AppScans API Scanning DAST, IAST Lunch & Learn
Api scanning with dast and iast in appscans next lunch n learn – API scanning with DAST and IAST in AppScan’s next lunch n’ learn? Count me in! Seriously, securing APIs is a HUGE deal these days. We’re talking about the heart of so many applications, and if they’re vulnerable, well, let’s just say it’s not pretty. This session dives deep into how Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST) help us find and fix those weaknesses before they become major headaches (or worse!).
We’ll be exploring AppScan’s powerful features and learning practical strategies to bolster our API security posture. Get ready to level up your app protection game!
We’ll cover the fundamentals of API scanning, exploring the key differences between DAST and IAST approaches. Think of DAST as a black-box test – it examines the application from the outside, mimicking real-world attacks. IAST, on the other hand, works from within the application, giving us a more granular view of vulnerabilities. We’ll see how AppScan cleverly combines both techniques for a comprehensive security analysis.
The session will also include a step-by-step guide on using AppScan, practical examples, and a Q&A session to address your burning questions. Think of it as a cheat sheet for building bulletproof APIs!
Introduction to API Scanning
APIs (Application Programming Interfaces) are the backbone of modern software, facilitating communication between different applications and services. As applications become increasingly interconnected, the security of these APIs becomes paramount. A single vulnerability in an API can expose sensitive data, disrupt services, or even allow attackers complete control of the system. This makes understanding and securing APIs a critical aspect of modern application security.API scanning is the automated process of identifying security vulnerabilities within APIs.
It involves systematically probing an API’s endpoints and functionalities to detect weaknesses that could be exploited by malicious actors. This proactive approach helps organizations identify and remediate risks before they can be leveraged for attacks, contributing significantly to a robust security posture.
Common API Vulnerabilities
Many vulnerabilities can compromise API security. These vulnerabilities often stem from poor design, insecure coding practices, or insufficient testing.
- Broken Object Level Authorization (BOLA): This occurs when an API doesn’t properly verify user permissions before granting access to resources. An attacker might be able to access data or perform actions they shouldn’t be authorized to do, potentially viewing or modifying other users’ information.
- Injection Flaws (SQL Injection, Command Injection): If an API doesn’t properly sanitize user inputs, attackers can inject malicious code into database queries or system commands, potentially gaining unauthorized access or control.
- Broken Authentication: Weak or improperly implemented authentication mechanisms can allow attackers to bypass security controls and gain unauthorized access. This could involve exploiting default credentials, guessing passwords, or using stolen authentication tokens.
- Excessive Data Exposure: APIs might expose more data than is necessary, potentially revealing sensitive information like personally identifiable information (PII) or credentials. This can happen due to improper data filtering or lack of sufficient data masking.
- Lack of Rate Limiting: Without rate limiting, attackers can flood an API with requests, causing denial-of-service (DoS) conditions. This makes the API unavailable to legitimate users.
DAST vs. IAST Approaches to API Security Testing
Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST) represent two distinct approaches to API security testing. Understanding their differences is crucial for selecting the appropriate method or combining them for comprehensive security assessment.DAST tools operate externally, scanning an API from the perspective of an attacker. They analyze the API’s responses to various requests to identify vulnerabilities.
Think of it like a black-box testing approach. DAST excels at finding vulnerabilities related to improper authentication, authorization, and data exposure. However, DAST might miss vulnerabilities that require internal application knowledge.IAST tools, conversely, operate internally, instrumenting the application to monitor its runtime behavior. They provide deeper insights into the application’s code and data flow, enabling the detection of vulnerabilities even during development.
This is a white-box testing approach, offering more comprehensive coverage than DAST alone. IAST is particularly effective at detecting injection flaws and other vulnerabilities that are difficult to discover using external scanning methods. However, IAST requires integrating agents into the application, which may not be feasible in all environments.
DAST in API Security
Dynamic Application Security Testing (DAST) offers a valuable approach to securing APIs by simulating real-world attacks against a running application. Unlike static analysis, which examines code without execution, DAST tools interact directly with the API, sending various requests and observing the responses to identify vulnerabilities. This black-box testing methodology makes it particularly effective in discovering unexpected behaviors and vulnerabilities that might be missed by other methods.DAST tools work by sending a series of automated requests to the API, mimicking the actions of a potential attacker.
