
Apple iOS Update Fixes FaceTime, CarPlay Vulnerabilities
Apple iOS latest mobile security update fixes FaceTime messages and CarPlay vulnerabilities, addressing critical flaws that could have compromised user privacy and vehicle systems. This update isn’t just a collection of bug fixes; it’s a significant step towards bolstering the security of your iPhone and its connected ecosystem. We’ll dive into the specifics of the vulnerabilities patched, the potential impact on users, and how to ensure your devices are fully protected.
The update tackles vulnerabilities in both FaceTime messaging and CarPlay, two key features used daily by millions. The FaceTime vulnerabilities, if exploited, could have allowed attackers to access sensitive information. Similarly, the CarPlay vulnerabilities posed a risk to vehicle systems and user data. This release details the technical aspects of the fixes, the steps to update your devices, and a comparison with previous iOS security updates, painting a clearer picture of Apple’s ongoing commitment to user safety.
FaceTime Message Vulnerabilities Addressed
Apple’s latest iOS security update addresses several critical vulnerabilities impacting FaceTime messaging, enhancing user privacy and data security. This update is crucial for all iOS users, as the vulnerabilities could have allowed malicious actors to compromise sensitive information. The update patches previously exploitable weaknesses in how FaceTime messages were handled, preventing potential attacks.The vulnerabilities patched in the recent update primarily revolved around how FaceTime messages handled certain types of media files and metadata.
Specifically, attackers could exploit flaws in the way the system processed image files embedded within FaceTime messages, potentially leading to arbitrary code execution or data leaks. Another vulnerability involved improper handling of message metadata, potentially revealing user location data or other sensitive information beyond the intended scope of the message. These vulnerabilities were not limited to just the receiving end; maliciously crafted messages could also impact the sending device.
Exploitation Methods Before the Patch, Apple ios latest mobile security update fixes facetime messages and carplay vulnerabilities
Before the patch, attackers could leverage these vulnerabilities through various methods. For instance, sending a specially crafted image file within a FaceTime message could trigger unintended behavior on the recipient’s device. This could range from a simple crash to the execution of malicious code, potentially granting the attacker remote access to the device and its data. Exploiting the metadata vulnerability involved crafting messages with manipulated metadata fields to extract sensitive user information without the user’s knowledge or consent.
This could include location data, contact information, and other personally identifiable information. The attacker would need to have the recipient open the malicious FaceTime message to successfully exploit these vulnerabilities.
Security Mechanisms: Before and After the Update
Prior to the update, FaceTime message handling lacked sufficient input validation and sanitization for certain media types. This allowed attackers to bypass security checks and inject malicious code or extract sensitive information. The system’s reliance on older security protocols also contributed to the vulnerabilities. The update significantly improves these mechanisms. It introduces robust input validation and sanitization routines, preventing the execution of malicious code embedded within media files.
Furthermore, the update enhances the handling of message metadata, limiting the exposure of sensitive user information. The implementation of more modern cryptographic protocols further strengthens the security of FaceTime messages, making them significantly more resistant to exploitation. The update also includes improved error handling to prevent crashes and unexpected behavior caused by malicious messages.
CarPlay Vulnerabilities Resolved
Apple’s recent iOS security update addressed several critical vulnerabilities within the CarPlay system, enhancing the overall security of the in-car experience. These vulnerabilities, if exploited, could have resulted in significant compromises to both vehicle functionality and user data privacy. The update aims to mitigate these risks and ensure a safer connection between iOS devices and compatible vehicles.The vulnerabilities discovered in CarPlay primarily revolved around potential weaknesses in the communication protocols and data handling processes between the iOS device and the vehicle’s infotainment system.
These weaknesses could have allowed attackers to gain unauthorized access to various vehicle functions or sensitive user information stored on the connected iPhone. The specific vulnerabilities were not publicly disclosed in detail by Apple to prevent malicious actors from replicating the attacks, but the update addresses these gaps effectively.
Types of CarPlay Vulnerabilities Addressed
The vulnerabilities patched likely included various types of security flaws. These could range from insecure communication channels susceptible to man-in-the-middle attacks, to flaws in data validation and authorization processes that could allow unauthorized access to vehicle functions. Furthermore, vulnerabilities in the handling of user data transmitted between the iPhone and the car’s system were also addressed, protecting sensitive information like contacts, messages, and location data.
