Amazon Detective Launched to Detect Cloud Security Anomalies
Amazon Detective launched to detect cloud security anomalies – it sounds like something straight out of a spy thriller, right? But this isn’t fiction; it’s a powerful new AWS tool designed to help us navigate the increasingly complex landscape of cloud security. Think of it as a highly skilled investigator, constantly monitoring your AWS environment for suspicious activity and alerting you to potential threats before they can cause serious damage.
This post dives into what Amazon Detective is, how it works, and why it’s a game-changer for anyone serious about cloud security.
Amazon Detective helps identify and investigate potential security issues within your AWS environment by analyzing various data sources, including VPC Flow Logs, CloudTrail logs, and GuardDuty findings. It uses machine learning to identify unusual patterns and behaviors that could indicate a security breach or compromise. This proactive approach allows for faster detection and response to threats, minimizing downtime and potential data loss.
The platform offers visualizations and detailed investigation tools to understand the root cause of anomalies, making it easier to implement effective remediation strategies.
Introduction to Amazon Detective

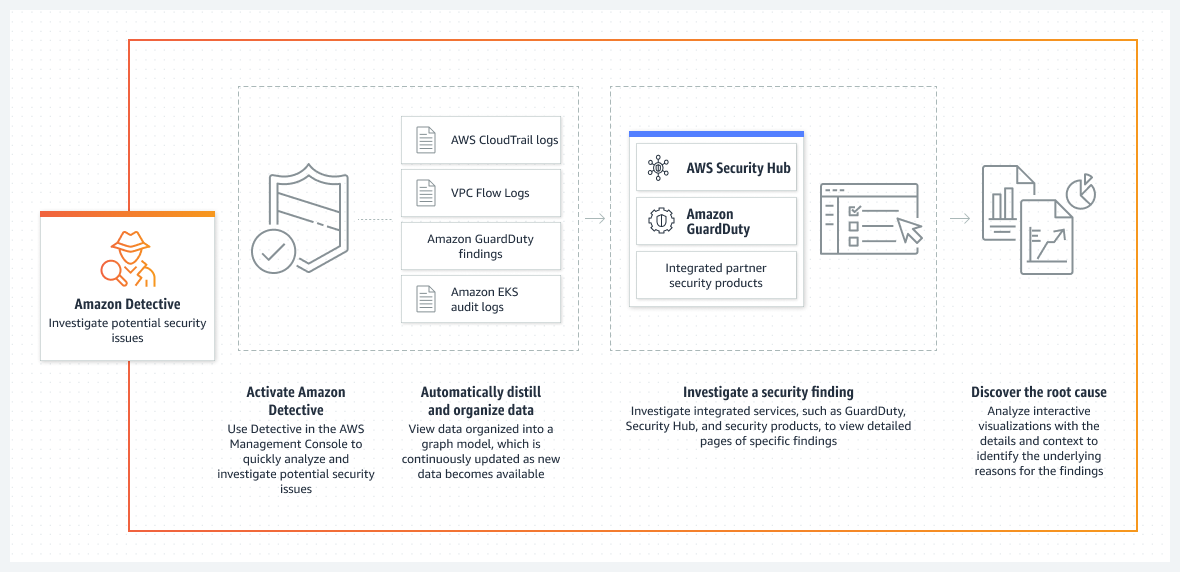
Amazon Detective is a security service that makes it easier to investigate, analyze, and find security issues within your Amazon Web Services (AWS) environment. It automatically collects and analyzes data from various AWS services to identify unusual behaviors and potential security risks, helping you proactively address threats before they escalate. Think of it as a powerful security detective, constantly monitoring your cloud infrastructure and alerting you to suspicious activity.Amazon Detective solves the significant challenge of effectively monitoring and analyzing the vast amounts of data generated by a typical cloud environment.
Manually sifting through logs and security alerts is time-consuming, prone to error, and often misses subtle but critical indicators of compromise. Detective automates this process, providing a consolidated view of your security posture and highlighting anomalies that might indicate malicious activity or misconfigurations. This allows security teams to focus on investigating genuine threats rather than chasing false positives.The benefits of using Amazon Detective for anomaly detection are substantial.
Firstly, it significantly reduces the time it takes to identify and respond to security incidents. By automating the analysis of massive datasets, Detective quickly flags suspicious patterns that would otherwise go unnoticed. Secondly, it improves the accuracy of threat detection. The service employs advanced machine learning algorithms to identify subtle anomalies that might indicate sophisticated attacks. Finally, Detective provides a comprehensive and centralized view of your security posture, facilitating more effective security management and compliance efforts.
