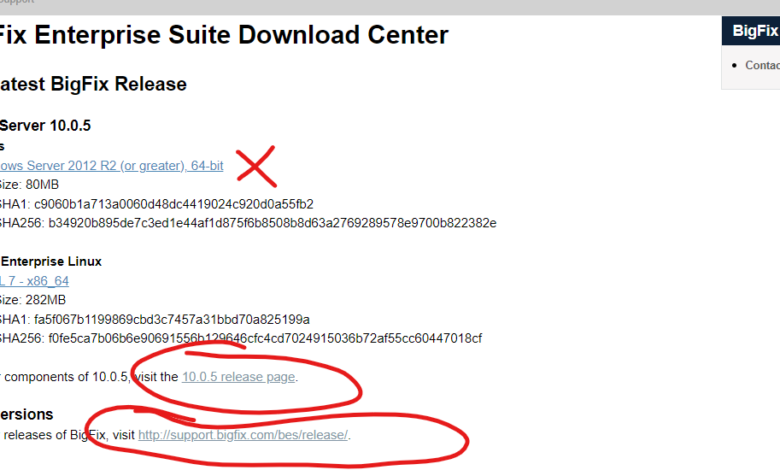
How to Simplify In-Place Windows Upgrades Using BigFix
How to simplify in place windows upgrades using bigfix – How to simplify in-place Windows upgrades using BigFix? It’s a question many IT admins grapple with. Traditional Windows upgrades can be a nightmare – downtime, compatibility issues, and the sheer complexity of managing it across numerous machines. But what if there was a simpler, more efficient way? This post dives into leveraging BigFix’s powerful capabilities to streamline the entire process, from pre-upgrade checks to post-upgrade verification, minimizing disruption and maximizing efficiency.
We’ll explore best practices, troubleshooting techniques, and even advanced strategies to optimize your upgrade deployments for even the largest environments.
We’ll cover everything from designing BigFix actions for automated pre-upgrade checks and creating streamlined task sequences to handling application compatibility issues and resolving potential upgrade conflicts. We’ll delve into the importance of BigFix relevance for targeted machine upgrades, explore post-upgrade verification methods, and discuss strategies for optimizing the BigFix deployment process for large-scale upgrades. Get ready to transform your Windows upgrade process from a dreaded event into a smoothly executed operation!
Understanding BigFix and Windows In-Place Upgrades
Windows in-place upgrades offer a streamlined approach to updating your operating system, allowing you to keep your applications and data intact while transitioning to a newer version. This method contrasts sharply with a clean installation, which requires a complete reinstallation of the OS and all associated software. However, managing these upgrades across a large enterprise environment can be a significant challenge without the right tools.
This is where BigFix steps in.BigFix, now part of IBM’s Endpoint Manager, is a powerful endpoint management solution that provides robust capabilities for software deployment, patching, and operating system upgrades. Its agent-based architecture allows for centralized control and automated deployment of updates to a vast number of endpoints.
Windows In-Place Upgrade Mechanics
An in-place upgrade involves installing a newer version of Windows over the existing installation. The process essentially overwrites the older files with newer ones while preserving user data, settings, and most applications. This differs from a clean installation, where everything is wiped and reinstalled from scratch. The success of an in-place upgrade depends on various factors, including the compatibility of the applications and drivers with the newer OS version and the health of the existing system.
A corrupted system may prevent a successful in-place upgrade, necessitating a clean installation instead. The upgrade process itself can be lengthy, and the system may be unavailable for a considerable amount of time.
BigFix’s Role in Software Deployment and Patching
BigFix uses a client-server architecture. The BigFix server manages policies and deployments, while BigFix agents, installed on each endpoint, receive and execute these instructions. This allows for centralized control over software updates and patching. BigFix can automatically detect the operating system version on each endpoint, identify which machines require an upgrade, and then deploy the upgrade package to those machines.
It can also schedule the upgrade for off-peak hours to minimize disruption. The system offers detailed reporting and logging, allowing administrators to track the progress of the upgrade and identify any issues. This detailed monitoring helps in proactive troubleshooting and ensures minimal downtime.
