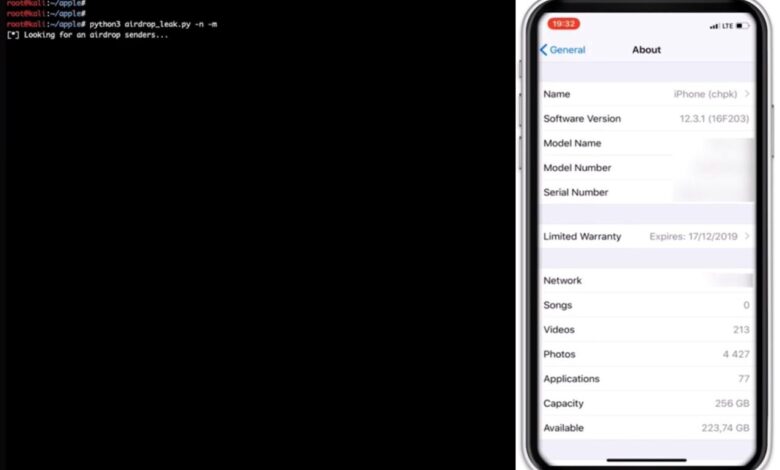
Apple AirDrop Vulnerability Leaking User Details
Apple AirDrop vulnerability to leak personal details of users? It sounds like a sci-fi plot, right? But the reality is, AirDrop, that handy Apple feature for quick file sharing, might have a dark side. This isn’t about some far-fetched theoretical exploit; we’re diving into the potential for real-world data breaches, exploring how vulnerabilities could expose your private information and what you can do about it.
Let’s unpack the security risks and see how to protect ourselves.
AirDrop’s ease of use comes with a trade-off: a potential vulnerability to malicious actors. This post explores the technical details of AirDrop, identifies potential weaknesses, examines the types of data at risk, and most importantly, offers practical steps to mitigate these threats. We’ll look at real-world examples of similar breaches to understand the potential impact and discuss strategies for both Apple and users to enhance AirDrop’s security.
AirDrop Mechanism and Functionality
AirDrop, Apple’s peer-to-peer file-sharing technology, allows for quick and easy transfer of files between Apple devices. It leverages Bluetooth and Wi-Fi to establish a connection and facilitate the transfer process, offering a seamless user experience. However, understanding its inner workings and security implications is crucial for responsible usage.AirDrop uses a combination of Bluetooth and Wi-Fi for discovery and data transfer.
Initially, Bluetooth is used to discover nearby compatible devices. Once a recipient is selected, a secure Wi-Fi connection is established between the two devices for the actual file transfer. This two-pronged approach ensures efficient discovery and relatively high-speed data transfer. The protocols employed are proprietary, but are based on established networking technologies to ensure secure and reliable file transfer.
Security features are built-in to protect against unauthorized access and data interception.
Data Transfer Protocols Used in AirDrop
AirDrop utilizes a proprietary protocol built upon established networking standards, including Wi-Fi Direct and Bluetooth Low Energy (BLE). While the precise details aren’t publicly documented by Apple, the system relies on secure encryption during the data transfer phase. This ensures that the files being transferred remain confidential and protected from eavesdropping. The speed of transfer depends on several factors including the size of the file, the distance between devices, and the network conditions.