Amazon Detective’s launch to pinpoint cloud security anomalies is a game-changer, especially considering the increasing complexity of modern systems. Building secure applications requires robust development practices, and that’s where understanding the future of app development comes in, like what’s discussed in this great article on domino app dev the low code and pro code future. Ultimately, both proactive development and reactive security tools like Amazon Detective are crucial for a truly secure cloud environment.
This consolidated view simplifies investigations and allows for quicker remediation of identified issues.
Amazon Detective’s Core Functionality
Amazon Detective’s core functionality centers around the automated collection and analysis of data from various AWS services. This data includes VPC Flow Logs, GuardDuty findings, and other relevant security logs. The service then uses machine learning to identify unusual activity and potential security issues, presenting this information in an easy-to-understand graphical interface. This interface allows security teams to visually explore relationships between different security events, helping them to understand the context and impact of potential threats.
Detective also provides visualizations of network traffic patterns, making it easier to identify suspicious communication flows. The service continuously monitors your environment, providing real-time alerts and updates on any identified anomalies.
Addressing the Problem of Cloud Security
The complexity and scale of modern cloud environments make traditional security approaches inadequate. The sheer volume of data generated by cloud services makes manual monitoring impractical. Furthermore, cloud environments are dynamic, with infrastructure and applications constantly changing. This dynamic nature makes it difficult to maintain a consistent and accurate security posture using traditional methods. Amazon Detective directly addresses these challenges by providing a scalable and automated solution for monitoring and analyzing cloud security data.
It simplifies the process of identifying and responding to threats, helping organizations maintain a strong security posture in complex and ever-evolving cloud environments. For example, a sudden spike in unusual network traffic from a specific instance, potentially indicative of a compromised server, would be quickly identified and flagged by Detective. This allows for immediate investigation and mitigation of the threat, preventing further damage.
Benefits of Anomaly Detection with Amazon Detective
Using Amazon Detective’s anomaly detection capabilities offers several key advantages. Faster incident response is paramount, and Detective achieves this by providing near real-time alerts on suspicious activity. Improved accuracy in threat detection is another major benefit; the machine learning algorithms are designed to identify subtle anomalies that might be missed by human analysts. Finally, Detective’s centralized view of your security posture simplifies investigation and remediation, leading to more efficient security management and better compliance posture.
This streamlined approach enables security teams to proactively address potential threats, reducing the risk of successful attacks and minimizing potential damage.
Anomaly Detection Mechanisms
Amazon Detective’s power lies in its sophisticated anomaly detection mechanisms, going beyond simple rule-based alerts to proactively identify unusual activity indicative of potential security compromises within your AWS environment. It achieves this by leveraging machine learning and analyzing vast amounts of data from various sources, offering a comprehensive view of your security posture. This allows security teams to focus on high-priority threats rather than sifting through countless low-level alerts.Amazon Detective employs a multi-faceted approach to identify anomalies.
It doesn’t rely on a single method but rather combines several techniques to provide a more robust and accurate detection system. This layered approach helps minimize false positives while maximizing the detection of genuine security threats. The system continuously learns and adapts, improving its accuracy over time as more data is processed.
Data Sources Analyzed by Amazon Detective
Amazon Detective analyzes a wide array of data sources to build a comprehensive picture of your AWS environment’s security state. This holistic approach is crucial for detecting anomalies that might otherwise go unnoticed if only a single data source was examined. The richness of the data provides context and enables more accurate anomaly detection.
- Amazon VPC Flow Logs: These logs provide information about network traffic within your virtual private clouds, revealing patterns of communication and potential unauthorized access attempts.
- Amazon GuardDuty Findings: GuardDuty’s threat detection capabilities are integrated, feeding Detective with information about malicious activity, compromised resources, and other security findings.
- AWS CloudTrail Logs: CloudTrail logs track API calls made to your AWS account, providing insights into changes to your infrastructure and potential unauthorized configuration modifications.
- Other AWS Services: Detective can integrate with other AWS security services, expanding its data sources and enhancing its ability to detect anomalies across your entire AWS ecosystem.