Traditional Upgrade Method vs. BigFix-Managed Upgrades
Traditionally, deploying Windows upgrades across a large enterprise involved manual processes, scripting, or less sophisticated management tools. This often led to inconsistencies, delays, and increased administrative overhead. Troubleshooting issues was a time-consuming process, and ensuring a consistent upgrade experience across all machines was difficult.In contrast, BigFix automates many aspects of the upgrade process. It streamlines the deployment, providing consistent application of updates across the entire infrastructure.
BigFix allows for targeted deployments, enabling administrators to apply upgrades only to specific groups of machines or based on other criteria. This precision minimizes the risk of unintended consequences and allows for more controlled rollouts. Furthermore, BigFix’s reporting and logging capabilities provide valuable insights into the upgrade process, facilitating quicker identification and resolution of problems.
Challenges of Managing In-Place Upgrades Without BigFix
Without a robust management solution like BigFix, managing in-place upgrades across a large number of machines is fraught with challenges. The process becomes extremely time-consuming and error-prone. Ensuring consistent upgrade deployment and addressing compatibility issues on a machine-by-machine basis is a significant undertaking. Tracking progress, identifying failed upgrades, and troubleshooting problems become considerably more difficult, potentially leading to extended downtime and lost productivity.
The lack of centralized control increases the risk of human error, which can have serious implications for system stability and security. Lack of automated reporting also hinders efficient monitoring and analysis.
Streamlining the Upgrade Process with BigFix
Automating Windows in-place upgrades with BigFix offers significant advantages over manual methods, primarily reducing downtime and ensuring consistency across your entire fleet. This approach leverages BigFix’s powerful capabilities for remote control, software distribution, and system management to streamline the upgrade process and minimize disruptions.BigFix provides a robust framework for managing the entire upgrade lifecycle, from pre-upgrade checks to post-upgrade validation.
This allows IT administrators to confidently deploy updates across hundreds or even thousands of machines simultaneously, with granular control and detailed reporting. This post will detail how to design and implement a streamlined in-place upgrade process using BigFix.
BigFix Action for Pre-Upgrade Checks
A crucial step before initiating any in-place upgrade is to perform thorough pre-upgrade checks. This action should verify hardware compatibility, software dependencies, disk space availability, and current Windows version. A well-designed BigFix action can automate these checks, preventing unnecessary upgrade attempts on incompatible machines. This action would consist of several individual checks, each reporting success or failure back to the BigFix console.
For example, one check might use WMI queries to verify sufficient free disk space, while another could use a custom script to examine the presence of crucial applications and drivers. The results of these checks would be aggregated, allowing administrators to identify and address potential issues before proceeding with the upgrade.
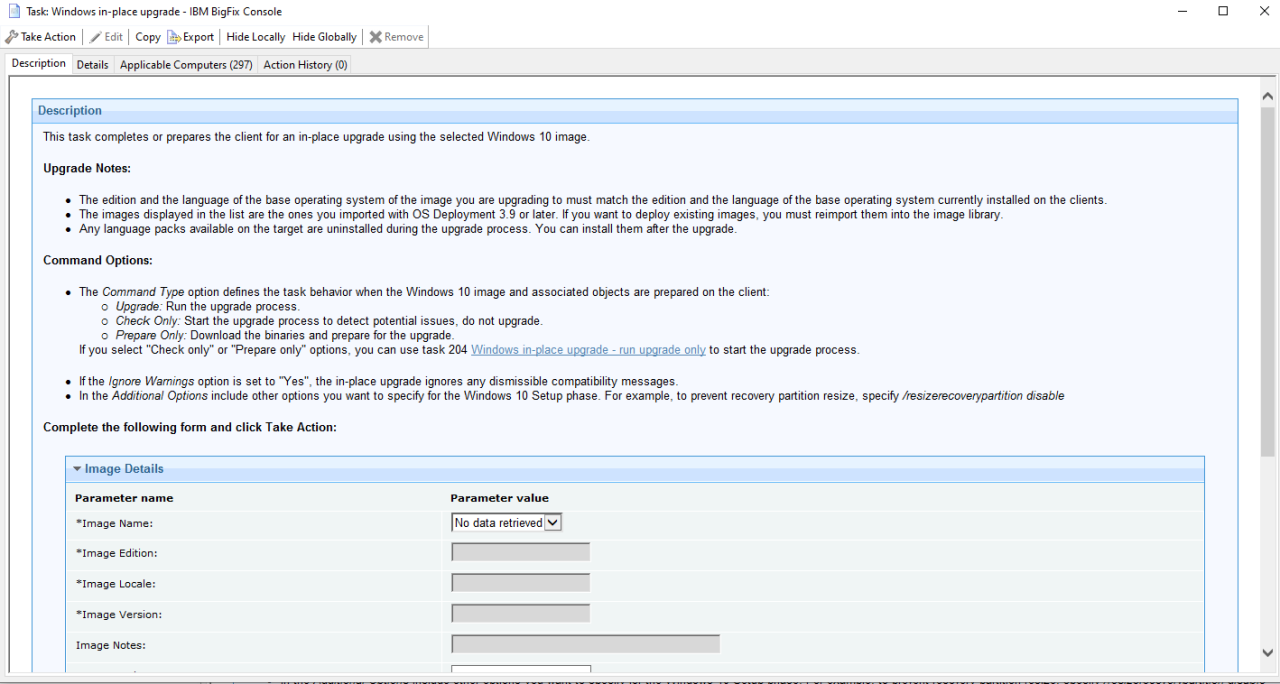
