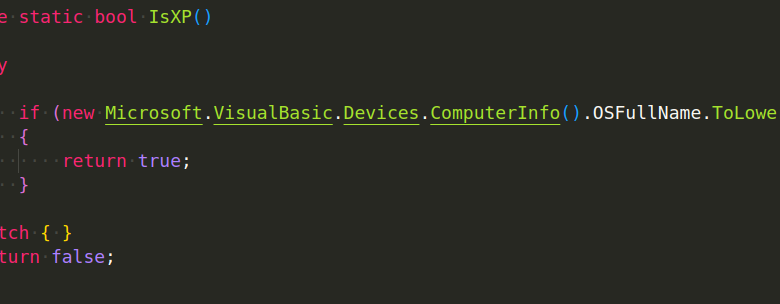
Asyncrat Loader Delivers Malware via JavaScript
Asyncrat Loader Delivers Malware via JavaScript – that’s a pretty scary headline, right? This insidious piece of code uses JavaScript, a language we all interact with daily, to sneak malware onto unsuspecting systems. It’s a clever attack, leveraging the very tools that make the internet function to wreak havoc. We’ll dive deep into how Asyncrat works, its sneaky techniques, and what you can do to protect yourself.
Imagine a seemingly harmless website, but lurking beneath the surface is Asyncrat. It silently downloads malicious payloads, potentially stealing your data, hijacking your system, or even turning your computer into a botnet node. The sophisticated nature of this attack vector highlights the ever-evolving threat landscape of online security. We’ll explore the specific JavaScript techniques used for obfuscation, the methods to bypass security measures, and the types of malware it typically delivers.
Asyncrat Loader Functionality
Asyncrat is a sophisticated malware loader, designed to evade detection and deliver a secondary payload. Its functionality relies on a multi-stage process, cleverly using JavaScript to execute malicious code within a victim’s browser environment. This allows it to bypass traditional antivirus solutions and gain a foothold on the system. The loader’s design emphasizes stealth and adaptability, making it a significant threat.Asyncrat Loader StagesThe Asyncrat loader operates through several distinct stages to ensure successful payload delivery.
Understanding these stages is crucial for effective defense. Each stage involves specific actions and techniques designed to increase the likelihood of successful infection.
JavaScript Exploitation
Asyncrat leverages JavaScript’s capabilities for several reasons. Firstly, JavaScript is ubiquitous in web browsers, making it an easily accessible execution environment. Secondly, the dynamic nature of JavaScript allows for obfuscation and code modification, hindering analysis and detection. Finally, its client-side execution means the initial infection vector often resides within the victim’s browser, making it more difficult to trace back to the original source.
The loader uses techniques such as base64 encoding and string manipulation to further obfuscate its malicious code, making it harder for security tools to identify.
Hypothetical Infection Scenario
Let’s consider a hypothetical scenario. A user visits a compromised website containing a malicious script. This script, unnoticed by the user, downloads the Asyncrat loader. The loader then decodes and executes its embedded JavaScript payload. This payload, in turn, establishes communication with a Command and Control (C2) server, receiving instructions for the next phase of the attack.
The Asyncrat loader’s use of Javascript to deliver malware highlights the critical need for secure coding practices. This is especially relevant when considering the rapid development capabilities offered by platforms like Domino, as discussed in this insightful article on domino app dev the low code and pro code future. While low-code solutions are beneficial, developers still need to be vigilant about potential security vulnerabilities introduced by external scripts, like the Asyncrat loader’s malicious Javascript.
The C2 server might then deliver a more destructive secondary payload, such as ransomware or a keylogger, depending on the attacker’s goals. The entire process happens discreetly, often without any visible indication to the user.