AirDrop Privacy Settings and Their Functionality
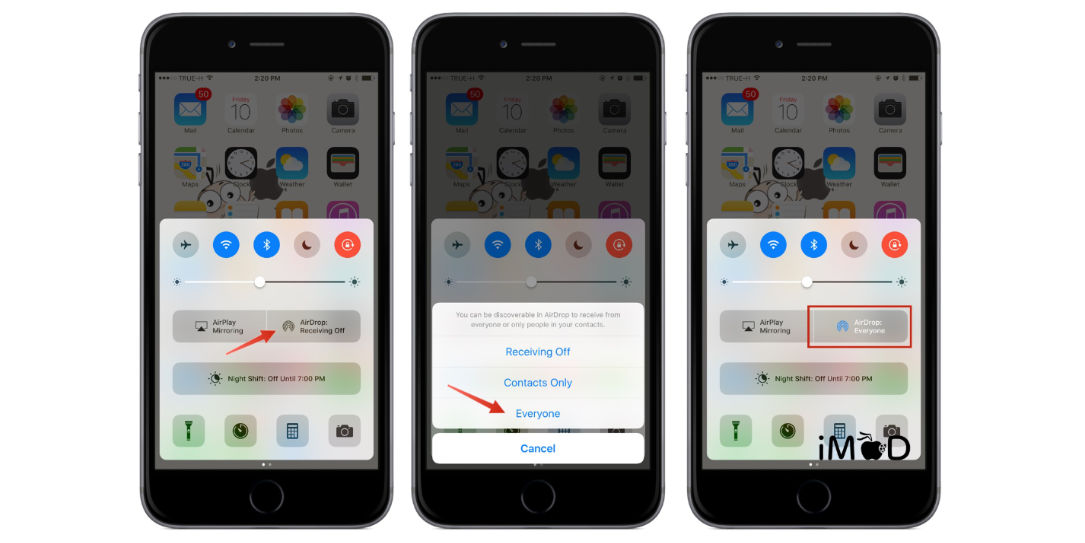
Apple provides several privacy settings to control AirDrop’s accessibility. These settings determine who can initiate a file transfer with your device. The options are designed to balance convenience with security. Users can choose between “Receiving Off,” “Contacts Only,” and “Everyone.” “Receiving Off” completely disables AirDrop, preventing any incoming transfers. “Contacts Only” limits AirDrop to only those listed in your contacts, providing a reasonable level of security.
“Everyone” allows anyone nearby to initiate a transfer, sacrificing privacy for convenience. Choosing the appropriate setting is essential for maintaining control over your data.
AirDrop Sharing Options and Their Security Implications
The following table summarizes the different AirDrop sharing options and their respective security implications:
| Sharing Option | Description | Security Level | Vulnerability |
|---|---|---|---|
| Receiving Off | AirDrop is completely disabled. | High | No vulnerability to unsolicited transfers. |
| Contacts Only | AirDrop is only accessible to contacts in your address book. | Medium | Vulnerable if your contacts list is compromised. |
| Everyone | AirDrop is accessible to any nearby Apple device. | Low | Highly vulnerable to unsolicited transfers and potential malicious attacks. |
Vulnerability Identification and Exploitation
AirDrop, while convenient, isn’t without its security flaws. The inherent design, prioritizing ease of use over stringent security measures, creates opportunities for malicious actors to exploit vulnerabilities and potentially access sensitive user data. This section delves into the specific vulnerabilities and how they can be leveraged for nefarious purposes.The primary vulnerability stems from AirDrop’s “Receive from Anyone” setting.
While convenient for quick file transfers, this setting effectively bypasses any form of authentication or verification, leaving users susceptible to unsolicited file transfers containing malicious payloads. Furthermore, the lack of robust metadata filtering allows attackers to embed personally identifiable information within seemingly innocuous file names or within the files themselves. This lack of scrutiny, coupled with the visual nature of the AirDrop interface, makes it easy for attackers to craft convincing prompts that trick users into accepting malicious files.
Malicious File Transfer Exploitation
A malicious actor could craft a file, seemingly innocuous like a picture or document, but containing malware or spyware. When a user accepts this file via AirDrop, the malware is installed, potentially granting the attacker access to the user’s contacts, photos, location data, and other sensitive information. The attacker might use social engineering techniques, such as naming the file something appealing or relevant to the user’s likely interests (e.g., a photo seemingly from a friend, a document related to their work), to increase the likelihood of the user accepting the file transfer.
The success of this attack hinges on the user’s trust and lack of awareness regarding the security implications of accepting unknown files via AirDrop.
Spoofing and Social Engineering Attacks
Another attack vector involves spoofing the sender’s identity. While AirDrop displays the sender’s name, a determined attacker could potentially manipulate this information to appear as a trusted contact or a legitimate source. This tactic, combined with social engineering techniques like creating a sense of urgency or using deceptive messaging, could trick users into accepting malicious files. For example, an attacker might spoof a name of a known contact and send a file with a seemingly urgent message, prompting the user to accept it without hesitation.