BigFix Task Sequence for In-Place Upgrade
The core of the upgrade process resides in the BigFix task sequence. This sequence should orchestrate the download of the Windows upgrade package, initiate the in-place upgrade process, and monitor its progress. The sequence needs to handle potential errors gracefully, allowing for retries or escalation to manual intervention if necessary. A key component is the use of BigFix’s built-in capabilities for executing commands remotely and monitoring their status.
The sequence would include steps for initiating the upgrade using the `DISM` command-line tool, and then for monitoring the process using system event logs or other indicators. This allows for real-time tracking of the upgrade’s progress and the identification of any potential problems.
Best Practices for Minimizing Downtime
Minimizing downtime during an in-place upgrade is paramount. Several strategies can be employed to achieve this goal. First, scheduling the upgrade during off-peak hours is crucial to minimize disruption to end-users. Second, leveraging BigFix’s ability to target specific machines allows for phased rollouts, allowing IT to test the upgrade process on a smaller subset of machines before deploying it to the entire fleet.
Third, robust error handling and logging within the BigFix task sequence are essential to identify and resolve any issues quickly. Finally, thorough pre-upgrade checks, as discussed previously, prevent unnecessary upgrade attempts on incompatible machines, further reducing potential downtime.
Step-by-Step Guide for Deploying the Upgrade Using BigFix
1. Create a BigFix Relevance
Define a relevance statement to precisely target the machines requiring the upgrade. This might include factors like operating system version, hardware specifications, or application installations.
2. Develop Pre-Upgrade Check Action
Create a BigFix action to perform pre-upgrade checks, including disk space, application compatibility, and hardware requirements. This action should report pass/fail status for each check.
3. Create Upgrade Task Sequence
Design a BigFix task sequence to download the upgrade package, run the in-place upgrade using DISM, and monitor the process for errors. Include retry mechanisms and logging for troubleshooting.
4. Deploy to Targeted Machines
Deploy the pre-upgrade check action to the targeted machines. Review the results to identify and resolve any issues.
5. Execute Upgrade Task Sequence
Deploy the upgrade task sequence to the machines that passed the pre-upgrade checks.
6. Monitor and Validate
Monitor the upgrade progress in the BigFix console. Verify the upgrade’s success and address any issues that arise.
Role of BigFix Relevance in Targeting Specific Machines
BigFix relevance is instrumental in precisely targeting the machines that need the upgrade. A well-crafted relevance statement ensures that only eligible machines receive the upgrade, preventing unintended upgrades on incompatible systems. This allows for a controlled rollout and minimizes the risk of widespread issues. For example, a relevance statement might target only machines running Windows 10 version 1909 and possessing sufficient disk space.
This granular control minimizes disruption and allows for efficient resource allocation. The use of complex relevance statements allows for sophisticated filtering, ensuring that the upgrade process is applied only to the appropriate systems.