Malware Delivery Data Flow
The following table illustrates the data flow during a hypothetical Asyncrat infection:
| Step | Description |
|---|---|
| 1. Initial Infection | User visits a compromised website containing a malicious script that downloads the Asyncrat loader. |
| 2. Loader Execution | The downloaded Asyncrat loader, encoded in JavaScript, executes within the victim’s browser. |
| 3. Decoding and Obfuscation | The loader decodes its embedded JavaScript payload, often using techniques like base64 decoding and string manipulation to evade detection. |
| 4. C2 Communication | The decoded payload establishes a connection with a Command and Control (C2) server. |
| 5. Payload Delivery | The C2 server sends a secondary payload (e.g., ransomware, keylogger) to the victim’s machine. |
| 6. Payload Execution | The secondary payload is executed, initiating the malicious activity on the victim’s system. |
JavaScript Exploitation Techniques
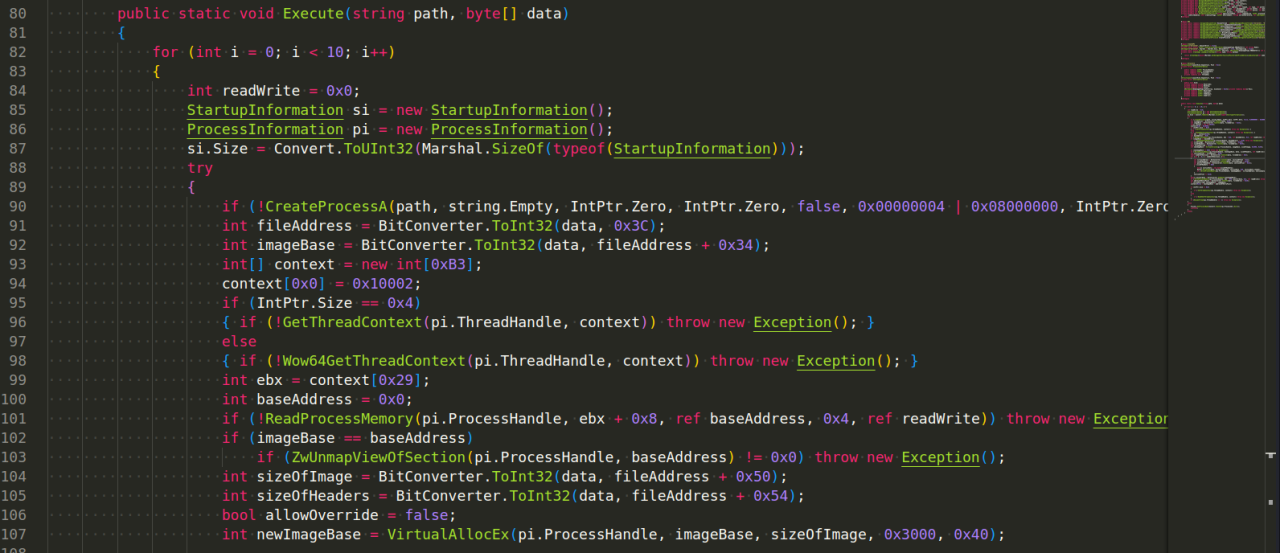
Asyncrat’s success hinges on its clever exploitation of JavaScript, a language ubiquitous in web browsers. Understanding its techniques reveals a sophisticated approach to evading security and compromising systems. This section delves into the specific methods Asyncrat employs for obfuscation, bypassing security measures, and exploiting browser vulnerabilities. We’ll also compare its strategies to those of other JavaScript-based malware, highlighting both similarities and differences.Asyncrat utilizes several JavaScript techniques to obfuscate its malicious code and evade detection by antivirus software and security tools.
A primary method is code packing, where the malicious script is compressed or encoded to reduce its size and make it harder to analyze. This often involves using base64 encoding, string manipulation, and control flow obfuscation to make the code appear nonsensical at first glance. Furthermore, Asyncrat employs polymorphism, altering its code structure slightly each time it runs, making it harder to create a signature-based detection mechanism.
Finally, the loader might leverage dynamic code generation, creating parts of the malicious code at runtime, further increasing the difficulty of static analysis.
