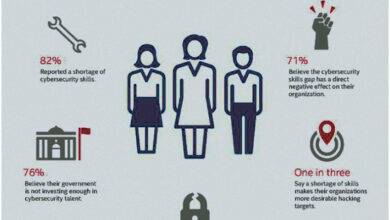
Ascension Suffers Cyber Attack
Ascension suffers cyber attack – that’s the headline that’s been making waves, and frankly, it’s terrifying. We’re talking about a major breach, potentially impacting everything from financial records to sensitive customer data. The sheer scale of the potential damage is staggering, and the questions surrounding the attack’s nature and motives are only just beginning to be answered.
This post dives into the details, exploring the immediate fallout, long-term consequences, and what needs to happen to prevent future incidents.
The attack itself could range from a simple data breach to a sophisticated ransomware campaign, potentially crippling Ascension’s operations. The impact on its reputation, customer trust, and overall financial stability could be devastating. We’ll look at the various types of attacks, the vulnerabilities exploited, and how Ascension’s response will shape its future.
The Nature of the Attack on Ascension
The recent cyberattack on Ascension, while thankfully addressed, highlights the critical vulnerabilities inherent in even the most robust healthcare systems. The potential consequences of such an attack extend far beyond simple data breaches, impacting patient care, operational efficiency, and the overall reputation of the organization. Understanding the nature of this attack, and the potential for future incidents, is crucial for improving security measures and ensuring patient safety.The multifaceted nature of modern cyberattacks means Ascension could have been targeted in numerous ways.
This isn’t simply a case of a single vulnerability being exploited; a sophisticated attack could involve a combination of techniques.
Types of Cyberattacks Targeting Ascension
A successful attack against Ascension could have involved several methods. Ransomware, designed to encrypt sensitive data and demand payment for its release, is a common threat to healthcare providers. This could cripple Ascension’s operations, delaying patient care and potentially jeopardizing lives. Data breaches, resulting from phishing scams or exploited vulnerabilities, could expose protected health information (PHI), leading to significant legal and financial penalties, as well as reputational damage.
Denial-of-service (DoS) attacks could overwhelm Ascension’s systems, rendering them inaccessible and disrupting critical services. Finally, more insidious attacks, such as supply chain attacks targeting vendors, could provide a backdoor into Ascension’s network.
Motives Behind the Attack
The motives behind a cyberattack on Ascension could be varied and complex. Financially motivated attacks, such as ransomware deployments, are prevalent. However, attacks could also be driven by espionage, aiming to steal intellectual property or sensitive patient data for illicit purposes. State-sponsored actors might target Ascension to disrupt healthcare services or gain access to sensitive government information if Ascension handles data related to government programs.
Finally, activist groups might target the organization to protest specific policies or practices. The complexity of motives underscores the need for a multi-layered security approach.
Vulnerabilities Compared to Similar Organizations
Ascension, like other large healthcare providers, faces similar vulnerabilities. The reliance on interconnected systems, the sheer volume of sensitive data handled, and the often-complex IT infrastructure create a large attack surface. However, the specific vulnerabilities might differ based on Ascension’s unique technological landscape and security protocols. A comparison with similar organizations requires a detailed analysis of their individual security postures, including the types of security technologies deployed, employee training programs, and incident response plans.
The lack of publicly available, detailed security audits for most healthcare providers makes a direct comparison challenging. However, industry reports and news articles frequently highlight common vulnerabilities like outdated software, weak passwords, and insufficient employee training as contributing factors in successful attacks against healthcare organizations. The impact of a successful attack would likely be similar across large healthcare providers, resulting in significant disruption and financial losses.
Immediate Consequences and Response
A successful cyberattack on a company like Ascension, a large healthcare provider, would have devastating and far-reaching consequences. The immediate impact would ripple across various aspects of the business, demanding a swift and coordinated response to minimize damage and restore operations. Understanding these immediate consequences and having a robust response plan in place is crucial for survival and maintaining public trust.
