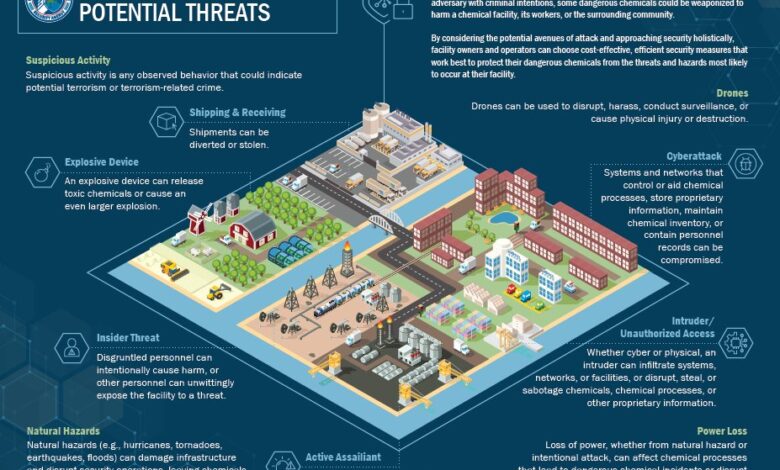
American Chemical Facilities Vulnerable to Cyberattacks
American chemical facilities are vulnerable to cyber attacks – American chemical facilities are vulnerable to cyberattacks, a chilling reality that demands our immediate attention. This isn’t just some abstract threat; it’s a potential catastrophe waiting to happen. We’re talking about facilities handling incredibly hazardous materials, where a successful cyberattack could lead to environmental disasters, economic ruin, and even loss of life. Think about the potential for a ransomware attack crippling a plant’s safety systems, or a sophisticated intrusion manipulating chemical processes with devastating consequences.
This post dives into the vulnerabilities, threats, and what we can do to prevent a disaster.
The sheer complexity of the chemical industry’s infrastructure, often relying on outdated systems and interconnected networks, makes it a particularly tempting target. Phishing scams, malware infections, and even simple human error can open the door to devastating consequences. We’ll explore the various attack vectors, the regulatory landscape, and the crucial role of public-private partnerships in mitigating this risk.
It’s a critical issue, and understanding the challenges and solutions is vital for safeguarding our communities and environment.
Types of Cyber Threats Facing American Chemical Facilities
American chemical facilities, vital components of our nation’s infrastructure, are increasingly vulnerable to sophisticated cyberattacks. These attacks not only disrupt operations and cause economic losses but also pose significant risks to public health and the environment. Understanding the nature and impact of these threats is crucial for implementing effective cybersecurity measures.
The chemical industry relies heavily on interconnected systems for process control, supply chain management, and data storage. This interconnectedness, while beneficial for efficiency, creates numerous entry points for malicious actors. The consequences of a successful cyberattack can range from minor operational disruptions to catastrophic failures with widespread repercussions.
Prevalent Cyber Threats and Attack Methods
Chemical facilities face a diverse range of cyber threats, each employing unique attack methods. Phishing attacks, for example, often target employees with deceptive emails or messages designed to trick them into revealing sensitive credentials or downloading malware. Malware, including viruses, worms, and Trojans, can compromise systems, steal data, and disrupt operations. Ransomware attacks encrypt critical data, demanding payment for its release, potentially halting production and causing significant financial losses.
Advanced Persistent Threats (APTs) involve sustained, stealthy attacks by state-sponsored or highly organized criminal groups, often aiming to steal intellectual property or gain long-term access to sensitive systems. Denial-of-Service (DoS) attacks flood systems with traffic, rendering them inaccessible and disrupting operations. Finally, supply chain attacks compromise vendors or third-party suppliers to gain access to the target facility’s network.
Effectiveness of Attack Vectors Against Implemented Security Measures
The effectiveness of various attack vectors varies depending on the security measures implemented by the chemical facility. While strong passwords, multi-factor authentication, and intrusion detection systems can mitigate the effectiveness of phishing and some malware attacks, more sophisticated threats like APTs can often bypass these defenses. Ransomware, particularly when coupled with social engineering techniques, can prove highly effective, even against well-protected facilities.
The effectiveness of any security measure is also dependent on employee training and awareness. Regular security audits and penetration testing are essential to identify vulnerabilities and strengthen defenses.
Potential Consequences of Successful Cyberattacks
The consequences of a successful cyberattack on a chemical facility can be devastating. A compromised safety system could lead to chemical leaks, explosions, or fires, resulting in environmental damage, injuries, and fatalities. Disruption of production processes can cause significant economic losses, impacting the facility’s profitability and potentially the entire supply chain. Theft of intellectual property can provide competitors with a significant advantage.
