Apple iPhones Pegasus Spyware Protection
Apple iphones to get protection against pegasus mobile spyware – Apple iPhones: Pegasus Spyware Protection – it’s a phrase that’s become increasingly relevant in today’s digital landscape. Pegasus, the infamous spyware, has proven capable of infiltrating even the most secure devices, raising serious concerns about privacy and security. This post dives deep into the threat Pegasus poses to iPhones, explores Apple’s countermeasures, and provides practical steps you can take to bolster your own defenses.
We’ll examine the technical aspects of Pegasus, analyze Apple’s security updates, and discuss the role of third-party security software – all to help you understand how to best protect your iPhone from this sophisticated threat.
We’ll unpack the intricacies of how Pegasus works, from its infection methods to its data exfiltration techniques. We’ll also cover Apple’s proactive measures, including software updates and security patches specifically designed to counter Pegasus vulnerabilities. Furthermore, we’ll look at practical user-level strategies, such as strengthening passwords, enabling two-factor authentication, and using a VPN to enhance privacy. Finally, we’ll touch on the legal and ethical implications surrounding the use of such powerful surveillance technology.
Pegasus Spyware
Pegasus is a highly sophisticated and invasive mobile spyware developed by the Israeli cyber-arms company NSO Group. Its notoriety stems from its ability to compromise even the most secure devices, including iPhones, and extract vast amounts of sensitive data without the user’s knowledge or consent. This has led to significant concerns about privacy violations and human rights abuses globally.
Pegasus Spyware Functionality: Infection and Data Exfiltration
Pegasus infects devices primarily through the exploitation of zero-day vulnerabilities – previously unknown software flaws – in the operating system. This means that the target doesn’t need to click on a malicious link or download a compromised app; the infection can occur passively. Once installed, Pegasus can access a wide range of data, including messages, emails, call logs, location data, photos, and even encrypted communications.
Data exfiltration, the process of secretly transferring stolen data to a remote server controlled by the attackers, is typically conducted discreetly over encrypted channels, making detection difficult. The spyware operates in a stealthy manner, often hiding its presence within the device’s system processes.
Pegasus Exploits in iOS
Pegasus has historically exploited several vulnerabilities within iOS, leveraging flaws in the operating system’s kernel, which is the core of the system responsible for managing hardware and software resources. These vulnerabilities allow Pegasus to gain root access, providing it with virtually unrestricted control over the device. Specific exploits have targeted vulnerabilities in iMessage, allowing the spyware to be installed simply by sending a specially crafted message to the victim’s phone.
The attackers would embed malicious code within the message itself, which is then executed when the message is processed by the device. The sophistication of these exploits lies in their ability to bypass Apple’s built-in security mechanisms, such as sandboxing and code signing, which are designed to prevent malicious code from running.
Pegasus’s Circumvention of Apple’s Security Features
Apple employs various security measures, including code signing, sandboxing, and regular security updates, to protect user data. However, Pegasus has demonstrated a capability to bypass these measures. It achieves this by exploiting zero-day vulnerabilities that are unknown to Apple, rendering these security mechanisms ineffective. Once a zero-day is exploited, Pegasus can gain root access and execute its malicious code, effectively disabling the protections Apple has put in place.
The use of zero-day vulnerabilities underscores the constant arms race between security researchers and attackers, with attackers constantly seeking new ways to exploit vulnerabilities before they are patched.
Comparison with Other Mobile Spyware
While other mobile spyware threats exist, Pegasus stands out due to its advanced capabilities, stealthy operation, and high cost. Other spyware might rely on user interaction, such as clicking a malicious link or installing a seemingly legitimate app. Pegasus, however, often operates without any user interaction, making it significantly more dangerous. Furthermore, the level of data it can access and the sophistication of its evasion techniques are unmatched by many other mobile spyware threats.
The targeted nature of Pegasus attacks, often focusing on high-profile individuals, journalists, and activists, further distinguishes it from more generalized malware.
