Assessing Critical Cyber Risks with UpGuard
Assessing critical cyber risks with UpGuard is more than just a security audit; it’s a proactive strategy to safeguard your digital assets. This post dives deep into how UpGuard’s powerful features help identify, prioritize, and mitigate critical vulnerabilities, transforming your cybersecurity posture from reactive to resilient. We’ll explore its functionality, compare it to other platforms, and even walk through practical examples of how to use UpGuard’s data to build a robust risk mitigation plan.
From understanding UpGuard’s vulnerability scanning process to mastering the art of interpreting its reports, this guide provides a comprehensive overview for anyone seeking to bolster their organization’s cyber defenses. We’ll uncover how to leverage UpGuard’s insights to create compelling reports for stakeholders, and share real-world scenarios showcasing the effectiveness of UpGuard in action. Get ready to transform your approach to cybersecurity!
UpGuard’s Functionality in Cyber Risk Assessment

UpGuard is a powerful platform for identifying and mitigating critical cyber risks. It goes beyond basic vulnerability scanning, offering a comprehensive view of an organization’s external attack surface and providing actionable insights to improve security posture. This deep dive explores UpGuard’s core features, integration process, comparative analysis with competitors, and a practical guide to using its vulnerability scanning capabilities.
UpGuard’s Core Features for Critical Cyber Risk Identification
UpGuard leverages a combination of automated scanning, threat intelligence, and human expertise to identify critical cyber risks. Its core features include automated vulnerability scanning of exposed assets, third-party risk assessment (identifying weaknesses in vendor networks), monitoring for data breaches and leaks, and providing detailed reports with remediation advice. The platform’s strength lies in its ability to correlate various data points to provide a holistic understanding of an organization’s risk profile, rather than just presenting a list of vulnerabilities.
This allows security teams to prioritize remediation efforts based on actual impact and likelihood.
Integrating UpGuard into an Existing Security Infrastructure
Integrating UpGuard typically involves configuring API connections to existing security information and event management (SIEM) systems or other security tools. This enables automated data sharing and centralized monitoring. The platform offers various integration options, including APIs, scheduled reports, and direct data imports. The specific integration process will depend on the existing infrastructure and the desired level of integration.
A dedicated UpGuard onboarding team often assists with this process, guiding users through the setup and configuration to ensure seamless data flow and effective monitoring. For example, integrating with a SIEM system allows for the automated import of UpGuard’s vulnerability scan results, enriching the existing security data and triggering alerts based on predefined thresholds.
Comparison of UpGuard with Other Leading Cyber Risk Assessment Platforms
UpGuard differentiates itself from other platforms through its comprehensive approach to external risk assessment. While platforms like Rapid7 InsightVM and Tenable.io focus primarily on vulnerability scanning, UpGuard incorporates threat intelligence, third-party risk management, and breach monitoring. This holistic approach provides a more complete picture of an organization’s overall risk exposure. However, direct feature-by-feature comparisons are difficult because the specific strengths and weaknesses vary depending on the specific needs and priorities of an organization.
For example, some organizations may prioritize in-depth vulnerability analysis offered by platforms like Nessus, while others might value the broader external risk visibility provided by UpGuard.
Step-by-Step Guide on Using UpGuard for Vulnerability Scanning
1. Account Setup and Configuration
Create an UpGuard account and configure the necessary settings, including defining the scope of the scan (e.g., specific domains or IP addresses).
2. Asset Discovery
UpGuard automatically discovers assets associated with the specified domains or IP addresses.
3. Vulnerability Scan Initiation
Initiate the vulnerability scan. This process typically involves automated crawling and analysis of the discovered assets.
4. Report Generation and Review
Once the scan is complete, UpGuard generates a detailed report outlining identified vulnerabilities, their severity, and remediation recommendations.
5. Remediation and Monitoring
Address the identified vulnerabilities based on their severity and the provided recommendations. Continuously monitor for new vulnerabilities and re-scan regularly to ensure ongoing security.
UpGuard Pricing Tiers and Features
| Tier | Price (USD/month – example) | Key Features | Suitable For |
|---|---|---|---|
| Basic | $XXX | Basic vulnerability scanning, limited asset discovery, basic reporting | Small businesses with limited IT resources |
| Standard | $YYY | Comprehensive vulnerability scanning, advanced asset discovery, detailed reporting, third-party risk assessment (limited) | Mid-sized businesses with moderate security needs |
| Enterprise | $ZZZ | All features of Standard, plus advanced threat intelligence, breach monitoring, dedicated support, custom reporting | Large enterprises with complex security requirements |
| Custom | Contact Sales | Highly customized solutions tailored to specific needs | Organizations with unique security challenges |
Note
Pricing is illustrative and subject to change. Contact UpGuard directly for current pricing information.*
Identifying Critical Vulnerabilities with UpGuard: Assessing Critical Cyber Risks With Upguard

UpGuard is a powerful tool for identifying and prioritizing critical vulnerabilities within your organization’s digital footprint. Its comprehensive scanning capabilities go beyond basic vulnerability assessments, offering a holistic view of your security posture and the risks posed by third-party vendors. This allows for proactive mitigation of potential breaches before they can impact your business.UpGuard’s ability to detect a wide range of critical vulnerabilities is a key advantage.