Furthermore, the release of sensitive data, such as customer information or trade secrets, can damage the facility’s reputation and lead to legal repercussions. The public health consequences could be severe, especially if hazardous materials are involved.
Frequency and Severity of Cyber Threats Against Chemical Facilities
| Threat Type | Frequency | Severity | Impact |
|---|---|---|---|
| Phishing | High | Medium | Data breaches, malware infections |
| Malware | High | High | System disruption, data theft, ransomware |
| Ransomware | Medium | High | Operational shutdown, data loss, financial losses |
| Advanced Persistent Threats (APTs) | Low | Very High | Data theft, intellectual property loss, long-term compromise |
| Denial-of-Service (DoS) | Medium | Medium | Service disruption, operational delays |
| Supply Chain Attacks | Low | High | Indirect access to systems, data breaches |
Vulnerabilities in Chemical Facility Cybersecurity Infrastructure

The cybersecurity of American chemical facilities is a critical concern, given the potential for devastating consequences from successful cyberattacks. These facilities rely heavily on Industrial Control Systems (ICS), which often present significant vulnerabilities due to a combination of outdated technology, legacy systems, and a lack of comprehensive security protocols. Understanding these vulnerabilities is crucial for developing effective mitigation strategies.The inherent vulnerabilities within ICS used in chemical plants stem from a variety of factors, making them particularly susceptible to cyberattacks.
These systems, designed decades ago, often lack the built-in security features found in modern IT systems. This creates a significant gap in protection against sophisticated attacks. Furthermore, the specialized nature of ICS and the expertise required to manage them can lead to a shortage of skilled cybersecurity professionals capable of adequately securing these critical infrastructures.
Outdated Software and Hardware in Chemical Facilities
Many chemical facilities still operate with outdated software and hardware, posing considerable security risks. Examples include legacy Programmable Logic Controllers (PLCs) running on obsolete operating systems with known vulnerabilities. These systems often lack patching mechanisms, leaving them exposed to exploits. Similarly, outdated Supervisory Control and Data Acquisition (SCADA) systems may lack robust authentication and authorization controls, allowing unauthorized access.
The risks associated with this outdated technology include remote compromise, data breaches, and even physical damage to equipment through malicious manipulation of control processes. For instance, a known vulnerability in a specific PLC model could allow an attacker to remotely inject malicious code, potentially disrupting chemical processes or causing a safety hazard.
Challenges in Implementing Robust Cybersecurity Measures in Legacy Systems, American chemical facilities are vulnerable to cyber attacks
Implementing robust cybersecurity measures in legacy systems presents numerous challenges. Upgrading or replacing these systems can be incredibly expensive and disruptive to operations, making it a difficult proposition for many facilities. Furthermore, finding compatible security solutions for older systems can be problematic, as many modern security tools are not designed to work with legacy hardware and software. The complexity of these systems also makes it difficult to conduct thorough security assessments and implement effective monitoring solutions.
The risk of introducing errors during upgrades or modifications adds another layer of complexity, potentially causing more harm than good. For example, a poorly planned upgrade could disrupt operations, leading to production downtime and financial losses.
Hypothetical Cyberattack Scenario
Imagine a scenario where a chemical plant relies on a legacy SCADA system with known vulnerabilities in its communication protocols. A sophisticated attacker could exploit these vulnerabilities to gain unauthorized access to the system. Once inside, the attacker could manipulate process variables, such as temperature or pressure, leading to a controlled chemical reaction. This could result in a chemical spill, explosion, or other catastrophic event.
The attacker might initially conduct reconnaissance, identifying weak points in the network and the specific vulnerabilities in the legacy SCADA system through open-source intelligence or social engineering. Subsequently, they could use custom-made malware to exploit these weaknesses, gaining control of the system and manipulating the plant’s operations for malicious purposes. This scenario highlights the severe consequences of neglecting cybersecurity in chemical facilities and the critical need for proactive security measures.
Regulatory Landscape and Compliance Measures
The cybersecurity of American chemical facilities is a complex issue, interwoven with a patchwork of federal, state, and sometimes even local regulations. These regulations aim to mitigate the risk of cyberattacks that could lead to catastrophic consequences, from environmental damage to public health crises. Navigating this regulatory landscape presents significant challenges for facilities, requiring a multifaceted approach to compliance.The primary federal legislation impacting chemical facility cybersecurity is the Cybersecurity Information Sharing Act (CISA) of 2015.
