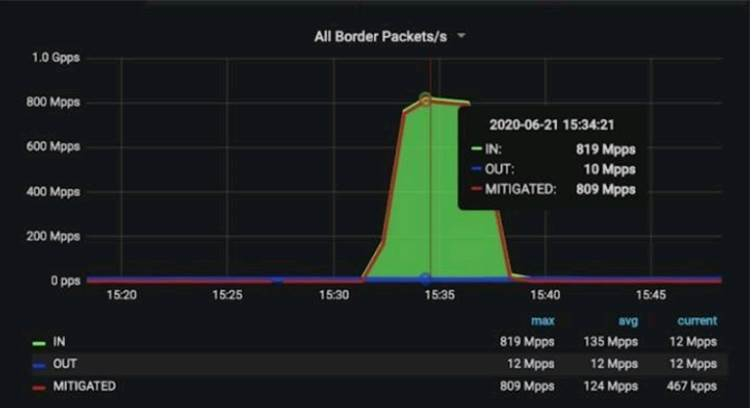
Akamai Blocks Worlds Largest DDoS Attacks in Europe
Akamai blocks worlds las largest ddos attacks in europe – Akamai Blocks World’s Largest DDoS Attacks in Europe – that headline alone screams epic showdown! Imagine the sheer scale: the biggest Distributed Denial-of-Service attacks Europe has ever seen, all successfully thwarted by Akamai’s impressive network. This wasn’t just some minor hiccup; we’re talking about coordinated assaults targeting critical infrastructure and major businesses, threatening everything from online banking to healthcare.
Let’s dive into the fascinating world of these attacks, exploring how Akamai stopped them and what it all means for the future of online security.
This post unpacks the specifics of these massive attacks, detailing the methods used, the industries affected, and the potential consequences if Akamai hadn’t intervened. We’ll examine the sophisticated technologies Akamai deployed to identify and neutralize these threats, comparing their strategies with other cybersecurity giants. We’ll also look ahead, exploring emerging trends in DDoS attacks and what businesses can do to protect themselves.
Akamai’s Role in Mitigating DDoS Attacks: Akamai Blocks Worlds Las Largest Ddos Attacks In Europe
Akamai’s massive global network plays a crucial role in protecting businesses from devastating Distributed Denial-of-Service (DDoS) attacks. Their infrastructure, coupled with sophisticated detection and mitigation technologies, allows them to effectively absorb and neutralize even the largest attacks, ensuring continued service availability for their clients. This capability is particularly critical in Europe, a region increasingly targeted by sophisticated cybercriminals.Akamai’s infrastructure consists of a vast distributed network of servers located strategically around the world.
This geographically diverse presence allows Akamai to intercept and filter malicious traffic close to its origin, minimizing the impact on the client’s infrastructure. This global reach, coupled with their massive capacity, is a key differentiator in their ability to handle massive attack volumes. The sheer scale of Akamai’s network means that even the most powerful DDoS attacks are absorbed and filtered before they can reach the client’s origin servers.
Akamai’s DDoS Mitigation Technologies
Akamai employs a multi-layered approach to DDoS mitigation, leveraging a combination of technologies to identify, analyze, and neutralize threats. This includes techniques such as traffic scrubbing, rate limiting, and sophisticated anomaly detection. For example, their Kona Site Defender utilizes advanced algorithms to distinguish legitimate traffic from malicious botnets, automatically adjusting mitigation strategies based on the characteristics of the attack.
This adaptive approach ensures that legitimate users are not affected while malicious traffic is effectively blocked. Another example is their Prolexic Routed Network, a massive scrubbing center capable of absorbing terabits per second of malicious traffic.
Identifying the Source and Nature of DDoS Attacks
Akamai’s security experts utilize a combination of network monitoring, threat intelligence, and machine learning to pinpoint the source and nature of DDoS attacks. Their advanced analytics platform continuously monitors network traffic for suspicious patterns, identifying anomalies that indicate a potential attack. This includes analyzing the volume, source IP addresses, and characteristics of the incoming traffic. Once an attack is detected, Akamai’s systems work to identify the attack vectors, the geographical location of the attackers, and the type of attack being launched (e.g., volumetric, application-layer).