Comparison with Other Cloud Security Monitoring Tools
While many cloud security monitoring tools exist, Amazon Detective distinguishes itself through its integrated approach and its use of machine learning for anomaly detection. Traditional tools often rely on predefined rules and signatures, which can miss novel or sophisticated attack techniques. Detective’s machine learning models can identify deviations from established baselines, even in the absence of known attack patterns.
| Feature | Amazon Detective | Traditional Cloud Security Monitoring Tools |
|---|---|---|
| Anomaly Detection | Machine learning-based, identifies deviations from established baselines | Rule-based, relies on predefined signatures and patterns |
| Data Sources | Multiple AWS services integrated, comprehensive view | Often limited to specific data sources or require manual integration |
| Alerting | Prioritizes anomalies based on severity and potential impact | Can generate high volumes of alerts, requiring manual filtering |
| Visualizations | Interactive graphs and visualizations aid in investigation | Often limited to textual logs or basic reports |
Investigating Security Anomalies
Amazon Detective provides a powerful suite of tools for identifying and investigating security anomalies within your AWS environment. Understanding how to effectively leverage these tools is crucial for maintaining a secure cloud posture. This section Artikels a practical approach to investigating alerts and prioritizing your response.
Step-by-Step Procedure for Investigating an Amazon Detective Alert
Upon receiving a security alert from Amazon Detective, a systematic approach is key to efficient investigation and remediation. The following steps provide a structured workflow:
- Review the Alert Details: Begin by carefully examining the alert in the Amazon Detective console. Pay close attention to the timestamp, affected resources, anomaly type, and any supporting evidence provided (e.g., network flows, log data). Understanding the context of the alert is the first crucial step.
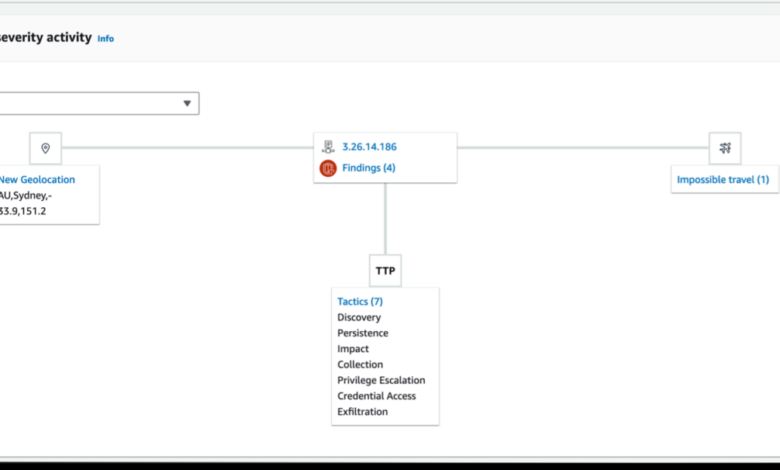
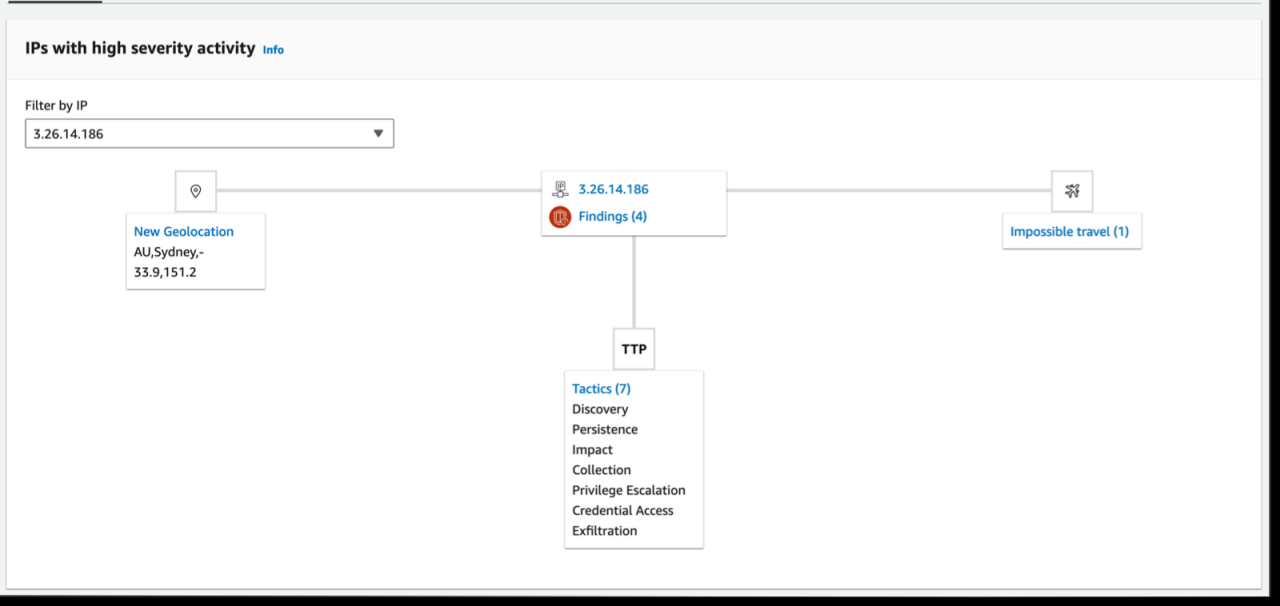
- Analyze the Graph: Amazon Detective visualizes your environment as a graph. Explore the graph to identify relationships between the resources involved in the anomaly. This helps determine the scope and potential impact of the event. Look for unusual connections or patterns of activity.