The effectiveness of this attack relies on the attacker’s ability to mimic the behavior of a trusted source and exploit the user’s trust.
Hypothetical Exploitation Scenario
Imagine a scenario where a malicious actor creates a seemingly innocuous image file named “BirthdayParty.jpg” and sends it via AirDrop, spoofing the sender’s name as a close friend of the target user. The image itself contains a cleverly concealed piece of spyware. Upon accepting the file, the spyware is installed, silently logging the user’s keystrokes, accessing their contacts list, and uploading the data to a remote server controlled by the attacker.
The attacker could then use this information for identity theft, blackmail, or other malicious purposes. The success of this attack relies on the user’s trust in the seemingly legitimate sender and the lack of awareness regarding the security risks associated with accepting unsolicited files via AirDrop. The simplicity of the attack underscores the importance of practicing caution and maintaining a healthy level of skepticism when using AirDrop.
Types of Leaked Personal Data

An AirDrop vulnerability, if exploited, can expose a surprisingly wide range of personal data. The severity of the leak depends heavily on the type of data exposed and the individual’s privacy settings. Understanding the potential consequences of each data type is crucial for mitigating risks and implementing appropriate security measures.The following sections categorize the types of data potentially leaked through an AirDrop vulnerability, analyzing their sensitivity and outlining mitigation strategies.
Remember, even seemingly innocuous data points can contribute to a larger picture of an individual’s life and identity.
Image Files
Images stored on a device are a prime target in an AirDrop exploit. These can range from casual snapshots to sensitive personal photos, potentially revealing details about location, relationships, lifestyle, and even financial status (e.g., images of bank statements or credit cards, although this is less common). The unauthorized release of such images can lead to significant emotional distress, reputational damage, and even blackmail.
- Sensitivity: High – Images often depict private moments and personal information.
- Potential Consequences: Emotional distress, reputational damage, blackmail, identity theft.
- Mitigation Strategies: Regularly review and delete unnecessary photos; enable strong passcodes and biometric authentication; avoid storing sensitive information within images; utilize encrypted cloud storage for important photos.
Contact Information
Contact lists, including names, phone numbers, email addresses, and physical addresses, are highly valuable to attackers. This information can be used for targeted phishing attacks, spam campaigns, or even identity theft. The more comprehensive the contact list, the greater the risk.
- Sensitivity: Medium-High – Can be used for targeted attacks and identity theft.
- Potential Consequences: Phishing attacks, spam, identity theft, stalking.
- Mitigation Strategies: Regularly review and minimize contacts; use strong passwords for email and online accounts; enable two-factor authentication; be cautious about sharing contact information via AirDrop.
Documents and Files
Depending on the user’s habits, documents stored on a device could contain highly sensitive personal information. This includes financial documents (bank statements, tax returns), medical records, legal documents, and work-related files. The consequences of leaking such data can be financially devastating and legally problematic.
- Sensitivity: High – Can lead to financial loss, legal issues, and reputational damage.
- Potential Consequences: Identity theft, financial loss, legal repercussions, reputational damage.
- Mitigation Strategies: Avoid storing sensitive documents on devices; use strong passwords and encryption for document storage; utilize password-protected cloud storage for important documents; regularly back up important files to secure locations.
Location Data
Metadata embedded in photos and videos, or location services data itself, can reveal an individual’s whereabouts. This information, when combined with other leaked data, can facilitate stalking or targeted attacks.
- Sensitivity: Medium – Can be used for stalking and targeted attacks.
- Potential Consequences: Stalking, targeted attacks, privacy violations.
- Mitigation Strategies: Disable location services when not needed; review and remove location data from photos and videos; be mindful of sharing geotagged content.
Impact and Consequences of Data Leaks
The AirDrop vulnerability, allowing the unauthorized access and transfer of personal data, carries significant consequences for both affected users and Apple itself. The potential impact extends beyond simple inconvenience, encompassing financial losses, reputational damage, and legal repercussions. Understanding the full scope of these consequences is crucial for mitigating future risks and ensuring user trust.The potential impact on users whose personal data is leaked via AirDrop is multifaceted.