Handling Dependencies and Conflicts: How To Simplify In Place Windows Upgrades Using Bigfix
In-place upgrades, while efficient, introduce the risk of application compatibility issues and conflicts. Successfully navigating these challenges is crucial for a smooth upgrade process. This section details strategies for identifying, mitigating, and resolving these potential problems using BigFix. We’ll cover application compatibility, conflict identification, driver management, and pre-upgrade cleanup.
Application Compatibility Issues
Application compatibility is a major concern during in-place upgrades. Older applications might not function correctly with the newer operating system. A thorough assessment of installed applications is necessary before initiating the upgrade. BigFix can inventory software, allowing for a pre-upgrade analysis to identify potential conflicts. This involves checking application compatibility matrices provided by vendors or using third-party tools to scan for potential issues.
For example, if an application is known to be incompatible with the target Windows version, BigFix can be used to exclude systems with that application installed from the upgrade process, preventing potential failures. Alternatively, BigFix actions can trigger the installation of updated, compatible versions before the upgrade begins.
Identifying and Mitigating Potential Upgrade Conflicts
BigFix facilitates proactive identification of potential upgrade conflicts. This involves analyzing system logs, registry keys, and other system data for potential issues. For example, BigFix can be configured to check for specific registry keys associated with known conflicting applications or services. If conflicts are detected, BigFix can then trigger actions such as uninstalling conflicting applications or modifying system settings to resolve the conflict.
Another strategy is to use BigFix to run compatibility checks before the upgrade, flagging systems that might experience problems. This allows for targeted remediation before initiating the wider upgrade process.
Managing Driver Updates During the Upgrade
Driver updates are often a critical component of a successful Windows upgrade. Outdated or incompatible drivers can lead to post-upgrade instability or hardware malfunctions. BigFix can manage this by deploying updated drivers before or after the upgrade. This can be achieved through custom BigFix actions that download and install the necessary drivers. Careful planning is essential, considering potential dependencies between drivers and ensuring compatibility with the new operating system.
For example, BigFix can be used to deploy a specific set of drivers known to be compatible with the target Windows version, ensuring that all critical hardware components function correctly after the upgrade.
Uninstalling Conflicting Applications Before the Upgrade
Proactively uninstalling conflicting applications before the upgrade minimizes the risk of failures. BigFix can automate this process. A BigFix action can be created to identify and uninstall applications known to be incompatible with the target operating system. This action can be targeted at specific systems or groups based on the results of pre-upgrade assessments. Careful consideration of dependencies is critical here, ensuring that uninstalling one application doesn’t negatively impact other essential software.
For instance, BigFix can be configured to uninstall an application only if certain dependent applications are already uninstalled or updated.
Dependency Management Approaches
| Approach | Description | Advantages | Disadvantages |
|---|---|---|---|
| Pre-Upgrade Assessment & Remediation | BigFix scans systems for incompatible applications and drivers before the upgrade. Incompatible software is either updated or uninstalled. | Reduces upgrade failures, minimizes downtime. | Requires thorough application compatibility analysis and potentially lengthy remediation time. |
| Conditional Upgrade Deployment | BigFix only upgrades systems that meet specific compatibility criteria. | Limits upgrade failures to a smaller subset of systems. | Some systems might be excluded unnecessarily, delaying upgrades. |
| Post-Upgrade Remediation | BigFix identifies and addresses issues after the upgrade. | Allows for a rapid initial upgrade rollout. | Potential for disruption and user impact if significant issues arise. |
| Phased Rollout | BigFix deploys the upgrade in stages, allowing for observation and correction of issues before a wider deployment. | Minimizes risk and allows for iterative improvements to the upgrade process. | Slower overall upgrade completion. |
Post-Upgrade Verification and Reporting
Successfully upgrading a large number of Windows machines using BigFix requires more than just initiating the upgrade process. Robust post-upgrade verification and comprehensive reporting are crucial to ensure the operation’s success and identify any issues requiring attention. This section details how to leverage BigFix’s capabilities to achieve this.Post-upgrade verification involves confirming the expected outcome across your entire fleet, and reporting provides a centralized view of the upgrade’s progress and results.
This allows for proactive identification and resolution of any problems that may arise.