These requests might include various HTTP methods (GET, POST, PUT, DELETE), different payloads, and attempts to exploit known vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure authentication. The tool then analyzes the responses, looking for indicators of vulnerabilities, such as error messages revealing database structures or unexpected behavior indicating a successful injection attempt.
DAST Advantages and Disadvantages for API Scanning
DAST offers several advantages for API security. Its black-box nature means it requires no access to the application’s source code, making it suitable for testing third-party APIs or legacy systems. It can uncover vulnerabilities that might be missed by static analysis, such as runtime errors or unexpected interactions between different components. However, DAST also has limitations. It can produce false positives, requiring manual verification of identified vulnerabilities.
It’s also less effective at detecting vulnerabilities that don’t manifest in the application’s responses, such as vulnerabilities in the underlying code that don’t trigger an error message. Comprehensive testing can be time-consuming and resource-intensive, especially for large and complex APIs. Furthermore, DAST struggles with detecting vulnerabilities hidden behind authentication mechanisms, requiring sophisticated techniques to bypass or handle authentication processes effectively.
Popular DAST Tools and Their API Testing Capabilities
Several popular DAST tools offer robust API scanning capabilities. PortSwigger Burp Suite, for example, allows for manual and automated scanning of APIs, providing detailed information about identified vulnerabilities and allowing for manual interaction with the API during testing. OWASP ZAP is another open-source option offering similar functionalities, with a focus on ease of use and community support. These tools often include features like vulnerability scanning, request modification, and reporting, allowing security professionals to thoroughly assess API security posture.
Commercial tools like Acunetix and Contrast Security also offer advanced API scanning features, often incorporating machine learning to improve accuracy and reduce false positives.
DAST Scan Identifying a REST API Vulnerability: A Hypothetical Scenario
Imagine a REST API endpoint responsible for user authentication. A DAST scan using Burp Suite might send a series of requests to this endpoint, including requests with intentionally malformed data. One such request might include a SQL injection attempt in the username parameter, such as: `’ OR ‘1’=’1`. If the API doesn’t properly sanitize user inputs, the database might return an unexpected response, such as revealing the entire database structure or allowing unauthorized access.
Burp Suite would detect this unusual response, flagging the vulnerability as a potential SQL injection flaw. The detailed report would include the specific request that triggered the vulnerability, the response from the server, and recommendations for remediation, such as input sanitization and parameterized queries.
IAST in API Security
Interactive Application Security Testing (IAST) offers a fundamentally different approach to API security compared to DAST. While DAST scans from the outside, IAST operates from within the application, providing a more comprehensive and accurate view of vulnerabilities. This internal perspective allows IAST to identify vulnerabilities that often go undetected by external scans.IAST tools work by instrumenting the application code, either through agents embedded within the application or by using bytecode instrumentation.
This instrumentation allows the IAST tool to monitor the application’s runtime behavior, analyzing the flow of data and identifying potential security flaws as they occur. This real-time analysis provides immediate feedback, allowing developers to address vulnerabilities early in the development lifecycle.
IAST Scanning Mechanisms in APIs
IAST tools achieve API security testing by embedding agents within the application server. These agents monitor API calls, analyze data flows, and detect vulnerabilities in real-time during runtime. The agent observes the application’s interaction with the API, including request parameters, response data, and internal application state. By analyzing this information, the IAST tool can identify security weaknesses such as SQL injection, cross-site scripting (XSS), and insecure deserialization, even if they are only triggered under specific circumstances.
The deep level of visibility into the application’s internal workings allows for a precise understanding of the vulnerability’s impact and context.
Comparison of IAST and DAST for API Security
The key difference between IAST and DAST lies in their testing approach. DAST performs external scans, simulating attacks from an attacker’s perspective. This is effective for detecting publicly exposed vulnerabilities but may miss vulnerabilities that only manifest under specific internal conditions. Conversely, IAST analyzes the application’s internal workings, providing a more comprehensive view of vulnerabilities. This makes IAST particularly useful for detecting vulnerabilities related to data flow and internal logic.
