical vulnerabilities facing organizations today, the innovative solutions Traceable AI offers, and the importance of proactive security measures. By implementing best practices and leveraging advanced technologies, organizations can significantly reduce their risk exposure and protect their valuable data. The future of API security is proactive, and this interview highlights the crucial steps organizations must take to stay ahead.
Q&A
What are the biggest misconceptions about API security?
Many believe that simply using HTTPS is sufficient. However, secure APIs require a multi-layered approach encompassing authentication, authorization, input validation, and robust monitoring.
How can small businesses effectively address API security concerns with limited resources?
Small businesses can prioritize essential security practices like strong authentication, input validation, and regular security audits. Leveraging cloud-based security solutions can often be a cost-effective approach.
What role does developer education play in advancing API security?
Developer training is crucial. They need to understand secure coding practices, the common vulnerabilities, and how to implement security measures from the design phase onwards.
How often should API security testing be performed?
Regular testing, ideally as part of a continuous integration/continuous delivery (CI/CD) pipeline, is essential. The frequency depends on the criticality of the API and the rate of code changes, but at least quarterly is recommended.