Amazon Web Services Mandates MFA Security
Amazon Web Services Mandates MFA Security: Let’s face it, keeping your AWS environment secure is a big deal. And lately, it’s become even more critical with AWS’s push towards mandatory multi-factor authentication (MFA). This isn’t just some suggestion; it’s a vital step to protect your data and resources from unauthorized access. This post dives into what MFA is, why AWS is enforcing it, and how you can smoothly implement it in your own systems.
We’ll explore various MFA methods, best practices, and even tackle some common troubleshooting issues – because let’s be honest, things don’t always go perfectly smoothly.
We’ll cover the different types of MFA offered by AWS, from virtual MFA devices to hardware tokens, and discuss the pros and cons of each. I’ll walk you through a step-by-step guide on enabling MFA for your IAM users, making the process as straightforward as possible. We’ll also explore how MFA integrates with various AWS services like EC2, S3, and RDS, and delve into best practices for managing MFA across your entire AWS infrastructure.
Finally, we’ll look at the compliance aspects, cost considerations, and how to ensure your MFA implementation is robust and effective.
AWS MFA Security Overview
Implementing robust security measures is paramount in the cloud, and Multi-Factor Authentication (MFA) is a cornerstone of a strong AWS security posture. This overview explores the different MFA options available within AWS, their benefits, and a practical guide to enabling MFA for your IAM users. By understanding and utilizing MFA, you significantly reduce the risk of unauthorized access to your valuable AWS resources.AWS offers several methods of MFA, each with varying levels of convenience and security.
Choosing the right method depends on your specific needs and technical capabilities. The key is to ensure that all users with access to sensitive resources are utilizing some form of MFA.
AWS MFA Methods
AWS provides a range of MFA options, catering to diverse user needs and preferences. These include virtual MFA devices (like Google Authenticator or Authy), hardware MFA devices (like security keys), and time-based one-time passwords (TOTP). Each method offers a different level of security and user experience. Virtual MFA devices are convenient and readily available, while hardware keys offer enhanced security.
Understanding the strengths and weaknesses of each option is crucial for informed decision-making.
Benefits of Implementing AWS MFA
The benefits of implementing MFA for your AWS accounts and resources are substantial. MFA adds an extra layer of security, significantly reducing the risk of unauthorized access even if credentials are compromised. This protects your sensitive data, infrastructure, and applications from malicious actors. Compliance requirements often mandate MFA, and its implementation demonstrates a commitment to robust security practices.
