Americold Suffers a Ransomware Attack
Americold suffers a ransomware attack – a chilling headline that sent shockwaves through the global cold storage industry. This wasn’t just another data breach; it highlighted the vulnerability of critical infrastructure to sophisticated cyberattacks. The incident forced us to question the security protocols of even the largest players in the food supply chain and examine the ripple effects of such attacks on consumers and the economy.
This post delves into the details of the attack, its impact, and the crucial lessons learned.
From the initial breach to the lengthy recovery process, we’ll explore the nature of the ransomware, the attackers’ methods, and Americold’s response. We’ll also analyze the long-term consequences, including financial losses, reputational damage, and the changes implemented to improve cybersecurity. Finally, we’ll consider the broader implications for the cold storage industry and discuss steps that can be taken to prevent similar incidents in the future.
Americold’s Business Operations Before the Attack

Americold Realty Trust is a global leader in temperature-controlled warehousing and logistics. Before the ransomware attack, the company boasted a vast network of facilities strategically located across the globe, enabling them to manage the complex cold chain for a wide range of perishable goods. Understanding their operations before the attack is crucial to grasping the full impact of the incident.Americold’s global cold storage network and its key clients were diverse and extensive.
The company served a broad spectrum of clients, from large multinational food producers and retailers to smaller regional distributors. Their facilities handled everything from frozen foods and produce to pharmaceuticals and other temperature-sensitive products, showcasing the critical role they played in maintaining the global food supply chain and ensuring the integrity of various products. Key clients often included major players in the grocery, food processing, and pharmaceutical industries.
The sheer scale of their operations meant any disruption would have far-reaching consequences.
Americold’s IT Infrastructure and Cybersecurity Protocols Before the Attack
Prior to the ransomware attack, Americold, like many large corporations, possessed a sophisticated IT infrastructure supporting its global operations. This infrastructure likely included numerous servers, networks, and data centers distributed across its facilities worldwide. The exact details of their cybersecurity protocols before the incident remain largely undisclosed, however, it’s reasonable to assume they employed a range of security measures, including firewalls, intrusion detection systems, and antivirus software.
The effectiveness of these measures, however, was ultimately tested by the ransomware attack. The specifics of their vulnerability remain largely undisclosed due to ongoing investigations and legal considerations.
Potential Impact of a Ransomware Attack on Americold’s Supply Chain and Logistics
A ransomware attack on a company like Americold, with its complex global supply chain, could have several severe consequences. Disruption to their operations could lead to significant financial losses due to spoiled goods, delayed shipments, and potential penalties for contract breaches. The attack could also damage Americold’s reputation and erode customer trust, impacting future business opportunities. Furthermore, the loss or corruption of crucial data, including inventory management and logistics information, could severely cripple their operational efficiency.
The disruption to the cold chain could also have serious implications for food safety and public health. A scenario where temperature-sensitive goods are compromised due to system failures would have wide-ranging consequences.
Comparison of Americold’s Operations Before and After the Attack
| Aspect | Before Attack | After Attack | Impact |
|---|---|---|---|
| Operational Efficiency | High, supported by robust IT infrastructure | Significantly reduced, system disruptions | Major disruption to logistics and supply chain |
| Data Availability | Complete and readily accessible | Partially or completely unavailable, potentially corrupted | Loss of crucial operational and business data |
| Customer Relationships | Strong, based on reliable service delivery | Potentially damaged due to service disruptions | Loss of trust and potential loss of business |
| Financial Performance | Stable and profitable | Negative impact due to operational disruptions and recovery costs | Significant financial losses |
The Ransomware Attack
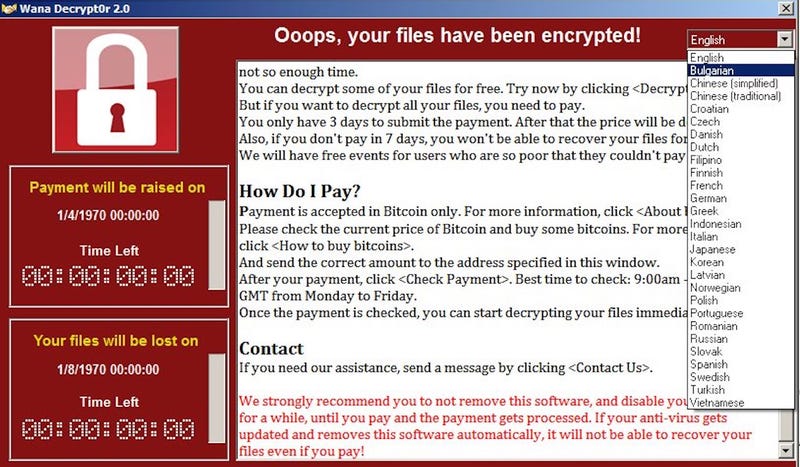
The ransomware attack on Americold in late 2020 caused significant disruption to the company’s operations and highlighted the vulnerability of even large, established businesses to cyber threats. While the specific type of ransomware used wasn’t publicly disclosed by Americold or authorities, the scale of the incident suggests a sophisticated and potent strain capable of widespread data encryption and system compromise.