Code Obfuscation Techniques
Asyncrat employs several layers of obfuscation to hinder reverse engineering and static analysis. These techniques include, but are not limited to, the use of heavily nested functions, meaningless variable names, and the extensive use of control flow obfuscation to obscure the actual logic of the malware. The use of packers and protectors further complicates analysis, often requiring unpacking and deobfuscation steps before the true nature of the malware can be understood.
For example, the code might employ a complex series of nested loops and conditional statements that serve no apparent purpose except to confuse analysis tools. The use of packed code also reduces the size of the payload, making it easier to transmit and evade detection by some security systems.
Bypassing Security Measures
Asyncrat’s ability to bypass security measures stems from its use of multiple evasion techniques. The malware might attempt to disable or circumvent browser security features, such as sandboxing mechanisms or content security policies (CSP). It might also leverage techniques to prevent the execution of scripts from being monitored or logged, potentially utilizing techniques to disable or interfere with browser developer tools.
Additionally, Asyncrat may use techniques like anti-debugging to hinder analysis efforts by security researchers. The malware may actively check for the presence of debuggers or virtual machines and alter its behavior accordingly.
Exploitation of Browser Vulnerabilities
While not explicitly relying on known zero-day exploits, Asyncrat could potentially leverage vulnerabilities in older or less-patched browser versions. These vulnerabilities might involve flaws in the JavaScript engine’s handling of specific data types or objects, allowing for memory corruption or arbitrary code execution. For example, a vulnerability in how the browser handles JSON data could be exploited to inject malicious code into the system.
The malware might also exploit vulnerabilities in the browser’s handling of plugins or extensions to gain access to system resources.
Comparison with Other JavaScript Malware
Compared to other JavaScript-based malware, Asyncrat exhibits a higher level of sophistication in its obfuscation techniques. While many JavaScript malware families rely on simpler techniques such as base64 encoding or simple code packing, Asyncrat goes beyond this, employing multiple layers of obfuscation and dynamic code generation. However, the core exploitation methods – leveraging browser vulnerabilities or manipulating DOM objects – are common across many JavaScript-based threats.
The key differentiator is the complexity and depth of Asyncrat’s evasion strategies. For instance, unlike simpler malware that might simply rely on a single vulnerability, Asyncrat may use multiple techniques in combination to maximize its chances of success.
Hypothetical Defense Mechanism
A robust defense against Asyncrat-like attacks requires a multi-layered approach. This would involve regularly updating browser software and plugins to patch known vulnerabilities, implementing strict Content Security Policies (CSP) to control the resources a webpage can access, and utilizing advanced sandboxing techniques to isolate potentially malicious code. Furthermore, employing runtime application self-protection (RASP) solutions that can monitor and block suspicious JavaScript activity within the browser would be crucial.
Finally, integrating advanced static and dynamic analysis techniques into security systems would help identify and neutralize obfuscated malware before it can execute. A combination of these preventative measures, along with regular security audits and updates, significantly reduces the likelihood of a successful Asyncrat infection.
Malware Payload Analysis: Asyncrat Loader Delivers Malware Via Javascript
Asyncrat, being a loader, doesn’t directly contain the malicious payload itself. Instead, it acts as a delivery mechanism, fetching and executing the actual malware from a remote server. This makes analysis more complex, as the specific malware delivered can vary greatly depending on the attacker’s goals and the current campaign. Understanding the typical payloads and their functionalities is crucial for effective defense.The types of malware delivered by Asyncrat often include information stealers, remote access trojans (RATs), and cryptocurrency miners.
These payloads are chosen for their ability to generate profit for the attacker or to compromise sensitive information. The sophistication of the delivered malware can range from simple scripts to highly advanced, polymorphic malware capable of evading detection.
Types of Malware Delivered by Asyncrat
Asyncrat’s modular nature allows for a wide variety of payloads. Common examples include information stealers designed to exfiltrate sensitive data like credentials, banking details, and personal information. RATs provide attackers with remote control over the infected system, allowing them to execute arbitrary commands, steal files, and monitor user activity. Cryptocurrency miners leverage the compromised system’s processing power to mine cryptocurrencies, generating profits for the attackers.