BigFix Action for Upgrade Verification
A BigFix action designed for post-upgrade verification should check for several key indicators. This action would ideally execute after the in-place upgrade action completes. We can use a combination of relevance statements and custom scripts to check the operating system version, registry keys indicating a successful upgrade, and the presence of critical post-upgrade files. For example, a relevance statement could check the Windows version: (Operating System = "Windows 10") and (Operating System Version > "10.0.22621").
This would verify if the system upgraded to at least a specific build number. Further verification can be performed using a custom script (e.g., PowerShell) to check for specific registry keys or file existence, indicating successful upgrade completion and the absence of errors during the process. The action’s success or failure would be logged within the BigFix console, providing immediate feedback on the upgrade status of each machine.
Comprehensive Upgrade Status Report
A comprehensive report should summarize the upgrade status across all targeted machines. BigFix’s reporting capabilities can be leveraged to create a report that includes the machine name, operating system version before and after the upgrade, upgrade start and end times, any error messages encountered during the upgrade, and the overall success or failure status. This report can be scheduled to run automatically after the upgrade process and can be exported in various formats (e.g., CSV, HTML) for further analysis.
The report could visually represent the success rate with color-coded indicators (green for success, red for failure), facilitating quick identification of problematic machines. A sample report might include columns for: “Computer Name”, “Pre-Upgrade OS Version”, “Post-Upgrade OS Version”, “Upgrade Status”, “Start Time”, “End Time”, “Error Details”.
Post-Upgrade System Health Monitoring
Monitoring system health post-upgrade is critical to identify potential regressions or unforeseen issues. BigFix can be used to proactively monitor key performance indicators (KPIs) such as CPU utilization, memory usage, disk space, and network activity. Custom actions can be created to collect this data at regular intervals and generate alerts if any KPIs exceed predefined thresholds. This allows for early detection of performance bottlenecks or system instability that may have resulted from the upgrade.
BigFix can also be configured to monitor event logs for critical errors or warnings related to the upgraded components.
Gathering Post-Upgrade System Logs with BigFix, How to simplify in place windows upgrades using bigfix
BigFix can efficiently collect system logs from upgraded machines. This can be achieved by creating a BigFix action that retrieves specific log files (e.g., Windows Event Logs, system logs) and uploads them to a central repository. This enables centralized analysis of log files for potential issues that may not be immediately apparent through other monitoring methods. The collected logs can be further analyzed using log analysis tools to identify patterns and trends.
This approach allows for a deep dive into the upgrade process and helps identify potential root causes of any post-upgrade problems.
Automating the Rollback Process
Automating the rollback process is crucial for mitigating the impact of failed upgrades. A BigFix action can be designed to revert the upgrade to the previous operating system version if the post-upgrade verification fails. This action would typically involve using a pre-defined system restore point or utilizing a system image backup. The rollback action should include logging mechanisms to record the rollback process, ensuring traceability and auditing capabilities.
The criteria for triggering the rollback action should be clearly defined based on the post-upgrade verification results. For instance, if a critical system component fails the post-upgrade health check, the rollback action is automatically initiated.
Advanced Techniques and Optimization
Taking our BigFix-driven Windows in-place upgrades to the next level involves leveraging its advanced capabilities for automation, optimization, and insightful reporting. This allows us to move beyond basic deployment and into a realm of highly efficient and predictable upgrade management, even across massive deployments.
This section delves into sophisticated strategies to refine your BigFix upgrade process, transforming it from a reactive measure into a proactive, streamlined operation. We’ll explore methods for automating image creation, optimizing deployment for large-scale scenarios, leveraging reporting for bottleneck identification, and comparing different patching strategies. Ultimately, we aim to uncover potential areas for ongoing improvement and continuous refinement of your BigFix upgrade workflow.
BigFix Automation of System Image Creation
Automating the creation of system images is crucial for consistent and repeatable deployments. BigFix can be integrated with tools like DISM to capture and manage these images. A well-defined BigFix action can automate the entire process, including the initial capture, subsequent modifications (such as adding specific applications or drivers), and finally, the deployment of the finalized image to target machines.