Furthermore, it can help limit the damage from phishing attacks and other social engineering tactics.
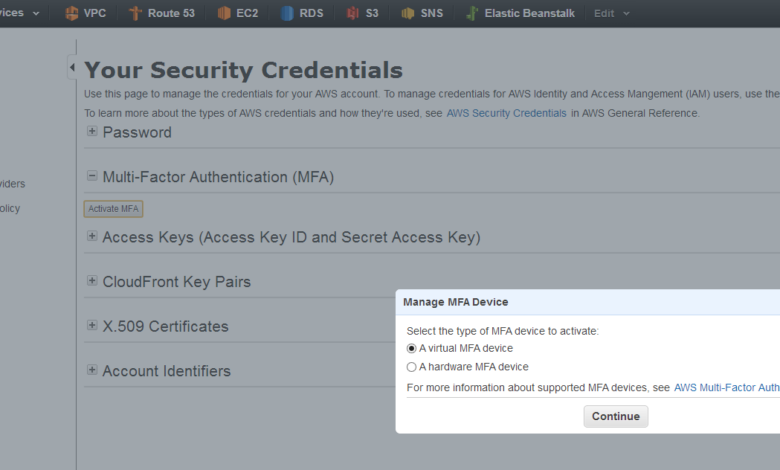
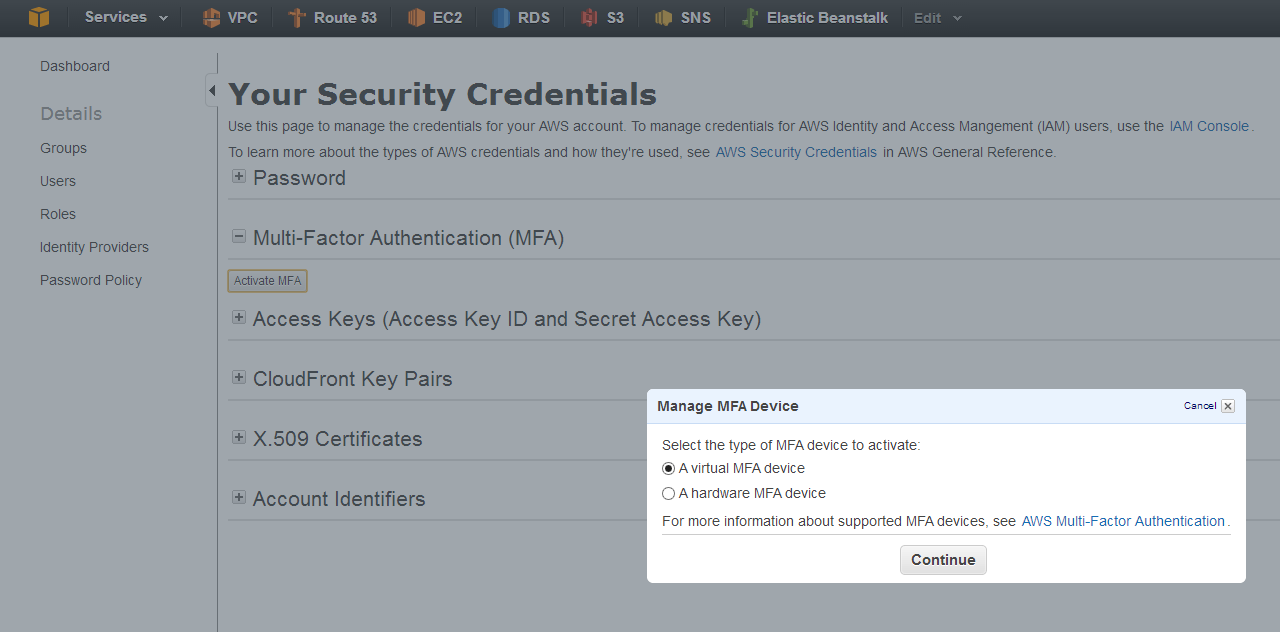
Enabling MFA for an IAM User
Enabling MFA for an IAM user is a straightforward process. These steps assume you are already logged into the AWS Management Console with appropriate permissions.
- Navigate to the IAM console and select “Users”.
- Choose the user for whom you want to enable MFA.
- Select “Security credentials” from the user’s details page.
- Click “Manage” next to “Multi-factor authentication (MFA)”.
- Choose your preferred MFA method (e.g., virtual MFA device). If selecting a virtual MFA device, you will need to download an authenticator app like Google Authenticator or Authy.
- Follow the on-screen instructions to activate your chosen MFA method. This will typically involve scanning a QR code with your authenticator app.
- After successful activation, verify the MFA by entering a code from your authenticator app.
Comparison of AWS MFA Methods
The following table compares the different AWS MFA methods based on their security level and complexity:
| MFA Method | Security Level | Complexity | Cost |
|---|---|---|---|
| Virtual MFA Device (e.g., Google Authenticator) | High | Low | Free (app cost may apply) |
| Hardware Security Key (e.g., YubiKey) | Very High | Medium | Moderate (key cost applies) |
| Time-Based One-Time Password (TOTP) | High | Low | Free |
Implementing MFA for Various AWS Services
Multi-factor authentication (MFA) is paramount for bolstering the security of your AWS environment. While the overview covered the “why” of MFA, this section dives into the “how,” focusing on practical implementation across key AWS services and best practices for management. We’ll explore specific steps for EC2, S3, and RDS, discuss cross-service and account management, and look at integrating with third-party providers.
MFA Implementation for Amazon EC2
Enabling MFA for EC2 primarily focuses on securing access to your EC2 instances and related resources. This is achieved through securing your IAM users and roles with MFA. The process involves associating an MFA device (like a virtual MFA device or a physical security key) with the IAM user or role that will interact with EC2. This ensures that even if someone compromises your credentials, they’ll still need the MFA code to access your EC2 instances.
Furthermore, restricting access through IAM roles with MFA attached, and using session management features like session profiles can further strengthen your EC2 security posture.