Capabilities and Functionalities of Delivered Malware
The capabilities of the malware delivered by Asyncrat are directly related to the type of malware deployed. For example, an information stealer might target specific browser data, including cookies, saved passwords, and autofill information. A RAT might enable keylogging, screen capture, and file manipulation. Cryptocurrency miners will typically consume significant system resources, leading to performance degradation. The attacker retains complete control over the functionality of the malware through its command-and-control (C2) server.
Impact on the Compromised System
The impact on a compromised system varies depending on the specific malware delivered. However, common consequences include data breaches, system instability due to resource consumption (especially with cryptocurrency miners), and potential loss of control over the system. The infected system may also become part of a botnet, used for distributed denial-of-service (DDoS) attacks or other malicious activities. The long-term consequences can be severe, including financial losses, reputational damage, and legal repercussions.
Examples of Malware Actions
The following list details some examples of actions a malware payload delivered via Asyncrat might execute:
The actions undertaken by the malware are determined by the attacker’s goals and the specific capabilities of the payload. These can range from relatively benign activities to highly destructive ones.
- Exfiltrating saved passwords from web browsers.
- Capturing screenshots of the user’s desktop.
- Monitoring keystrokes (keylogging).
- Downloading and executing additional malware.
- Mining cryptocurrency using the system’s CPU and GPU.
- Establishing a persistent backdoor for remote access.
- Sending stolen data to a remote server.
- Disabling security software.
Data Stolen by Malware
The data stolen can vary significantly but often includes sensitive information. The table below organizes some examples into categories:
This table illustrates the diverse range of data potentially targeted by malware delivered through Asyncrat. The specific data exfiltrated depends on the malware’s capabilities and the attacker’s objectives.
| Credentials | Financial Data | Personal Information | System Information |
|---|---|---|---|
| Website logins | Credit card numbers | Name, address, phone number | Operating system, IP address |
| Email accounts | Bank account details | Social Security number | Hardware specifications |
| Social media accounts | Bitcoin wallets | Date of birth | Installed software |
| VPN credentials | Online payment details | Driver’s license information | Network configuration |