While not specifically targeted at the chemical industry, CISA encourages information sharing between the private sector and the government regarding cybersecurity threats. This voluntary information sharing is crucial for developing a comprehensive understanding of evolving threats and vulnerabilities. Beyond CISA, sector-specific regulations, often enforced by agencies like the Environmental Protection Agency (EPA) and the Department of Homeland Security (DHS), add layers of complexity.
These regulations often incorporate cybersecurity requirements within broader safety and environmental mandates. For example, regulations concerning the reporting of chemical releases may indirectly impact cybersecurity by necessitating robust data management and security protocols.
Key Regulations and Compliance Standards
Several key regulations and compliance standards directly or indirectly influence the cybersecurity posture of American chemical facilities. These include, but are not limited to, the aforementioned CISA, EPA regulations related to risk management plans (RMPs), and DHS guidance on critical infrastructure protection. Compliance with these regulations often involves implementing robust security measures such as network segmentation, intrusion detection systems, and employee security awareness training.
Furthermore, industry best practices, like those Artikeld by the National Institute of Standards and Technology (NIST), are frequently incorporated into compliance programs.
Challenges in Meeting Compliance Standards
Meeting these standards presents numerous challenges for chemical facilities. Budgetary constraints are a significant hurdle. Implementing and maintaining comprehensive cybersecurity systems requires substantial investment in hardware, software, personnel, and ongoing training. Smaller facilities, in particular, may struggle to allocate the necessary resources. Technological limitations also pose a significant challenge.
Many older facilities rely on legacy systems that may be incompatible with modern cybersecurity solutions, requiring costly upgrades or replacements. The sheer complexity of modern cybersecurity threats, coupled with the evolving regulatory landscape, further complicates compliance efforts. Keeping abreast of the latest threats and vulnerabilities requires ongoing investment in expertise and resources. Finally, a shortage of skilled cybersecurity professionals adds another layer of difficulty for many facilities.
Best Practices for Compliance
To effectively navigate the regulatory landscape and achieve compliance, chemical facilities should adopt a multi-layered approach. This includes:
- Regular vulnerability assessments and penetration testing to identify and address weaknesses in their systems.
- Implementation of robust access control measures, including multi-factor authentication and strong password policies.
- Development and implementation of incident response plans to effectively manage and mitigate cybersecurity incidents.
- Employee training programs to raise awareness of cybersecurity threats and best practices.
- Regular security audits to ensure compliance with relevant regulations and standards.
- Collaboration with industry peers and government agencies to share information and best practices.
Comparison of Regulatory Approaches Across Countries
Different countries employ varying approaches to regulating cybersecurity in the chemical sector. Some countries, like the United States, rely on a combination of sector-specific regulations and voluntary information sharing initiatives. Others adopt a more prescriptive approach, mandating specific security controls and technologies. The effectiveness of these different approaches is a subject of ongoing debate. A purely prescriptive approach may stifle innovation and place undue burden on smaller facilities.
A more flexible, risk-based approach, however, may not provide sufficient protection against sophisticated cyberattacks. The optimal approach likely involves a balance between regulatory mandates and incentives for proactive security measures, tailored to the specific risks and capabilities of different facilities and national contexts. The European Union’s General Data Protection Regulation (GDPR), for example, while not solely focused on chemical facilities, has influenced cybersecurity practices globally by emphasizing data protection and privacy, impacting how chemical companies handle sensitive information.
Mitigation Strategies and Best Practices: American Chemical Facilities Are Vulnerable To Cyber Attacks

Protecting American chemical facilities from cyberattacks requires a multi-layered approach encompassing robust technological safeguards and comprehensive employee training. Failing to implement effective mitigation strategies can lead to devastating consequences, including operational disruptions, environmental damage, and even loss of life. This section Artikels key strategies and best practices for bolstering cybersecurity in the chemical industry.
Multi-Factor Authentication (MFA) Implementation and Effectiveness
Multi-factor authentication (MFA) significantly enhances security by requiring users to provide multiple forms of verification before accessing systems or data. Instead of relying solely on a password, MFA adds another layer, such as a one-time code sent to a mobile device, a biometric scan, or a security token. This makes it exponentially more difficult for attackers to gain unauthorized access, even if they manage to obtain a password.
For example, even if a hacker obtains an employee’s password through phishing, they would still need to overcome the additional MFA hurdle. The effectiveness of MFA is demonstrated by its widespread adoption across various sectors, significantly reducing successful breaches. A well-implemented MFA system can dramatically reduce the risk of unauthorized access and data breaches, protecting sensitive operational technology (OT) and critical infrastructure.