MFA Implementation for Amazon S3
Securing Amazon S3 buckets with MFA involves securing the IAM users and roles that have permissions to access your S3 buckets. Similar to EC2, this involves associating an MFA device with the relevant IAM identities. Additionally, using IAM policies to control access to specific S3 buckets, along with S3 access logs for auditing, are vital components of a robust S3 security strategy.
Enabling MFA Delete for S3 buckets adds an extra layer of protection by requiring MFA to delete buckets. This prevents accidental or malicious deletion of important data.
MFA Implementation for Amazon RDS
Protecting your Amazon RDS instances with MFA primarily involves securing the database users and their associated IAM roles. This is crucial to prevent unauthorized access to your databases. You can leverage IAM roles with MFA to connect to your RDS instances. Additionally, database-level security measures like encryption and access controls complement MFA and enhance overall security. Regularly reviewing and updating IAM permissions is crucial to maintain a secure configuration.
Managing MFA Across AWS Services and Accounts
Efficient MFA management across various AWS services and accounts requires a structured approach. Centralized management of IAM users and roles, along with consistent MFA device assignment policies, are key. Using AWS Identity and Access Management (IAM) groups to assign permissions and MFA requirements to multiple users simplifies administration. Regular audits of IAM access and MFA device status help maintain security and identify potential vulnerabilities.
Consider using AWS Organizations to manage MFA policies across multiple accounts consistently.
Integrating MFA with Third-Party Authentication Providers
AWS supports integration with various third-party authentication providers, allowing you to leverage existing identity management systems. This integration often involves using SAML (Security Assertion Markup Language) or other federation protocols. This streamlines user management and allows for a more unified authentication experience across your AWS and other enterprise systems. Proper configuration of the third-party provider and its integration with AWS IAM is essential for seamless and secure MFA implementation.
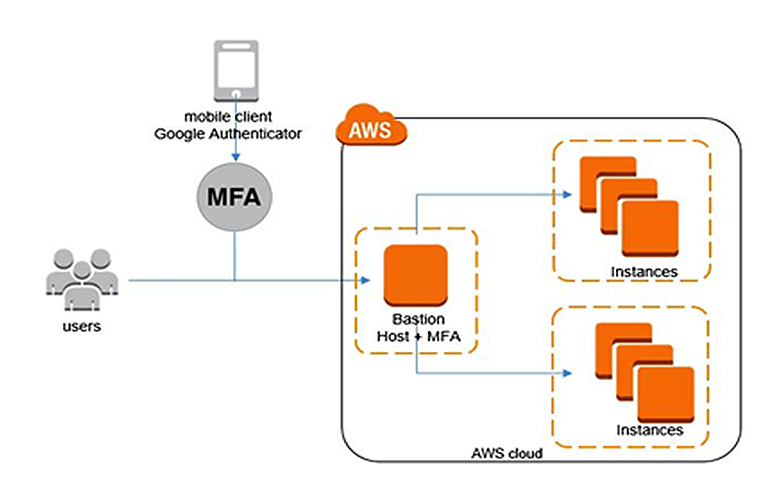
Authentication Process with MFA Enabled
This diagram illustrates the authentication flow with MFA enabled. First, the user attempts to access an AWS service. The AWS system verifies the username and password. If successful, a request for an MFA code is sent to the user’s registered MFA device (e.g., a phone or security key). The user enters the code. Finally, upon successful verification of the MFA code, the AWS system grants access to the requested service. The entire process involves several steps, ensuring a strong authentication mechanism. Failure at any step results in access denial.
Security Best Practices and Considerations
Implementing Multi-Factor Authentication (MFA) is a crucial step in bolstering AWS security, but its effectiveness hinges on proper configuration and ongoing vigilance. Failing to address potential vulnerabilities can negate the benefits of MFA, leaving your AWS environment exposed to various threats. This section delves into best practices and considerations for maximizing the security provided by MFA.
Potential Security Risks Associated with Improper MFA Configuration
Incorrectly configured MFA can introduce significant security risks. For example, using weak or easily guessable passwords in conjunction with MFA provides a false sense of security. An attacker who compromises a user’s password could still gain access if the MFA method is poorly implemented or if the user is tricked into providing their MFA codes (e.g., through phishing). Another risk involves failing to enforce MFA for all privileged accounts, leaving critical systems vulnerable.