Known Pegasus Exploits and Affected iOS Versions
The following table summarizes some known Pegasus exploits and their corresponding iOS versions:
| Exploit Name | iOS Version | Vulnerability Type | Mitigation Strategy |
|---|---|---|---|
| FORCEDENTRY | iOS 14.6 and earlier | Kernel vulnerability | iOS updates |
| TRIBULATION | iOS 13.5 – 14.7.1 | iMessage vulnerability | iOS updates |
| KINAGINTAN | iOS 14.6 | Kernel vulnerability | iOS updates |
| KISMET | iOS 14.6 | Kernel vulnerability | iOS updates |
Apple’s Security Measures Against Pegasus
Apple’s response to the Pegasus spyware threat has been multifaceted, involving rapid security updates, proactive development strategies, and transparent communication with its users. The company’s approach highlights its commitment to robust device security and user privacy in the face of sophisticated cyberattacks. This response has been arguably more proactive and comprehensive than its reactions to other major security breaches, setting a high bar for the industry.Apple’s Security Updates and Patches Addressing Pegasus VulnerabilitiesFollowing the revelations about Pegasus’s capabilities, Apple swiftly released a series of iOS updates designed to patch the vulnerabilities exploited by the spyware.
These updates included improvements to the operating system’s kernel, memory management, and messaging applications – key targets of Pegasus’s attack vectors. For example, iOS 14.8, released in September 2021, addressed several zero-day exploits that NSO Group, the developers of Pegasus, had used to gain unauthorized access to iPhones. These patches weren’t merely superficial fixes; they involved significant architectural changes to enhance the overall security posture of the iOS ecosystem.
The updates weren’t just reactive; they demonstrated a proactive approach to anticipating and neutralizing future threats.
Proactive Measures to Prevent Future Pegasus Infections
Apple’s response to Pegasus extended beyond simply patching existing vulnerabilities. The company invested in proactive security measures aimed at preventing future infections. This involved enhancing its threat detection and response capabilities, improving its sandboxing technology (which isolates potentially malicious code), and strengthening its code signing processes to prevent the installation of unauthorized software. Furthermore, Apple intensified its collaboration with security researchers and independent auditing firms to identify and address potential weaknesses in its software before they could be exploited by malicious actors.
This proactive approach reflects a shift towards a more predictive security model, aiming to prevent attacks before they can occur.
The Role of iOS Updates in Mitigating Pegasus Threats
Regular iOS updates are crucial in mitigating Pegasus threats. Apple consistently releases updates containing security patches and improvements, including those addressing vulnerabilities exploited by spyware like Pegasus. Users who keep their devices updated with the latest iOS version significantly reduce their risk of infection. This highlights the importance of user participation in maintaining their device’s security. Failure to update the operating system leaves devices vulnerable to exploitation.
The rapid release of patches following the discovery of new vulnerabilities demonstrates Apple’s commitment to timely and effective security updates. This ongoing process of improvement and patching is a critical element of Apple’s defense against sophisticated spyware.
Comparison of Apple’s Response to Pegasus with Other Security Breaches
Compared to its responses to other major security breaches, Apple’s reaction to Pegasus stands out for its speed, transparency, and comprehensiveness. While Apple has addressed other vulnerabilities and security flaws in the past, the Pegasus incident prompted a particularly swift and visible response. The company publicly acknowledged the threat, communicated directly with users about the risks, and released updates with unprecedented speed.
This level of transparency and proactive engagement contrasted with some of its previous responses to other security concerns, demonstrating a heightened awareness of the severity of state-sponsored spyware attacks.
Examples of Apple’s Communication Strategies Regarding Pegasus to its Users, Apple iphones to get protection against pegasus mobile spyware
Apple employed several communication strategies to inform its users about the Pegasus threat and the steps they could take to protect themselves. These strategies included public statements acknowledging the threat, detailed security advisories explaining the vulnerabilities and the patches, and proactive push notifications urging users to update their devices. Apple also worked with journalists and researchers to disseminate information about the threat and its mitigation.
This open and proactive communication built trust with its users and demonstrated a commitment to transparency in addressing a significant security concern. The company’s actions went beyond simply releasing updates; they included educating users on the importance of keeping their software up-to-date and understanding the risks of sophisticated cyberattacks.
User-Level Protection Strategies Against Pegasus
Protecting your iPhone from sophisticated spyware like Pegasus requires a multi-layered approach. While Apple implements robust security measures, proactive user actions significantly enhance your overall protection. This involves understanding the risks and taking concrete steps to minimize your vulnerability. Remember, even the best security systems can be circumvented with targeted attacks, but layering defenses makes a significant difference.
Practical Steps to Minimize Pegasus Infection Risk
Taking preventative measures is crucial in safeguarding your iPhone from Pegasus. These steps, while not foolproof, dramatically reduce your attack surface. Combining these strategies provides a robust defense.
- Be cautious about unknown links and attachments: Avoid clicking on links or opening attachments from untrusted sources, including suspicious emails, text messages, or social media posts. Phishing attempts often use seemingly legitimate links to deliver malicious payloads.