This ensures uniformity across the upgraded systems and significantly reduces manual intervention, minimizing the risk of human error. For instance, a BigFix action could trigger the DISM command to capture a reference image from a clean, patched system, then subsequent actions could apply necessary updates and configurations before finally packaging the image for deployment via a separate BigFix task.
Optimizing BigFix Deployment for Large-Scale Upgrades
Scaling BigFix deployments for thousands of machines requires careful planning and optimization. This involves techniques like phased rollouts, leveraging BigFix’s relevance capabilities for granular control over target selection, and utilizing multiple deployment relays to distribute the workload. Prioritization based on factors like criticality or business impact allows for a controlled upgrade process. For example, a phased rollout might target a small pilot group initially, followed by larger departmental segments, and finally, the entire organization.
Careful monitoring of resource utilization on both the BigFix server and client machines is essential to prevent bottlenecks and ensure timely upgrades.
Leveraging BigFix Reporting to Identify Upgrade Bottlenecks
BigFix’s robust reporting features provide invaluable insights into the upgrade process. By analyzing the data, we can pinpoint common failure points, slowdowns, and resource constraints. Custom reports can be generated to highlight machines requiring attention, identify specific error codes, and track overall upgrade progress. This data-driven approach allows for proactive problem-solving, minimizing downtime and ensuring a smooth upgrade process.
For example, a report focusing on failed upgrades could highlight specific error messages, revealing common issues like insufficient disk space or driver conflicts. This allows IT administrators to proactively address these issues before they impact a larger number of machines.
Comparing BigFix Patching Strategies for Pre- and Post-Upgrade
Choosing the right patching strategy is crucial for both pre- and post-upgrade phases. Pre-upgrade patching ensures a stable base image, minimizing conflicts during the upgrade process. Post-upgrade patching addresses any vulnerabilities or updates missed during the initial upgrade. BigFix allows for flexible patching strategies, such as deploying critical updates before the upgrade, then applying remaining updates after the upgrade is complete.
This segmented approach reduces the overall upgrade time and minimizes the risk of complications. For instance, pre-upgrade patching could focus on critical security updates and driver updates, while post-upgrade patching can incorporate optional updates and feature enhancements.
Potential Areas for Improvement in the BigFix-Managed Upgrade Process
Continuous improvement is key. Regularly reviewing the upgrade process, analyzing reports, and soliciting feedback from end-users identifies areas for refinement. This might involve optimizing BigFix actions for speed, refining the relevance criteria for target selection, or improving error handling and reporting. Proactive monitoring and automated alerts can also enhance the process. For example, identifying and addressing slow upgrade times on specific machine models or operating systems could lead to the development of more targeted upgrade strategies.
This iterative approach ensures that the BigFix-managed upgrade process remains efficient and effective.
Troubleshooting Common Issues
Even with careful planning, BigFix in-place Windows upgrades can encounter unexpected hurdles. This section provides solutions to common problems and strategies for effective troubleshooting. Understanding the potential pitfalls and how to address them is crucial for a smooth and successful upgrade process.
Common BigFix Upgrade Errors and Solutions
This section details some frequent errors encountered during BigFix-managed Windows in-place upgrades and their corresponding solutions. Addressing these issues promptly minimizes downtime and ensures a successful deployment.
| Error | Possible Cause | Solution |
|---|---|---|
| Upgrade Failure: Error Code 0x80070002 | Insufficient disk space, file system corruption, or permission issues. | Check disk space, run CHKDSK, and verify appropriate permissions for the BigFix client and upgrade files. Ensure the target drive has ample free space (at least twice the size of the OS installation). |
| Upgrade hangs at a specific percentage. | Driver incompatibility, resource contention, or a faulty installation file. | Review the BigFix logs for clues. Try restarting the machine. If the issue persists, investigate potential driver conflicts or replace the upgrade installation files. Consider a clean boot to minimize resource contention. |
| Upgrade rollback occurs. | Critical error during the upgrade process, possibly due to hardware failure or software conflict. | Analyze the BigFix logs and Windows event logs for detailed error messages. Check system logs for hardware errors. If a specific application is suspected, temporarily disable it and retry the upgrade. |
| BigFix reports a failure, but the upgrade appears successful. | A problem with the BigFix reporting mechanism, not the upgrade itself. | Check the BigFix console for any misconfigurations in reporting. Verify the upgrade’s success manually by checking the OS version. Consider adjusting the BigFix reporting settings. |
Application Compatibility Issues
Application compatibility is a major concern during in-place upgrades. This section Artikels strategies for addressing application compatibility problems.Many applications may not be compatible with the new Windows version. Pre-upgrade testing is essential to identify potential conflicts. Creating a comprehensive compatibility matrix helps prioritize applications for testing. Tools like the Application Compatibility Toolkit (ACT) can assist in assessing application compatibility before deploying the upgrade.