- Correlate with Other Logs and Data: Don’t rely solely on Detective’s findings. Integrate the information with other security logs (e.g., CloudTrail, VPC Flow Logs, GuardDuty findings) to gain a comprehensive understanding of the event. This cross-referencing often reveals critical details not immediately apparent in the Detective alert.
- Identify Root Cause: Based on the collected data, determine the root cause of the anomaly. This might involve misconfigured security groups, compromised credentials, malicious activity, or simply a legitimate but unusual activity pattern.
- Implement Remediation: Once the root cause is identified, implement the necessary remediation steps. This could range from updating security group rules, rotating credentials, applying security patches, or implementing stricter access controls.
- Validate Remediation: After implementing the remediation, validate its effectiveness by monitoring the affected resources and ensuring the anomaly no longer persists. Regular monitoring is essential to prevent recurrence.
Security Alert Triaging and Prioritization Workflow
Effectively managing security alerts requires a well-defined workflow for triaging and prioritizing them. A common approach involves assigning severity levels based on the potential impact and urgency of remediation.
- Severity Assessment: Assign a severity level (e.g., Critical, High, Medium, Low) based on the potential impact of the anomaly on your systems and data. Consider factors like data sensitivity, system criticality, and the potential for widespread disruption.
- Impact Analysis: Determine the scope and potential impact of the anomaly. This involves assessing the affected resources, the volume of compromised data (if any), and the potential for further exploitation.
- Urgency Determination: Assess the urgency of remediation based on the severity and potential impact. Critical and high-severity alerts require immediate attention, while lower-severity alerts can be addressed with a less urgent response.
- Alert Assignment: Assign the alert to the appropriate security team member or group based on their expertise and availability. This ensures timely investigation and resolution.
- Remediation Tracking: Track the remediation process, including the assigned personnel, the steps taken, and the outcome. This provides valuable insights for future incident response efforts.
Anomaly Types, Causes, and Remediation Strategies, Amazon detective launched to detect cloud security anomalies
The following table illustrates different anomaly types, their potential causes, and remediation strategies.
| Anomaly Type | Potential Causes | Remediation Strategies | Example |
|---|---|---|---|
| Unusual Network Traffic | Compromised EC2 instance, misconfigured security groups, malware | Isolate affected instance, review security group rules, scan for malware | High volume of outbound connections to a known malicious IP address from an EC2 instance. |
| Elevated API Calls | Unauthorized access, automated attacks, compromised credentials | Review IAM policies, implement multi-factor authentication, investigate unusual access patterns | A significant increase in calls to the AWS S3 API from an unexpected location. |
| Data Exfiltration | Malware, insider threat, compromised credentials | Implement data loss prevention (DLP) tools, review access logs, strengthen security controls | Large amounts of data transferred from a database instance to an external IP address. |
| Resource Consumption Spike | Malicious activity, resource exhaustion, application errors | Monitor resource utilization, scale resources as needed, investigate error logs | A sudden increase in CPU utilization on an EC2 instance resulting in performance degradation. |
Integration with Other AWS Services
Amazon Detective doesn’t operate in a vacuum; its true power lies in its seamless integration with other AWS security services. By combining Detective’s anomaly detection capabilities with the data and insights provided by services like GuardDuty and CloudTrail, you can build a robust, layered security posture that proactively identifies and responds to threats. This integration allows for a more comprehensive understanding of your security landscape, improving both detection speed and response efficiency.Effective integration with your existing security infrastructure is crucial for maximizing Detective’s value.