The attack’s impact underscores the critical need for robust cybersecurity measures within supply chain logistics.The attackers likely employed a multi-stage attack, potentially exploiting vulnerabilities in Americold’s systems or utilizing phishing techniques to gain initial access. Once inside, they would have moved laterally across the network, identifying and targeting critical systems for encryption. The speed and efficiency of the attack suggest a level of planning and expertise, possibly indicating a professional ransomware group operating for financial gain.
Ransomware Type and Capabilities
While the specific ransomware variant remains undisclosed, the widespread disruption suggests a highly capable strain. It likely possessed the ability to encrypt various file types, including crucial operational data, financial records, and customer information. Advanced ransomware often incorporates techniques to evade detection by security software and to ensure data remains encrypted even after system restoration attempts. The attackers likely used a combination of encryption algorithms, making decryption exceptionally challenging without the decryption key held by the attackers.
Attack Methods and System Breach
The methods employed by the attackers likely involved a combination of social engineering and technical exploitation. Phishing emails targeting employees, potentially containing malicious attachments or links, could have been used to gain initial access. Alternatively, the attackers may have exploited known vulnerabilities in Americold’s software or infrastructure, leveraging zero-day exploits or known weaknesses to bypass security measures. Once inside the network, lateral movement would have been crucial, allowing the attackers to identify and compromise high-value targets.
This likely involved scanning the network, exploiting further vulnerabilities, and gaining administrator-level access to critical systems.
Extent of Data Encryption and Systems Affected
The attack resulted in widespread data encryption across Americold’s systems. While the exact extent of the data affected remains unclear, reports suggest that the disruption affected various aspects of the company’s operations, including warehouse management systems, logistics software, and potentially customer databases. The impact extended beyond simple file encryption, affecting the ability to access and manage critical operational data, leading to significant delays and disruptions in the supply chain.
The interconnected nature of Americold’s global network likely contributed to the wide-reaching impact of the attack.
The Americold ransomware attack highlights the vulnerability of even large corporations to cyber threats. Building robust, secure systems is crucial, and that’s where the future of app development comes in; learning more about efficient and secure application building is key, like exploring options detailed in this article on domino app dev the low code and pro code future.
Ultimately, understanding these advancements could help prevent future incidents like the Americold breach.
Attacker Demands and Ransom Payment
The attackers’ demands, like the specific ransomware used, weren’t publicly disclosed by Americold. However, it’s highly probable that the attackers demanded a ransom payment in exchange for the decryption key and a promise not to release stolen data. Whether or not Americold paid the ransom is unknown; many companies choose not to disclose such payments for various reasons, including fear of encouraging further attacks and potential legal ramifications.
However, the significant disruption caused by the attack, the potential loss of customer trust, and the costs associated with recovery likely weighed heavily in their decision-making process. The incident highlights the complex ethical and financial considerations faced by organizations when dealing with ransomware attacks.