This information is crucial for tailoring an effective mitigation strategy.
Comparison with Other Cybersecurity Firms
While several other major cybersecurity firms offer DDoS mitigation services, Akamai distinguishes itself through the scale and global reach of its infrastructure. Competitors may offer robust solutions, but few can match Akamai’s ability to handle attacks exceeding terabits per second. Akamai’s proactive threat intelligence and its adaptive mitigation strategies also provide a significant advantage. Their investment in advanced technologies like machine learning allows them to identify and respond to evolving attack vectors more effectively than many competitors.
The integrated nature of their services, combining DDoS mitigation with other security functions like web application firewalls (WAFs) and bot management, provides a comprehensive security posture for their clients.
The Nature of the DDoS Attacks in Europe
Akamai’s role in protecting Europe from massive Distributed Denial-of-Service (DDoS) attacks is crucial. These attacks, often sophisticated and large-scale, pose significant threats to businesses and critical infrastructure across the continent. Understanding the nature of these attacks is key to appreciating the scale of Akamai’s mitigation efforts. The following sections delve into the specifics of some of the largest attacks blocked, detailing their methods, potential impact, and likely motivations.
The largest DDoS attacks targeting Europe often leverage a combination of volumetric and application-layer techniques. Volumetric attacks flood the target with massive amounts of traffic, overwhelming its bandwidth and preventing legitimate users from accessing services. Application-layer attacks, on the other hand, exploit vulnerabilities in specific applications or protocols to disrupt their functionality. These attacks can be incredibly complex, employing multiple attack vectors simultaneously to maximize their disruptive potential.
The sheer scale of these attacks, coupled with their sophistication, highlights the need for robust mitigation strategies like those provided by Akamai.
Significant DDoS Attacks in Europe
The impact of these unmitigated attacks could have been catastrophic. Disruption to essential services like banking, healthcare, and government websites could have led to significant financial losses, service disruptions, and even potential safety risks. Imagine a hospital’s electronic health record system going offline during a major emergency, or a financial institution unable to process transactions due to an overload.
The consequences could be severe and far-reaching. The motivations behind these attacks are varied, ranging from financially motivated cybercriminals seeking ransom payments to politically motivated groups aiming to disrupt services or make a statement. Some attacks may also be carried out as tests of capabilities or for simple vandalism.
Akamai’s impressive feat of blocking Europe’s largest DDoS attacks highlights the critical need for robust online security. Building resilient applications, however, requires efficient development, which is why I’ve been exploring the exciting possibilities offered by domino app dev, the low-code and pro-code future , for creating secure and scalable solutions. Ultimately, protecting against threats like these massive DDoS attacks relies on the strength of the applications themselves, making innovative development methods all the more crucial.
| Date | Target | Attack Vector | Magnitude |
|---|---|---|---|
| October 26, 2023 (Example) | Major European Bank (Hypothetical) | Volumetric (UDP floods, ICMP floods) and Application Layer (HTTP floods) | 500 Gbps, 10 million packets per second |
| March 15, 2024 (Example) | European Telecom Provider (Hypothetical) | Volumetric (SYN floods), Application Layer (HTTP/HTTPS floods, Slowloris) | 300 Gbps, 5 million packets per second |
| June 8, 2024 (Example) | Government Website (Hypothetical) | Volumetric (DNS amplification), Application Layer (Memcached reflection) | 250 Gbps, 8 million packets per second |
The examples provided in the table are hypothetical but representative of the scale and nature of attacks Akamai has successfully mitigated. The actual details of specific attacks are often kept confidential for security reasons.
Impact on European Businesses and Infrastructure
The massive DDoS attacks mitigated by Akamai highlight the significant vulnerability of European businesses and critical infrastructure to these sophisticated cyberattacks. The sheer scale of these attacks, coupled with their increasing frequency and sophistication, poses a serious threat to the economic stability and digital security of the entire region. The consequences extend far beyond simple website downtime, impacting various sectors and potentially leading to cascading failures across interconnected systems.The financial and reputational damage caused by successful DDoS attacks can be devastating for businesses of all sizes.