Vulnerability Types Effectively Detected by IAST in APIs
IAST excels at identifying vulnerabilities that are context-dependent or require internal application state to trigger. This includes:
- SQL Injection: IAST can pinpoint vulnerable SQL queries by monitoring the interaction between the application and the database.
- Cross-Site Scripting (XSS): IAST can detect XSS vulnerabilities by analyzing the data flow and identifying points where user-supplied data is improperly sanitized before being rendered on a webpage or within API responses.
- Insecure Deserialization: IAST can identify instances of insecure deserialization by monitoring the deserialization process and checking for vulnerabilities related to the handling of untrusted data.
- Business Logic Vulnerabilities: IAST can detect vulnerabilities in the application’s logic that may not be visible from external scans. For example, it could detect flaws in authorization checks or improper handling of sensitive data within the API.
DAST and IAST Feature Comparison
| Tool Type | Strengths | Weaknesses | Best Use Cases |
|---|---|---|---|
| DAST | Wide coverage, relatively easy to implement, identifies publicly accessible vulnerabilities | Limited visibility into application logic, high false positives, may miss context-dependent vulnerabilities | Initial security assessment, identifying externally facing vulnerabilities, automated vulnerability scanning |
| IAST | High accuracy, identifies context-dependent vulnerabilities, provides detailed information about vulnerabilities | Requires instrumentation, may impact application performance, limited coverage of externally facing vulnerabilities | Identifying vulnerabilities during development, testing specific code paths, confirming vulnerabilities found by DAST |
AppScan and API Scanning
AppScan, a leading application security testing platform from IBM, offers robust capabilities for securing APIs. It combines both Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST) methodologies to provide a comprehensive view of API vulnerabilities, going beyond simple functional testing to uncover deep-seated security flaws. This approach allows for the identification of a wider range of vulnerabilities than either technique could achieve alone, leading to a more secure application.AppScan’s integration of DAST and IAST techniques facilitates a holistic API security analysis.
DAST, the external approach, analyzes the API’s behavior from the outside, mimicking real-world attacks to identify vulnerabilities like SQL injection and cross-site scripting (XSS). Simultaneously, IAST, an internal approach, monitors the application’s runtime behavior to pinpoint vulnerabilities within the application’s code itself. This dual approach allows for a more accurate and comprehensive assessment of the API’s security posture.
AppScan’s API Security Testing Capabilities
AppScan provides several key capabilities for API security testing, including automated vulnerability scanning, comprehensive reporting, and integration with various development workflows. Its ability to handle various API protocols (REST, SOAP, GraphQL, etc.) and authentication mechanisms makes it highly adaptable to diverse API architectures. The tool also offers advanced features like fuzzing, which helps to uncover unexpected vulnerabilities by testing the API’s behavior with unexpected inputs.
Furthermore, AppScan’s reporting features provide detailed information about identified vulnerabilities, including their severity, location, and remediation advice. This detailed information facilitates efficient vulnerability mitigation.
Integrating DAST and IAST in AppScan for API Security
AppScan’s strength lies in its seamless integration of DAST and IAST. DAST scans identify vulnerabilities externally, while IAST identifies vulnerabilities from within the application’s code during runtime. For example, DAST might detect a potential SQL injection vulnerability by sending malformed SQL queries to the API. Simultaneously, IAST could confirm this vulnerability by identifying the point in the application’s code where the vulnerable SQL query is executed.
This combined approach provides a more accurate and complete picture of the API’s security risks. The results are correlated to provide a consolidated view, reducing false positives and ensuring that genuine vulnerabilities are not overlooked.
Step-by-Step Guide to Using AppScan for API Scanning
A step-by-step guide to using AppScan for API scanning is dependent on the specific AppScan version and setup. However, a general Artikel includes:
1. Configuration
Define the target API endpoint(s), authentication details (if required), and any specific parameters or headers. Configure the scan scope to focus on the specific APIs being tested. This is crucial to avoid unnecessary scanning and optimize scan time.
2. Scan Execution
Initiate the scan. AppScan will automatically analyze the API using its DAST and IAST engines. The scan duration will vary depending on the API’s complexity and size. Progress updates will be provided throughout the process.