This means understanding how data flows between different services and configuring Detective to receive and process relevant information. Proper configuration ensures that Detective can effectively analyze your environment and identify meaningful anomalies, rather than being overwhelmed by irrelevant data or missing crucial details. A well-integrated Detective deployment enhances the overall effectiveness of your security operations.
GuardDuty Integration
Amazon GuardDuty continuously monitors your AWS environment for malicious or unauthorized activity. It analyzes various data sources, including VPC Flow Logs, CloudTrail logs, and DNS logs, to detect suspicious behaviors. Detective integrates with GuardDuty by receiving findings from GuardDuty as input. This allows Detective to correlate GuardDuty findings with other security data to gain a broader context and potentially uncover deeper, more complex threats that GuardDuty might miss in isolation.
For example, a GuardDuty finding indicating unusual network traffic might be further investigated by Detective, revealing a pattern of compromised instances that GuardDuty alone wouldn’t have identified. The integration streamlines the investigation process by providing a central location to analyze all relevant security information.
CloudTrail Integration
CloudTrail is a service that provides a record of API calls made within your AWS account. This audit trail is essential for security monitoring and incident response. Detective leverages CloudTrail logs to analyze user activity and identify unusual patterns. By analyzing CloudTrail data, Detective can detect anomalous login attempts, excessive resource creation, or suspicious administrative actions. This integration helps identify insider threats or account compromises that might not be immediately apparent through other security tools.
For instance, Detective might detect an unusual spike in API calls from a specific user account, prompting further investigation to determine if the account has been compromised.
Best Practices for Integration
Effective integration of Amazon Detective requires a strategic approach. Here are some best practices to ensure maximum benefit:
Before listing best practices, it’s important to understand that a holistic approach is key. Proper configuration and data flow between services are paramount for success. This involves carefully considering data volume, retention policies, and potential impact on performance.
- Enable relevant data sources: Ensure that VPC Flow Logs, CloudTrail logs, and other relevant data sources are properly configured and sent to Detective. The quality of Detective’s analysis depends directly on the completeness and accuracy of the input data.
- Regularly review Detective findings: Proactively review Detective’s findings to identify and address potential security issues promptly. Don’t just rely on automated alerts; regular manual review is crucial for detecting subtle anomalies.
- Integrate with SIEM: Connect Detective with your Security Information and Event Management (SIEM) system to centralize security monitoring and incident response. This allows for correlation of Detective findings with other security events from across your infrastructure.
- Establish clear incident response procedures: Develop and test clear incident response procedures that Artikel how to investigate and respond to security anomalies identified by Detective. This includes defining roles and responsibilities.
- Regularly review and update configurations: As your AWS environment evolves, ensure that your Detective configurations remain up-to-date to reflect changes in your infrastructure and security needs. This ensures continuous and accurate monitoring.
Cost Optimization and Resource Management
Amazon Detective is a powerful tool, but its cost can escalate if not managed effectively. Understanding how to optimize its usage is crucial for maintaining a healthy cloud security posture without breaking the bank. This section Artikels strategies for controlling costs and efficiently managing the resources consumed by Amazon Detective.Effective cost management hinges on carefully considering data volume, retention policies, and the scope of your investigation.
Unnecessary data collection and analysis directly translate to higher expenses. By implementing the strategies below, you can significantly reduce your Detective bill while retaining the security benefits.
Data Volume Optimization
Minimizing the amount of data ingested by Amazon Detective is a primary cost-saving measure. This involves strategically selecting the data sources you integrate with Detective and configuring appropriate filtering rules. For example, instead of ingesting all VPC flow logs, you can filter for only those logs from specific subnets known to contain sensitive applications. Similarly, focusing on specific AWS services relevant to your critical infrastructure reduces the overall data processed and subsequently, the costs.
This targeted approach ensures you’re only analyzing the data truly necessary for effective threat detection.
Retention Policy Management
Amazon Detective allows you to configure data retention policies. By default, data is retained for a specific period. Reducing this retention period can dramatically lower your costs, especially if you are analyzing large volumes of data. However, you must carefully weigh the cost savings against the potential loss of historical security context. For example, a shorter retention period might make it harder to investigate incidents that occurred several weeks ago.