Immediate Impacts of a Cyberattack on Ascension
The following table illustrates the immediate consequences of a successful cyberattack on Ascension, categorized by its impact on different business aspects. These impacts are not mutually exclusive; they often intertwine and amplify each other. For example, operational disruptions can lead to significant financial losses and reputational damage.
| Aspect | Immediate Impact | Example | Severity |
|---|---|---|---|
| Financial | Loss of revenue, increased operational costs (e.g., incident response, remediation, legal fees), potential fines and penalties (e.g., HIPAA violations), insurance claims | Loss of access to billing systems resulting in delayed payments and potential loss of millions in revenue. Costs associated with hiring cybersecurity experts and legal counsel could run into hundreds of thousands. | High |
| Operational | Disruption of services (e.g., patient care, administrative functions), data loss or corruption, system downtime, inability to access critical information | Inability to access electronic health records, delaying patient care and potentially causing harm. Disruption of appointment scheduling leading to lost appointments and frustrated patients. | Critical |
| Reputational | Loss of public trust, damage to brand image, negative media coverage, decreased patient confidence, potential loss of investors | Negative news reports highlighting data breaches and patient privacy violations could lead to a significant drop in patient volume and investor confidence. This could be further exacerbated by social media commentary. | High |
| Legal and Regulatory | Investigations by regulatory bodies (e.g., HIPAA, FTC), lawsuits from affected patients, potential criminal charges | Investigations from the Office for Civil Rights (OCR) for HIPAA violations, leading to significant fines and reputational damage. Class-action lawsuits from patients whose data was compromised. | High |
Ascension’s Initial Response Plan
A comprehensive initial response plan is paramount. This plan should be tested and updated regularly to ensure its effectiveness. The plan should be activated immediately upon detection of a cyberattack. Key elements include:
First, containment is key. This involves isolating affected systems to prevent further spread of the attack. This might involve disconnecting affected networks or servers from the internet. Simultaneously, damage assessment begins, identifying the scope and extent of the breach, including what data has been compromised and the potential impact.
Next, evidence preservation is critical for legal and regulatory compliance. This involves securing all relevant logs, data, and system information to support investigations and potential legal proceedings. This is a legally mandated step for healthcare providers.
Finally, restoration of systems and data begins, prioritizing critical systems and data first. This may involve restoring from backups, rebuilding systems, and implementing enhanced security measures. Throughout this process, continuous monitoring is crucial to detect any further malicious activity.
Effective Communication Strategies
Open and transparent communication is essential during a cyberattack. Ascension needs a clear communication plan outlining how and when to inform various stakeholders. This includes:
Internal communication should keep employees informed about the situation, their roles in the response, and the company’s efforts to resolve the issue. This helps maintain morale and ensures everyone is working together effectively. Regular updates, clear instructions, and accessible resources are crucial.
External communication should focus on transparency and empathy. Ascension should promptly notify affected patients and other stakeholders about the breach, explaining what happened, what data was compromised, and what steps are being taken to mitigate the damage. This should include clear instructions on what steps patients should take to protect themselves. This could involve using a dedicated website, press releases, and direct communication with affected individuals.
The goal is to build trust and minimize negative impacts. Examples of effective communication include providing regular updates on the incident response, offering credit monitoring services to affected individuals, and establishing a dedicated point of contact for inquiries.