3. Report Interpretation
Review the generated report, which provides a detailed list of identified vulnerabilities, categorized by severity. Each vulnerability will include information on its location, description, and recommended remediation steps. This detailed information aids in prioritization of remediation efforts. Prioritize vulnerabilities based on severity and potential impact.
4. Remediation
Address identified vulnerabilities by modifying the API’s code or configuration. After remediation, conduct another scan to verify the effectiveness of the changes.
Best Practices for Using AppScan to Effectively Scan APIs
Effective API scanning with AppScan requires a strategic approach. Consider these best practices:* Regular Scanning: Regularly scan APIs to identify vulnerabilities early in the development lifecycle. This proactive approach minimizes the risk of exploitation.* Prioritize Remediation: Focus on addressing high-severity vulnerabilities first. Prioritize based on potential impact and exploitability.* Use Appropriate Scan Settings: Configure AppScan’s scan settings appropriately for the specific API being tested.
This includes specifying authentication methods, request parameters, and other relevant information.* Integrate with CI/CD: Integrate AppScan into the Continuous Integration/Continuous Delivery (CI/CD) pipeline for automated security testing. This ensures that security testing is performed consistently throughout the development process.* Test Different Scenarios: Simulate various attack vectors and user scenarios to identify a wider range of vulnerabilities. Consider edge cases and boundary conditions during testing.
Lunch & Learn Session Structure
This Lunch & Learn session on API scanning with DAST and IAST using AppScan aims to provide a practical understanding of these crucial security testing methods. We’ll cover the fundamentals, explore AppScan’s capabilities, and even get hands-on with a simulated exercise. The session is designed to be engaging and informative, leaving you with actionable insights to improve your API security posture.
Presentation Design
The presentation will follow a logical flow, starting with a brief overview of API security and the importance of scanning. We’ll then delve into the differences between DAST and IAST, highlighting their strengths and weaknesses. A significant portion will be dedicated to demonstrating AppScan’s features and capabilities for API security testing. We’ll use clear visuals, including diagrams and screenshots, to illustrate key concepts and processes.
The final segment will focus on interpreting scan results and taking corrective actions.
Key Takeaways for Attendees
Attendees will leave with a clear understanding of:
- The significance of API security in modern application development.
- The differences between DAST and IAST approaches to API security testing.
- The core functionalities of AppScan for API scanning.
- How to interpret AppScan scan results and prioritize remediation efforts.
- Practical strategies for integrating API security testing into the software development lifecycle (SDLC).
The session will equip participants with the knowledge and skills to effectively utilize AppScan for identifying and mitigating API vulnerabilities.
Interactive Elements
To enhance engagement and knowledge retention, the session will incorporate several interactive elements. A dedicated Q&A session will allow attendees to clarify any doubts or discuss specific challenges they face. Furthermore, a hands-on exercise will provide practical experience using AppScan to scan a sample API. This exercise will allow participants to apply the concepts learned during the presentation and gain confidence in using the tool.
The exercise will be carefully structured with step-by-step instructions and readily available support from the presenter.
Sample Agenda
The following is a proposed agenda for the Lunch & Learn session:
| Time | Activity |
|---|---|
| 12:00 PM – 12:10 PM | Introduction and Welcome; Setting the Stage for API Security |
| 12:10 PM – 12:30 PM | DAST and IAST: A Comparative Overview |
| 12:30 PM – 1:00 PM | AppScan and API Scanning: Features and Capabilities; Demonstration |
| 1:00 PM – 1:30 PM | Hands-on Exercise: Scanning a Sample API with AppScan |
| 1:30 PM – 1:45 PM | Q&A and Discussion |
| 1:45 PM – 2:00 PM | Wrap-up and Next Steps |
Lunch will be served throughout the session.