Finally, neglecting regular audits and reviews of MFA configurations can lead to outdated or ineffective security measures. A comprehensive approach to MFA configuration necessitates careful consideration of all potential weaknesses.
Comparison of Different MFA Strategies for Various Security Levels
Various MFA strategies exist, each offering different levels of security. Time-based One-Time Passwords (TOTP), using applications like Google Authenticator or Authy, provide a strong balance between security and usability. Hardware security keys, such as Yubikeys, offer the highest level of security by utilizing cryptographic methods to verify identity. SMS-based MFA, while convenient, is considered less secure due to vulnerabilities in SMS infrastructure, making it susceptible to SIM swapping attacks.
The choice of MFA strategy should align with the sensitivity of the data and resources being protected. For highly sensitive systems, hardware security keys are recommended, while TOTP might suffice for less critical accounts. Organizations should implement a tiered approach, tailoring the MFA method to the risk level associated with each account and its associated privileges.
Examples of MFA Mitigation of Common AWS Security Threats
MFA significantly mitigates common AWS security threats. For instance, it acts as a strong deterrent against brute-force attacks, where attackers attempt to guess passwords repeatedly. Even if an attacker obtains a user’s password, they still require access to the MFA device to gain access. Similarly, MFA protects against credential stuffing attacks, where attackers use stolen credentials from other breaches to attempt to access AWS accounts.
MFA also helps prevent unauthorized access from compromised devices or malware-infected systems. By requiring an additional factor of authentication, MFA adds a layer of defense that significantly reduces the likelihood of successful attacks.
Recommended Security Audits for Verifying MFA Implementation
Regular security audits are vital to ensure the continued effectiveness of MFA. These audits should encompass verification of MFA enforcement across all relevant AWS services, review of access keys and IAM roles to ensure appropriate MFA policies are applied, assessment of the strength and security of MFA methods in use, and examination of logs for any suspicious MFA-related activity.
Furthermore, regular testing of the MFA infrastructure, including simulating attacks and checking for vulnerabilities, should be performed. The frequency of these audits should depend on the sensitivity of the data and the risk profile of the organization. A well-defined audit plan, including a schedule and defined responsibilities, is essential for maintaining a robust MFA security posture.
Troubleshooting and Common Issues
Setting up and using Multi-Factor Authentication (MFA) on AWS is generally straightforward, but occasional hiccups can occur. This section addresses common problems encountered during MFA setup and provides solutions for regaining access when necessary. Understanding these potential issues can significantly improve your overall security posture and minimize downtime.
Common MFA Setup Problems and Solutions
Troubleshooting MFA often involves verifying basic connectivity and configuration settings. Incorrectly configured MFA devices or network issues are frequently the root cause of problems. Below are some common problems and their solutions.
- Problem: Unable to activate MFA on a specific AWS service. Solution: Verify that the service supports MFA and that the correct IAM permissions are assigned to the user. Check for any service-specific configuration requirements.
- Problem: Incorrect MFA codes are consistently being rejected. Solution: Double-check the code entered for typos. Ensure your MFA device is synchronized with the correct time. If using a time-based one-time password (TOTP) device, check the device’s battery and ensure it’s properly configured.
- Problem: MFA device is not recognized by AWS. Solution: Ensure the device is properly registered with your AWS account. If using a virtual MFA device, verify that the appropriate application is installed and configured correctly. Review the AWS documentation for your specific MFA device type.
- Problem: Network connectivity issues prevent MFA authentication. Solution: Verify your internet connection and check for any network firewalls or proxies that might be blocking access to AWS MFA services. Try connecting from a different network to rule out network-related problems.
Recovering Access After MFA Device Loss or Compromise
Losing or compromising your MFA device can severely restrict your access to AWS resources. Fortunately, AWS provides mechanisms to recover access. The specific recovery process depends on the type of MFA device used.
- Virtual MFA Devices (e.g., Google Authenticator, Authy): If you lose access to your smartphone, you’ll need to add a new virtual MFA device to your AWS account. This involves going through the MFA registration process again. You may need to contact your AWS administrator for assistance.