For example, leaked contact information could lead to targeted phishing scams or unwanted marketing calls. Shared photos and videos could be misused for blackmail or harassment. Exposure of location data might facilitate stalking or physical threats. The emotional distress and disruption caused by such invasions of privacy are substantial and cannot be easily quantified. Furthermore, the leaked data could be used for identity theft, resulting in fraudulent activities like opening credit accounts or filing false tax returns.
The financial and emotional costs associated with rectifying such situations can be overwhelming.
Legal and Financial Consequences for Apple and Affected Users
Apple faces potential legal action from users whose data was compromised due to the AirDrop vulnerability. Class-action lawsuits are a distinct possibility, particularly if the company is found negligent in addressing the known vulnerability in a timely manner. Financial penalties could range from fines to compensation payouts to affected individuals. The legal ramifications will also depend on the specific laws and regulations in different jurisdictions, as data privacy laws vary globally.
Users may also pursue individual legal action to recover damages resulting from identity theft, financial losses, or emotional distress stemming from the data breach. The costs associated with legal battles, settlements, and reputational damage could significantly impact Apple’s bottom line.
Severity Compared to Other Data Breaches
While the scale of this AirDrop vulnerability might seem smaller than massive data breaches involving millions of records, its impact on individual users can be just as devastating. Unlike large-scale breaches where the victim may be one of many, the AirDrop vulnerability targets specific individuals, allowing attackers to access highly personal and sensitive information. This targeted nature intensifies the potential for harm and emotional distress.
This vulnerability’s severity is comparable to targeted phishing attacks or malware infections aimed at specific individuals, rather than large-scale breaches like those experienced by Equifax or Yahoo. The personal nature of the data accessed makes this vulnerability particularly damaging.
Reputational Damage to Apple
The AirDrop vulnerability significantly damages Apple’s reputation for prioritizing user privacy and security. The revelation of such a flaw undermines consumer trust, particularly among users who rely on Apple’s products for secure data handling. Negative media coverage and public outcry can erode brand loyalty and potentially impact future sales. The reputational damage could be long-lasting, affecting Apple’s ability to attract and retain customers in a competitive market.
This reputational damage is compounded by the potential for competitors to leverage this vulnerability to highlight the perceived shortcomings of Apple’s security measures. The long-term impact on Apple’s brand image and customer confidence remains a significant concern.
Mitigation and Prevention Strategies
Protecting yourself from AirDrop vulnerabilities requires a multi-faceted approach, encompassing user awareness, careful configuration, and reliance on Apple’s ongoing security updates. Understanding the risks and implementing the right settings is crucial to minimizing your exposure to data leaks. This section Artikels practical steps you can take to enhance your AirDrop security.
AirDrop Configuration for Enhanced Security
To bolster your AirDrop security, adjusting your settings is paramount. This involves carefully choosing who can send you AirDrop requests. By limiting this access, you significantly reduce the chances of unwanted data transfers, including those potentially containing malicious content or exploiting vulnerabilities.
- Access AirDrop Settings: Open Control Center on your iPhone or iPad (swipe down from the top-right corner on iPhones with Face ID, or swipe up from the bottom on iPhones with a Home button and iPads). Long-press the network controls, then tap “AirDrop”.
- Select Receiving Options: Choose one of the three options:
- Receiving Off: Completely disables AirDrop, preventing any files from being sent to your device. This offers the strongest security but limits the functionality of AirDrop.
- Contacts Only: Allows AirDrop transfers only from individuals listed in your contacts. This is a good balance between security and convenience.
- Everyone: Allows AirDrop transfers from any nearby device. This setting is the most convenient but poses the highest security risk.
- Regularly Review Settings: It’s good practice to periodically check your AirDrop settings to ensure they align with your current security needs and preferences. Changes in your social circles or concerns about potential threats may warrant adjusting your settings.