Vulnerability Remediation Strategies: Api Scanning With Dast And Iast In Appscans Next Lunch N Learn
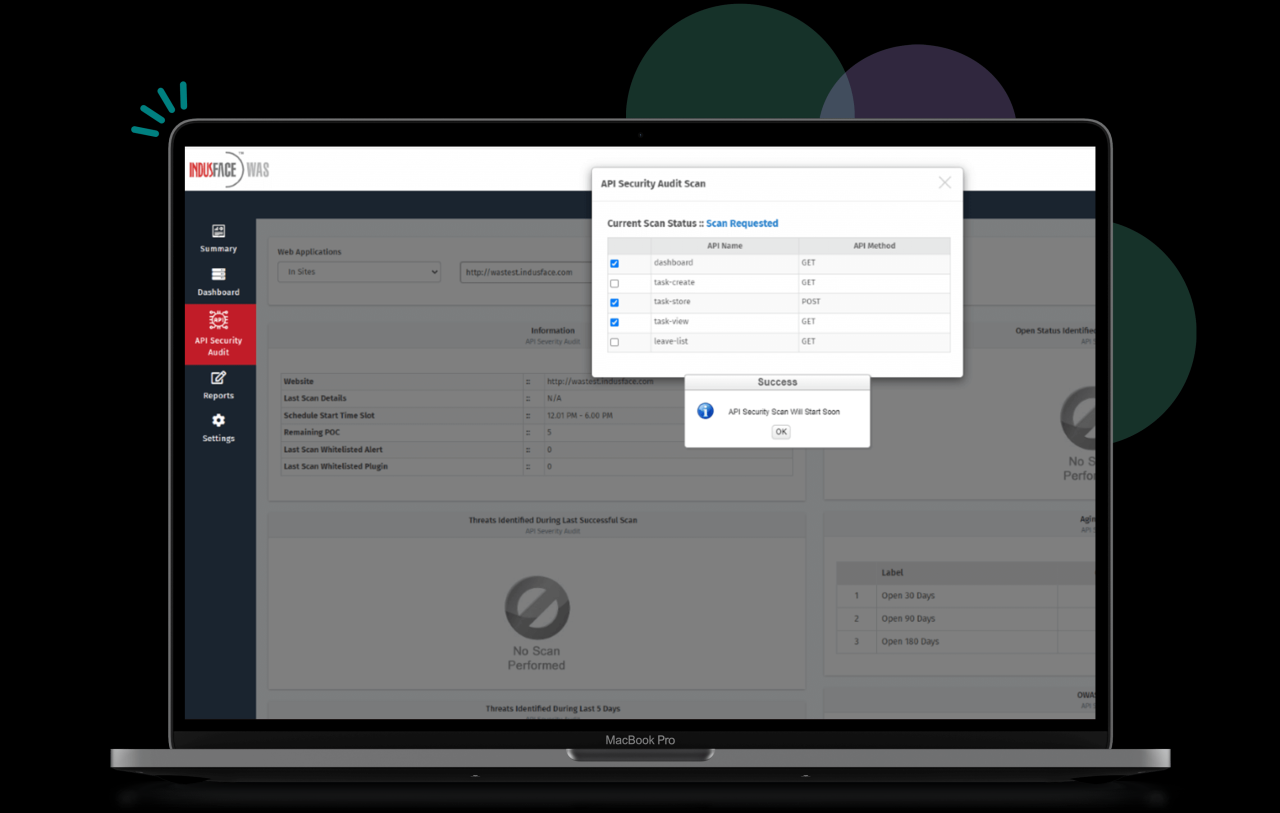
Addressing API vulnerabilities effectively requires a multi-faceted approach encompassing proactive secure design, robust testing, and efficient remediation. Ignoring vulnerabilities can lead to significant security breaches, data loss, and reputational damage. This section details strategies for identifying, prioritizing, and resolving common API security flaws.
Successful remediation hinges on a clear understanding of the vulnerability, its potential impact, and the available mitigation techniques. A well-defined process, integrated into the SDLC, is crucial for timely and effective remediation.
Common API Vulnerabilities and Remediation Strategies
Several common API vulnerabilities pose significant risks. Understanding these vulnerabilities and their associated remediation strategies is paramount for building secure APIs.