Long-Term Effects and Recovery
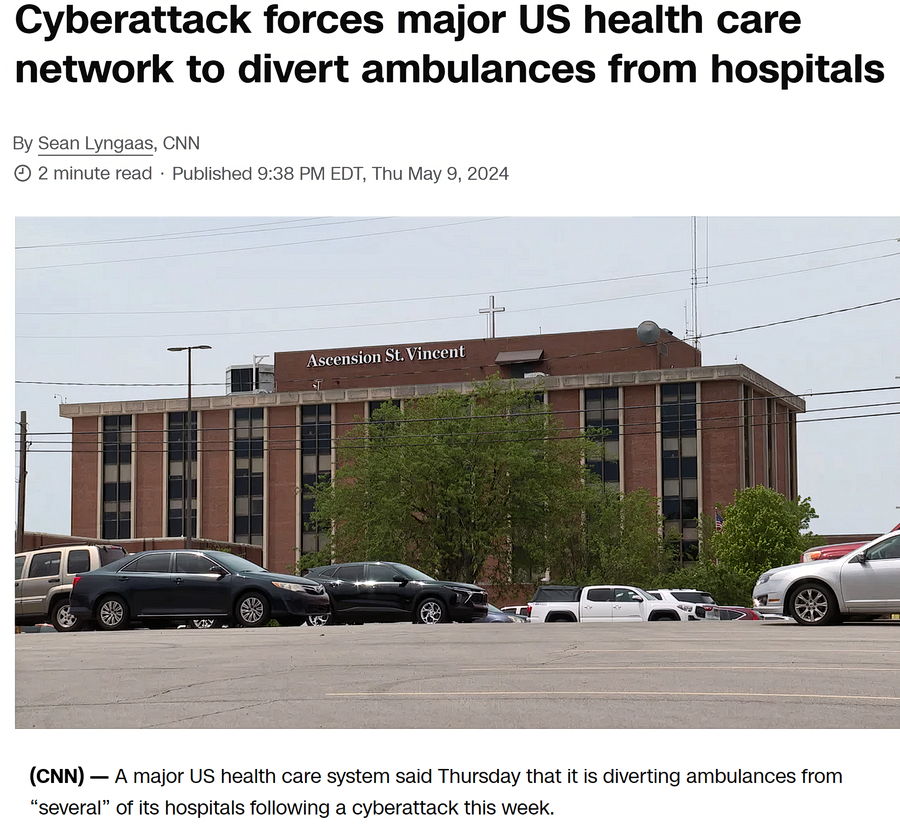
The cyberattack on Ascension will undoubtedly leave a lasting impact, extending far beyond the immediate disruption of services. The long-term effects will ripple through its reputation, market standing, and financial health, demanding a comprehensive and meticulously planned recovery. Addressing these challenges requires a multifaceted approach focusing on rebuilding trust, restoring operational efficiency, and strengthening security infrastructure.The potential long-term effects on Ascension’s reputation and market position are significant.
A loss of customer confidence, fueled by negative media coverage and the perception of inadequate security measures, could lead to decreased market share and reduced profitability. Competitors might capitalize on this vulnerability, attracting Ascension’s clients with promises of superior security and reliability. The financial repercussions could be substantial, encompassing legal fees, regulatory fines, and the costs associated with remediation and enhanced security measures.
Furthermore, the damage to brand image could take years to repair, even with a successful recovery. Consider the case of Target, whose 2013 data breach resulted in long-term reputational damage and significant financial losses despite their efforts to address the issue.
Reputational Repair and Trust Rebuilding
Rebuilding trust with customers and stakeholders is paramount. This involves transparent communication about the attack, the steps taken to mitigate the damage, and the measures implemented to prevent future incidents. Ascension should proactively engage with affected customers, offering support and compensation where appropriate. A public apology acknowledging the shortcomings and outlining the company’s commitment to improved security is crucial.
Furthermore, investing in independent security audits to demonstrate a commitment to enhanced security practices will build confidence. Transparency and proactive communication are key; consider how companies like Equifax handled (or mishandled) their data breach—their response significantly impacted their long-term reputation.
System Restoration and Operational Recovery
A phased approach to system restoration is essential. This begins with securing the affected systems, eradicating malware, and restoring data from backups. Next, critical systems should be brought back online, followed by a gradual restoration of less essential services. Rigorous testing and validation are necessary at each stage to ensure stability and security. Parallel to system restoration, Ascension needs to develop and implement improved security protocols, including enhanced network security, intrusion detection systems, and employee security awareness training.