A balanced approach involves regularly reviewing your retention settings based on your organization’s specific security and compliance requirements. Perhaps maintain longer retention for critical systems and shorter retention for less sensitive areas.
Resource Allocation
Amazon Detective’s resource consumption is directly tied to the volume of data processed. While Detective automatically scales to handle varying workloads, understanding the relationship between data volume and cost allows for better resource planning. Regular monitoring of your Detective usage, including data ingested, queries executed, and storage consumed, provides valuable insights into potential areas for optimization. AWS Cost Explorer and CloudWatch can provide this granular visibility, allowing you to identify trends and make informed decisions about resource allocation.
Minimizing Unnecessary Data Collection and Analysis
Consider implementing robust logging and monitoring strategiesbefore* relying heavily on Detective for investigation. This proactive approach might involve using other AWS services like CloudTrail and GuardDuty to detect anomalies earlier in the lifecycle. This reduces the need for extensive Detective analysis, leading to cost savings. Additionally, regularly reviewing and refining your Detective configurations – such as removing unused data sources or adjusting filter rules – ensures you’re only analyzing relevant information.
Think of it as a continuous improvement process; regularly audit your Detective setup to identify and eliminate unnecessary data collection.
Case Studies
Amazon Detective’s power lies not just in its features, but in its real-world application. Seeing how it’s helped organizations navigate complex security challenges brings its capabilities into sharp focus. Let’s explore some hypothetical scenarios and examine how Detective could be used to detect various attack types.
Below is a hypothetical case study illustrating the effectiveness of Amazon Detective in identifying and resolving a significant security breach. This scenario highlights the platform’s ability to pinpoint anomalies, streamline investigations, and accelerate incident response.
Hypothetical Security Breach Scenario
Imagine a fictional e-commerce company, “ShopSmart,” experienced a surge in unusual database activity late one Friday evening. This wasn’t the usual weekend slowdown; instead, there was a significant increase in read and write operations far exceeding typical patterns. Initially, ShopSmart’s security team was overwhelmed, struggling to pinpoint the source and scope of the issue. This is where Amazon Detective stepped in.
- Scenario: A sophisticated attacker gained unauthorized access to ShopSmart’s database server through a compromised employee account (weak password). The attacker began exfiltrating sensitive customer data, including credit card information and personal details.
- Detection: Amazon Detective, integrated with ShopSmart’s AWS environment, immediately flagged the anomalous database activity. The platform’s machine learning algorithms identified unusual access patterns, data transfer volumes, and geographical locations of the requests, all pointing towards a potential breach.
- Response: The Detective console provided ShopSmart’s security team with a clear visual representation of the attack, including the compromised account, the affected resources, and the data exfiltration pathways. This allowed them to quickly isolate the compromised server, revoke the employee’s access, and initiate a forensic investigation.
- Outcome: Thanks to the rapid detection and clear visualization provided by Amazon Detective, ShopSmart was able to contain the breach within hours, minimizing data loss and preventing further compromise. The swift response also reduced the potential financial and reputational damage significantly.
Detecting Different Attack Types
Amazon Detective isn’t limited to detecting just one type of attack. Its ability to analyze network and resource behavior makes it effective against a broad spectrum of threats.
- Insider Threats: Detective can identify unusual access patterns from trusted users, such as employees accessing sensitive data outside of normal work hours or downloading large amounts of information. This helps to detect and prevent malicious insider activity.
- Data Breaches: As seen in the ShopSmart example, Detective effectively detects unauthorized data exfiltration attempts by identifying anomalous data transfer volumes and unusual network connections.
- Denial-of-Service (DoS) Attacks: By monitoring network traffic patterns and resource utilization, Detective can detect sudden spikes in traffic or resource consumption indicative of a DoS attack, allowing for timely mitigation strategies.
Impact on Security Posture and Incident Response Time
Integrating Amazon Detective significantly improves an organization’s security posture and reduces incident response times. The platform’s proactive anomaly detection capabilities empower security teams to address threats before they cause significant damage.
- Improved Security Posture: By continuously monitoring the environment and identifying potential vulnerabilities, Detective helps organizations maintain a strong security posture and proactively mitigate risks.
- Reduced Incident Response Time: The platform’s ability to quickly identify and visualize security anomalies significantly reduces the time it takes to investigate and respond to incidents, minimizing the impact of attacks.
- Enhanced Threat Visibility: Detective provides a centralized view of security events across the AWS environment, giving security teams a comprehensive understanding of their security landscape and potential threats.