| Vulnerability | Description | Remediation Strategy |
|---|---|---|
| SQL Injection | Malicious SQL code is injected into API requests to manipulate database queries. | Use parameterized queries or prepared statements to prevent direct SQL code execution. Validate all user inputs rigorously. Employ an ORM (Object-Relational Mapper) to abstract database interactions. |
| Cross-Site Scripting (XSS) | Malicious scripts are injected into API responses, affecting clients consuming the API. | Encode all user-supplied data before displaying it in API responses. Use a Content Security Policy (CSP) to control the resources that can be loaded on the client-side. Validate and sanitize all input data. |
| Broken Authentication and Session Management | Weaknesses in authentication mechanisms or session management allow unauthorized access. | Implement strong authentication methods (e.g., OAuth 2.0, OpenID Connect). Use secure session management techniques, including short session timeouts and HTTPS. Regularly rotate API keys. |
| Sensitive Data Exposure | APIs expose sensitive data (e.g., credentials, personal information) without proper protection. | Encrypt sensitive data both in transit (using HTTPS) and at rest (using encryption at the database level). Implement access control mechanisms to restrict access to sensitive data based on roles and permissions. Minimize the amount of data exposed in API responses. |
| Lack of Rate Limiting | APIs are vulnerable to denial-of-service (DoS) attacks due to a lack of rate limiting. | Implement rate limiting to restrict the number of requests from a single IP address or user within a specific timeframe. Use techniques like token buckets or leaky buckets to manage request rates effectively. |
Prioritizing Vulnerability Remediation Based on Risk Level
Not all vulnerabilities are created equal. Prioritizing remediation efforts based on risk level ensures that the most critical vulnerabilities are addressed first. Risk is typically assessed by considering the likelihood of exploitation and the potential impact of a successful attack.
A common approach involves using a risk matrix to categorize vulnerabilities based on severity (e.g., critical, high, medium, low). This matrix helps to prioritize remediation efforts, focusing resources on the most critical vulnerabilities first. For example, a critical vulnerability allowing unauthorized access to sensitive customer data would be prioritized over a low-severity vulnerability that might only cause minor inconvenience.
Best Practices for Secure API Design and Development, Api scanning with dast and iast in appscans next lunch n learn
Proactive measures taken during the design and development phases significantly reduce the risk of API vulnerabilities. These practices form a strong foundation for secure APIs.
- Principle of Least Privilege: Grant only the necessary permissions to API users and components.
- Input Validation and Sanitization: Thoroughly validate and sanitize all user inputs to prevent injection attacks.
- Output Encoding: Encode all data before displaying it in API responses to prevent XSS attacks.
- Secure Authentication and Authorization: Implement robust authentication and authorization mechanisms to verify user identities and control access to API resources.
- HTTPS: Always use HTTPS to encrypt communication between the API and clients.
- Regular Security Audits and Penetration Testing: Conduct regular security assessments to identify and address vulnerabilities.
- API Documentation: Provide comprehensive documentation to developers and users, outlining security considerations and best practices.
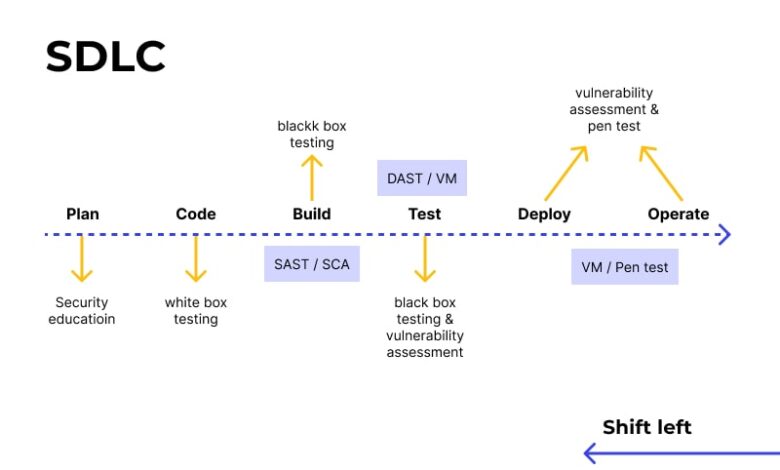
Integrating Security Testing into the SDLC
Integrating security testing into the SDLC ensures that security is considered throughout the entire software development lifecycle. This proactive approach helps to identify and address vulnerabilities early in the development process, reducing the cost and effort required for remediation.
This integration can involve incorporating security testing activities into each phase of the SDLC, such as requirements gathering, design, development, testing, and deployment. Tools like static application security testing (SAST), dynamic application security testing (DAST), and interactive application security testing (IAST) can be integrated into the CI/CD pipeline to automate security testing.