Best Practices for Minimizing AirDrop Data Leak Risk
Beyond configuring AirDrop settings, adopting proactive behaviors can further reduce the risk of data leaks. These practices contribute to a more secure mobile environment, reducing vulnerabilities and safeguarding personal information.
- Be Mindful of Your Surroundings: In crowded places, the risk of unwanted AirDrop requests increases. Consider turning off AirDrop when in such environments.
- Scrutinize Incoming Requests: Before accepting an AirDrop request, carefully examine the sender’s name and the file name. Suspicious names or file types should be avoided. Never accept files from unknown senders.
- Keep Software Updated: Apple regularly releases software updates that address security vulnerabilities, including those related to AirDrop. Ensure your device’s operating system is always up-to-date.
- Strong Passcode/Biometrics: Even with careful AirDrop settings, a strong passcode or reliable biometric authentication adds an extra layer of protection to your device, preventing unauthorized access to your data.
Apple’s Role in Patching and Addressing Vulnerabilities
Apple plays a critical role in mitigating AirDrop vulnerabilities. Their responsibility extends to promptly identifying, patching, and disseminating updates to address security flaws. They typically release software updates containing security patches through their established distribution channels. Users should proactively install these updates as soon as they become available. This proactive approach is essential in preventing exploitation of known vulnerabilities.
Technological Solutions to Enhance AirDrop Security
While Apple continues to improve AirDrop’s security through software updates, additional technological solutions could further enhance its robustness. These might include implementing more sophisticated authentication methods, such as end-to-end encryption for all AirDrop transfers, or incorporating advanced techniques to verify the authenticity of the sender. This could involve integrating stronger identity verification systems to prevent malicious actors from impersonating legitimate users.
Further research and development in this area are crucial to continually strengthening the security of AirDrop and similar technologies.
Case Studies and Examples
While a widespread, exploitable AirDrop vulnerability hasn’t yet been publicly documented, understanding similar incidents involving data leaks through proximity-based sharing technologies helps illustrate the potential impact. Analyzing these cases allows us to better prepare for and mitigate risks associated with potential future vulnerabilities in AirDrop or similar systems. The following examples highlight the consequences of such breaches and the lessons learned.
Bluetooth Vulnerability Leading to Data Leaks, Apple airdrop vulnerability to leak personal details of users
In 2018, researchers discovered a vulnerability in Bluetooth technology that allowed attackers to remotely access and exfiltrate data from nearby devices. This vulnerability exploited a weakness in the Bluetooth pairing process, allowing malicious actors to connect to and extract information from unsuspecting users without their knowledge or consent. The impact of this vulnerability was significant, potentially exposing sensitive personal data like contact lists, calendar entries, and even location data.
The incident underscored the importance of regularly updating Bluetooth firmware and being cautious about accepting unknown Bluetooth connections.
NFC-Based Payment System Compromise
Several instances of compromised Near Field Communication (NFC) payment systems have highlighted the risks associated with proximity-based data transfer. In one particular case, attackers were able to intercept payment information by using specially crafted NFC readers that mimicked legitimate payment terminals. This allowed them to steal credit card details and other financial information from unsuspecting users. The consequences were substantial, resulting in financial losses for both individuals and businesses.
This case study emphasizes the need for robust security measures in NFC-based systems and the importance of user education about potential scams.
Comparison with Potential AirDrop Vulnerability
The Bluetooth and NFC examples demonstrate how proximity-based sharing technologies can be exploited to leak sensitive personal data. A similar vulnerability in AirDrop could have equally severe consequences. The potential for an attacker to gain unauthorized access to photos, videos, contact details, and other files stored on an iPhone or Mac presents a significant risk to user privacy and security.
The ease of initiating AirDrop connections and the often-unaware acceptance of incoming requests exacerbate this vulnerability. The lessons learned from past incidents – the need for robust security protocols, regular software updates, and user awareness – are directly applicable to the potential threat posed by an AirDrop vulnerability.