Security Awareness Training: Preventing Human Error
Human error remains a major vulnerability in cybersecurity. Phishing emails, social engineering tactics, and accidental clicks on malicious links can all compromise a facility’s security. Comprehensive security awareness training is crucial to mitigate these risks. Effective training programs should educate employees about various cyber threats, such as phishing, malware, and ransomware, and provide practical guidance on identifying and responding to suspicious activities.
Regular training sessions, including simulated phishing attacks, reinforce best practices and keep employees updated on evolving threats. For instance, training could cover recognizing suspicious email attachments, avoiding clicking on unknown links, and reporting any suspected security incidents immediately. A culture of security awareness, fostered through ongoing training and reinforcement, is essential for reducing human error-related cyberattacks.
Intrusion Detection and Prevention Systems (IDPS) in Chemical Facilities
Intrusion detection and prevention systems (IDPS) are critical components of a robust cybersecurity infrastructure. These systems monitor network traffic and system activity for malicious behavior, providing early warning of potential attacks. Intrusion detection systems (IDS) identify suspicious activity and alert security personnel, while intrusion prevention systems (IPS) actively block or mitigate threats. In chemical facilities, IDPS can be deployed to monitor control systems, industrial networks, and other critical infrastructure.
For example, an IDPS could detect unauthorized access attempts to a facility’s process control system, alerting security personnel and potentially preventing a catastrophic event. The real-time monitoring and threat mitigation capabilities of IDPS are invaluable in protecting chemical facilities from sophisticated cyberattacks. The implementation of an IDPS requires careful planning and configuration to ensure optimal performance and effectiveness.
Cybersecurity Best Practices for American Chemical Facilities
Implementing a comprehensive cybersecurity strategy requires a multifaceted approach. The following best practices should be adopted by all American chemical facilities:
- Regularly update software and firmware on all systems and devices.
- Segment networks to isolate critical infrastructure from less critical systems.
- Implement strong password policies and enforce multi-factor authentication.
- Conduct regular security audits and vulnerability assessments.
- Develop and maintain an incident response plan.
- Provide comprehensive security awareness training to all employees.
- Employ robust data backup and recovery procedures.
- Monitor network traffic and system activity for suspicious behavior.
- Implement access control measures to restrict access to sensitive systems and data.
- Regularly review and update security policies and procedures.
The Role of Public-Private Partnerships
The cybersecurity of American chemical facilities is a shared responsibility, demanding a collaborative approach that transcends traditional boundaries. Effective protection requires a robust public-private partnership (PPP) encompassing government agencies, chemical industry stakeholders, and leading cybersecurity experts. This collaborative model leverages the unique strengths of each participant, fostering a more resilient and secure landscape for the chemical sector.The importance of collaboration stems from the multifaceted nature of cyber threats.
Government agencies possess regulatory power, intelligence gathering capabilities, and access to broader threat information. Industry stakeholders, on the other hand, possess intimate knowledge of their own systems, vulnerabilities, and operational realities. Cybersecurity experts bring specialized skills in threat detection, response, and prevention. By working together, these entities can develop and implement comprehensive strategies that address the full spectrum of cyber risks.
Examples of Successful Public-Private Partnerships in Critical Infrastructure
Successful PPPs in other critical infrastructure sectors offer valuable lessons for the chemical industry. For example, the partnership between the Department of Homeland Security (DHS) and the electric power sector has significantly enhanced grid security through information sharing initiatives and joint vulnerability assessments. Similarly, collaborations between the transportation sector and government agencies have led to improved cybersecurity protocols for critical transportation systems.
These examples demonstrate the tangible benefits of coordinated efforts in mitigating cyber risks across various critical infrastructure domains. The key element in these successful partnerships is the establishment of trust and open communication channels.
Benefits of Information Sharing and Threat Intelligence Collaboration
The free flow of information is crucial for effective cybersecurity. Information sharing allows chemical facilities to learn from each other’s experiences, identify emerging threats, and proactively implement preventative measures. Threat intelligence collaboration enables the early detection of malicious activity, facilitating timely responses and minimizing potential damage. A centralized platform for sharing threat intelligence, managed by a neutral party (potentially a government agency or a trusted third-party organization), could be particularly valuable.
This would allow companies to anonymously report incidents, share vulnerability information, and receive alerts on emerging threats without fear of competitive disadvantage.
Framework for a Public-Private Partnership for Chemical Facility Cybersecurity
A successful PPP for enhancing cybersecurity in American chemical facilities should include several key components. First, a clear governance structure is essential, defining roles and responsibilities for each participating entity. This structure should facilitate effective communication and decision-making. Second, a robust information sharing mechanism is needed, ensuring the timely dissemination of threat intelligence and best practices. This could involve a secure online platform or a series of regular meetings and workshops.