This requires significant investment in technology and expertise. For example, a phased restoration might prioritize customer-facing websites and critical internal systems before moving to less urgent applications.
Resource Allocation for Recovery
A successful recovery necessitates a substantial allocation of resources. This includes:
- Human Resources: A dedicated team of cybersecurity experts, IT specialists, public relations professionals, and legal counsel will be required to manage the recovery effort.
- Technological Resources: Investment in new security technologies, data recovery tools, and system upgrades will be necessary. This may include cloud-based solutions for enhanced resilience and disaster recovery.
- Financial Resources: Significant funding will be required to cover the costs of system restoration, legal fees, regulatory fines, customer compensation, and enhanced security measures. Securing additional funding through insurance claims or lines of credit might be necessary.
Preventive Measures and Security Enhancements
The Ascension cyberattack underscores the critical need for proactive security measures. A reactive approach, focused solely on damage control after an attack, is insufficient. A robust, multi-layered security strategy is essential to prevent future incidents and minimize the impact of any successful breaches. This requires a shift from simply reacting to threats to actively anticipating and mitigating them.Proactive security measures are not merely a cost; they are an investment in the long-term health and stability of the organization.
The financial and reputational damage caused by a successful cyberattack far outweighs the cost of implementing and maintaining comprehensive security protocols. Furthermore, a strong security posture fosters trust with patients, partners, and investors, reinforcing Ascension’s commitment to data protection.
Multi-Factor Authentication Implementation
Ascension should mandate multi-factor authentication (MFA) across all systems and accounts. MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password, a one-time code from a mobile app, or a biometric scan, before gaining access. This significantly reduces the risk of unauthorized access, even if credentials are compromised. For example, even if an attacker obtains an employee’s password through phishing, they will still be unable to access the account without the second authentication factor.
Enhanced Network Security
Strengthening network security involves several key enhancements. This includes implementing robust firewalls to filter malicious traffic, intrusion detection and prevention systems (IDPS) to monitor network activity and block suspicious behavior, and regular security patching to address known vulnerabilities in software and operating systems. Regular updates to antivirus and anti-malware software on all devices are also crucial. A well-defined network segmentation strategy can also limit the impact of a breach by isolating critical systems from less sensitive ones.
For instance, isolating patient data networks from administrative networks minimizes the potential for widespread compromise in case of a breach in one segment.
Regular Security Audits and Penetration Testing
Regular security audits provide a systematic review of an organization’s security posture. These audits identify weaknesses and vulnerabilities in systems, processes, and employee practices. Penetration testing, on the other hand, simulates real-world cyberattacks to assess the effectiveness of existing security controls and identify exploitable vulnerabilities. A combination of both, performed by independent security experts, offers a comprehensive evaluation of Ascension’s security defenses.
For example, a penetration test might reveal a weakness in a web application that could allow attackers to gain unauthorized access to sensitive data. A subsequent security audit would then assess the organization’s processes for addressing such vulnerabilities.
Employee Security Awareness Training
It’s crucial to equip employees with the knowledge and skills to recognize and respond to cyber threats. This requires ongoing, comprehensive security awareness training.
- Regular phishing simulations to train employees to identify and report suspicious emails.
- Training on password security best practices, including the use of strong, unique passwords and password managers.
- Education on social engineering tactics and how to avoid becoming victims of scams.
- Guidance on safe internet browsing practices, including avoiding suspicious websites and downloads.
- Instructions on how to report security incidents promptly and correctly.
- Regular updates on emerging cyber threats and best practices.