Summary of Key Findings
| Technology | Vulnerability Type | Data Leaked | Impact |
|---|---|---|---|
| Bluetooth | Remote data access via pairing vulnerability | Contact lists, calendar entries, location data | Privacy breach, potential identity theft |
| NFC Payment System | Man-in-the-middle attack using spoofed reader | Credit card details, financial information | Financial losses, fraud |
| Potential AirDrop Vulnerability | Unauthorized file transfer | Photos, videos, contacts, documents | Privacy breach, potential identity theft, reputational damage |
Future Implications and Recommendations
The AirDrop vulnerability, while seemingly patched, highlights a crucial need for ongoing security improvements and a renewed focus on user education regarding data privacy. The long-term implications extend beyond immediate data breaches, impacting user trust in Apple’s ecosystem and potentially influencing the design of future file-sharing technologies. Addressing this requires a multi-pronged approach involving both Apple and individual users.
Potential Future Security Improvements for AirDrop
Apple could implement several enhancements to bolster AirDrop’s security. These include incorporating stronger authentication methods beyond proximity, such as two-factor authentication or biometric verification before accepting file transfers. Further, implementing granular control over what types of files can be shared and received, allowing users to selectively restrict sensitive data transfer, would significantly reduce the risk of unwanted data exposure.
The recent Apple AirDrop vulnerability, allowing the easy sharing of personal data, really highlights the need for robust security in all our tech. It makes you think about secure app development, and how platforms like Domino are pushing the boundaries with their approach to domino app dev the low code and pro code future , offering potentially more secure and controlled development processes.
Ultimately, though, even the best development practices can’t fully protect against vulnerabilities if users aren’t careful about their AirDrop settings.
Finally, improved user interface design could make security settings more intuitive and accessible, reducing reliance on users having advanced technical knowledge. For example, a visual representation of the data being shared, alongside clear warnings about potential risks, would empower users to make more informed decisions.
Long-Term Implications for User Trust and Data Privacy
The vulnerability eroded user trust in Apple’s commitment to data security. This is particularly concerning given the increasing reliance on Apple devices for personal and professional use. The long-term impact could manifest in reduced user adoption of AirDrop, a shift towards alternative file-sharing methods with perceived stronger security, or even a broader decline in trust in Apple’s overall ecosystem.
This loss of trust could be difficult to regain, potentially affecting Apple’s market share and brand reputation. The incident serves as a reminder of the critical need for transparency and proactive security measures from technology companies.
Areas for Further Research into AirDrop Security
Further research should explore the potential for more sophisticated attacks leveraging the underlying Bluetooth technology used by AirDrop. This includes investigating the feasibility of exploiting vulnerabilities in Bluetooth itself to circumvent any new security measures implemented by Apple. Additionally, research into user behavior and awareness regarding AirDrop’s security features is crucial to understand how best to design user-friendly yet secure interfaces.
Analyzing the effectiveness of different security mechanisms in real-world scenarios, through penetration testing and user studies, will be essential to inform future design choices.
Recommendations for Apple and Users
Apple should prioritize proactive security audits and penetration testing of AirDrop and its underlying technologies. They should also invest in improving user education through clear and concise messaging about security best practices and the potential risks associated with file sharing. For users, being vigilant about accepting incoming AirDrop requests is paramount. Actively reviewing the AirDrop settings and restricting access when not actively using the feature is a crucial step.
Furthermore, users should educate themselves about the types of data they share and understand the potential consequences of inadvertently transferring sensitive information. Regular software updates and enabling automatic updates are also crucial for patching any newly discovered vulnerabilities.