Seriously, the vulnerability of American chemical facilities to cyberattacks is terrifying. We need robust, secure systems to protect these critical infrastructure points, and that’s where advancements like those discussed in this article on domino app dev the low code and pro code future become crucial. Faster, more efficient development cycles could mean quicker deployment of essential security upgrades, ultimately making those facilities less susceptible to attack.
It’s a critical area needing immediate attention.
Third, a program for joint vulnerability assessments and penetration testing should be established, allowing facilities to identify and address their weaknesses proactively. Fourth, the development of standardized cybersecurity protocols and guidelines, tailored to the specific needs of the chemical industry, is crucial for consistent and effective protection. Finally, a mechanism for providing financial incentives and technical assistance to smaller facilities, which may lack the resources to implement robust cybersecurity measures independently, should be incorporated.
This comprehensive framework would create a proactive and collaborative environment to effectively combat cyber threats against American chemical facilities.
Final Thoughts
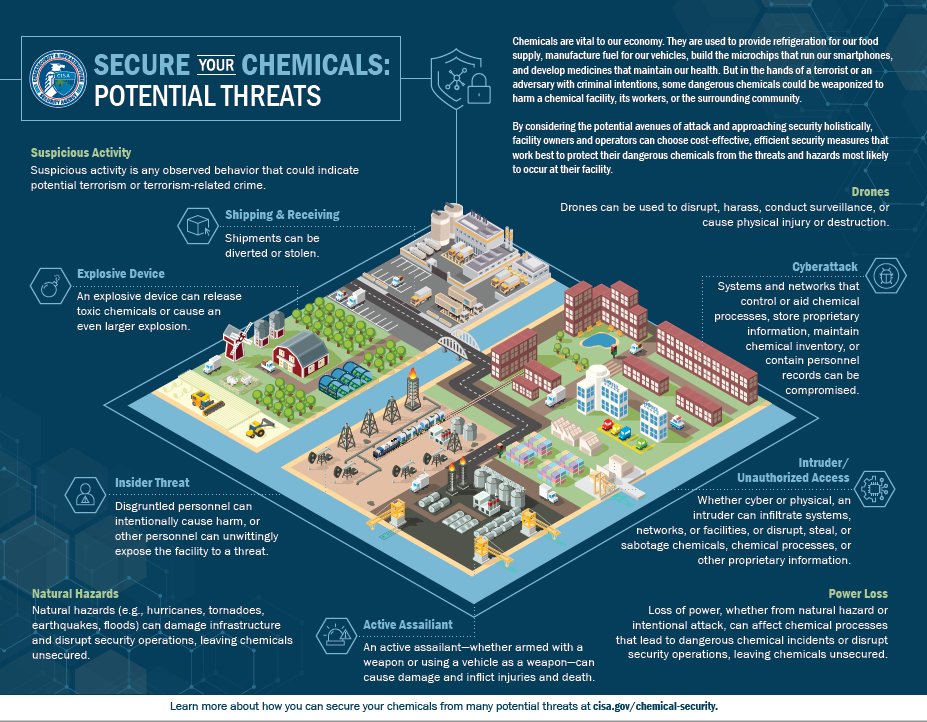
The vulnerability of American chemical facilities to cyberattacks is a serious and multifaceted problem. While the challenges are significant, ranging from legacy systems to budgetary constraints, the potential consequences of inaction are far greater. By understanding the threats, implementing robust cybersecurity measures, and fostering strong public-private partnerships, we can significantly reduce the risk. This isn’t just about protecting industry profits; it’s about protecting our lives, our environment, and our national security.
Let’s work together to make our chemical facilities safer and more resilient in the face of these ever-evolving threats.
Questions and Answers
What are the most common types of malware targeting chemical facilities?
Common malware includes industrial espionage tools designed to steal process data, ransomware encrypting critical systems, and viruses designed to disrupt operations.
How can employees be trained to better prevent cyberattacks?
Regular security awareness training, including phishing simulations and best practice education, is key. This empowers employees to identify and report suspicious activity.
What is the role of the government in protecting chemical facilities?
Government agencies set regulations, provide guidance, and often partner with the private sector to share threat intelligence and improve overall cybersecurity posture.
What are some examples of successful public-private partnerships in cybersecurity?
Information sharing platforms and joint cybersecurity exercises between government agencies and industry groups are examples of successful partnerships.