- Hardware MFA Devices (e.g., physical security keys): Recovery from a lost or compromised hardware device is more complex. It often involves contacting AWS support and potentially undergoing a more rigorous verification process to prove your identity. Having a backup recovery method in place, such as a trusted contact, is highly recommended.
Managing MFA for Departing Employees
When an employee leaves an organization, it’s crucial to immediately revoke their access to AWS resources. This includes disabling their MFA devices. Failing to do so poses a significant security risk.
The process typically involves removing the employee’s IAM user from all relevant groups and policies, effectively removing their access privileges. Then, their MFA device should be explicitly deactivated or deregistered within the AWS Management Console. This prevents the former employee from accessing the AWS account even if they still possess their MFA device.
MFA Troubleshooting Flowchart
Start -> Is there a network connection issue? -> Yes: Check internet connection, firewall, proxy settings -> No: Is the MFA code correct? -> Yes: Proceed to AWS service -> No: Verify code, check device time, battery -> Is the MFA device registered? -> Yes: Contact AWS Support -> No: Register MFA device -> End
So Amazon Web Services is cracking down on security, mandating MFA for everyone. It makes sense, right? Better security for our cloud apps. This got me thinking about application development in general, and how platforms like those discussed in this great article on domino app dev the low code and pro code future are also stepping up their security game.
Ultimately, robust security, whether it’s MFA on AWS or secure coding practices, is crucial for any modern application.
AWS MFA and Compliance: Amazon Web Services Mandates Mfa Security
Implementing multi-factor authentication (MFA) in your AWS environment isn’t just a good security practice; it’s often a requirement for meeting various industry compliance standards. Failing to do so can expose your organization to significant financial and reputational risks. This section explores how AWS MFA contributes to compliance and how to effectively document and report on its implementation.AWS MFA significantly strengthens your security posture, making it a key component in achieving compliance with several regulatory frameworks.
By adding that extra layer of verification, you reduce the likelihood of unauthorized access, data breaches, and subsequent non-compliance penalties. Proper documentation and reporting are crucial for demonstrating to auditors that you’re meeting these requirements.
Meeting Industry Compliance Standards with AWS MFA
Many regulatory frameworks mandate or strongly recommend the use of MFA for accessing sensitive systems and data. For example, HIPAA (Health Insurance Portability and Accountability Act) requires robust security measures to protect Protected Health Information (PHI). PCI DSS (Payment Card Industry Data Security Standard) mandates strong authentication for accessing systems that store, process, or transmit cardholder data. Implementing AWS MFA helps demonstrate adherence to these requirements by providing a verifiable second factor of authentication, thereby reducing the risk of unauthorized access and data breaches.
Other relevant standards, such as NIST Cybersecurity Framework and ISO 27001, also benefit from the enhanced security provided by MFA.
Documenting MFA Implementation for Audits
Thorough documentation is vital for demonstrating compliance during audits. This documentation should include a clear Artikel of your MFA implementation strategy, detailing which AWS services have MFA enabled, the types of MFA devices used (e.g., virtual MFA devices, hardware tokens), and the policies governing MFA access. Maintain a detailed record of all configuration changes, including dates, users involved, and the reasons for the changes.
This meticulous record-keeping will streamline the audit process and show your commitment to security. Consider using a centralized documentation repository, accessible only to authorized personnel, to maintain version control and ensure the integrity of your documentation. For instance, a wiki or a dedicated section within your security information and event management (SIEM) system could serve this purpose.
Reporting on MFA Usage and Effectiveness
Regular reporting on MFA usage and effectiveness provides valuable insights into the security posture of your AWS environment. AWS CloudTrail can be leveraged to track MFA usage, providing logs of successful and unsuccessful MFA attempts. This data can be analyzed to identify trends, potential weaknesses, and areas for improvement. For example, reports can show the percentage of users who are using MFA, the types of MFA devices used, and the frequency of MFA failures.
This information can be used to improve security policies, address potential vulnerabilities, and demonstrate compliance to auditors. Consider using AWS services like Amazon Athena or Amazon QuickSight to visualize and analyze this data, creating dashboards that present key metrics in a clear and concise manner. These reports should be regularly reviewed and updated to reflect the current state of your security posture.