Immediate Response and Recovery Efforts
Americold’s immediate response to the ransomware attack was swift and multi-faceted, prioritizing the containment of the breach and the preservation of critical data. The company activated its incident response plan, immediately engaging a team of cybersecurity experts and forensic investigators to assess the damage and begin the recovery process. This involved a coordinated effort across various departments, demanding a high level of collaboration and quick decision-making under immense pressure.The initial focus was on isolating affected systems to prevent further spread of the ransomware.
This involved shutting down vulnerable networks and servers, effectively creating a quarantine zone to contain the threat. Simultaneously, efforts began to identify the source of the attack and understand the extent of data encryption. This phase was crucial in determining the most effective recovery strategies and establishing a realistic timeline for restoring operations. The company’s experience in managing large-scale logistical operations proved invaluable in organizing and executing this complex response.
Data Recovery and System Restoration
Americold employed a multi-pronged approach to data recovery. Given the scale of the operation and the sensitivity of the data, a combination of strategies was deemed necessary. This included attempts to decrypt data using available decryption tools, exploring the possibility of recovering data from backups, and, as a last resort, rebuilding critical systems from scratch using redundant infrastructure.
The choice of approach varied depending on the specific system and the extent of encryption. The recovery team meticulously prioritized data based on its criticality to business operations, ensuring that essential functions were restored first. Regular updates and progress reports were crucial to maintaining transparency and managing stakeholder expectations.
Mitigation and Prevention Measures
Following the successful restoration of systems, Americold implemented a series of robust measures to mitigate further damage and prevent future attacks. This involved a comprehensive review and update of security protocols, including the implementation of multi-factor authentication, enhanced firewall protection, and rigorous employee training on cybersecurity best practices. Furthermore, Americold invested in advanced threat detection and response systems, enabling proactive monitoring and rapid identification of any future malicious activity.
The company also conducted a thorough post-incident review to identify vulnerabilities and improve its overall security posture. This included examining the effectiveness of existing security controls and identifying areas for improvement.
Key Steps During the Recovery Phase
The recovery phase involved a coordinated series of actions, prioritizing the restoration of critical systems and data. The following steps were key:
- Isolation of affected systems to prevent further spread of the ransomware.
- Engagement of cybersecurity experts and forensic investigators.
- Assessment of the extent of data encryption and system compromise.
- Prioritization of data recovery based on business criticality.
- Implementation of data recovery strategies (decryption, backups, system rebuild).
- Restoration of critical systems and functionalities.
- Implementation of enhanced security measures (multi-factor authentication, advanced threat detection).
- Comprehensive review and update of security protocols and employee training.
- Conducting a thorough post-incident review to identify vulnerabilities.
Long-Term Impacts and Lessons Learned
The Americold ransomware attack, while ultimately contained, left a significant mark on the company, impacting its finances, reputation, and operational efficiency. The long-term consequences extended beyond the immediate costs of recovery, highlighting crucial vulnerabilities in their pre-attack cybersecurity posture and underscoring the need for substantial improvements. Understanding these impacts is critical not only for Americold but also for other cold storage and logistics companies facing similar threats.The financial impact was substantial, encompassing direct costs like ransom payments (though Americold didn’t publicly confirm payment), the expense of incident response teams, legal fees, and the cost of restoring systems and data.
Indirect costs included lost revenue due to operational disruptions, potential penalties for regulatory non-compliance, and the expense of bolstering cybersecurity defenses. Reputational damage, though less easily quantified, was considerable. News of the attack could erode customer trust, potentially leading to lost contracts and impacting future business opportunities. The attack also highlighted the vulnerability of the global cold chain, a critical infrastructure sector, to cyberattacks, raising concerns amongst stakeholders.
Financial and Reputational Impact
The exact financial losses Americold suffered remain undisclosed, a common practice for companies affected by ransomware. However, based on similar incidents in the logistics sector, we can reasonably assume the costs involved millions of dollars. This includes the direct costs mentioned previously, plus the longer-term costs associated with rebuilding trust with customers, investors, and regulatory bodies. Reputational damage, potentially leading to decreased market share and difficulty attracting and retaining top talent, represents a significant, albeit less easily quantifiable, loss.