Future Directions and Enhancements
Amazon Detective is a powerful tool, but like all technology, it’s constantly evolving. Its future lies in enhancing its capabilities to address the increasingly sophisticated threats facing cloud environments. This involves improving its detection accuracy, expanding its coverage, and integrating more seamlessly with other AWS services and third-party tools.The roadmap for Amazon Detective’s future enhancements should focus on refining its core functionality and expanding its scope to cover a wider range of security concerns.
This includes not only improving its ability to detect anomalies but also providing more context and actionable insights to security teams.
Enhanced Anomaly Detection Capabilities
Improving the accuracy and precision of anomaly detection is paramount. Current machine learning models could be refined through the incorporation of more sophisticated algorithms and the integration of additional data sources, such as network flow data from VPC Flow Logs and application logs. For example, incorporating behavioral baselines specific to individual accounts or workloads could dramatically reduce false positives.
This would involve analyzing historical data to establish normal activity patterns for each entity, allowing for a more nuanced understanding of deviations from the norm. This approach could significantly improve the signal-to-noise ratio, making it easier for security teams to focus on genuine threats.
Expanded Threat Detection Coverage
Currently, Amazon Detective focuses primarily on network-based anomalies. Future enhancements could extend its capabilities to include detection of anomalies within databases, serverless functions, and other cloud services. This would require integrating with a wider range of AWS services and incorporating data from different sources to build a more holistic view of the security posture. For instance, detecting unusual access patterns to databases or anomalous behavior within Lambda functions would significantly enhance its overall effectiveness.
This comprehensive approach would provide a more complete picture of security risks across the entire cloud environment.
Improved Integration with Other AWS Services
Seamless integration with other AWS security services, such as GuardDuty, Security Hub, and IAM Access Analyzer, is crucial. This integration should go beyond simple data aggregation; it should enable automated remediation actions based on detected anomalies. For example, if Detective identifies suspicious activity, it could automatically trigger an alert in Security Hub, escalate the issue to a designated security team, or even automatically implement mitigation strategies, such as temporarily restricting access to compromised resources.
This proactive approach would significantly reduce the time to response and minimize the impact of security incidents.
Advanced Visualization and Reporting
The current visualization capabilities could be significantly improved. This includes providing more interactive dashboards, custom report generation options, and the ability to drill down into specific anomalies for detailed analysis. The ability to create custom reports tailored to specific security requirements would greatly enhance the utility of the service for organizations of varying sizes and complexities. A more intuitive and informative interface would improve the overall user experience and make it easier for security teams to understand and act on the insights provided by Amazon Detective.
Automated Response and Remediation
Adding automated response and remediation capabilities would significantly enhance the value of Amazon Detective. This could involve integrating with other AWS services to automatically take corrective actions based on detected anomalies. For instance, automatically blocking malicious IP addresses or suspending compromised user accounts based on pre-defined rules and thresholds. This proactive approach would minimize the impact of security breaches and improve overall security posture.
A well-designed system of automated responses would reduce the burden on security teams and allow them to focus on more strategic security initiatives.
Final Wrap-Up: Amazon Detective Launched To Detect Cloud Security Anomalies
In short, Amazon Detective isn’t just another security tool; it’s a proactive, intelligent system that empowers you to take control of your cloud security posture. By providing clear visualizations and actionable insights, Amazon Detective helps you move beyond reactive security measures and towards a more proactive and robust defense. It’s a powerful addition to any cloud security arsenal, and with its seamless integration with other AWS services, it’s a must-have for organizations of all sizes.
So, ditch the guesswork and embrace the power of proactive security with Amazon Detective.
Questions and Answers
What types of anomalies does Amazon Detective detect?
Amazon Detective can detect a wide range of anomalies, including unusual network activity, suspicious API calls, and compromised accounts. The specific types of anomalies detected depend on the data sources configured and the machine learning models used.
How much does Amazon Detective cost?
Pricing is based on the amount of data analyzed and the number of data sources configured. Check the AWS pricing page for the most up-to-date information.
Can I use Amazon Detective with non-AWS cloud environments?
No, Amazon Detective is specifically designed for monitoring AWS environments. It analyzes data from various AWS services and is integrated with other AWS security tools.
How do I get started with Amazon Detective?
You can easily enable Amazon Detective through the AWS Management Console, AWS CLI, or AWS SDKs. The AWS documentation provides detailed instructions and tutorials to get you started.