Detection and Prevention Strategies
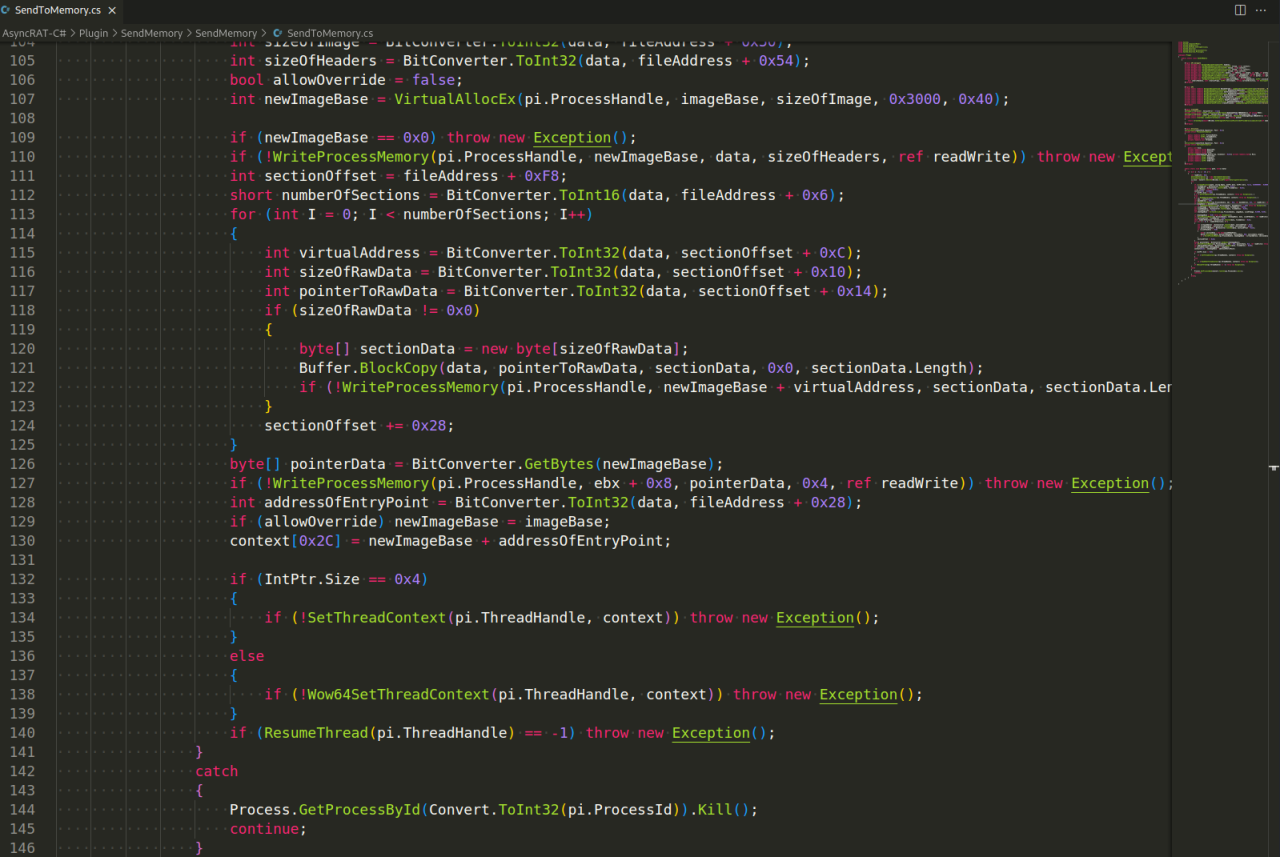
Successfully combating the Asyncrat loader requires a multi-layered approach encompassing proactive prevention and reactive detection. Understanding the characteristics of this malware and employing robust security measures are crucial in minimizing the risk of infection and mitigating its impact. This section details key strategies for identifying and preventing Asyncrat infections.
Effective detection and prevention hinge on recognizing suspicious activities and implementing strong security practices. A combination of proactive measures and reactive analysis is essential for a comprehensive defense.
Indicators of Compromise (IOCs), Asyncrat loader delivers malware via javascript
Identifying compromised systems early is vital. Several indicators can signal an Asyncrat infection. These IOCs can include unusual network connections to known malicious domains or IP addresses, the presence of suspicious files or registry keys associated with Asyncrat’s known file hashes or behavior, and unexpected processes running in the background. Furthermore, a sudden increase in outbound network traffic, particularly to obscure or previously unknown locations, might indicate malicious activity.
Unusual system performance degradation, such as slowdowns or crashes, could also be a sign of infection. Finally, observing the execution of JavaScript code from untrusted sources, especially those downloaded dynamically, warrants immediate investigation. A thorough analysis of system logs and network traffic is critical for uncovering these indicators.
Security Best Practices to Prevent Asyncrat Infections
Implementing strong security practices significantly reduces the likelihood of infection.
Proactive security measures are the first line of defense against malware like Asyncrat. Following these best practices can drastically minimize the attack surface and reduce the chances of compromise.
- Keep your operating system and software up-to-date with the latest security patches. Regular updates address known vulnerabilities exploited by malware like Asyncrat.
- Enable automatic software updates wherever possible. This ensures your systems are always protected against the latest threats.
- Use strong, unique passwords for all accounts. Avoid reusing passwords across different platforms.
- Practice safe browsing habits. Avoid clicking on suspicious links or downloading files from untrusted sources. Verify the legitimacy of websites before interacting with them.
- Enable two-factor authentication (2FA) wherever available. This adds an extra layer of security, making it significantly harder for attackers to gain access to your accounts.