- Scrutinize app permissions: Before installing any app, carefully review the requested permissions. If an app requests access to features beyond what it logically needs (like microphone access for a calculator app), it might be malicious. Only install apps from trusted sources like the App Store.
- Regularly review installed apps: Periodically check your installed apps to ensure you recognize them all. If you find an unfamiliar app, immediately delete it.
- Enable two-factor authentication (2FA) wherever possible: 2FA adds an extra layer of security, making it significantly harder for attackers to access your accounts even if they obtain your password.
- Use strong, unique passwords: Employ complex passwords for all your accounts, and ensure they differ across platforms. Consider using a password manager to help generate and manage strong passwords securely.
- Keep your operating system updated: Apple regularly releases security updates that patch vulnerabilities. Install these updates promptly to benefit from the latest protections.
- Be wary of jailbreaking: Jailbreaking your iPhone compromises its security and significantly increases your vulnerability to malware like Pegasus.
- Limit Wi-Fi usage in untrusted locations: Public Wi-Fi networks are often less secure than private networks. Avoid using sensitive apps or conducting sensitive transactions on public Wi-Fi.
Enhancing iPhone Security Settings: A Step-by-Step Guide
Configuring your iPhone’s security settings correctly provides a fundamental layer of protection. Following these steps will strengthen your device’s defenses.
- Enable automatic software updates: Go to Settings > General > Software Update and enable automatic downloads and installations. This ensures your iPhone is always running the latest security patches.
- Turn on Find My iPhone: Go to Settings > [Your Name] > Find My and ensure Find My iPhone is activated. This allows you to remotely locate, lock, or erase your device if it’s lost or stolen.
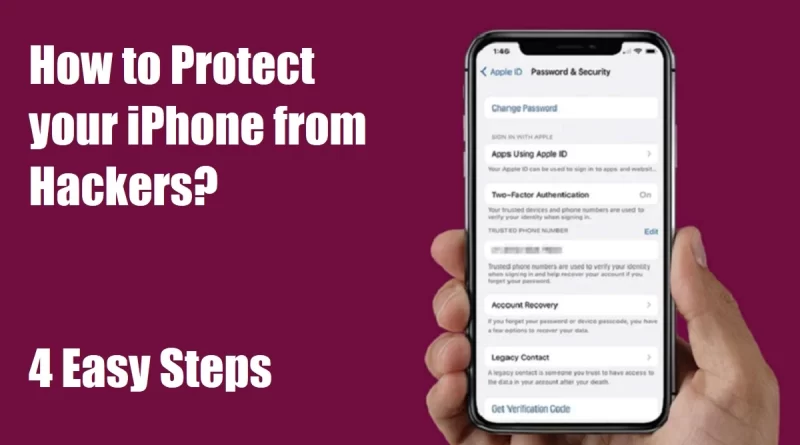
- Use a strong passcode: Go to Settings > Face ID & Passcode (or Touch ID & Passcode) and set a complex alphanumeric passcode. Avoid simple, easily guessable codes.
- Enable two-factor authentication for Apple ID: Go to Settings > [Your Name] > Password & Security and set up two-factor authentication for your Apple ID. This adds an extra layer of security to your account.
- Review app permissions: Go to Settings > Privacy & Security and review the permissions granted to each app. Revoke any unnecessary permissions.
The Importance of Software Updates in Mitigating Risks
Software updates are crucial for maintaining your iPhone’s security. Apple regularly releases updates that address security vulnerabilities, including those that could be exploited by Pegasus. Failing to update your device leaves it susceptible to known exploits, significantly increasing your risk of compromise. For instance, the release of iOS 16.6 included important security patches, demonstrating the ongoing need for timely updates.
Delaying updates, even for a short period, can expose your device to attacks.
Strong Passwords and Two-Factor Authentication
Employing strong, unique passwords for all your accounts and enabling two-factor authentication (2FA) are paramount for online security. A strong password is long, complex, and includes a mix of uppercase and lowercase letters, numbers, and symbols. 2FA adds an extra layer of security by requiring a second verification method, such as a code sent to your phone or email, in addition to your password.
This significantly reduces the risk of unauthorized access, even if your password is compromised. For example, using a password manager can help generate and manage strong, unique passwords across all your accounts.