The incident served as a stark reminder that the cost of a successful ransomware attack extends far beyond the immediate financial outlay. For instance, the Maersk NotPetya attack in 2017 cost the company an estimated $300 million, illustrating the potential scale of such incidents.
Cybersecurity Infrastructure and Protocol Changes
Following the attack, Americold undoubtedly implemented significant changes to its cybersecurity infrastructure and protocols. This likely involved upgrading its network security equipment (firewalls, intrusion detection systems), enhancing endpoint protection on employee devices, and implementing multi-factor authentication (MFA) across all systems. They likely also invested in advanced threat detection and response capabilities, including security information and event management (SIEM) systems to better monitor and analyze network activity.
Furthermore, they probably strengthened their data backup and recovery procedures, ensuring regular offsite backups and a robust disaster recovery plan. Employee training programs focused on cybersecurity awareness and phishing prevention were also likely enhanced.
Comparison of Pre- and Post-Attack Cybersecurity Posture
Before the attack, Americold’s cybersecurity posture, based on available information, appears to have been inadequate to withstand a sophisticated ransomware attack. Post-attack, the company’s posture is significantly improved, though the exact extent of the improvements remains confidential. The pre-attack state likely lacked sufficient investment in preventative measures, robust monitoring capabilities, and employee training. The post-attack state, ideally, now features a more proactive and layered security approach, incorporating preventative measures, detection mechanisms, and incident response plans.
The shift represents a transition from a reactive to a more proactive security model, crucial for mitigating future threats.
Hypothetical Improved Cybersecurity Plan for Americold
An improved cybersecurity plan for Americold should focus on a multi-layered defense strategy. This would involve strengthening network security with advanced firewalls and intrusion prevention systems, implementing robust endpoint detection and response (EDR) solutions, and enforcing strict access controls with strong password policies and MFA. Regular security audits and penetration testing are essential to identify and address vulnerabilities.
Comprehensive employee training programs focusing on phishing awareness, social engineering tactics, and safe browsing habits are crucial. A robust data backup and recovery plan with geographically dispersed backups is paramount. Finally, a well-defined incident response plan, including procedures for containment, eradication, recovery, and post-incident analysis, is essential for minimizing the impact of future attacks. The plan should also incorporate regular security awareness training and simulated attack exercises to ensure preparedness.
This layered approach, combining preventative measures with robust detection and response capabilities, would significantly enhance Americold’s overall cybersecurity posture.
Regulatory and Legal Implications
The Americold ransomware attack raises significant regulatory and legal concerns, impacting not only the company itself but also its customers and stakeholders. Understanding the applicable laws and regulations is crucial for assessing the potential consequences and implementing effective mitigation strategies. This section explores the legal landscape surrounding data breaches and ransomware attacks, focusing on Americold’s specific obligations and potential liabilities.
Applicable Regulations and Laws
Numerous laws and regulations govern data breaches and ransomware attacks, varying by jurisdiction. Key regulations often cited include the Health Insurance Portability and Accountability Act (HIPAA) if Protected Health Information (PHI) was compromised, the California Consumer Privacy Act (CCPA) and the California Privacy Rights Act (CPRA) if California residents’ data was affected, and the General Data Protection Regulation (GDPR) if European Union residents’ data was involved.
Further, depending on the nature of the data compromised and the location of the affected individuals, other state and federal laws related to data security and privacy could apply. These laws mandate specific requirements for data security, breach notification, and consumer protection. Failure to comply can lead to significant penalties and legal repercussions.
Americold’s Legal Obligations Regarding Data Breach Notification and Customer Communication
Americold has legal obligations regarding data breach notification, stemming from both federal and state laws. These obligations typically require timely notification to affected individuals and regulatory bodies about the breach, the types of data compromised, and steps being taken to mitigate the harm. The specific timeframe for notification varies by jurisdiction. Moreover, Americold is legally obligated to provide clear and concise communication to its customers, outlining the incident, its potential impact, and the measures taken to protect their data.