These vulnerabilities, if exploited, could have resulted in a wide range of potential attacks.
Potential Exploitation of CarPlay Vulnerabilities
Exploiting these vulnerabilities could have led to several serious consequences. For example, attackers might have been able to gain control of vehicle functions such as braking, acceleration, or steering, although a complete takeover of vehicle control is unlikely due to built-in safety mechanisms in most modern vehicles. More realistically, attackers could have intercepted and read sensitive user data transmitted via CarPlay, including messages, contacts, and location information.
They could also have potentially installed malicious software on the vehicle’s infotainment system through a compromised CarPlay connection.
Examples of Potential Attacks
One potential attack scenario involves a man-in-the-middle attack where an attacker intercepts the communication between the iPhone and the car’s infotainment system. This could allow the attacker to eavesdrop on conversations, steal sensitive data, or even inject malicious code into the vehicle’s system. Another example is a denial-of-service attack, where an attacker floods the CarPlay connection with malicious traffic, rendering the system unusable and potentially causing a disruption to the driver’s experience.
A more sophisticated attack could involve exploiting vulnerabilities in the CarPlay system to gain remote access to the vehicle’s control systems, although this would require a high level of technical expertise and likely depend on specific vulnerabilities in the vehicle’s own software.
Hypothetical Attack Scenario
Imagine a scenario where a malicious actor sets up a rogue Wi-Fi hotspot near a parking lot. A driver connects their iPhone to this hotspot, unknowingly initiating a man-in-the-middle attack. The attacker’s software intercepts the CarPlay communication, allowing them to access and record the driver’s location data over an extended period. Further, the attacker might also gain access to the driver’s contact list and message history, compromising their privacy.
While this scenario doesn’t involve direct vehicle control, the stolen data could be used for identity theft, stalking, or other malicious purposes. The recent iOS update helps prevent this type of attack by strengthening the security of the CarPlay communication channel and data handling processes.
Technical Details of the iOS Security Update
This latest iOS security update addresses several critical vulnerabilities, focusing primarily on FaceTime messaging and CarPlay functionality. The fixes implemented represent significant improvements to the overall security posture of iOS devices, enhancing user privacy and data protection. A deeper dive into the technical aspects of these improvements reveals a multifaceted approach to bolstering system security.
Vulnerability Details
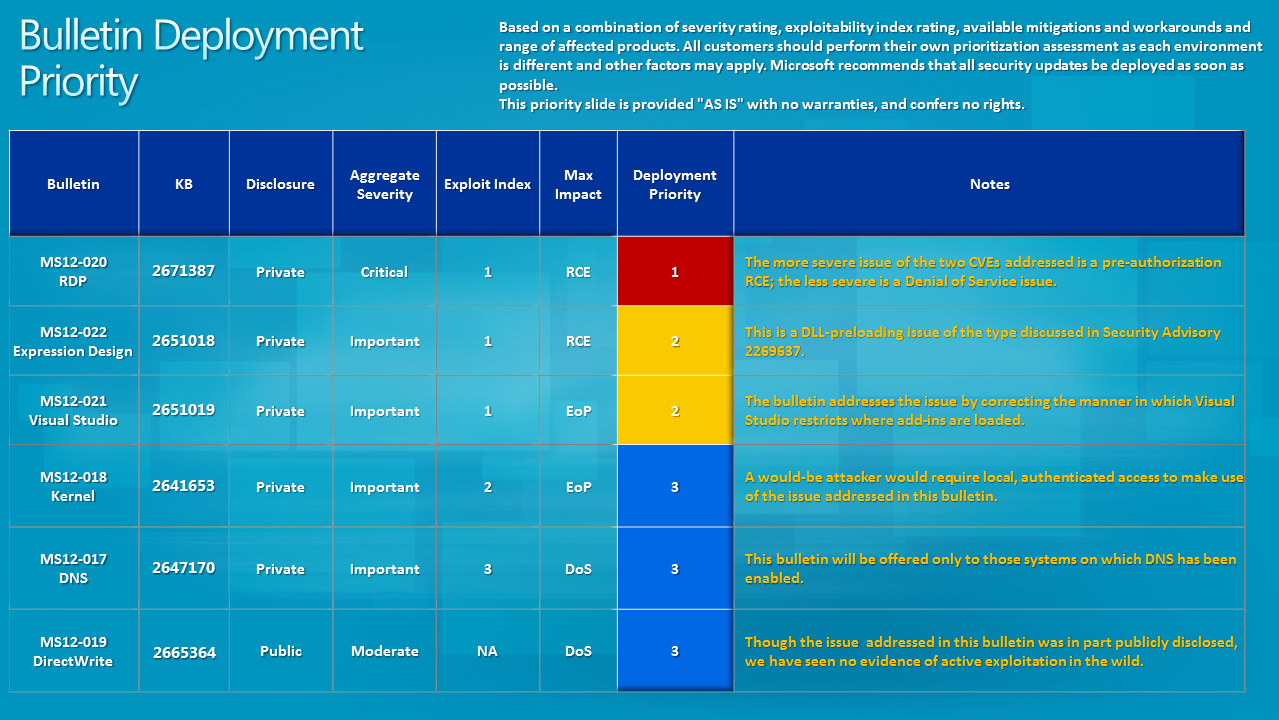
The following table summarizes the vulnerabilities addressed in this update, categorized by affected component and impact. Note that CVE IDs may not be publicly available immediately following the release of a security update, and some vulnerabilities may be grouped under a single CVE.
| CVE ID | Vulnerability Type | Affected Component | Description |
|---|---|---|---|