Final Conclusion
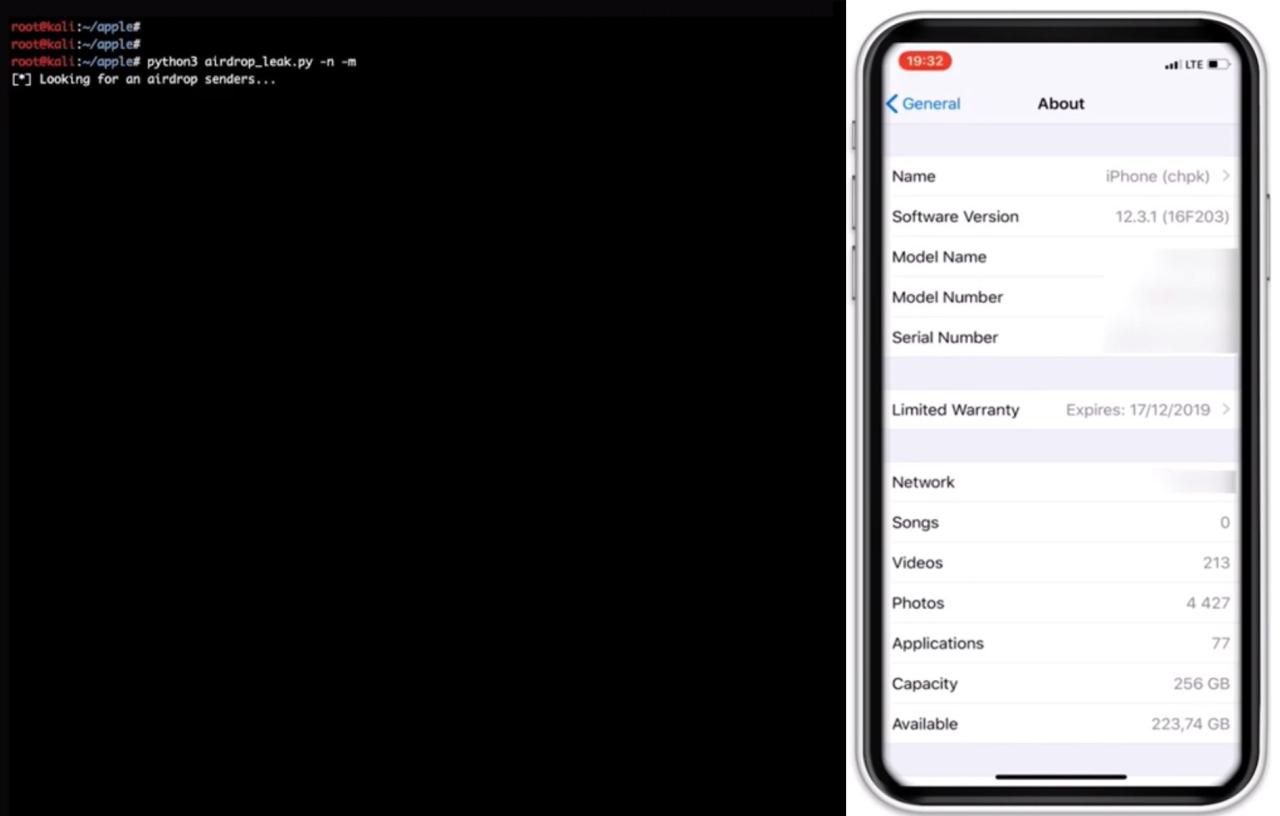
So, is AirDrop safe? The answer, like most things in tech, is nuanced. While AirDrop offers a convenient way to share files, it’s not without its risks. By understanding the potential vulnerabilities and following the security best practices Artikeld here, you can significantly reduce your chances of becoming a victim of a data leak. Staying informed and proactive is key to protecting your personal information in our increasingly interconnected world.
Remember, your digital security is your responsibility, and taking these precautions is a small price to pay for peace of mind.
Top FAQs: Apple Airdrop Vulnerability To Leak Personal Details Of Users
What types of personal data are most at risk through an AirDrop vulnerability?
Photos, videos, contact details, location data, and even sensitive documents are all potentially exposed.
Can I completely disable AirDrop to eliminate the risk?
Yes, you can completely disable AirDrop, but this removes its convenient functionality. A better approach is to carefully manage its settings.
How often does Apple release security updates addressing AirDrop vulnerabilities?
Apple regularly releases iOS updates that address security vulnerabilities, including those potentially affecting AirDrop. Keeping your software updated is crucial.
What should I do if I suspect my data has been compromised via AirDrop?
Immediately change your Apple ID password, review your privacy settings, and monitor your accounts for suspicious activity. Consider reporting the incident to Apple.