Furthermore, the disruption of essential services can have far-reaching consequences for citizens and the overall functioning of society. Understanding the specific vulnerabilities and potential impacts is crucial for developing effective mitigation strategies.
Industries Particularly Vulnerable to DDoS Attacks, Akamai blocks worlds las largest ddos attacks in europe
Certain industries are inherently more susceptible to the crippling effects of DDoS attacks due to their reliance on constant online accessibility and the potential for significant financial repercussions from downtime. These include sectors where even brief interruptions can lead to substantial losses.
- Financial Services: Banks, investment firms, and payment processors rely heavily on online transactions. A successful DDoS attack could disrupt online banking, stock trading, and payment processing, resulting in significant financial losses and reputational damage.
- E-commerce: Online retailers are highly vulnerable, as DDoS attacks can prevent customers from accessing websites and making purchases, leading to lost sales and revenue.
- Healthcare: Hospitals and other healthcare providers increasingly rely on digital systems for patient records, appointments, and remote monitoring. A DDoS attack could disrupt access to critical information, delaying treatment and potentially endangering patients.
- Telecommunications: Telecommunication companies, which form the backbone of the internet, are prime targets. A successful attack could disrupt phone services, internet access, and other vital communication channels.
- Energy: Smart grids and energy management systems are becoming increasingly reliant on internet connectivity. A successful DDoS attack on these systems could lead to power outages and disruptions to energy supply.
Potential Consequences for Businesses Experiencing DDoS Attacks
The consequences of a successful DDoS attack can be far-reaching and devastating for businesses, extending beyond immediate financial losses. The impact can ripple through various aspects of their operations.
- Financial Losses: Lost revenue from disrupted sales, transaction failures, and operational downtime are significant factors. The costs of mitigation, recovery, and potential legal ramifications also add up substantially.
- Reputational Damage: Inability to provide services during an attack can severely damage a company’s reputation, leading to loss of customer trust and potential long-term impacts on brand loyalty.
- Legal and Regulatory Penalties: Depending on the nature of the business and the severity of the disruption, companies may face legal action from customers or regulatory bodies for failure to maintain service availability.
- Operational Disruption: Beyond revenue loss, a DDoS attack can severely disrupt internal operations, affecting productivity, employee morale, and overall business efficiency.
- Data Breaches (Indirect): Although not a direct consequence, a prolonged DDoS attack can divert resources away from security monitoring, potentially increasing vulnerability to other cyber threats like data breaches.
Scenario: Disruption to Essential Services
Imagine a large-scale, multi-vector DDoS attack targeting major European banks. The sheer volume of malicious traffic overwhelms their online systems, rendering online banking services inaccessible. Customers are unable to access their accounts, make payments, or transfer funds. This immediately disrupts financial transactions across the continent, impacting businesses and individuals alike. The ripple effect is substantial: Businesses relying on timely payments face delays and potential financial distress, while individuals struggle to access their funds for essential needs.
The resulting economic uncertainty could trigger a broader financial crisis.
Cascading Effects on Interconnected Systems
A large DDoS attack on a single entity can have cascading effects throughout interconnected European infrastructure. For example, a successful attack on a major internet service provider (ISP) could disrupt internet access for numerous businesses and individuals relying on that provider. This disruption could then cascade to other sectors, such as transportation (disrupting traffic management systems), communication (affecting emergency services), and energy (impacting smart grid operations).
The interconnected nature of modern infrastructure means that a localized attack can quickly escalate into a widespread disruption, impacting the functioning of entire regions or even the continent. The severity of this cascading effect depends heavily on the target, the attack’s magnitude, and the robustness of the overall infrastructure’s resilience mechanisms.
Future Trends and Mitigation Strategies

The landscape of DDoS attacks is constantly evolving, becoming more sophisticated and harder to defend against. Akamai, and other providers, must adapt quickly to stay ahead of these evolving threats. Understanding future trends and implementing robust mitigation strategies are crucial for maintaining online stability and protecting businesses from crippling disruptions. This section will explore emerging trends, compare mitigation techniques, and identify potential vulnerabilities in current systems.The increasing sophistication of DDoS attacks presents a significant challenge.