Future Trends in API Security
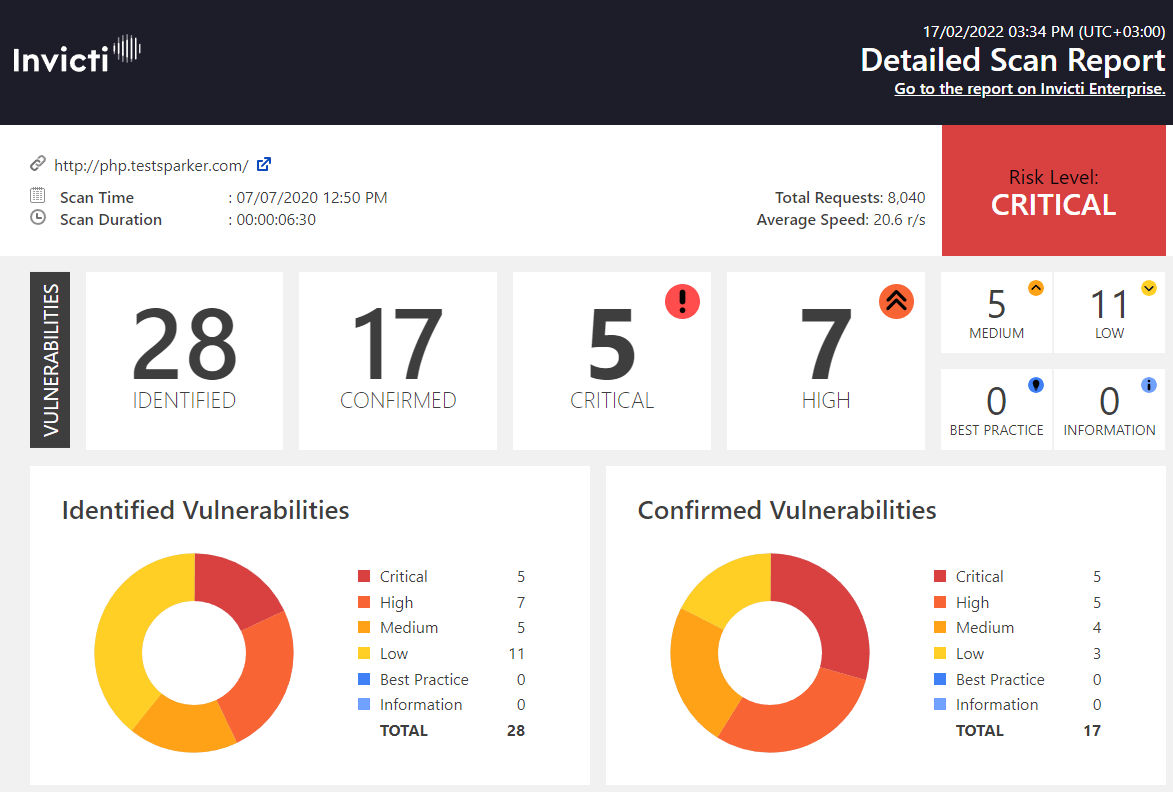
The landscape of API security is constantly evolving, driven by the increasing reliance on APIs for application functionality and data exchange. New threats emerge alongside innovative technologies designed to combat them, creating a dynamic environment requiring constant adaptation and vigilance. Understanding these emerging trends is crucial for organizations seeking to protect their valuable data and maintain the integrity of their systems.The proliferation of APIs and their integration into diverse applications has broadened the attack surface, making them increasingly attractive targets for malicious actors.
Simultaneously, the complexity of modern API architectures, coupled with the rapid pace of development and deployment, presents significant challenges for security professionals. These challenges necessitate the adoption of advanced security measures and a proactive approach to risk management.
The Rise of AI and Machine Learning in API Security Testing
AI and machine learning (ML) are transforming API security testing by automating previously manual and time-consuming tasks. ML algorithms can analyze vast amounts of API traffic data to identify patterns indicative of malicious activity, significantly improving the accuracy and efficiency of threat detection. For example, ML models can be trained to recognize anomalies in API request patterns, such as unusual frequency or data volumes, that might indicate a denial-of-service attack or data exfiltration attempt.