Transparency and proactive communication are crucial in mitigating reputational damage and legal liability. Failure to comply with these notification requirements can result in hefty fines and lawsuits.
Potential Legal Consequences for Americold and its Stakeholders
The legal consequences for Americold could be substantial, encompassing significant fines, lawsuits from affected individuals and businesses, and reputational damage. Depending on the extent of the data breach and the nature of the compromised information, Americold could face class-action lawsuits alleging negligence, breach of contract, and violations of privacy laws. Shareholders might also file lawsuits alleging that the company failed to adequately protect its assets and shareholder value.
Insurance coverage may help mitigate some financial losses, but the cost of legal defense and potential settlements could still be substantial. Stakeholders, including customers, suppliers, and investors, could suffer financial losses and reputational harm as a result of the attack.
Summary of Legal and Regulatory Requirements, Americold suffers a ransomware attack
| Regulation/Law | Key Requirements | Applicable Jurisdiction | Potential Penalties |
|---|---|---|---|
| HIPAA | Notification of breach to individuals and HHS; implementation of security measures | US (for PHI) | Significant fines, legal action |
| CCPA/CPRA | Data breach notification to California residents; data security measures | California | Fines, legal action |
| GDPR | Notification of breach to supervisory authority and individuals; data security measures | EU | High fines, legal action |
| State Data Breach Notification Laws | Vary by state; typically require notification to affected individuals and state authorities | Various US States | Vary by state; fines, legal action |
Impact on the Cold Storage Industry
The Americold ransomware attack sent shockwaves through the cold storage industry, highlighting the vulnerability of a sector crucial to global food security. The incident underscored the significant financial and operational risks associated with inadequate cybersecurity defenses, raising concerns about the potential for widespread disruption and the cascading effects on supply chains. This attack wasn’t just about lost data; it impacted the integrity of temperature-sensitive goods, potentially leading to spoilage and substantial financial losses for Americold and its clients.The attack exposed the interconnectedness of the cold chain and its susceptibility to cyber threats.
Many cold storage facilities rely on sophisticated technology for temperature monitoring, inventory management, and logistics. A successful ransomware attack can compromise these systems, leading to operational paralysis, data breaches, and significant financial losses. The potential for food spoilage due to temperature fluctuations adds another layer of complexity and cost, impacting not only the storage company but also the entire supply chain, from producers to consumers.
Vulnerabilities of Cold Storage Companies to Ransomware Attacks
Cold storage facilities often operate with older systems and legacy infrastructure, making them potentially more vulnerable to cyberattacks. Many companies may lack the resources or expertise to implement robust cybersecurity measures, leaving them exposed to sophisticated ransomware attacks. Furthermore, the reliance on interconnected systems, including IoT devices for temperature monitoring and automation, creates numerous potential entry points for malicious actors.
A lack of employee training and awareness regarding cybersecurity best practices further exacerbates the risk. For example, a phishing email targeting an employee could easily compromise the entire network if not properly addressed. The reliance on third-party vendors also presents a vulnerability; a breach in a vendor’s system could indirectly compromise the cold storage facility.
Recommendations for Enhancing Cybersecurity Practices
Implementing a multi-layered security approach is crucial for cold storage companies. This includes robust network security, including firewalls, intrusion detection systems, and regular security audits. Regular software updates and patching are essential to mitigate vulnerabilities exploited by ransomware. Data backups should be stored offline and regularly tested for recoverability. Investing in employee cybersecurity awareness training is paramount.
This training should cover phishing awareness, password security, and safe internet practices. Furthermore, cold storage companies should consider implementing advanced threat detection and response solutions, including threat intelligence platforms and security information and event management (SIEM) systems. Finally, establishing strong relationships with cybersecurity experts and incident response teams is crucial for effective mitigation and recovery.
Creating a Security Awareness Training Program
A comprehensive security awareness training program for cold storage companies should be designed to address the specific risks faced by the industry. The program should include modules on phishing awareness, teaching employees to identify and report suspicious emails. It should also cover password security best practices, promoting the use of strong, unique passwords and multi-factor authentication. Safe internet usage should be emphasized, highlighting the risks of downloading files from untrusted sources and visiting malicious websites.