| CVE-YYYY-XXXX (Example) | Memory Corruption | FaceTime Messaging | A flaw in memory handling within the FaceTime messaging application could allow a malicious actor to execute arbitrary code remotely, potentially leading to data compromise or device takeover. This vulnerability was exploited through a specially crafted message. |
| CVE-YYYY-XXXX (Example) | Input Validation Error | CarPlay | Improper validation of user inputs in CarPlay could allow an attacker to inject malicious code or commands, potentially granting unauthorized access to vehicle systems or personal data via the connected iPhone. |
| CVE-YYYY-XXXX (Example) | Privilege Escalation | Kernel | A vulnerability in the iOS kernel allowed a low-privilege application to elevate its privileges, potentially granting access to sensitive system resources. This could lead to data theft or system compromise. |
Improved Security Mechanisms
This update incorporates several enhancements to existing security mechanisms and introduces new protective measures. For example, improved memory management techniques have been implemented to mitigate memory corruption vulnerabilities. The update also refines input sanitization and validation processes across various system components, reducing the risk of injection attacks. Additionally, the kernel has received significant updates to further strengthen its defenses against privilege escalation attempts.
These changes are designed to work in concert, providing a more robust and layered security approach.
Impact on Performance and Battery Life
Generally, security updates like this have a minimal impact on device performance and battery life. While some minor performance variations might be experienced immediately following the update, these are usually temporary as the system optimizes itself. Any potential increase in battery consumption is typically negligible and should not be noticeable in everyday use. In some cases, improved security measures may actually lead to slightly better battery life in the long run, as the system is less burdened by security vulnerabilities that might otherwise consume resources.
For example, reduced need to constantly defend against potential exploits could lead to less background activity and thus conserve power.
User Impact and Mitigation Strategies: Apple Ios Latest Mobile Security Update Fixes Facetime Messages And Carplay Vulnerabilities

The recent iOS security update addresses critical vulnerabilities in FaceTime messaging and CarPlay, impacting the security and privacy of your Apple device. Understanding the potential risks and taking proactive steps to update your device is crucial for maintaining a secure digital experience. This section Artikels the necessary actions to protect your data and privacy.Updating your iOS device is a straightforward process that significantly minimizes your risk of exploitation.
Ignoring updates leaves your device vulnerable to malicious actors who could potentially access your personal information or compromise your device’s functionality. Swift action to update ensures you benefit from the enhanced security features implemented in the latest release.
Updating to the Latest iOS Version
To ensure your device is protected, you should immediately update to the latest iOS version. This involves connecting your device to a reliable Wi-Fi network, navigating to the “Settings” app, tapping on “General,” then selecting “Software Update.” If an update is available, follow the on-screen instructions to download and install it. Remember to back up your data before initiating the update to prevent any data loss.