It leverages various data sources and advanced technologies to identify potential weaknesses in your systems and applications.
Examples of Critical Vulnerabilities Detected by UpGuard
UpGuard can detect a wide array of critical vulnerabilities, including outdated software versions (like unpatched versions of Apache Struts or Log4j), exposed databases with sensitive data, misconfigured cloud storage buckets leaking sensitive files, and weak or default passwords. For example, UpGuard might flag a server running an outdated version of WordPress, which is known to be vulnerable to various exploits, including SQL injection and cross-site scripting (XSS) attacks.
Another example would be the detection of an unsecured Amazon S3 bucket containing customer Personally Identifiable Information (PII). These are just a few examples; the platform’s breadth of detection capabilities covers many more potential threats.
UpGuard’s Vulnerability Prioritization
UpGuard prioritizes vulnerabilities based on a combination of severity and impact. Severity is determined by factors such as the potential for exploitation and the damage that could result. Impact considers the sensitivity of the data at risk and the potential business disruption a successful attack could cause. This prioritization system ensures that the most critical vulnerabilities are addressed first, maximizing the effectiveness of remediation efforts.
A vulnerability with a high severity score and a high impact score (e.g., exposed database containing customer PII) would be ranked higher than a vulnerability with a low severity score and low impact score (e.g., a minor bug in a rarely used internal application).
Workflow for Using UpGuard Vulnerability Reports
A typical workflow for using UpGuard’s vulnerability reports to inform remediation strategies begins with regular scanning of your assets. Following the scan, you receive a detailed report that lists identified vulnerabilities, categorized by severity and impact. Next, your security team prioritizes vulnerabilities based on UpGuard’s scoring and your organization’s risk tolerance. Then, remediation plans are developed and implemented, with progress tracked and verified through subsequent scans.
Finally, the effectiveness of the remediation efforts is assessed. This iterative process ensures ongoing protection against emerging threats.
UpGuard’s Role in Identifying Third-Party Risks
UpGuard plays a crucial role in identifying third-party risks by assessing the security posture of your vendors and partners. The platform can scan their publicly accessible assets for vulnerabilities and misconfigurations, providing insights into their security practices. This information allows you to make informed decisions about vendor selection and manage the risks associated with third-party relationships. For example, if a critical vendor has a history of data breaches or exhibits poor security practices, UpGuard can help you identify these risks and take appropriate actions, such as negotiating improved security measures or finding alternative vendors.
Best Practices for Interpreting UpGuard Vulnerability Reports
To effectively interpret UpGuard’s vulnerability reports, several best practices should be followed. First, understand the scoring system used to prioritize vulnerabilities. Second, correlate findings with your organization’s risk profile. Third, validate findings with additional investigation to ensure accuracy and avoid false positives. Fourth, develop and implement remediation plans based on prioritized vulnerabilities.
Finally, regularly monitor your assets for new vulnerabilities and update your security measures accordingly. This approach ensures that your organization’s security posture is continuously improved and that critical vulnerabilities are addressed promptly.
Mitigating Risks Identified by UpGuard
UpGuard provides a wealth of data on your organization’s cybersecurity posture. The real value, however, lies in translating this data into actionable steps to mitigate identified risks. This involves developing a comprehensive risk mitigation plan, prioritizing remediation efforts, and tracking the effectiveness of your interventions. A well-defined process ensures that you address the most critical vulnerabilities first, minimizing your exposure to cyber threats.
A robust mitigation plan uses UpGuard’s findings to create a prioritized list of vulnerabilities, outlining remediation strategies, assigning responsibilities, and setting deadlines. It should also incorporate regular review cycles to assess the effectiveness of implemented controls and adapt to evolving threats. UpGuard’s data allows for precise tracking of progress and the identification of areas needing further attention.
Remediation Processes for Different Vulnerability Types
UpGuard identifies various vulnerability types, each requiring a specific remediation approach. For example, a discovered outdated software version might require an immediate update to the latest patch. This update should follow the vendor’s recommended procedures and include rigorous testing to ensure functionality and compatibility. Similarly, misconfigured cloud storage, often highlighted by UpGuard, needs immediate attention, perhaps involving tightening access controls, implementing multi-factor authentication, or encrypting sensitive data.