Furthermore, the training should address the importance of reporting any suspicious activity promptly. Regular refresher training and simulated phishing exercises should be incorporated to maintain employee vigilance. The training should be tailored to different roles within the company, ensuring that all employees receive training relevant to their responsibilities. Finally, the program should be evaluated regularly and updated to address emerging threats.
A successful program will emphasize the importance of cybersecurity not only for the company’s bottom line but also for the safety and security of the food supply chain.
Visual Representation of the Attack’s Impact
Understanding the Americold ransomware attack requires visualizing its progression and impact. The following diagrams offer a clearer picture of the events and their consequences across the company’s operations. These representations are simplified for clarity, but they highlight key stages and affected areas.
Timeline of the Ransomware Attack
A flowchart effectively illustrates the timeline of the attack. The process begins with an initial breach, possibly through a phishing email or a vulnerable system. This is followed by the ransomware’s deployment, encrypting critical data and systems. The next stage involves the discovery of the attack and the subsequent response, which includes isolating affected systems, initiating incident response protocols, and potentially contacting law enforcement and cybersecurity experts.
The attack’s impact is shown by the disruption of operations, including potential delays in shipments, inventory management issues, and communication disruptions. Recovery efforts, including data restoration from backups and system remediation, follow, eventually leading to the resumption of normal operations. The entire process, from initial breach to full recovery, could take weeks or even months depending on the severity of the attack and the effectiveness of the response.
The flowchart would visually represent these stages with boxes and arrows, showing the sequence of events.
Impact on Americold’s Business Operations
A diagram depicting the impact on various aspects of Americold’s operations would be useful. The diagram could be a tree-like structure, with “Americold Business Operations” at the root. Branching from this would be key areas like warehouse management, transportation, customer relations, and financial operations. Each branch could further subdivide to show specific impacted functions. For example, under “Warehouse Management,” we might see disruptions in temperature monitoring, inventory tracking, and order fulfillment.
“Transportation” might show delays in shipments due to disrupted logistics systems and communication failures. “Customer Relations” could highlight difficulties in responding to inquiries and managing client orders. Finally, “Financial Operations” might illustrate delays in invoicing, payment processing, and reporting. The diagram would visually demonstrate how the ransomware attack cascaded through the organization, disrupting various interconnected functions and highlighting the significant operational challenges Americold faced.
For instance, a specific example of disruption could be the inability to track perishable goods in real-time, leading to potential spoilage and significant financial losses. Another example would be the delay in processing payments to suppliers, impacting the company’s relationships and potentially its supply chain.
Final Conclusion: Americold Suffers A Ransomware Attack

The Americold ransomware attack serves as a stark reminder of the ever-evolving threat landscape facing businesses globally. The incident underscores the need for robust cybersecurity measures, proactive threat intelligence, and comprehensive incident response plans. While the immediate crisis may have passed, the long-term implications continue to resonate, emphasizing the critical need for continuous improvement in cybersecurity practices across all sectors, especially those integral to our daily lives like the cold storage industry.
The lessons learned from this attack should be a wake-up call for every organization, urging them to invest in comprehensive security measures to protect themselves from similar threats.
FAQ Corner
What type of ransomware was used in the Americold attack?
The specific type of ransomware used hasn’t been publicly disclosed by Americold or authorities. This information is often kept confidential to prevent further attacks using similar methods.
Did Americold pay the ransom?
Americold has not publicly confirmed whether a ransom was paid. Many companies choose not to disclose this information due to legal and security concerns.
What data was affected by the attack?
The exact nature and extent of the data affected haven’t been fully disclosed. However, it’s likely that operational data, customer information, and potentially financial records were compromised.
How long did it take Americold to recover from the attack?
The full recovery timeline hasn’t been publicly shared. Recovering from a significant ransomware attack can take weeks, months, or even longer depending on the extent of the damage and the complexity of the systems involved.