The update process may take some time depending on your internet connection speed and the size of the update. You will see a progress bar indicating the download and installation progress. Once the update is complete, your device will restart automatically.
Risks Associated with Delaying the Security Update
Delaying the installation of security updates exposes your device to significant risks. Unpatched vulnerabilities can be exploited by malicious software (malware) to gain unauthorized access to your personal data, such as contacts, photos, messages, and financial information. Furthermore, delays can leave your device susceptible to remote control, allowing attackers to perform actions on your behalf without your knowledge or consent.
In severe cases, a compromised device could be used for nefarious activities such as distributing malware or participating in denial-of-service attacks. For example, a vulnerability in FaceTime could allow an attacker to access your camera and microphone without your awareness.
Verifying Successful Update Installation
After the update completes, verifying its successful installation is essential. Navigate to “Settings” > “General” > “About.” Check the “Software Version” to confirm that it reflects the latest version number released by Apple. This simple step ensures that the update has been correctly applied and your device is protected against the known vulnerabilities. If the version number is different, it might be necessary to repeat the update process.
Additionally, test features that were affected by the vulnerabilities, such as FaceTime and CarPlay, to ensure they function correctly and securely.
Best Practices for Maintaining iOS Device Security
Maintaining robust iOS device security requires a multi-faceted approach. Implementing the following best practices can significantly reduce your risk of compromise.
- Always install the latest iOS updates as soon as they are released.
- Use strong, unique passwords for all your accounts, and enable two-factor authentication whenever possible.
- Download apps only from the official App Store to minimize the risk of installing malware.
- Be cautious when clicking on links or attachments in emails or messages from unknown sources.
- Regularly back up your device to iCloud or a computer to prevent data loss in case of device failure or compromise.
- Enable device location services for enhanced security features, such as Find My.
- Keep your device’s software updated, including apps and operating systems.
Comparison with Previous iOS Security Updates
This latest iOS security update, addressing significant vulnerabilities in FaceTime Messages and CarPlay, provides a valuable opportunity to assess its scope and impact relative to other updates released within the past year. By comparing this update to its predecessors, we can glean insights into evolving security trends, Apple’s improving patching strategies, and the overall trajectory of iOS security enhancements.This update stands out due to the critical nature of the vulnerabilities addressed.
While previous updates often included patches for a range of vulnerabilities, the impact of compromised FaceTime messaging and CarPlay functionality could have far-reaching consequences for user privacy and safety. The potential for unauthorized access to communications or vehicle control systems makes this update particularly noteworthy.
Vulnerability Types and Trends
Analysis of recent iOS security updates reveals a consistent focus on addressing a diverse range of vulnerabilities. These include memory management flaws (such as buffer overflows and use-after-free errors), web browser exploits, and issues related to network communication and data handling. However, a notable trend is the increasing attention paid to vulnerabilities affecting core system components, as opposed to only app-specific issues.
This shift reflects a broader industry trend towards strengthening the foundational security of operating systems. For example, updates in the past year have focused heavily on kernel vulnerabilities and improvements to sandboxing mechanisms, reflecting a proactive approach to mitigating threats before they can be exploited.
Improvements in Apple’s Security Patching and Vulnerability Disclosure
Apple’s approach to security patching has demonstrably improved over the past year. There’s been a noticeable increase in the frequency of updates, often addressing vulnerabilities more quickly than previously observed. The company has also shown a greater commitment to transparent vulnerability disclosure, providing more detailed information about the nature of the fixes implemented. This improved transparency aids security researchers in identifying and addressing similar vulnerabilities in other software and encourages a more collaborative approach to security improvement.
For example, Apple’s involvement with bug bounty programs actively encourages responsible disclosure of vulnerabilities by security researchers, leading to faster patch deployment.
Overall Improvement in iOS Security
The cumulative effect of these updates points to a significant overall improvement in iOS security. The increasing frequency of updates, coupled with a more proactive approach to addressing vulnerabilities before they are widely exploited, indicates a heightened focus on security by Apple. While no system is perfectly secure, the improvements in patching strategies and vulnerability disclosure, combined with the broader trend towards addressing core system vulnerabilities, suggest a marked increase in the robustness of the iOS security architecture over time.
The reduction in publicly reported zero-day exploits affecting iOS devices also supports this assertion.