Legal and Regulatory Implications: Ascension Suffers Cyber Attack
A cyberattack on an organization like Ascension, a large healthcare provider, triggers a cascade of legal and regulatory ramifications, extending far beyond simple IT remediation. Understanding these implications is crucial for effective response and long-term recovery, impacting not only the organization’s financial stability but also its reputation and public trust. Failure to comply with relevant regulations can lead to substantial fines, legal battles, and lasting damage to the organization’s image.The legal landscape surrounding data breaches is complex and varies depending on the jurisdiction and the type of data compromised.
Ascension must navigate a multitude of federal and state laws, as well as industry-specific regulations, to ensure compliance. This includes not only immediate responses to the attack itself but also long-term measures to prevent future incidents and mitigate the impact of any residual vulnerabilities. The potential for legal action from affected individuals, regulatory bodies, and even business partners is significant, demanding a proactive and comprehensive approach.
Data Breach Notification Laws
Ascension is obligated to comply with various state and federal data breach notification laws. These laws mandate that individuals whose protected health information (PHI) has been compromised be notified within a specific timeframe. Failure to comply with these notification requirements can result in significant penalties. For instance, some states impose per-record penalties, while others levy fines based on the nature and extent of the breach.
The notification process itself requires careful planning and execution to ensure accuracy and compliance across all affected jurisdictions. This often involves coordinating with legal counsel and utilizing specialized breach notification services. The specific requirements vary widely; for example, California’s CCPA (California Consumer Privacy Act) differs significantly from HIPAA (Health Insurance Portability and Accountability Act) in its notification requirements and scope of affected data.
HIPAA Compliance
As a healthcare provider, Ascension is subject to the Health Insurance Portability and Accountability Act (HIPAA). HIPAA regulations dictate stringent security measures to protect the privacy and security of protected health information (PHI). A cyberattack that results in a breach of PHI can trigger investigations by the Office for Civil Rights (OCR), potentially leading to substantial fines and corrective action plans.
HIPAA violations can range from minor administrative failures to severe security breaches, each carrying its own set of penalties. The OCR assesses the severity of the violation based on factors such as the organization’s preparedness, the number of individuals affected, and the extent of the harm caused. Examples of significant HIPAA violations include failing to implement appropriate safeguards, inadequate employee training, and delayed breach notification.
Potential Legal Ramifications for Ascension and its Executives
The legal ramifications extend beyond the organization itself. Executives and other responsible individuals within Ascension could face personal liability for failures in cybersecurity practices leading to the breach. This liability could include civil lawsuits from affected individuals, as well as potential criminal charges in cases of negligence or willful misconduct. Examples of such cases are numerous, with executives facing both financial penalties and reputational damage.
Adequate cybersecurity insurance and a robust incident response plan are crucial to mitigating these risks. The legal responsibility extends to demonstrating a reasonable level of care in protecting patient data, a standard that is constantly evolving with advancements in technology and cyber threats.
Best Practices for Data Privacy Compliance
Implementing robust data privacy best practices is paramount to minimizing legal risks. This includes regularly updating security protocols, conducting thorough risk assessments, and providing comprehensive employee training on data security. Implementing multi-factor authentication, data encryption, and intrusion detection systems are essential security measures. Regular security audits and penetration testing can help identify vulnerabilities before they can be exploited.
Hearing about the Ascension cyberattack got me thinking about security vulnerabilities in general. Building robust, secure applications is crucial, and that’s where learning about platforms like Domino and its approach to domino app dev the low code and pro code future becomes really important. After all, a strong foundation in development is key to preventing future attacks like the one Ascension suffered.
Furthermore, establishing clear incident response protocols and a dedicated security team are crucial for handling cyberattacks effectively and minimizing their legal consequences. Maintaining detailed records of security measures and incident responses is vital for demonstrating compliance during any legal proceedings. Proactive engagement with regulatory bodies can also significantly reduce the likelihood and severity of penalties in the event of a breach.
Illustrative Scenario: A Ransomware Attack

Let’s imagine a scenario where Ascension Healthcare, a large and complex healthcare system, falls victim to a sophisticated ransomware attack. This isn’t a far-fetched scenario; ransomware attacks on healthcare providers are sadly becoming increasingly common, driven by the high value of patient data and the potential for significant disruption.This hypothetical attack leverages a phishing email targeting Ascension’s IT department.