The Benefits of Using a VPN and Its Impact on Privacy
A Virtual Private Network (VPN) encrypts your internet traffic and masks your IP address, making it harder for attackers to track your online activity. While a VPN doesn’t directly prevent Pegasus infection, it enhances your overall privacy and security by protecting your data from interception on public Wi-Fi networks or by malicious actors monitoring your internet traffic. For example, a VPN can prevent your internet service provider (ISP) from tracking your browsing history and other online activities.
Using a reputable VPN provider further enhances your security.
The Role of Third-Party Security Software
Third-party security apps offer an additional layer of protection against sophisticated threats like Pegasus, supplementing Apple’s built-in security features. While not a foolproof solution, they can enhance your iPhone’s defenses by providing real-time monitoring, threat detection, and potentially blocking malicious activities. However, it’s crucial to understand their limitations and potential risks before relying on them.The effectiveness of third-party security apps in preventing Pegasus infections varies significantly depending on the app’s capabilities and the sophistication of the attack.
These apps typically function by monitoring network traffic, analyzing app behavior, and detecting suspicious activities. While they can identify some known malicious patterns, they might not always detect zero-day exploits or highly advanced attacks like Pegasus, which often utilize previously unknown vulnerabilities.
Effectiveness of Third-Party Security Apps
The effectiveness of these apps is a complex issue. Many boast advanced features like intrusion detection and VPN services, but their ability to detect and prevent Pegasus-like attacks is limited. Pegasus often exploits unknown vulnerabilities, making it difficult for even the most advanced security software to proactively block it. However, some apps can detect theaftermath* of an infection by identifying unusual network activity or data exfiltration attempts.
The best approach is to consider these apps as an additional layer of defense, not a guaranteed shield against all threats. Their value lies in providing an extra layer of monitoring and potentially alerting you to suspicious behavior, prompting you to take further action.
Potential Risks and Limitations of Third-Party Security Software
Using third-party security software introduces its own set of risks. Some apps might collect excessive user data, potentially compromising privacy. Others might slow down your device’s performance or interfere with other apps. It’s crucial to research the app’s privacy policy and security practices thoroughly before installing it. Furthermore, relying solely on third-party software without practicing good security hygiene (like keeping your software updated and being cautious about suspicious links) is not a comprehensive solution.
False positives are another potential issue; the app might flag legitimate activities as suspicious, leading to unnecessary alerts and inconvenience.
Types of Third-Party Security Software for iPhones
Several types of third-party security software cater to iPhones, each with a different focus. Some focus on antivirus protection, scanning for malware and potentially harmful apps. Others offer VPN services to encrypt your internet traffic and mask your IP address, enhancing privacy and potentially hindering surveillance. Some combine both, offering a comprehensive security suite. Finally, there are apps specializing in intrusion detection, monitoring system activity for unusual behavior.
The choice depends on your specific needs and risk tolerance.
Features to Look for When Choosing Security Software
When selecting a third-party security app, consider several key features. Look for apps with a strong reputation, positive user reviews, and a clear privacy policy. Transparency regarding data collection practices is crucial. Check for features like real-time malware scanning, network traffic monitoring, VPN capabilities (if needed), and intrusion detection. Consider apps with regular updates to address newly discovered vulnerabilities.
A user-friendly interface and reliable customer support are also important factors.
Comparison of Popular Security Apps
Choosing the right app requires careful consideration. Below is a comparison of three popular security apps, highlighting their key features and limitations. Note that the information provided is based on publicly available data and may change over time.
| App Name | Key Features | Limitations | Price |
|---|---|---|---|
| Example App 1 | Antivirus scanning, VPN, intrusion detection | Potential performance impact, limited free version | Free (limited) / $X per year |
| Example App 2 | VPN, privacy monitoring, web protection | No antivirus scanning, limited features in free version | Free (limited) / $Y per year |
| Example App 3 | Antivirus, anti-phishing, network monitoring | Can be resource-intensive, complex interface | $Z per year |
Legal and Ethical Implications of Pegasus

The development and deployment of Pegasus spyware, capable of penetrating the most secure mobile devices, raises profound ethical and legal questions. Its potential for misuse significantly impacts individual privacy, civil liberties, and the very fabric of democratic societies. The lack of transparency surrounding its use further exacerbates these concerns.Pegasus’s capabilities extend far beyond legitimate law enforcement practices. Its ability to access virtually all aspects of a target’s digital life—from communications and location data to personal files and even microphone recordings—presents a chilling prospect for abuse.
The potential for targeting journalists, activists, and political opponents for surveillance and intimidation undermines fundamental human rights.