Unpatched servers represent a significant risk, requiring immediate patching and, potentially, vulnerability scanning to ensure complete remediation. Each vulnerability requires a tailored approach based on its severity and potential impact.
So, I’ve been diving deep into assessing critical cyber risks using UpGuard lately – it’s a game-changer. The speed and efficiency are amazing, but it made me think about the security implications of rapid application development. This is especially relevant when considering the future of app development, as highlighted in this great article on domino app dev, the low-code and pro-code future , and how it impacts vulnerability management.
Ultimately, understanding these development trends is crucial for effectively using tools like UpGuard to stay ahead of potential threats.
Key Metrics for Tracking Mitigation Effectiveness
Tracking the effectiveness of your risk mitigation efforts is crucial. UpGuard’s data allows for the monitoring of several key metrics. The number of high-severity vulnerabilities remediated over time provides a clear picture of progress. Similarly, tracking the reduction in your overall risk score, as calculated by UpGuard, demonstrates the overall impact of your mitigation activities. Analyzing the time taken to remediate vulnerabilities can highlight areas where processes need improvement.
Finally, monitoring the frequency of new vulnerabilities discovered after remediation efforts can reveal potential weaknesses in your security posture. Regular review of these metrics ensures continuous improvement.
Comparison of Mitigation Strategies
Different mitigation strategies exist for common vulnerabilities. Consider, for example, the vulnerability of exposed databases. One mitigation strategy involves implementing robust access controls, restricting access to authorized personnel only. Another involves encrypting sensitive data within the database, minimizing the impact of a potential breach. A third strategy could be migrating the database to a more secure cloud environment with enhanced security features.
The choice of strategy depends on factors like cost, complexity, and the specific sensitivity of the data. Similarly, SQL injection vulnerabilities can be mitigated through input validation, parameterized queries, and regular security audits. Each vulnerability demands a carefully considered and tailored approach.
Prioritization of Remediation Tasks, Assessing critical cyber risks with upguard
Prioritizing remediation tasks is essential to maximize efficiency and minimize risk. A decision-making flowchart can streamline this process.
Imagine a flowchart beginning with “Vulnerability Identified by UpGuard.” This leads to a decision point: “Is the vulnerability high-severity (critical or high)?” If yes, the path proceeds to “Immediate Remediation.” If no, the path moves to another decision point: “Is the vulnerability medium-severity?” If yes, the path goes to “Schedule Remediation within [timeframe].” If no, the path leads to “Low-Severity – Evaluate and Prioritize.” This final step involves a further assessment of the vulnerability’s potential impact and resources required for remediation.
This structured approach ensures that critical vulnerabilities receive immediate attention while other vulnerabilities are addressed systematically according to their risk level.
Case Studies
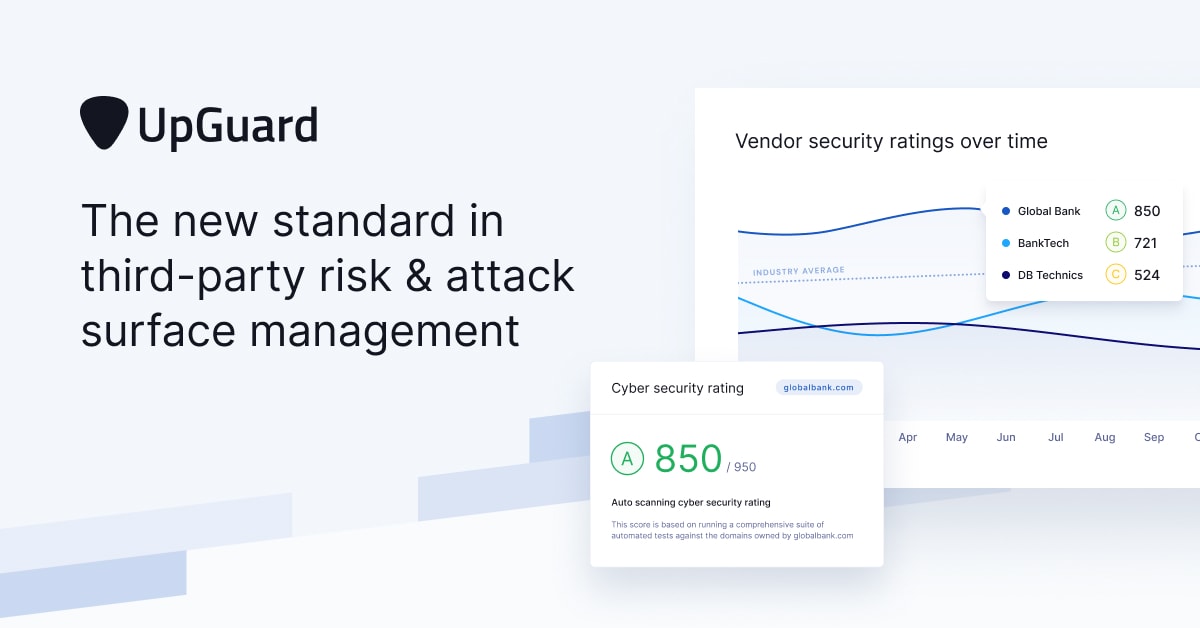
UpGuard’s effectiveness in identifying and mitigating cyber risks is best illustrated through real-world examples. The following case studies showcase how organizations of different sizes have leveraged UpGuard’s capabilities to strengthen their cybersecurity posture and prevent significant data breaches.