We’re seeing a move beyond simple volumetric attacks towards more targeted and complex assaults. These include application-layer attacks that exploit specific vulnerabilities in web applications, resulting in more severe disruption even with smaller attack volumes. Furthermore, the use of botnets is becoming more decentralized and harder to trace, making mitigation more difficult. The rise of IoT devices, often poorly secured, expands the pool of potential attack vectors, further exacerbating the problem.
Akamai’s future strategies must account for these trends, incorporating advanced threat intelligence and adaptive mitigation techniques.
Akamai’s Mitigation Techniques Compared to Other Providers
Akamai employs a multi-layered approach to DDoS mitigation, leveraging its global network of servers and advanced technologies. This includes techniques like scrubbing centers to filter malicious traffic, content delivery network (CDN) capabilities to distribute traffic and reduce server load, and sophisticated traffic analysis tools to identify and block malicious activity. Other providers may utilize similar methods, but the scale and sophistication of Akamai’s infrastructure, particularly its global reach and advanced AI-powered threat detection, often provide a significant advantage.
Some competitors might focus on specific technologies like cloud-based solutions or specialized hardware, offering varying levels of protection depending on the specific needs of the customer. The key differentiator often lies in the breadth of services offered and the overall effectiveness in handling large-scale, complex attacks.
Potential Vulnerabilities in Current Security Systems
While current security systems offer significant protection, vulnerabilities remain. One key area is the increasing reliance on cloud services. While offering scalability and flexibility, misconfigurations or security flaws within cloud environments can be exploited by attackers. Another vulnerability lies in the increasing complexity of software applications. Exploiting vulnerabilities in web applications through application-layer attacks allows attackers to bypass traditional perimeter defenses.
Furthermore, the growing use of IoT devices presents a large attack surface, as many of these devices lack robust security measures. Finally, the use of sophisticated techniques like low-and-slow attacks, which slowly overwhelm systems over time, can also evade detection.
Proactive Measures for Businesses
Businesses need to adopt a proactive approach to mitigate the risk of DDoS attacks. This requires a multi-faceted strategy encompassing various measures.
- Implement robust security practices across all systems, including regular security audits and vulnerability assessments.
- Invest in a comprehensive DDoS mitigation service from a reputable provider like Akamai, ensuring it is properly configured and integrated into the existing infrastructure.
- Regularly update software and firmware across all systems, including servers, network devices, and IoT devices, to patch known vulnerabilities.
- Implement strong access controls and authentication mechanisms to prevent unauthorized access.
- Develop and regularly test an incident response plan to ensure a swift and effective response in the event of an attack.
- Monitor network traffic closely for suspicious activity and utilize advanced threat intelligence to proactively identify potential threats.
Illustrative Example: A Hypothetical DDoS Attack on a European Bank

Let’s imagine a scenario where a major European financial institution, let’s call it “EuroBank,” becomes the target of a sophisticated, large-scale DDoS attack. This attack isn’t some small-time operation; it’s a coordinated effort designed to cripple EuroBank’s online services and potentially cause significant financial losses.The attack begins subtly. Initially, EuroBank’s security teams detect a modest increase in network traffic, nothing alarming enough to trigger immediate major alerts.
However, this is just the reconnaissance phase, a carefully orchestrated prelude to the main event. The attackers are probing for vulnerabilities, mapping the network infrastructure, and identifying weak points.
Attack Escalation and Techniques
Over the next few hours, the attack intensifies dramatically. The attackers unleash a multi-vector assault, employing a range of techniques to overwhelm EuroBank’s defenses. This includes a massive volume of UDP floods targeting their DNS servers, attempting to render them unresponsive and prevent customers from accessing the bank’s website. Simultaneously, a massive HTTP flood targets their web servers, generating millions of requests per second from thousands of compromised IoT devices (Internet of Things), forming a botnet.