If compatibility issues are discovered, consider upgrading applicationsbefore* the OS upgrade or deploying compatibility fixes. For critical applications without readily available updates, virtual machine testing can provide a safe environment for compatibility assessments.
Effective Error Handling in BigFix Actions
BigFix actions can incorporate robust error handling to improve the reliability of the upgrade process. This involves using appropriate error codes and logging mechanisms to track issues.
Example: A BigFix action could check the return code of the upgrade executable. If the return code indicates failure, the action can log the error, send notifications, and potentially trigger remediation steps (like rollback or restarting the upgrade).
Diagnosing Upgrade Failures Using BigFix Logs
BigFix logs are invaluable for troubleshooting upgrade failures. These logs provide detailed information about the upgrade process, including any errors encountered. Locating relevant logs requires understanding the BigFix logging architecture.The BigFix client logs typically reside in the client’s log directory (the location varies depending on the BigFix client version and operating system). The logs contain timestamps, error codes, and detailed descriptions of events.
Analyzing these logs often reveals the root cause of the upgrade failure. Using log analysis tools or searching for specific error messages can streamline the troubleshooting process.
Frequently Asked Questions (FAQ) Regarding BigFix Upgrades
Addressing common questions proactively can significantly reduce support requests. This section answers some frequently asked questions about BigFix-managed Windows in-place upgrades.
- Q: What is the best way to prepare for a BigFix in-place upgrade? A: Thorough pre-upgrade testing, application compatibility assessments, and sufficient disk space are crucial preparations.
- Q: How can I minimize downtime during the upgrade? A: Scheduling upgrades during off-peak hours, utilizing efficient BigFix actions, and robust error handling are key to minimizing downtime.
- Q: What should I do if the upgrade fails? A: Analyze BigFix and Windows event logs, check disk space and permissions, and consider potential driver or application conflicts.
- Q: How can I ensure data integrity during the upgrade? A: Regularly backing up critical data before initiating the upgrade process is crucial.
- Q: How can I monitor the upgrade progress? A: BigFix provides real-time monitoring capabilities, allowing administrators to track the progress of upgrades across multiple machines.
Final Review
Simplifying in-place Windows upgrades using BigFix isn’t just about saving time; it’s about minimizing disruption and ensuring a seamless transition for your entire organization. By leveraging BigFix’s automation capabilities and following the best practices Artikeld here, you can transform your upgrade process from a source of anxiety into a well-oiled machine. Remember to utilize the pre-upgrade checks, meticulously manage dependencies, and thoroughly verify the post-upgrade status.
With careful planning and execution, you can confidently upgrade your Windows environment with minimal downtime and maximum efficiency. Happy upgrading!
FAQ Guide
What if BigFix detects a critical incompatibility during the pre-upgrade checks?
BigFix will halt the upgrade process and alert you to the specific incompatibility. You can then address the issue before proceeding. This prevents potentially disastrous outcomes.
How does BigFix handle user data during an in-place upgrade?
BigFix itself doesn’t directly handle user data. The in-place upgrade process managed by BigFix maintains user data as part of the standard Windows upgrade process. However, it’s crucial to back up important data before any upgrade, regardless of the method used.
Can BigFix be used to upgrade different versions of Windows simultaneously?
Yes, BigFix allows for targeted deployments. You can create separate actions and relevance statements to target specific Windows versions, enabling simultaneous upgrades across different versions within your environment.
What are the minimum system requirements for BigFix to manage Windows upgrades effectively?
The minimum requirements depend on the scale of your deployment and the complexity of your actions. Generally, a reasonably powerful server with sufficient memory and network bandwidth is recommended. Consult the official BigFix documentation for precise requirements.