Hypothetical Scenario: UpGuard Prevents a Supply Chain Attack
Imagine a mid-sized manufacturing company, “Precision Parts,” heavily reliant on a third-party logistics provider for its supply chain. UpGuard’s continuous monitoring identified a critical vulnerability in the logistics provider’s network – an outdated and unpatched version of Apache Struts, known to be susceptible to remote code execution. This vulnerability could have allowed attackers to gain unauthorized access to Precision Parts’ sensitive data, including customer information, intellectual property, and financial records.
The potential impact included significant financial losses, reputational damage, legal liabilities, and operational disruptions. UpGuard’s alerts enabled Precision Parts to immediately engage with their logistics provider, urging them to update the vulnerable software. The swift remediation prevented a potential catastrophe.
Fictional Organization: Improving Cybersecurity Posture at “GreenTech Solutions”
GreenTech Solutions, a rapidly growing renewable energy company, implemented UpGuard to enhance its cybersecurity posture. UpGuard’s vulnerability scanning quickly identified several critical weaknesses, including exposed databases with default credentials, outdated software on several servers, and weak password policies across the organization. These vulnerabilities could have resulted in data breaches, unauthorized access to sensitive information, and potential service disruptions.
GreenTech Solutions addressed these issues proactively. They immediately changed default credentials, implemented a robust password management system enforcing strong passwords, and initiated a comprehensive software update schedule. UpGuard’s automated reporting and dashboards provided GreenTech Solutions with a clear overview of their security posture, enabling them to track progress and prioritize remediation efforts. Furthermore, UpGuard’s external attack surface management capabilities highlighted potential risks associated with shadow IT, leading GreenTech Solutions to implement stricter policies for managing and monitoring employee-owned devices.
Benefits of UpGuard for Various Organizations
The benefits of using UpGuard extend across various organizational types. The following points highlight its value proposition:
- Small Businesses: UpGuard provides cost-effective and scalable security solutions, enabling small businesses to protect themselves against cyber threats without significant upfront investment. The platform’s ease of use and automated reporting make it ideal for organizations with limited IT resources.
- Large Enterprises: UpGuard offers comprehensive visibility across complex IT environments, allowing large enterprises to effectively manage and mitigate risks across their entire attack surface. The platform’s integration capabilities streamline security operations and provide valuable insights for strategic decision-making.
- Government Agencies: UpGuard’s robust security capabilities help government agencies meet stringent compliance requirements and protect sensitive citizen data. The platform’s ability to continuously monitor for vulnerabilities and identify potential threats ensures a proactive approach to cybersecurity.
Final Conclusion
Ultimately, assessing critical cyber risks with UpGuard isn’t just about identifying vulnerabilities; it’s about building a culture of proactive security. By understanding how to leverage UpGuard’s comprehensive features – from vulnerability scanning and prioritization to reporting and mitigation – you can significantly reduce your organization’s risk profile. This isn’t just about patching holes; it’s about building a resilient system that can withstand future threats.
So, take the plunge, explore UpGuard’s capabilities, and embark on your journey towards a more secure digital future!
FAQ Guide
What types of organizations benefit most from using UpGuard?
UpGuard benefits organizations of all sizes, from small businesses to large enterprises and government agencies. Its scalability and comprehensive features make it adaptable to diverse needs.
Is UpGuard easy to integrate with existing security tools?
UpGuard offers various integration options, aiming for seamless integration with your existing security infrastructure. However, the specific ease of integration will depend on your current setup.
How does UpGuard handle sensitive data during assessments?
UpGuard employs robust security measures to protect sensitive data throughout the assessment process, adhering to industry best practices and relevant regulations.
What kind of support does UpGuard provide to its users?
UpGuard typically offers various support channels, including documentation, online help resources, and potentially direct customer support depending on your subscription level.