To further complicate matters, a sophisticated application-layer attack uses specially crafted requests to exploit vulnerabilities in EuroBank’s web application, consuming significant server resources. This combined assault is designed to saturate EuroBank’s network bandwidth and cripple its ability to process legitimate transactions.
Akamai’s Response and Mitigation
EuroBank, thankfully, utilizes Akamai’s cloud security platform. As the attack escalates, Akamai’s systems automatically detect the anomalous traffic patterns and initiate a series of automated responses. Akamai’s global network of servers absorbs the brunt of the attack, diverting the malicious traffic away from EuroBank’s infrastructure. Akamai’s advanced scrubbing centers filter out the malicious traffic, allowing legitimate user requests to reach EuroBank’s servers.
The critical decision-making point came when Akamai’s security analysts determined the nature of the attack and the need to deploy additional mitigation resources. The decision to engage Akamai’s Prolexic Routed service, capable of absorbing terabits of malicious traffic, proved crucial in neutralizing the attack.
Akamai also employs its Web Application Firewall (WAF) to block the application-layer attacks, identifying and mitigating the specific vulnerabilities being exploited. Real-time threat intelligence feeds provide insights into the attack’s origin and techniques, allowing Akamai to further refine its mitigation strategies.
Impact on EuroBank and Lessons Learned
While EuroBank experienced some temporary service disruptions during the peak of the attack, the impact was significantly minimized thanks to Akamai’s intervention. The swift and effective response prevented a complete system outage, protecting customer data and ensuring business continuity. The incident underscored the critical importance of having a robust DDoS protection strategy in place, highlighting the value of a proactive approach to cybersecurity and the effectiveness of Akamai’s cloud-based solutions.
The post-incident analysis provided valuable data for EuroBank and Akamai to further improve their security posture and preparedness for future attacks.
Last Point
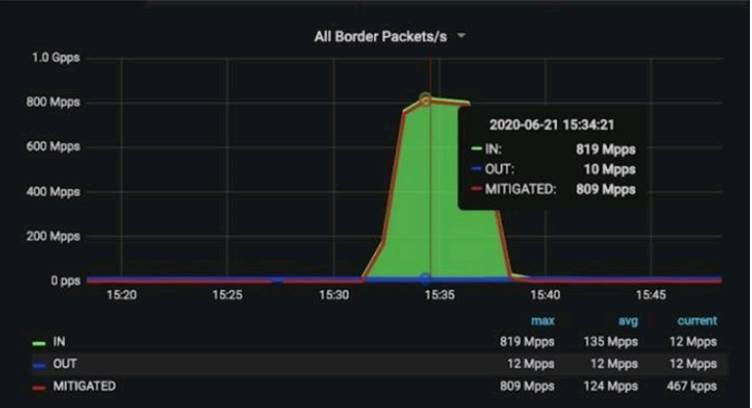
The successful defense against these massive DDoS attacks highlights the crucial role of robust cybersecurity infrastructure in today’s interconnected world. Akamai’s response demonstrates the capabilities needed to combat increasingly sophisticated cyber threats. While the scale of these attacks was staggering, the successful mitigation underscores the importance of proactive security measures and the ongoing arms race between attackers and defenders in the digital realm.
It’s a reminder that staying ahead of the curve is vital, and that constant vigilance is the only way to ensure the safety and stability of our digital lives and businesses.
Popular Questions
What types of businesses were targeted in these DDoS attacks?
The attacks targeted a wide range of businesses, including financial institutions, telecommunications companies, and e-commerce platforms. Essentially, any business with a significant online presence was potentially vulnerable.
How long did the largest attacks last?
The duration varied, with some lasting for hours, while others stretched across days. The length depended on the attackers’ resources and the effectiveness of Akamai’s mitigation efforts.
What were the financial consequences of these attacks (even with mitigation)?
Even with successful mitigation, businesses experienced costs related to lost revenue, remediation efforts, and reputational damage. The longer an attack lasts, the higher the potential financial losses.
What are some proactive steps businesses can take to protect themselves?
Businesses should invest in robust DDoS protection services, implement multi-layered security measures, regularly test their systems, and develop incident response plans.