Relevant Compliance Standards and Their Relation to AWS MFA
The following table summarizes some key compliance standards and their relationship to AWS MFA:
| Compliance Standard | Relevance to AWS MFA |
|---|---|
| HIPAA | MFA helps protect PHI by adding an extra layer of security to access control. |
| PCI DSS | MFA is a crucial element in securing systems that handle cardholder data. |
| NIST Cybersecurity Framework | MFA aligns with the framework’s principles for identity and access management. |
| ISO 27001 | MFA contributes to the overall security controls required by this standard. |
Cost Considerations of MFA Implementation
Implementing multi-factor authentication (MFA) significantly enhances AWS security, but it’s crucial to understand the associated costs. This isn’t just about the price of hardware or software; it also involves considering the time investment in setup, training, and potential troubleshooting. A thorough cost-benefit analysis is essential before rolling out MFA across your AWS environment.
MFA Method Costs, Amazon web services mandates mfa security
Different MFA methods carry varying price tags. Hardware tokens, such as those from YubiKey, involve upfront costs for purchasing the physical devices themselves. These costs increase proportionally with the number of users requiring MFA. Virtual MFA devices, often provided through applications like Google Authenticator or Authy, generally have lower upfront costs, as they are often free to download and use, though you may have management costs associated with distributing and supporting them.
However, reliance on users to download and manage these apps introduces a degree of operational overhead. Finally, SMS-based MFA, while seemingly inexpensive, can be vulnerable to SIM swapping attacks and should be considered a less secure option, despite its apparent low cost.
Cost-Benefit Analysis of MFA Implementation
The cost-benefit analysis of MFA hinges on balancing the expense of implementation against the potential financial losses from security breaches. A successful breach can result in significant costs associated with data recovery, regulatory fines, reputational damage, and legal fees. For example, a hypothetical company experiencing a data breach costing $1 million would find the cost of implementing MFA across its entire AWS environment easily justified even if the upfront costs were significant.
The prevention of even a single major breach typically far outweighs the cost of MFA.
Strategies for Optimizing MFA Costs
Several strategies can help optimize MFA costs without sacrificing security. Firstly, carefully consider the level of security required for different user groups. Administrators managing sensitive resources might warrant the enhanced security of hardware tokens, while less sensitive roles could potentially utilize virtual MFA devices. Secondly, leveraging AWS’s built-in MFA capabilities, such as those integrated with IAM, can minimize the need for third-party solutions and reduce costs.
Thirdly, proper training and clear documentation can reduce the support overhead associated with MFA implementation, decreasing the long-term cost. Finally, regular audits and reviews of your MFA setup can identify and rectify any inefficiencies.
Cost Comparison Table for Various MFA Options
| MFA Method | Upfront Cost per User | Recurring Cost per User (Annual) | Security Level |
|---|---|---|---|
| Hardware Token (e.g., YubiKey) | $30 – $70 | $0 | High |
| Virtual MFA Device (e.g., Google Authenticator) | $0 | $0 | Medium |
| SMS-Based MFA | $0 | Variable (depending on SMS provider) | Low |
Final Summary
Securing your AWS environment is a continuous process, and implementing MFA is a huge step in the right direction. While it might seem like an extra layer of complexity at first, the enhanced security it provides far outweighs any initial inconvenience. Remember, proactive security measures are far better than reactive ones, especially when dealing with sensitive data. By understanding the different MFA options, implementing best practices, and addressing potential issues proactively, you can significantly reduce your risk and build a more secure and resilient AWS infrastructure.
So, take the time to understand and implement MFA – your data will thank you for it!
FAQ Compilation
What happens if I lose my MFA device?
AWS provides mechanisms for recovering access. You’ll typically need to contact AWS support or follow their recovery procedures, which might involve verifying your identity through other means.
Is MFA required for all AWS services?
While AWS strongly encourages MFA for all services, the specific requirement might vary depending on the service and your configuration. However, enabling MFA for your IAM users is crucial regardless.
How much does MFA cost?
The cost varies depending on the MFA method you choose. Virtual MFA devices are generally less expensive than hardware tokens. Check the AWS pricing page for the most up-to-date costs.
Can I use a third-party MFA provider with AWS?
Yes, AWS supports integration with several third-party authentication providers, offering flexibility in your security setup.