The email appears to be from a legitimate vendor, containing a malicious attachment disguised as an invoice. Once opened, the attachment silently deploys the ransomware, encrypting critical files across Ascension’s network.
Attack Vector and Initial Impact
The ransomware, a variant of Ryuk, known for its aggressive encryption and high ransom demands, quickly spreads through Ascension’s network. The initial infection point is a workstation in the IT department, but the malware exploits vulnerabilities in the network infrastructure – specifically, a lack of multi-factor authentication and outdated anti-malware software – to rapidly propagate. Within hours, numerous servers, workstations, and even medical devices are compromised, leading to a system-wide shutdown.
The ransomware displays a menacing message demanding a substantial Bitcoin payment for decryption. Patient data, medical records, administrative files, and even operational systems are inaccessible.
Visual Representation of the Attack’s Spread
Imagine a network diagram showing Ascension’s IT infrastructure: interconnected servers, workstations, and medical devices represented by nodes. From the initially infected workstation (a red node), thick red lines radiate outward, representing the ransomware’s spread. These lines branch out, infecting various departments—patient records (blue nodes), billing (green nodes), administrative systems (yellow nodes), and even critical medical devices (purple nodes).
The intensity of the red lines would visually depict the speed and extent of encryption, with some areas (like the server room) becoming intensely red, indicating a high concentration of infected systems. This visual would clearly demonstrate the rapid and widespread impact of the attack.
Data Integrity and Recovery, Ascension suffers cyber attack
The ransomware’s encryption renders a significant portion of Ascension’s data inaccessible. The immediate impact is the inability to access patient records, delaying or preventing treatment. Billing systems are crippled, halting revenue streams. Internal communications are disrupted, impacting staff coordination. The recovery process involves several crucial steps: first, isolating infected systems to prevent further spread.
Second, engaging a specialized cybersecurity firm with experience in ransomware recovery. Third, carefully evaluating the feasibility of paying the ransom (a risky proposition with no guarantee of data recovery). Fourth, implementing a robust data recovery strategy, utilizing backups (if available and unencrypted) and potentially employing data recovery specialists to attempt decryption. Finally, a thorough forensic investigation is conducted to identify vulnerabilities and prevent future attacks.
The recovery period could span weeks, even months, depending on the extent of the encryption and the availability of reliable backups. The potential financial and reputational damage is immense. Data loss, even partial, could lead to regulatory fines and lawsuits, while the disruption of services can severely damage public trust.
Ending Remarks

The Ascension cyberattack serves as a stark reminder of the ever-present threat facing even the most secure organizations. While the full extent of the damage may not be known for some time, the incident highlights the critical need for robust cybersecurity measures, proactive threat detection, and comprehensive incident response plans. The lessons learned from this breach will undoubtedly shape future cybersecurity strategies across numerous industries, pushing for more sophisticated defenses and a heightened awareness of the ever-evolving landscape of cyber threats.
Let’s hope this incident prompts significant changes and improvements in cybersecurity practices for everyone.
Questions Often Asked
What type of data might have been compromised in the Ascension cyberattack?
That information hasn’t been officially released yet. The nature of the stolen data will likely depend on the specific type of attack and the systems targeted. It could include anything from customer personal information to financial records and internal business documents.
Who is responsible for the attack on Ascension?
Currently, the perpetrators remain unknown. Investigations are underway, and it may take time to identify and apprehend those responsible. The motives behind the attack are also still unclear.
What is Ascension doing to prevent future attacks?
While specifics haven’t been publicly released, it’s safe to assume Ascension is undertaking a thorough review of its security infrastructure, implementing new safeguards, and strengthening its defenses against future attacks. This likely includes enhanced security protocols, employee training, and regular security audits.