Furthermore, AI-powered tools can automate the process of vulnerability scanning, identifying potential weaknesses in API design and implementation far more quickly than traditional methods. This allows security teams to focus their efforts on addressing the most critical vulnerabilities. The use of AI and ML also allows for predictive analysis, identifying potential threats before they can be exploited.
Predictive API Security and Shift-Left Security
The future of API scanning technologies points towards a more predictive and proactive approach to security. Instead of simply reacting to known vulnerabilities, organizations will increasingly leverage AI-powered tools to predict potential threats based on historical data, code analysis, and emerging attack patterns. This shift-left approach integrates security testing earlier in the software development lifecycle (SDLC), allowing for the identification and remediation of vulnerabilities before they reach production.
For instance, integrating automated API security testing into CI/CD pipelines allows for continuous monitoring and early detection of vulnerabilities. This proactive approach minimizes the risk of costly breaches and ensures that security is built into the application from the start.
The Importance of Collaboration and Information Sharing
Effective API security relies heavily on collaboration and information sharing. The rapid evolution of API threats requires a collective effort to identify, understand, and respond to emerging vulnerabilities. Organizations can benefit significantly from sharing threat intelligence and best practices with industry peers and security researchers. This collaborative approach accelerates the identification of new threats and fosters the development of more effective security solutions.
Initiatives such as vulnerability disclosure programs and open-source security projects play a crucial role in this collaborative ecosystem. Sharing information about discovered vulnerabilities enables the broader community to develop and deploy patches quickly, minimizing the window of opportunity for attackers. Furthermore, open-source tools and frameworks facilitate the development of community-driven security solutions.
Outcome Summary
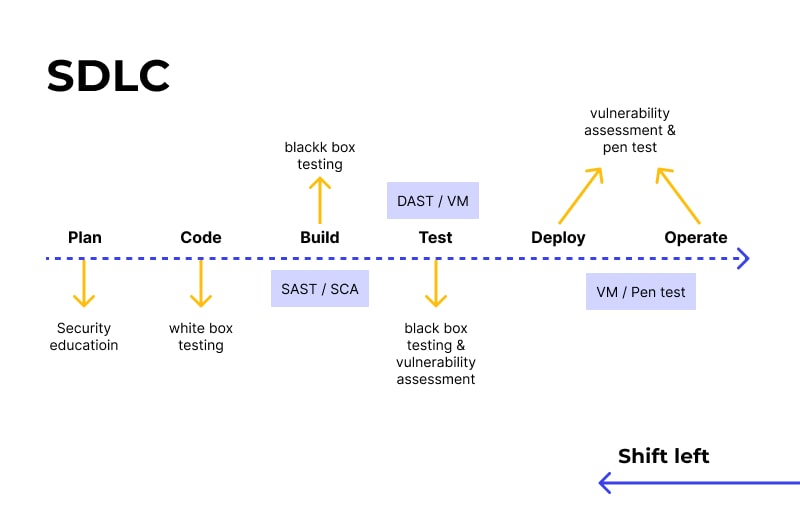
So, after our deep dive into API scanning with DAST and IAST using AppScan, the key takeaway is this: proactive security is no longer a luxury, it’s a necessity. By understanding the strengths and weaknesses of different testing methodologies and leveraging powerful tools like AppScan, we can significantly reduce our attack surface and build more resilient applications. Remember, securing your APIs isn’t just about checking boxes; it’s about safeguarding your users’ data and your organization’s reputation.
Let’s make API security a priority, and let’s do it together!
Quick FAQs
What if my API uses a custom protocol? Can AppScan still handle it?
AppScan’s capabilities depend on the protocol. While it excels with REST and SOAP, custom protocols might require more configuration or potentially custom scripting to ensure thorough scanning.
How often should I scan my APIs?
The frequency depends on your risk tolerance and development cycle. Regular scans, ideally integrated into your CI/CD pipeline, are crucial. Consider scanning after every major code change or at least weekly for production APIs.
Is AppScan suitable for all sizes of APIs?
Yes, AppScan can handle APIs of varying sizes and complexities. However, very large APIs might require careful resource planning to ensure efficient scanning.