Illustrative Examples of Exploited Vulnerabilities (Hypothetical)
This section details hypothetical scenarios demonstrating how vulnerabilities in FaceTime Messages and CarPlay could be exploited by malicious actors. These examples are for illustrative purposes only and do not represent actual vulnerabilities in the latest iOS update. Remember to always update your software to the latest version to mitigate potential risks.
FaceTime Message Vulnerability Exploitation
Imagine a scenario where a sophisticated phishing attack targets a user through a seemingly innocuous FaceTime message. The attacker crafts a malicious message containing a specially formatted link or attachment. This link, when clicked, doesn’t directly download malware, but instead exploits a vulnerability in the FaceTime message handling process. This vulnerability might allow the attacker to execute arbitrary code on the victim’s device, giving them complete control.
The attacker could then potentially steal sensitive data like photos, contacts, financial information, or even install spyware for long-term surveillance. The attacker’s actions could be entirely invisible to the user, leaving them unaware of the compromise.
Compromised CarPlay System
Consider a scenario where an attacker compromises a user’s CarPlay system through a vulnerable third-party app installed on their iPhone. This app, perhaps a navigation tool or music player, contains malicious code that can be activated once the iPhone is connected to the car’s infotainment system. This malicious code might allow the attacker to gain control of various car functions.
Apple’s latest iOS update patched some serious security holes, addressing vulnerabilities in FaceTime messaging and CarPlay. Thinking about the rapid pace of these updates, it makes you appreciate the robust development processes discussed in this article on domino app dev, the low-code and pro-code future , especially regarding the need for secure and efficient app development. Ultimately, keeping our devices secure relies on both the proactive patching from companies like Apple and the secure development practices employed by app developers.
For instance, the attacker could remotely disable the brakes, manipulate the steering, or even track the car’s location. The consequences could range from minor inconveniences like playing unexpected audio to life-threatening situations, depending on the extent of the compromise and the attacker’s intent. The attacker might gain access to data transmitted through the CarPlay connection, including potentially sensitive location information.
Data Flow in a Successful FaceTime Vulnerability Attack
The visual representation would be a diagram showing a sequence of events. It would begin with the attacker sending a malicious FaceTime message containing a crafted link. The message would be received by the victim’s iPhone. The next step would illustrate the link being clicked, triggering the exploitation of the vulnerability. A line would then depict the malicious code executing on the victim’s device.
Finally, arrows would show the data exfiltration, with data flowing from the victim’s device to the attacker’s server. The overall flow would visually represent the progression from initial contact to data compromise.
Steps in a Successful CarPlay Vulnerability Attack
This visual would be a flowchart depicting the attack. It would start with the installation of a seemingly legitimate, yet malicious, third-party CarPlay app on the victim’s iPhone. The next step would show the iPhone connecting to the car’s infotainment system via CarPlay. The flowchart would then illustrate the activation of the malicious code within the app upon connection.
The subsequent steps would show the attacker gaining control of specific car functions (represented by icons like a steering wheel, brake pedal, etc.) and potentially exfiltrating data from the car’s system or the connected iPhone. The final step would depict the attacker maintaining control or achieving their objective, highlighting the vulnerability’s impact.
Final Review
This latest iOS security update is a crucial step in maintaining the privacy and security of your Apple devices. By addressing critical vulnerabilities in FaceTime and CarPlay, Apple demonstrates a proactive approach to patching and protecting its users. While no system is entirely impenetrable, this update significantly reduces the risk of exploitation. Remember to update your devices immediately to benefit from these essential security enhancements and practice good digital hygiene to further protect your data.
Stay vigilant, stay updated!
FAQ Insights
What specific FaceTime vulnerabilities were addressed?
The update addressed vulnerabilities that could have allowed attackers to access and potentially manipulate messages or even gain access to a user’s device through manipulated messages.
How long does the update take to install?
Installation time varies depending on your device and internet connection speed, but generally takes between 15-30 minutes.
Will this update affect my device’s performance?
While there might be a slight temporary impact, Apple generally optimizes updates to minimize any performance or battery life reduction.
What happens if I don’t update my iOS?
You remain vulnerable to the security flaws addressed in the update, increasing the risk of data breaches, unauthorized access, and other security compromises.