- Regularly back up your important data. This allows you to restore your system to a clean state if an infection occurs.
- Educate users about phishing and social engineering tactics. These are common methods used to distribute malware.
- Employ a robust email filtering system to block malicious emails and attachments.
- Use a reputable antivirus and anti-malware solution and keep it updated. Regular scans are crucial for detecting and removing malware.
The Role of Antivirus Software and Firewalls
Antivirus software and firewalls play a crucial role in mitigating the Asyncrat threat. Antivirus software can detect and remove malicious files associated with Asyncrat, while firewalls can block malicious network connections attempting to communicate with command-and-control servers. Real-time protection offered by many modern security suites is vital for preventing infections before they can fully establish themselves. However, it’s important to note that no single security solution offers complete protection; a layered approach is essential.
Effectiveness of Sandboxing Techniques
Sandboxing is a powerful technique for analyzing potentially malicious code like Asyncrat in a controlled environment. By isolating the code within a virtual machine or container, analysts can observe its behavior without risking damage to the main system. This allows for safe analysis of the malware’s actions, including network connections, file system modifications, and registry changes. Effective sandboxing techniques can significantly aid in understanding Asyncrat’s functionality and identifying its IOCs.
However, sophisticated malware might employ techniques to evade detection even within a sandbox.
Network Traffic Analysis for Asyncrat Detection
Network traffic analysis can be a highly effective method for detecting Asyncrat activity. By monitoring network connections, security professionals can identify suspicious patterns, such as connections to known malicious domains or unusual communication patterns. Analyzing network packets can reveal the communication protocols used by Asyncrat, the data exchanged, and the target of the attack. Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) systems can be configured to alert on suspicious network traffic associated with Asyncrat’s behavior, providing real-time insights into potential threats.
The use of network forensics tools enables detailed investigation of past network activity to identify compromised systems and the extent of the breach.
Case Studies and Real-World Examples
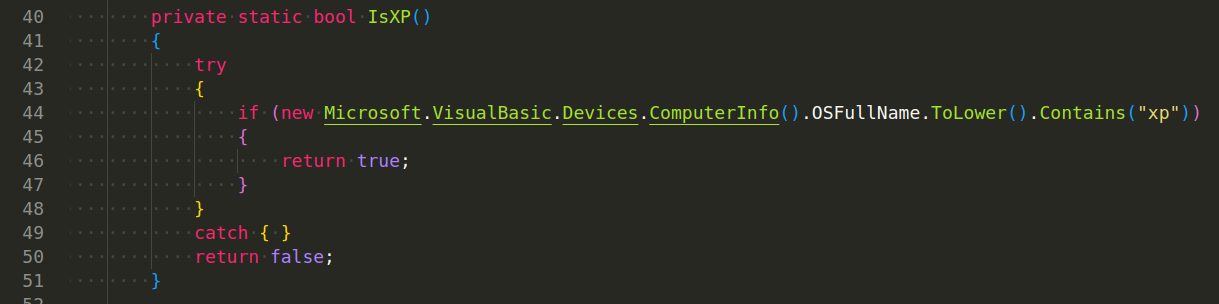
This section delves into a hypothetical case study illustrating a real-world Asyncrat infection scenario, highlighting the impact, remediation process, challenges encountered, and a proposed response plan. Understanding these aspects is crucial for effective cybersecurity preparedness.
Let’s consider a fictional mid-sized marketing agency, “AdVenture Corp,” with approximately 100 employees. Their primary vulnerability was a lack of up-to-date security patching across their employee workstations. Many employees also routinely accessed personal email and social media accounts on their work machines. This created a ripe environment for exploitation.
Asyncrat Infection at AdVenture Corp
AdVenture Corp experienced a significant Asyncrat infection originating from a seemingly innocuous email attachment. An employee, believing the attachment to be a client presentation, opened it, triggering the Asyncrat loader. The loader subsequently downloaded and executed a sophisticated piece of malware, encrypting sensitive client data and financial records. This led to a complete system shutdown affecting multiple departments. The malware also exfiltrated sensitive information, including client contact details, marketing strategies, and financial projections.