Ethical Concerns Surrounding Pegasus
The ethical implications of Pegasus are multifaceted. The lack of informed consent from targets is a primary concern. Surveillance conducted without knowledge or permission is a violation of basic ethical principles. Furthermore, the potential for misuse by authoritarian regimes to suppress dissent and silence critics raises serious ethical red flags. The opacity surrounding the distribution and use of the software further complicates the ethical landscape, making accountability difficult to achieve.
The potential for collateral damage—the unintended surveillance of innocent individuals associated with the target—also raises ethical dilemmas.
Legal Ramifications of Unauthorized Surveillance with Pegasus
The use of Pegasus for unauthorized surveillance constitutes a serious violation of numerous legal frameworks. Depending on the jurisdiction, this could lead to prosecution under laws relating to privacy violations, data protection, and even wiretapping. The legality of mass surveillance programs employing such technology is also intensely debated, with many countries having strict limitations on government surveillance powers.
Apple iPhones are finally getting some serious upgrades to combat the Pegasus spyware threat, which is fantastic news for privacy. This kind of robust security development makes me think about the broader implications for app development, especially as we explore the possibilities outlined in this article on domino app dev, the low code and pro code future , and how these advancements could help build even more secure apps.
Ultimately, stronger security measures for our devices, like the improvements to iPhone’s defenses against Pegasus, are crucial in this evolving digital landscape.
For example, the European Union’s General Data Protection Regulation (GDPR) sets strict requirements for data processing, including consent and data minimization, which Pegasus frequently violates. Similarly, the US Fourth Amendment protects against unreasonable searches and seizures, raising significant legal challenges to the use of Pegasus without a warrant.
Impact of Pegasus on Individual Privacy and Civil Liberties
Pegasus’s capabilities pose a significant threat to individual privacy and civil liberties. The unrestricted access it provides to personal data erodes the trust individuals place in their devices and online interactions. The chilling effect of knowing one’s communications and activities are potentially under constant surveillance can suppress free speech and hinder democratic participation. This erosion of trust can extend beyond the targeted individuals to society as a whole, fostering a climate of suspicion and fear.
The psychological impact on individuals targeted by Pegasus can be substantial, leading to anxiety, stress, and a feeling of vulnerability.
Legal Frameworks Governing Surveillance Technologies
Legal frameworks governing surveillance technologies vary considerably across countries. Some nations have robust data protection laws and regulations that limit government surveillance powers, while others have far less stringent oversight. The legal interpretations of what constitutes a legitimate basis for surveillance also differ widely. Some countries allow for mass surveillance under broad national security provisions, while others require individualized warrants based on probable cause.
This disparity in legal frameworks creates a global landscape where the use of spyware like Pegasus can be legally permissible in some places but illegal in others, complicating international efforts to regulate its use.
Role of International Organizations in Addressing Spyware Misuse
International organizations like the United Nations and the Council of Europe play a crucial role in addressing the misuse of spyware like Pegasus. They can facilitate international cooperation in investigating instances of misuse, develop international standards for surveillance technologies, and promote the adoption of robust legal frameworks that protect individual privacy and human rights. However, the effectiveness of these organizations is limited by the varying legal and political landscapes of their member states.
The challenge lies in achieving consensus on international norms and enforcement mechanisms in a world where the use of such technologies is often shrouded in secrecy.
Final Conclusion
In the ongoing battle against sophisticated spyware like Pegasus, vigilance and proactive security measures are paramount. While Apple consistently works to patch vulnerabilities and improve iPhone security, individual responsibility remains crucial. By understanding how Pegasus operates, staying updated with iOS releases, and implementing the security tips Artikeld in this post, you can significantly reduce your risk of becoming a victim.
Remember, your digital privacy is worth protecting. Stay informed, stay secure.
Commonly Asked Questions: Apple Iphones To Get Protection Against Pegasus Mobile Spyware
What is Pegasus spyware?
Pegasus is a highly sophisticated spyware capable of infecting smartphones and extracting vast amounts of data, including messages, photos, location data, and even microphone recordings.
Are all iPhones vulnerable to Pegasus?
While Apple actively works to patch vulnerabilities, older iOS versions may remain susceptible. Keeping your iPhone updated with the latest iOS version is critical.
Can I completely eliminate the risk of Pegasus infection?
No technology offers 100% protection, but by following best practices, you can significantly reduce your risk.
What should I do if I suspect my iPhone has been compromised?
Immediately update your iOS, change your passwords, and consider contacting Apple Support or law enforcement.