Impact of the Infection
The Asyncrat infection resulted in significant disruptions and financial losses for AdVenture Corp. The data encryption caused immediate operational paralysis, halting ongoing projects and impacting client deliverables. The exfiltration of sensitive data posed a significant legal and reputational risk. Estimates place the total cost of remediation, including data recovery, legal fees, and business interruption, at over $250,000.
Furthermore, the loss of client trust resulted in the cancellation of several lucrative contracts, leading to further financial setbacks. This incident also highlighted the importance of having robust incident response planning and security awareness training in place. A similar incident impacting a real-world organization, such as a hospital’s ransomware attack, could result in even greater consequences, including potential patient harm.
Identification and Remediation
The infection was initially identified through unusual system behavior and performance degradation. The IT team observed an abnormally high volume of outbound network traffic, indicating data exfiltration. Forensic analysis confirmed the presence of Asyncrat malware and the encryption of sensitive files. Remediation involved isolating affected systems, restoring data from backups (fortunately, regular backups were in place), and implementing comprehensive malware removal.
This process took several days, requiring collaboration between internal IT staff and external cybersecurity experts. A detailed investigation into the infection vector and subsequent compromise was undertaken. This involved reviewing email logs, system logs, and network traffic to understand the sequence of events leading to the infection.
Challenges During Investigation and Remediation
Several challenges hampered the investigation and remediation efforts. The sophistication of the malware made complete data recovery difficult. Some data was irretrievably lost. The complexity of the malware also made the analysis time-consuming, prolonging the recovery period. The lack of detailed security logs further complicated the investigation, hindering the accurate identification of the attack’s origin and extent.
The significant disruption to operations also placed significant pressure on the IT team and management.
Hypothetical Response Plan for Asyncrat Attacks
A robust response plan should include: proactive security measures (regular patching, security awareness training, robust email filtering), incident detection mechanisms (intrusion detection systems, security information and event management (SIEM) systems), incident response procedures (clear roles and responsibilities, communication protocols, escalation procedures), data recovery mechanisms (regular backups, offline backups, disaster recovery planning), and post-incident analysis and remediation (forensic investigation, vulnerability assessments, security improvements).
This comprehensive approach, tailored to the specific organization’s needs and risk profile, would provide a strong defense against future Asyncrat or similar attacks. The plan should be regularly tested and updated to ensure its effectiveness in responding to evolving threats. The plan should also include provisions for communication with stakeholders (employees, clients, regulatory bodies) during and after the incident.
Last Word
The Asyncrat loader is a stark reminder that the digital world isn’t always as safe as it seems. Its clever use of JavaScript to deliver malware underscores the need for constant vigilance and proactive security measures. Understanding how Asyncrat operates, its attack vectors, and the potential consequences is crucial for both individuals and organizations. By staying informed and implementing robust security practices, we can minimize our vulnerability to these sophisticated threats.
Remember, knowledge is the best defense in the ongoing battle against cybercrime.
Commonly Asked Questions
What specific types of data might Asyncrat steal?
Asyncrat could steal a wide range of data, including login credentials, financial information, personal documents, and intellectual property. The specific data targeted depends on the malware payload delivered.
Can antivirus software detect and block Asyncrat?
Many modern antivirus solutions can detect and block Asyncrat, but it’s crucial to keep your software updated with the latest virus definitions. A multi-layered approach to security is always recommended.
How effective are firewalls in preventing Asyncrat infections?
Firewalls can help by blocking malicious network traffic associated with Asyncrat, but they’re not foolproof. They are a vital part of a layered security strategy, working in conjunction with other protective measures.
Are there any telltale signs of an Asyncrat infection?
Indicators of compromise (IOCs) can include unusual system performance, unexplained network activity, and the presence of unknown files or processes. Regular system monitoring is crucial.





